Almost-Minimal-Round BBB-Secure Tweakable Key-Alternating Feistel Block Cipher
Abstract
:1. Introduction
1.1. Our Contributions
1.2. Structure of This Paper
2. Preliminaries
2.1. Notations and General Definitions
2.1.1. Block Cipher
2.1.2. Tweakable Block Cipher
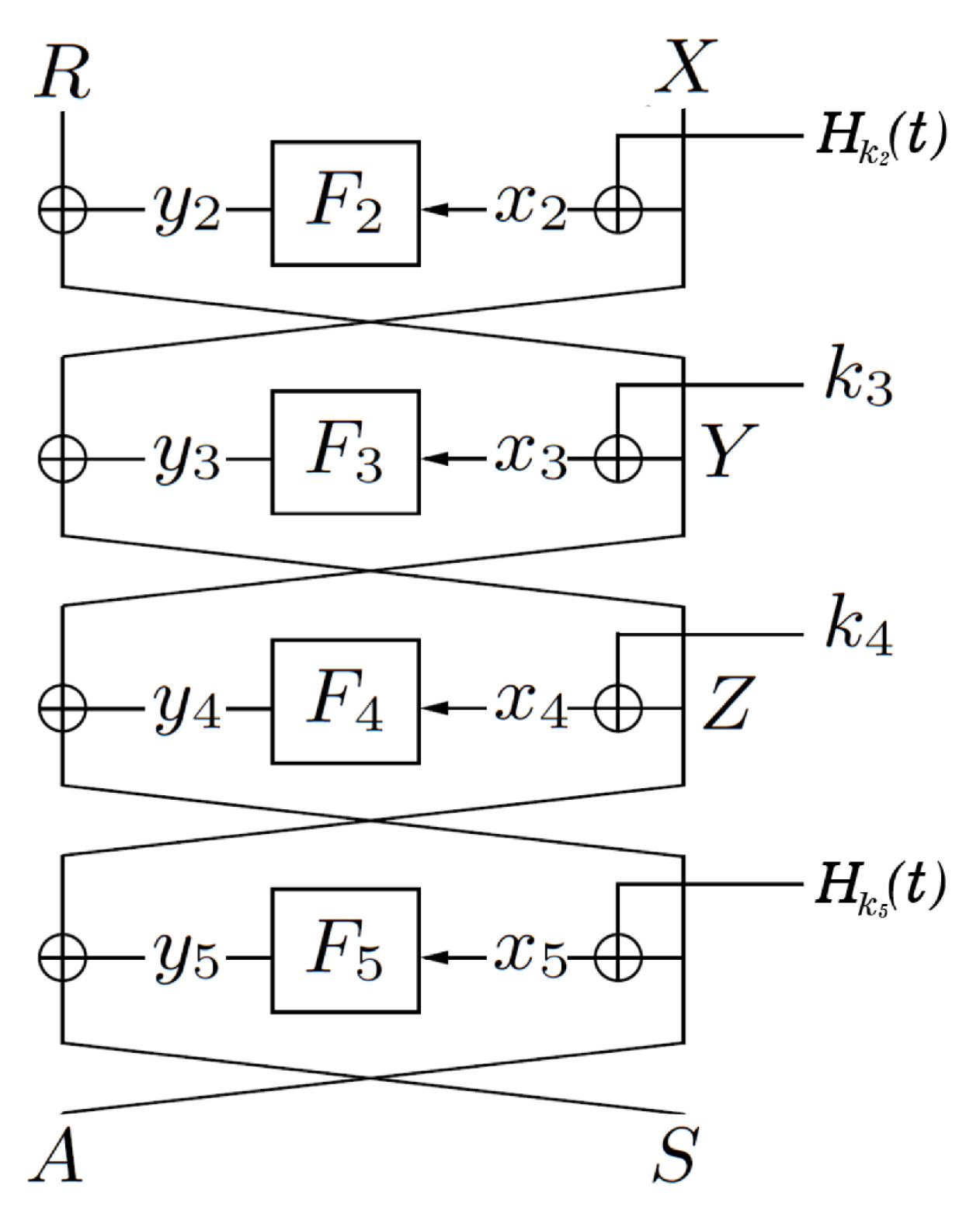
2.1.3. Key-Alternating Feistel () Cipher
2.1.4. Uniform AXU Hash Functions
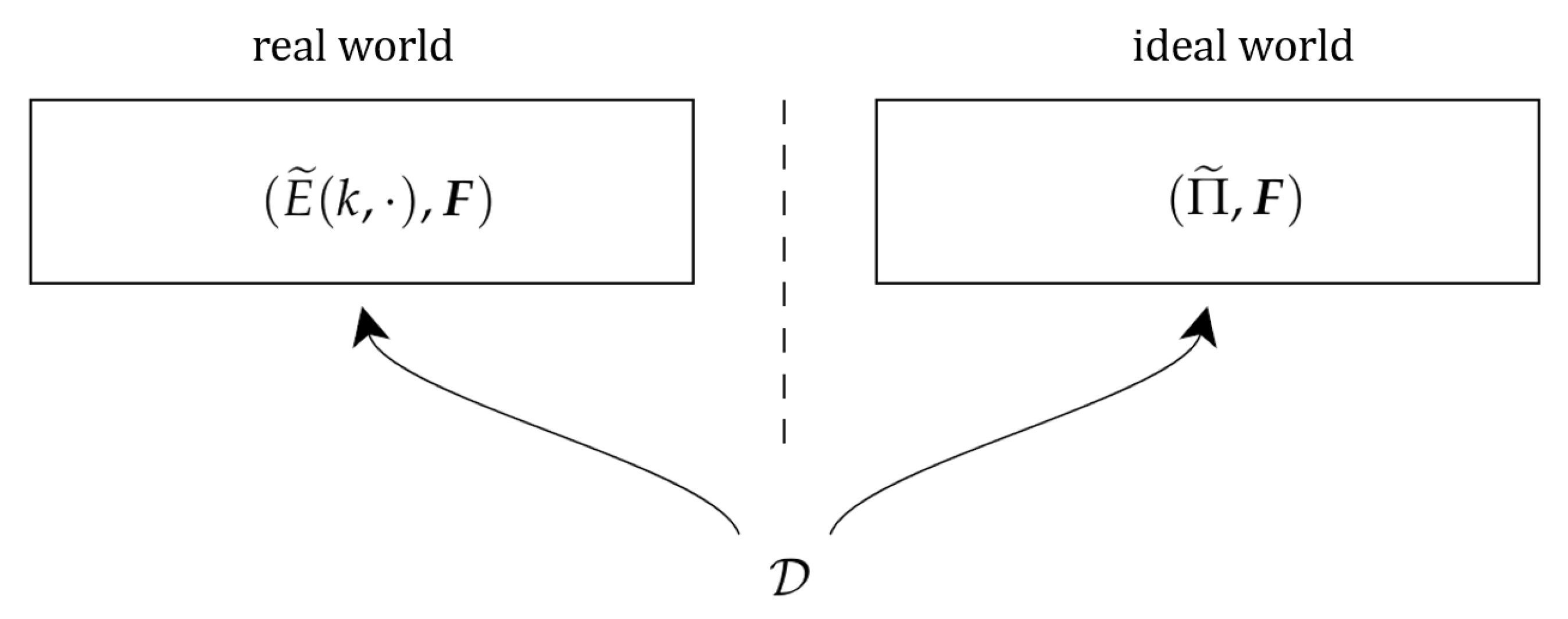
2.2. Security Definitions
H-Coefficient Technique
3. Overview
3.1. Beyond Birthday-Bound Security for Six Rounds
- (i)
- are uniformly distributed in ;
- (ii)
- for , and are independent.
3.2. Core Contribution
4. Security Proof of Theorem 1
4.1. Bad Key Vectors and Probability
- (A-1)there exists , , , such that , ;
- (A-2)there exists , , , such that , ;
- (A-3)there exists , , , such that , .
4.2. Analysis for Good Keys
Peeling Off the Outer Two Rounds
- (B-1) there exists , , , such that , ;
- (B-2) there exists , , , such that , ;
- (B-3) there exists , , , such that , ;
- (B-4) there exist two distinct , , such that and ; or symmetrically two distinct , , such that and ;
- (B-5) there exist two distinct , , such that and ; or symmetrically two distinct , , such that and ;
- Case 1: when , if it holds , i.e., for the - property of H function, the probability of is at most . If , we note that , , otherwise (A-2) is fulfilled. Thus, on the condition of , and are independent with each other, also keep uniformly random. Then it holds . Therefore, the probability of the collision at the position and is at most .
- Case 2: if and , for , the probability of is at most . AndIn addition, for , the probability of is at most . For the property of H, we have the probability of the collision at the position X is at most .
- Case 3: if and but , it can not cannot be held that and .
- Case 1: it holds , then for the distinct and , they all have choices.
- -
- If , if it holds , then the probability of is at most ;
- -
- If , if it holds , then and are independent and uniformly random. Thus, on the condition of , we haveOn the condition of , is also uniform. Hence, similar with (B-4), we have
- -
- If but , if , then it holdsand for , the probability of is at most ;
- -
- If and but , it could not be held that or .
Under the above cases, we have the probability of the collision at the position and is at most . In addition, for , the probability of (B-5)’s front part is at most . - Case 2: For , the choices of are . Similar with Case 1, we have . Therefore, the probability of holding at least one such transcript is at most .
4.3. Analysis of the Inner Four Rounds
- ;
- ;
- ;
- .
- (i)
- The two intermediate values Y and Z derived from and will not collide with the values that have been queried in the past time. So, the probability of this case is at least
- (ii)
- The intermediate value Y collides with some values of the past queries, but Z is still “free”. So, the probability of this case is at least
- (iii)
- This case is symmetrical to the second one, where Z collides with some past values, but Y is “free”. The probability is at least
5. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Proof of Lemma 5
Appendix A.1.
- Case 1-no collision: and satisfyIt holds and ;
- Case 2-left collision: satisfies , but satisfies . It holds and ;
- Case 3-right collision: satisfies , but satisfies . It holds and .
Appendix A.1.1. Case 1
Appendix A.1.2. Case 2
- Subcase 2.1:For each , by definition, we have the number of which satisfies the collision is . In addition, similar with Case 1, we can still deem as uniformly random. Thus, it holds . Therefore, the upper bound of Subcase 2.1 is
- Subcase 2.2: Define a key-dependent value:Then we have the quantity of which satisfies the collision condition is . Same as Subcase 2.1,Thus, we haveIt can be seen, is uniform in N values. So, the expectation of is at most . Thus Thus, the upper bound of the probability on the condition of Subcase 2.2 is at most .
- Subcase 2.3: By definition, we writewhere , and for i-th tuple , we have . In addition, if and only if i is the smallest index that satisfies , since .First, we focus on . Considering the probability on the condition that fits into Case 1,2 and 3. It can be seen that if fits into Case 3, then we have , it contradicts the Subcase 2.3. Let , write .
- (i)
- fits into Case 1We derive from , and keeps uniform. Then we haveFurthermore, we have . Thus
- (ii)
- fits into Case 2Let . We have . By definition, the number of choices for such is . Furthermore, for these choices of , the probability of the following two collisions is at most , i.e.,Thus
From the above, - Subcase 2.4: By definition, we writewhere , and for i-th tuple , we have . In addition, if and only if i is the smallest index that satisfies , since .First, we focus on . Let , write . That is . Thus, the collision can be seen as . Same as Subcase 2.3, we only need to consider two cases on .
- (i)
- fits into Case 1We know that and keep uniform. Then it holdsThen, we have . Thus
- (ii)
- fits into Case 3Let . We have because of . We note that if , and are “fixed”, then the possibility of choices of is at most 1. Therefore, if collides with , the following two collisions have to happen:Thus
According to Subcase 2.3, we have - Subcase 2.5: By definition, we writewhere , and for i-th tuple , we have . In addition, if and only if i is the smallest index that satisfies , since . In addition, , and for j-th tuple , we have . In addition, if and only if j is the smallest index that satisfies , since .
- (i)
- When , due to , according to Subcase 2.3, the number of choices for such is . Furthermore, for each , the upper bound of the probability is .
- (ii)
- When , due to , according to Subcase 2.4, the upper bound of the probability for each is .
To sum up, - Summing over all five subcases: We haveThe five cases above are opposite conditions to Case 2. Moreover, if it holds , then we have , , that implies the position of can be deemed as “new”.For these arguments above, we have
Appendix A.1.3. Case 3
- Subcase 3.1: On this condition, as the constraint , we havewhere
- Subcase 3.2: Define a key-dependent value:On account of the uniformity of in N choices, we have
- Subcase 3.3: By definition, we writewhere , and for i-th tuple , we have . In addition, if and only if i is the smallest index that satisfies , since . Similar with Subcase 2.3,
- (i)
- fits into Case 1We have
- (ii)
- fits into Case 3We have . Therefore,
From above with the similar calculation, we have - Subcase 3.4: By definition, we writeIt also holds . When fits into Case 2, due to , we have.Therefore,
- Subcase 3.5: Similar to Subcase 2.5, we have
- Summing over all five subcases: We have
Appendix A.1.4. Conclusions of
Appendix A.2.
- (i)
- , where ;
- (ii)
- there exists , such that , where ;
- (iii)
- there exists , such that .
- (i)
- the probability of condition (i) fulfilled is at most ;
- (ii)
- for each , if the corresponding , we haveIf the two tuples are distinct, i.e., : (a) , , and , then ; (b) if , , and , then it must be .
- (iii)
- for each , we have
- (i)
- , where , the probability is at most ;
- (ii)
- there exists , such that , where , and the probability is at most ;
- (iii)
- there exists , such that , and the probability is at most .
Appendix A.3.
- left part: consider :
- (i)
- , on account of the randomness of , for each , the probability of which is at most ;
- (ii)
- there exists , such that . For distinct two tuples in , (a) it might be , such that Y collides with some “previously-ly determined” , the probability of which is ; (b) if but (it can not cannot be ), by the randomness of , for each , the upper bound of the probability is .
- right part: consider , similar to the above:
- (i)
- , for each , the probability of which is at most ;
- (ii)
- there exists another distinct , such that . For each , the upper bound of the probability is .
References
- Liskov, M.; Rivest, R.L.; Wagner, D. Tweakable block ciphers. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 31–46. [Google Scholar]
- Landecker, W.; Shrimpton, T.; Terashima, R.S. Tweakable blockciphers with beyond birthday-bound security. In Proceedings of the Annual Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 14–30. [Google Scholar]
- Andreeva, E.; Bogdanov, A.; Luykx, A.; Mennink, B.; Tischhauser, E.; Yasuda, K. Parallelizable and authenticated online ciphers. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Bangalore, India, 1–5 December 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 424–443. [Google Scholar]
- Rogaway, P. Efficient instantiations of tweakable blockciphers and refinements to modes OCB and PMAC. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Jeju Island, Korea, 5–9 December 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 16–31. [Google Scholar]
- Rogaway, P.; Bellare, M.; Black, J. OCB: A block-cipher mode of operation for efficient authenticated encryption. ACM Trans. Inf. Syst. Secur. (TISSEC) 2003, 6, 365–403. [Google Scholar] [CrossRef]
- Crowley, P. Mercy: A fast large block cipher for disk sector encryption. In Proceedings of the International Workshop on Fast Software Encryption, New York, NY, USA, 10–12 April 2000; Springer: Berlin/Heidelberg, Germany, 2000; pp. 49–63. [Google Scholar]
- Ferguson, N.; Lucks, S.; Schneier, B.; Whiting, D.; Bellare, M.; Kohno, T.; Callas, J.; Walker, J. The Skein hash function family. NIST (Round 3) 2010, 7, 3, submitted. [Google Scholar]
- Schroeppel, R. Hasty pudding cipher specification. In Proceedings of the First AES Candidate Workshop, Ventura, CA, USA, 20–22 August 1998. [Google Scholar]
- Cogliati, B.; Seurin, Y. Beyond-birthday-bound security for tweakable Even-Mansour ciphers with linear tweak and key mixing. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Auckland, New Zealand, 29 November–3 December 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 134–158. [Google Scholar]
- Mennink, B. XPX: Generalized tweakable even-mansour with improved security guarantees. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 64–94. [Google Scholar]
- Naito, Y. Tweakable blockciphers for efficient authenticated encryptions with beyond the birthday-bound security. IACR Trans. Symmetric Cryptol. 2017, 1–26. [Google Scholar] [CrossRef]
- Feistel, H. Cryptography and computer privacy. Sci. Am. 1973, 228, 15–23. [Google Scholar] [CrossRef]
- Even, S.; Mansour, Y. A construction of a cipher from a single pseudorandom permutation. J. Cryptol. 1997, 10, 151–161. [Google Scholar] [CrossRef]
- Jean, J.; Nikolić, I.; Peyrin, T. Tweaks and keys for block ciphers: The TWEAKEY framework. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Kaoshiung, Taiwan, 7–11 December 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 274–288. [Google Scholar]
- Cogliati, B.; Lampe, R.; Seurin, Y. Tweaking even-mansour ciphers. In Proceedings of the Annual Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 189–208. [Google Scholar]
- Cogliati, B.; Seurin, Y. On the provable security of the iterated Even-Mansour cipher against related-key and chosen-key attacks. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Sofia, Bulgaria, 26–30 April 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 584–613. [Google Scholar]
- Farshim, P.; Procter, G. The related-key security of iterated Even—Mansour ciphers. In Proceedings of the International Workshop on Fast Software Encryption, Istanbul, Turkey, 8–11 March 2015; Springer: Berlin/Heidelberg, Germany, 2015; pp. 342–363. [Google Scholar]
- Granger, R.; Jovanovic, P.; Mennink, B.; Neves, S. Improved masking for tweakable blockciphers with applications to authenticated encryption. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Vienna, Austria, 8–12 May 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 263–293. [Google Scholar]
- Luby, M.; Rackoff, C. How to construct pseudorandom permutations from pseudorandom functions. SIAM J. Comput. 1988, 17, 373–386. [Google Scholar] [CrossRef]
- Mitsuda, A.; Iwata, T. Tweakable pseudorandom permutation from generalized feistel structure. In Proceedings of the International Conference on Provable Security, Shanghai, China, 30 October–1 November 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 22–37. [Google Scholar]
- Lampe, R.; Seurin, Y. Security analysis of key-alternating Feistel ciphers. In Proceedings of the International Workshop on Fast Software Encryption, London, UK, 3–5 March 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 243–264. [Google Scholar]
- Goldenberg, D.; Hohenberger, S.; Liskov, M.; Schwartz, E.C.; Seyalioglu, H. On tweaking luby-rackoff blockciphers. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Kuching, Malaysia, 2–6 December 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 342–356. [Google Scholar]
- Yan, H.; Wang, L.; Shen, Y.; Lai, X. Tweaking Key-Alternating Feistel Block Ciphers. In Proceedings of the International Conference on Applied Cryptography and Network Security, Rome, Italy, 9–22 October 2020; Springer: Cham, Switzerland, 2020; pp. 69–88. [Google Scholar]
- Guo, C.; Wang, L. Revisiting key-alternating Feistel ciphers for shorter keys and multi-user security. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Brisbane, QLD, Australia, 2–6 December 2018; Springer: Cham, Switzerland, 2018; pp. 213–243. [Google Scholar]
- Patarin, J. The “coefficients H” technique. In Proceedings of the International Workshop on Selected Areas in Cryptography, Sackville, NB, Canada, 14–15 August 2008; Springer: Berlin/Heidelberg, Germany, 2008; pp. 328–345. [Google Scholar]
- Chen, S.; Steinberger, J. Tight security bounds for key-alternating ciphers. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Copenhagen, Denmark, 11–15 May 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 327–350. [Google Scholar]
- Hoang, V.T.; Tessaro, S. Key-alternating ciphers and key-length extension: Exact bounds and multi-user security. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 3–32. [Google Scholar]


Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, M.; Wang, L. Almost-Minimal-Round BBB-Secure Tweakable Key-Alternating Feistel Block Cipher. Symmetry 2021, 13, 649. https://doi.org/10.3390/sym13040649
Jiang M, Wang L. Almost-Minimal-Round BBB-Secure Tweakable Key-Alternating Feistel Block Cipher. Symmetry. 2021; 13(4):649. https://doi.org/10.3390/sym13040649
Chicago/Turabian StyleJiang, Ming, and Lei Wang. 2021. "Almost-Minimal-Round BBB-Secure Tweakable Key-Alternating Feistel Block Cipher" Symmetry 13, no. 4: 649. https://doi.org/10.3390/sym13040649
APA StyleJiang, M., & Wang, L. (2021). Almost-Minimal-Round BBB-Secure Tweakable Key-Alternating Feistel Block Cipher. Symmetry, 13(4), 649. https://doi.org/10.3390/sym13040649






