Application of Polling Scheduling in Mobile Edge Computing
Abstract
1. Introduction
- We propose a two-level priority exhaustive service model, and the parameters of normal nodes are asymmetrical, corresponding to the 3rd section of this paper.
- We computed specific expressions for the model’s average queue length and polling period. We calculated the average delay with an approximate analysis of periodic query way, corresponding to this paper’s fourth and fifth sections.
- We designed a Monte Carlo experiment with a small error between the theoretical and experimental values for many repetitions, corresponding to the 7th section of this paper.
2. Literature Review
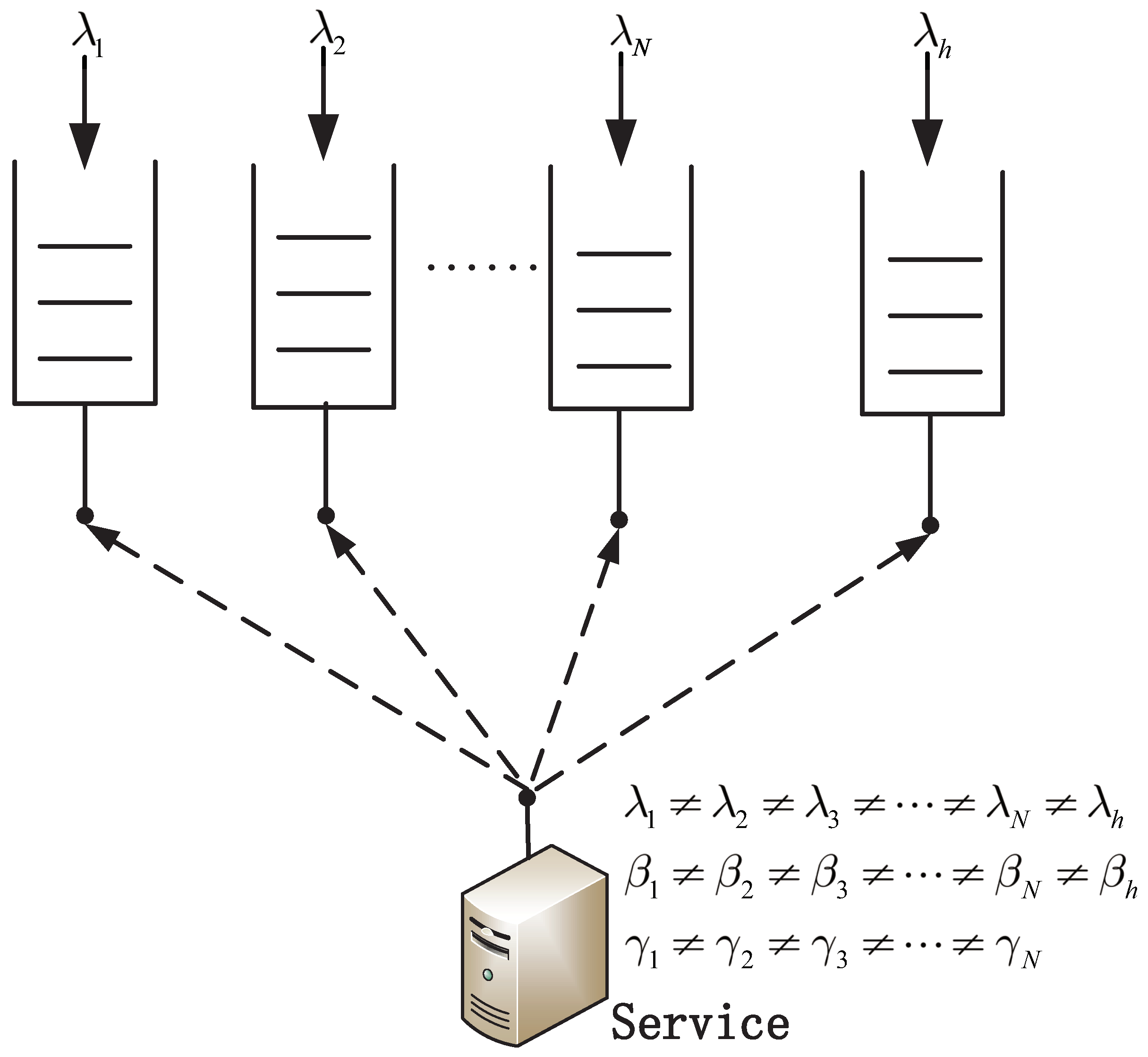
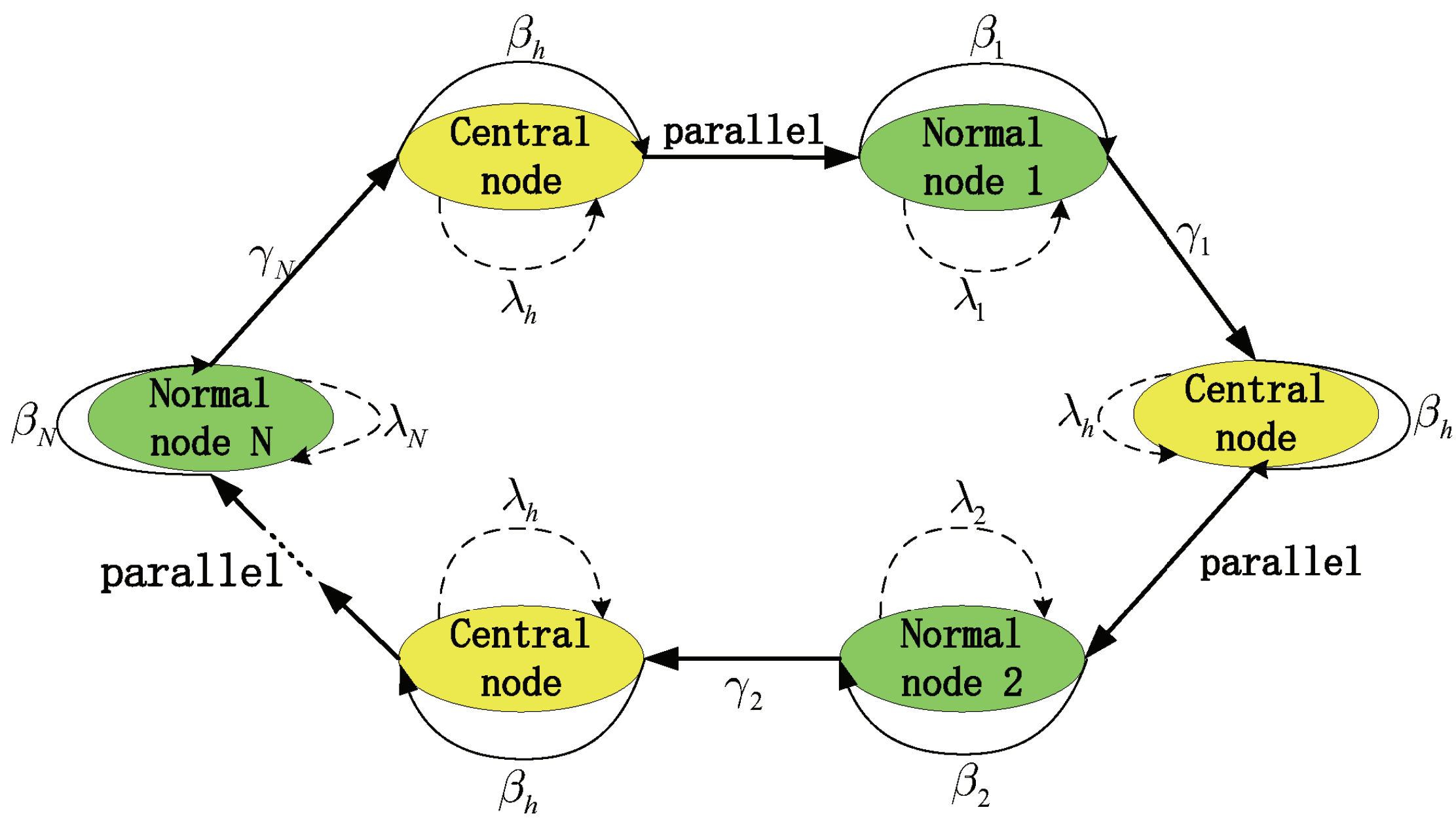
3. System Model
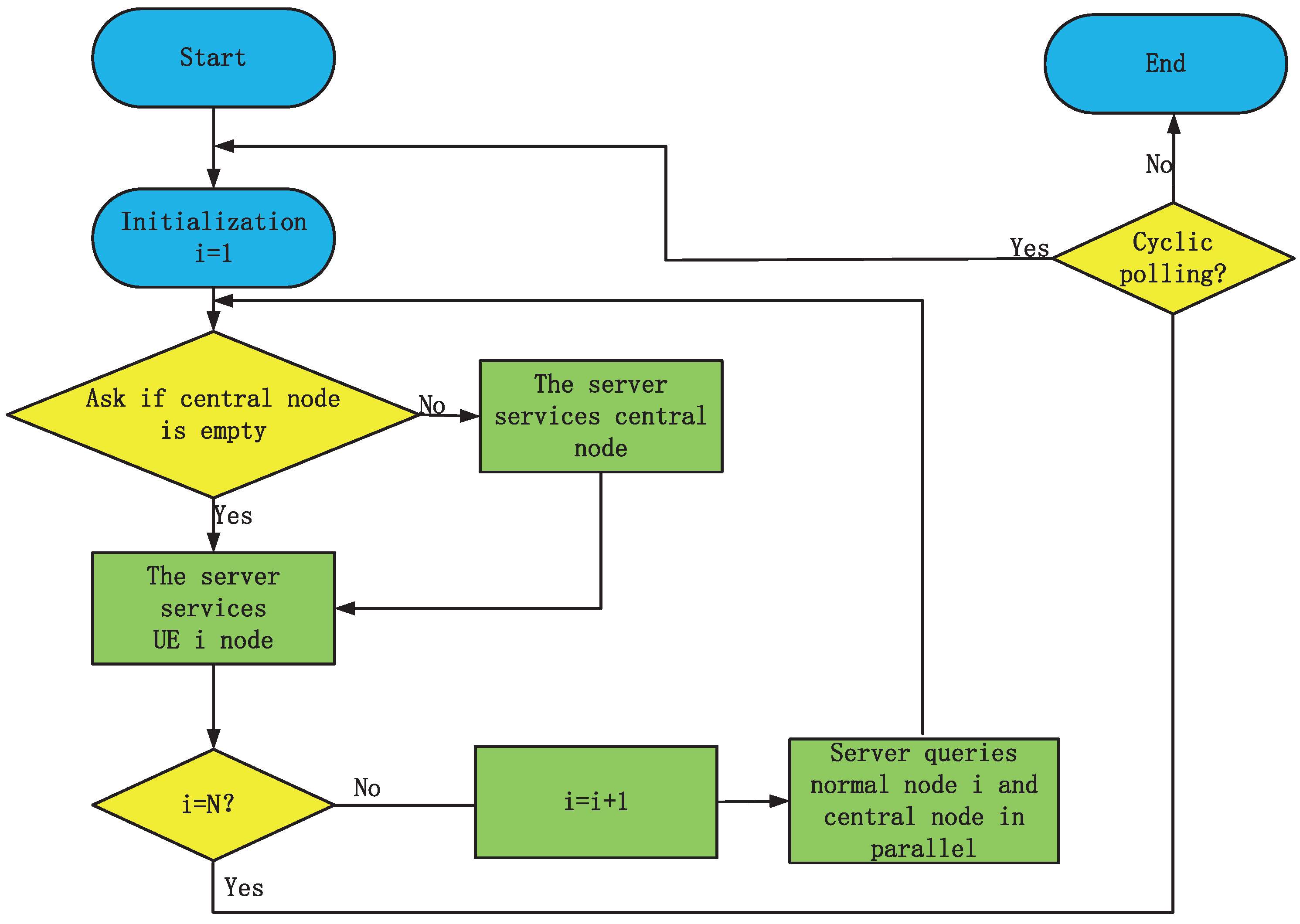
- Server initialization
- Edge servers use parallel scheduling to query the central node and node i
- Edge server service center node if the central node needs to process data
- Server servicing of node i
- Let , and return to step (2) if , else step (1)
4. System Model Analysis
4.1. Variable Definitions
4.2. System Conditions
4.3. Mathematical Models
- Each information packet arrives at the nodes independently and Poisson distribution. The probability-generating function of normal node is , and the mean and variances are and . And the central node, the probability-generating function is , and the mean and variances are and
- The time for the server to serve any normal nodes is independent and Poisson distribution, and its probability-generating function is , the mean is , and the variance is . And the central node, the probability-generating function is , the mean is , and the variance is
- The switch times of the server from node i to another node are independent and Poisson distribution. The probability-generating function is , the mean is , and its variance is
- Each data is First Input First Output (FIFO)
- Sufficient node capacity, no data overflow [45]
5. Analysis of System Variables
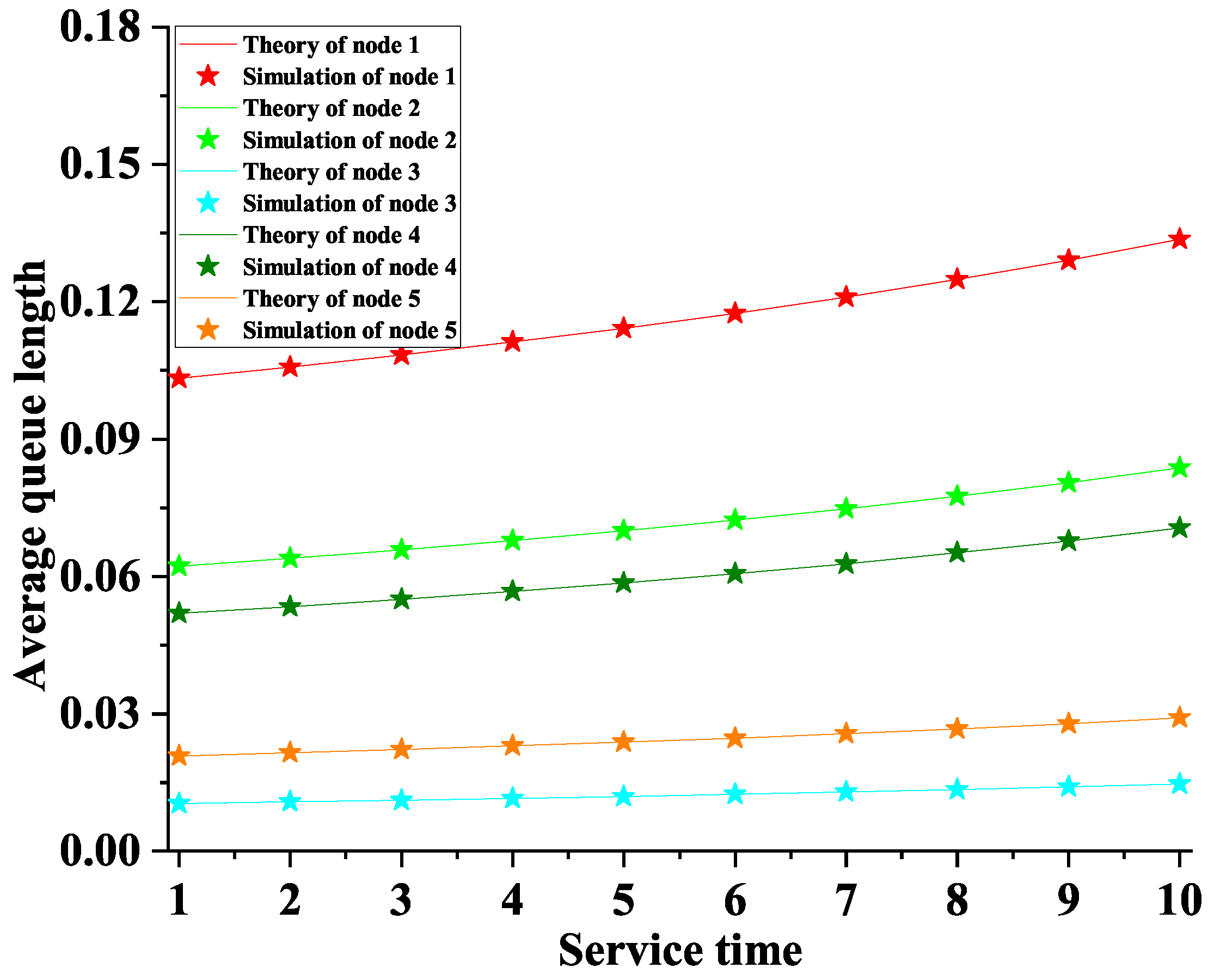
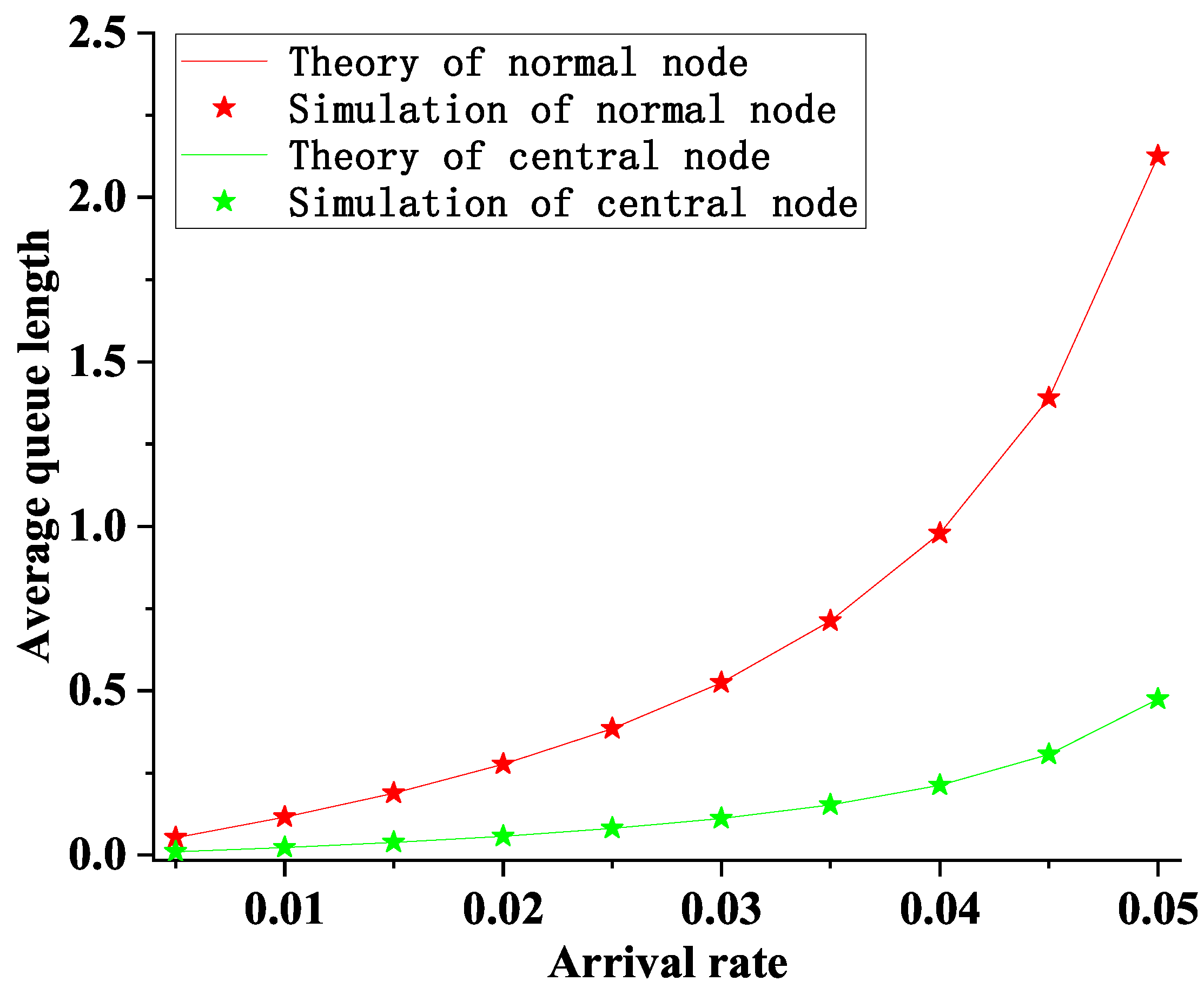
5.1. The Average Queue Length
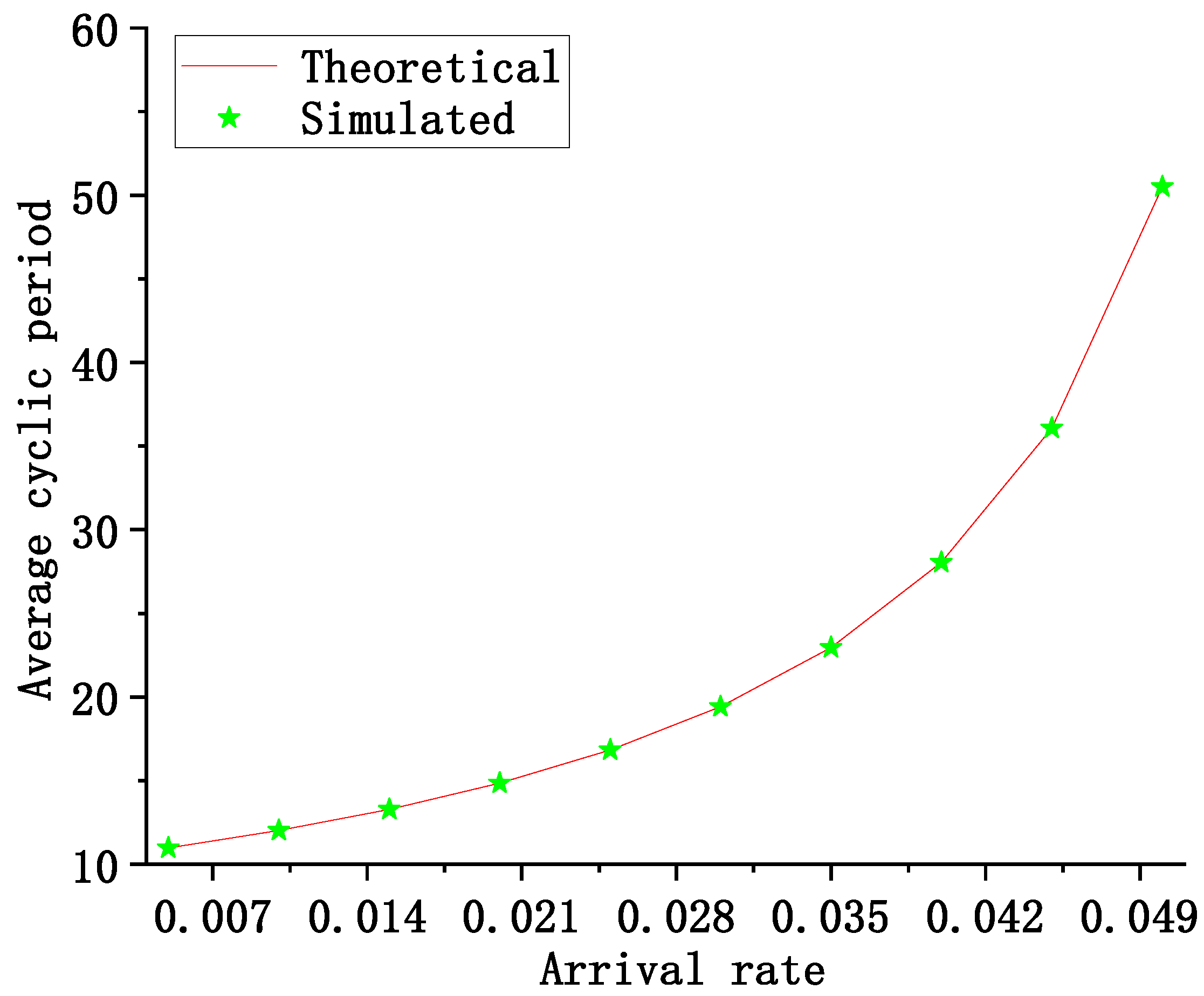
5.2. The Average Cycle
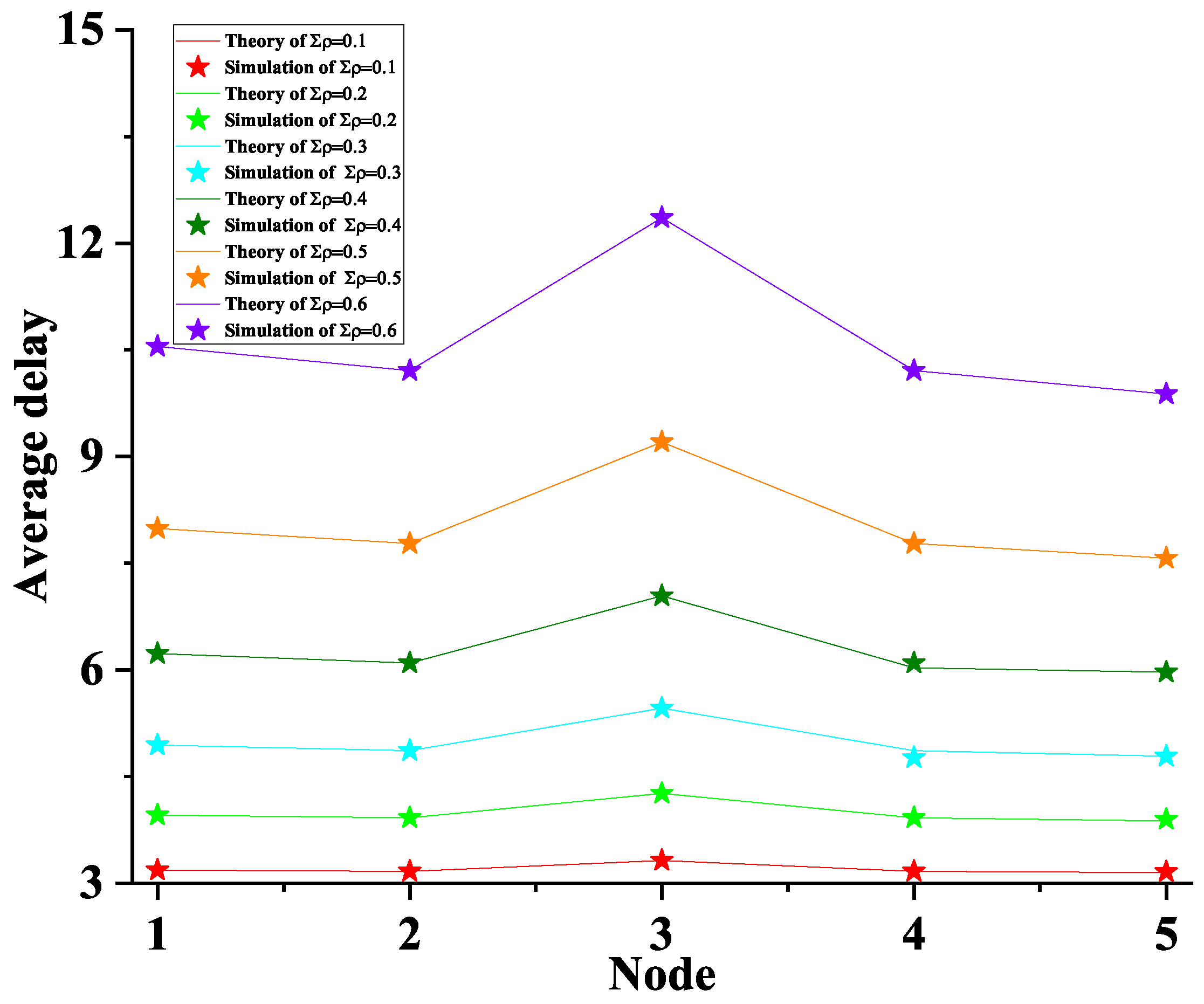
5.3. The Average Delay
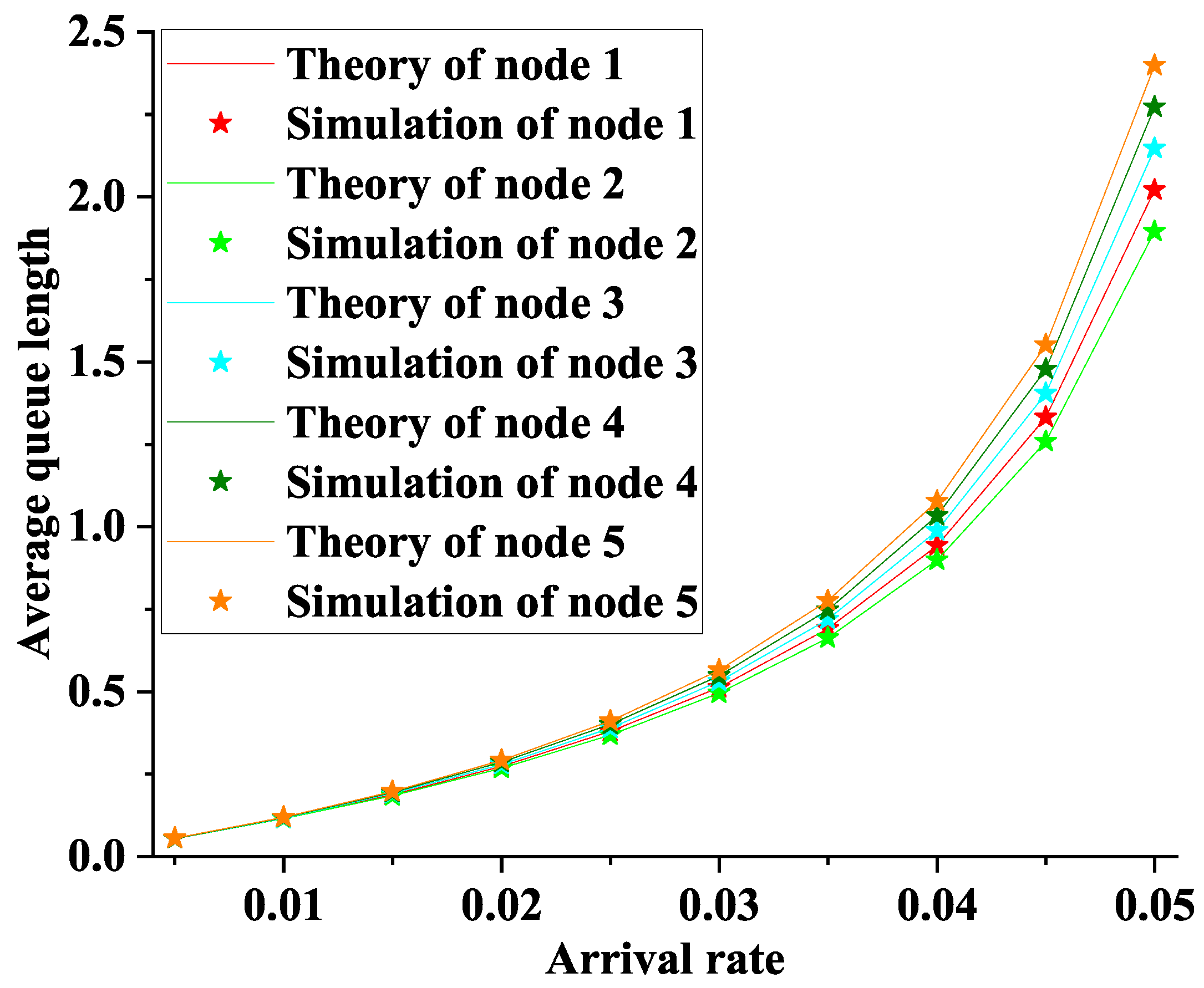
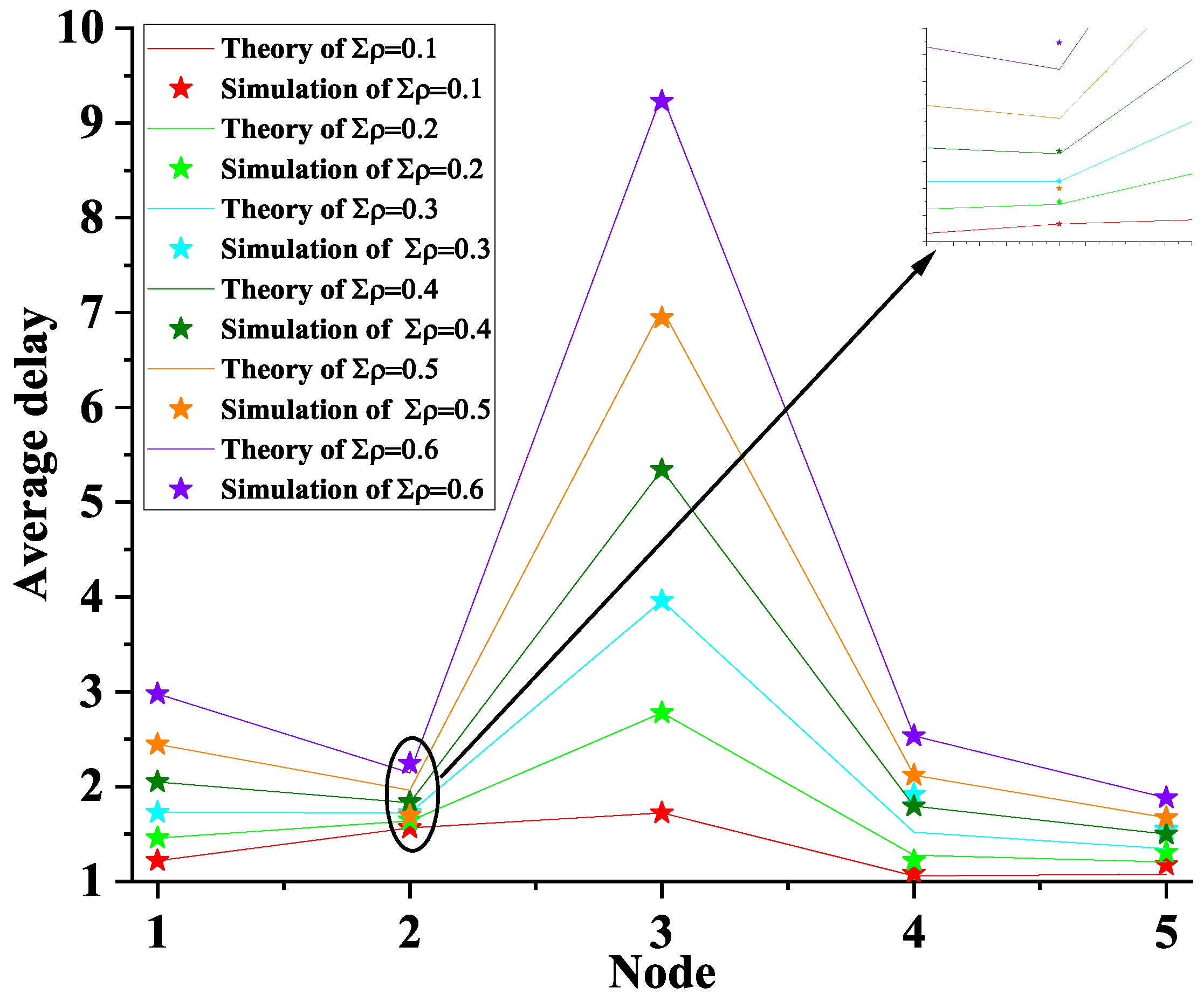
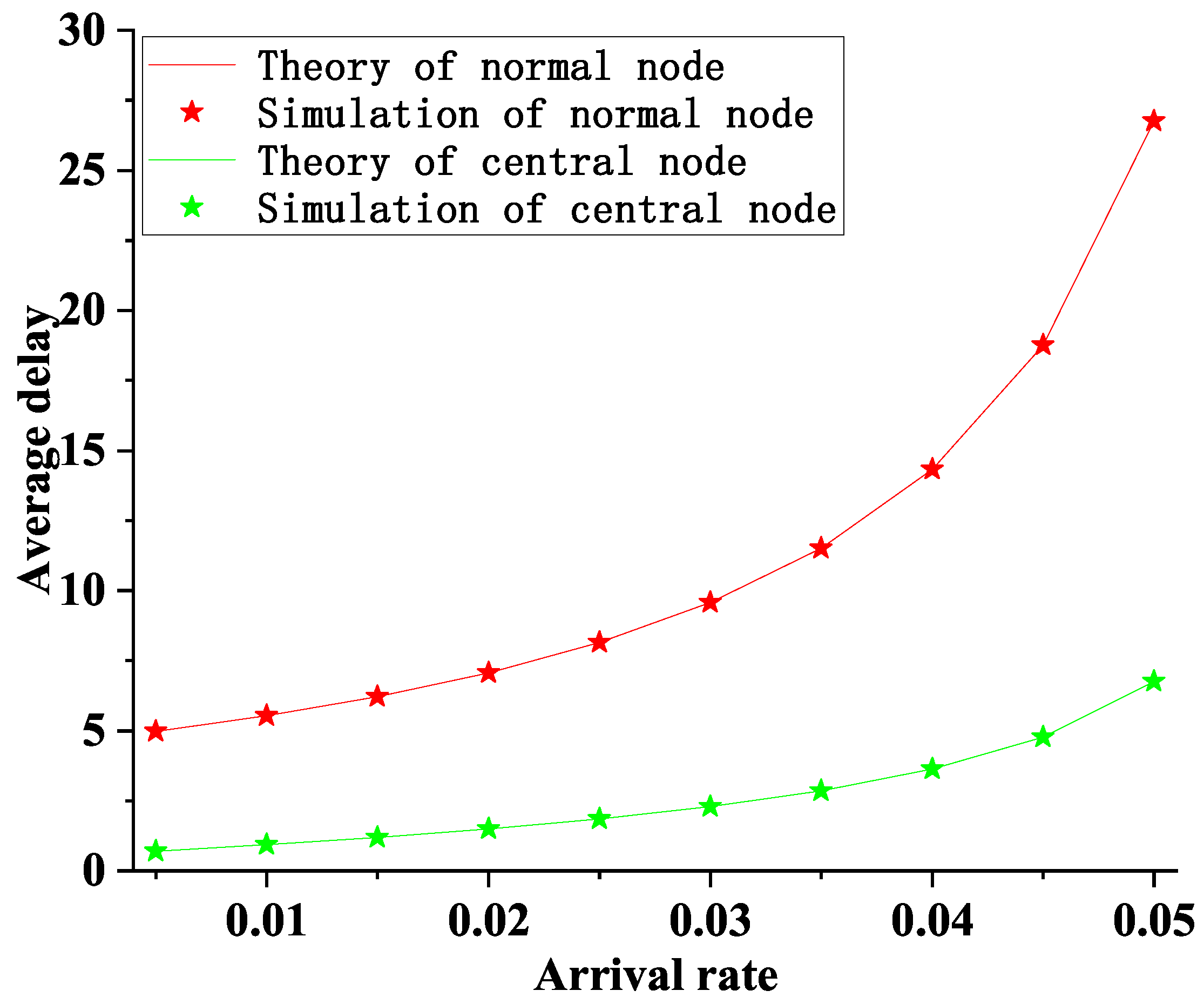
6. Simulation
- Each information packet of the nodes is asymmetric
- Each information packet arrives at the nodes independently and Poisson process
- The experiment was repeated 300,000 times, and the mean was taken as the statistic.
- The system remains stable under the condition of
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Zhang, J.; Letaief, K.B. Mobile edge intelligence and computingfor the internet of vehicles. Proc. IEEE 2020, 108, 246–261. [Google Scholar] [CrossRef]
- Chen, Y.; Zhao, F.; Chen, X.; Wu, Y. Efficient Multi-Vehicle Task Offloading for Mobile Edge Computing in 6G Networks. IEEE Trans. Veh. Technol. 2022, 71, 4584–4595. [Google Scholar] [CrossRef]
- Zhao, H.; Deng, S.; Liu, Z.; Yin, J.; Dustdar, S. Distributed Redundant Placement for Microservice-based Applications at the Edge. IEEE Trans. Serv. Comput. 2022, 15, 1732–1745. [Google Scholar] [CrossRef]
- Mao, S.; Wu, J.; Liu, L.; Lan, D.; Taherkordi, A. Energy-Efficient Cooperative Communication and Computation for Wireless Powered Mobile-Edge Computing. IEEE Syst. J. 2022, 16, 287–298. [Google Scholar] [CrossRef]
- Chen, X.; Zhang, J.; Lin, B.; Chen, Z.; Wolter, K.; Min, G. Energy-Efficient Offloading for DNN-Based Smart IoT Systems in Cloud-Edge Environments. IEEE Trans. Parallel Distrib. Syst. 2022, 33, 683–697. [Google Scholar] [CrossRef]
- Wang, X.; Li, J.; Ning, Z.; Song, Q.; Guo, L.; Guo, S.; Obaidat, M.S. Wireless powered mobile edge computing networks: A survey. Acm Comput. Surv. 2023, 55, 263. [Google Scholar] [CrossRef]
- Hou, P.; Li, B.; Wang, Z.; Ding, H. Joint hierarchical placement and configuration of edge servers in C-V2X. Hoc Netw. 2022, 131, 102842. [Google Scholar]
- Ghafoor, S.; Boujnah, N.; Rehmani, M.H.; Davy, A. MAC Protocols for Terahertz Communication: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2020, 22, 2236–2282. [Google Scholar] [CrossRef]
- Su, H.; Pan, M.-S.; Chen, H.; Liu, X. MDP-Based MAC Protocol for WBANs in Edge-Enabled eHealth Systems. Electronics 2023, 12, 947. [Google Scholar] [CrossRef]
- Hu, L.; Wang, W.; Zhong, S.; Guo, H.; Li, J.; Pan, Y. APP-Aware MAC Scheduling for MEC-Backed TDM-PON Mobile Fronthaul. IEEE Commun. Lett. 2023, 27, 1175–1179. [Google Scholar] [CrossRef]
- Li, B.; Hou, F.; Yang, G.; Zhao, H.; Chen, S. Data Analysis-Oriented Stochastic Scheduling for Cost Efficient Resource Allocation in NFV Based MEC Network. IEEE Trans. Veh. Technol. 2023, 72, 6695–6708. [Google Scholar] [CrossRef]
- Tian, J.; Wang, D.; Zhang, H.; Wu, D. Service Satisfaction-Oriented Task Offloading and UAV Scheduling in UAV-Enabled MEC Networks. IEEE Trans. Wirel. Commun. 2023. [Google Scholar] [CrossRef]
- Jiang, X.; Hou, P.; Zhu, H.; Li, B.; Wang, Z.; Ding, H. Dynamic and intelligent edge server placement based on deep reinforcement learning in mobile edge computing. Hoc Netw. 2023, 145, 103172. [Google Scholar] [CrossRef]
- Lin, L.; Zhou, W.A.; Yang, Z.; Liu, J. Deep reinforcement learning-based task scheduling and resource allocation for NOMA-MEC in Industrial Internet of Things. Peer-Peer Netw. Appl. 2023, 16, 170–188. [Google Scholar] [CrossRef]
- Niu, L.; Chen, X.; Zhang, N.; Zhu, Y.; Yin, R.; Wu, C.; Cao, Y. Multi-Agent Meta-Reinforcement Learning for Optimized Task Scheduling in Heterogeneous Edge Computing Systems. IEEE Internet Things J. 2023, 10, 10519–10531. [Google Scholar] [CrossRef]
- Al-Hammadi, I.; Li, M.; Islam, S.M.N. Independent tasks scheduling of collaborative computation offloading for SDN-powered MEC on 6G networks. Soft Comput. 2023, 27, 9593–9617. [Google Scholar] [CrossRef]
- Qin, Z.; Wang, H.; Wei, Z.; Qu, Y.; Xiong, F.; Dai, H.; Wu, T. Task Selection and Scheduling in UAV-Enabled MEC for Reconnaissance With Time-Varying Priorities. IEEE Internet Things J. 2021, 8, 17290–17307. [Google Scholar] [CrossRef]
- Lin, D.; Hu, S.; Gao, Y.; Tang, Y. Optimizing MEC Networks for Healthcare Applications in 5G Communications With the Authenticity of Users’ Priorities. IEEE Access 2019, 7, 88592–88600. [Google Scholar] [CrossRef]
- Jiang, L.; Chang, X.; Mišić, J.; Mišić, V.B.; Bai, J. Understanding MEC empowered vehicle task offloading performance in 6G networks. Peer-to-Peer Netw. Appl. 2022, 15, 1090–1104. [Google Scholar] [CrossRef]
- Zhou, W.; Fan, L.; Zhou, F.; Li, F.; Lei, X.; Xu, W.; Nallanathan, A. Priority-Aware Resource Scheduling for UAV-Mounted Mobile Edge Computing Networks. IEEE Trans. Veh. Technol. 2023, 72, 9682–9687. [Google Scholar] [CrossRef]
- Paymard, P.; Mokari, N. Resource allocation in PD-NOMA–based mobile edge computing system: Multiuser and multitask priority. Trans. Emerg. Telecommun. Technol. 2022, 33, e3631. [Google Scholar] [CrossRef]
- Shukla, P.; Pandey, S.; Agarwal, D. An Efficient Offloading Technique using DQN for MEC-IoT Networks. In Proceedings of the 2023 6th International Conference on Information Systems and Computer Networks (ISCON), Mathura, India, 3–4 March 2023; pp. 1–7. [Google Scholar] [CrossRef]
- Sharif, Z.; Jung, L.T.; Ayaz, M.; Yahya, M.; Pitafi, S. Priority-based task scheduling and resource allocation in edge computing for health monitoring system. J. King Saud Univ.-Comput. Inf. Sci. 2023, 35, 544–559. [Google Scholar] [CrossRef]
- Boon, M.A.A.; van der Mei, R.D.; Winands, E.M.M. Applications of polling systems. Appl. Poll. Syst. 2011, 16, 67–82. [Google Scholar] [CrossRef]
- Suman, R.; Krishnamurthy, A. Analysis of tandem polling queues with finite buffers. Ann. Oper. Res. 2020, 293, 343–369. [Google Scholar] [CrossRef]
- Suman, R. Krishnamurthy, A. Analysis of two-station polling queues with setups using continuous time markov chain. arXiv 2022, arXiv:2202.10045. [Google Scholar] [CrossRef]
- Lê, A.T. A Tandem Queueing Model to Optimize the Efficiency of Public Administrative Services. Master’s Thesis, Vietnam National University, Hanoi, Vietnam, 2021. [Google Scholar]
- Miculescu, D.; Karaman, S. Polling-Systems-Based Autonomous Vehicle Coordination in Traffic Intersections With No Traffic Signals. IEEE Trans. Autom. Control 2020, 65, 680–694. [Google Scholar] [CrossRef]
- Li, S.; Shu, K.; Chen, C. Planning and Decision-making for Connected Autonomous Vehicles at Road Intersections: A Review. Chin. J. Mech. Eng. 2021, 34, 133. [Google Scholar] [CrossRef]
- Talamali, M.S.; Saha, A.; Marshall, J.A.; Reina, A. When less is more: Robot swarms adapt better to changes with constrained communication. Sci. Robot. 2021, 6, eabf1416. [Google Scholar] [CrossRef]
- Zakir, R.; Dorigo, M.; Reina, A. Robot Swarms Break Decision Deadlocks in Collective Perception Through Cross-Inhibition. In Swarm Intelligence; ANTS 2022; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2022; Volume 13491. [Google Scholar]
- Nasser, N.; Fadlullah, Z.M.; Fouda, M.M.; Ali, A.; Imran, M. A lightweight federated learning based privacy preserving B5G pandemic response network using unmanned aerial vehicles: A proof-of-concept. Comput. Netw. 2022, 205, 108672. [Google Scholar] [CrossRef]
- Chour, K.; Reddinger, J.P.; Dotterweich, J.; Childers, M.; Humann, J.; Rathinam, S.; Darbha, S. An agent-based modeling framework for the multi-UAV rendezvous recharging problem. Robot. Auton. Syst. 2023, 166, 104442. [Google Scholar] [CrossRef]
- Kumar, S.; Raw, R.S.; Bansal, A. LoCaL: Link-optimized cone-assisted location routing in flying ad hoc networks. Int. J. Commun. Syst. 2023, 36, e5375. [Google Scholar] [CrossRef]
- Yang, Z.; Zheng, H.; Ding, H. Research on polling MAC protocol for multi-robot system in WLAN. Appl. Res. Comput. 2022, 39, 1178–1182. [Google Scholar] [CrossRef]
- Wang, Z.; Ding, H.; Li, B.; Bao, L.; Yang, Z. An energy efficient routing protocol based on improved artificial bee colony algorithm for wireless sensor networks. IEEE Access 2020, 8, 133577–133596. [Google Scholar] [CrossRef]
- Zhou, W.; Xia, J.; Zhou, F.; Fan, L.; Lei, X.; Nallanathan, A.; Karagiannidis, G.K. Profit maximization for cache-enabled vehicular mobile edge computing networks. IEEE Trans. Veh. Technol. 2023. [Google Scholar] [CrossRef]
- Boxma, O.J.; Kella, O.; Kosinski, K.M. Queue lengths and workloads in polling systems. Oper. Res. Lett. 2011, 39, 401–405. [Google Scholar] [CrossRef]
- Chu, Y.Q.; Liu, Z.M. The impact of priority policy in a two queue markovian polling system with multi-class priorities. In Proceedings of the 12th International Conference on Queueing Theory and Network Applications, Qinhuangdao, China, 21–23 August 2017; Springer: China, Switzerland, 2017; pp. 282–296. [Google Scholar]
- Mu, W.-H.; Bao, L.-Y.; Ding, H.-W.; Zhao, Y.-F. An exact analysis of discrete time two-level priority polling system based on multi-times gated service policy. Acta Electron. Sin. 2018, 46, 276–280. [Google Scholar]
- Guan, Z.; Yang, Z.-J.; He, M.; Qian, W.-H. Study on the delay performance of station dependent two-level polling systems. Acta Autom. Sin. 2016, 42, 1207–1214. [Google Scholar]
- Yang, Z.; Mao, L.; Yan, B.; Wang, J.; Gao, W. Performance analysis and prediction of asymmetric two-level priority polling system based on BP neural network. Appl. Soft Comput. 2021, 99, 106880. [Google Scholar] [CrossRef]
- Yang, Z.J.; Zhao, D.F.; Ding, H.W.; Zhao, Y.F. Research on two-class priority based polling system. Acta Electron. Sin. 2009, 37, 1452–1456. [Google Scholar]
- Siddiqui, S.; Ghani, S. Towards dynamic polling: Survey and analysis of channel polling mechanisms for wireless sensor networks. In Proceedings of the 2016 International Conference on Intelligent Systems Engineering, Islamabad, Pakistan, 15–17 January 2016; IEEE: Piscataway Township, NJ, USA, 2016; pp. 356–363. [Google Scholar]
- Rehman, M.U.; Drieberg, M.; Badruddin, N. Probabilistic polling MAC protocol with unslotted CSMA for wireless sensor networks (WSNs). In Proceedings of the 2014 5th International Conference on Intelligent and Advanced Systems, Kuala Lumpur, Malaysia, 3–5 June 2014; IEEE: Piscataway Township, NJ, USA, 2014; pp. 1–5. [Google Scholar]
- Siddiqui, S.; Ghani, S.; Khan, A.A. ADP-MAC: An adaptive and dynamic polling based mac protocol for wireless sensor networks. IEEE Sens. J. 2018, 18, 860–874. [Google Scholar] [CrossRef]
- Zhao, D.; Zheng, S. Analysis of a polling model with exhaustive service. Acta Electron. Sin. 1994, 22, 102–107. [Google Scholar]
- He, M.; Guan, Z.; Bao, L.; Ge, J. Mean cyclic period analysis of polling access control for wireless sensor networks. Chin. J. Sci. Instrum. 2016, 37, 2637–2644. [Google Scholar]



| Literature | Asymmetrical | Machine Learning | Priority | Indicators of Measurement | Accurate Calculation |
|---|---|---|---|---|---|
| [10] | No | No | No | channel utilization, the system throughput | No |
| [11] | No | Yes | No | Packet blockage rate and average delay | No |
| [12] | No | No | No | Lyapunov function of queue backlog of operation functions and overall cost of communication and computing in the MEC | No |
| [13] | No | Yes | Yes | Server utilization and number of users | No |
| [14] | No | Yes | No | Server utilization | No |
| [15] | No | Yes | No | Average delay and | No |
| [16] | No | Yes | No | Average task queuing delay per time slot | No |
| [17] | No | Yes | No | Total execution time and Average task failure | No |
| Our work | Yes | No | Yes | Average queue length and average polling period, and average delay | Yes |
| Variables | Definition |
|---|---|
| i or j or k | Normal nodes |
| h | Central node |
| The server switching time from node i to other nodes | |
| The time of service provided by server to node i | |
| The time of service provided by the server to the central node | |
| The amount of data entering the node j within time | |
| The amount of data entering the central node within time | |
| The amount of data entering the node j within time | |
| The amount of data entering the node within time | |
| The amount of data entering the node j within time | |
| The amount of data entering the central node within time |
| i | |||
|---|---|---|---|
| Node | Arrival Rate | Service Time | Switch Time |
| 1 | 0.01 | 4 | 2 |
| 2 | 0.006 | 5 | 3 |
| 3 | 0.001 | 3 | 1.5 |
| 4 | 0.005 | 2 | 1.7 |
| 5 | 0.002 | 1 | 1.9 |
| h | 0.008 | 1 | 0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, X.; Yang, Z.; Ding, H. Application of Polling Scheduling in Mobile Edge Computing. Axioms 2023, 12, 709. https://doi.org/10.3390/axioms12070709
Wang X, Yang Z, Ding H. Application of Polling Scheduling in Mobile Edge Computing. Axioms. 2023; 12(7):709. https://doi.org/10.3390/axioms12070709
Chicago/Turabian StyleWang, Xiong, Zhijun Yang, and Hongwei Ding. 2023. "Application of Polling Scheduling in Mobile Edge Computing" Axioms 12, no. 7: 709. https://doi.org/10.3390/axioms12070709
APA StyleWang, X., Yang, Z., & Ding, H. (2023). Application of Polling Scheduling in Mobile Edge Computing. Axioms, 12(7), 709. https://doi.org/10.3390/axioms12070709






