1. Introduction
With the rapid development of the Internet and information technology, the amount of people using smart phones has risen. Additionally, it is notable that the usage of smart phones has been enriched with functions such as sending e-mails, searching information on the Internet, or shopping on websites, paying online or credit transferring with confidential information features. Therefore, the security when transferring sensitive data should be ensured, otherwise people might suffer from the theft of personal property.
It is noteworthy that QR codes can store data and be used for obtaining data when the device is offline. They have been used widely in daily life for functions such as ticketing systems, product tracing, electronic transactions, social networks, etc. However, people usually scan them directly, without confirming their trustworthiness. Cryptography is a common method to assure the information security in the digital transmission. There are two ways to encrypt private data via cryptography, symmetric cryptography and asymmetric cryptography [
1]. A QR code uses an asymmetric encryption scheme to store and retrieve data efficiently [
2,
3]; QR codes are not readable with the naked eye and people usually rely on optical instruments when scanning for data. When operating the information obtained from public environments, it is possible that the users might expose their sensitive information, as they are not aware that the QR code might have been tampered with, and the website address they are accessing could possibly be a phishing website [
4,
5,
6,
7,
8]. Therefore, it is necessary that people have a way to validate if the website address is issued by the publisher. If paying information is usurped, it might bring about financial losses. Moreover, if the personal and private information is leaked to a phishing website, it could endanger the personal safety of the user. In other words, it is more and more important to verify the data or website addresses from QR codes in this information based society we live in.
Owing to the designed mechanism, anyone who has a camera built into their smart phone and installs QR code scanning software could scan a QR code to acquire the information of it. That shows the potential risks: it is possible that the information of QR code might be divulged to hackers. For the most part, to protect the private data that would be shared by QR code, the administrator will store the message in the database in the cloud, and replace the message with an URL showing a website address that could link to the backend database. Only a user who has right to pass the access permission can retrieve the data. However, this method of showing the database website address may attract attackers’ attention to try to access the secret message.
Recently, in order to prevent the data which have to be hidden from exposure to the public, many studies have focused on QR codes. In 2009, Chen et al. [
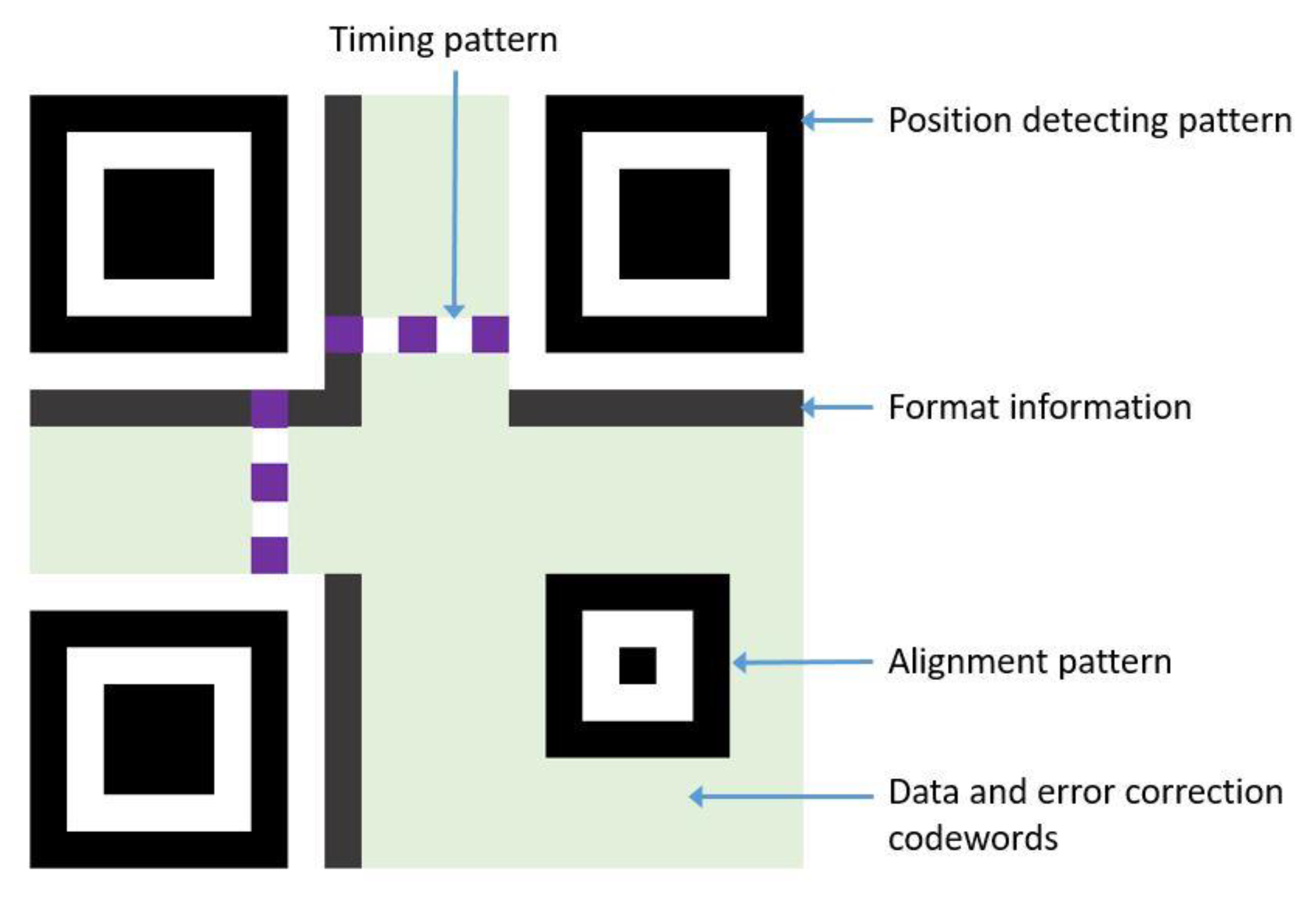
9] proposed a scheme that utilizes steganography. It firstly generates a QR code with a text, then removes some functional patterns of QR code. As a result of removing the position detecting pattern and alignment pattern, the QR code would only retain the important information, such as version, error correction level, data and error correction codewords, etc. Then, flatten them from a 2-D bit stream into 1-D bit stream. Finally, after choosing the coefficients of discrete cosine transform (DCT), the 1-D bit stream would be embedded into the cover image. The secret payload would depend on the version of QR code image. However, this scheme would cost lots of computational resources.
On the other hand, Sun et al. [
10] proposed a watermarking scheme applied to QR codes. There are two algorithms in the scheme; both of them are utilized with Discrete Wavelet Transform (DWT). One firstly generates random serial numbers as secret key, then embeds them into the cover of the QR code for authentication. The other one embeds a binary image, such as a logo, into the cover of the QR code, preventing counterfeits. However, neither algorithm modifies modules in the QR code, which would make the cover QR code, and the fact that it is embedded with some information, easily found.
There are distributed data sharing schemes [
11,
12,
13,
14,
15,
16,
17] that allow the message to be segmented into numerous shadows. The original message can be recovered when the participants hold enough shares which contain the shadows. Furthermore, these data sharing schemes use QR codes as cover images, and all of them modify the modules to share the data (except Chuang et al.’s scheme [
13]). Utilizing the error correction characteristic of QR codes, the schemes could allow the marked QR code to remain meaningful. However, Lin et al.’s scheme [
12] would cause additional issues on distributing the keys, though it could hold more space for data. In [
15], Huang et al. proposed an efficient QR code data embedding mechanism based on the Hamming code. The (8, 4) Hamming code is utilized for embedding the secret message into the cover of a QR code. In [
16], Alajmi et al. proposed a steganographic system that adopts the notion of quick response (QR) code as a container for hiding the payload. By doing so, misleading information can easily be exposed to the adversary.
Although Chuang et al.’s scheme [
13] and Huang et al.’s scheme [
15] can share data without additional information, the message would be obtained as a meaningless number stream by anyone who has a QR code reader. It would be a serious problem if everyone can access the shadow of secret bits without any permission or requirement. In another aspect, Lin’s scheme can make the marked QR codes be meaningful, but it needs to manage key distribution. Without knowing the keys, the scheme cannot recover the original message.
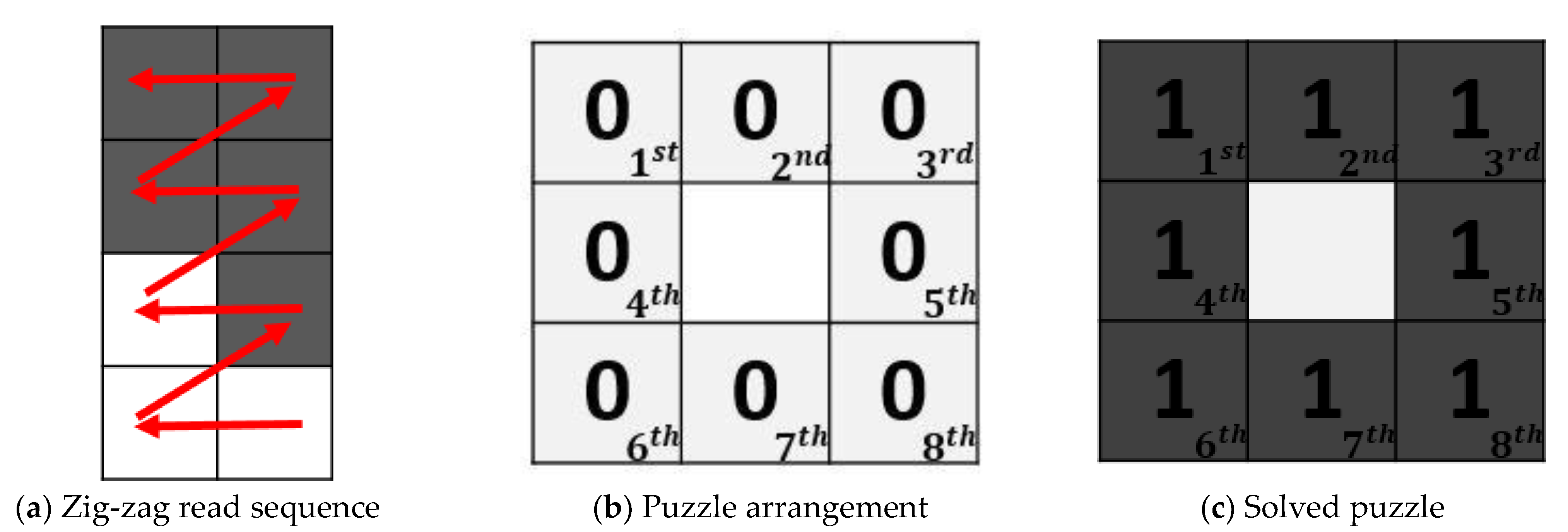
To overcome the above-mentioned issues, Huang et al. [
11] proposed a scheme that utilizes a Sudoku puzzle to encode secret message and embed it into QR codes. However, using Sudoku puzzle to encode data would raise two issues: (1) a low capacity for the message and (2) a limited position of the puzzle. The issue of low capacity for the message is due to the fact that embedding a whole Sudoku puzzle would cost lots of bits. However, using a Sudoku puzzle to encode a message may cost a lot of digits of QR code for embedding the puzzle into QR code. For example, it could be referred that novenary
Sudoku puzzle size = 4 bits
(9
9) = 364 bits for each share when we embed a message with 0 bits. Moreover, the method of Sudoku puzzle encoding is coordinate-like, which leads to the issue of a limited position of the puzzle. As a result, it would cost additional bits to represent the coordinates of each cell of the Sudoku embedded in QR codes. As shown in Huang et al.’s work [
11], when the secret message is “2015”, firstly transform it into novenary:
. Then, it would be represented as
accordingly. Finally, it will cost 4 bits hexadecimal
8 = 32 bits, simply for sharing a 4-digit number. To address the issues raised by the Sudoku puzzle-based QR code scheme, in this paper, we propose a new breed of puzzle which is coordinate-free. Based on our proposed coordinate-free puzzle, we propose a new scheme which can preserve more capacity for data. Through a series of experiments, we provide sufficient evidence to prove that our proposal outperforms state-of-the-art QR code data embedding schemes.
The rest of this paper is organized as follows. We first introduce some related work in
Section 2.
Section 3 explains the deep learning-based approaches for Image Authentication and Recovery System.
Section 4 presents the experiment and discussion, and
Section 5 contains the conclusion.
4. Experimental Result
To evaluate the practical applicability of the proposed scheme, an application is developed with the open-source library, ZXing library [
19] which is based on Java program language and used to generate and decode QR codes. According to the QR code standard, the 5-H version of QR code consists of 134 codewords. There would be 46 data codewords and 88 error correction codewords in the QR code. We choose the byte mode to generate QR code images in the proposed system. Then,
Figure 5 shows the other example of the proposed scheme with version 10, and the error correction level is Q.
Figure 5a,b show the public message of QR codes with “
https://www.nchu.edu.tw/” (accessed date: 9 September 2021) and
http://mis.nchu.edu.tw/ (accessed date: 28 September 2021), the website addresses to the homepages of National Chung Hsing University and Management Information System Department of National Chung Hsing University.
Figure 5c,d are the marked QR codes. The result shows that the higher version of QR code may cause delay time as the camera of smart phone needs to focus on the QR code image when the size of itself is fixed.
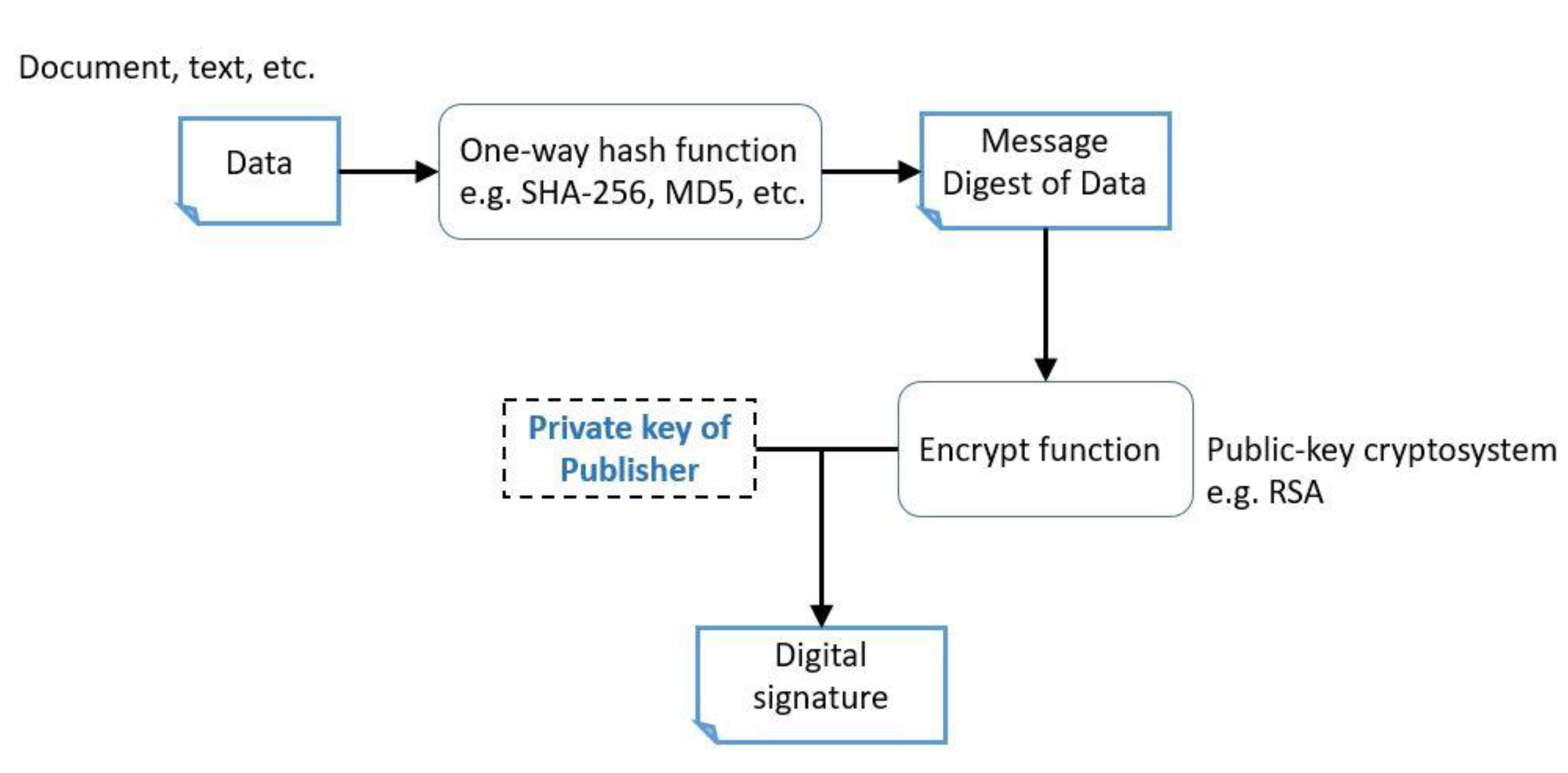
The feature of meaningful QR codes could decrease the curiosity of common QR code users when scanning in public environment. Moreover, the designed scheme, which is puzzle-based and cheater preventing, could protect the secret message from a malicious attack of altering the QR code image. According to the cheater identification phase of the proposed scheme, the digital signature will be obviously different, as the technique can distinguish if even one bit from the real marked QR code is modified. In addition, the designed puzzle in the proposed scheme would be totally changed if there is a bit different from original bit stream of puzzle.
Table 2 illustrates the capacity of private data storage of the proposed scheme. The digital signature is composed of 32 bytes which is equal to at least 256 bits. The more bits of public and private keys chosen, the more bytes the digital signature would need. Additionally, the minimum secret message is one character; in other words, 1 byte of secret message is needed. Then, the digital signature appended after the minimal secret message will result in a 33-bytes camouflage message. Beside the least length calculation, the mechanism of error correction of the QR code is generated by the Reed Solomon Code algorithm [
30], therefore, there should be two error correction codewords to recover one data codeword for the marked QR code.
In a drastic situation, the 33 bytes of camouflage message with the minimum amount of data, there must be more than 66 error correction codewords on the QR code image. By calculating with the QR code standard, it can be found that version 5, with error correction level Q, could be in accordance with the minimum that the bytes of the least camouflaged message needs. The schemes mentioned in
Section 2 will be discussed and compared to the proposed scheme.
Table 3 shows the summary of feature comparison among them. To overcome the drawback brought from the Sudoku puzzle, a new puzzle-based scheme has been proposed in this paper. By applying the puzzle algorithm, the shadows can be protected in an efficient way, and there is no need to put additional information with it. In addition, the technique of a digital signature could not only verify the publisher, but also procure the purpose of authentication. Though it requires more bits than only utilizing the one-way hash function, it can protect the information with better security.
Aside from providing an efficient encoding method, the marked QR code can resist many kinds of defects which may be caused by the transmission process.
Table 4 shows that the marked QR code version 10, with error correction level Q, suffered from Gaussian noise by standard deviations of 10 to 100, and can still be scanned for data.
Table 5 points out that the same mark QR code could still be decodable after Gaussian blur with different radii of pixels.
Table 6 indicates that the marked QR code can perform well under JPEG compression with disparities of compression rates.
Table 7 illustrates the fact that the marked QR code can still be scanned for information from different angles of rotation.
Figure 6a shows the tempered marked QR code with different blocks alteration.
Figure 6b indicates the tempered marked QR code with a large block modification. All could be decoded for a meaningful message.
The feature comparison among the proposed method and previous schemes is shown in
Table 3. The proposed scheme can not only ensure the marked QR code remains meaningful, but can also accomplish cheater identification. Moreover, the proposed scheme can use a lower version of QR code, which means the size of QR code image could be smaller. The capacity of the proposed scheme can hold more data than the others, except Lin’s scheme. Though Lin’s scheme could hold more bits than ours, the ability of identifying cheater is varied down to nothing. Notice that in the data capacity of Huang’s scheme, the maximum is 9260 bits with careful calculation, and not 9260 guaranteed, which is pointed out in Huang et al.’s scheme.