Adversarial Malicious Encrypted Traffic Detection Based on Refined Session Analysis
Abstract
1. Introduction
- 1.
- After a thorough literature review, first, a method to detect adversarial malicious encrypted traffic is proposed in this study.
- 2.
- Based on the research of adversarial malicious encrypted traffic generation technology, this paper proposes several feasible adversarial sample generation methods for malicious encrypted traffic. The malicious encrypted traffic generated for this purpose is able to deceive the current malicious encrypted traffic detection methods, with a probability of more than 99%.
- 3.
- By analyzing the adversarial sample generation method of malicious encrypted traffic, an improved session analysis method is proposed to better detect adversarial encrypted traffic. The key idea of this method is to extract and compute malicious traffic features that are not easily affected by encryption, reduce the impact of malicious encrypted traffic forgery, and improve the accuracy of adversarial malicious encrypted traffic detection. In the existing adversarial malicious encryption traffic samples, the detection accuracy is more than 95%.
2. Related Work
2.1. Research on the Classification of Encrypted Traffic
2.1.1. Research on Traditional Encrypted Traffic Classification
2.1.2. Current Research on Encrypted Traffic Classification
2.2. Detection of Malicious Encrypted Traffic
2.2.1. Traditional Malicious Encrypted Traffic Detection Methods
2.2.2. Current Research on Malicious Encrypted Traffic Detection
2.3. Adversarial Malicious Encrypted Traffic Research
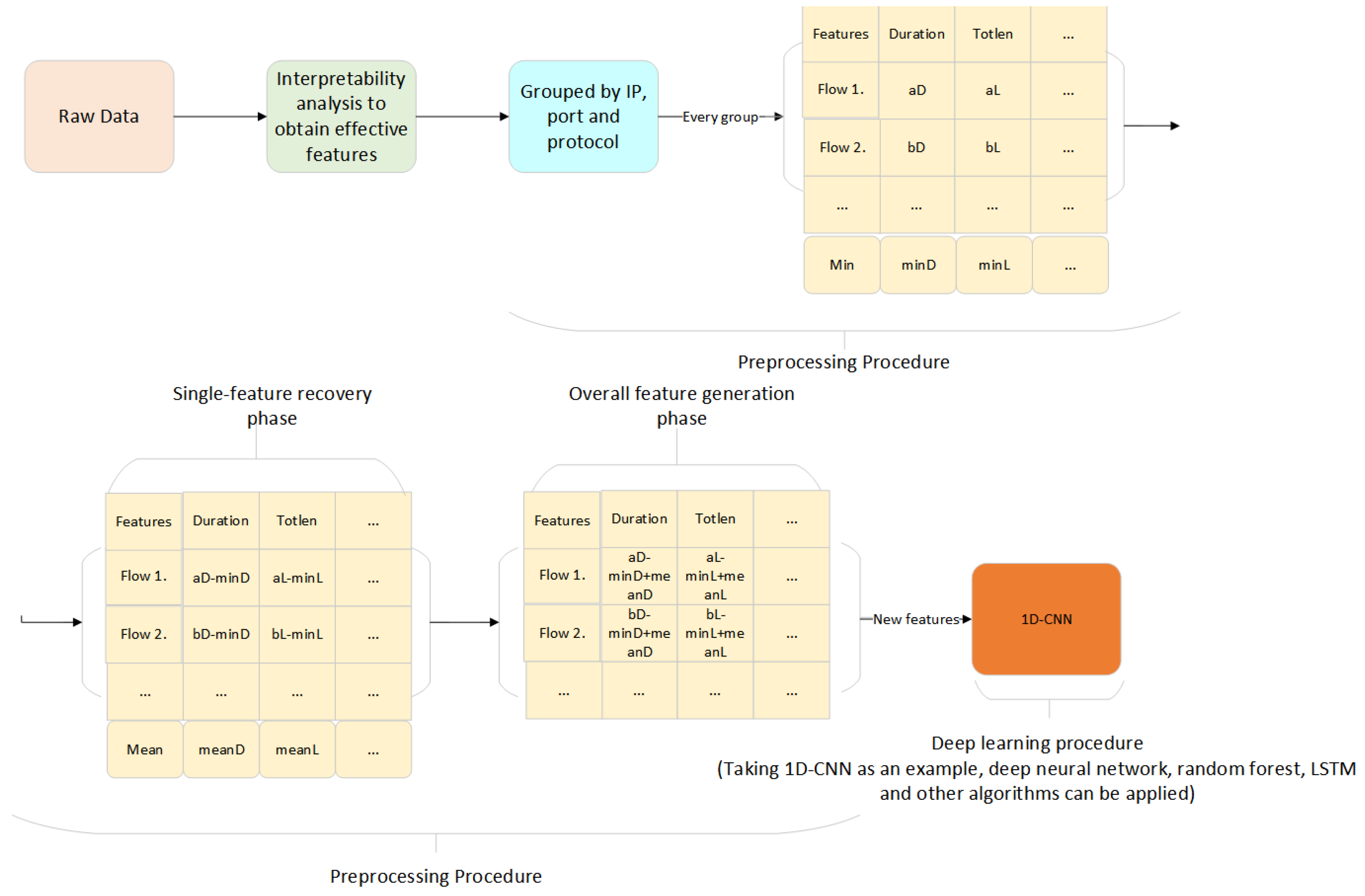
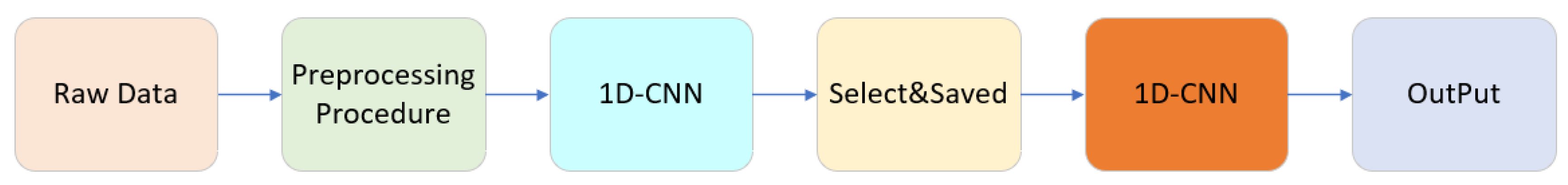
3. ADRSA
3.1. Analysis of Encrypted Traffic Features and Refined Session Analysis
| Algorithm 1 Refined detection of session analysis |
| INPUT: A feature file F containing statistical features obtained from traffic files OUTPUT: Refined feature file O Prepare a queue Q to store each group //Step 1. Gets groups with IP as the key to Q Group feature file F by IP Put each group into queue Q //Step 2. Each group is processed while Q is not empty do Take Q out of the queue and assign it to Qi Purify flow by removing extraneous features (IP address, port, protocol, timestamp) Get the average value MEANi of each grouping //Step 3. Each flow in the grouping gets the overall features while Qi is not empty do //Processing of each data group Take Qi out of the queue and assign it to V while Vi is not empty do //Each field of each data is processed Vi plus the average MEANi of the corresponding field end while end while //Step 4. Save as a new feature file O Write the result to file O end while |
3.2. Generation of a Malicious Encrypted Traffic Adversarial Sample
- (1)
- Both variables are of continuous data, obtained by measurement.
- (2)
- The overall distribution of the two variables is a normal distribution, close to a normal distribution, or at least a unimodal symmetric distribution.
- (3)
- The data must be paired, and the two variables should come from the same population or sample measurement.
- (4)
- There is a linear relationship between the two samples.
- (5)
- A large sample size (≥30) is required.
| Algorithm 2 Generation of malicious encrypted traffic adversarial sample |
| INPUT: Configure information (CI), Adversarial modes (MOD) CI includes IP port certificate, etc. MOD =0 modify time features, =1 modify static features OUTPUT: Generate a large number of adversarial samples //Step 1. Initialize connection parameters. Establish encrypted connection //Step 2. Send data while is not break do Read data from the buffer If MOD = 0 then //Extend time The sleep time is calculated according to the normal traffic time and malicious traffic time Sleep for a specified period of time Send read buffer data Close encrypted connection else //Send redundant packets Construct redundant packets Send redundant packets Send read buffer data Close encrypted connections end if end while |
3.3. Detection of Malicious Encrypted Traffic Adversarial Samples
| Algorithm 3 Detection of malicious encrypted traffic adversarial samples |
| INPUT: A feature file F containing statistical features obtained from traffic files OUTPUT: The restored feature file O Prepare a queue Q to store each group //Step 1. Gets groups with IP as the key to Q Group feature file F by IP Put each group into queue Q //Step 2. Each group is processed while Q is not empty do Take Q out of the queue and assign it to Qi Purify flow by removing extraneous features (IP address, port, protocol, timestamp) Get the minimum flow duration MIN for each group, MIN = EMIN + S. EX is the duration of X. X is malicious encrypted traffic without forgery; S is the extended time to forgery. //Step 3. Restore the forged features //The minimum flow duration of each flow is calculated, and the minimum value is subtracted from each flow. Other features are calculated according to the flow duration while Qi is not empty do //Processing of each data group Take Qi out of the queue and assign it to T, T = ET + S if T is flow duration then //After restoration T = T—MIN = (ET + S) − (EMIN + S), The effect of extended time S is eliminated. else Additional features are calculated based on flow duration end if end while //Step 4. Save as a new feature file O Write the result to file O end while |
4. Experimental Results and Analysis
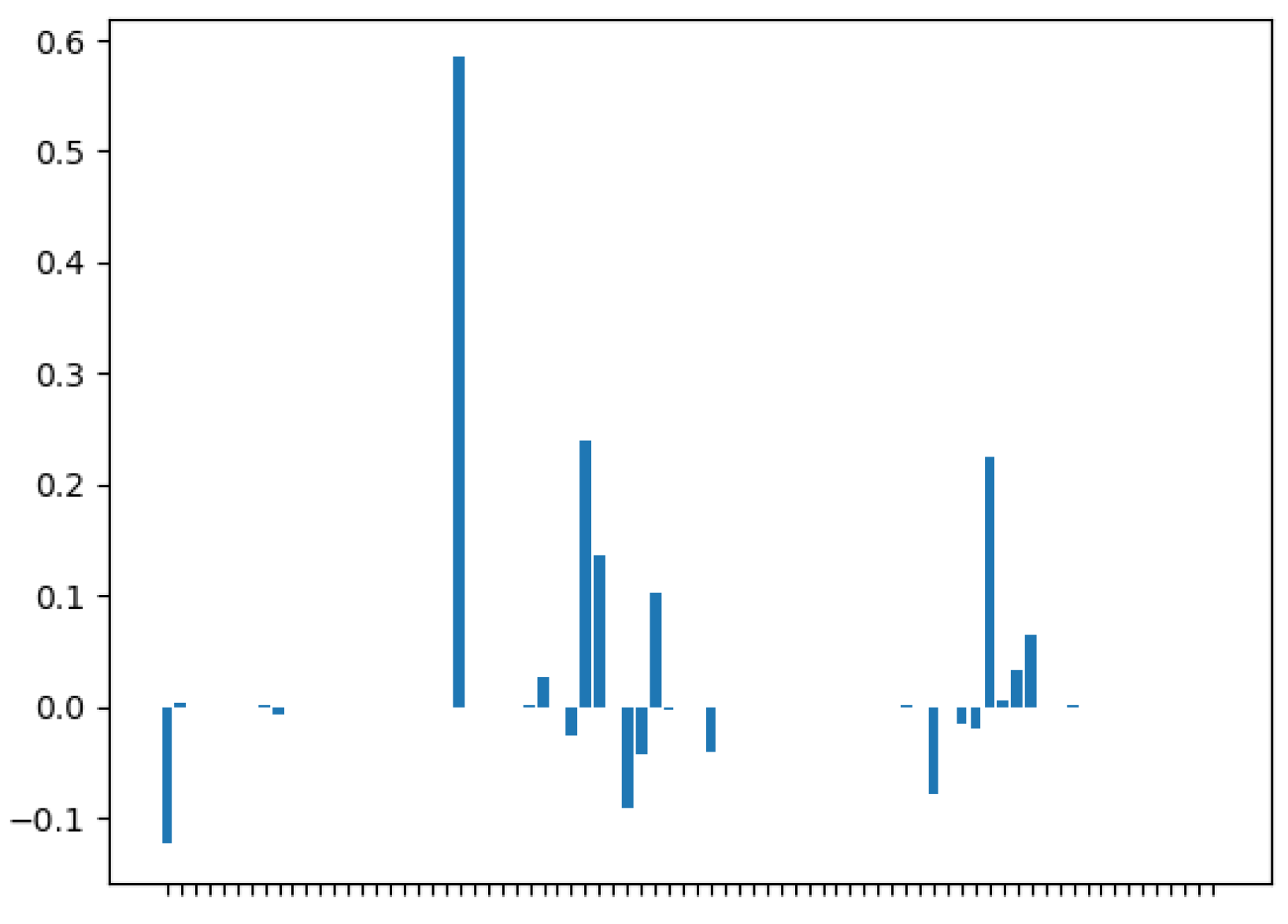
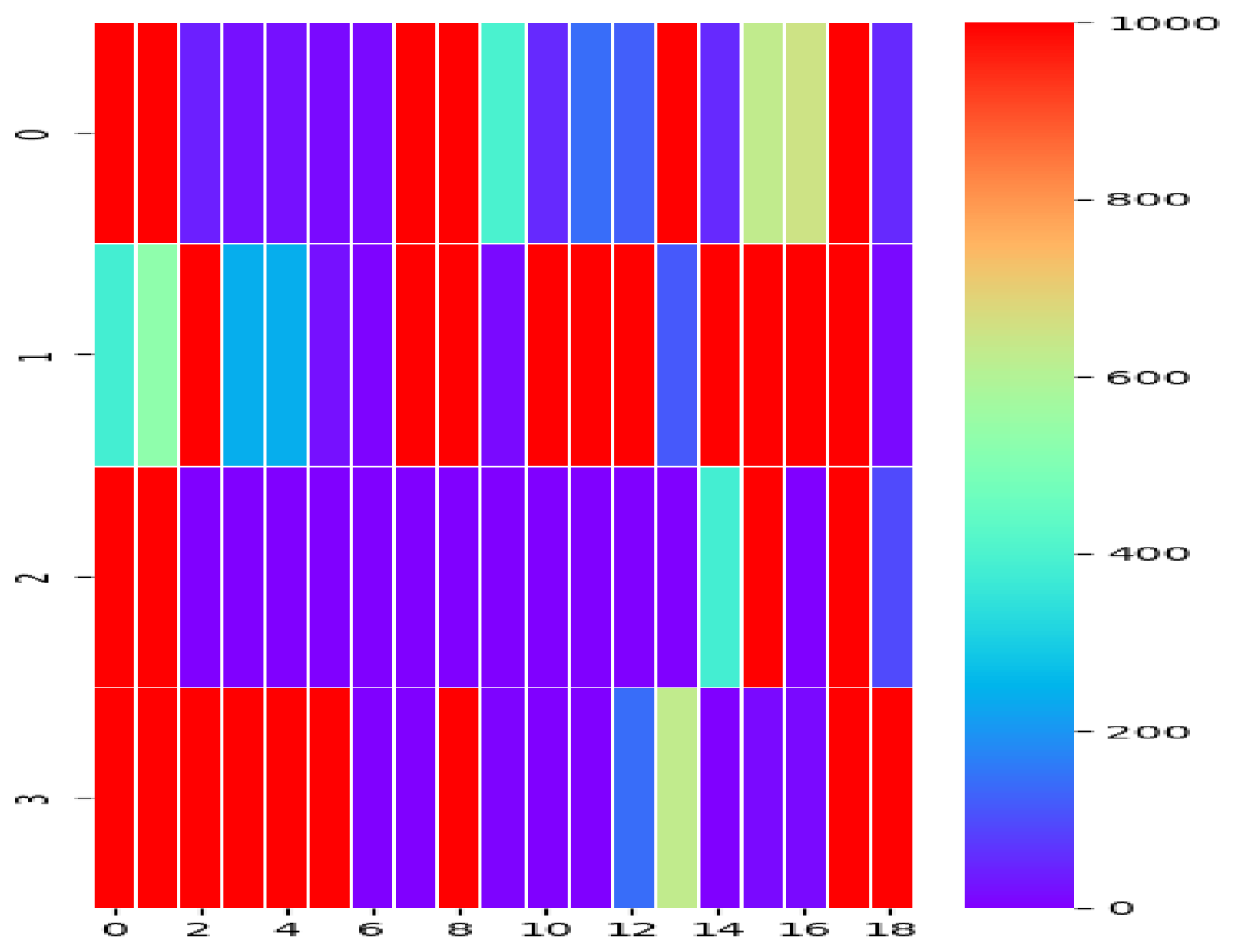
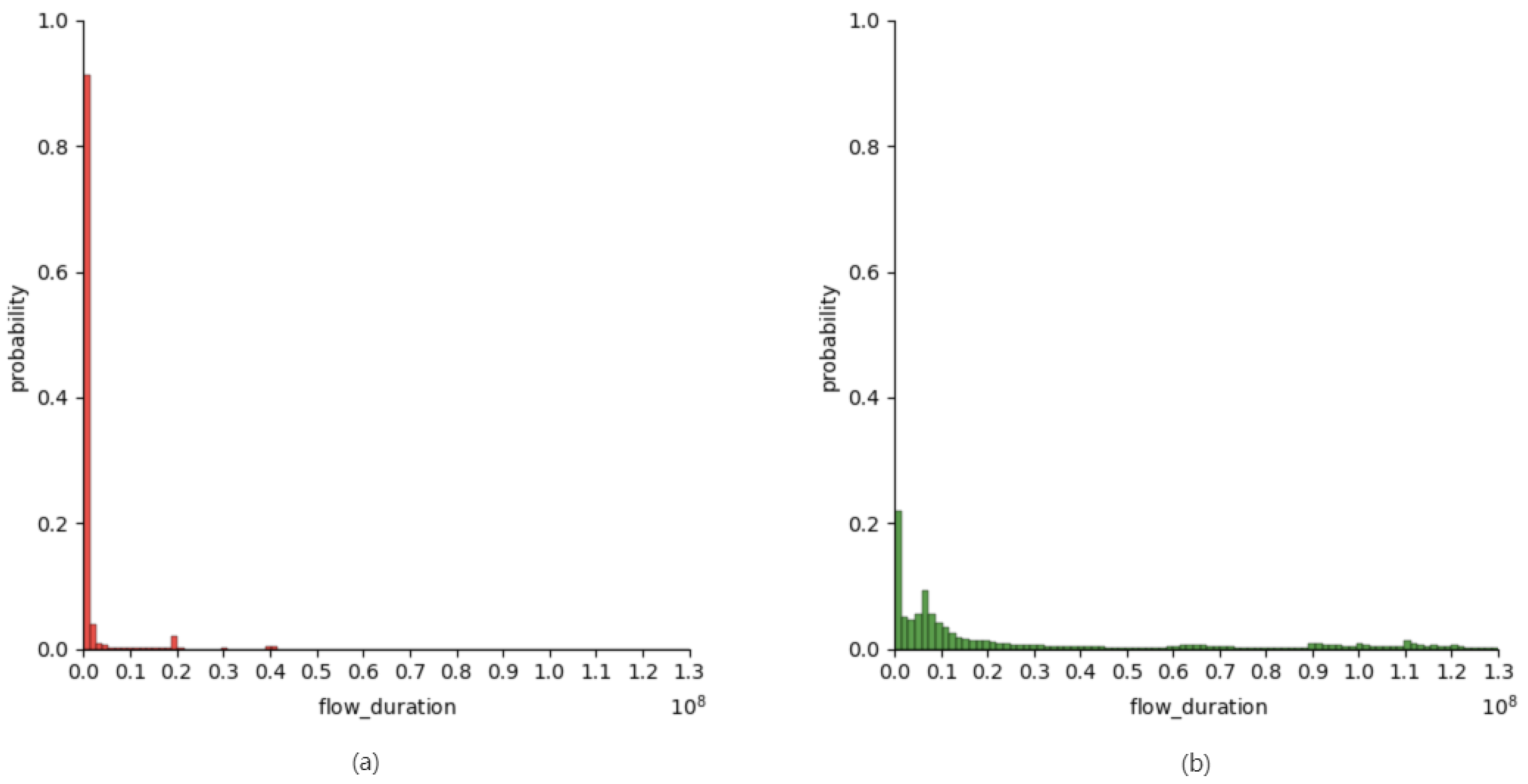
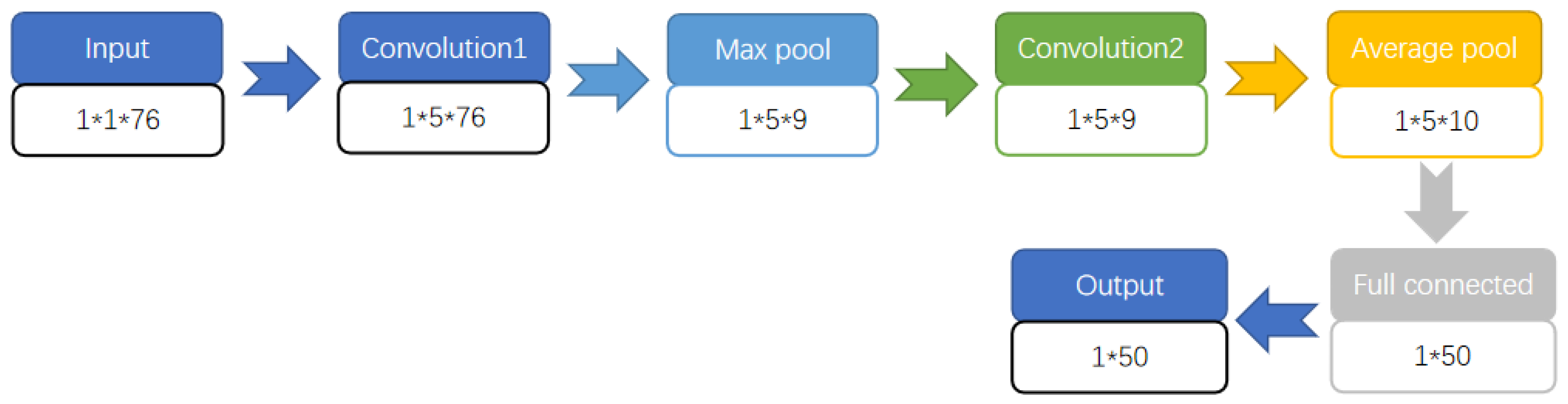
4.1. Detection of Malicious Encrypted Traffic
4.2. Adversarial Malicious Encrypted Traffic Generation
4.3. Detection of Adversarial Malicious Encrypted Traffic
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Taylor, V.F.; Spolaor, R.; Conti, M.; Martinovic, I. Robust smartphone app identification via encrypted network traffic analysis. IEEE Trans. Inf. Forensics Secur. 2017, 13, 63–78. [Google Scholar] [CrossRef]
- Kundu, P.P.; Truong-Huu, T.; Chen, L.; Zhou, L.; Teo, S.G. Detection and classification of botnet traffic using deep learning with model explanation. IEEE Trans. Dependable Secur. Comput. 2022, 19, 1–15. [Google Scholar] [CrossRef]
- Rezaei, S.; Liu, X. Deep learning for encrypted traffic classification: An overview. IEEE Commun. Mag. 2019, 57, 76–81. [Google Scholar] [CrossRef]
- ElSayed, M.S.; Le-Khac, N.A.; Albahar, M.A.; Jurcut, A. A novel hybrid model for intrusion detection systems in SDNs based on CNN and a new regularization technique. J. Netw. Comput. Appl. 2021, 191, 103160. [Google Scholar] [CrossRef]
- Saharkhizan, M.; Azmoodeh, A.; Dehghantanha, A.; Choo, K.K.R.; Parizi, R.M. An ensemble of deep recurrent neural networks for detecting IoT cyber attacks using network traffic. IEEE Internet Things J. 2020, 7, 8852–8859. [Google Scholar] [CrossRef]
- Liu, J.; Xiao, Q.; Jiang, Z.; Yao, Y.; Wang, Q. Effectiveness Evaluation of Evasion Attack on Encrypted Malicious Traffic Detection. In Proceedings of the 2022 IEEE Wireless Communications and Networking Conference (WCNC), Austin, TX, USA, 10–13 April 2022; IEEE: Piscataway, NJ, USA; pp. 1158–1163. [Google Scholar]
- Pierazzi, F.; Pendlebury, F.; Cortellazzi, J.; Cavallaro, L. Intriguing properties of adversarial ml attacks in the problem space. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (S&P), San Francisco, CA, USA, 17–21 May 2020; IEEE: Piscataway, NJ, USA; pp. 1332–1349. [Google Scholar]
- Sharon, Y.; Berend, D.; Liu, Y.; Shabtai, A.; Elovici, Y. Tantra: Timing-based adversarial network traffic reshaping attack. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3225–3237. [Google Scholar] [CrossRef]
- Usama, M.; Qayyum, A.; Qadir, J.; Al-Fuqaha, A. Black-box Adversarial Machine Learning Attack on Network Traffic Classification. In Proceedings of the 2019 15th International Wireless Communications and Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019. [Google Scholar]
- Yao, H.; Liu, C.; Zhang, P.; Wu, S.; Jiang, C.; Yu, S. Identification of encrypted traffic through attention mechanism based long short term memory. IEEE Trans. Big Data 2019, 8, 241–252. [Google Scholar] [CrossRef]
- Rezaei, S.; Kroencke, B.; Liu, X. Large-scale mobile app identification using deep learning. IEEE Access 2019, 8, 348–362. [Google Scholar] [CrossRef]
- Lotfollahi, M.; Jafari Siavoshani, M.; Shirali Hossein Zade, R.; Saberian, M. Deep packet: A novel approach for encrypted traffic classification using deep learning. Soft Comput. 2020, 24, 1999–2012. [Google Scholar] [CrossRef]
- Draper-Gil, G.; Lashkari, A.H.; Mamun, M.S.I.; Ghorbani, A.A. Characterization of encrypted and vpn traffic using time-related. In Proceedings of the 2nd International Conference on Information Systems Security and Privacy (ICISSP), Rome, Italy, 19–21 February 2016; pp. 407–414. [Google Scholar]
- Hodo, E.; Bellekens, X.; Iorkyase, E.; Hamilton, A.; Tachtatzis, C.; Atkinson, R. Machine learning approach for detection of nontor traffic. In Proceedings of the 12th International Conference on Availability, Reliability and Security, Reggio Calabria, Italy, 29 August–1 September 2017; pp. 1–6. [Google Scholar]
- Shen, M.; Liu, Y.; Zhu, L.; Du, X.; Hu, J. Fine-grained webpage fingerprinting using only packet length information of encrypted traffic. IEEE Trans. Inf. Forensics Secur. 2020, 16, 2046–2059. [Google Scholar] [CrossRef]
- Wu, Z.; Kang, J.; Jiang, Q. Semantic key generation based on natural language. Int. J. Intell. Syst. 2022, 37, 4041–4064. [Google Scholar] [CrossRef]
- Wu, Z.; Lv, Z.; Kang, J.; Ding, W.; Zhang, J. Fingerprint bio-key generation based on a deep neural network. Int. J. Intell. Syst. 2022, 37, 4329–4358. [Google Scholar] [CrossRef]
- Zeng, Y.; Gu, H.; Wei, W.; Guo, Y. Deep-full-range: A deep learning based network encrypted traffic classification and intrusion detection framework. IEEE Access 2019, 7, 45182–45190. [Google Scholar] [CrossRef]
- Yang, J.; Liang, G.; Li, B.; Wen, G.; Gao, T. A deep-learning-and reinforcement-learning-based system for encrypted network malicious traffic detection. Electron. Lett. 2021, 57, 363–365. [Google Scholar] [CrossRef]
- Chen, J.; Huang, J.; Lu, X. Convolutional neural network-based identification of malicious traffic for TLS encryption. In Proceedings of the 2022 7th International Conference on Intelligent Computing and Signal Processing (ICSP), Bucharest, Romania, 29–30 September 2022; IEEE: Piscataway, NJ, USA; pp. 1544–1549. [Google Scholar]
- Cuzzocrea, A.; Martinelli, F.; Mercaldo, F.; Vercelli, G. Tor traffic analysis and detection via machine learning techniques. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; IEEE: Piscataway, NJ, USA; pp. 4474–4480. [Google Scholar]
- Niu, W.; Zhuo, Z.; Zhang, X.; Du, X.; Yang, G.; Guizani, M. A heuristic statistical testing based approach for encrypted network traffic identification. IEEE Trans. Veh. Technol. 2019, 68, 3843–3853. [Google Scholar] [CrossRef]
- Wang, S.; Chen, Z.; Yan, Q.; Yang, B.; Peng, L.; Jia, Z. A mobile malware detection method using behavior features in network traffic. J. Netw. Comput. Appl. 2019, 133, 15–25. [Google Scholar] [CrossRef]
- Rabbani, M.; Wang, Y.L.; Khoshkangini, R.; Jelodar, H.; Zhao, R.; Hu, P. A hybrid machine learning approach for malicious behaviour detection and recognition in cloud computing. J. Netw. Comput. Appl. 2020, 151, 102507. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. A two-level flow-based anomalous activity detection system for IoT networks. Electronics 2020, 9, 530. [Google Scholar] [CrossRef]
- MontazeriShatoori, M.; Davidson, L.; Kaur, G.; Lashkari, A.H. Detection of doh tunnels using time-series classification of encrypted traffic. In Proceedings of the 2020 IEEE International Conference on Dependable, Autonomic and Secure Computing, International Conference on Pervasive Intelligence and Computing, International Conference on Cloud and Big Data Computing, International Conference on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Calgary, AB, Canada, 17–22 August 2020; IEEE: Piscataway, NJ, USA; pp. 63–70. [Google Scholar]
- Ma, C.; Du, X.; Cao, L. Improved KNN Algorithm for Fine-Grained Classification of Encrypted Network Flow. Electronics 2020, 9, 324. [Google Scholar] [CrossRef]
- Samy, A.; Yu, H.; Zhang, H. Fog-based attack detection framework for internet of things using deep learning. IEEE Access 2020, 8, 74571–74585. [Google Scholar] [CrossRef]
- Zheng, R.; Liu, J.; Niu, W.; Liu, L.; Li, K.; Liao, S. Preprocessing Method for Encrypted Traffic Based on Semisupervised Clustering. Secur. Commun. Netw. 2020, 2020, 8824659. [Google Scholar] [CrossRef]
- Zebin, T.; Rezvy, S.; Luo, Y. An explainable AI-based intrusion detection system for DNS over HTTPS (DoH) Attacks. IEEE Trans. Inf. Forensics Secur. 2022. [Google Scholar] [CrossRef]
- Hajimaghsoodi, M.; Jalili, R. RAD: A Statistical Mechanism Based on Behavioral Analysis for DDoS Attack Countermeasure. IEEE Trans. Inf. Forensics Secur. 2022, 17, 2732–2745. [Google Scholar] [CrossRef]
- Maarouf, R.; Sattar, D.; Matrawy, A. Evaluating resilience of encrypted traffic classification against adversarial evasion attacks. In Proceedings of the 2021 IEEE Symposium on Computers and Communications (ISCC), Athens, Greece, 5–8 September 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–6. [Google Scholar]
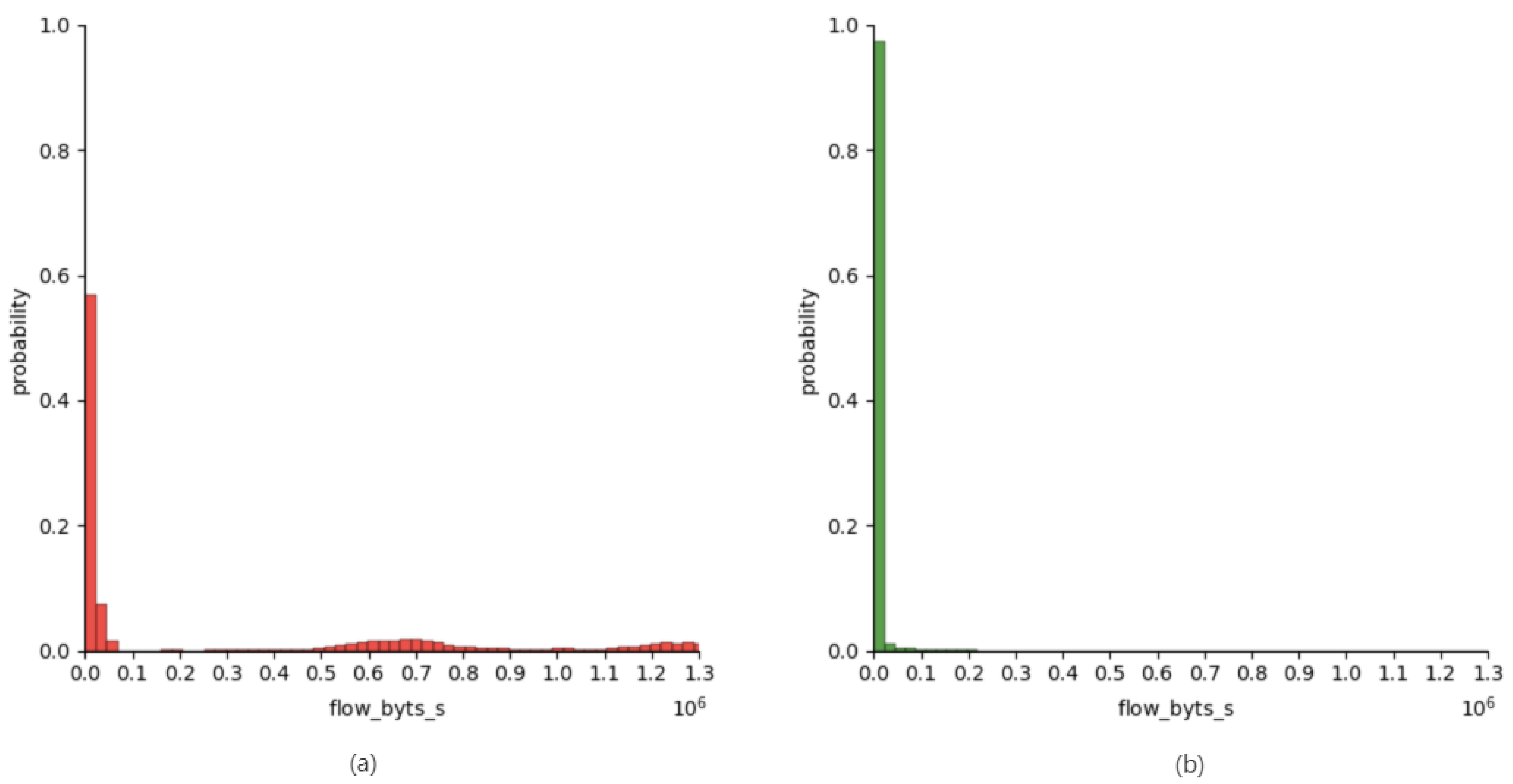
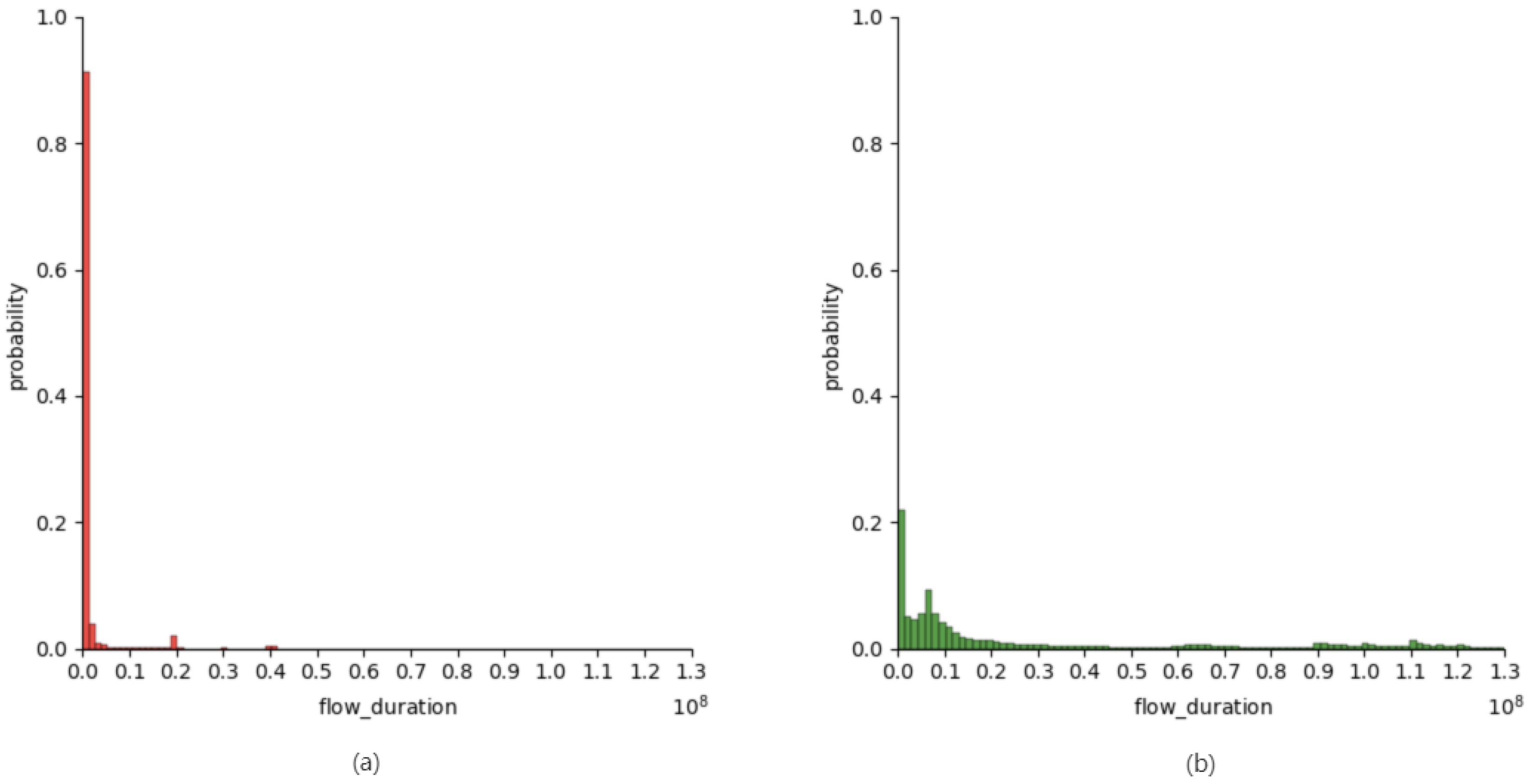
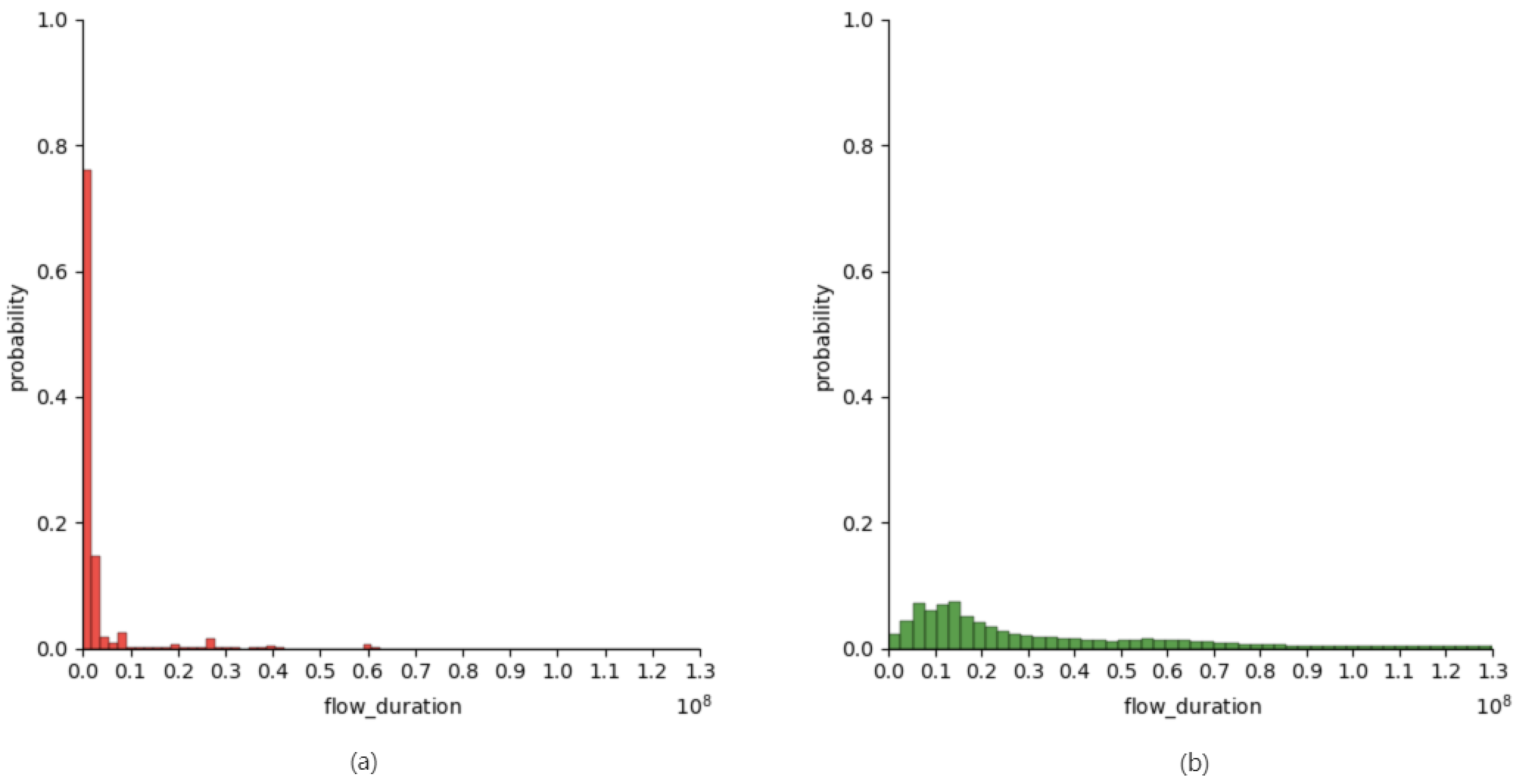
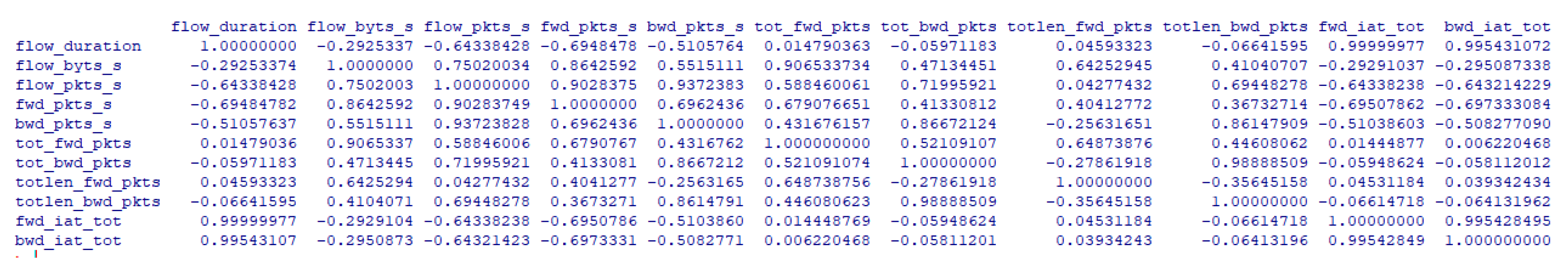
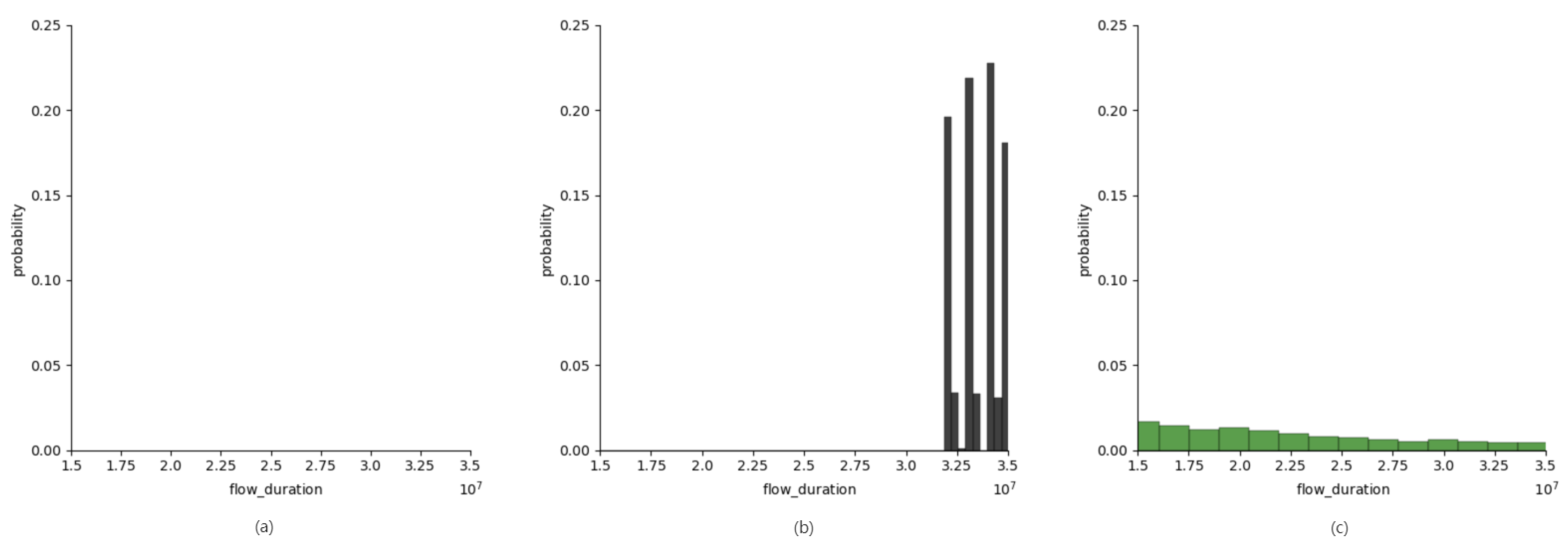
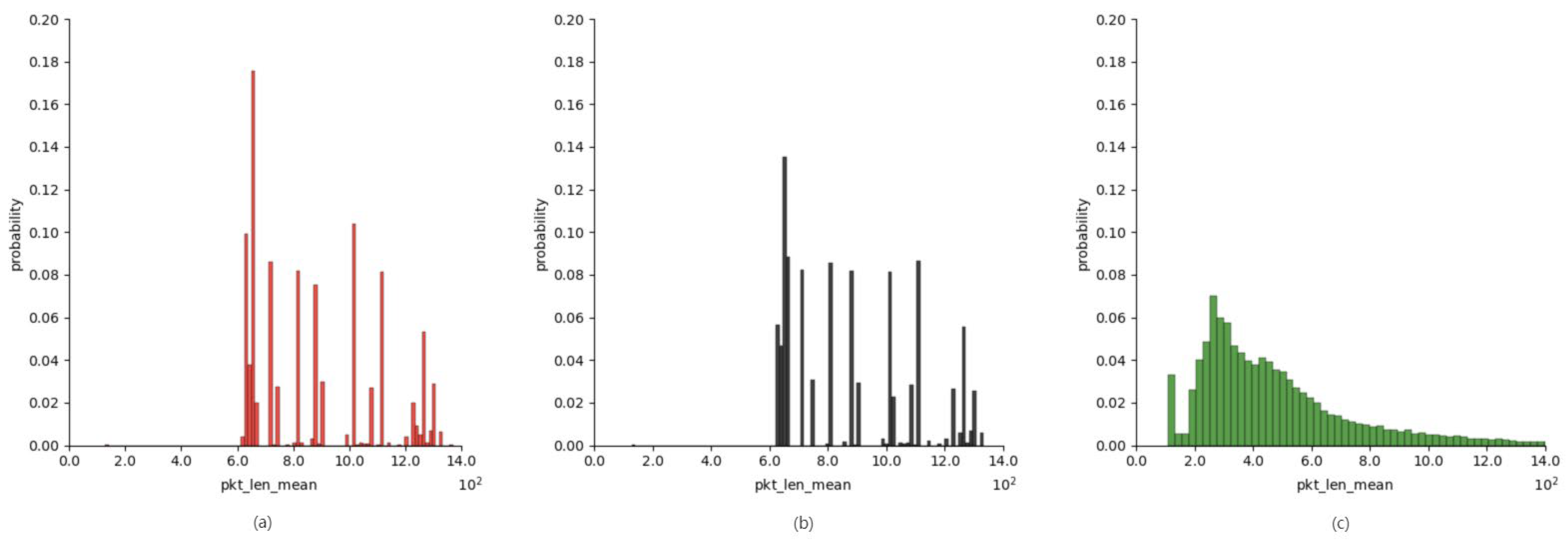
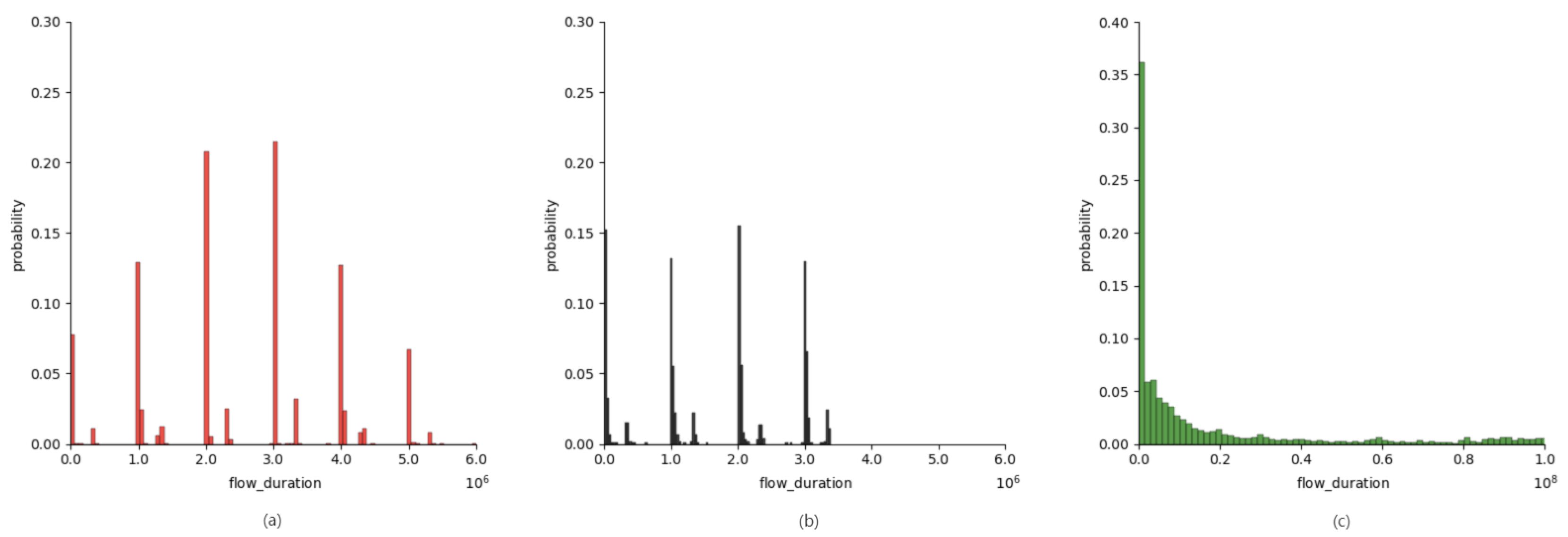
| flow_duration | Duration of the entire flow |
| flow_iat | The arrival time interval between two datagrams in a flow |
| fwd_iat | The arrival time interval between two datagrams in a forward flow |
| bwd_iat | The arrival time interval between two datagrams in a backward flow |
| totlen_fwd_pkts | Total number of packets in the forward flow |
| totlen_bwd_pkts | Total number of packets in the backward flow |
| ... | ... |
| Methods | Precision (%) | Accuracy (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| CICFLOWMETER | 99.60 | 99.55 | 99.50 | 99.55 |
| 99.50 | 99.60 | 99.70 | 99.60 | |
| 99.70 | 99.70 | 99.70 | 99.70 | |
| DOHLYZER | 98.22 | 98.70 | 99.20 | 98.71 |
| 97.26 | 98.25 | 99.30 | 98.27 | |
| 99.70 | 99.60 | 99.50 | 99.60 | |
| ADRSA | 99.90 | 99.95 | 100 | 99.95 |
| 99.90 | 99.85 | 99.80 | 99.85 | |
| 99.70 | 99.75 | 99.80 | 99.75 |
| Methods | Precision (%) | Accuracy (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| CICFLOWMETER | 98.61 | 99.10 | 99.60 | 99.10 |
| 99.01 | 99.35 | 99.70 | 99.35 | |
| 99.10 | 99.30 | 99.50 | 99.30 | |
| DOHLYZER | 99.01 | 99.30 | 99.60 | 99.30 |
| 99.10 | 99.35 | 99.60 | 99.35 | |
| 99.00 | 99.15 | 99.30 | 99.15 | |
| ADRSA | 99.80 | 99.90 | 100 | 99.90 |
| 99.30 | 99.55 | 99.80 | 99.55 | |
| 99.40 | 99.55 | 99.70 | 99.55 |
| Methods | Precision (%) | Accuracy (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| CICFLOWMETER | 99.20 | 99.45 | 99.70 | 99.45 |
| 99.60 | 99.65 | 99.70 | 99.65 | |
| 99.43 | 99.63 | 99.83 | 99.63 | |
| DOHLYZER | 98.71 | 99.11 | 99.50 | 99.10 |
| 98.11 | 98.48 | 98.85 | 98.48 | |
| 98.93 | 99.27 | 99.60 | 99.26 | |
| ADRSA | 99.80 | 99.80 | 99.80 | 99.80 |
| 99.75 | 99.83 | 99.90 | 99.83 | |
| 99.95 | 99.90 | 99.85 | 99.90 |
| Methods | Precision (%) | Accuracy (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| CICFLOWMETER | 98.90 | 99.05 | 99.20 | 99.05 |
| 99.00 | 99.05 | 99.10 | 99.05 | |
| 99.27 | 99.24 | 99.20 | 99.24 | |
| DOHLYZER | 99.00 | 99.10 | 99.20 | 99.10 |
| 99.35 | 99.10 | 98.85 | 99.10 | |
| 99.25 | 99.28 | 99.30 | 99.28 | |
| ADRSA | 99.20 | 99.30 | 99.40 | 99.30 |
| 99.50 | 99.70 | 99.90 | 99.70 | |
| 99.50 | 99.65 | 99.80 | 99.65 |
| Methods | Precision (%) | Accuracy (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| CICFLOWMETER | 99.80 | 99.90 | 100 | 99.90 |
| DOHLYZER | 96.68 | 96.45 | 96.20 | 96.44 |
| Methods | Precision (%) | Accuracy (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| CICFLOWMETER | 99.60 | 99.80 | 100 | 99.80 |
| DOHLYZER | 96.37 | 97.34 | 98.30 | 97.33 |
| Methods | Precision (%) | Accuracy (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| CICFLOWMETER | 0 | 50.00 | 0 | 0 |
| DOHLYZER | 0 | 50.00 | 0 | 0 |
| Methods | Precision (%) | Accuracy (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| CICFLOWMETER | 0 | 50.00 | 0 | 0 |
| DOHLYZER | 0 | 50.00 | 0 | 0 |
| Methods | Precision (%) | Accuracy (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| CICFLOWMETER | 0 | 50.00 | 0 | 0 |
| DOHLYZER | 0 | 50.00 | 0 | 0 |
| ADRSA | 99.90 | 99.90 | 99.90 | 99.90 |
| Methods | Precision (%) | Accuracy (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|---|
| CICFLOWMETER | 0 | 50.00 | 0 | 0 |
| DOHLYZER | 0 | 50.00 | 0 | 0 |
| ADRSA | 99.90 | 99.95 | 100 | 99.95 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, M.; Wu, Z.; Chen, K.; Wang, W. Adversarial Malicious Encrypted Traffic Detection Based on Refined Session Analysis. Symmetry 2022, 14, 2329. https://doi.org/10.3390/sym14112329
Li M, Wu Z, Chen K, Wang W. Adversarial Malicious Encrypted Traffic Detection Based on Refined Session Analysis. Symmetry. 2022; 14(11):2329. https://doi.org/10.3390/sym14112329
Chicago/Turabian StyleLi, Minghui, Zhendong Wu, Keming Chen, and Wenhai Wang. 2022. "Adversarial Malicious Encrypted Traffic Detection Based on Refined Session Analysis" Symmetry 14, no. 11: 2329. https://doi.org/10.3390/sym14112329
APA StyleLi, M., Wu, Z., Chen, K., & Wang, W. (2022). Adversarial Malicious Encrypted Traffic Detection Based on Refined Session Analysis. Symmetry, 14(11), 2329. https://doi.org/10.3390/sym14112329





