Image Encryption Based on Local Fractional Derivative Complex Logistic Map
Abstract
:1. Introduction
2. Materials and Methods
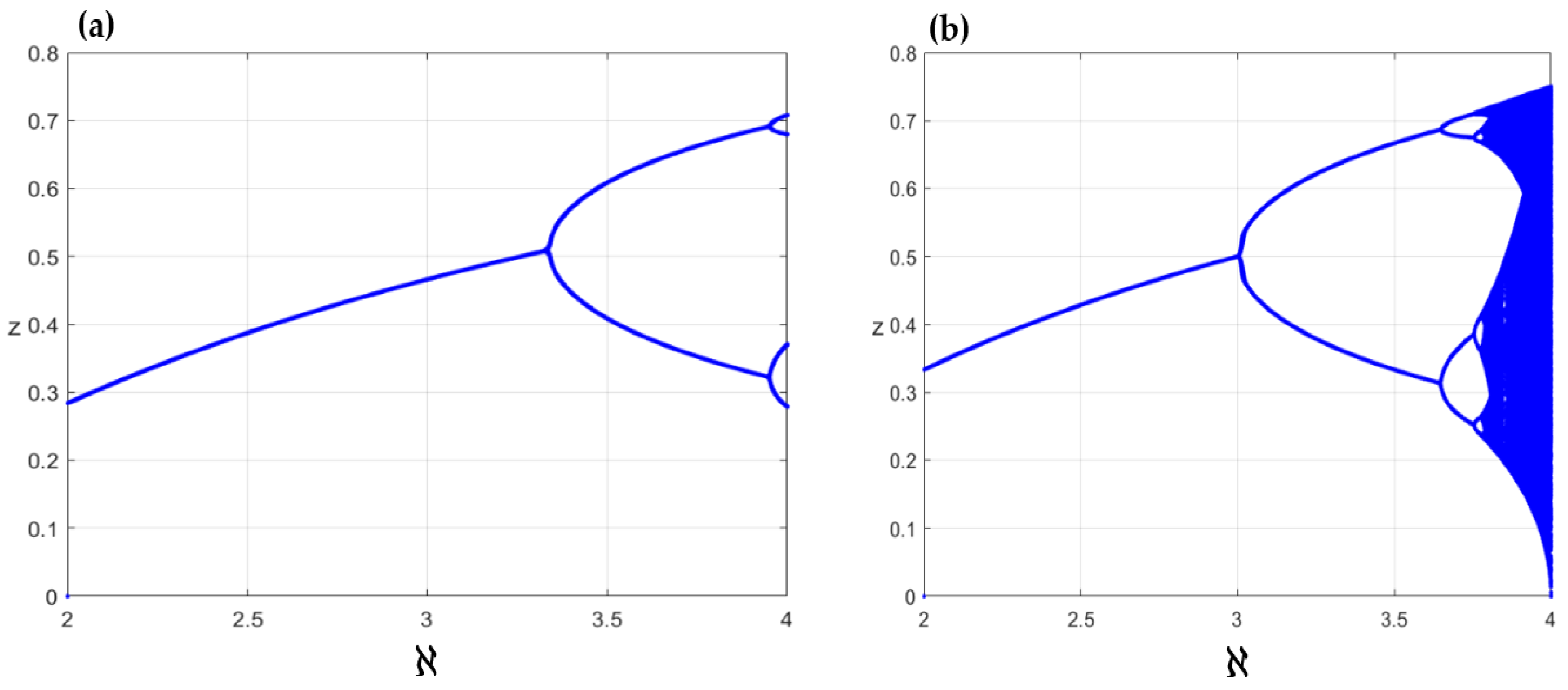
2.1. Fractal Complex Logistic (FCL) Map
2.2. Structure of FCL Map
2.3. Properties of FCL Map
2.3.1. Equilibrium Points
2.3.2. Geometric Properties
- 1.
- Ifthen
- 2.
- Ifthen
2.4. The FCL Map Algorithm
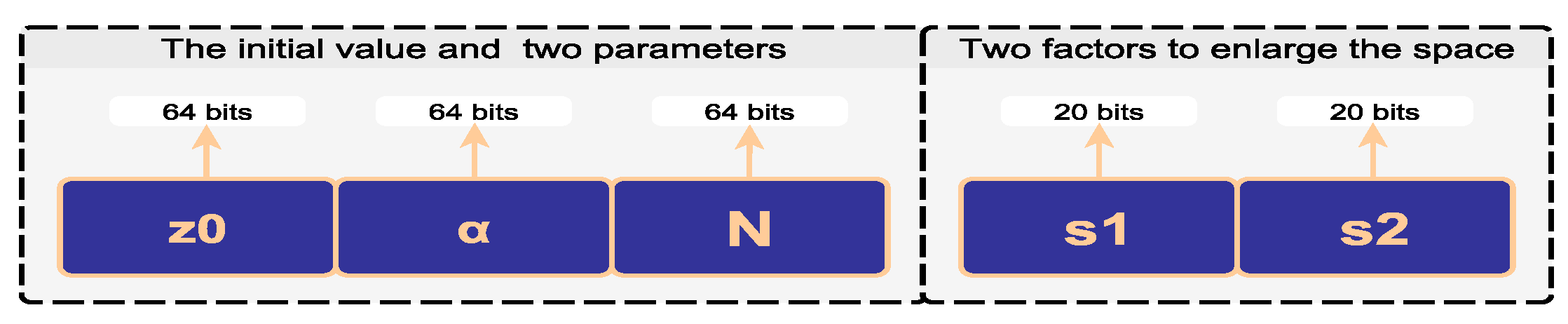
2.5. The Encryption Method
- 1.
- Read the input image (I), and convert the values to a 52-bit binary stream using IEEE 754 float standard; then, the digital numbers from 33rd to 40th in each binary stream are used;
- 2.
- Set the secret key, which is mainly generated from the initial value and control parameters of the FCL map, as illustrated in Figure 3;
- 3.
- Use proposed FCL to generate the chaotic sequences . Note that for all ;
- 4.
- Start the confusion of the input image by changing the position of pixels by using conditional shift, which stops the algorithm for any shifting cases to make the variable z outside the open unit disk;
- 5.
- Convert the chaotic sequences to binary numbers using IEEE 754 float standard in which each chaotic output produces eight binary numbers;
- 6.
- Start the diffusion of the confusing image to obtain the encrypted image by using the XOR operation between the binary input image and the binary form of chaotic sequence as: I(i) = bitxor (Ib(i),(z(i));
- 7.
- Convert I into a two-dimensional encrypted image (Ie);
- 8.
- The previous steps are applied in reverse to decrypt the image.
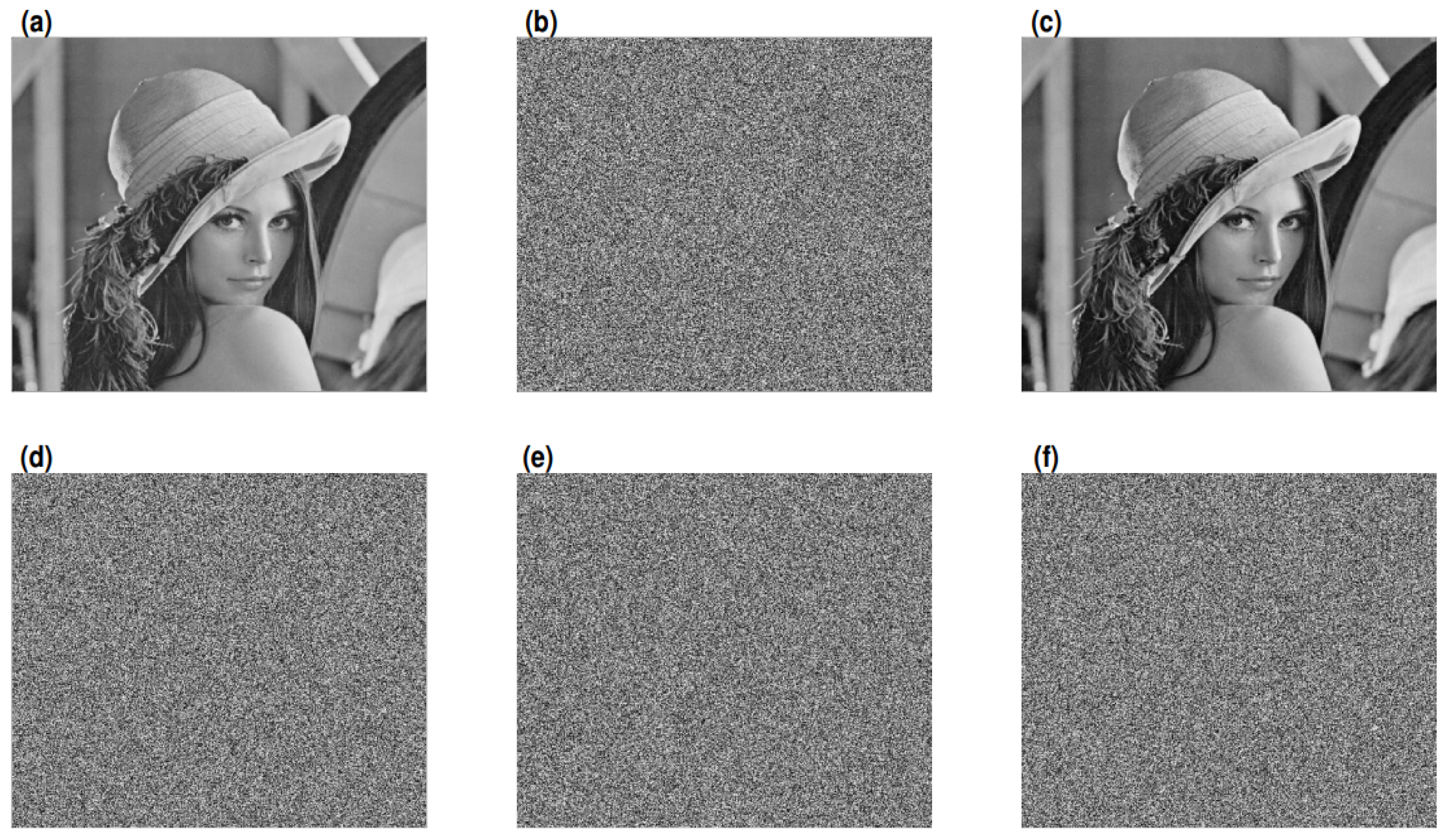
3. Results
3.1. Encrypting Different Kinds of Images
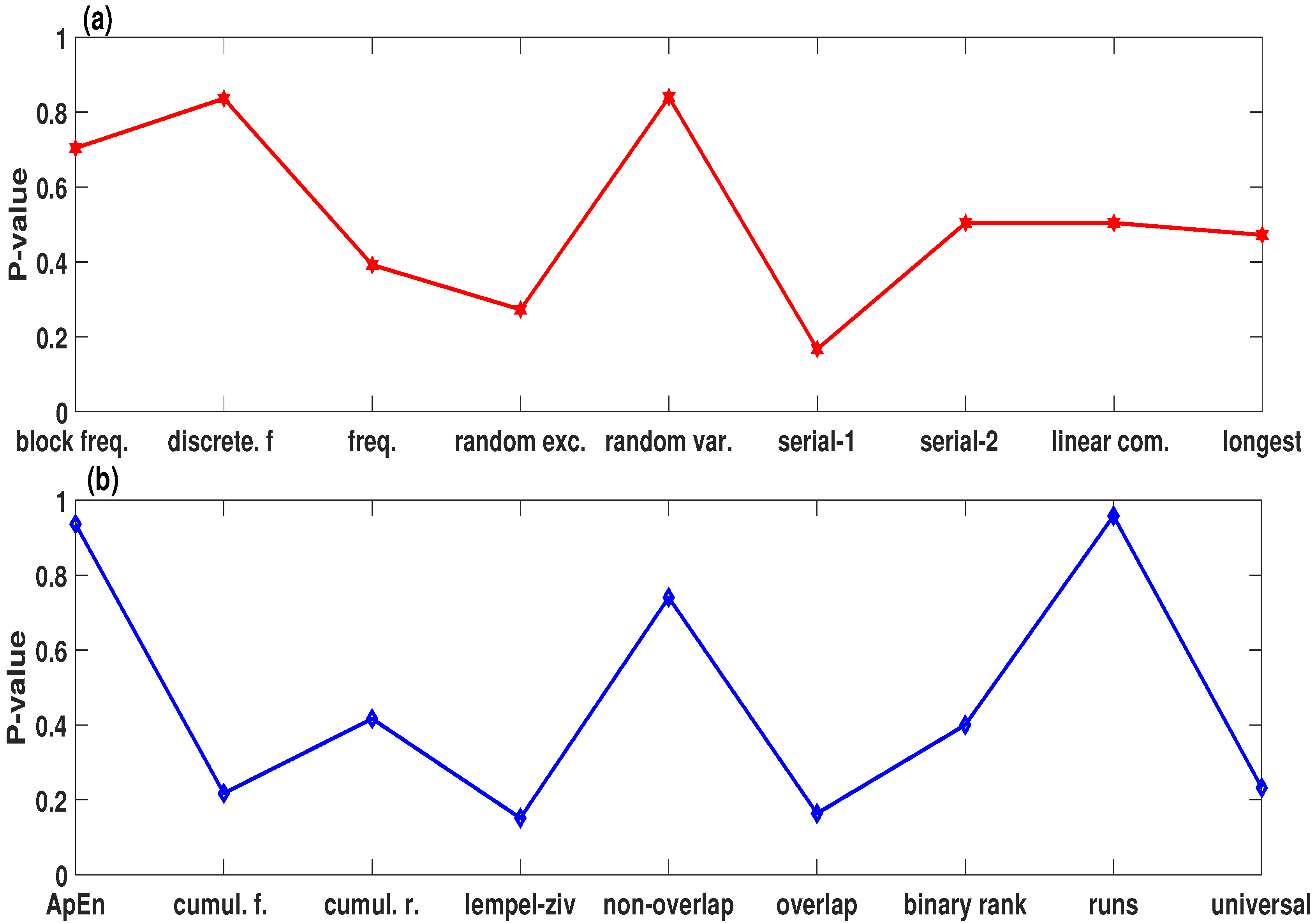
3.2. Information Entropy Analysis
3.3. Correlation Analysis
3.4. Key Sensitivity Analysis
3.5. Differential Attack Analysis
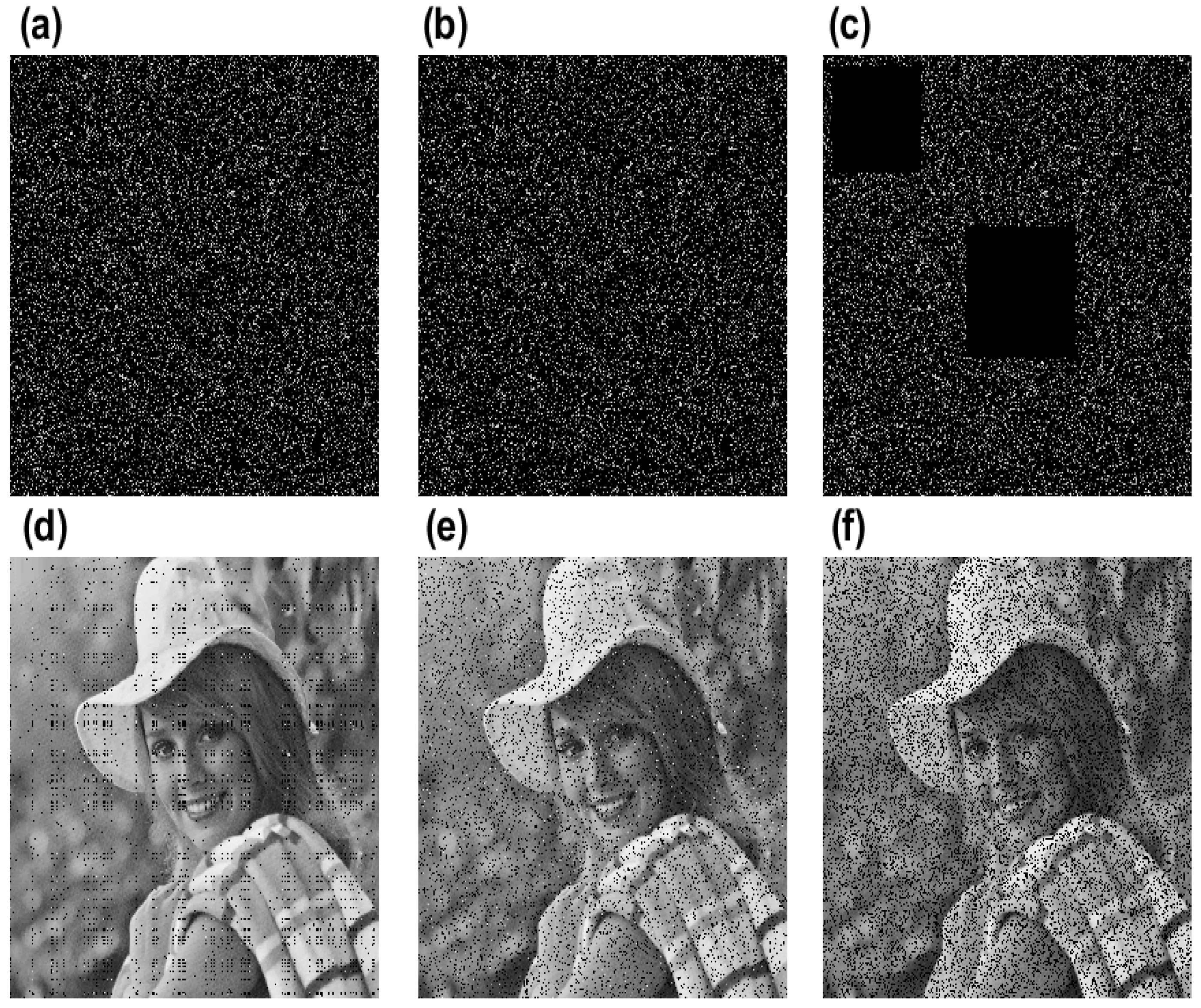
3.6. Noise and Data Loss Analysis
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Pourasad, Y.; Ranjbarzadeh, R.; Mardani, A. A new algorithm for digital image encryption based on chaos theory. Entropy 2021, 23, 341. [Google Scholar] [CrossRef] [PubMed]
- Askar, S.S.; Karawia, A.A.; Alshamrani, A. Image Encryption Algorithm Based on Chaotic Economic Model. Math. Probl. Eng. 2015, 2015, 341729. [Google Scholar] [CrossRef]
- Tang, Z.; Yang, Y.; Xu, S.; Yu, C.; Zhang, X. Image encryption with double spiral scans and chaotic maps. Secur. Commun. Netw. 2019, 2019, 8694678. [Google Scholar] [CrossRef]
- Erkan, U.; Toktas, A.; Toktas, F.; Alenezi, F. 2D eπ-map for image encryption. Inf. Sci. 2022, 589, 770–789. [Google Scholar] [CrossRef]
- Erkan, U.; Toktas, A.; Enginoğlu, S.; Akbacak, E.; Thanh, D.N. An image encryption scheme based on chaotic logarithmic map and key generation using deep CNN. Multimed. Tools Appl. 2022, 81, 7365–7391. [Google Scholar] [CrossRef]
- Toktas, A.; Erkan, U. 2D fully chaotic map for image encryption constructed through a quadruple-objective optimization via artificial bee colony algorithm. Neural Comput. Appl. 2022, 34, 4295–4319. [Google Scholar] [CrossRef]
- Martsenyuk, V.; Augustynek, K.; Urbas, A. On qualitative analysis of the nonstationary delayed model of coexistence of two-strain virus: Stability, bifurcation, and transition to chaos. Int. J.-Non-Linear Mech. 2021, 128, 103630. [Google Scholar] [CrossRef]
- Al-Saidi, N.M.; Younus, D.; Natiq, H.; Ariffin, M.R.K.; Asbullah, M.A.; Mahad, Z. A new hyperchaotic map for a secure communication scheme with an experimental realization. Symmetry 2020, 12, 1881. [Google Scholar] [CrossRef]
- Gopalakrishnan, T.; Ramakrishnan, S. Chaotic image encryption with hash keying as key generator. IETE J. Res. 2017, 63, 172–187. [Google Scholar] [CrossRef]
- Luo, Y.; Yu, J.; Lai, W.; Liu, L. A novel chaotic image encryption algorithm based on improved baker map and logistic map. Multimed. Tools Appl. 2019, 78, 22023–22043. [Google Scholar] [CrossRef]
- Aslam, M.N.; Belazi, A.; Kharbech, S.; Talha, M.; Xiang, W. Fourth order MCA and chaos-based image encryption scheme. IEEE Access 2019, 7, 66395–66409. [Google Scholar]
- Tsafack, N.; Sankar, S.; Abd-El-Atty, B.; Kengne, J.; Jithin, K.; Belazi, A.; Mehmood, I.; Bashir, A.K.; Song, O.-Y.; Abd El-Latif, A.A. A new chaotic map with dynamic analysis and encryption application in internet of health things. IEEE Access 2020, 8, 137731–137744. [Google Scholar] [CrossRef]
- Yang, X.-J. Advanced Local Fractional Calculus and Its Applications; World Science Publisher: New York, NY, USA, 2012. [Google Scholar]
- Yang, X.-J.; Baleanu, D.; Srivastava, H.M. Local Fractional Integral Transforms and Their Applications; Academic Press: Cambridge, MA, USA, 2015. [Google Scholar]
- Yang, X.-J.; Baleanu, D.; Srivastava, H. Local fractional similarity solution for the diffusion equation defined on Cantor sets. Appl. Math. Lett. 2015, 47, 54–60. [Google Scholar] [CrossRef]
- Kilbas, A.A.; Srivastava, H.M.; Trujillo, J.J. Theory and Applications of Fractional Differential Equations; Elsevier: Amsterdam, The Netherlands, 2006; Volume 204. [Google Scholar]
- Zhou, Y.; Wang, J.; Zhang, L. Basic Theory of Fractional Differential Equations; World Scientific: Singapore, 2016. [Google Scholar]
- Ibrahim, R.W.; Altulea, D. Controlled homeodynamic concept using a conformable calculus in artificial biological systems. Chaos Solitons Fractals 2020, 140, 110132. [Google Scholar] [CrossRef]
- Jalab, H.A.; Ibrahim, R.W.; Hasan, A.M.; Karim, F.K.; Al-Shamasneh, A.a.R.; Baleanu, D. A New Medical Image Enhancement Algorithm Based on Fractional Calculus. CMC-Comput. Mater. Contin. 2021, 68, 1467–1483. [Google Scholar] [CrossRef]
- Ibrahim, R.W. A new image.)denoising model utilizing the conformable fractional calculus for multiplicative noise. SN Appl. Sci. 2020, 2, 1–11. [Google Scholar] [CrossRef]
- Ramakrishnan, B.; Nkandeu Kamdeu, P.Y.; Natiq, H.; Pone, J.R.M.; Karthikeyan, A.; Kingni, S.T.; Tiedeu, A. Image encryption with a Josephson junction model embedded in FPGA. Multimed. Tools Appl. 2022, 81, 23819–23843. [Google Scholar] [CrossRef]
- Meshram, C.; Ibrahim, R.W.; Obaidat, M.S.; Sadoun, B.; Meshram, S.G.; Tembhurne, J.V. An effective mobile-healthcare emerging emergency medical system using conformable chaotic maps. Soft Comput. 2021, 25, 8905–8920. [Google Scholar] [CrossRef]
- Ji, Y.; Lai, L.; Zhong, S.; Zhang, L. Bifurcation and chaos of a new discrete fractional-order logistic map. Commun. Nonlinear Sci. Numer. Simul. 2018, 57, 352–358. [Google Scholar] [CrossRef]
- Natiq, H.; Al-Saidi, N.M.G.; Said, M.R.M.; Kilicman, A. A new hyperchaotic map and its application for image encryption. Eur. Phys. J. Plus 2018, 133, 6. [Google Scholar] [CrossRef]
- Zahmoul, R.; Ejbali, R.; Zaied, M. Image encryption based on new Beta chaotic maps. Opt. Lasers Eng. 2017, 96, 39–49. [Google Scholar] [CrossRef]
- Zhang, G.; Ding, W.; Li, L. Image encryption algorithm based on tent delay-sine cascade with logistic map. Symmetry 2020, 12, 355. [Google Scholar] [CrossRef]
- Zhang, Y.-Q.; Hao, J.-L.; Wang, X.-Y. An efficient image encryption scheme based on S-boxes and fractional-order differential logistic map. IEEE Access 2020, 8, 54175–54188. [Google Scholar] [CrossRef]
- Veeman, D.; Natiq, H.; Al-Saidi, N.M.; Rajagopal, K.; Jafari, S.; Hussain, I. A New Megastable Chaotic Oscillator with Blinking Oscillation terms. Complexity 2021, 2021, 5518633. [Google Scholar] [CrossRef]
- Sangavi, V.; Thangavel, P. An image encryption algorithm based on fractal geometry. Procedia Comput. Sci. 2019, 165, 462–469. [Google Scholar] [CrossRef]
- Cattani, C.; Srivastava, H.M.; Yang, X.-J. Fractional Dynamics; De Gruyter Open Poland: Berlin, Germany, 2016. [Google Scholar]
- Campbell, D.M. Majorization-subordination theorems for locally univalent functions, II. Can. J. Math. 1973, 25, 420–425. [Google Scholar] [CrossRef]
- Li, T.; Du, B.; Liang, X. Image encryption algorithm based on logistic and two-dimensional lorenz. IEEE Access 2020, 8, 13792–13805. [Google Scholar] [CrossRef]
- Wang, X.; Guo, K. A new image alternate encryption algorithm based on chaotic map. Nonlinear Dyn. 2014, 76, 1943–1950. [Google Scholar] [CrossRef]
- Liu, L.; Miao, S. A new image encryption algorithm based on logistic chaotic map with varying parameter. SpringerPlus 2016, 5, 1–12. [Google Scholar] [CrossRef]
- Zhang, F.; Zhang, X.; Cao, M.; Ma, F.; Li, Z. Characteristic Analysis of 2D Lag-Complex Logistic Map and Its Application in Image Encryption. IEEE Multimed. 2021, 28, 96–106. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Pun, C.-M.; Chen, C.P. 2D Sine Logistic modulation map for image encryption. Inf. Sci. 2015, 297, 80–94. [Google Scholar] [CrossRef]
- Tong, X.J.; Wang, Z.; Zhang, M.; Liu, Y.; Xu, H.; Ma, J. An image encryption algorithm based on the perturbed high-dimensional chaotic map. Nonlinear Dyn. 2015, 80, 1493–1508. [Google Scholar] [CrossRef]

| Images | Plain | Encrypted |
|---|---|---|
| Barbara | 7.8056 | 7.9785 |
| Baboon | 7.3583 | 7.9995 |
| Boat | 7.1901 | 7.9865 |
| Lena | 7.7481 | 7.9995 |
| Average | 7.5255 | 7.9910 |
| Encryption Algorithm | Entropy |
|---|---|
| Wang and Guo 2014 [33] | 7.9977 |
| Liu Lingfeng 2016 [34] | 7.9995 |
| Li, Tao 2020 [32] | 7.9894 |
| Zhang Fangfanf 2021 [35] | 7.9994 |
| Proposed FCL map model | 7.9995 |
| Image | Plain | Encrypted | |
|---|---|---|---|
| Barbara | H | 0.8135 | −0.0006 |
| V | 0.8708 | 0.0025 | |
| D | 0.9294 | −0.0315 | |
| Baboon | H | 0.9371 | 0.0007 |
| V | 0.9485 | 0.0006 | |
| D | 0.9325 | −0.0459 | |
| Boat | H | 0.9371 | 0.0045 |
| V | 0.9324 | 0.0006 | |
| D | 0.9342 | 0.0218 | |
| Lena | H | 0.9387 | 0.0045 |
| V | 0.9812 | 0.0016 | |
| D | 0.97261 | 0.0017 | |
| Average | H | 0.9066 | 0.0025 |
| V | 0.93322 | 0.0013 | |
| D | 0.9421 | −0.0134 |
| Algorithm | Encryption Time (s) | Encrypted | |
|---|---|---|---|
| Hua et al. 2015 [36] | 0.2338 | H | 0.0024 |
| V | −0.0086 | ||
| D | 0.0402 | ||
| Tong et al. 2015 [37] | 0.1900 | H | 0.0038 |
| V | 0.0058 | ||
| D | 0.0133 | ||
| Liu, Lingfeng 2016 [34] | 0.0659 | H | 0.0021 |
| V | 0.0046 | ||
| D | 0.0033 | ||
| Li, Tao 2020 [32] | 0.4604 | H | 0.0033 |
| V | 0.0011 | ||
| D | 0.0008 | ||
| Proposed FCL map model | 0.0589 | H | 0.0025 |
| V | 0.0013 | ||
| D | −0.0134 |
| Image | NPCR | UACI |
|---|---|---|
| Barbara | 0.9967 | 0.3343 |
| Baboon | 0.9966 | 0.3396 |
| Boat | 0.9968 | 0.3358 |
| Lena | 0.99 68 | 0.3312 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Natiq, H.; Al-Saidi, N.M.G.; Obaiys, S.J.; Mahdi, M.N.; Farhan, A.K. Image Encryption Based on Local Fractional Derivative Complex Logistic Map. Symmetry 2022, 14, 1874. https://doi.org/10.3390/sym14091874
Natiq H, Al-Saidi NMG, Obaiys SJ, Mahdi MN, Farhan AK. Image Encryption Based on Local Fractional Derivative Complex Logistic Map. Symmetry. 2022; 14(9):1874. https://doi.org/10.3390/sym14091874
Chicago/Turabian StyleNatiq, Hayder, Nadia M. G. Al-Saidi, Suzan J. Obaiys, Mohammed Najah Mahdi, and Alaa Kadhim Farhan. 2022. "Image Encryption Based on Local Fractional Derivative Complex Logistic Map" Symmetry 14, no. 9: 1874. https://doi.org/10.3390/sym14091874
APA StyleNatiq, H., Al-Saidi, N. M. G., Obaiys, S. J., Mahdi, M. N., & Farhan, A. K. (2022). Image Encryption Based on Local Fractional Derivative Complex Logistic Map. Symmetry, 14(9), 1874. https://doi.org/10.3390/sym14091874









