A Systematic Review of the State of Cyber-Security in Water Systems
Abstract
1. Introduction
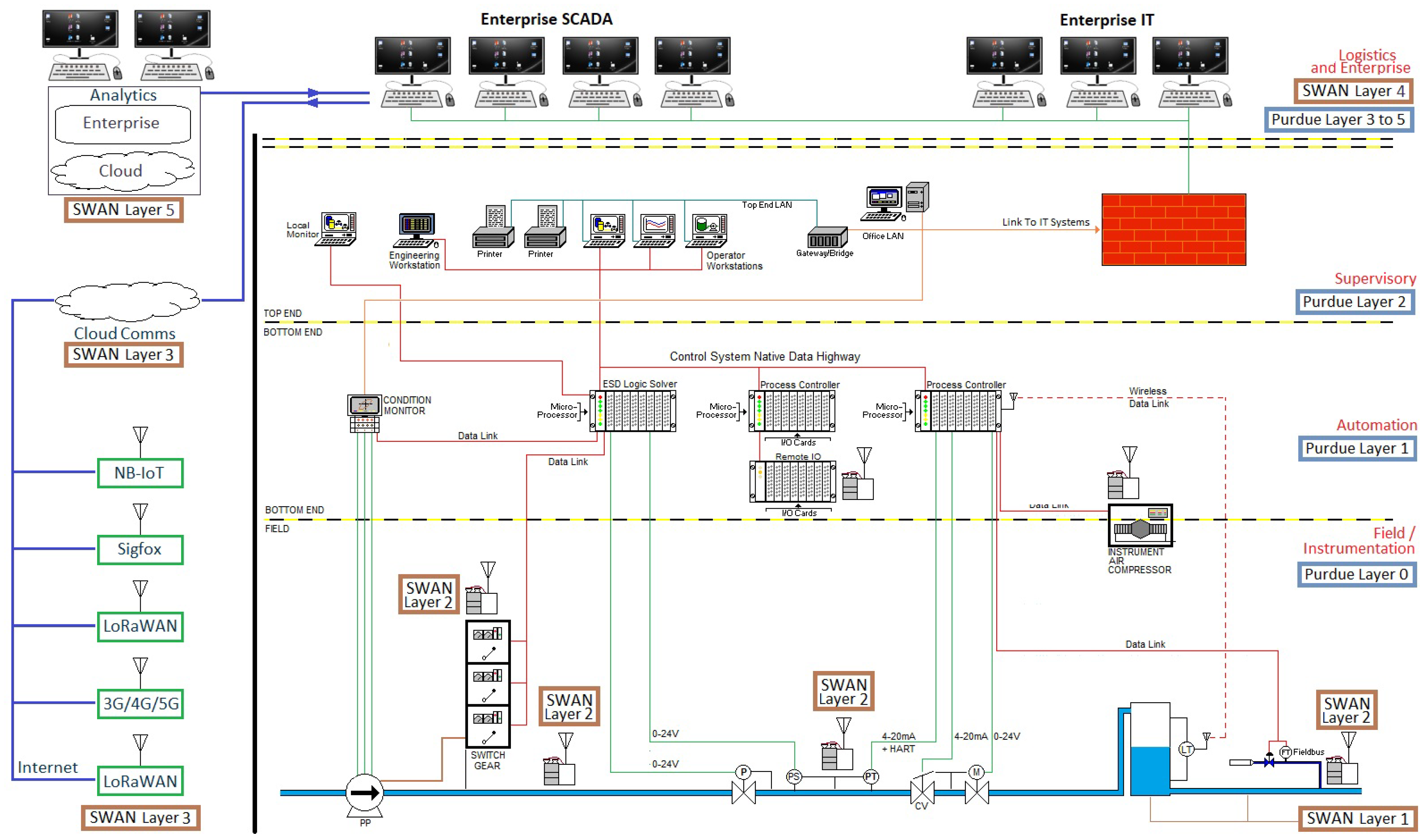
- Level 1: Physical layer is composed of physical devices that provide the distribution and delivery of water services. This includes pipes, pumps, valves, reservoirs and endpoints for delivering water.
- Level 2: Sensing and control layer is composed of equipment and sensors responsible for gathering measurements for monitoring and controlling water delivery and distribution; and remote-controlled actuators to remotely operate water networks.
- Level 3: Collection and communications layer provides the data collection, transmission, and storage between layer 2 and level 4 where the instructions for sensors and actuators are computed. All network protocols used for data transfer are found in this layer.
- Level 4: Data management and display layer is responsible for gathering and managing data from different sources. Supervisory control and data acquisition (SCADA) systems, control systems, visualisation systems and tools such as human-machine interface (HMI), data storage repositories and control systems are found in this layer. This is where decisions taken by upper layers are interpreted into control and other commands such as settings for devices at lower layers.
- Level 5: The data fusion and analysis layer is where raw data is processed into information and where the “smart” emerging technologies are deployed. These include modelling and optimisation systems, network infrastructure monitoring, and other supporting and decision support systems for managing water networks.
2. Cyber–Physical Systems
2.1. Securing Cyber–Physical Systems
2.2. Attacks against Cyber–Physical Systems
2.3. Security Measures for Cyber–Physical Systems
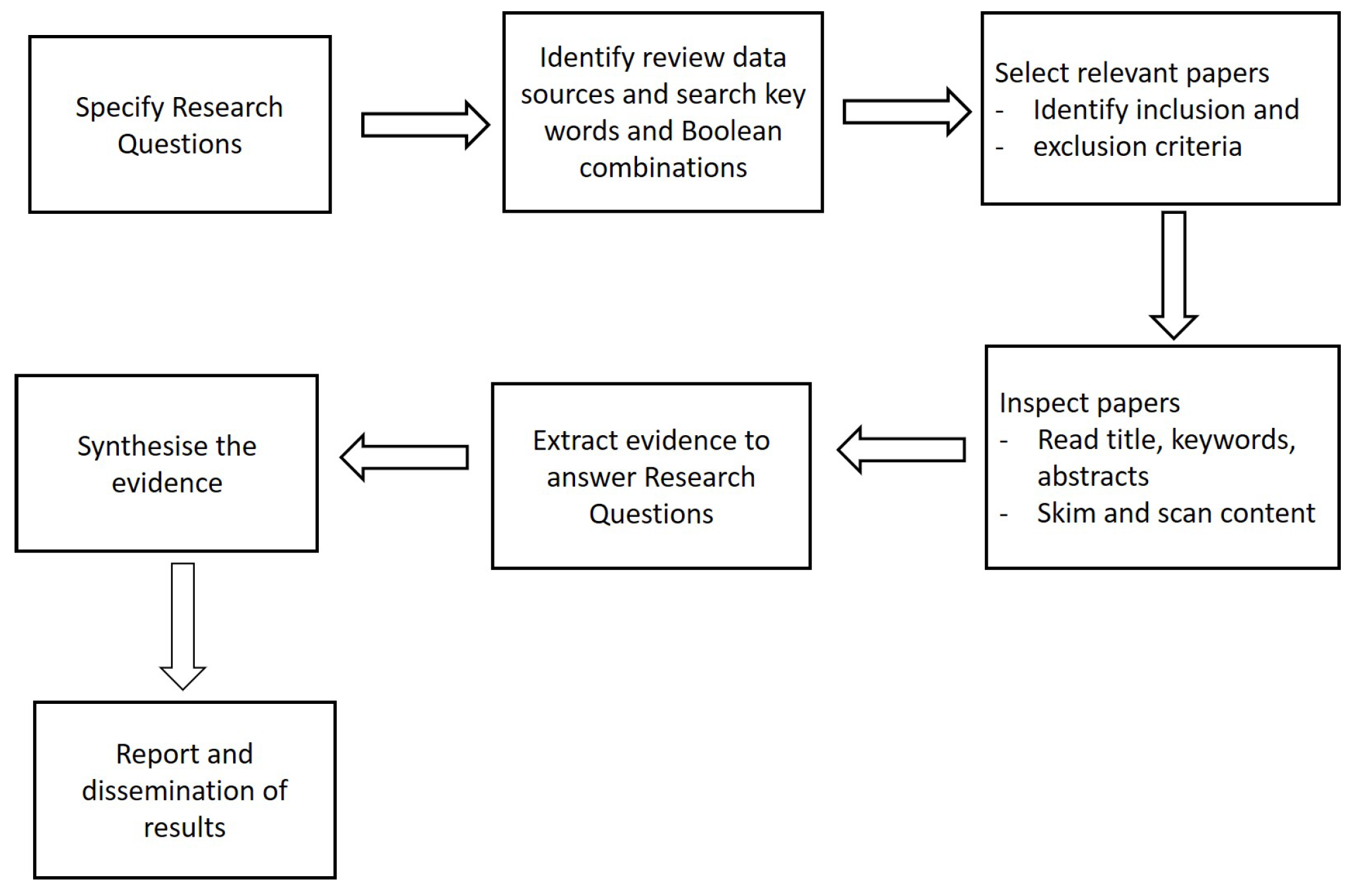
3. Methodology for Systematic Review
3.1. Research Questions
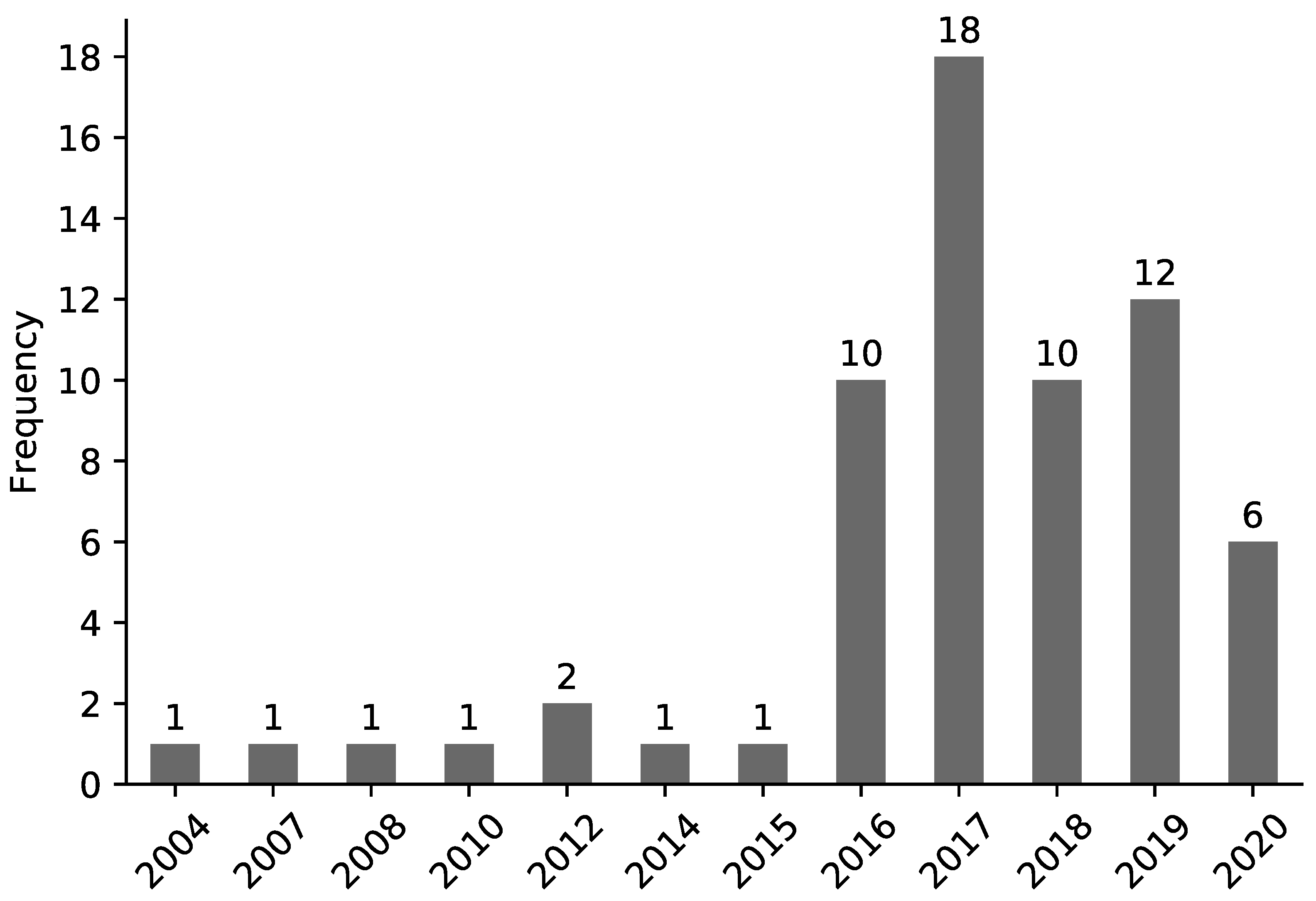
- RQ1 How did the number of publications change over the years? To understand the publication trends over the years, and to understand if the topic is gaining more research focus with moves towards IIoT and Industry 4.0. Answering this question might also enable us to see any trends that might have motivated more work from the research community.
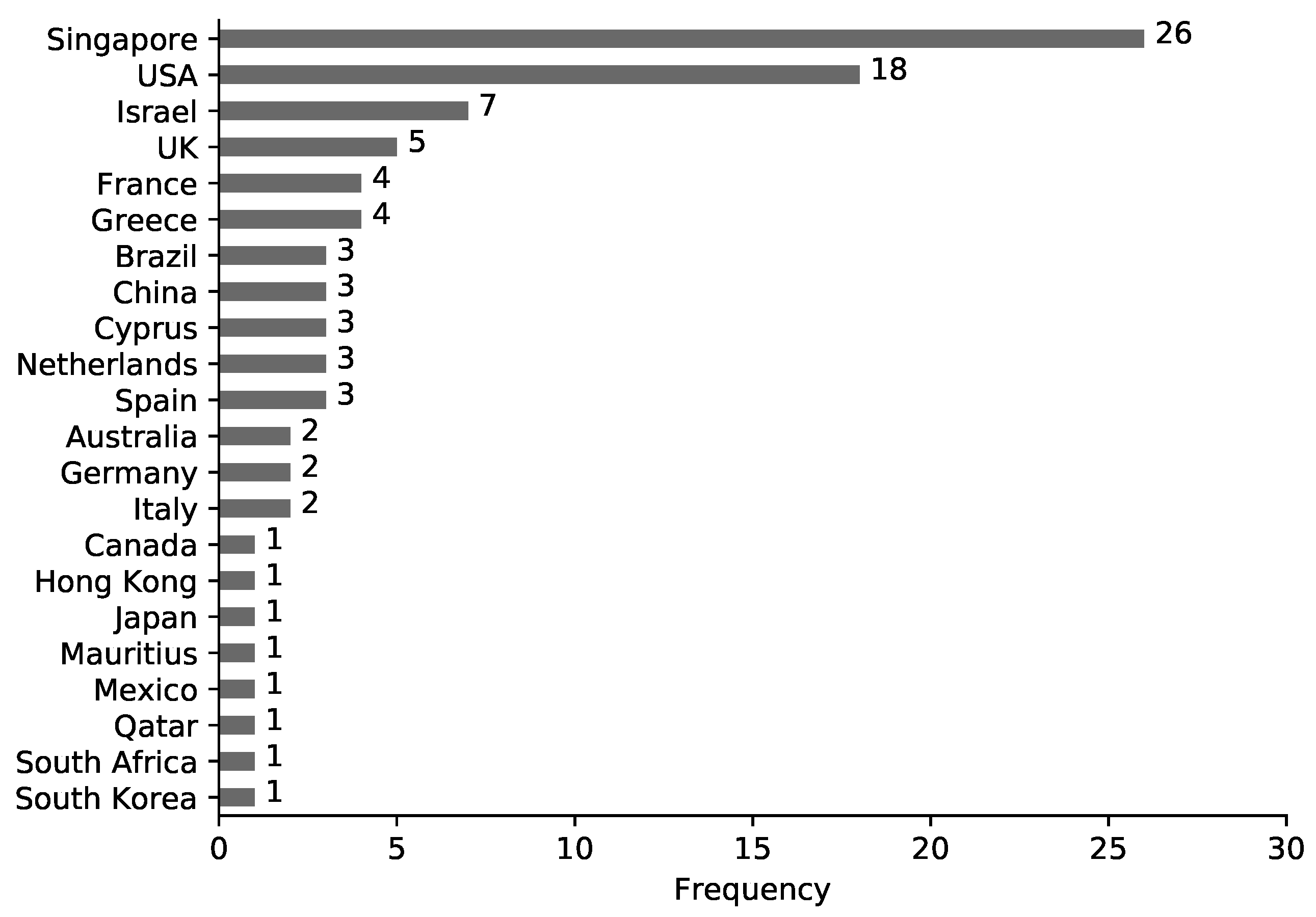
- RQ2 What is the geographic distribution of these studies? To understand by whom and from where these studies are being conducted. Answering RQ2 will help to determine countries investing the least and most in research in these areas, and why this could be the case. Security of national infrastructure services such as water often require a joint effort from academia, governmental bodies and industry.
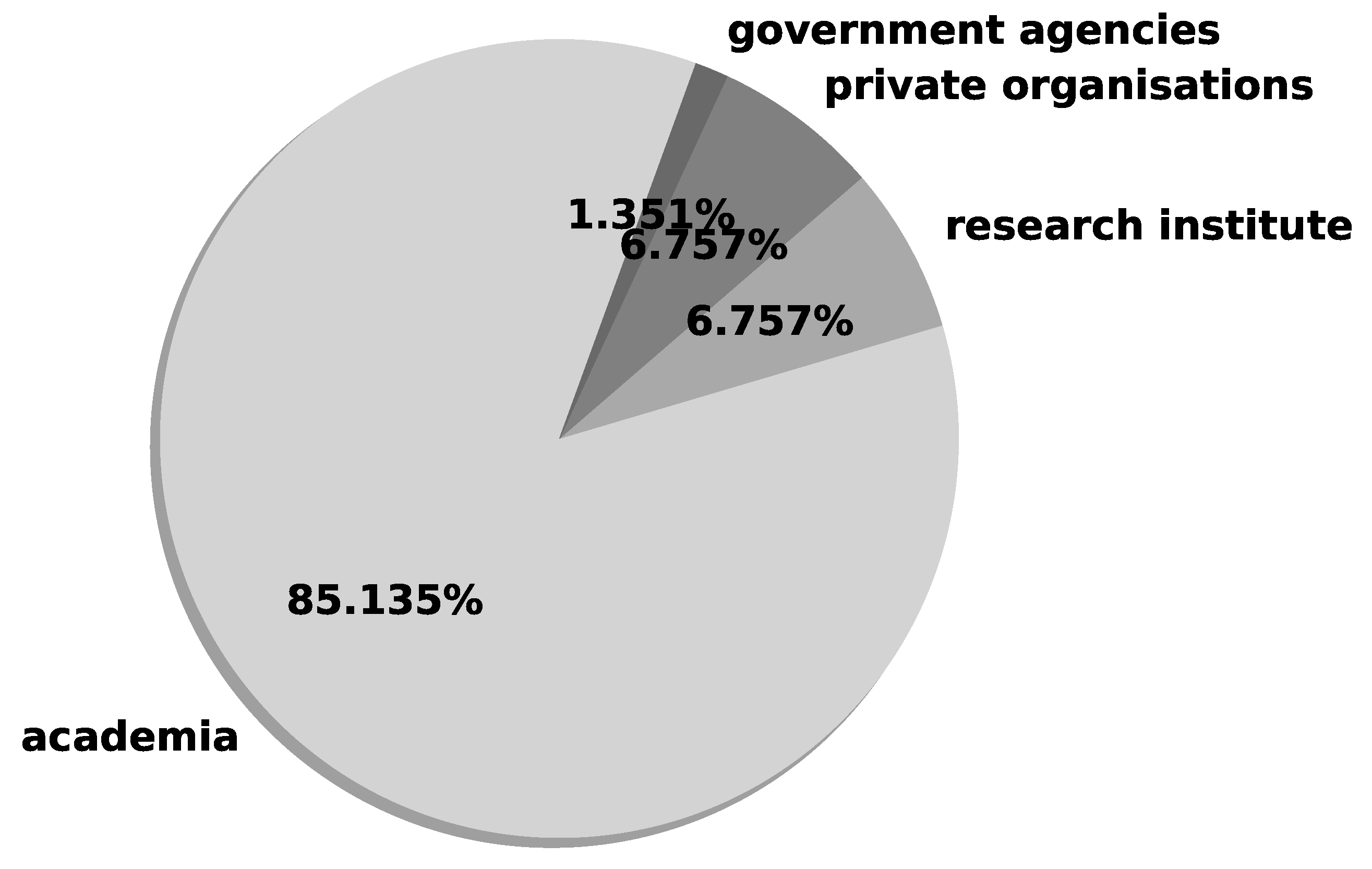
- RQ3 What is the distribution of academic, governmental and industry studies? To identify the level of involvement, and the support of government and industry in research studies. Answering this question will enable assessment of whether relevant government and industry bodies are participating in these studies. Their involvement is crucial for these studies, as they are essentially the clients that will deploy and implement security solutions.
- RQ4 What are the target venues for publishing these studies? To identify publication venues targeted by these studies. Answering this question will help to identify the top target venues for publication, and gain some understanding of the maturity and quality of publications by analysing the rating of the journals and conferences.
- RQ5 Which security aspects are covered in these studies? To understand the security themes of interest, proposed solutions and focus of these studies. Answering this question will inform the security problems that are being solved.
- RQ6 Can one classify security aspects in RQ5 further? To see if there are popular areas of research that can be classified further. If there are popular research aspects, answering this question could help to compare different approaches.
3.2. Identification of Sources and Search Term
3.3. Criteria for Selection of Papers
- Must address cyber–physical systems in water.
- Must have a technical content and address cyber-security.
- Must be peer-reviewed and must have appeared in an international journal, conference or workshop.
3.4. Paper Inspection
3.5. Extraction of Appropriate Information
4. Analysis of Results
4.1. Publication Trends
4.2. Classification of Studies
4.2.1. Testbeds, Simulation and Datasets
4.2.2. Cyber-Attack Models
4.2.3. Cyber-Attack Detection Models
4.3. Model-Based Security Analysis
4.4. Risk and Resilience Management
4.5. Security Frameworks
4.6. Security Benchmarks and Case Studies
4.7. Security Monitoring Capabilities
5. Open Issues and Future Research Areas
5.1. Building Testbeds for Water Systems
5.2. Threat and Attack Models
5.3. Attack Detection Models
5.4. Collaboration with Industry
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- WWAP (United Nations World Water Assessment Programme)/UN-Water the United Nations World Water Development Report 2018: Nature-based Solution for Water. Paris, UNESCO. 2018. Available online: www.unwater.org/publications/world-water-development-report-2018/ (accessed on 6 November 2020).
- Bank, W. The World Bank and the International Water Association to Establish a Partnership to Reduce Water Losses. 2016. Available online: https://www.worldbank.org/en/news/press-release/2016/09/01/the-world-bank-and-the-international-water-association-to-establish-a-partnership-to-reduce-water-losses (accessed on 6 November 2020).
- Discoverwater. Leaking Pipes. 2020. Available online: https://discoverwater.co.uk/leaking-pipes (accessed on 14 November 2020).
- Li, J.; Yang, X.; Sitzenfrei, R. Rethinking the Framework of Smart Water System: A Review. Water 2020, 12, 412. [Google Scholar] [CrossRef]
- Giudicianni, C.; Herrera, M.; Nardo, A.D.; Adeyeye, K.; Ramos, H.M. Overview of Energy Management and Leakage Control Systems for Smart Water Grids and Digital Water. Modelling 2020, 1, 134–155. [Google Scholar] [CrossRef]
- Adedeji, K.B.; Hamam, Y. Cyber-Physical Systems for Water Supply Network Management: Basics, Challenges, and Roadmap. Sustainability 2020, 12, 9555. [Google Scholar] [CrossRef]
- Ofwat. PR19 Draft Determinations: UK Government Priorities 2019 Price Review Draft Determinations; Technical Report; Ofwat: Birmingham, UK, 2019. [Google Scholar]
- Ofwat. Time to Act, Together: Ofwat’s Strategy; Technical Report; Ofwat: Birmingham, UK, 2019. [Google Scholar]
- Schickhuber, G.; McCarthy, O. Distributed fieldbus and control network systems. Comput. Control Eng. J. 1997, 8, 21–32. [Google Scholar] [CrossRef]
- SWAN Forum. A Layered View of Smart Water Networks. Available online: https://www.swan-forum.com/swan-tools/a-layered-view (accessed on 1 November 2020).
- Falliere, N.; Murchu, L.O.; Chien, E. W32.Stuxnet Dossier (Version 1.4); White Paper, Symantec Security Response; Symantec: Mountain View, CA, USA, 2011. [Google Scholar]
- Symantec. W32.Duqu: The Precursor to the Next Stuxnet (Version 1.4); White Paper, Symantec Security Response; Symantec: Mountain View, CA, USA, 2011. [Google Scholar]
- Kaspersky. BlackEnergy APT Attacks in Ukraine. Available online: https://www.kaspersky.co.uk/resource-center/threats/blackenergy (accessed on 30 November 2020).
- Havex Hunts For ICS/SCADA Systems. 2014. Available online: https://www.f-secure.com/weblog/archives/00002718.html (accessed on 30 October 2020).
- Gleick, P.H. Water and terrorism. Water Policy 2006, 8, 481–503. [Google Scholar] [CrossRef]
- Interpol. The Protection of Critical Infrastructure against Terrorist Attacks: Compendium of Good Practices. Compiled by CTED and UNOCT in 2018. 2018. Available online: https://www.un.org/sc/ctc/wp-content/uploads/2019/01/Compendium_of_Good_Practices_Compressed.pdf (accessed on 1 August 2020).
- Hassanzadeh, A.; Rasekh, A.; Galelli, S.; Aghashahi, M.; Taormina, R.; Ostfeld, A.; Banks, M.K. A Review of Cybersecurity Incidents in the Water Sector. J. Environ. Eng. 2020, 146, 03120003. [Google Scholar] [CrossRef]
- Clark, R.M.; Panguluri, S.; Nelson, T.D.; Wyman, R.P. Protecting Drinking Water Utilities from Cyberthreats. J. AWWA 2017, 109, 50–58. [Google Scholar] [CrossRef]
- ZDNet. Israel Government Tells Water Treatment Companies to Change Passwords. 2020. Available online: https://www.zdnet.com/article/israel-says-hackers-are-targeting-its-water-supply-and-treatment-utilities/ (accessed on 6 November 2020).
- The Coloradoan. Cyberattacker Demands Ransom from Northern Colorado Utility. 2019. Available online: https://eu.coloradoan.com/story/money/2019/03/14/cyberattacker-demands-ransom-colorado-utility/3148951002/ (accessed on 11 September 2020).
- Eweek. Water Utility in Europe Hit by Cryptocurrency Malware Mining Attack. 2018. Available online: https://www.eweek.com/security/water-utility-in-europe-hit-by-cryptocurrency-malware-mining-attack (accessed on 11 September 2020).
- The Registry. Water Treatment Plant Hacked, Chemical Mix Changed for Tap Supplies. 2016. Available online: https://www.theregister.com/2016/03/24/water_utility_hacked (accessed on 14 November 2020).
- The New York Times. A Dam, Small and Unsung, Is Caught Up in an Iranian Hacking Case. 2016. Available online: https://www.nytimes.com/2016/03/26/nyregion/rye-brook-dam-caught-in-computer-hacking-case.html (accessed on 11 September 2020).
- The United States Department of Justice. United States District Court Southern District of New York: Sealed Indictment. 2016. Available online: https://www.justice.gov/opa/file/834996/download (accessed on 31 December 2020).
- Govtech. Report: Hacking Lands Florida Wastewater Official in Hot Water. 2012. Available online: https://www.govtech.com/public-safety/Report-Hacking-Lands-Florida-Wastewater-Official-in-Hot-Water.html (accessed on 31 December 2020).
- Computer World. Insider charged with hacking California canal system. 2007. Available online: https://www.computerworld.com/article/2540235/insider-charged-with-hacking-california-canal-system.html (accessed on 10 October 2020).
- TechRepublic. Pennsylvania Water System Hack Demonstrates Lax Security. 2006. Available online: https://www.techrepublic.com/blog/it-security/pennsylvania-water-system-hack-demonstrates-lax-security/ (accessed on 11 September 2020).
- The MITRE Corporation. Malicious Control System Cyber Security Attack Case Study–Maroochy Water Services, Australia. 2008. Available online: http://www.mitre.org/sites/default/files/pdf/08_1145.pdf (accessed on 11 September 2020).
- Jill, J.S.; Miller, M. Lessons Learned from the Maroochy Water Breach. In Critical Infrastructure Protection; Goetz, E., Shenoi, S., Eds.; Springer: New York, NY, USA, 2008; Volume 253, pp. 73–82. [Google Scholar]
- Rid, T.; Buchanan, B. Attributing Cyber Attacks. J. Strateg. Stud. 2015, 38, 4–37. [Google Scholar] [CrossRef]
- Rogers, M.K. A two-dimensional circumplex approach to the development of a hacker taxonomy. Digit. Investig. 2006, 3, 97–102. [Google Scholar] [CrossRef]
- Green, B.; Krotofil, M.; Abbasi, A. On the Significance of Process Comprehension for Conducting Targeted ICS Attacks. In Proceedings of the 2017 Workshop on Cyber-Physical Systems Security and PrivaCy, CPS ’17, Dallas, TX, USA, 3 November 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 57–67. [Google Scholar] [CrossRef]
- Dragos. Cyber Threat Perspective Manufacturing Sector. 2020. Available online: https://www.dragos.com/resource/manufacturing-threat-perspective/ (accessed on 5 December 2020).
- Gill, H. From Vision to Reality: Cyber-Physical Systems. In Proceedings of the HCSS National Workshop on New Research Directions for High Confidence Transportation CPS: Automotive, Aviation, and Rail, Washington, DC, USA, 18–20 November 2008. [Google Scholar]
- Lee, E.A. The Past, Present and Future of Cyber-Physical Systems: A Focus on Models. Sensors 2015, 15, 4837–4869. [Google Scholar] [CrossRef] [PubMed]
- Stouffer, K.; Zimmerman, S.; Timothy, T.C.; Lubell, J.; Cichonski, J.; McCarthy, J. NISTIR 8183: Cybersecurity Framework Manufacturing Profile; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2017. [Google Scholar]
- Hu, V.; Ferraiolo, D.; Kuhn, R. Assessment of Access Control Systems; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2006. [Google Scholar]
- Initiative, J.T.F.T. Security and Privacy Controls for Federal Information Systems and Organizations, NIST Special Publication 800-53 Revision 4; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2015. [Google Scholar]
- Ross, R.; McEvilley, M.; Oren, C.J. Systems Security Engineering Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems, NIST Special Publication 800-160; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2016. [Google Scholar]
- Stouffer, K.; Lightman, S.; Pillitteri, V.; Abrams, M.; Hahn, A. NIST Special Publication 800-82: Guide to Industrial Control Systems (ICS) Security; Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2014. [Google Scholar]
- Hahn, A.; Thomas, R.K.; Lozano, I.; Cardenas, A. A multi-layered and kill-chain based security analysis framework for cyber-physical systems. Int. J. Crit. Infrastruct. Prot. 2015, 11, 39–50. [Google Scholar] [CrossRef]
- Moher, D.; Liberati, A.; Tetzlaff, J.; Altman, D.; The PRISMA Group. Preferred Reporting Items for Systematic Reviews and Meta-Analyses: The PRISMA Statement. PLoS Med. 2009, 6, 1–6. [Google Scholar] [CrossRef] [PubMed]
- Mathur, A.P.; Tippenhauer, N.O. SWaT: A water treatment testbed for research and training on ICS security. In Proceedings of the 2016 International Workshop on Cyber-physical Systems for Smart Water Networks (CySWater), Vienna, Austria, 11 April 2016; pp. 31–36. [Google Scholar]
- Ahmed, C.M.; Palleti, V.R.; Mathur, A.P. WADI: A Water Distribution Testbed for Research in the Design of Secure Cyber Physical Systems. In Proceedings of the 3rd International Workshop on Cyber-Physical Systems for Smart Water Networks, Pittsburgh, PA, USA, 18–21 April 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 25–28. [Google Scholar] [CrossRef]
- ITrust. Dataset Characteristics: SWaT, WADI and BATADAL. Available online: https://itrust.sutd.edu.sg/itrust-labs_datasets/dataset_info/ (accessed on 8 November 2020).
- iTrust—Singapore University of Technology and Design (SUTD). Testbeds. Available online: https://itrust.sutd.edu.sg/testbeds (accessed on 30 November 2020).
- Taormina, R.; Galelli, S.; Tippenhauer, N.O.; Salomons, E.; Ostfeld, A.; Eliades, D.G.; Aghashahi, M.; Sundararajan, R.; Pourahmadi, M.; Banks, M.K.; et al. Battle of the Attack Detection Algorithms: Disclosing Cyber Attacks on Water Distribution Networks. J. Water Resour. Plan. Manag. 2018, 144, 04018048. [Google Scholar] [CrossRef]
- Facies Project. Available online: http://facies.dia.uniroma3.it/ (accessed on 30 November 2020).
- The STOP-IT Project. Available online: https://stop-it-project.eu/ (accessed on 30 November 2020).
- Goh, J.; Adepu, S.; Junejo, K.N.; Mathur, A. A Dataset to Support Research in the Design of Secure Water Treatment Systems. In Proceedings of the International Conference on Critical Information Infrastructures Security, Paris, France, 10–12 October 2017; Havarneanu, G., Setola, R., Nassopoulos, H., Wolthusen, S., Eds.; Springer International Publishing: Cham, Switzerland, 2017; pp. 88–99. [Google Scholar]
- Kartakis, S.; Abraham, E.; McCann, J.A. WaterBox: A Testbed for Monitoring and Controlling Smart Water Networks. In Proceedings of the 1st ACM International Workshop on Cyber-Physical Systems for Smart Water Networks, CySWater’15, Seattle, WA, USA, 14–16 April 2015; Association for Computing Machinery: New York, NY, USA, 2015. [Google Scholar] [CrossRef]
- Taormina, R.; Galelli, S.; Tippenhauer, N.; Ostfeld, A.; Salomons, E. Assessing the Effect of Cyber-Physical Attacks on Water Distribution Systems. In Proceedings of the World Environmental and Water Resources Congress 2016, Palm Beach, FL, USA, 22–26 May 2016; pp. 436–442. [Google Scholar] [CrossRef]
- Taormina, R.; Galelli, S.; Douglas, H.; Tippenhauer, N.; Salomons, E.; Ostfeld, A. A toolbox for assessing the impacts of cyber-physical attacks on water distribution systems. Environ. Model. Softw. 2019, 112, 46–51. [Google Scholar] [CrossRef]
- Etchevés Miciolino, E.; Setola, R.; Bernieri, G.; Panzieri, S.; Pascucci, F.; Polycarpou, M.M. Fault Diagnosis and Network Anomaly Detection in Water Infrastructures. IEEE Des. Test 2017, 34, 44–51. [Google Scholar] [CrossRef]
- Nikolopoulos, D.; Makropoulos, C.; Kalogeras, D.; Monokrousou, K.; Tsoukalas, I. Developing a Stress-Testing Platform for Cyber-Physical Water Infrastructure. In Proceedings of the 2018 International Workshop on Cyber-physical Systems for Smart Water Networks (CySWater), Porto, Portugal, 10–13 April 2018; pp. 9–11. [Google Scholar] [CrossRef]
- Nikolopoulos, D.; Moraitis, G.; Bouziotas, D.; Lykou, A.; Karavokiros, G.; Makropoulos, C. RISKNOUGHT: A cyber-physical stress-testing platform for water distribution networks. In Proceedings of the 11th World Congress on Water Resources and Environment (EWRA 2019) Managing Water Resources for a Sustainable Future, Madrid, Spain, 25–29 June 2019. [Google Scholar]
- Nikolopoulos, D.; Moraitis, G.; Bouziotas, D.; Lykou, A.; Karavokiros, G.; Makropoulos, C. Cyber-Physical Stress-Testing Platform for Water Distribution Networks. J. Environ. Eng. 2020, 146, 04020061. [Google Scholar] [CrossRef]
- Teixeira, M.; Salman, T.; Zolanvari, M.; Jain, R.; Meskin, N.; Samaka, M. SCADA System Testbed for Cybersecurity Research Using Machine Learning Approach. Future Internet 2018, 10, 76. [Google Scholar] [CrossRef]
- EPANET Application for Modeling Drinking Water Distribution Systems. United States Environmental Protection Agency. Available online: https://www.epa.gov/water-research/epanet (accessed on 31 December 2020).
- Amin, S.; Litrico, X.; Sastry, S.; Bayen, A.M. Cyber Security of Water SCADA Systems—Part I: Analysis and Experimentation of Stealthy Deception Attacks. IEEE Trans. Control Syst. Technol. 2013, 21, 1963–1970. [Google Scholar] [CrossRef]
- Adepu, S.; Mathur, A. An Investigation into the Response of a Water Treatment System to Cyber Attacks. In Proceedings of the 2016 IEEE 17th International Symposium on High Assurance Systems Engineering (HASE), Orlando, FL, USA, 7–9 January 2016; pp. 141–148. [Google Scholar]
- Adepu, S.; Prakash, J.; Mathur, A. WaterJam: An Experimental Case Study of Jamming Attacks on a Water Treatment System. In Proceedings of the 2017 IEEE International Conference on Software Quality, Reliability and Security Companion (QRS-C), Prague, Czech Republic, 25–29 July 2017; pp. 341–347. [Google Scholar]
- Tomić, I.; Breza, M.J.; Jackson, G.; Bhatia, L.; McCann, J.A. Design and Evaluation of Jamming Resilient Cyber-Physical Systems. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 687–694. [Google Scholar]
- Robles-Durazno, A.; Moradpoor, N.; McWhinnie, J.; Russell, G.; Maneru-Marin, I. Implementation and Detection of Novel Attacks to the PLC Memory of a Clean Water Supply System; Botto-Tobar, M., Pizarro, G., Zúñiga-Prieto, M., D’Armas, M., Zúñiga Sánchez, M., Eds.; Technology Trends; Springer International Publishing: Cham, Switzerland, 2019; pp. 91–103. [Google Scholar]
- Amin, S.; Litrico, X.; Sastry, S.S.; Bayen, A.M. Stealthy Deception Attacks on Water SCADA Systems. In Proceedings of the 13th ACM International Conference on Hybrid Systems: Computation and Control, HSCC ’10, Stockholm, Sweden, 12–15 April 2010; Association for Computing Machinery: New York, NY, USA, 2010; pp. 161–170. [Google Scholar] [CrossRef]
- Taormina, R.; Galelli, S.; Tippenhauer, N.O.; Salomons, E.; Ostfeld, A. Characterizing Cyber-Physical Attacks on Water Distribution Systems. J. Water Resour. Plan. Manag. 2017, 143, 04017009. [Google Scholar] [CrossRef]
- Erba, A.; Taormina, R.; Galelli, S.; Pogliani, M.; Carminati, M.; Zanero, S.; Tippenhauer, N.O. Constrained Concealment Attacks against Reconstruction-Based Anomaly Detectors in Industrial Control Systems. In Proceedings of the Annual Computer Security Applications Conference, ACSAC ’20, Austin, TX, USA, 7–10 December 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 480–495. [Google Scholar] [CrossRef]
- Mitchell, R.; Chen, I.R. A Survey of Intrusion Detection Techniques for Cyber-Physical Systems. ACM Comput. Surv. 2014, 46. [Google Scholar] [CrossRef]
- Amin, S.; Litrico, X.; Sastry, S.S.; Bayen, A.M. Cyber Security of Water SCADA Systems—Part II: Attack Detection Using Enhanced Hydrodynamic Models. IEEE Trans. Control Syst. Technol. 2013, 21, 1679–1693. [Google Scholar] [CrossRef]
- Adepu, S.; Mathur, A. Using Process Invariants to Detect Cyber Attacks on a Water Treatment System. In Proceedings of the ICT Systems Security and Privacy Protection, Ghent, Belgium, 30 May–1 June 2016; Hoepman, J.H., Katzenbeisser, S., Eds.; Springer International Publishing: Cham, Switzerland, 2016; pp. 91–104. [Google Scholar]
- Adepu, S.; Mathur, A. Distributed Detection of Single-Stage Multipoint Cyber Attacks in a Water Treatment Plant. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, ASIA CCS ’16, Xi’an, China, 30 May 2016; Association for Computing Machinery: New York, NY, USA, 2016; pp. 449–460. [Google Scholar] [CrossRef]
- Adepu, S.; Mathur, A. From Design to Invariants: Detecting Attacks on Cyber Physical Systems. In Proceedings of the 2017 IEEE International Conference on Software Quality, Reliability and Security Companion (QRS-C), Prague, Czech Republic, 17 July 2017; pp. 533–540. [Google Scholar]
- Adepu, S.; Mathur, A. Distributed Attack Detection in a Water Treatment Plant: Method and Case Study. IEEE Trans. Dependable Secur. Comput. 2018. [Google Scholar] [CrossRef]
- Cárdenas, A.A.; Amin, S.; Lin, Z.S.; Huang, Y.L.; Huang, C.Y.; Sastry, S. Attacks against Process Control Systems: Risk Assessment, Detection, and Response. In Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security, ASIACCS ’11, Hong Kong, China, March, 20–21 March 2011; Association for Computing Machinery: New York, NY, USA, 2011; pp. 355–366. [Google Scholar] [CrossRef]
- Yoong, C.H.; Heng, J. Framework for Continuous System Security Protection in SWaT. In Proceedings of the 2019 3rd International Symposium on Computer Science and Intelligent Control, ISCSIC 2019, Amsterdam, The Netherlands, 25–27 September 2019; Association for Computing Machinery: New York, NY, USA, 2019. [Google Scholar] [CrossRef]
- Zohrevand, Z.; Glasser, U.; Shahir, H.; Tayebi, M.A.; Costanzo, R. Hidden Markov based anomaly detection for water supply systems. In Proceedings of the 2016 IEEE International Conference on Big Data (Big Data), Washington, DC, USA, 5–8 December 2016; IEEE Computer Society: Los Alamitos, CA, USA, 2016; pp. 1551–1560. [Google Scholar] [CrossRef]
- Ahmed, C.M.; Murguia, C.; Ruths, J. Model-Based Attack Detection Scheme for Smart Water Distribution Networks. In Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security, ASIA CCS ’17, New York, NY, USA, 2–6 April 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 101–113. [Google Scholar] [CrossRef]
- Moazeni, F.; Khazaei, J. MINLP Modeling for Detection of SCADA Cyberattacks in Water Distribution Systems. In Proceedings of the World Environmental and Water Resources Congress 2020, Henderson, NV, USA, 17–21 May 2020; pp. 340–350. [Google Scholar] [CrossRef]
- Inoue, J.; Yamagata, Y.; Chen, Y.; Poskitt, C.M.; Sun, J. Anomaly Detection for a Water Treatment System Using Unsupervised Machine Learning. In Proceedings of the 2017 IEEE International Conference on Data Mining Workshops (ICDMW), Atlantic City, NY, USA, 14–17 November 2017; pp. 1058–1065. [Google Scholar]
- Hindy, H.; Brosset, D.; Bayne, E.; Seeam, A.; Bellekens, X. Improving SIEM for Critical SCADA Water Infrastructures Using Machine Learning; Katsikas, S.K., Cuppens, F., Cuppens, N., Lambrinoudakis, C., Antón, A., Gritzalis, S., Mylopoulos, J., Kalloniatis, C., Eds.; Computer Security; Springer International Publishing: Cham, Switzerland, 2019; pp. 3–19. [Google Scholar]
- Taormina, R.; Galelli, S. Real-Time Detection of Cyber-Physical Attacks on Water Distribution Systems Using Deep Learning. In Proceedings of the World Environmental and Water Resources Congress 2017, Sacramento, CA, USA, 21–25 May 2017; pp. 469–479. [Google Scholar] [CrossRef]
- Taormina, R.; Galelli, S. Deep-Learning Approach to the Detection and Localization of Cyber-Physical Attacks on Water Distribution Systems. J. Water Resour. Plan. Manag. 2018, 144, 04018065. [Google Scholar] [CrossRef]
- Abokifa, A.A.; Haddad, K.; Lo, C.S.; Biswas, P. Detection of Cyber Physical Attacks on Water Distribution Systems via Principal Component Analysis and Artificial Neural Networks. In Proceedings of the World Environmental and Water Resources Congress 2017, Sacramento, CA, USA, 21–25 May 2017; pp. 676–691. [Google Scholar] [CrossRef]
- Abokifa, A.A.; Haddad, K.; Lo, C.; Biswas, P. Real-Time Identification of Cyber-Physical Attacks on Water Distribution Systems via Machine Learning Based Anomaly Detection Techniques. J. Water Resour. Plan. Manag. 2019, 145, 04018089. [Google Scholar] [CrossRef]
- Giacomoni, M.; Gatsis, N.; Taha, A. Identification of Cyber Attacks on Water Distribution Systems by Unveiling Low-Dimensionality in the Sensory Data. In Proceedings of the World Environmental and Water Resources Congress 2017, Sacramento, CA, USA, 21–25 May 2017; pp. 660–675. [Google Scholar] [CrossRef]
- Pasha, M.F.K.; Kc, B.; Somasundaram, S.L. An Approach to Detect the Cyber-Physical Attack on Water Distribution System. In Proceedings of the World Environmental and Water Resources Congress 2017, Sacramento, CA, USA, 21–25 May 2017; pp. 703–711. [Google Scholar] [CrossRef]
- Brentan, B.M.; Campbell, E.; Lima, G.; Manzi, D.; Ayala-Cabrera, D.; Herrera, M.; Montalvo, I.; Izquierdo, J.; Luvizotto, E. On-Line Cyber Attack Detection in Water Networks through State Forecasting and Control by Pattern Recognition. In Proceedings of the World Environmental and Water Resources Congress 2017, Sacramento, CA, USA, 21–25 May 2017; pp. 583–592. [Google Scholar] [CrossRef]
- Chandy, S.E.; Rasekh, A.; Barker, Z.A.; Campbell, B.; Shafiee, M.E. Detection of Cyber-Attacks to Water Systems through Machine-Learning-Based Anomaly Detection in SCADA Data. In Proceedings of the World Environmental and Water Resources Congress 2017, Sacramento, CA, USA, 21–25 May 2017; pp. 611–616. [Google Scholar] [CrossRef]
- Housh, M.; Ohar, Z. Model Based Approach for Cyber-Physical Attacks Detection in Water Distribution Systems. In Proceedings of the World Environmental and Water Resources Congress 2017, Sacramento, CA, USA, 21–25 May 2017; pp. 727–736. [Google Scholar] [CrossRef]
- Housh, M.; Ohar, Z. Model-based approach for cyber-physical attack detection in water distribution systems. Water Res. 2018, 139, 132–143. [Google Scholar] [CrossRef] [PubMed]
- Aghashahi, M.; Sundararajan, R.; Pourahmadi, M.; Banks, M.K. Water Distribution Systems Analysis Symposium: Battle of the Attack Detection Algorithms (BATADAL). In Proceedings of the World Environmental and Water Resources Congress 2017, Sacramento, CA, USA, 21–25 May 2017; pp. 101–108. [Google Scholar] [CrossRef]
- Quiñones-Grueiro, M.; Prieto-Moreno, A.; Verde, C.; Llanes-Santiago, O. Decision Support System for Cyber Attack Diagnosis in Smart Water Networks. IFAC-PapersOnLine 2019, 51, 329–334, Part of special issue: 2nd IFAC Conference on Cyber-Physical and Human Systems CPHS 2018, Miami, Florida. [Google Scholar] [CrossRef]
- Ramotsoela, D.; Hancke, G.; Abu-Mahfouz, A. Attack detection in water distribution systems using machine learning. Hum. Centric Comput. Inf. Sci. 2019, 9, 13. [Google Scholar] [CrossRef]
- Kadosh, N.; Frid, A.; Housh, M. Detecting Cyber-Physical Attacks in Water Distribution Systems: One-Class Classifier Approach. J. Water Resour. Plan. Manag. 2020, 146, 04020060. [Google Scholar] [CrossRef]
- Bakalos, N.; Voulodimos, A.; Doulamis, N.; Doulamis, A.; Ostfeld, A.; Salomons, E.; Caubet, J.; Jimenez, V.; Li, P. Protecting Water Infrastructure From Cyber and Physical Threats: Using Multimodal Data Fusion and Adaptive Deep Learning to Monitor Critical Systems. IEEE Signal Process. Mag. 2019, 36, 36–48. [Google Scholar] [CrossRef]
- Min, K.W.; Choi, Y.H.; Al-Shamiri, A.K.; Kim, J.H. Application of Artificial Neural Network for Cyber-Attack Detection in Water Distribution Systems as Cyber Physical Systems. In Advances in Harmony Search, Soft Computing and Applications; Kim, J.H., Geem, Z.W., Jung, D., Yoo, D.G., Yadav, A., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 82–88. [Google Scholar]
- Macas, M.; Wu, C. An Unsupervised Framework for Anomaly Detection in a Water Treatment System. In Proceedings of the 2019 18th IEEE International Conference On Machine Learning And Applications (ICMLA), Boca Raton, FL, USA, 16–19 December 2019; pp. 1298–1305. [Google Scholar]
- Zou, X.Y.; Lin, Y.L.; Xu, B.; Guo, Z.B.; Xia, S.J.; Zhang, T.Y.; Gao, N.Y. A Novel Event Detection Model for Water Distribution Systems Based on Data-Driven Estimation and Support Vector Machine Classification. Water Resour. Manag. 2019, 33, 4569–4581. [Google Scholar] [CrossRef]
- Ghaeini, H.R.; Tippenhauer, N.O. HAMIDS: Hierarchical Monitoring Intrusion Detection System for Industrial Control Systems. In Proceedings of the 2nd ACM Workshop on Cyber-Physical Systems Security and Privacy, CPS-SPC 2016, Vienna, Austria, 28 October 2016; Association for Computing Machinery: New York, NY, USA, 2016; pp. 103–111. [Google Scholar] [CrossRef]
- Ostfeld, A.; Salomons, E.; Ormsbee, L.; Uber, J.G.; Bros, C.M.; Kalungi, P.; Burd, R.; Zazula-Coetzee, B.; Belrain, T.; Kang, D.; et al. Battle of the Water Calibration Networks. J. Water Resour. Plan. Manag. 2012, 138, 523–532. [Google Scholar] [CrossRef]
- Pasha, M.F.K. Development of an Effective Hybrid Method to Detect Cyber-Physical Attack on Water Distribution Systems. In Proceedings of the World Environmental and Water Resources Congress 2018, Minneapolis, MI, USA, 3–7 June 2018; pp. 410–421. [Google Scholar] [CrossRef]
- Aggarwal, C.C. High-Dimensional Outlier Detection: The Subspace Method. In Outlier Analysis; Springer New York: New York, NY, USA, 2013; pp. 135–167. [Google Scholar] [CrossRef]
- Breunig, M.M.; Kriegel, H.P.; Ng, R.T.; Sander, J. LOF: Identifying Density-Based Local Outliers. In Proceedings of the 2000 ACM SIGMOD International Conference on Management of Data, SIGMOD ’00, Dallas, TX, USA, 16–18 May 2000; Association for Computing Machinery: New York, NY, USA, 2000; pp. 93–104. [Google Scholar] [CrossRef]
- Kang, E.; Adepu, S.; Jackson, D.; Mathur, A.P. Model-Based Security Analysis of a Water Treatment System. In Proceedings of the 2016 IEEE/ACM 2nd International Workshop on Software Engineering for Smart Cyber-Physical Systems (SEsCPS), Austin, TX, USA, 16 May 2016; pp. 22–28. [Google Scholar]
- Patlolla, S.S.; McMillin, B.; Adepu, S.; Mathur, A. An Approach for Formal Analysis of the Security of a Water Treatment Testbed. In Proceedings of the 2018 IEEE 23rd Pacific Rim International Symposium on Dependable Computing (PRDC), Taipei, Taiwan, 4–8 December 2018; pp. 115–124. [Google Scholar]
- Howser, G.; McMillin, B. A Modal Model of Stuxnet Attacks on Cyber-physical Systems: A Matter of Trust. In Proceedings of the 2014 Eighth International Conference on Software Security and Reliability (SERE), San Francisco, CA, USA, 30 June–2 July 2014; pp. 225–234. [Google Scholar] [CrossRef]
- Liau, C.-J. Belief, information acquisition, and trust in multi-agent systems—A modal logic formulation. Artif. Intell. 2003, 149, 31–60. [Google Scholar] [CrossRef]
- Mishra, V.K.; Palleti, V.R.; Mathur, A. A modeling framework for critical infrastructure and its application in detecting cyber-attacks on a water distribution system. Int. J. Crit. Infrastruct. Prot. 2019, 26, 100298. [Google Scholar] [CrossRef]
- Douglas, H.C.; Taormina, R.; Galelli, S. Pressure-Driven Modeling of Cyber-Physical Attacks on Water Distribution Systems. J. Water Resour. Plan. Manag. 2019, 145, 06019001. [Google Scholar] [CrossRef]
- Moraitis, G.; Nikolopoulos, D.; Bouziotas, D.; Lykou, A.; Karavokiros, G.; Makropoulos, C. Quantifying Failure for Critical Water Infrastructures under Cyber-Physical Threats. J. Environ. Eng. 2020, 146, 04020108. [Google Scholar] [CrossRef]
- Jeong, H.S.; Abraham, D.M.; Qiao, J.; Lawley, M.A.; Richard, J.P.P.; Yih, Y. Issues in Risk Management of Water Networks Against Intentional Attacks. In Proceedings of the ASCE Pipeline Division Specialty Congress—Pipeline Engineering and Construction, San Diego, CA, USA, 1–4 August 2004; pp. 1–10. [Google Scholar] [CrossRef]
- Shin, S.; Lee, S.; Burian, S.J.; Judi, D.R.; McPherson, T. Evaluating Resilience of Water Distribution Networks to Operational Failures from Cyber-Physical Attacks. J. Environ. Eng. 2020, 146, 04020003. [Google Scholar] [CrossRef]
- Mathur, A. SecWater: A Multi-Layer Security Framework for Water Treatment Plants. In Proceedings of the 3rd International Workshop on Cyber-Physical Systems for Smart Water Networks, CySWATER ’17, Pittsburgh, PA, USA, 21 April 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 29–32. [Google Scholar] [CrossRef]
- Luiijf, E.; Ali, M.; Zielstra, A. Assessing and Improving SCADA Security in the Dutch Drinking Water Sector. In Critical Information Infrastructure Security; Setola, R., Geretshuber, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 190–199. [Google Scholar]
- Falliere, N.; Murchu, L.O.; Chien, E. SCADA Security Good Practices for the Drinking Water Sector; TNO Defence, Security and Safety; Report: TNO-DV 2008 C096; TNO: Den Haag, The Netherlands, 2008. [Google Scholar]
- Burghouwt, P.; Maris, M.; van Peski, S.; Luiijf, E.; van de Voorde, I.; Spruit, M. Cyber Targets Water Management. In Critical Information Infrastructures Security; Havarneanu, G., Setola, R., Nassopoulos, H., Wolthusen, S., Eds.; Springer International Publishing: Cham, Switzerland, 2017; pp. 38–49. [Google Scholar]
- Adepu, S.; Mishra, G.; Mathur, A. Access Control in Water Distribution Networks: A Case Study. In Proceedings of the 2017 IEEE International Conference on Software Quality, Reliability and Security (QRS), Prague, Czech Republic, 25–29 July 2017; pp. 184–191. [Google Scholar]
- Lenzi, S.; Terenghi, G.; Taormina, R.; Galelli, S.; Ciuccarelli, P. Disclosing cyber attacks on water distribution systems: An experimental approach to the sonification of threats and anomalous data. In Proceedings of the International Conference on Auditory Display, Tyne, UK, 23–27 June 2019. [Google Scholar]
- Tatbul, N.; Lee, T.J.; Zdonik, S.; Alam, M.; Gottschlich, J. Precision and Recall for Time Series. In Proceedings of the 32nd International Conference on Neural Information Processing Systems, NIPS 2018, Denver, CO, USA, 3–8 December 2018; Curran Associates Inc.: Red Hook, NY, USA, 2018; pp. 1924–1934. [Google Scholar]
- Kurakin, A.; Goodfellow, I.; Bengio, S. Adversarial Machine Learning at Scale. arXiv 2016, arXiv:1611.01236. [Google Scholar]
- Madry, A.; Makelov, A.; Schmidt, L.; Tsipras, D.; Vladu, A. Towards Deep Learning Models Resistant to Adversarial Attacks. arXiv 2019, arXiv:1706.06083. [Google Scholar]





| Reference | Year | Target | Attribution | Infection Vector | Details | Impact |
|---|---|---|---|---|---|---|
| Israel’s water system [19] | 2020 | OP | Hacktivist/Nation state | Unknown | Israeli government reported cyber-attacks against water supply and treatment facilities and urged these facilities to change passwords. | Unknown. |
| Northern Colorado [20] | 2019 | OP | Cybercrime | Ransomware | Locked access to technical and engineering data. | Disruption, took about three weeks to unlock data. |
| Cryptojacking [21] | 2018 | OP | Cybercrime | Cryptocurrency mining | Cryptocurrency malware installed on HMI on the SCADA network. | Unknown. |
| Kemuri water [22] | 2016 | OP | Hacktivist | Remote access | Accessed PLC responsible for controlling water treatment chemicals. | Engineers were able to identify and reverse the changes made to process control parameters. |
| Bowman Avenue Dam [23,24] | 2016 | OP | Hackers/Nation state | Remote access | According to US authorities, hackers linked to Iranian Armed Forces infiltrated ICS of Bowman Avenue Dam and accessed the SCADA for the dam. | Data exfiltration and over $30k on remediation costs. Physical damage was not possible due to disconnected sluice gates. |
| Florida Wastewater [25] | 2012 | IT | Ex-Employee | Remote access | Stolen login credentials were used to access district’s computer system. | Deleting and modifying information. Ex-employee was arrested on account of computer crime. |
| Tehama-Colusa Canal [26] | 2007 | OP | Ex-employee | Physical access | Installed malware on SCADA system responsible for controlling agricultural irrigation [26]. | Damage to equipment, and additional unknown amount of monetary loss due to replacing production. |
| Harrisburg water plant [27] | 2006 | IT | Hackers | Remote Access | Compromised and installed malware on an employee’s laptop which could have been used as an entry point to reach water treatment system. | Unknown. |
| Maroochy Shire [28,29] | 2000 | OP | Ex-employee of a contractor | Physical access | Masqueraded as a controller using stolen equipment and sent fake commands to the pumping station. | Approximately 800,000 litres of sewage was released into the environment, harming local parks and rivers, impacting public health, killing marine life, and caused large monetary loss. |
| Source | Search String |
|---|---|
| Springer | where the title contains: Water AND with at least one of the words: cyber-security OR cybersecurity |
| ACM Digital Library | [Document Title: water] AND [[Abstract: cyber-security] OR [Abstract: cybersecurity]] |
| IEEE Xplore | “All Metadata”: water cyber-security |
| ScienceDirect | Find articles with these terms: cyber-security OR cybersecurity, title, abstract, keywords: water |
| ASCE Library | water AND (cyber-security OR cybersecurity) |
| Google Scholar | allintitle: water cyber |
| Type | Name | Count |
|---|---|---|
| conference | World Environmental and Water Resources Congress | 11 |
| workshop | International Workshop on Cyber-Physical Systems for Smart Water Networks | 6 |
| journal | Journal of Water Resources Planning and Management | 5 |
| journal | Journal of Environmental Engineering | 3 |
| conference | IEEE International Conference on Software Quality, Reliability and Security | 3 |
| conference | International Conference on Critical Information Infrastructures Security | 2 |
| conference | ACM on Asia Conference on Computer and Communications Security | 2 |
| journal | IEEE Transactions on Control Systems Technology | 2 |
| workshop | International Workshop on the Security of Industrial Control Systems and CPS | 1 |
| workshop | International Workshop on Critical Information Infrastructures Security | 1 |
| workshop | IEEE/ACM International Workshop on Software Engineering for Smart CPS | 1 |
| workshop | ACM Workshop on Cyber–Physical Systems Security and Privacy | 1 |
| journal | Water Resources Management | 1 |
| journal | Water Research | 1 |
| journal | Journal of Systems Science and Systems Engineering | 1 |
| journal | International Journal of Critical Infrastructure Protection | 1 |
| journal | IEEE Transactions on Dependable and Secure Computing | 1 |
| journal | IEEE Signal Processing Magazine | 1 |
| journal | IEEE Design and Test | 1 |
| journal | Human-centric Computing and Information Services | 1 |
| journal | Future Internet | 1 |
| journal | Environmental Modelling and Software | 1 |
| conference | Pipeline Division Specialty Congress | 1 |
| conference | International Symposium on Computer Science and Intelligent Control | 1 |
| conference | International Conference on Technology Trends | 1 |
| conference | International Conference on Harmony Search Algorithm | 1 |
| conference | International Conference on Critical Infrastructure Protection | 1 |
| conference | International Conference on Auditory Display | 1 |
| conference | IFIP TC 11 International Conference on ICT Systems Security and Privacy Protection | 1 |
| conference | IFAC Conference on Cyber–Physical and Human Systems | 1 |
| conference | IEEE/ACM Int’l Conference on Cyber, Physical and Social Computing | 1 |
| conference | IEEE Pacific Rim International Symposium on Dependable Computing | 1 |
| conference | IEEE International Symposium on High Assurance Systems Engineering | 1 |
| conference | IEEE International Conference on Machine Learning and Applications | 1 |
| conference | IEEE International Conference on Data-Mining Workshops | 1 |
| conference | IEEE International Conference on Big Data | 1 |
| conference | ACM international conference on Hybrid systems: Computation and Control | 1 |
| conference | Annual Computer Security Applications Conference | 1 |
| Publication | Details | Dataset |
|---|---|---|
| WaterBox (2015) [51] | A small-scale cyber–physical testbed designed for an in-lab environment to simulate smart water networks using components designed from acrylic, Arduino boards, small-scale sensors (pressure sensor, flow meter) and a motorised valve (using a small stepper motor). | - |
| SWaT (2016) [43,46] | An operational small-scale water treatment testbed with real cyber and physical equipment to investigate cyber-security research in 2015 by Singapore University of Technology and Design. It consists of a six-stage water treatment process with the modern-day components. | Available [45,50] |
| WADI (2016) [44,46] | A testbed launched by Singapore University of Technology and Design funded in 2016 as an extension of SWaT testbed to form a complete water treatment, storage and distribution system. | Available [45] |
| epanetCPA (2016) [52,53] | EPANET-based toolbox that is designed to assess the impact of cyber–physical attacks. | - |
| FACIES (2017) [54] | A water distribution system prototype funded by EU project FACIES based on a small fictitious city distributing water to different residential areas with a reservoir represented as tanks of different sizes. | - |
| RISKNOUGHT (2018) [55,56,57] | A cyber–physical stress testing platform leveraging EPANET software library to simulate the physical process and a custom network model for SCADA system. | |
| Water storage control (2018) [58] | A SCADA testbed simulating water storage control consisting of water tank, PLC, historian, HMI, water level sensors and actuators (pumps and valve). The testbed was used to evaluate machine learning detection models against reconnaissance, command injection, and DoS attacks. | - |
| Publication | Attacks | Application Environment | Dataset | Detection Model |
|---|---|---|---|---|
| Amin et al. [69] | deception attacks against PVs | a simplified canal hydrodynamic model | - | model-based |
| Adepu and Mathur [70,71,72,73] | bias attacks [74] | SWaT testbed | - | model-based: invariants |
| Yoong and Heng [75] | - | SWaT testbed | - | machine learning invariants |
| Miciolino et al. [54] | DoS, replay | FACIES | - | standard deviation |
| Zohrevand et al. [76] | attacking water flow | water supply system | operational water supply system in Canada | hidden Markov model |
| Ahmed et al. [77] | false data injection and zero-alarm attacks against PVs and MVs | simulation: EPANET | - | model-based |
| Moazeni and Khazaei [78] | - | simulation: MATLAB OPTi toolbox | - | model-based: MINLP |
| Inoue et al. [79] | deception attacks against PVs and MVs | - | SWaT | LSTM and one-class SVM |
| Hindy et al. [80] | DoS, spoofing | physical testbed | - | classic machine learning methods |
| Studies using BATADAL dataset [47] | deception attacks, replay against PVs and MVs | - | BATADAL | autoencoders [81,82], MLP and PCA [83,84], data-mining [85,86], NARX [87], rule-based and deep learning [88], model-based (MILP) [89,90], model-based(feature extraction and random forest) [91], PCA, EWMA and RBC [92], ensemble (SOD, LOF and QDA) [93], |
| Kadosh et al. [94] | deception attacks, replay | C-Town, E-Town WDSs | BATADAL and generated dataset | SVDD |
| Bakalos et al. [95] | deception attacks against PVs, physical intrusions | water infrastructure SCADA systems | STOP-IT | TDL-CNN |
| Min et al. [96] | deception attacks against PVs and MVs | simulation: EPANET | - | ANN |
| Macas et al. [97] | deception attacks against PVs and MVs | - | SWaT | deep autoencoders |
| Zou et al. [98] | - | WDS in US | - | data-driven estimation (ANNs) and one-class SVM |
| Ghaeini and Tippenhauer [99] | network attacks | SWaT testbed | - | deep packet inspection |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tuptuk, N.; Hazell, P.; Watson, J.; Hailes, S. A Systematic Review of the State of Cyber-Security in Water Systems. Water 2021, 13, 81. https://doi.org/10.3390/w13010081
Tuptuk N, Hazell P, Watson J, Hailes S. A Systematic Review of the State of Cyber-Security in Water Systems. Water. 2021; 13(1):81. https://doi.org/10.3390/w13010081
Chicago/Turabian StyleTuptuk, Nilufer, Peter Hazell, Jeremy Watson, and Stephen Hailes. 2021. "A Systematic Review of the State of Cyber-Security in Water Systems" Water 13, no. 1: 81. https://doi.org/10.3390/w13010081
APA StyleTuptuk, N., Hazell, P., Watson, J., & Hailes, S. (2021). A Systematic Review of the State of Cyber-Security in Water Systems. Water, 13(1), 81. https://doi.org/10.3390/w13010081





