1. Introduction
Quantum Secure Direct Communication (QSDC) protocol is one of the quantum cryptography concepts that securely transmits the message directly in the quantum channel, where all the information deals with the quantum state. QSDC promotes a high level of protocol security by instantly transmitting the message directly to the quantum channel. Long and Liu introduced the first QSDC protocol in 2002, which securely and directly transmitted the secret message without using a key in advanced [
1]. The modified version of the basic QSDC protocol has been introduced, which are (Einstein–Podolsky–Rosen) EPR QSDC [
2] and single-photon QSDC. EPR QSDC utilized the block of EPR pairs as carriers to directly transmit information, while single photon QSDC combined a one-time pad protocol with the secret message [
3].
The security requirement in QSDC is stricter compared to Quantum Key Distribution (QKD) since an eavesdropper must not uncover the transmitted messages. Like QKD, QSDC is divided into three approaches: Quantum entanglement [
4], single-photon [
5,
6], and multiple photons [
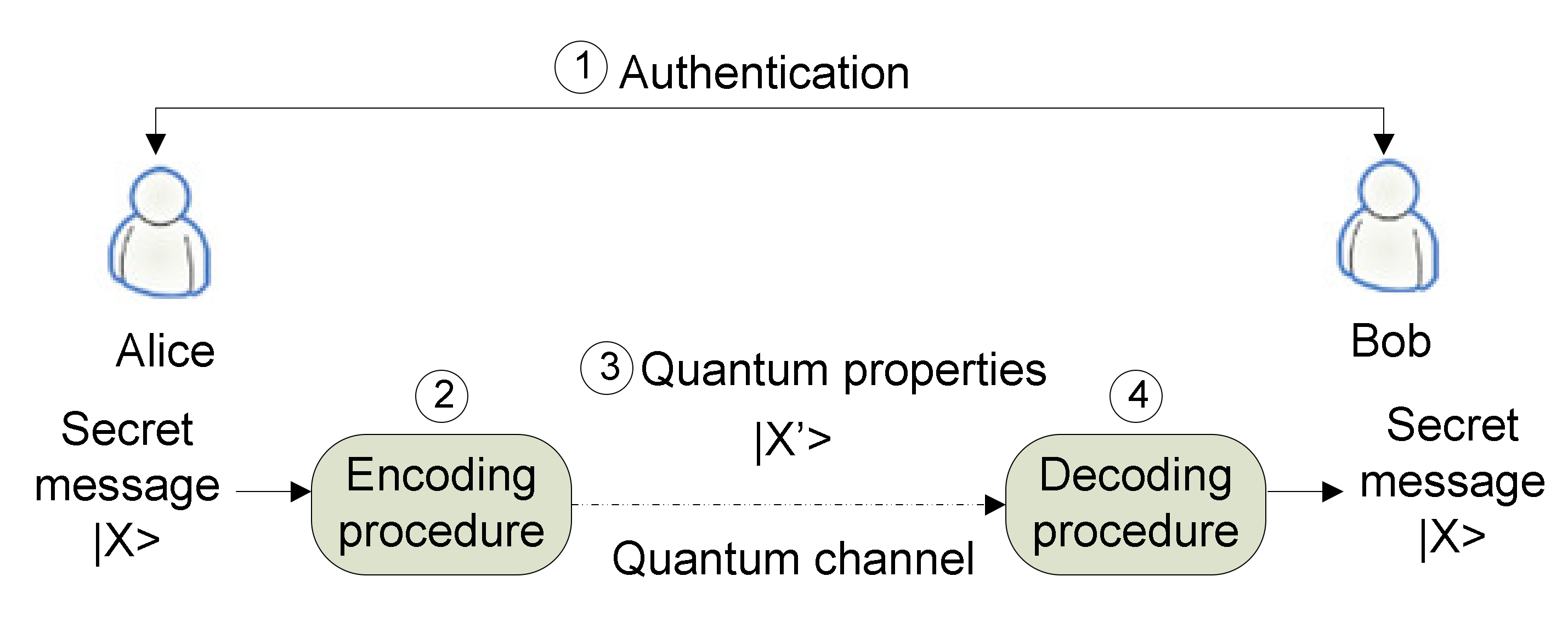
7]. All of the QSDC protocols consist of four parts: Authentication, encoding, the transformation of quantum properties, and decoding, as illustrated in
Figure 1. QSDC starts with the authentication process to verify the identity of Alice and Bob. After the successful authentication process, Alice embeds the sensitive information using the proposed QSDC encoding procedure and sends the secret message over the quantum channel. To encode the information, various properties of photons can be employed such as phase, polarization, EPR quantum correlation pairs, wavelength, or quadrature components of squeezed state of light [
8]. Bob will then retrieve the contents of the secret message through the proposed decoding process.
One of the biggest limitations of QSDC is the low transfer rate in the long-distance quantum channel [
7,
9]. To overcome this limitation, a concept of multi-photon was proposed by Subhash Kak [
10], namely the three-stage protocol that can directly share the message over the multi-stages of the quantum channel using a rotational change in polarization. The multi-photon provides security features without the involvement of the key distribution step, and no entanglement is required. In the multi-photon protocol, photons act as the carrier to carry the quantum information by polarizing their quantum properties, i.e., |
and |
.
Given the advantages of multi-photon QSDC, it remains a challenge to enforce QSDC authentication on behalf of each entity. Throughout quantum communication, a good authentication component is essential to ensure the legitimacy of users. Moreover, the participants in the communication must be authenticated to secure the transmitted message from the man-in-the-middle (MITM) attack [
11,
12]. The problem of today’s authentication is the complex environment of networks. A network administrator, therefore, finds it very difficult to apply a consistent set of authentication, quality of service, and security schemes that are safe from security breaches and comply with regulations [
13].
Unlike our previous work [
14] that focused on increasing the transmission rates by reducing the transmission time in multi-photon over multi-stage protocol, here, the issue of authentication is focused. The aim of this paper is, therefore, to recommend a secure way to share the initial secret angle and authentication key between users over a multi-stage quantum channel. In this work, the symmetry key is applied to secure the user’s data communications in QSDC protocol, where the same secret key is used to encrypt and decrypt the message. Therefore, the secret key must be exchanged securely over the communication channel, thus that the sender and receiver are symmetry on both sides. To solve the problem of initial communication in the authentication phase, a quantum handshake protocol is proposed to share Alice’s secret angle and the authentication key [
15]. In addition, an update function of the secret angle and the authentication key is proposed based on a mutually agreed algorithm. The proposed protocol in this paper sends multi-photon over the single-stage and implements bit-by-bit authentication to defend against a MITM attack. It should be noted that Alice is a trusted party that does not mislead the information. This protocol will significantly improve the existing multi-photon works of references [
7,
9] that need to share the secret angle at the onset of the transmission over the secret channel. This protocol significantly improves communication efficiency without losing security. The main contributions of this work are as follows:
- (1)
The secret angle and authentication key are generated by Alice, and no third party is involved in the process to enhance the confidentiality of the communication. Thus, no pre-shared authentication key and initial secret angle are exchanged between Alice and Bob at the onset of the communication, which occurs in public channels.
- (2)
The secret angles and the authentication key are updated using a mutually agreed algorithm after a number of bits sent to increase the security level.
- (3)
The QSDC protocol is operated in single-stage, and the authentication is applied bit-by-bit, thus reducing the transmission time, and the security check is done along with the data transmission process.
The remainder of this paper is organized as follows. In
Section 2, the importance of the authentication procedure in QSDC is discussed. Related works are presented in
Section 3, while
Section 4 presents the secure shared authentication key protocol.
Section 5 shows the example of the proposed protocol.
Section 6 discusses the performance analysis, while
Section 7 provides the implementation issues of the proposed protocol. Finally, the conclusion of this paper is summarized in
Section 8.
2. The Importance of Authentication for QSDC
The authentication procedure is significant to avoid the legitimate parties’ identities being impersonated by an eavesdropper that contributes to the leak of secret messages. In order to avoid eavesdroppers’ attacks, existing quantum cryptography protocols typically require a third-party authentication for Alice and Bob to initiate the communication. However, some drawbacks may occur when a third party is involved in the communication. Third-party authentication is typically based on the classical cryptography assumptions that utilize computational complexity. Another problem noted is Eve can still attack the quantum communication channels after Alice and Bob are authenticated to circumvent the third party authentication, leaving such attack undetected as revealed in reference [
16]. This type of attack is called the Intercept-Resend attack, which will be discussed later in this paper.
Thus, to overcome the aforementioned problem, the authentication process should be performed during the quantum data communication process. It is important to ensure that the parties involved in the protocol are whom they are supposed to be; this is what we call identity authentication. In addition, the data origin authentication can be done on a bit-by-bit basis to eliminate the possibility that Eve attacks the quantum channel after Alice and Bob are authenticated. This step is important to ensure that the data originate from the right sender and is received by the right receiver. The important part of the authentication is to share the authentication key between Alice and Bob to allow the recognition process [
16]. The authentication key is important to avoid a MITM attack launched by Eve, who is pretending to be Alice and Bob at the same time. The authentication key must not be revealed to Eve and needs to be shared secretly between Alice and Bob before the process of authentication has started. This process is done in the initial part of the authentication by sharing the sender’s secret angle and the authentication key since pre-shared is not suitable to be adapted because it deals with the public channel.
In quantum communication, it is essential to reduce the level of complexity and, at the same time, maintain the security of the system against eavesdropping attacks. However, a direct link between Alice and Bob will significantly be affected where an eavesdropper can overhear, jam, or spoof the communication between them [
17]. Recent work by [
18] showed that an eavesdropper might span into multiple smart attackers that can overhear the secure message depending on their location between the transmitter and the receiver. In addition, the investigation by reference [
19] proved that an attacker might use several transmitter antennas to increase the attack rate. It can be concluded that the eavesdroppers can utilize various types of attacks to intercept secret messages. Thus, the improvement of data and transmission secrecy is an urgent issue to be solved in the communication area.
3. Related Works
In the last few years, several authentication protocols for multiphoton QSDC have been proposed. The main objective of those approaches was to ensure that the messages are delivered securely to the legitimate parties. This section reviews several multiphoton QSDC’s authentication approaches over multi-stage to validate the parties involved in quantum communication, discussing their basic concepts, and describing their advantages and drawbacks.
In reference [
20], a single-stage protocol was proposed to transmit the photon in a stage using secret unitary transformation. The security strength of this protocol relies on the secret value of the polarization angle, θ, and it must be secret along with the communication between Alice and Bob. Otherwise, the security of this protocol cannot be compromised anymore when the eavesdropper is able to get the value of θ. This protocol assumes that there is another protocol operated, such as a trusted certificate exchanged before the secure transmission begins. The authors in [
9] presented a secure quantum communication over a single-stage, hereafter called it a Braided Single Stage protocol. The idea of Braided Single Stage protocol is to overcome the drawback of the three-stage protocol by reducing the overhead to encode the photons. Later, the IV Three-stage protocol [
7] was proposed based on the adoption of an Initialization Vector (IV) to be a one-time pad key as the extra dimension of security for the three-stage protocol.
All of the mentioned approaches utilized the three-stage protocol to handle the authentication process in the first phase by sharing the initial value of secret polarization angle
(e.g., 0°, 25°, 50°, …, 180°) that is predetermined among users. The set is usually exchanged via a secret channel [
21,
22] over the public channel or using face to face communication. However, the technique of exchanging the secret angle is omitted. Besides, the reviewed multi-photon approaches only assumed that the sender and receiver to be mutually trusted parties, and they are already authenticated to each other [
7,
23]. The usage of the authentication key that is only known by legal parties is able to provide secrecy in the authentication of QSDC [
16,
24,
25]. Hence, combining the unitary transformation with the authentication key has become an appropriate strategy to construct high-level security of the cryptographic protocol. Therefore, an important question in this research is how to share the secret angle and authentication key securely in the quantum channel? Most of the authentication schemes are based on pre-shared secret information, which is not so practical for the initial communication of trusted parties [
15]. To mitigate these issues, a secure shared authentication key (SSAK) is proposed in this paper. The SSAK protocol shares the secret angle and authentication key using the quantum handshake mechanism. The main objective of the proposed SSAK protocol is to improve the efficiency of authentication and reduce the communication cost by avoiding public channel usage.
4. Secure Shared Authentication Key (SSAK) Protocol
This section presents the proposed SSAK protocol. The SSAK protocol focuses on the idea of sharing a secret angle and an authentication key between Alice and Bob over a multi-stage quantum channel. In the proposed protocol, an Information Travel Time (ITT) or Time Stamp technique associated with the data [
26] is adopted to detect the presence of eavesdroppers in the initial authentication procedure. In the condition, Eve is located midway between Alice and Bob, the ITT is obviously different due to the fact that the distances between Alice and Bob are greater than the distance between Alice and Eve as well as Eve and Bob. However, in the case of Eve located far away from Alice and Bob, the ITT would be doubled and shows a sign of eavesdroppers’ attack. Thus, when quantum particles pass through optical polarization devices on the sender’s site, and an eavesdropper is present in the communication to read the photon, the response by the receiver might induce abnormal timing information. Moreover, this work utilizes the Pauli-X quantum gate to increase the difficulty for Eve to steal the information. Theoretically, a wire of transmission carries a qubit of information, and the quantum gate will take that qubit as an input. Here, the function of the quantum gate is to perform the unitary transformation on this qubit and produce a new state of qubit as an output. Pauli-X gate is also known as a bit flip operator that is responsible for altering the qubit state by flipping bit 0 to 1 and vice versa. Based on previous research, the quantum gate provides many benefits such as being easy-to-use as the information related to the operators is not necessarily shared between the parties, has less precision requirement compared to in arbitrary rotation such as half-wave plate (HWP), and provides accurate measurement [
27].
The details of the proposed protocol can be described in three phases: Initial authentication, secure message sharing, and security checking.
Figure 2 shows the whole process of the proposed SSAK protocol.
4.1. Initial Authentication Procedure
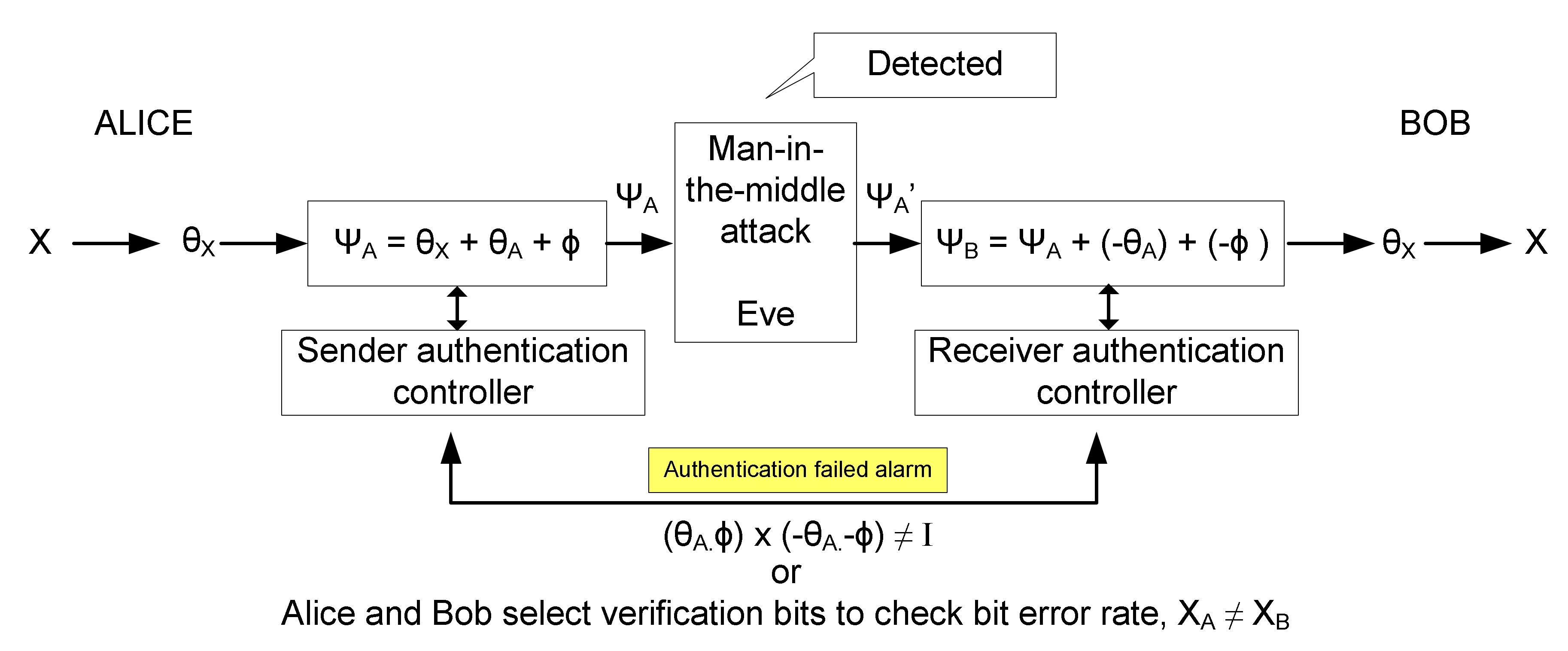
Alice is the party that supposedly sends a message to Bob. For Alice, it is extremely important to ensure the messages are only received by the authenticated user who is Bob. However, Bob faces difficulties when he receives the message; he does not know whether it comes from Alice or an eavesdropper. The initial part of authentication is important to verify the party that initiates the communication. Therefore, in this paper, a novel quantum handshake for sharing initial secret angle and authentication key, which is utilized before the quantum communication session is proposed. The objective of the proposed protocol is to allow Alice to identify herself to Bob and Bob can prove that Alice is a legitimate party. Note that operator
and
operators in
Figure 2 are defined as encrypt and decrypt operations with key
.
The steps of the proposed protocol are discussed below:
First item, Alice prepares a private orthogonal state and generates a random quantum state using a random number generator. Based on the decimal value of , she prepares five binary digits and do Pauli-X quantum gate operation to produce . She then encrypts with to produce the quantum state . The is set to
Second item, Bob generates a random quantum state using a random number generator and encrypts it with the received quantum state and produces . The is set to
Third item, Alice decrypts the received with to generate and sends it back to Bob. At this stage, Alice is able to extract Alice will verify the after she gets the photon replied by Bob. Alice starts to analyze the difference between the sending and receiving time. If Alice gets , an eavesdropper is detected and she will terminate the communication. Otherwise, the communication will be continued. Then, the is set to 4.
Bob applies to obtain the and successfully extracted . Bob gets the value of and converts it into five binary digits. He then does the Pauli-X quantum gate operation to generate new value of . Next, he encrypts it with the received quantum state to produce quantum state and sends it to Alice.
Alice authenticates Bob by comparing and analysing using measurement. If the value is correct, she will then send the authentication key that is generated using a random number generator. The is then encrypted with the that she had extracted in step 3 to produce and passed it back to Bob. If the value is different, the communication will be terminated and needs to be restarted.
Bob couples the receiving with , to get the authentication key .
After the authentication is successfully completed, Alice will start to convert the string of bit message into the photons and directly sends it to Bob using the initial secret polarization angle ( and authentication key (.
4.2. Secure Message Sharing Procedure
It is assumed that Alice and Bob have the same secret angle and authentication key that they shared in the initial stage of authentication in
Section 4.1. Suppose that Alice’s secret message
is a series of classical bit of 0 and 1 in order,
.
Alice encrypts her secret message by generating a state with a linear polarization using a 0° polarizer as bit 0 or using 90° polarizer as bit 1 to get .
Quantum state is then coupled with initial and sent along with the initial authentication key by Alice. The combination of , and generates are sent to Bob.
Bob receives the quantum state and couples it with and obtains information .
Alice and Bob frame the received bits and convert the last
to integer value
, given by
where
k is the number of transmitted keys,
b is the sequence of the transmitted bits (i.e., the bits
) using the last n bits to generate the new angle
θ.
Alice and Bob compute new value of θ and
, given by
4.3. Security Checking Procedure
Alice and Bob will check the authenticity between them by performing a measurement. By doing so, if there is no eavesdropper, Alice will be ensured that she received the same value as Bob, given by
where “
” is the multiplication operator and
is the identity matrix. If there is an eavesdropper, in the case of Alice’s result is not the same with Bob, then Alice will announce to Bob to abort the communication, where
5. Example of the Proposed Protocol
Let us illustrate an example of the proposed protocol and describe the three parts of secure QSDC, which is the initial authentication procedure, message sharing procedure, and security phase procedure. The implementation of proposed SSAK has been tested using a simulation developed via Python programming language. Python is chosen due to its capabilities to simulate the quantum state in superposition via mathematical form. The pseudo-code of SSAK protocol is detailed in Algorithm 1.
5.1. Initial Authentication Procedure
The initial authentication procedure is explained as follows:
Suppose that Alice prepares a photon and generates a random secret angle, . Based on the decimal value of , she converts it into binary digits and employs Pauli-X quantum gate operation to produce . She converts it back to decimal value,. The new value will be used as the security check for the next procedure. She starts to encrypt using and produce quantum state . The is set to .
Bob generates a random secret angle and encrypts it with the received quantum state and produces . The is set to .
Alice decrypts the received with to generate and sends it back to Bob. At this stage, Alice gets Alice will verify the after she gets the photon replied by Bob. If Alice gets the , an eavesdropper is detected, and she will terminate the communication. Otherwise, the communication will be continued. The is set to .
Bob applies to obtain . He gets the value of and converts it into the binary digits . Using the Pauli-X quantum gate, he gets , and he converts it back into decimal value and generates . He then encrypts it with the received quantum state to produce quantum state and sends it to Alice. The is set to .
Alice authenticates Bob by comparing and analyzing using measurement. If , she sends the initial authentication key that is generated using a random number generator and encrypts it with . If , the communication will be terminated and need to be restarted.
Finally, Bob couples the receiving with to get the authentication key .
It can be concluded that the security of the proposed scheme depends entirely on the initial authentication procedure, where the eavesdropping check and identity authentication are implemented at the same time.
5.2. Message Sharing Procedure
In this section, the implementation of SSAK protocol over free space optics using passive optical components is discussed.
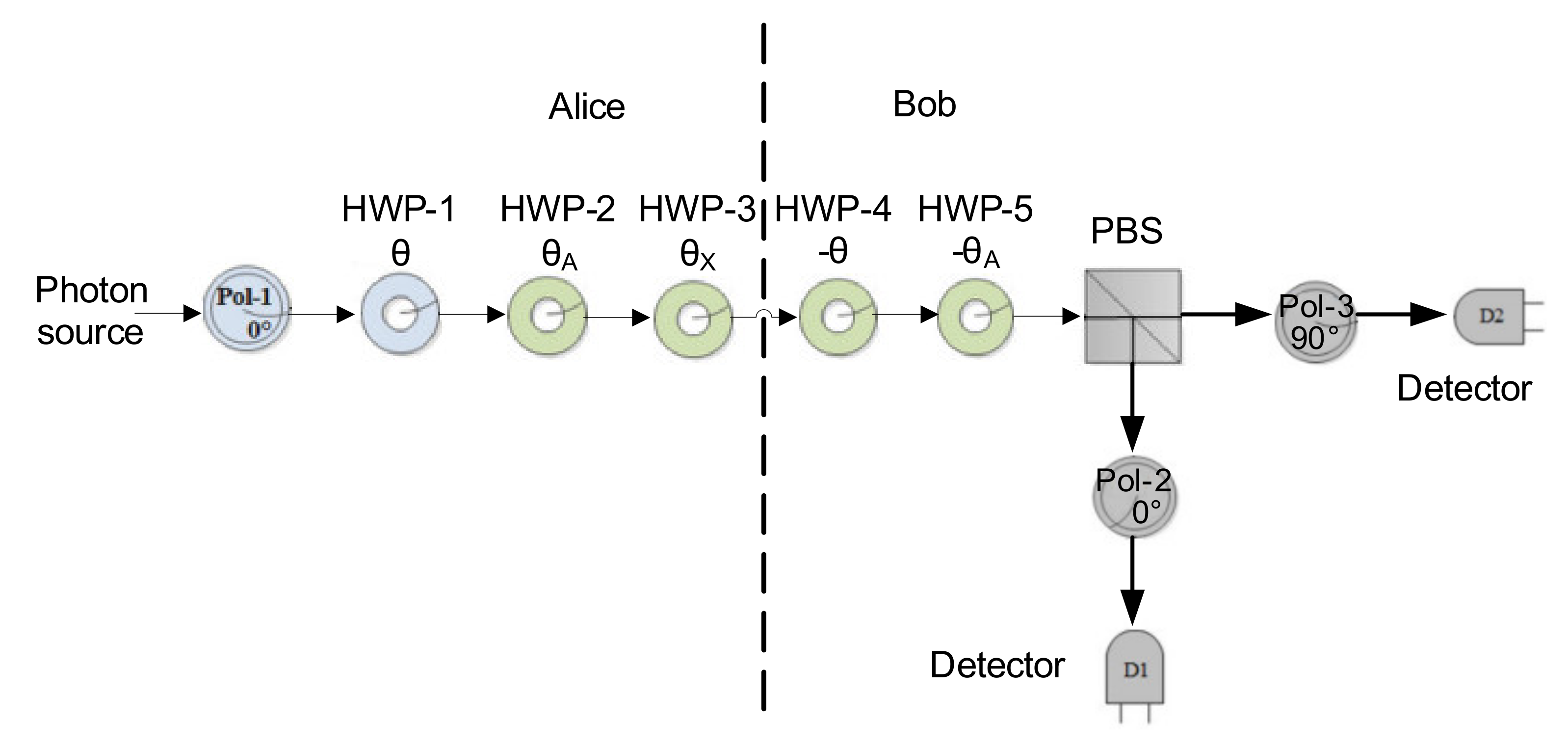
Figure 3 shows the setup of the implementation.
Alice will have three half-wave plates (HWPs) in her possession while Bob will have two HWPs. A linearly polarized laser is used as the photon source in our implementation [
28]. At the beginning of the protocol, Alice generates a state with a 0° linear polarization using a 0° polarizer. The polarization procedure is to encrypt the classical bits using the photons to produce the quantum bit (qubit). After the classical bits are encrypted to the photons, she will apply a transformation using HWP-1 at the angle θ and apply her second HWP-2 at angle
, which results in the superposition state, |
. The superposition states carry the secret message that will be shared between Alice and Bob in quantum manners [
27]. The rotation of HWP operation is represented as
where
It is noted that HWP-1 at the angle θ is the authentication key set from 0° to 45°, coupled with information
to make the protocol more secure. Alice then applies the transformation associated with the encoded bit using HWP-3 that will be set at an angle
0° in the case of bit 0 being sent or
45° if bit 1 is being sent.
where
is the Stokes parameter’s sequence of the input light that is illustrated as
while
is the Stokes parameter’s sequence of the output light
The light polarization angle after passing through the HWP can be measured [
28,
29] by
where “
” is the multiplication operator and
is the norm operator.
Alice will send the optical beam containing the message to Bob, who will first pass it through his first HWP (HWP-4). Then he will remove his transformation using a HWP-5 sets at the angle . Bob will receive a beam polarizer at either 0° or 90° and pass it through a polarization beam splitter. The detectors will detect whether it is bit 0 or bit 1.
A basic description of the proposed protocol is discussed here. First, the message that is translated into the binary code is encrypted into a single particle called a quantum bit or qubit. The quantum bit is then transmitted from Alice to Bob using the proposed protocol as follows.
Suppose that Alice prepares a photon. Alice wants to send the first qubit, |
the qubit is then encrypted to the photons using the first agreed angle from the first procedure,
. Alice prepares photons based on Equation (9) and encrypts it using the rotation of HWP based on Equation (6).
Alice encrypts the
with the authentication key, which is previously shared in the initial authentication procedure,
.
Alice then applies the transformation associated with the encoded bit. In the case of bit 0 is being sent, the angle is set at
0° or
45° if bit 1 is being sent.
Bob receives
and decrypts it by rotating it back with the angle
.
Bob receives
and decrypts it by rotating it back using the angle of authentication key
Bob receives the original message.
5.3. Security Check Procedure
After
is delivered successfully, the process continues with the remaining qubits using the same procedure. Alice and Bob will check the authenticity between them by comparing Alice’s and Bob’s secret rotations using Equation (4).
| Algorithm 1 SSAK protocol |
- 1:
Notation: - 2:
TimeStamp ← calibration using time synchronization/time stamp - 3:
← is the secret polarization angle - 4:
f(Pauli )← is a function bit flip operator using Pauli-X gate - 5:
1. Initialization authentication procedure - 6:
← is the random string message of (0,1) - 7:
← is the rotation of HWP using Equation (6) - 8:
← is the photon associate with - 9:
Alice prepares a photon using Equation (8) - 10:
Alice converts the decimal of into binary and does Pauli-X operation - 11:
← f(Pauli) - 12:
Alice initializes the authentication by sharing secret polarization - 13:
- 14:
TimeStamp=0 - 15:
- 16:
TimeStamp = 2 - 17:
- 18:
TimeStamp = 4 - 19:
if TimeStamp ≠4 then - 20:
detect Eve and terminate communication - 21:
elif - 22:
- 23:
TimeStamp = 6 - 24:
end if - 25:
Bob analyzed the result - 26:
Determine the value of using Equation (12) and the corresponding bit - 27:
← f(Pauli ) - 28:
Generate new - 29:
- 30:
Alice compares and analyses newaccording to her previous calculation, verifies Bob and sends authentication key - 31:
Determine the new value of using Equation (12) and the corresponding bit - 32:
if ≠ then - 33:
detect Eve and terminate communicatione - 34:
elif - 35:
Alice sends authentication key using to Bob - 36:
- 37:
end if - 38:
Bob gets authentication key - 39:
- 40:
2. Message sharing procedure of bit sequence, B - 41:
B ← A bit sequence - 42:
len(B) ← is the length of bit sequence B is set to 8 photons per block - 43:
Alice prepares photons based on Equation (8), encrypts it usingand. - 44:
Notation: - 45:
f(B, , ) ← is the function that returns the updated secret polarization angle and authentication key for every block of photon (8 photons per block) - 46:
for i (,) in enumerate (f(B, , )) do - 47:
for j = 1 in range B do - 48:
Transmission of photon using single-stage - 49:
if i * B + j ≥ len(B) then - 50:
break transmission; - 51:
end if - 52:
end for - 53:
end for - 54:
Alice and Bob checks for authenticity - 55:
ifthen - 56:
Alice and Bob are authenticated - 57:
else - 58:
detect Eve and terminate communication - 59:
end if
|
7. Implementation Issues of the Proposed Protocol
The security of the protocol proposed is based on how hard it is for an eavesdropper to construct the authentication key and secret angle that Alice and Bob exchange. Eve has to find Alice’s secret information using a probability of up to
by intercepting their communications. The ease of implementation is one of the key factors in the design of QSDC. It can be observed that there are no entangled states, which are difficult to implement in the proposed protocol. The performance analysis showed that the proposed protocol is low-cost, and it can be implemented with today’s technology using optical devices, as discussed in
Section 4. As discussed in the literature, the proposed work intends to secure the information against an eavesdropper’s attack. In the real implementation of the QSDC protocol, several practical issues need to be considered other than security issues. The practical issues that will impact the implementation of quantum communication are the noise and error in the quantum channel. Besides, photon loss may occur in the large communication distance due to the features of quantum mechanics [
34]. The channel loss will lead to photon loss, which results in the secret information loss due to the information been encoded into individual photons. In addition, an eavesdropper could hide her presence in the channel noise and take the advantages to gain a certain amount of information [
6]. Thus, a quantum error correction is necessary during transmission via a noisy channel.
8. Conclusions
This work implements a secure mutual authentication to ensure the legitimacy of users without any involvement of the third party. Unlike the most well-known QSDC protocols that rely on a slight classical communication to share the pre-shared authentication key at the onset of communication, the proposed protocol fully utilizes the quantum channel to share the secret angle and authentication key at the initial stage of authentication. Firstly, the proposed scheme is enhanced with ITT implementation by allowing the sender to detect any disturbance by the third party. When quantum particles pass through optical polarization devices at the sender’s site, and an eavesdropper is present in the communication to read the photon, the response by the receiver might induce additional time. Secondly, Pauli-X quantum gate operation is employed where the received qubit is flipped according to the numerical secret rotation angle to increase the difficulty for Eve to steal the information. The proposed protocol can be concluded that public communication or public states are not used to transmit a secret message or verify the parties. The security of the proposed scheme is discussed in the context of eavesdropping attacks during initial authentication and transmission of messages. Security analysis of initial authentication and transmission of messages has shown that the eavesdropper is unable to reveal any information about the authentication key or the transmitted message. That is because Alice only knows the secret angle of polarization and authentication key, and this is successfully shared with Bob through the quantum channel without being exposed to Eve.
The authentication is also prepared before the message is exchanged, and bit-by-bit checks are performed during quantum communication. The security analysis demonstrates that the suggested quantum authentication scheme is secure against most of the well-known attacks. There is no chance Eve could impersonate either Alice or Bob. In the proposed protocol, we only considered two parties involved in the communication. Recently, the authors of [
35] proposed an effective way to share the authentication key among three parties using a single photon in polarization and spatial-mode degree of freedom. Following their work, we will study the authentication parts of three-party on multi-stage using unitary transformation of QSDC in the future. The problem of photon loss in the real implementation of the QSDC protocol has been studied in our work [
14]. Therefore, the implementation of practical QSDC in a realistic environment of high information loss and noise using the proposed protocol should be focused on in our future research.