1. Introduction
As a kind of ubiquitously aware, centralized data center (DC) symmetric network [
1,
2], the wireless network is a fully self-organizing automatic network. The main characteristics of a wireless network are identified as self-management, self-optimization, and automation configuration of the network parameters. Therefore, the research of wireless networks has attracted extensive attention in recent years. As a result, nowadays, wireless networks have a great application foreground in the fields of intelligent society, industry, agriculture, etc. These benefit from the excellent performances of wireless networks, for example, multi-dimensional information collection and transmission [
3], end-to-end (E2E) and device-to-device (D2D) transmission with low latency [
4].
As of now, the wireless industry may be preparing for a transition to 5G wireless/virtual networks, and it has been widely used in various aspects. Based on the characteristics of high-density deployment, multi-link, and the high mobility of microbase stations (mBSs) in 5G wireless networks, there are three main application scenarios [
5]: enhancing mobile broadband (eMBB), ultra-reliable and low latency communication (uRLLC), and massive machine type of communication (mMTC). The comparison of key performance indicators (KPIs) for the three application scenarios is shown in
Table 1 [
6]. In addition, wireless networks can be used in vehicle-to-everything (V2X), Internet of things (IoT), and other applications [
5]. Therefore, the wireless network can not only ensure the technical requirements of different intelligent networks from the application layer, but also realize the logical application isolation of different application scenarios from the network layer.
The main purpose of studying the wireless network is to assist in various aspects of industrial automation, convenience of life, artificial intelligence (AI), the spatial information network of multi-functional satellite platform, the dataset of remote sensing images, and other aspects of vertical services [
7]. The vertical services have been involved in all walks of daily life, and further promote the research needs of the wireless network [
1,
3]. Moreover, the above applications have a high requirement for performance of the wireless network [
7]. The constructed network often needs to meet some KPI requirements, such as high throughput, low E2E data transmission latency, low packet drop ration, and energy efficiency of the wireless network. On the other hand, the allocation optimization techniques of limited network resources (i.e., bandwidth, spectrum, energy, communication and computing resources) are also limited to these applications [
2], which further increases the requirements of the network topology.
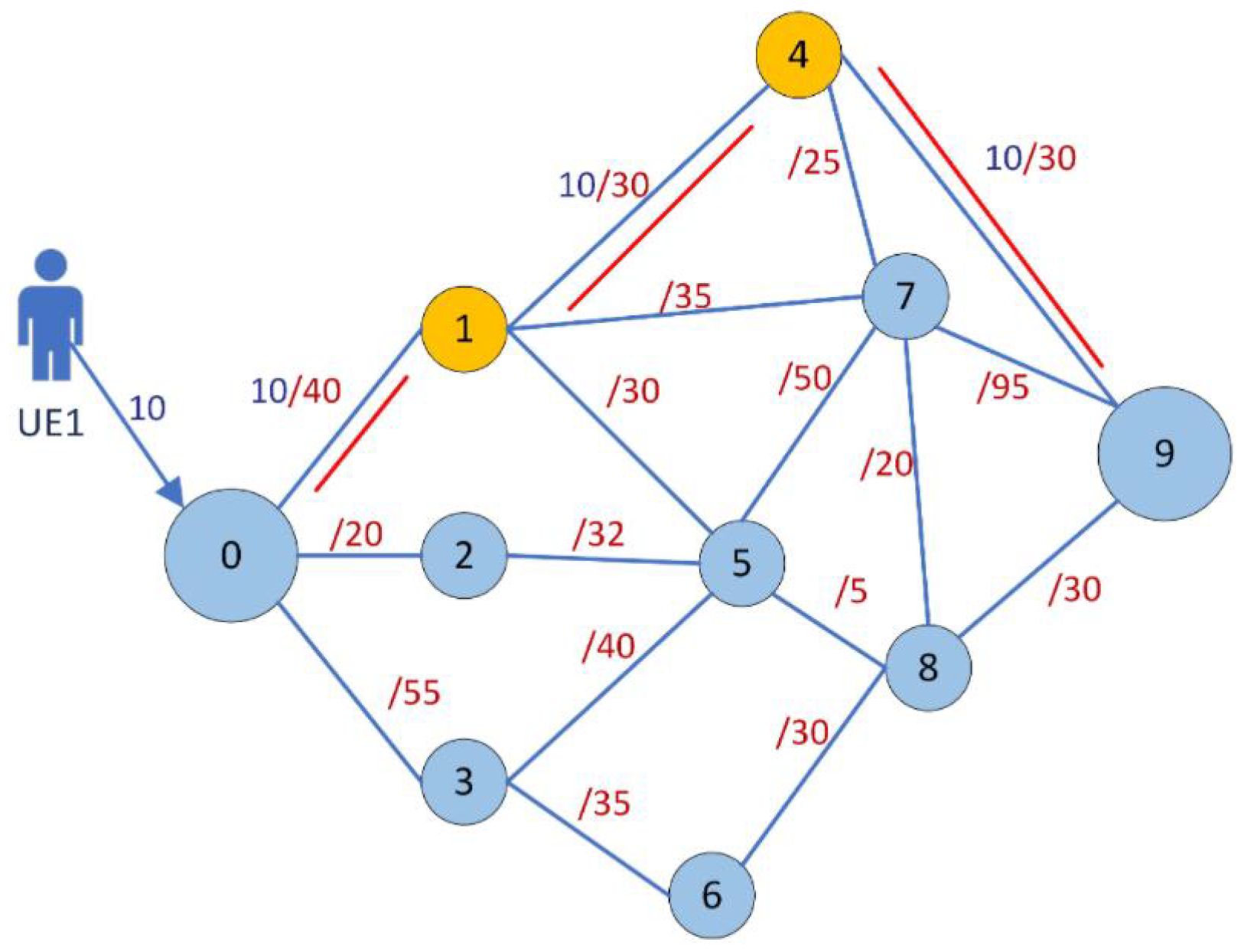
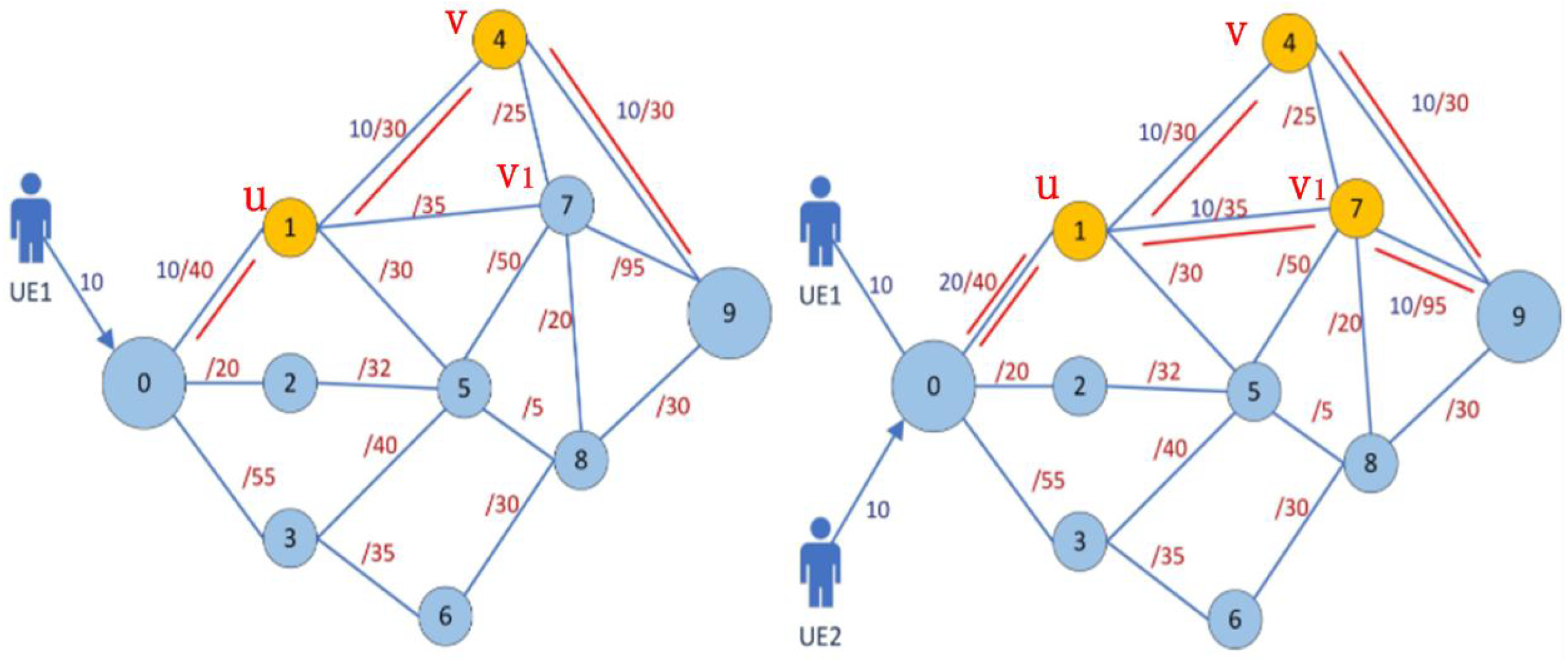
Traffic engineering (TE)-based wireless networks are one of the hot research issues of recent years. In a TE-based wireless network, each microbase station (mBS) needs to transmit the collected data packets from the source mBS to the terminal mBS, and this results in traffic of different sizes occurring simultaneously on network links. However, the network is limited to the maximum allowable traffic rate between two mBSs (i.e., peak rate [
8]), and traffic congestion will occur if the traffic rate is greater than the peak rate on a traffic link. The traffic congestion can result in the increase of the network latency or data losses when the traffic arriving at the terminal mBS [
9,
10,
11]. Therefore, it is necessary to migrate the traffic of the congestion links to other links nearby, so as to complete the reconfiguration of the data transmission paths. Because the traffic in the network is constantly changing, the network has low resource utilization and high operating expenses (OPEX) even though the traditional TE architecture can commonly meet the demand of peak rate for network traffic [
12,
13].
At present, a large number of studies have shown that the traffic routing optimization problem is an NP-hard problem. This is mainly due to the problem of the multiple constraints of non-convex smoothness [
14,
15,
16]. However, there have been many approximate solutions and interesting results [
17,
18,
19,
20], in particular for link traffic optimization of slice layers in 5G network architecture. Therefore, our main research objective is to solve the traffic optimization problem of the wireless network. Meanwhile, we can also solve the problem of resource allocation optimization by solving the traffic routing optimization problem.
The main strategy in this paper is to establish a single-objective optimization mathematical model. Although the model is a single objective, several subobjectives are combined by the weighted coefficient. In order to get the best approximation for this optimization objective, we propose an adaptive data traffic control scheme (a-ADTC) to solve the traffic transmission optimization problem in this paper. The proposed a-ADTC algorithm is a heuristic greedy strategy. All in all, compared with some mature traffic routing schemes, the proposed scheme achieves a certain optimization effect.
Let us point out that our work has the following takeaways.
(1) The joint optimization problem of TE, network energy resources, and KPIs is formulated as a mixed mathematical programming model.
(2) Load balancing for wireless network is guaranteed through the effective traffic migration. The traffic migration can effectively reduce the link congestion and improve the utilization rate of mBSs and links in wireless networks.
(3) The corresponding optimization scheme a-ADTC is a solution framework that quickly solves the mathematical model, and the algorithm has good expansibility. The proposed a-ADTC algorithm can provide a theoretical basis for the development of the 6G wireless network and the architecture of urban intelligent transportation.
The rest of the paper is organized as follows. In
Section 2, we introduce the related work and current state of the art. In
Section 3, we study the traffic routing problem by abstracting it into a topology, and we transform the traffic problem into a mathematical optimization programming. Then an approximate optimization algorithm is introduced.
Section 4 is the simulation validation and results discussion. Finally,
Section 5 concludes the paper.
2. Related Work
In recent years, a lot of research achievements have been obtained for the TE-based wireless network, and many of them are solved by heuristic algorithms [
21,
22,
23,
24,
25]. These algorithms have the following advantages: low complexity, easy deployment, and strong application value. As one of the most classical algorithms in a TE-based wireless network, the A* Search algorithm [
21] efficiently completes the task of traffic allocation and optimization in network links. In [
21], the authors use a two-node storage set to separate the active nodes and sleep nodes, which are the open set and closed set. Then the authors prioritize the importance of nodes and use heuristic algorithms to explore the routing scheme from the source node to the destination node.
According to the instance of TE and traffic matrix measurement, Wang et al. [
22] propose a joint optimization model named MLRF for online traffic measurement and TE based on the software defined network (SDN). The core strategy is to first establish a mathematical model with a traffic problem and to transform the problem into a mixed-integer linear programming model. The objective is to maximize the traffic throughput of the wireless network, and the authors use a feasible traffic matrix rule to describe the traffic status of the network. Finally, to solve the model, the authors present an effective heuristic algorithm. The simulation results and application analysis show that the algorithm is a very advanced and practical algorithm. In 5G TE adjustment and migration metro-aggregation networks, Yu et al. [
23] propose a dynamic traffic prediction scheme for wavelength division multiplexing (WDM). Based on the metro traffic prediction, this method dynamically migrates the link to meet the dynamic data transmission, which provides an application basis for optimal allocation of TE.
Nowadays, the increasing demands for quality of service (QoS) of smart city construction are notable. In order to provide more reliable and fast communication services, Wang et al. [
24] consider the dense and highly dynamic characteristics of cellular network traffic and use an integrated multiple-access edge computing framework to enhance the accuracy of data traffic prediction. Thus, we notice the importance of traffic prediction in the TE-based wireless network, and we find that is worth considering the use of matrix storage technology as an effective prediction scheme.
Furthermore, in the industrial Internet of things (IIoT), a large amount of data traffic will be generated with the rapid increase of intelligent devices. Therefore, the way to distribute this traffic quickly is via the premise of efficient management in IIoT networks. Lin et al. [
25] propose an encrypted traffic algorithm based on the flow spatiotemporal features, which improves the adaptive management ability of IIoT effectively. In [
25], traffic segmentation, sampling, and vectorization are carried out for the original data stream. In the shunting stage, the traffic is classified efficiently by extracting the time characteristics of the data and introducing the time characteristics of stack bidirectional long short-term memory learning. There are also many algorithms for traffic control of network resource allocation through TE, and these algorithms have been successfully applied to practical applications [
26,
27,
28,
29].
Wireless networks support a variety of vertical business services. The network operators allocate the network resources to users when the service users have a resource demand through data traffic. Golkarifard et al. [
30] consider the time dynamic features of such requests and then propose a joint optimization method for traffic licensing, resource activation, virtualized network function (VNF) setting, resource allocation, and traffic routing for request of data traffic. Agarwal et al. [
31] developed a mathematical model based on traffic queues to match the vertical demands and to optimize the allocation of the network resources in the network.
Eramo et al. [
32] proposed an integration algorithm to migrate VNF routes by taking into account the losses of data traffic information, which was caused by the VNF link migration. The research goal of this paper is to minimize the total OPEX caused by energy consumption and reduce the losses of revenue caused by QoS degradation during migration. In order to efficiently coordinate the traffic congestion problem during VNF migration, Pham et al. [
33] absorbed a traffic-aware and energy-efficient placement for service chaining TE. In this migration scheme, the authors perform a joint match on the collected data, and thus use a method similar to data aggregation to reduce the redundant data in the links of the network. A traffic prediction scheme [
34] is proposed by analyzing the traffic characteristics in the operator network, and then two VNF layout algorithms are designed to accomplish the dynamic VNF instance scaling in operator DCs. Finally, the effectiveness of the dynamic VNF instance scaling system in the resources allocation algorithm is verified through the actual data simulation. There are also some authors who focus on the networked state estimation problem over lossy channels [
35,
36], and the results are very interesting and provide some references for the problem of traffic estimation in lossy channels.
Much progress has been made in recent work on the TE basis and resource allocation in wireless networks. However, such progress often aims at a single optimization objective and has a good optimization effect, and it is difficult to meet the demands of vertical services. Otherwise, the authors often optimize subobjectives separately. Although multiple KPIs can be optimized at the same time, the algorithm complexity is often too high. To this end, we try to join these KPIs as one objective to optimize. The detailed algorithm is described in the following section.
4. Validation and Analysis of the Proposed Algorithm
In this section, we perform a lot of repeated simulations to verify the effectiveness of the proposed a-ADTC algorithm by comparison with MLRF algorithm [
22] and A* Search algorithm [
21]. The concerned KPIs of the comparison mainly include the lifetime, throughput, and latency of the network. Extraordinarily, we also perform the Pareto probability distribution of the lifetime, latency, and throughput for the a-ADTC algorithm under different mBSs, and reflect the performance of the proposed algorithm from the perspective of probability statistics. The simulation environment is a Win7 64-bit system with CPU being Intel Core i5-7500 3.4 GHz, and memory being 4.00 GB. The simulation software used in this research are Visual C++ 6.5 and MATLAB 2017B. In our simulation, we generate 50–400 mBSs in the wireless network and the communication radius for each mBS is 100 m, the link inherent latency is
s. The data packet size generated by each mBS is 1024 KB. The channel bandwidth is 20 Mb. The duration of mBSs monitoring data is 1 ms. The initial energy for each mBS is 600 J. The energy consumption for 1 KB packets is 0.001 J [
39], and
are 0.2, 0.4, and 0.2, respectively.
4.1. Lifetime of the Network
The lifetime of the network represents the run time of the wireless networks, and we use “round” to represent the network run one time and a higher value indicates a better network performance in our simulation.
Figure 4 shows the lifetime of MLRF, A* Search and a-ADTC. From
Figure 4, we can observe that the proposed algorithm a-ADTC prolongs the lifetime of the network with the increasing number of mBSs.
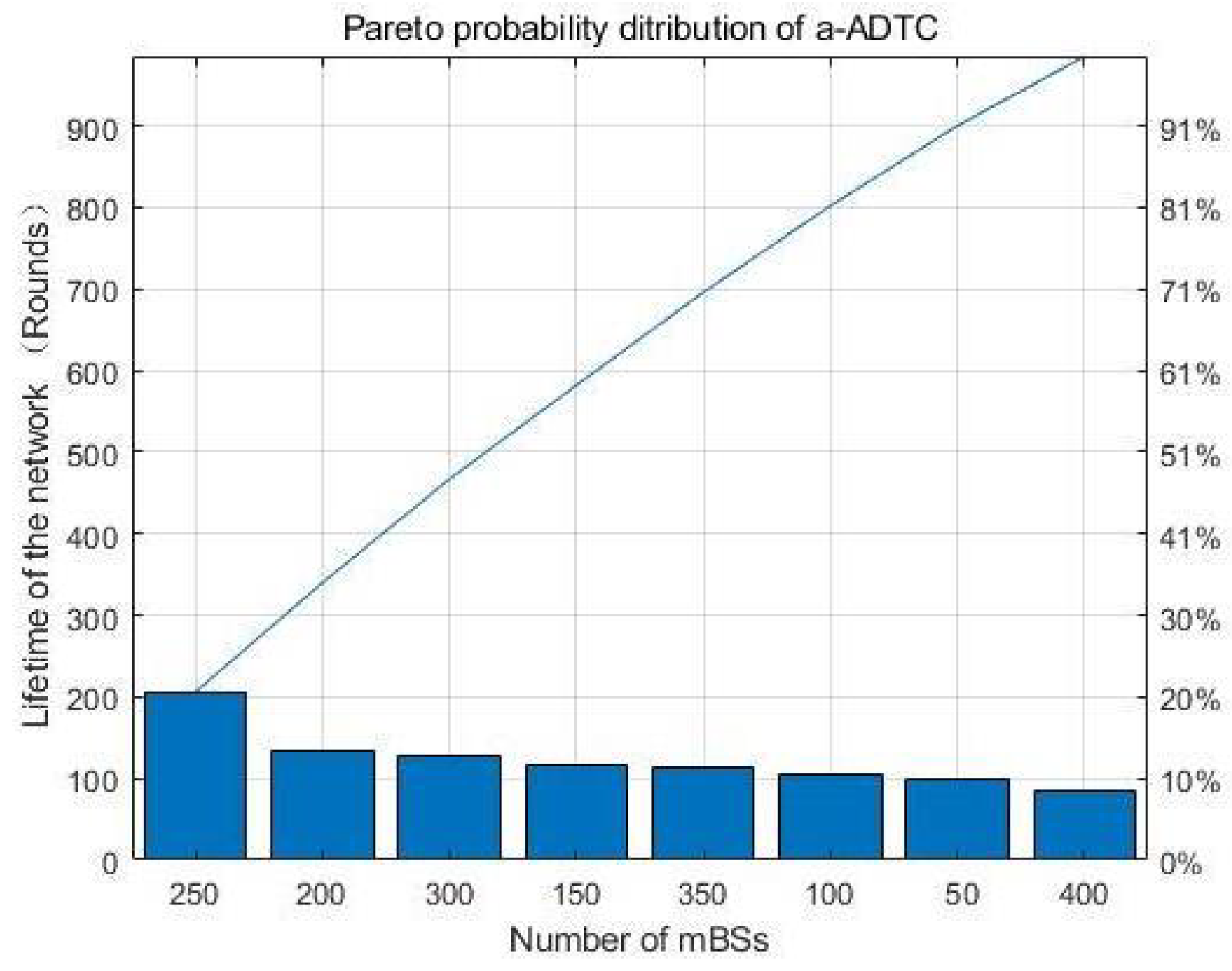
The results demonstrate that a-ADTC algorithm can achieve better performance in KPIs of energy consumption under the proposed algorithm. Most importantly, we can see from
Figure 5, the Pareto probability distribution of the lifetime for the a-ADTC algorithm under 250 mBSs are much better than other numbers. When the lifetime of the wireless network reaches 210 rounds, the optimization efficiency of our proposed algorithm is more than 60%. This means that the optimal number of mBSs is 250 in our simulation. If the number of mBSs in the region is too small, the link of data transmission is too long, which is not conducive to the saving of node energy. Moreover, if there are too many mBSs in the network, it is easy to cause link congestion due to the large amount of data. The congestion data transmission always needs more energy of the mBSs. This shows that the optimization of node deployment in the network is very important for saving the mBS resources and improving the efficiency of data transmission.
4.2. Latency of the Network
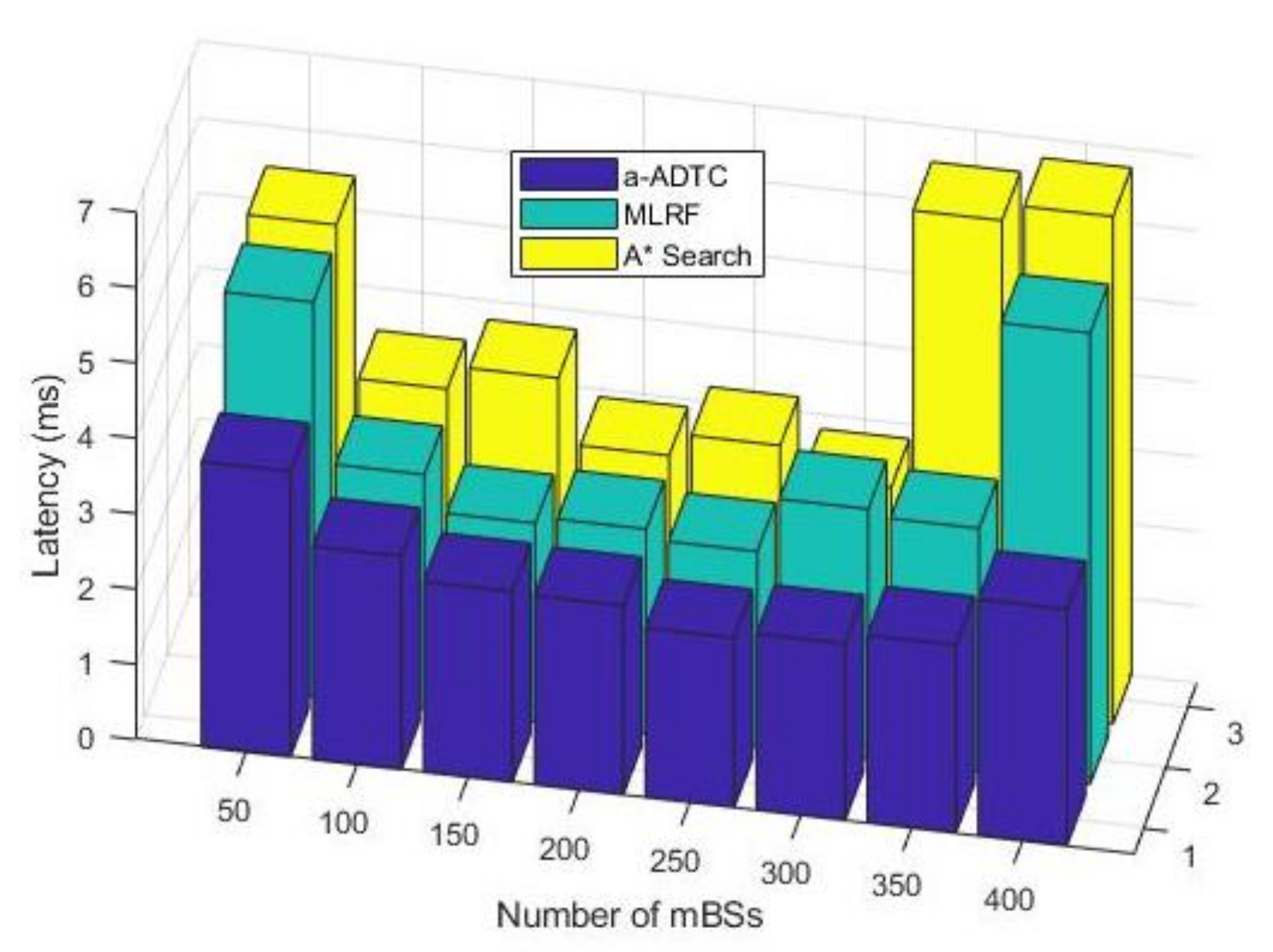
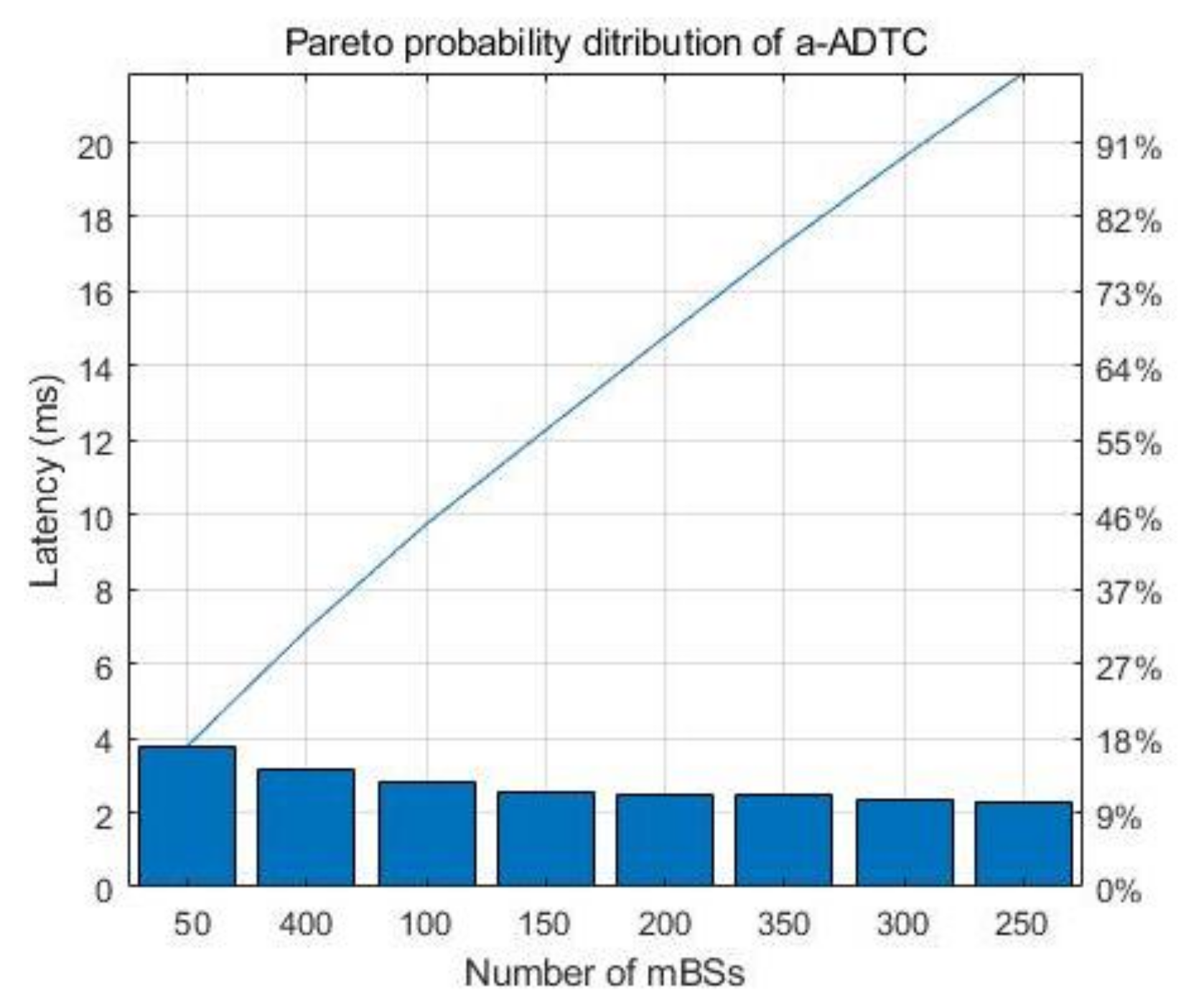
To evaluate the improvement performance of the timeliness for network data transmission, we conduct latency simulations under different numbers of mBSs. In
Figure 6, we can see that the proposed a-ADTC algorithm has the lower latency compared with the MLRF and A* Search algorithms. Moreover, the latency of the a-ADTC algorithm is always stable and has a narrower fluctuation margin with the increasing number of mBSs. This is because the a-ADTC algorithm can find the optimal data transmission path dynamically and formulate adaptive data traffic rules with lower latency.
As shown in
Figure 7, we can also observe that the Pareto probability distributions of the network lifetime for the a-ADTC under 250 and 300 mBSs are much better than other numbers of mBSs. The main reasons are the same as
Section 4.1.
4.3. Throughput of the Network
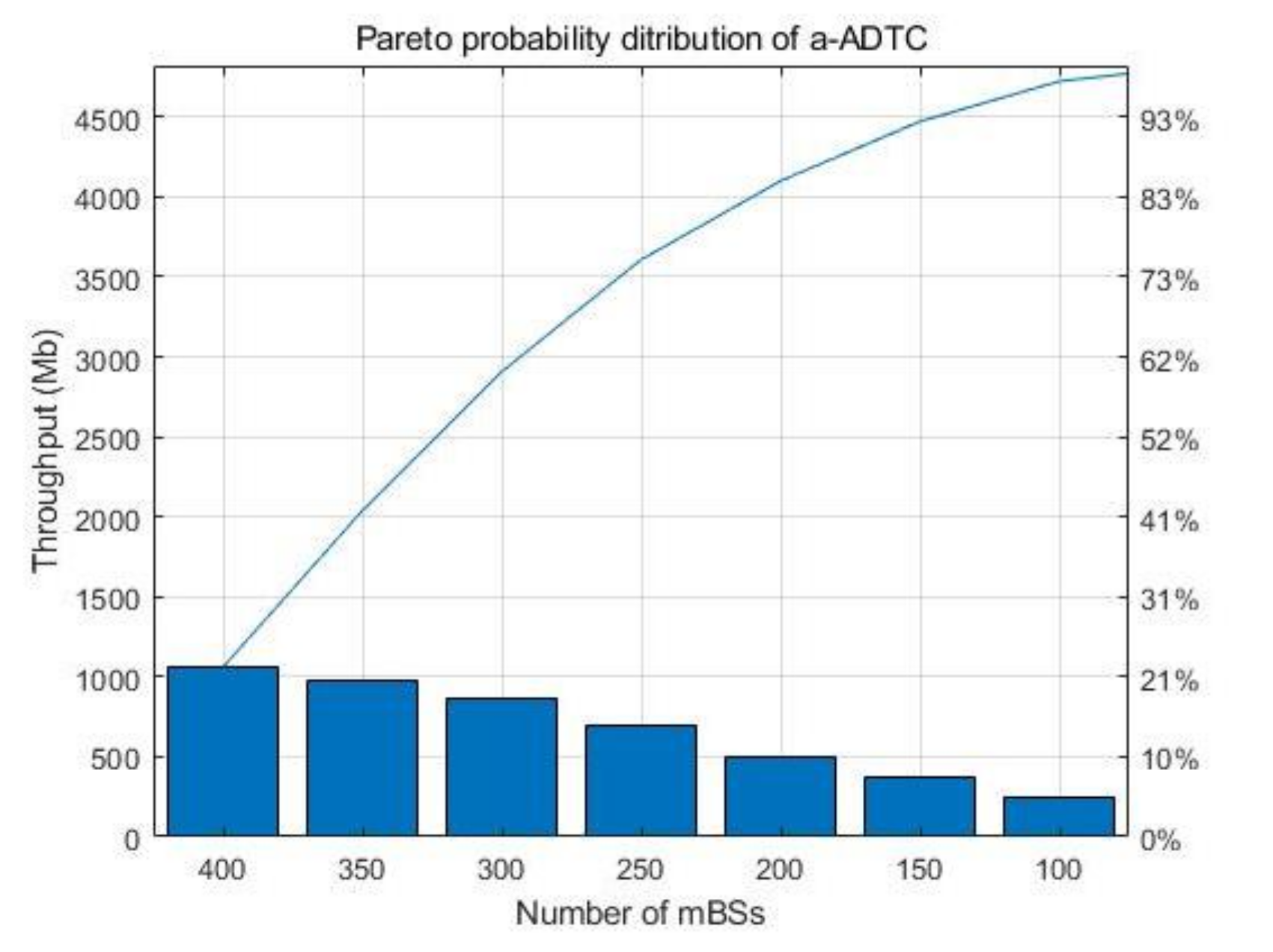
The throughput of the network reflects the strength of the network to carry data.
Figure 8 and
Figure 9 show the network throughput with different numbers of mBSs in the wireless network. We can see from
Figure 8 that the network throughput increases gradually with the increasing number of mBSs for three algorithms. However, the proposed a-ADTC algorithm has the higher throughput than the other two algorithms in the same number of mBSs. This is because the a-ADTC algorithm migrates the traffic of the congestion link and avoids the data losses or damages in the congestion link. Simultaneously, the more mBSs there are, the greater the throughput optimization efficiency.
In summary, the above simulations indicate that the proposed a-ADTC algorithm has a better performance in KPIs. Therefore, the corresponding approximate optimization scheme and quick solution a-ADTC algorithm solves the constructed mathematical model more effectively. The simpler the proposed algorithm is, the easier it is to deploy and minimize the network cost. In addition, the proposed a-ADTC algorithm meets these properties.
4.4. Load-Balancing Experiment
Load balancing is an important aspect to measure to determine the performance of data transmission in the wireless network. Different traffic will cause the unevenness of energy consumption of the mBSs in the network. In our simulation, we use the residual energy of each mBS to show the load balancing of the wireless network.
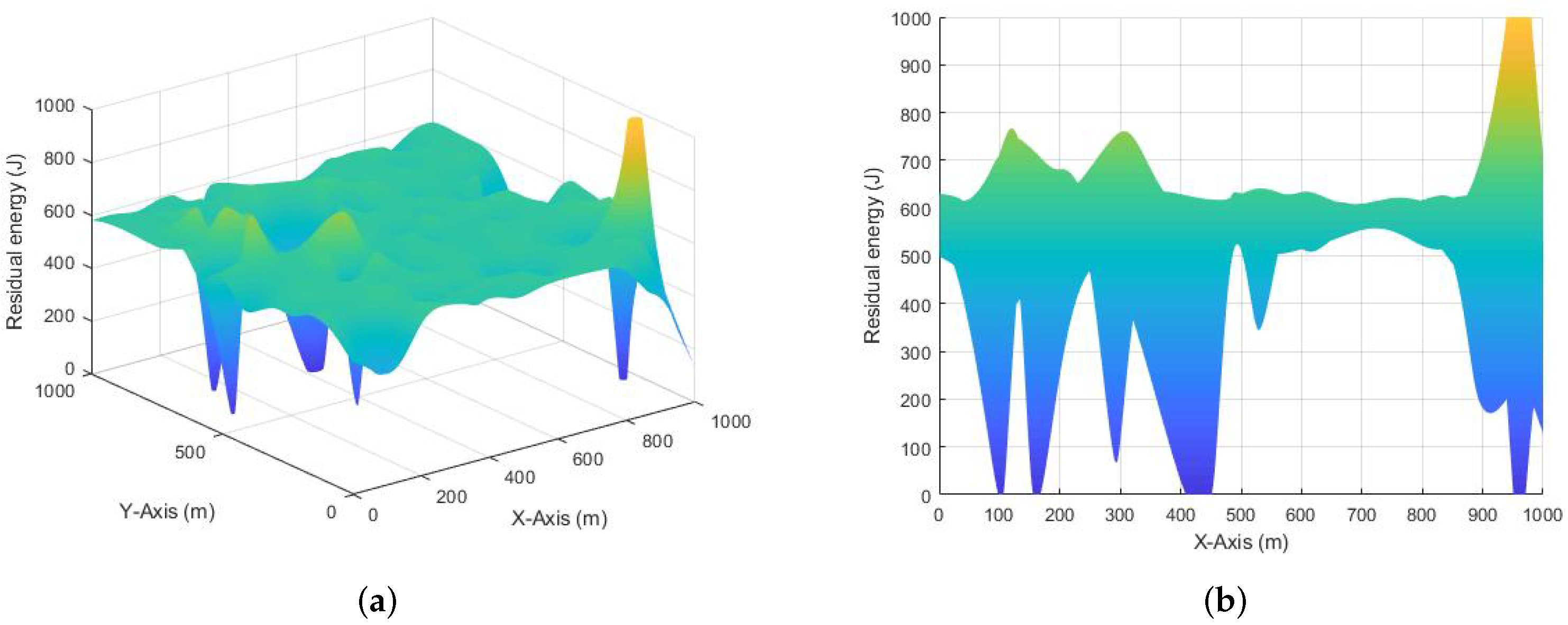
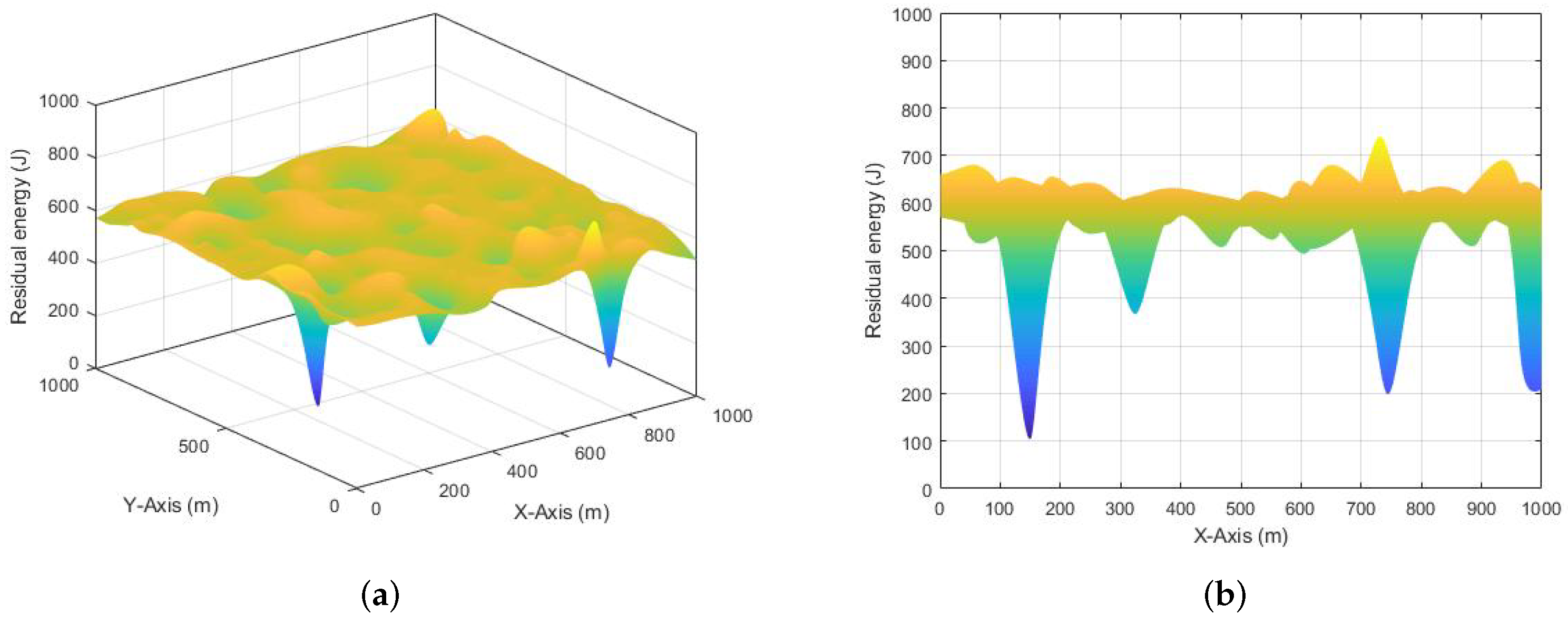
Figure 10,
Figure 11 and
Figure 12 show the residual energy surface figures of each mBS and the two-dimensional cross-sectional figures under the three-dimensional observation (view [0,0]) when the network runs 100 times.
We can see from
Figure 10 that the residual energy surface figure and cross-sectional figure of each mBS of the A* Search algorithm are not smooth and fluctuate greatly. There are many mBSs that consume the energy too fast, and the traffic load is unbalanced.
Figure 11 shows that the residual energy surface figure of the MLRF algorithm also has large fluctuation, and a few mBSs have lower energy when the network runs 100 times. Therefore, the MLRF algorithm is significantly better than that of the A* Search algorithm. Moreover,
Figure 12 shows that the residual energy surface figure of the proposed a-ADTC algorithm is smoother and has a smaller fluctuation range. When the wireless network runs 100 times, each mBS also has nearly the same residual energy, and that means the traffic load is balanced in each link. The network has better performance in TE, and the network can continue to transfer the data to the destination in an optimal state.
The above experimental results indicate that the energy resources in a small part of mBSs in both the A* Search and MLRF algorithms are likely to be drained quickly, and these mBSs cannot undertake the task of network traffic transmission any more when the network running time reaches 100 times. That means the network traffic loads of the MLRF and A* Search algorithms are unbalanced, which caused the rapid depletion of energy for a part of mBSs because the links have the overloaded traffic. In addition, it is good to see that the proposed a-ADTC algorithm in this paper has relatively balanced residual energy resources for all mBSs, when the network runs 100 rounds.
In conclusion, the simulation results in
Figure 10,
Figure 11 and
Figure 12 verify the effectiveness of the proposed traffic migration algorithm from the load-balancing aspect. Consequently, we need to consider and solve the KPI-aware optimal problem first when making any decisions regarding traffic routing.
4.5. Results Discussion
Section 4.1,
Section 4.2,
Section 4.3 and
Section 4.4 show the simulation comparison results. We find that the maximum optimization rate of the lifetime of the network can reach 60%, compared with the MLRF algorithm. This result is encouraging and fully indicates that some overloaded mBSs are effectively prolonged through traffic migration. Therefore, the wireless networks we construct in this paper are energy efficient and load balancing. Furthermore, the latency of our proposed a-ADTC algorithm is always kept in a small range, that is, 2–3 ms. This fact further proves that the distribution of traffic in the wireless network has a great influence on the link latency. Finally, through the simulation in
Section 4.3, we verify that traffic migration can improve the network throughput at the same time. In a word, for some traffic optimization problems in wireless networks, we must evaluate and migrate the traffic on some overloaded mBSs or links, which is more conducive to guarantee the QoS of the network.