Abstract
Reversible data hiding is a technique for embedding secret data into a cover media. Such technique has the ability to recover marked cover media to its original version after extracting the secret data. In this paper, a new reversible data hiding algorithm for videos H.264/AVC is proposed to improve the embedding capacity while the distortion drift is prevented. To embed the secret data into videos H.264/AVC without any intra-frame distortion drift, in our proposed scheme, the relationship of QDCT coefficients is explored. Then, a coefficient pair mapping mechanism in 2D histogram is introduced for embedding data. The experimental results demonstrated that the proposed scheme obtains reversibility. The proposed scheme prevents intra-frame distortion drift on the marked videos. In addition, the embedding capacity of the proposed scheme is superior to that of existing schemes while guaranteeing the high visual quality of marked videos.
1. Introduction
A huge amount of digital data containing private information is transmitted through the Internet each second. To prevent third parties from accessing the private information, many studies [1,2,3,4,5,6,7,8,9,10,11,12,13,14,15] have been proposed. Data hiding is one of the promising techniques to conceal digital secret message into the cover media i.e., audios, images, videos, database, DNA sequence, etc., to protect the security and privacy of such digital information from malicious attacks. Many data hiding algorithms [1,2,3,4,5,6,7,16,17,18,19,20] have been proposed for digital cover media in the last ten years.
Recently, Video, one of digital media, is used for data hiding due to its wide applications, i.e., surveillance camera and YouTube channels. In 2003, I.E.G. Richardson [8], proposed a new compression technique for video, called H.264/AVC (advanced video coding) for compressing the video sequences to save storage space. Recently, many data hiding schemes based on H.264/AVC coding [9,10,11,12,13,14,15,21,22,23] have been proposed to enhance the security of video sequences. In [9], Nguyen et al. embedded the secret data into motion vectors. However, their scheme obtained the low embedding capacity (EC), always smaller than 2 Kbit. Later on, to improve robustness, Zhang et al. [10] proposed a new scheme to embed a 2-D 8-bit watermark into the videos. Noorkami and Mersereau [11] used the quantized AC coefficients to conceal the watermark into H.264/AVC videos. Later, to enhance the robustness, Gong and Lu [12] employed a texture-masking-based perceptual model to hide the secret data. However, in two aforementioned schemes [11,12], the original version of embedded watermark is required to evaluate the existence of the embedded watermark in the marked video sequences.
Discrete cosine transform (DCT) coefficients of I-frames were used in all state-of-the-art schemes for embedding data into video sequences. However, these schemes suffered the intra-frame distortion drift issue. In order to solve this problem, Ma et al. [13] proposed a novel DCT-based data hiding algorithm by selecting three quantized DCT paired-coefficients (QDCT) for carrying the secret data. Nevertheless, their scheme provided the low visual quality of marked video sequences, and unsatisfied embedding capacity. In 2011, Huo et al. [14] applied controllable error-drift elimination for a new data hiding scheme to enhance the quality of the marked videos. However, their scheme offered a low embedding capacity. In 2013, to increase embedding capacity of Ma et al.’s scheme [13], in [15], Lin et al. explored the QDCT coefficients’ characteristic for data embedding. Lin et al.’s scheme obtained a higher embedding capacity than that of Ma et al.’s scheme. However, the scheme [15] obtained the unsatisfactory quality of marked videos. To enhance visual quality of marked videos while keeping high EC, Nguyen et al. [23] partitioned the blocks into two coefficient groups, i.e., hiding coefficient group and preventing coefficient group. Then, the coefficients in the hiding group are applied to conceal the secret information while the other group is utilized to avoid the distortion drift in the marked video sequences. Their scheme obtained high performance in terms of EC while maintaining good quality of marked videos. However, their cover videos are affected permanently and cannot be restored to their original version.
In order to solve this shortcoming, in 2006, Ni et al. [21] introduced histogram shifting (HS) to reversible data hiding (RDH) scheme for still images. In their scheme, zero-point values and peak-point values of the histogram are utilized to hide data. Ni et al.’s scheme guaranteed the reversibility. However, their visual quality of marked images is always smaller than 49 dB for different kinds of images. To improve the visual quality further, some RDH schemes based on histogram shifting [4,7] are proposed. Recently, several RDH studies are proposed for H.264/AVC videos [22,24,25,26,27,28]. The secret data can be embedded into the QDCT coefficients of intra-frames, which meet the directions of intra-frame prediction, therefore they could avert the distortion drift [24,25]. The algorithm [24] could achieve good visual distortion while the algorithm [25] improved the robustness by using BCH syndrome code before data hiding. However, these schemes [24,25] obtained the low EC. Later on, RDH schemes [26,27] applied motion vector (MV) data pre-processing, the selection of most suitable embedding region for H.264/AVC code. However, Chung et al.’s method [26] only embedded MVs of MBs into zero QDCT coefficients. To solve the shortcoming in Chung et al.’s scheme, in [28]. Xu et al. fully exploited the number of coefficients and produced extra nonzero residual blocks for embedding data. Although, these schemes [26,27,28] achieved the good quality of marked videos, however, their schemes suffered the distortion drift. To avert the distortion drift, in [22], Liu et al. used Shamir’s (t, n)-threshold secret sharing to embed the secret data into videos H.264/AVC. However, the EC of Liu et al.’s scheme is too low, when it is always smaller than 200 bits.
To avoid distortion drift, many data hiding schemes [13,15,22,23] have been proposed. However, most of them suffered from the low EC. Moreover, after containing the secret data, the marked videos obtained by these previous schemes are affected permanently and cannot be restored to their original version to improve. Inspired from the histogram shifting-based RDH scheme [21] for the still images, in this paper, to further improve embedding capacity while obtaining reversibility, a new RDH scheme is proposed for H.264/AVC videos. In the proposed scheme, to prevent the distortion drift, QDCT coefficient pairs of H.264/AVC videos are selected according to its context. Then, to achieve reversibility, a 2D histogram is generated by counting suitable QDCT coefficient pairs. The CPM mapping, injective mapping, is defined to project a coefficient pair to another pair for embedding the secret data. To enhance the security, the secret data are encrypted by using symmetric key cryptography. Finally, RDH algorithm is implemented by using CPM mapping. By using the 2D histogram and the CPM mapping, more pairs are applied to contain the secret bits while the distortion drift is avoided as well. Experimental results illustrated that our proposed scheme obtains reversibility. In addition, the proposed scheme outperforms some previous schemes in terms of the EC while maintaining good visual quality of marked videos.
2. Related Works
2.1. Intra-Frame Prediction
H.264/AVC coding [8] is proposed to decrease the redundancy of Intra-frames. H.264/AVC algorithm partitions intra-frames into 4 × 4 or 16 × 16 macroblocks (MBs). However, the alternation of 16 × 16 intra MBs is easy to be recognized in a human eye system. Therefore, to overcome this shortcoming, 4 × 4 intra MB blocks are usually used for further processing. In the H.264/AVC algorithm, the left block and the upper block are used to predict the values of the current luminance block. Sixteen samples of the current block in Figure 1, labeled from a to p in the current luminance block, will be predicted according to the boundary pixels of the left and upper blocks, labeled from A to M. The prediction of current luminance block is calculated by one of nine modes, shown as in Figure 2.
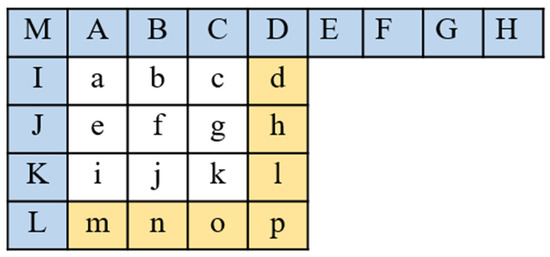
Figure 1.
The current luminance block .
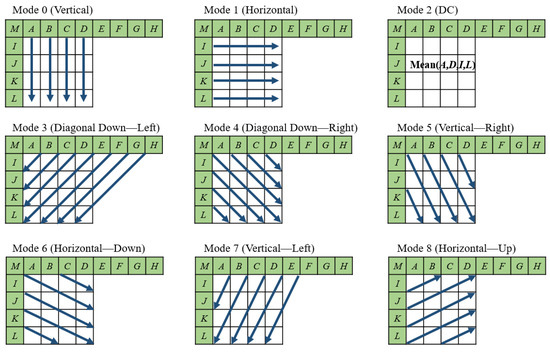
Figure 2.
Nine 4 × 4 luminance prediction modes [8].
2.2. DCT-Based Data Hiding Schemes for Video H.264/AVC
In [13], Ma et al. divided 4 × 4 blocks into three different conditions, i.e., Condition 1, Condition 2, and Condition 3, as shown in Table 1. Condition 1, named Right-Mode, is defined by prediction of the right block, effects by mode 0, 3, or 7. Meanwhile, Condition 2 is determined by Under-Left-Mode ∈ {0, 1, 2, 3, 4, 5, 6, 8} and Under-Mode ∈ {1, 8} in 4 × 4 block mode. The determination of Condition 3 is performed by Under-Right-Mode ∈ {0, 1, 2, 3, 7, 8}. By doing so, Ma et al.’s scheme [13] prevented the distortion drift in the MB blocks during the embedding process. However, Ma et al.’s scheme offered the low EC.

Table 1.
Three different conditions of Ma et al.’s scheme.
Later on, to increase the EC of Ma et al.’s scheme, in [15], Lin et al. fully exploited the characteristic of MB blocks; up to the remaining 54% MB blocks are used for embedding. For embedding data, Lin et al. re-classified 4 × 4 blocks into five different categories, i.e., Cat1, Cat2, Cat3, Cat4, and Cat5. Then, the Cat3 has no reference pixels, thus, they can embed more secret bits, up to 16 bits into one block. While the reference pixels in Cat5 are all of the pixels at under and right of the block, so only one bit can be embedded. According to schemes [13,15], three types can be launched as shown in Table 2. In Type 1, Condition 1 is equal to True (T) and Condition 2 is equal to False (F), respectively. This type refers to pixels d, h, l, and p. The Case2, with the reference pixels m, n, o and p, is used if the Condition 2 is True, and Condition 1 is False. For the Type 3, by reference pixel is p, the Condition 3 must be True, but the Condition 1 and Condition 2 are both False.

Table 2.
Three launched cases according to schemes [13,15].
By applying five categories, Lin et al.’s scheme [15] obtained the higher EC when the remaining 54% of MB blocks are exploited. However, Lin et al.’s scheme suffered losing a part of the video stream which cannot be completely recovered after extracting the secret data. Therefore, to reconstruct the marked videos to its original version completely, the new RDH scheme for videos H.264/AVC is proposed and described in the next section to obtain reversibility while maintaining the high EC and good quality of marked videos.
3. Proposed Scheme
In this section, the RDH scheme is proposed without intra-frame distortion drift. In the proposed scheme, an 2D QDCT histogram is constructed. Then, a coefficient pair mapping (CPM) which is an injective mapping defined on QDCT pairs is used for embedding data. In this section, we first introduce the CPM technique defined on QDCT coefficient pairs in Section 3.1. Then in Section 3.2, we present our CPM-based RDH scheme. By using the 2D QDCT histogram, the secret data can be embedded by our approach without any distortion drift while the reversibility is maintained. Then, the detailed embedding and extracting algorithms of our proposed scheme are summarized in Section 3.3 and 3.4, respectively.
3.1. Coefficient Pair Mapping
In H.264/AVC coding, integer discrete cosine transform (IDCT) is used for the 4 × 4 residual block Ri,j. Then, Equation (1) is applied to generate quantized DCT (QDCT) coefficients.
where is the QDCT coefficients of the residual block Ri,j; the matrix CTf is transformed from the matrix Cf,
The ⊗ operator denotes an element-by-element product of two matrices, and Q is the step size of quantizer which is determined by a quantization parameter.
Then, a dequantization mechanism is used to reconstruct the residual block Ri,j, and inverse IDCT operation is performed by using Equation (2).
where ,
To avoid distortion drift, in Ma et al.’s scheme, the pair of coefficients is perturbed. Take a pair of coefficients (Y11, Y31) belonging to Type 2 in Table 2 as an example. It can be seen that after permutation, (Y11 + 1, Y31 − 1) is obtained. Then, the difference value between two matrices, and , is presented in Equation (3).
Assume that the block is perturbed to generate , then their difference value can be computed by Equation (4).
It is obvious that in , the fourth row is a zero vector and . Obviously the fourth row of both and is the same value, as a result, in this type, the reference pixels are kept unchanged during the process, meaning that distortion drift is free. Taking these characteristics, to achieve the reversibility, in the proposed scheme, coefficient pair mapping (CPM) is used. All suitable coefficient pairs in three types in Table 2 are selected for containing the secret bits. In addition, to prevent the distortion drift, an 2D histogram is constructed according to the frequency of pairs of coefficients. Then, the secret data are hidden by shifting the 2D histogram. It is obvious that the pair of coefficients is an element of . Then, we need to partition into three disjoint subsets in Figure 3, one subset (black point) is kept unchanged during the embedding process, the second one (blue point) is used to embed the secret data by expansion process, and the third one (red point) is shifted to generate vacant room to guarantee reversibility. It is obvious that each blue point is projected to red one (orange arrows). Each red point is projected to another red point (indicated by dash green arrows).
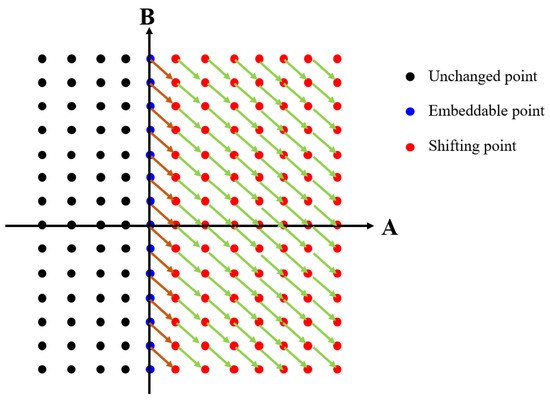
Figure 3.
Illustration for the 2D QDCT histogram.
In particular, each point indicates a coefficient pair. According to the CPM mechanism, for each cover coefficient pair (Ai, Bi), the marked value is obtained by using the following way:
- (1)
- If (Ai, Bi) is the black point, it is kept unchanged.
- (2)
- If (Ai, Bi) is the blue point
- If the secret bit w = 0, the marked coefficient pair is equal to (Ai, Bi).
- If the secret bit w = 1, the marked coefficient pair is set to the corresponding red point.
- (3)
- If (Ai, Bi) is the red point, the marked coefficient pair is set to the corresponding red point.
The process of the data extraction and the cover image reconstruction can be applied to the CPM mechanism because of the injection property, i.e., each point has at most one inverse.
3.2. CPM Based RDH Scheme
To embed the secret bit w into a coefficient pair (Ai, Bi), we will modify this pair to either (Ai + w, Bi − w) or (Ai − w, Bi + w). In this situation, since the pair (Ai, Bi) has two modification directions, only the direction with minimum modification is selected for concealing the secret data. Based on these two modification directions, we will introduce a new RDH scheme based on the CPM algorithm.
Here, our embedding algorithm based on CPM is briefly described. First, to avoid distortion drift, for each selected type, four pairs of coefficients are extracted as (Ai, Bi) = {(Y11, Y13), (Y21, Y23), (Y31, Y33), (Y41, Y43)}. Then, each pair is located in the 2D histogram. To embed one secret bit, each blue point in the histogram is projected to a red one while each red point is projected to another red one. This means that the shifting process is easily implemented in the 2D histogram to guarantee the reversibility, as shown in Figure 3. Note that there are many ways to utilize the CPM for various RDH schemes. As for CPM shown in Figure 3, the main idea is to choose as many as the high frequency points to conceal the secret information. It is obvious that most of QDCT coefficients Ai of video streams are concentrated on around the value of 0 in the histogram. To obtain the high embedding capacity, the coefficient Ai with the value of 0 should be used. To give a better explanation, we take blue points (Ai, Bi) = (0, Bi) for containing the secret data. In addition, the other points are shifted according to the one selected direction with the minimum distortion. The superior performance of CPM will be experimentally shown in the next section.
Notice that the coefficient pairs selected to carry secret data belong to the block case of these coefficient pairs. By this means, when the block case is equal to 1, coefficient pairs are vertically selected as Figure 4a, while the block case is equal to 2 or 3, the pairs of coefficients in the current block are horizontally used as Figure 4b. Suppose that the secret data bit is w. For Type 1, the coefficient Ai is equal to Yi,1, i = 1, …, 4. And for Type 2 and Type 3, the coefficient Ai is equal to Y1,i, i = 1, …, 4. The proposed embedding process is implemented by CPM mapping in the 2D histogram. The secret bit w is hidden into the coefficient pair by Equation (5).
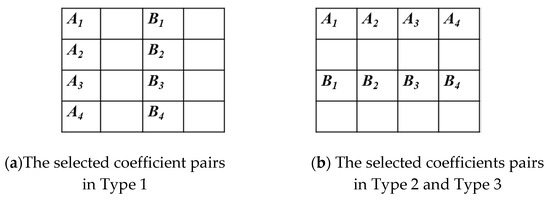
Figure 4.
The selected coefficient pairs belong to the block type.
3.3. Embedding Algorithm
In this section, the secret data M is embedded into the H.264/AVC video H. In Figure 5, the embedding process contains several basic steps. First, the entropy encoder is used to decode the raw video streams into the intra-frame modes and QDCT coefficients. Then, the appropriate coefficient pairs of the blocks in Types of 1, 2, or 3 are collected for constructing the 2D histogram. It is noted that the I-frames, P-frames, and B-frames both are obtained after decoding. To preserve the quality of marked videos, embedding algorithm is only performed on the I-frames. After the decoding process, the I-frames are used for mode prediction. Then, macroblocks are determined. For each macroblock, all corresponding embeddable coefficient pairs are selected for CPM mapping.
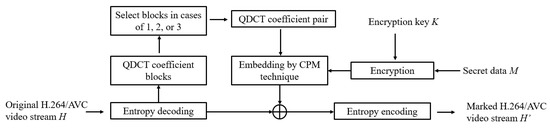
Figure 5.
The flowchart of the embedding process.
For each coefficient pair, the value of coefficient Ai is checked to embed the secret bit by using Equation (5). To avoid drift distortion, as discussed above, the CPM mechanism is used. Therefore, if the value of Ai is increased, then the value of Bi is reduced, and vice versa. Moreover, in the proposed scheme, to increase the security of the proposed scheme, before the embedding process, the secret data M should be encrypted with encryption key K by using one of the well-known encryption algorithms, i.e., RSA, AES, … [29]. The detailed embedding algorithm, Algorithm 1, is described as following.
| Algorithm 1: Embedding algorithm |
| Input: The original H.264/AVC video stream H, the secret data M and the encryption key K. Output: The marked H.264/AVC video stream H’. Step 1: The H.264/AVC video stream H is decoded by Entropy encoder to generate blocks of QDCT coefficients. Step 2: Encrypt the message M with the encryption key K. Step 3: from QDCT coefficient blocks. Step 4: Read coefficient pair (Ai, Bi) from the QDCT coefficient blocks, and apply Equation (5) to hide the secret bit w. Step 5: Steps 3 to 4 are repeatedly used until the entire of QDCT coefficients are handled completely, then the entropy encoder is used to generate the marked video stream H’. |
After the above-mentioned four steps are processed completely, the marked H.264/AVC video stream is obtained and transferred to the receiver. To ensure the security of the proposed scheme, the encryption key K is sent to the receiver through the secure channel.
3.4. Extracting Algorithm
After receiving the marked video, the receiver applies the extracting algorithm to extract the secret message and to restore the marked video to its original version. Figure 6 shows all the main steps of the extracting process. After entropy decoding, the hidden data are extracted from MB blocks. The hidden data W (w1, w2, …, wn), where wi ∈ {0, 1}) is extracted by Equation (6).
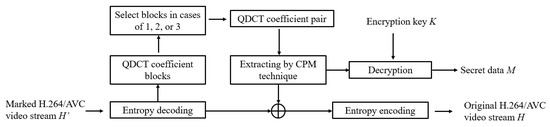
Figure 6.
The diagram of the extracting process.
Since the hidden data are extracted completely, the values of coefficient pairs are restored by Equation (7).
The following algorithm, Algorithm 2, illustrates the extracting process.
| Algorithm 2: Extracting algorithm |
| Input: The marked video stream H’ and the encryption key K. Output: The original video stream H, the secret data M. Step 1: The Entropy encoder is used to decode the marked video H’ into QDCT coefficient blocks. Step 2: Read the block from QDCT coefficient blocks. Step 3: Read coefficient pairs (Ai, Bi) from the QDCT coefficient block. For each QDCT coefficient pair, one secret bit is extracted by Equation (6) while the original coefficient pair is reconstructed by Equation (7). Step 4: Repeat Steps 3 to 4 until the entire QDCT coefficient blocks are encoded completely, the encrypted secret data are extracted and decrypted with the encryption key K to obtain the secret data M. Then the entropy encoder is used to generate the original H.264/AVC video stream H. |
4. Experimental Results
A number of experiments are conducted to compare existing algorithms [13,15,22,23] with the proposed algorithm on ten test video streams with quarter common intermediate format, QCIF, 176 × 144, i.e., Akiyo, Bridge-Close, Bridge-Far, Carphone, Claire, Claire, Container, Hall, Mother-Daughter, News, Salesman. The test streams are encoded into 300 frames at 30 fps (frames per second) with ten I-frames for each stream. All algorithms are programmed by Matlab R2015a. All implementations were realized on a computer with Core i3 CPU, 4 GB RAM. The operating system was Microsoft Windows 10. All of them with the size of GOP were selected to be 30 frames and its structure was equal to IBPBP. To compare with other methods, we used six different QPs, 22, 24, 26, 28, 30, and 32 for the above ten sequences. This study used encoding and decoding methods developed by Muhit et al.’s [30].
Table 3 shows the statistics of possible data that can be embedded into each video when the quantization parameter (QP) is in {22, 24, 26, 28, 30, 32}. The embedding capacity of Claire video (27,504 bits) is highest with QP = 32 while the embedding capacity of Salesman video (11,225 bits) is lowest with QP = 22 among ten test videos. The average capacity of videos with QP = 28 is 19,551 bits.

Table 3.
The embedding capacity of ten test videos with various QPs.
The peak signal-to-noise-ratio (PSNR) is applied to evaluate the quality of two frames as follows.
where MSE which is computed by Equation (9) is mean square error.
where m, n are the number of rows and columns of the current frame, O and M are the original and marked frames, respectively.
The well-known SSIM index [31] is adopted to evaluate the visual quality. In our experiment, the SSIM index between the original and marked frames is computed by Equation (10).
where Oi and Ei indicate the ith MB block of original and marked frames; N is the number of MB blocks; and are the mean variance of the block O and the block E; is the covariance of O and E; c1 = (k1 × L)2 and c2 = (k2 × L)2 with L = 255, k1 = 0.01, and k2 = 0.03.
In the experiment, to evaluate the visual quality of marked video, both PSNR and SSIM values are used. Table 4 presents the proposed scheme’s visual quality when embedding maximum secret bits. It is obvious that the PSNR and SSIM values are reduced when the value of QP is increased. The main reason is since the large value of QP is used, more QDCT coefficient pairs are found for embedding data causing more distortion in the marked videos. However, the average PSNR of the proposed scheme is still larger than 33 dB, while the value of SSIM is greater than 0.84.

Table 4.
The quality of the marked videos with various QPs.
In this section, to show the solid results of the proposed scheme, two DNA sequences [32], downloaded from the GenBank database, are also used as the secret data. The DNA sequence consists of four base types, i.e., A, G, C, and T. Each base type is encoded by a corresponding bits of 00, 01, 10, and 11, respectively. Table 5 and Table 6 show the quality of marked videos after embedding the different size of the DNA sequences, i.e., the sequence NC_007020, contained 11,440 nucleotides (~22,880 bits) and the sequence NC_007203 with 6909 nts (~13,818 bits), respectively. It is noted that, in Table 5, with the larger embedding capacity, the average of PSNR and the average of SSIM are still high, with 32.63 dB and 0.844, respectively. It is obvious that if the smaller embedding capacity is embedded then the better visual quality is obtained by the proposed scheme and vice versa.

Table 5.
The quality of marked videos with the large embedding capacity after embedding DNA sequences NC_007020 (11,440 nts = ~22,880 bits)) with QP = 28.

Table 6.
The quality of marked videos with the smaller embedding capacity after embedding DNA sequences NC_007203 (6909 nts = ~13,818 bits) with QP = 28.
Table 7 compares the performance of the proposed scheme with four previous schemes, including: Liu et al. [22], Ma et al. [13], Lin et al. [15], and Nguyen et al. [23], when the quantization step QP = 28 is used. The PSNR and the SSIM of the proposed scheme is smaller than the other four schemes [13,15,22,23]. However, the maximum capacity of the proposed scheme is the highest one among the five schemes, up to ten times larger than that of Lui et al.’s scheme [22]. Moreover, the proposed algorithm has the ability to reconstruct the marked videos to their original version.

Table 7.
Performance comparison among five schemes with QP = 28.
5. Conclusions
In this paper, a new RDH scheme is proposed for videos H.246/AVC. In the proposed scheme, the cover video is decoded by using the entropy encoder to generate QDCT coefficients. The 2D histogram of QDCT coefficients is generated by counting suitable coefficient pairs. Then, the CPM mapping mechanism, injective mapping, is defined for embedding data. To increase the security of the proposed scheme, the secret data are encrypted by using symmetric key cryptography. Then, the CPM mechanism is used to hide the encrypted secret data into the videos without any distortion drift while guaranteeing the reversibility. The experimental results showed that the proposed algorithm obtains the highest embedding capacity among five schemes while maintaining the good visual quality of marked videos. Moreover, the proposed algorithm obtains the reversibility and prevents intra-frame distortion drift on the marked videos during the embedding process. Although obtaining both the high embedding capacity and the good quality of marked videos, however, in the future, more research should be taken to improve the quality of marked videos when containing the large embedding capacity.
Funding
This research was funded by Tra Vinh University under grant contract number 207/HĐ.HĐKH–ĐHTV.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Jing, Z.; Ho, A.T.S.; Gang, Q.; Marziliano, P. Robust Video Watermarking of H.264/AVC. IEEE Trans. Circuits Syst. II Express Briefs 2007, 54, 205–209. [Google Scholar]
- Dragoi, I.C.; Coltuc, D. On the Security of Reversible Data Hiding in Encrypted Images by MSB Prediction. IEEE Trans. Inf. Forensics Secur. 2021, 16, 187–189. [Google Scholar] [CrossRef]
- Zheng, S.; Wang, Y.; Hu, D. Lossless Data Hiding Based on Homomorphic Cryptosystem. IEEE Trans. Depend. Secur. Comput. 2021, 18, 692–705. [Google Scholar] [CrossRef]
- He, J.; Chen, J.; Tang, S. Reversible Data Hiding in JPEG Images Based on Negative Influence Models. IEEE Trans. Inf. Forensics Secur. 2019, 15, 2121–2133. [Google Scholar] [CrossRef]
- Chang, C.C.; Nguyen, T.S. A reversible data hiding scheme for SMVQ indices. Informatica 2014, 25, 523–540. [Google Scholar] [CrossRef]
- He, J.; Chen, J.; Luo, W.; Tang, S.; Huang, J. A Novel High-Capacity Reversible Data Hiding Scheme for Encrypted JPEG Bitstreams. IEEE Trans. Circuits Syst. Video Technol. 2019, 29, 3501–3515. [Google Scholar] [CrossRef]
- Nguyen, T.S.; Tram, H.N. New Reversible Data Hiding Algorithm Based on Edge Detection and PVO Mechanisms. J. Commun. Inf. Syst. 2022, 37, 77–85. [Google Scholar] [CrossRef]
- Richardson, I.E.H. 264 and MPEG-4 Video Compression: Video Coding for Next-Generation Multimedia; Wiley: Chichester, UK, 2003. [Google Scholar]
- Nguyen, C.V.; Tay, D.; Deng, G. A fast watermarking system for H.264/AVC video. In Proceedings of the IEEE Asia-Pacific Conference on Circuits and Systems, Singapore, 4–7 December 2006; pp. 81–84. [Google Scholar]
- Nguyen, T.S. Fragile watermarking for image authentication based on DWT-SVD-DCT techniques. Multimed. Tools Appl. 2021, 80, 25107–25119. [Google Scholar] [CrossRef]
- Noorkami, M.; Mersereau, R.M. A frame work for robust watermarking of H.264-encoded video with controllable detection performance. IEEE Trans. Inform. Forensics Secur. 2007, 2, 14–23. [Google Scholar] [CrossRef]
- Gong, X.; Lu, H.M. Towards fast and robust watermarking scheme for H.264 video. In Proceedings of the 2008 Tenth IEEE International Symposium on Multimedia, Berkeley, CA, USA, 15–17 December 2008; pp. 649–653. [Google Scholar]
- Ma, X.J.; Li, J.T.; Tu, H.; Zhang, B. A data hiding algorithm for H.264/AVC video streams without intra-frame distortion drift. IEEE Trans. Circuits Systs. Video Technol. 2010, 20, 1320–1330. [Google Scholar] [CrossRef]
- Huo, W.; Zhu, Y.; Chen, H. A controllable error-drift elimination scheme for watermarking algorithm in H.264/AVC stream. IEEE Signal Process. Lett. 2011, 18, 535–538. [Google Scholar] [CrossRef]
- Lin, T.J.; Chung, K.L.; Chang, P.C.; Huang, Y.H.; Liao, H.Y.M.; Fang, C.Y. An improved DCT-based perturbation scheme for high capacity data hiding in H.264/AVC intra frames. J. Syst. Softw. 2013, 86, 604–614. [Google Scholar] [CrossRef]
- Chang, Q.; Li, X.; Zhao, Y. Reversible Data Hiding for Color Images Based on Adaptive Three-Dimensional Histogram Modification. IEEE Trans. Circuits Syst. Video Technol. 2022, 1. [Google Scholar] [CrossRef]
- Nguyen, T.S.; Chang, C.C.; Lin, C.C. High capacity reversible data hiding scheme based on AMBTC for encrypted images. J. Internet Technol. 2022, 23, 255–266. [Google Scholar] [CrossRef]
- Chang, C.-C.; Nguyen, T.-S.; Lin, C.C. A Reversible Database Watermark Scheme for Textual and Numerical Datasets. In Proceedings of the 2021 IEEE/ACIS 22nd International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD), Taichung, Taiwan, 24–26 November 2021; pp. 208–212. [Google Scholar]
- Lin, C.C.; Nguyen, T.S.; Chang, C.C. LRW-CRDB: Lossless robust watermarking scheme for categorical relational databases. Symmetry 2021, 13, 2191. [Google Scholar] [CrossRef]
- Ning, Z.; Niu, K.; Lin, Y.; Pan, F. Video Reversible Data Hiding Based on Motion Vector. In Proceedings of the 7th International Conference on Intelligent Computing and Signal Processing (ICSP), Xi’an, China, 15–17 April 2022; pp. 656–660. [Google Scholar] [CrossRef]
- Ni, Z.; Shi, Y.-Q.; Ansari, N.; Su, W. Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 2006, 16, 354–362. [Google Scholar]
- Liu, Y.; Chen, L.; Hu, M.; Jia, Z.; Jia, S.; Zhao, H. A reversible data hiding method for H.264 with Shamir’s (t, n)-threshold secret sharing. Neurocomputing 2016, 188, 63–70. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Nguyen, T.S.; Hsu, F.R.; Hsien, H.Y. A novel data hiding scheme for video H. 264/AVC without distortion drift. Multimed. Tools Appl. 2019, 78, 16033–16052. [Google Scholar] [CrossRef]
- Liu, Y.; Zhitang, L.; Ma, X. Reversible data hiding scheme based on H. 264/AVC without distortion drift. J. Softw. 2012, 7, 1059–1065. [Google Scholar] [CrossRef][Green Version]
- Liu, Y.; Ju, L.; Hu, M.; Ma, X.; Zhao, H. A robust reversible data hiding scheme for H.264 without distortion drift. Neurocomputing 2015, 151, 1053–1062. [Google Scholar] [CrossRef]
- Chung, K.L.; Huang, Y.H.; Chang, P.C.; Liao, H.Y.M. Reversible Data Hiding-Based Approach for Intra-Frame Error Concealment in H.264/AVC. IEEE Trans. Circuits Syst. Video Technol. 2010, 20, 1643–1647. [Google Scholar] [CrossRef]
- Fallahpour, M.; David, M. Reversible data hiding based on H. 264/AVC intra prediction. In Digital Watermarking; Springer: Berlin/Heidelberg, Germany, 2008; pp. 52–60. [Google Scholar]
- Xu, D.; Wang, R.; Shi, Y.Q. An improved reversible data hiding-based approach for intra-frame error concealment in H.264/AVC. J. Vis. Commun. Image Represent. 2014, 25, 410–422. [Google Scholar] [CrossRef]
- Bertaccini, M. Cryptography Algorithms; Packt Publishing: Birrmingham, UK, 2022. [Google Scholar]
- Muhit, A.A.; Pickering, M.R.; Frater, M.R.; Arnold, J.F. Video Coding Using Elastic Motion Model and Larger Blocks. IEEE Trans. Circuits Syst. Video Technol. 2010, 20, 661–672. [Google Scholar] [CrossRef]
- Wang, Z.; Bovik, A.C.; Sheikh, H.R.; Simoncelli, E.P. Image quality assessment: From error visibility to structural similarity. IEEE Trans. Image Process. 2004, 13, 600–612. [Google Scholar] [CrossRef]
- Chien, N.D.; Nguyen, T.S.; Hsu, F.R. An algorithm for DNA sequence hiding in H. 264/AVC video. In Proceedings of the Seventh Symposium on Information and Communication Technology ACM, Ho Chi Minh, Vietnam, 8–9 December 2016; pp. 229–234. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).