Design of IP Camera Access Control Protocol by Utilizing Hierarchical Group Key
Abstract
:1. Introduction
2. Related Work
2.1. IP Camera System
2.2. Security Requirements of Group Keys Management
2.3. Centralized Group Key Method
2.3.1. Logical Key Hierarchy (LKH)
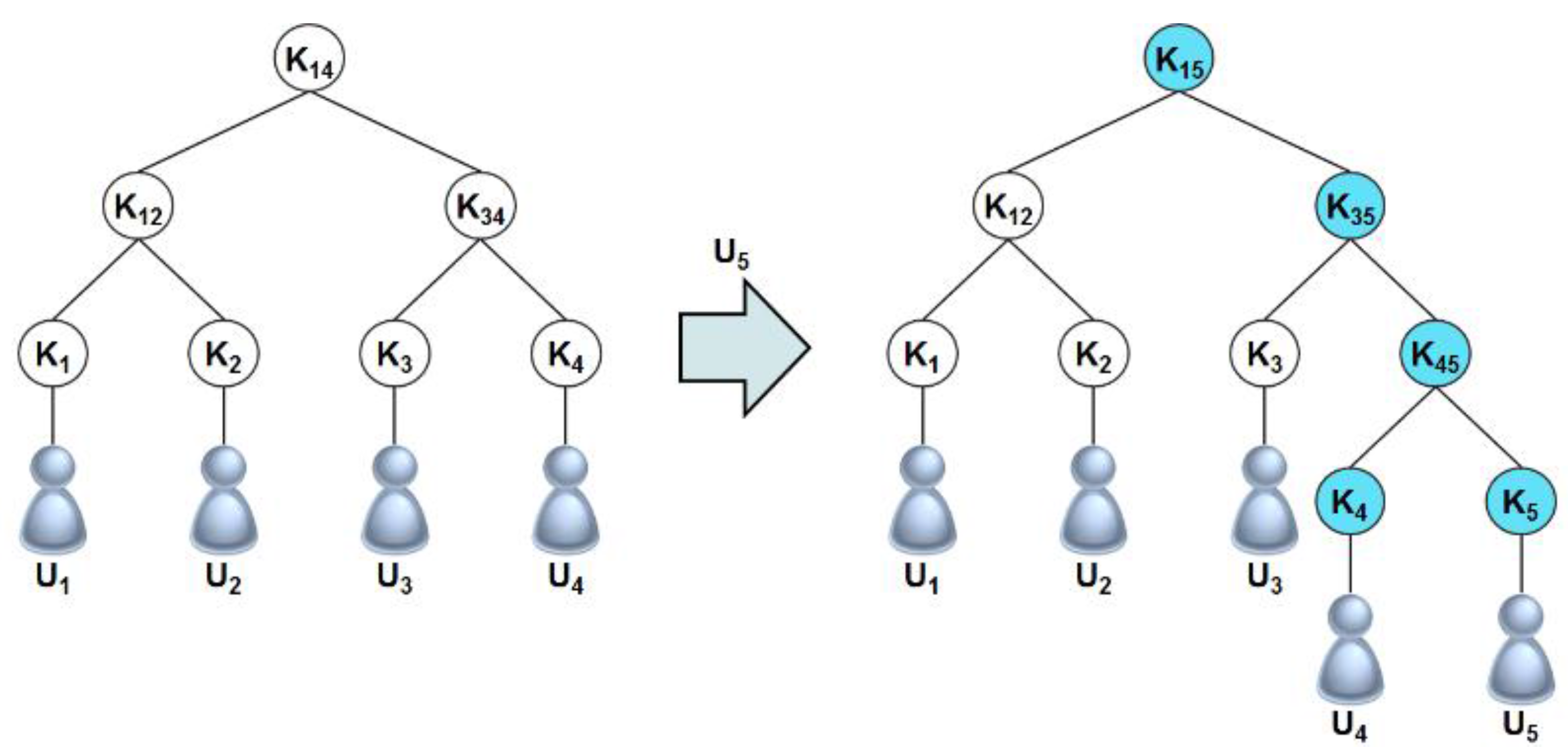
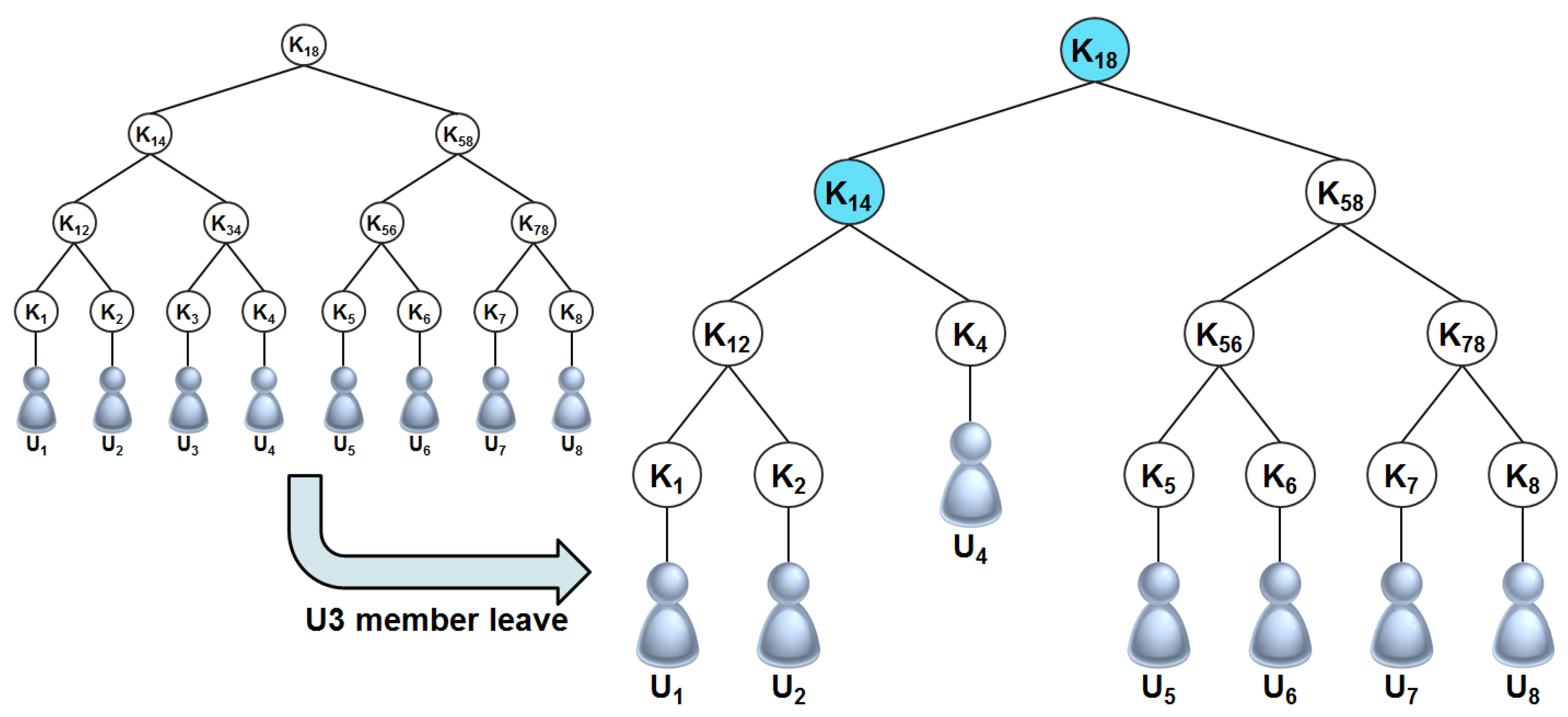
2.3.2. One Way Function Tree (OFT)
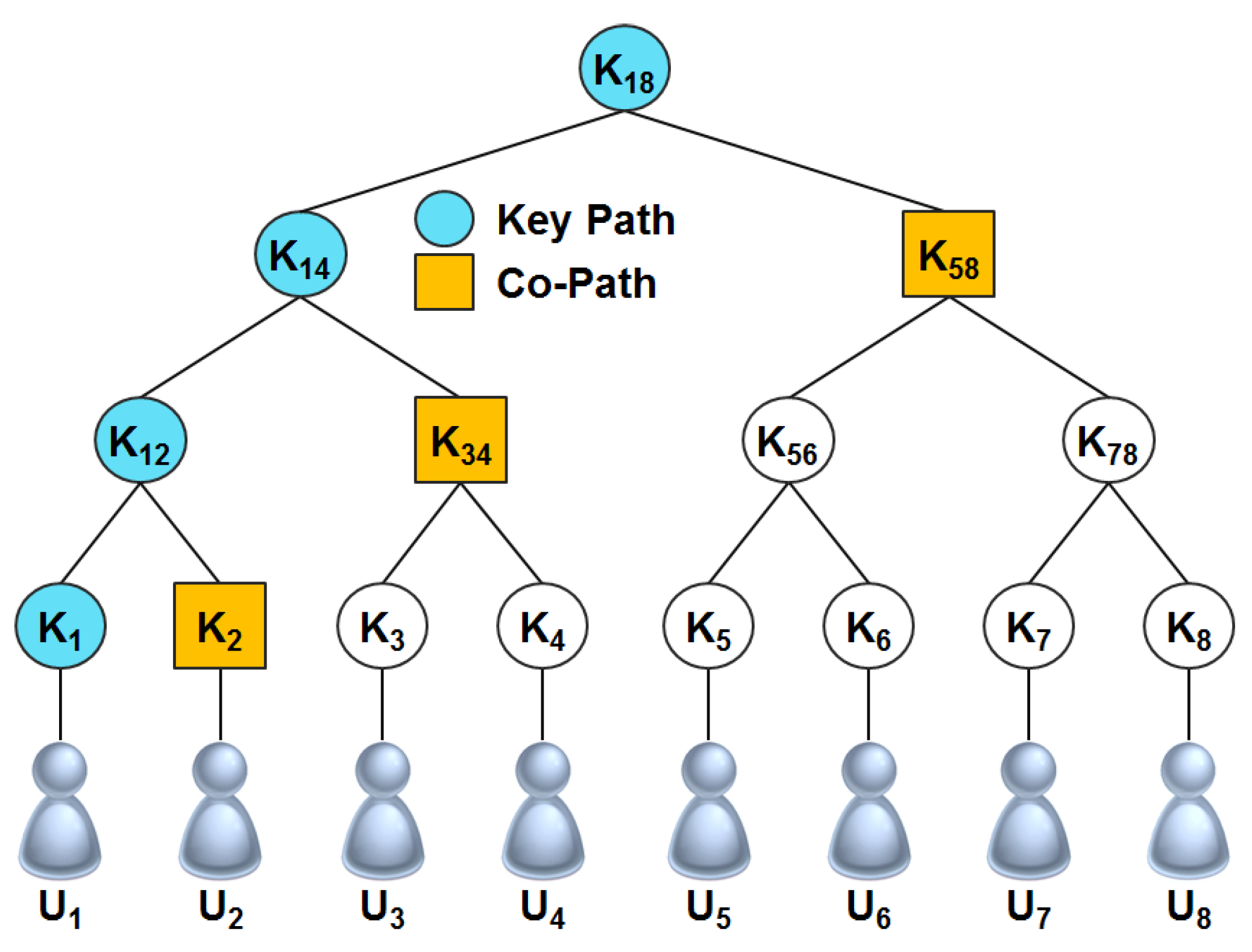
2.3.3. Efficient Large-Group Key (ELK)
2.4. Distributed Group Key Method
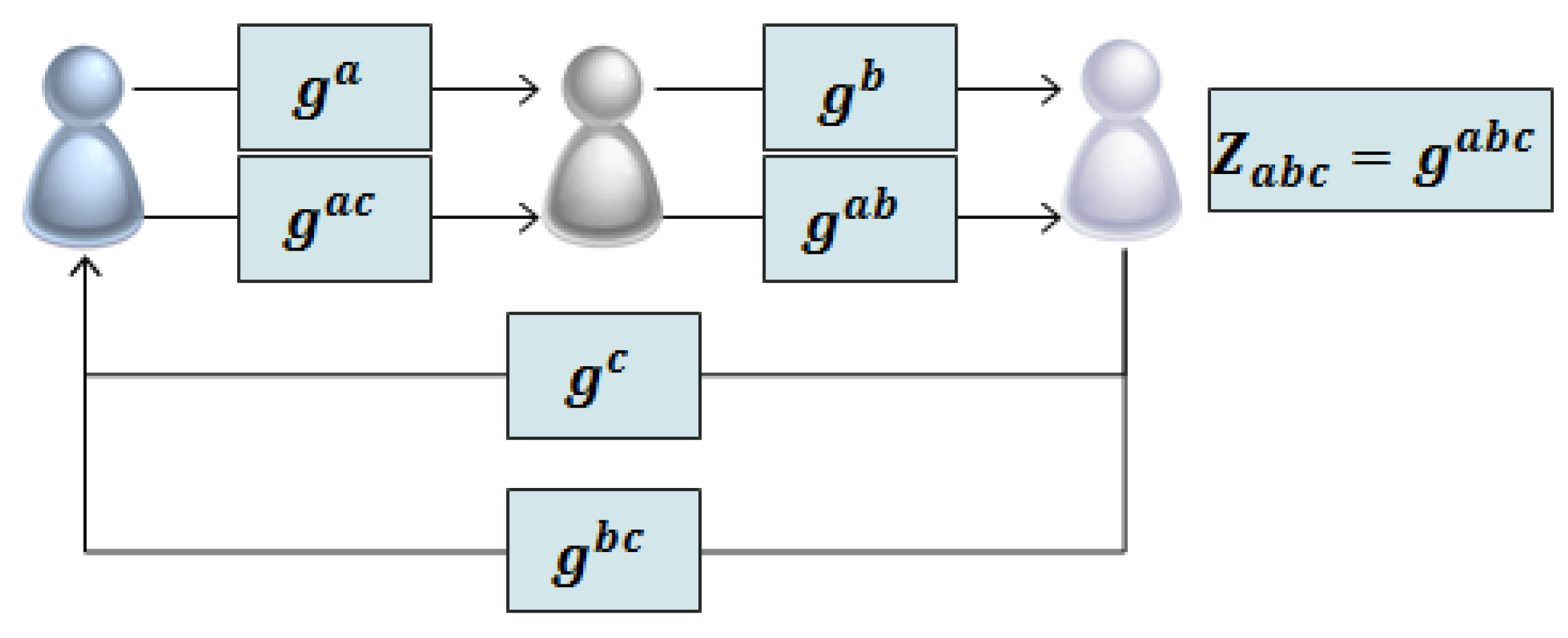
2.4.1. Expansion of Diffie-Hellman Protocol
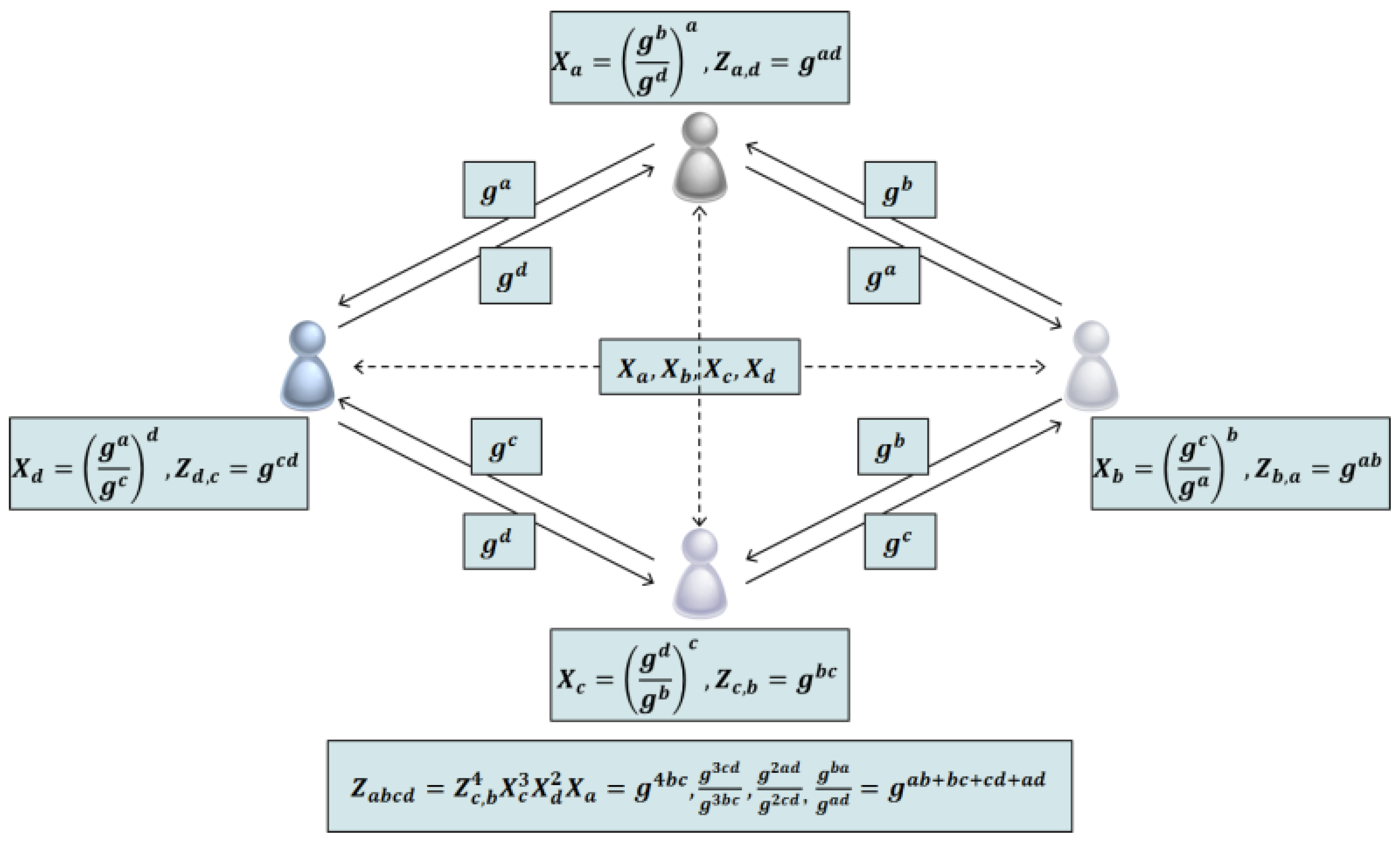
2.4.2. Distributed Group Key Protocol using Logical Key Tree
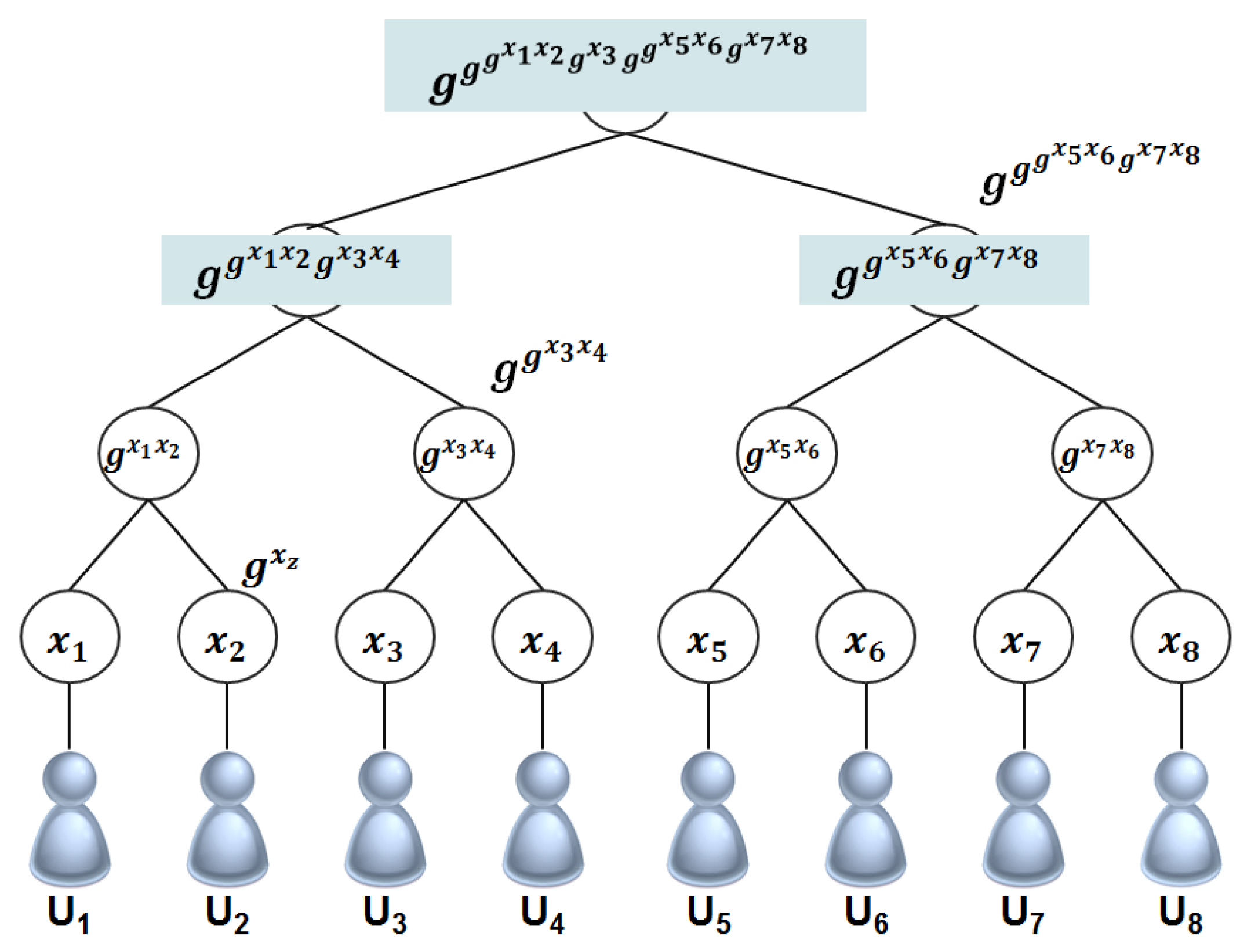
3. Access Control Using Group Key
3.1. Composition of Proposed System
| Symbols | Description |
|---|---|
| PSV | Secret Sharing Random Value |
| CIDX | Camera X’s ID |
| pri_X | X’s Private Key |
| pub_X | X’s Public Key |
| SKXY | Session Key between X and Y |
| E_sk | Encryption using session key |
| D_sk | Decryption using session key |
| SigX | Signature Value |
| GIDX | Camera X’s Group ID |
| hn(s) | Value executed by hash function n times using s as seed value |
| s | Random seed value generated by group leader camera |
| GKX | Camera X’s Group Key |
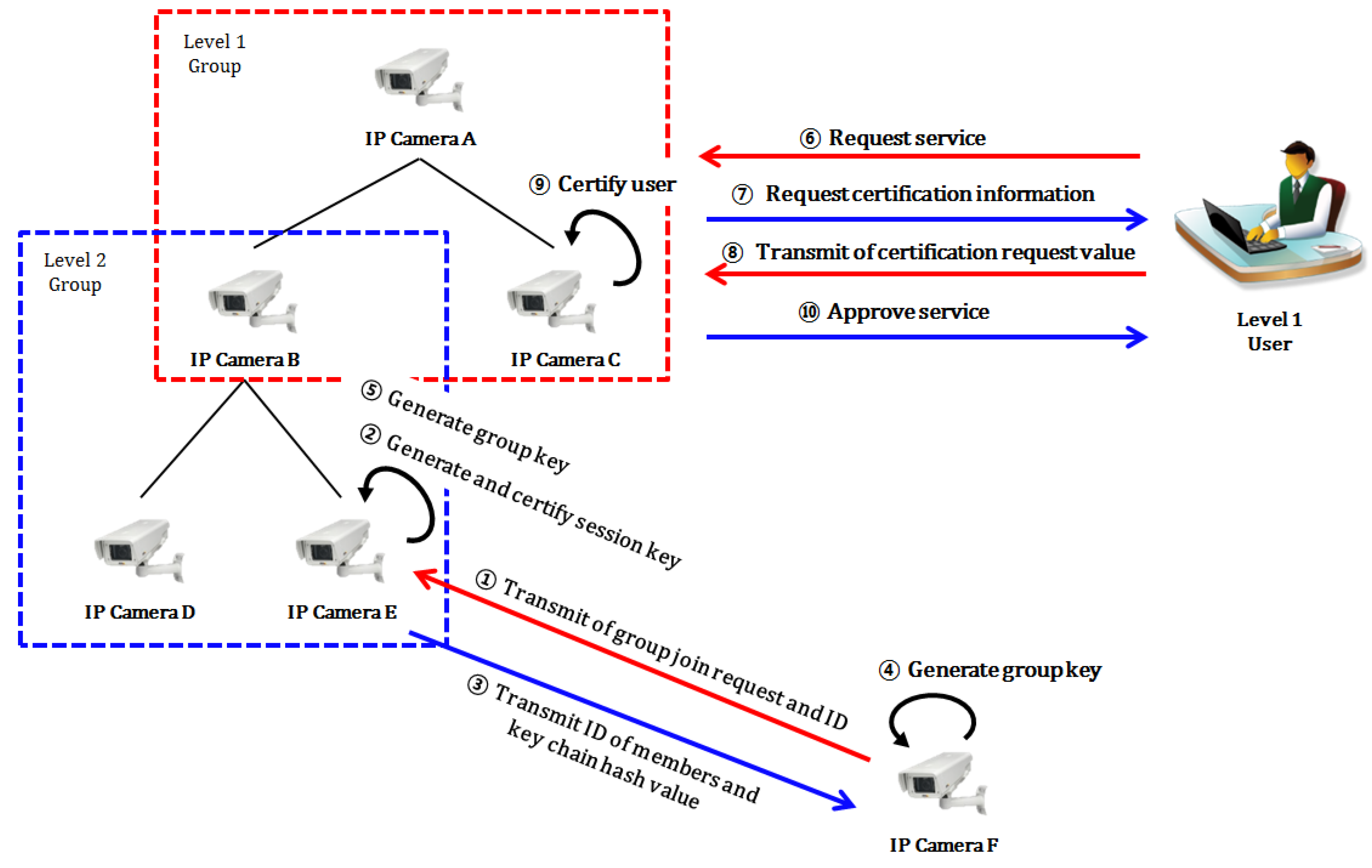
3.2. Specific Protocol
3.2.1. Early Group Key Generation Protocol

- Step 1.
- (B→A): In order to compose the early group, the camera B requests a group join to a camera which is going to be a root node. The input formula has a process like Formula (1):Request Group Join
- Step 2.
- (A→B): In order to compose the early group, the camera A requests a CID value when it receives a group join request. The input formula has a process like Formula (2):Request CID
- Step 3.
- (B→A): The camera B generates its own ID by using a random value and transmits it to group leader A. The formula to generate its own ID has a process like Formula (3):CID = grb mod p
- Step 4.
- (A): The group leader A applies a multiplying operation to the ID of its own, the ID which was transmitted from B, a pre-shared value, and generates a temporary session key. The calculation formula has a process like Formula (4):SKAB = CIDA × CIDB × PSV
- Step 5.
- (A→B): The group leader A signs the information, which is necessary to generate a group key, such as an ID of its own, certification, hash value and ID of other members by using its own personal key, and encodes them with the session key, which was generated in Step 4, and transmits them to the camera B. The formula to transmit information for generation of group key has a process like Formula (5):A’s certificate, ESKAB(h(s)||CIDC), Sigpri_A[ESKAB{h(s)||CIDC}]
- Step 6.
- (B): The camera B generates a session key with the A’s ID which was transmitted from the group leader A, the ID of its own, and pre-shared value. Then it decodes the encoded text. It verifies the signature value with the public key, which was acquired from the certification of A, and verifies whether it is a legitimate member or not. The formula to generate the session key has a process like Formula (6) and the formula to decode the encoded text and to verify the signature value has a process like Formulas (7) and (8):SKAB = CIDA × CIDB × PSVDSKAB[ESKAB{h(s)||CIDC}]Verify A’s signature
- Step 7.
- (B→A): The camera B transmits to the group leader A the signature value which was encoded with the ID of its own and the session key in order to verify whether it, itself, is a legitimate member or not. The formula to transmit has a process like Formula (9):B’s certificate, ESKAB(h2(s)||CIDC), Sigpri_B[ESKAB {h2(s)||CIDC}]
- Step 8.
- (A): The group leader A decodes the encoded text which was transmitted from the member B into the session key and verifies the signature value with B’s public key, which was acquired from B’s certification, and then verifies whether it is a legitimate member or not. Then, the group leader A makes a group ID through a calculation of the IDs of its own, B, and other members, and generates a group key by using the hash value which it, itself, has. The certification formula to decode the encoded text and to verify member B have processes like Formulas (10) and (11), respectively, and the calculation key to generate the group key has a process like Formula (12):DSKAC[ESKAC(h2(s)||CIDB)]Verify C’s signatureGKABC = h(hn(s) ⊕ GIDABC)
3.2.2. Group Member Withdrawal Protocol
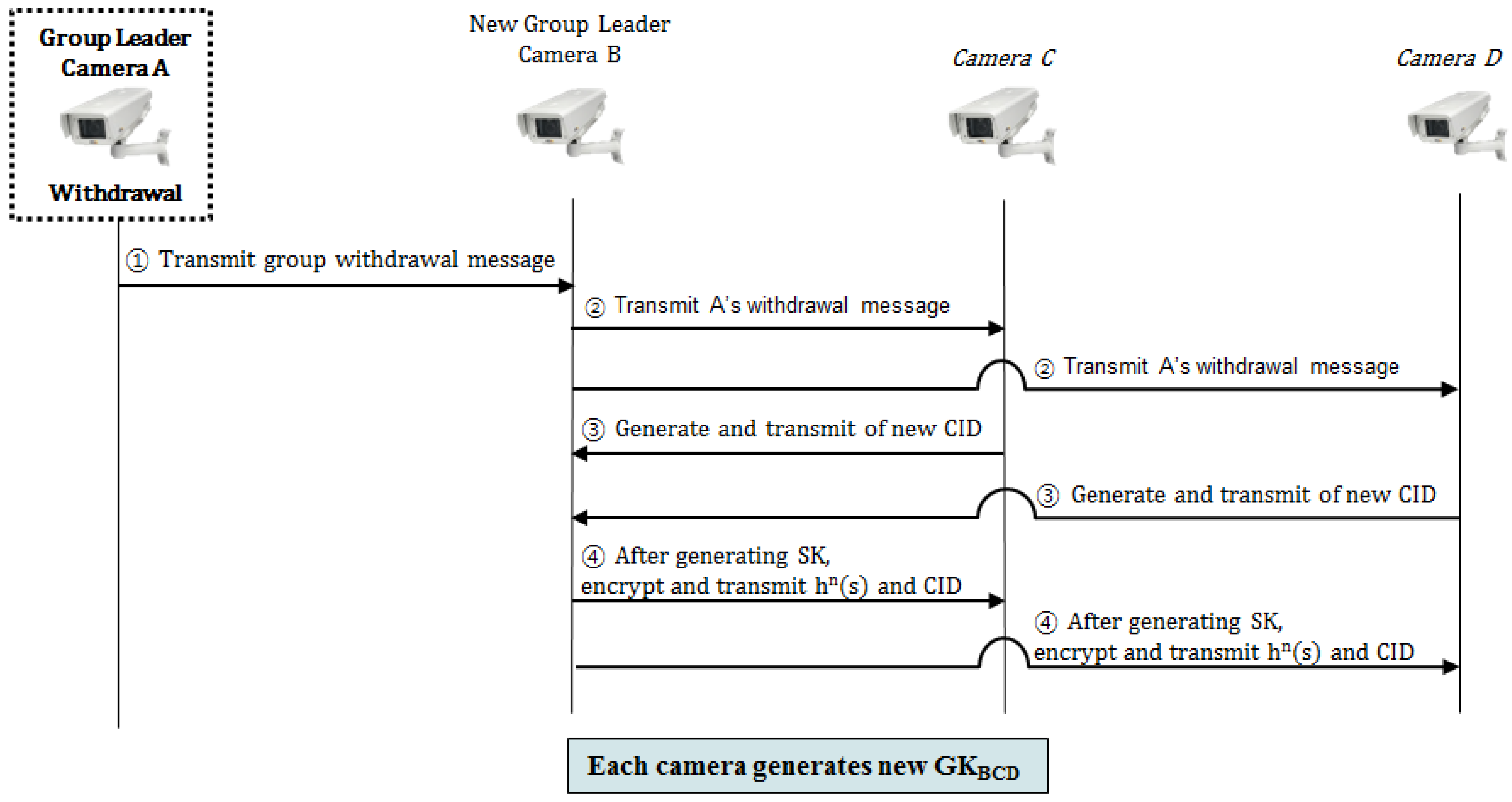
- Step 1.
- (A→B): The withdrawing member A transmits the withdrawal message to the member B which is going to the new group leader, and withdraws from the group.
- Step 2.
- (B→C, B→D): The new group leader B transmits the withdrawal message of A to members C and D, and informs that the member A withdraws from the group.
- Step 3.
- Each member which receives the withdrawal message proceeds with the same process as that from Step 3 to Step 7 of the early group key generation protocol, and generates a new group key.
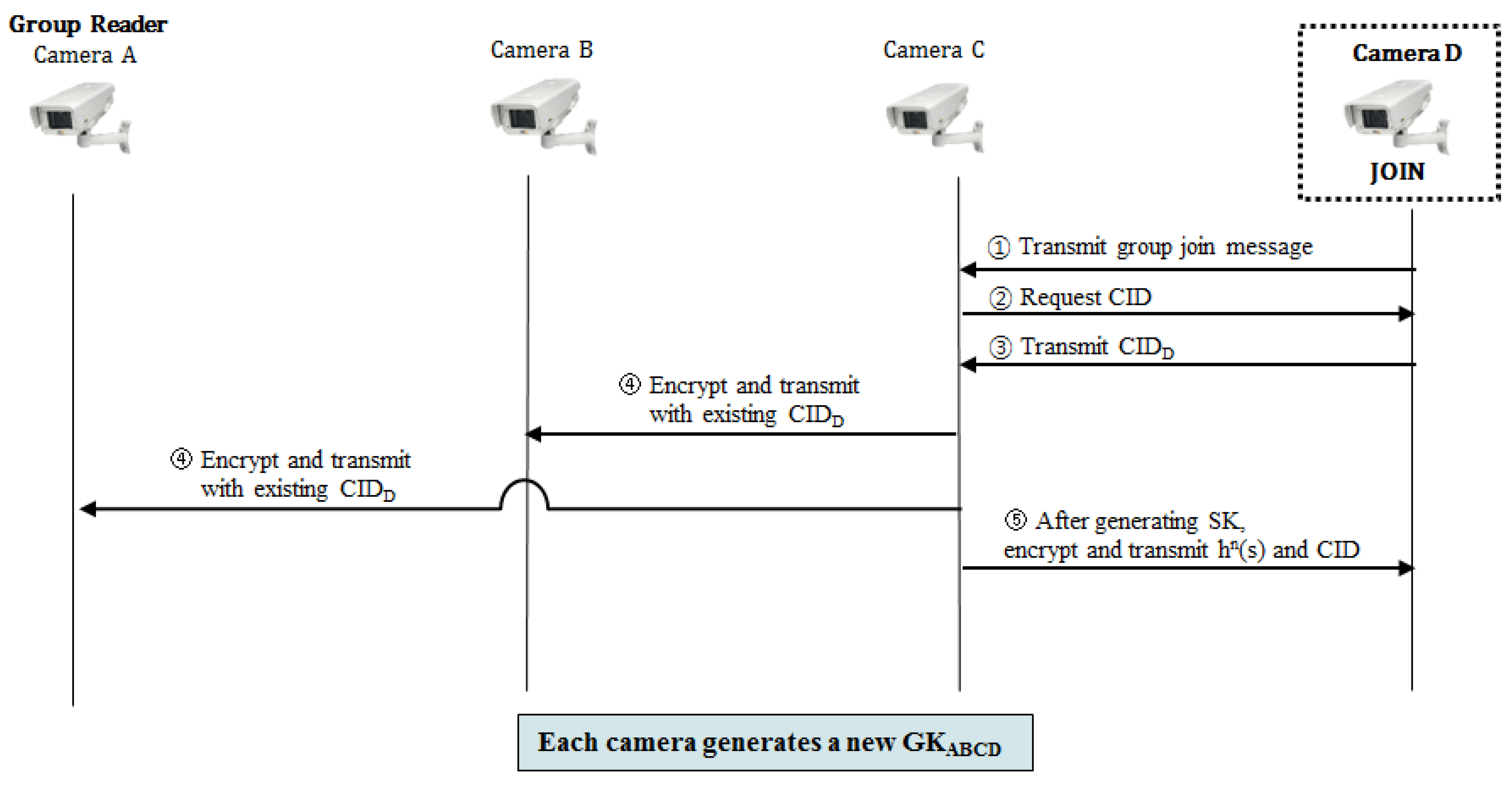
3.2.3. Join Protocol
- Step 1.
- A new group member joining the group transmits its group join request message to an existing member.
- Step 2.
- The group member who receives the join request message requests the ID from the joining member.
- Step 3.
- The new member who receives the ID request message generates its own ID in the same process as Formula (3) of the early group key generation protocol, and transmits it to the existing member.
- Step 4.
- The member which receives the ID of the new member informs other members about the joining of the new member, encodes the ID of the new member with the existing group key, and transmits it.
- Step 5.
- Each member proceeds with the same process as from Step 4 to Step 7 of the early group key generation protocol, and generates a new group key.
3.2.4. User Registration Protocol
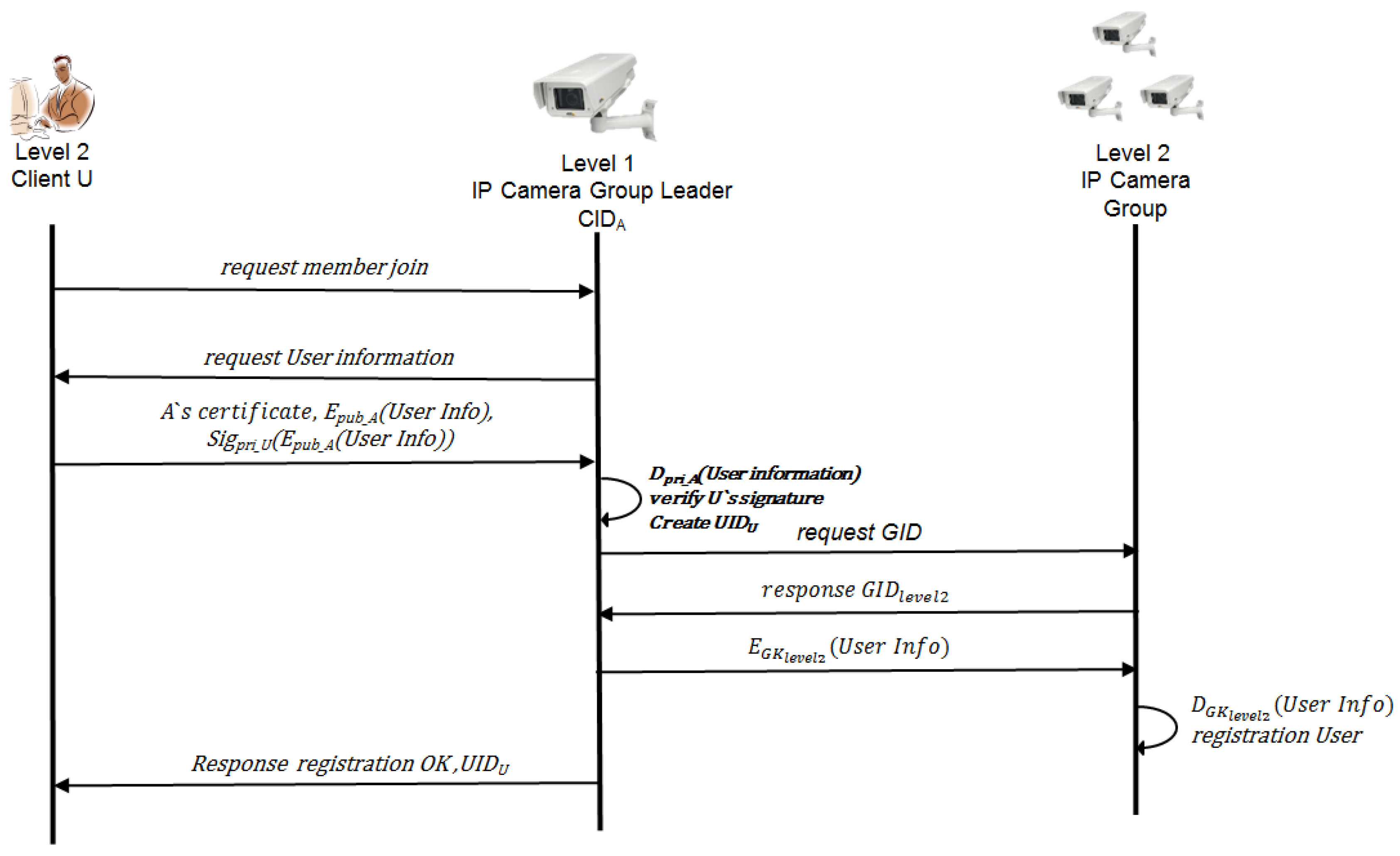
- Step 1.
- (U→A) A user transmits its user registration request message to the group leader of the highest level.
- Step 2.
- (A→U) If the group leader of the highest level receives the user registration request message, it requests the user information that wants to register.
- Step 3.
- (U→A) The user signs its own certificate and user information with its own private key, encodes it with the public key of the group leader, and transmits it. The formula to encode with the public key and to transmit has a process like Formula (13):U’s certificate, Epub_A(Sigpri_U(UserInfo))
- Step 4.
- (A): After the highest group leader A decodes its own private key, it verifies the signature value with the certification which was transmitted from the user. After the verification is approved, leader A assigns the access authority according to the access authority policy and requests the group leader of the corresponding level for its group ID. The formula to decode the transmitted message and verify the signature value has a process like Formulas (14) and (15):Dpri_A(Sigpri_U(UserInfo))Verify U’s signature
- Step 5.
- (A→level_n Group leader): The highest group leader requests the group leader of level_n for the group ID. On receiving the response, the highest group leader encodes the user information with the group key of the corresponding level (the group key of the corresponding level can be calculated by using a hash chain.), and transmits it. The formula to encode the user information and transmit has a process like Formula (16):EGKlevel_n(UserInfo)
- Step 6.
- The group leader of the corresponding level registers the user, encodes the user information with the group key, and multicasts it to members of the same group.
- Step 7.
- The highest group leader transmits the registration success message, user ID and the group ID of level corresponding to the access authority.
4. Realization and Comparative Analysis
4.1. Realization Environment
| Classification | Content | |
|---|---|---|
| Server & Client (PC) | OS | Microsoft Window 7 Enterprise K 32 bit |
| Hardware | CPU: Intel Core Quad CPU @ 2.66 Ghz | |
| RAM: 3.00 GB | ||
| Development tool | eclipse-java-juno-win32-x86 | |
| Password algorithm | AES128 | |
| Client (Mobile) | OS | Android JellyBean 4.1 |
| Hardware | CPU: 1.7 GHz Quad Core SnapDragon 600 | |
| RAM: 2 GB | ||
| Development tool | eclipse-java-juno-win32-x86 android SDK windows | |
| Password algorithm | AES128 | |
4.2. Realization Result
4.2.1. Early Group Key Generation Realization
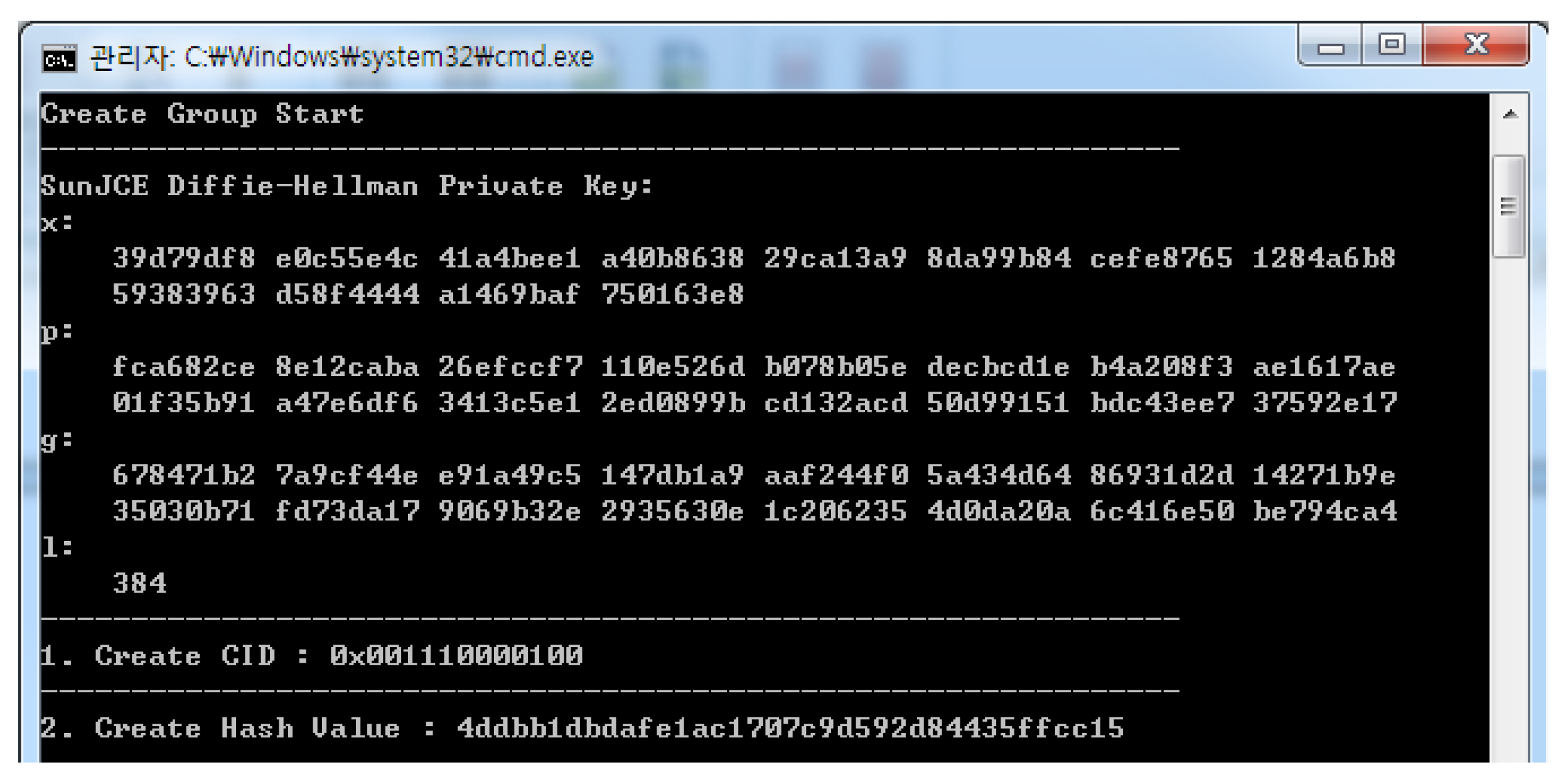
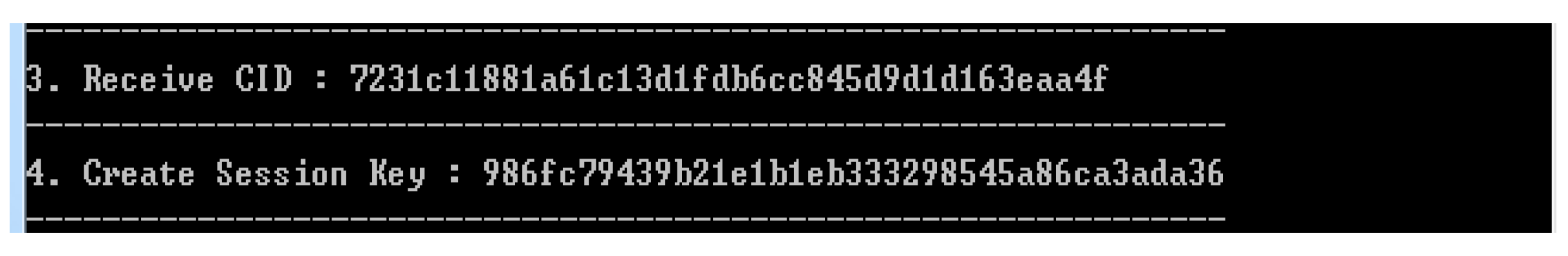
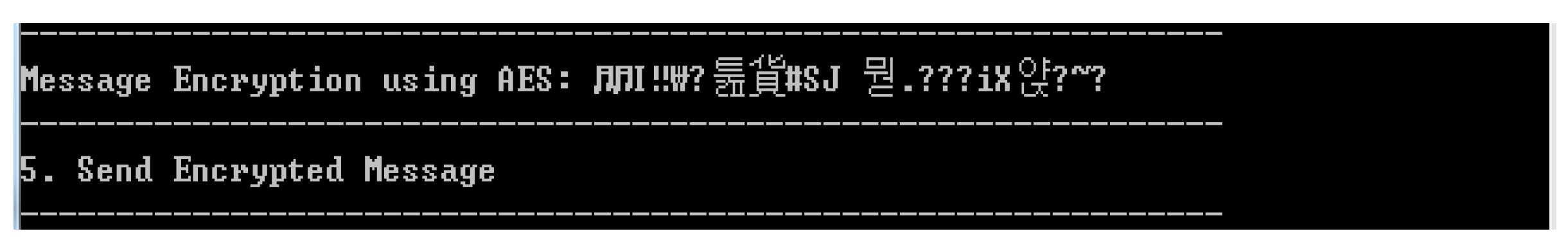
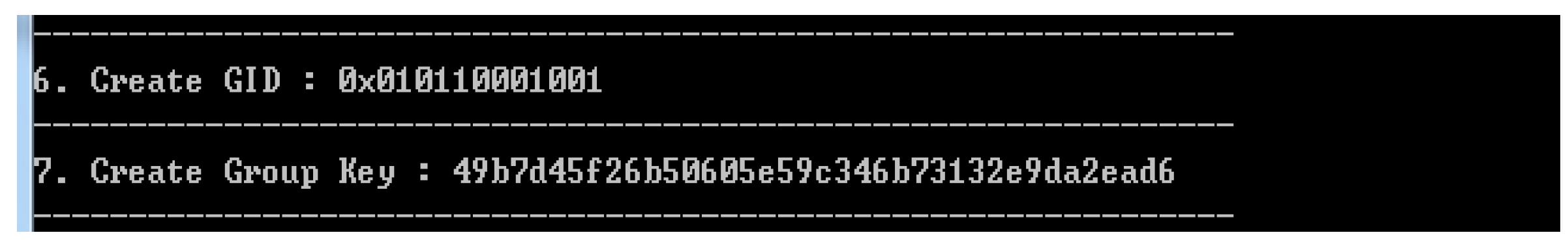
4.2.2. Realization of User Access Control According to Access Authority
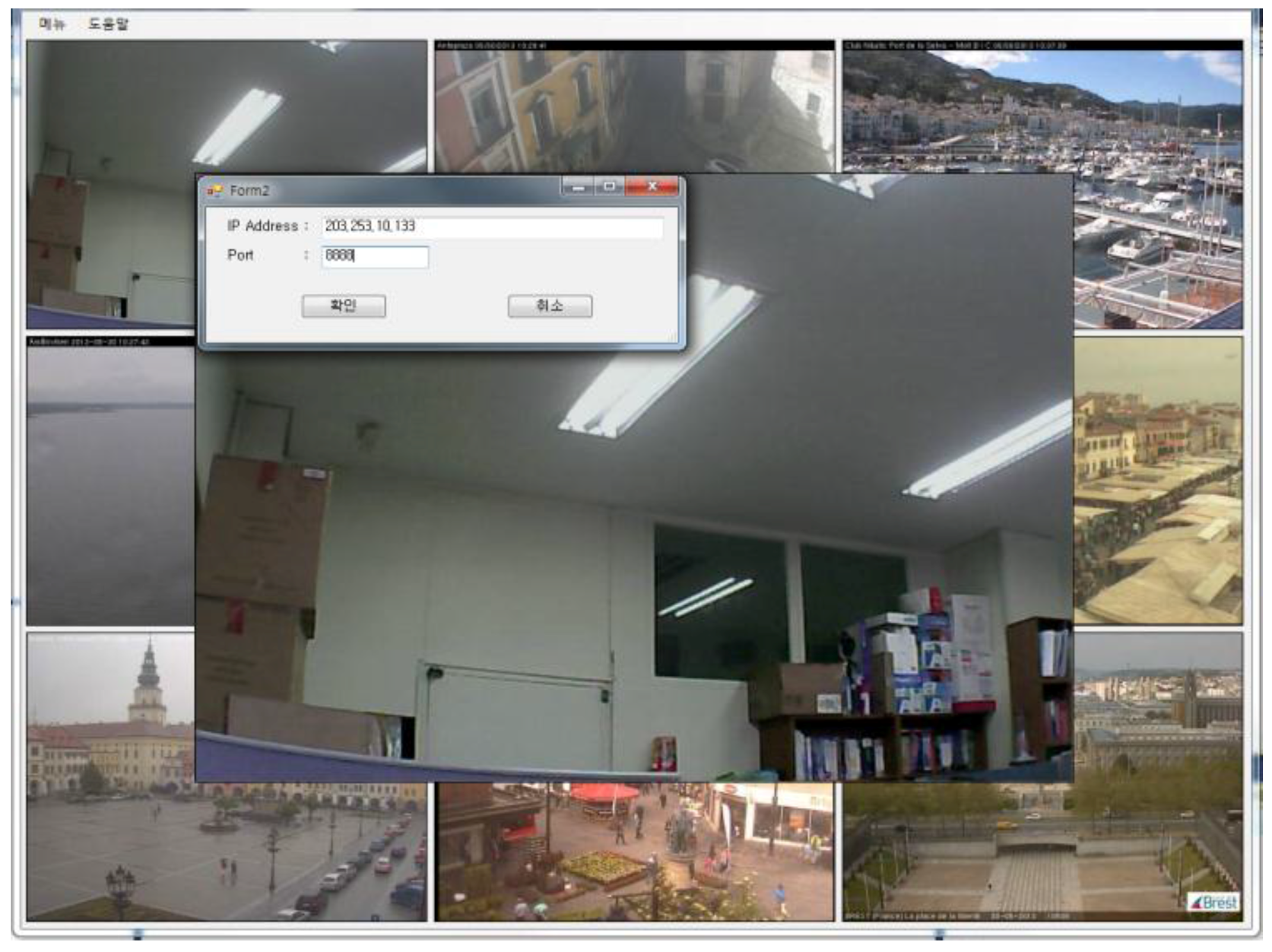
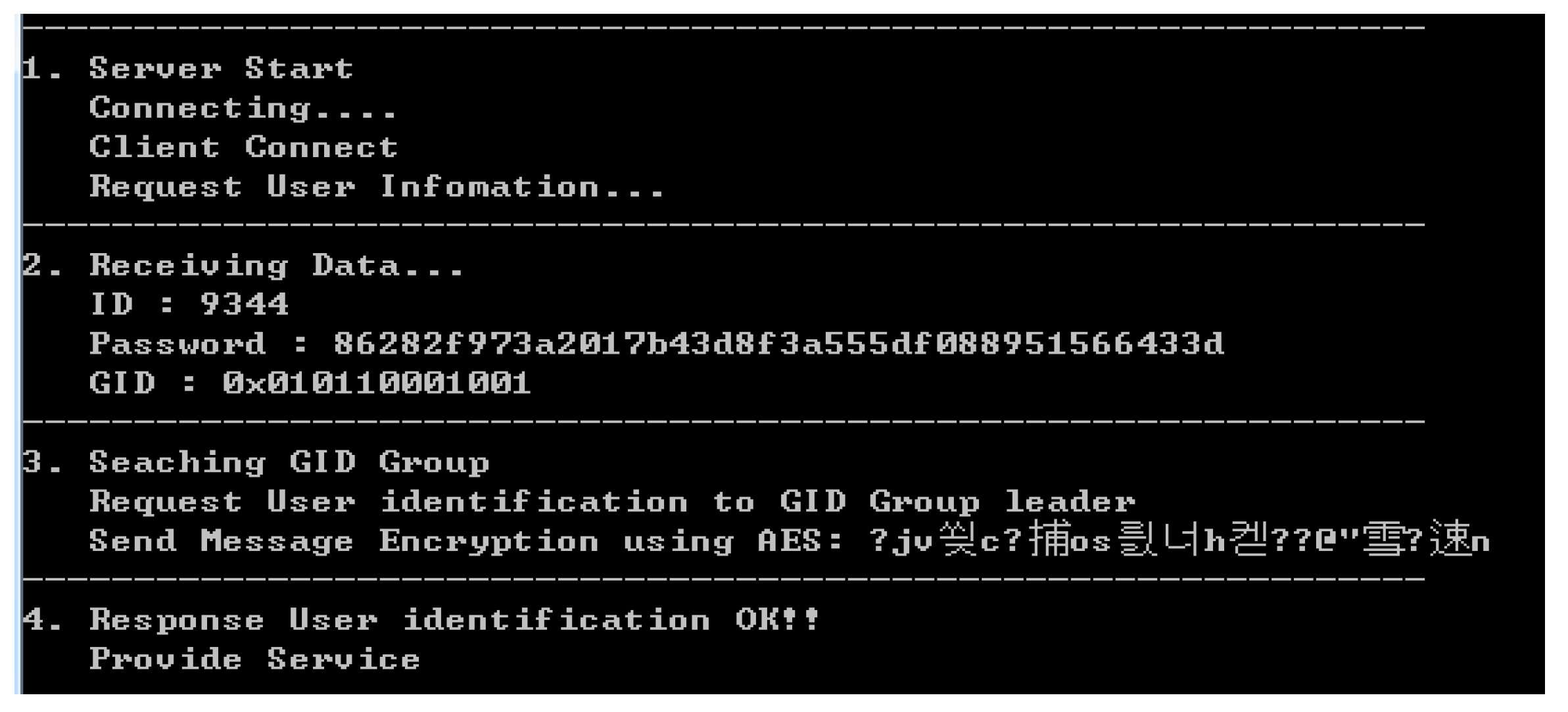
4.3. Comparative Analysis
4.3.1. Requirements for Video Surveillance System
4.3.2. Analysis of Security and Efficiency
| Item | CCTV System | Existing IP Camera | Proposed System |
|---|---|---|---|
| Management policy | Only wired equipment can be managed | Not Supported | Group management is possible, even though installed places are different |
| Information modification | Information can be modified only by manager | It can be managed in camera server individually | Distributed management is possible by group leaders by grouping cameras |
| Access authority | Central control center | Every registered user | Management by group |
| Access denial | Only central control center can monitor | Random access attempts are possible | Supported |
| User certification | Supported | Not Supported | Supported |
| Password encryption | Supported | Not Supported | Supported |
| Support group key | Not Supported | Not Supported | Supported |
| Computational complexity (for group key) | – | – | |
| Mutual authentication | – | – | Supported |
| Brute-force attack | 2256 | 21024 | 21024 × 2256 × i (i: the number of camera) |
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Lee, K.J.; Park, J.S.; Kim, D.H.; Huh, M.J.; Park, J.H.; Jeon, Y.S. Analyses of Research Trends on Networked-Camera. In Proceedings of the Korea Multimedia Society Conference, Seoul, Korea, November 2010; pp. 424–426.
- Ibrahim, N.; Mohammad, M.; Alagar, V. Publishing and discovering context-dependent services. Hum. Centric Comput. Inf. Sci. 2013, 3. [Google Scholar] [CrossRef]
- Ryu, D.H.; Han, J. Distributed Smart Camera Systems Security Issues; Review of KIISC; Korea Institute of Information Security and Cryptology: Seoul, Korea, 2010; Volume 20, pp. 31–42. [Google Scholar]
- Gnanaraj, J.W.K.; Ezra, K.; Rajsingh, E.B. Smart card based time efficient authentication scheme for global grid computing. Hum. Centric Comput. Inf. Sci. 2013, 3. [Google Scholar] [CrossRef]
- Chu, H.H.; Qiao, L.; Nahrstedt, K. Secure Multicast Protocol with Copyright Protection. ACM SIGCOMM Comput. Commun. Rev. 2002, 32, 42–60. [Google Scholar] [CrossRef]
- Dondeti, L.R.; Mukherjee, S.; Samal, A. A Dual Encryption Protocol for Scalable Secure Multicasting. In Proceedings of the IEEE Symposium on Computers and Communications, Red Sea, Egypt, July 1999; pp. 2–8. [CrossRef]
- Juneja, M.; Sandhu, P.S. A New Approach for Information Security Using an Improved Steganography Technique. J. Inf. Process. Syst. 2013, 9, 405–424. [Google Scholar] [CrossRef]
- Panduranga, H.T.; Naveen Kumar, S.K.; Sharath Kumar, H.S. Hardware Software Co-Simulation of the Multiple Image Encryption Technique Using the Xilinx System Generator. J. Inf. Process. Syst. 2013, 9, 499–510. [Google Scholar] [CrossRef]
- Chung, Y.; Choi, S.; Won, D. Lightweight anonymous authentication scheme with unlinkability in global mobility networks. J. Converg. 2013, 4, 23–29. [Google Scholar]
- Vanus, J.; Kucera, P.; Martinek, R.; Koziorek, J. Development and testing of a visualization application software, implemented with wireless control system in smart home care. Hum. Centric Comput. Inf. Sci. 2014, 4. [Google Scholar] [CrossRef]
- Bae, K.; Lee, K.; Yim, K. Proxy Server Providing Multi-level Privileges for Network Cameras on the Video Surveillance System. Korean Soc. Int. Inf. Rev. Korean Soc. Int. Inf. 2011, 12, 126–133. [Google Scholar]
- Zheng, X.; Huang, C.; Matthews, M. Chinese Remainder Theorem Based Group Key Management. In Proceedings of the ACM Southeast Conference, Winston-Salem, NC, USA, 23–24 March 2007.
- Chung, W.H.; Kumar, S.; Paluri, S.; Nagaraj, S.; Annamalai, A., Jr.; Matyjas, J.D. A Cross-Layer Unequal Error Protection Scheme for Prioritized H.264 Video using RCPC Codes and Hierarchical QAM. J. Inf. Process. Syst. 2013, 9, 53–68. [Google Scholar] [CrossRef]
- Degefa, F.B.; Won, D. Extended Key Management Scheme for Dynamic Group in Multi-cast Communication. J. Converg. 2013, 4, 7–13. [Google Scholar]
- Goswami, K.; Hong, G.S.; Kim, B.G. A Novel Mesh-Based Moving Object Detection Technique in Video Sequence. J. Converg. 2013, 4, 20–24. [Google Scholar]
- Ogiela, M.R.; Ogiela, U. Linguistic Protocols for Secure Information Management and Sharing. Comput. Math. Appl. 2012, 63, 564–572. [Google Scholar] [CrossRef]
- Ogiela, M.R.; Ogiela, U. Security of Linguistic Threshold Schemes in Multimedia Systems. In New Directions in Intelligent Interactive Multimedia Systems and Services—2, Studies in Computational Intelligence; Damiani, E., Jeong, J., Howlett, R.J., Jain, L.C., Eds.; Springer-Verlag Berlin Heidelberg: Berlin, Germany; Heidelberg, Germany, 2009; Volume 226, pp. 13–20. [Google Scholar]
- Kim, C.O.; Kang, K.; Cho, Y.J. A Distributed Multicast Group Key Management Scheme for a Hierarchically Structured Network. Korea information science society. J. Korea Inf. Sci. Soc. Data Commun. 2011, 38, 22–32. [Google Scholar]
- Pegueroles, J.; Rico-Novella, F.; Hernandez-Serrano, J.; Soriano, M. Improved LKH for batch re-keying in multicast groups. In Proceedings of International Conference on Information Technology, Research and Education 2003, Neward, NJ, USA, August 2003; pp. 269–273.
- Sherman, A.T.; McGrew, D.A. Key Establishment in Large Dynamic Groups using One Way Function Trees. IEEE Trans. Softw. Eng. May 2003, 29, 444–458. [Google Scholar] [CrossRef]
- Perrig, A. Efficient Collaborative Key Management Protocols for Secure Autonomous Group Communication. In Proceedings of the International Workshop on Cryptographic Techniques and Electronic Commerce, Hong Kong, China, July 1999; pp. 192–202.
- Ingemarsson, I.; Tang, D.; Wong, C. A Conference Key Distribution System. IEEE Trans. Inf. Theory 1982, 28, 714–720. [Google Scholar] [CrossRef]
- Steiner, M.; Tsudik, G.; Waidner, M. Diffie-Hellman Key Distribution Extended to Group Communication. In Proceedings of the 3rd ACM Conference on Computer and Communications Security, New York, NY, USA, 1996; pp. 31–37.
- Burmester, M.; Desmedt, Y. A Secure and Efficient Conference Key Distribution System. In Advances in Cryptology, Eurocrypt; Springer Berlin Heidelberg: Berlin, Germany; Heidelberg, Germany, 1994; pp. 275–286. [Google Scholar]
- Perrig, A.; Song, D.; Tygar, J.D. ELK, a New Protocol for Efficient Large-Group Key Distribution. In Proceedings of the IEEE Symposium on Security and Privacy 2001, Oakland, CA, USA, 14–16 May 2001; pp. 247–262.
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kang, J.; Han, J.; Park, J.H. Design of IP Camera Access Control Protocol by Utilizing Hierarchical Group Key. Symmetry 2015, 7, 1567-1586. https://doi.org/10.3390/sym7031567
Kang J, Han J, Park JH. Design of IP Camera Access Control Protocol by Utilizing Hierarchical Group Key. Symmetry. 2015; 7(3):1567-1586. https://doi.org/10.3390/sym7031567
Chicago/Turabian StyleKang, Jungho, Jaekyung Han, and Jong Hyuk Park. 2015. "Design of IP Camera Access Control Protocol by Utilizing Hierarchical Group Key" Symmetry 7, no. 3: 1567-1586. https://doi.org/10.3390/sym7031567
APA StyleKang, J., Han, J., & Park, J. H. (2015). Design of IP Camera Access Control Protocol by Utilizing Hierarchical Group Key. Symmetry, 7(3), 1567-1586. https://doi.org/10.3390/sym7031567





_Park.png)

