The Hybridisation of Conflict: A Prospect Theoretic Analysis
Abstract
:1. Introduction
2. The Contemporary Nature of State Competition
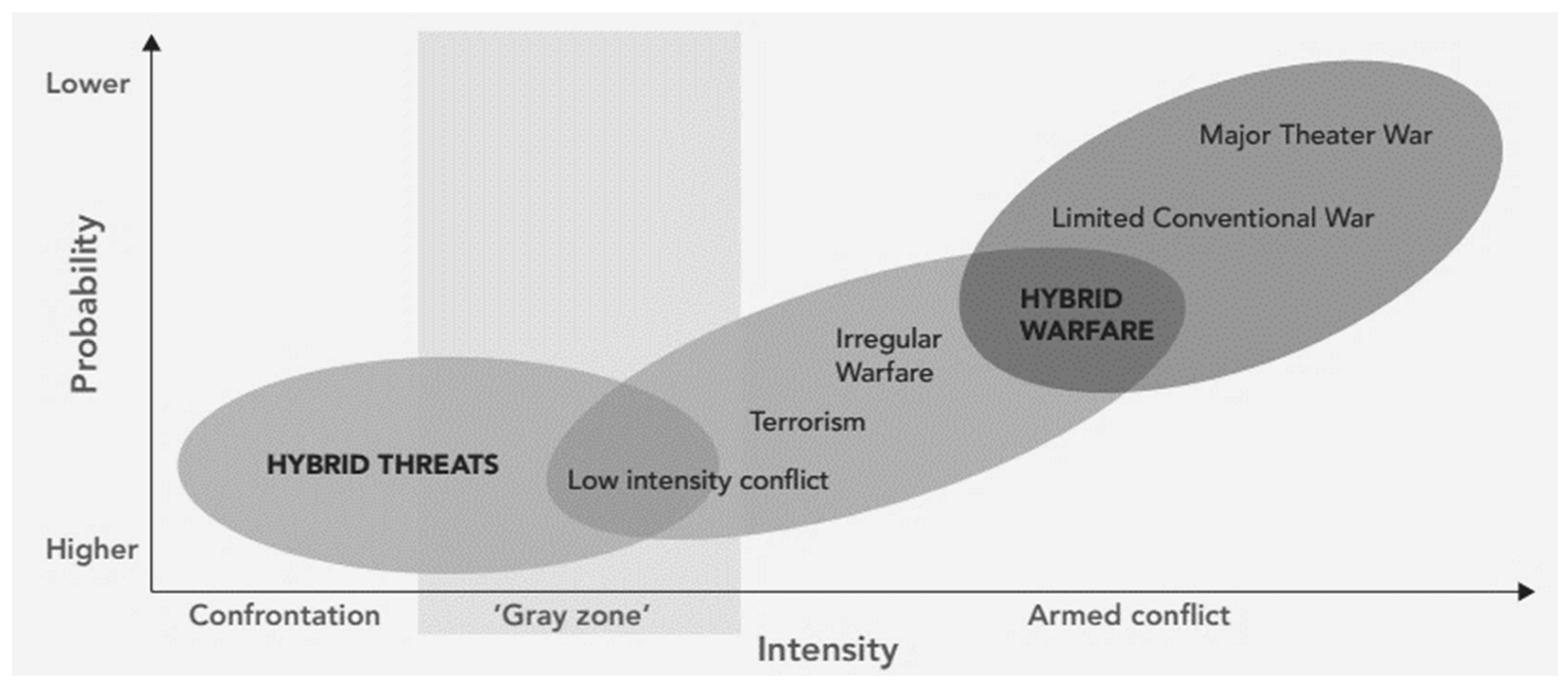
2.1. Characteristics of Hybrid Threats
3. Prospect Theory and Decision Making under Risk
3.1. An Introduction to Prospect Theory
3.2. The Application of Prospect Theory within the Field of International Relations
4. Studying the Contemporary Conflict Environment from a Prospect Theoretic Perspective
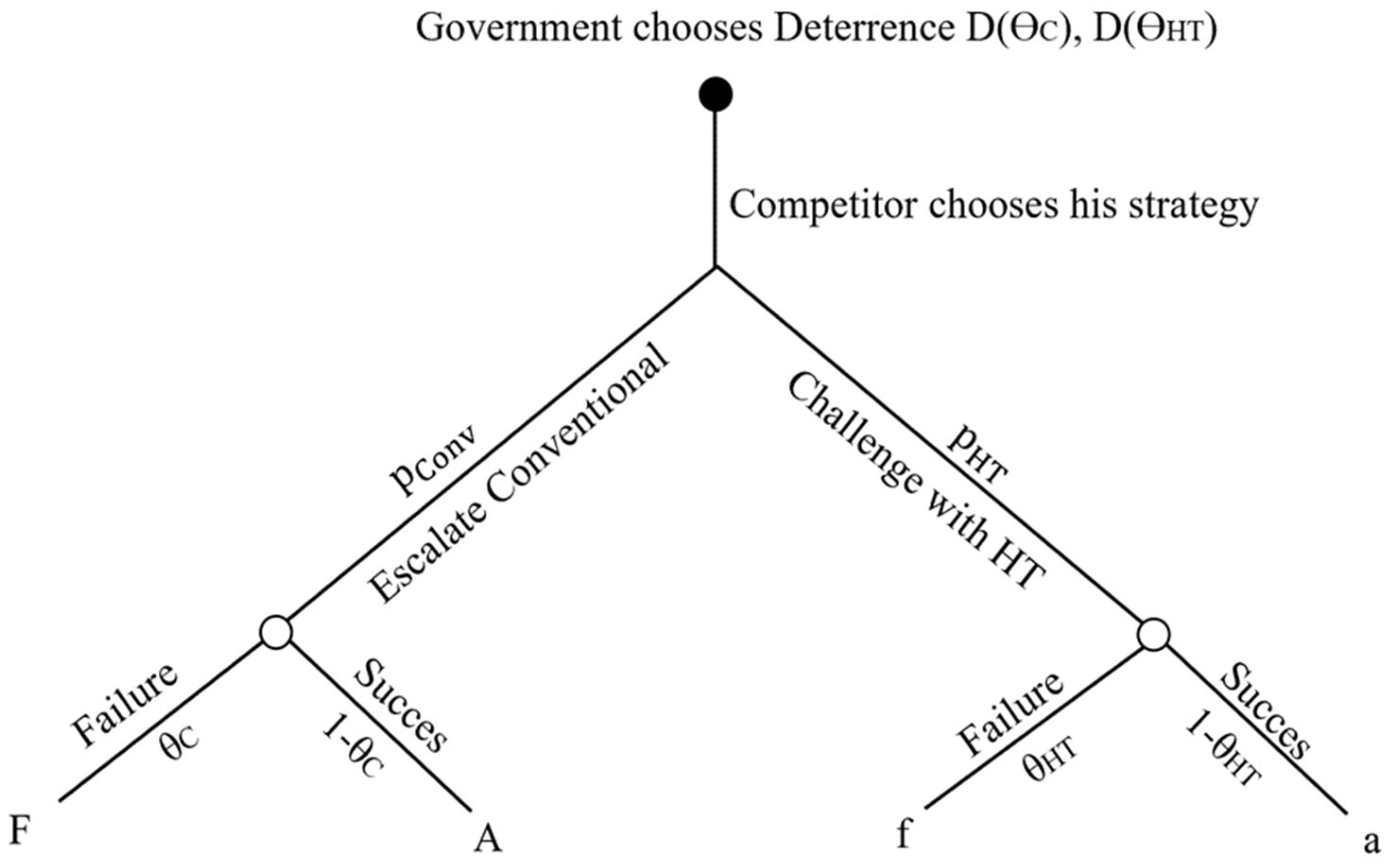
4.1. Modelling Contemporary State Competition: The Joint Analysis of Conventional and Hybrid Threats
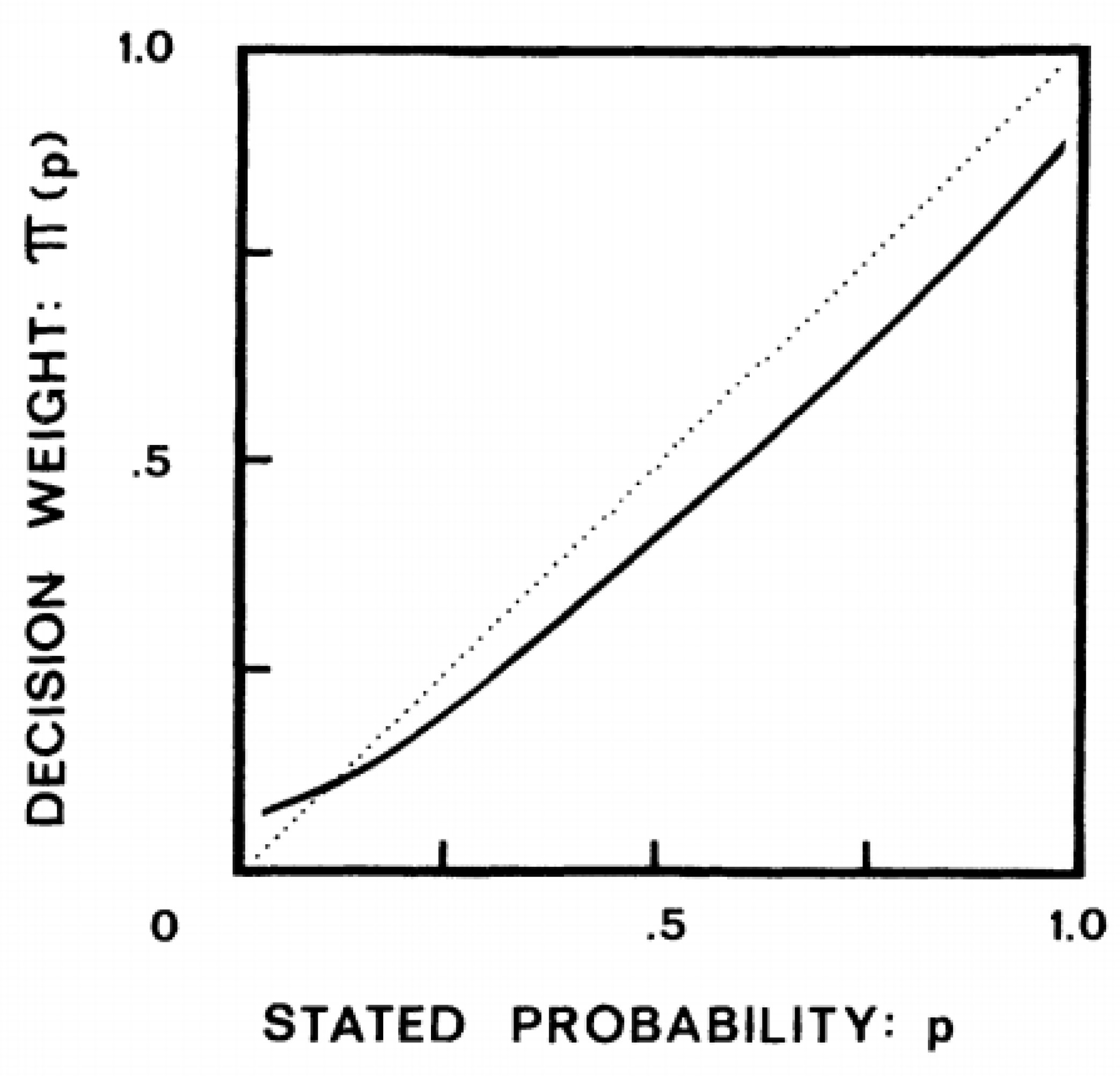
4.2. Insights from the Weighting Function
4.3. The Use of Hybrid Threats in Contemporary State Competition: Insights from the Value Function
They (strategic nuclear weapons), not incidentally, served as shiny objects to distract Western intelligence analysts in an area where Western countries were then obligated to continue spending money, soaking up attention and resources even as Russia’s true transformation took place in the realms of asymmetric and conventional warfare.
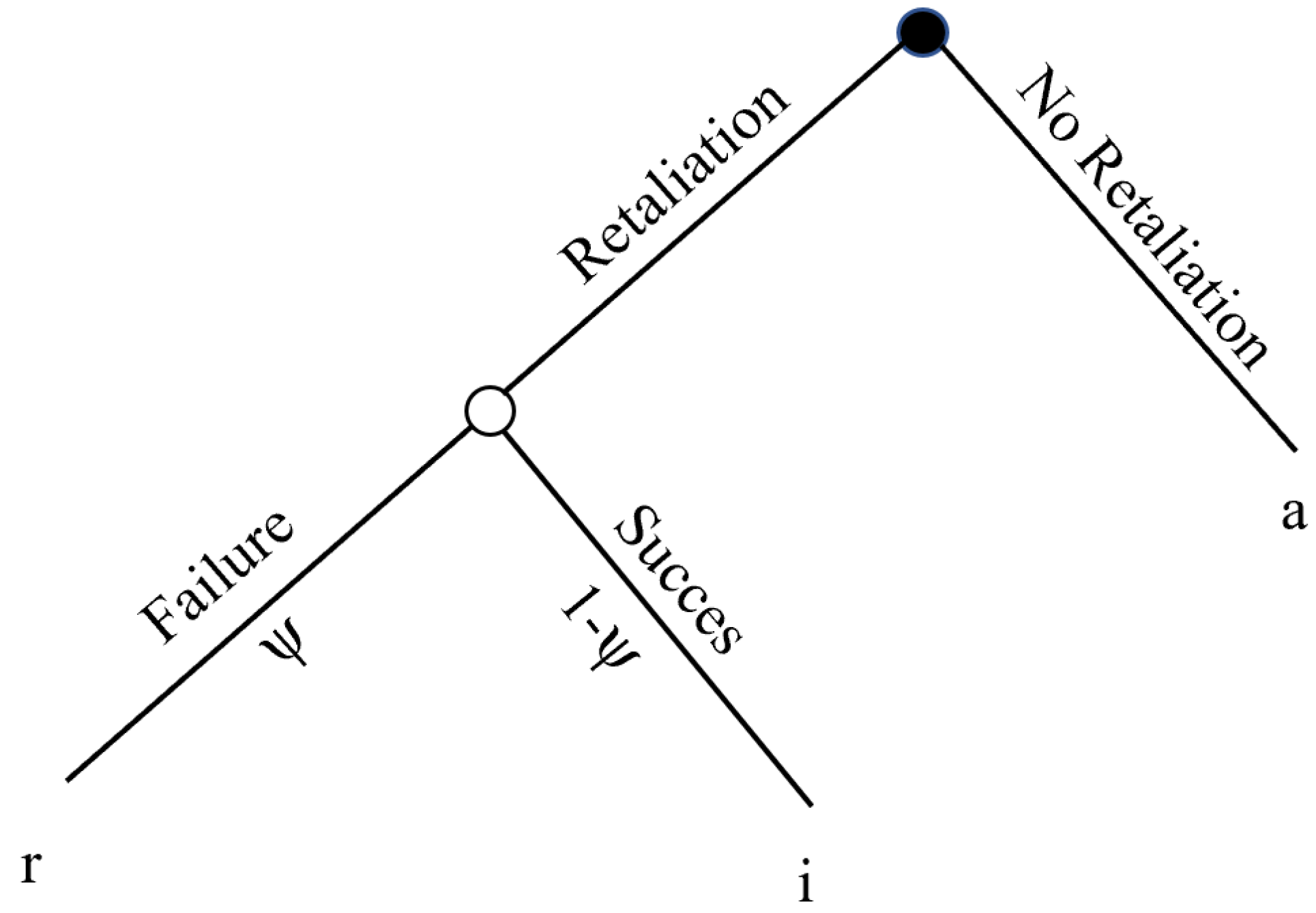
4.4. The Credibility of Cross-Domain Deterrence by Punishment
5. Discussion
6. Conclusions and Suggestions for Future Research
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- US Department of Defense. Summary of the 2018 US National Defense Strategy. Available online: https://dod.defense.gov/Portals/1/Documents/pubs/2018-National-Defense-Strategy-Summary.pdf (accessed on 25 May 2021).
- Pettyjohn, S.L.; Wasser, B. Competing in the Grey Zone; The Rand Corporation: Santa Monica, CA, USA, 2019; Available online: https://www.rand.org/content/dam/rand/pubs/research_reports/RR2700/RR2791/RAND_RR2791.pdf (accessed on 10 June 2021).
- NATO. NATO 2030: United for a New Era: Analysis and Recommendations of the Reflection Group Appointed by the NATO Secretary General. Available online: https://www.nato.int/nato_static_fl2014/assets/pdf/2020/12/pdf/201201-Reflection-Group-Final-Report-Uni.pdf (accessed on 10 March 2021).
- NATO. Annual Report 2020. Available online: https://www.nato.int/cps/en/natohq/opinions_182236.htm (accessed on 24 April 2021).
- Lindsay, J.R.; Gartzke, E. Politics by many other means: The comparative strategic advantages of operational domains. J. Strateg. Studies. 2020, 1–34. [Google Scholar] [CrossRef]
- Coats, D.R. Worldwide Threat Assessment. US Intelligence Community. 2019. Available online: https://www.dni.gov/files/ODNI/documents/2019-ATA-SFR---SSCI.pdf (accessed on 15 June 2021).
- Kilcullen, D. The Dragons and the Snakes, How the Rest Learned to Fight the West; Oxford University Press: Oxford, UK, 2020. [Google Scholar]
- Levy, J.S. An introduction to prospect theory. Political. Psychol. 1992, 13, 171–186. [Google Scholar]
- Berejikian, J.D.; Zwald, Z. Why language matters: Shaping public risk tolerance during deterrence crisis. Contemp. Secur. Policy 2020, 41, 507–540. [Google Scholar] [CrossRef]
- Knopf, J.W. The fourth wave in deterrence research. Contemp. Secur. Policy 2010, 31, 1–33. [Google Scholar] [CrossRef] [Green Version]
- Mallory, K. New Challenges in Cross-Domain Deterrence; The Rand Corporation: Santa Monica, CA, USA, 2008; Available online: https://www.rand.org/pubs/perspectives/PE259.html (accessed on 15 June 2021).
- Sweijs, T.; Zilincik, S. Cross Domain Deterrence and Hybrid Conflict; The Hague Center for Strategic Studies: the Hague, The Netherlands, 2019; Available online: https://hcss.nl/report/cross-domain-deterrence-and-hybrid-conflict (accessed on 29 April 2021).
- Lindsay, J.R.; Gartzke, E. Cross-Domain Deterrence: Strategy in An Era of Complexity; Oxford University Press: Oxford, UK, 2019. [Google Scholar]
- Galeotti, M. Hybrid, ambiguous, and non-linear? How new is Russia’s ‘new way of war’? Small Wars Insur. 2016, 27, 282–301. [Google Scholar] [CrossRef]
- Caliskan, M.; Liégeois, M. The concept of ‘hybrid warfare’ undermines NATO’s strategic thinking: Insights from interviews with NATO officials. Small Wars Insur. 2020, 32, 295–319. [Google Scholar] [CrossRef]
- Giannopoulus, G.; Smith, H.; Theocharidou, M. The Landscape of Hybrid Threats: A Conceptual Model; The Hybrid Centre of Excellence: Helsinki, Finland, 2020; Available online: https://op.europa.eu/en/publication-detail/-/publication/b534e5b3-7268-11eb-9ac9-01aa75ed71a1 (accessed on 15 June 2021).
- Chivvis, C. Understanding Russian ‘Hybrid Warfare’ and What Can Be Done about It; The RAND Corporation: Santa Monica, CA, USA, 2017; Available online: https://www.rand.org/content/dam/rand/pubs/testimonies/CT400/CT468/RAND_CT468.pdf (accessed on 30 June 2021).
- Seely, R. Defining contemporary Russian warfare: Beyond the hybrid headline. RUSI J. 2017, 162, 40–49. [Google Scholar] [CrossRef]
- Monaghan, S. Countering hybrid warfare. PRISM 2019, 8, 82–99. [Google Scholar]
- Kilcullen, D. The evolution of unconventional warfare. Scand. J. Mil. Stud. 2019, 2, 61–71. [Google Scholar] [CrossRef]
- Liang, Q.; Xiangsui, W. Unrestricted Warfare; Foreign Broadcast Information Service (FBIS); PLA Literature and Arts Publishing House: Beijing, China, 1999. [Google Scholar]
- Hoffman, F. Examining complex forms of conflict: Grey zone and hybrid challenges. PRISM 2019, 7, 30–47. [Google Scholar]
- Radin, A.; Reach, C. Russian Views of the International Order; The Rand Corporation: Santa Monica, CA, USA, 2017; Available online: https://www.rand.org/pubs/research_reports/RR1826.html (accessed on 25 May 2021).
- Bijlsma, T. What’s on the human mind? Decision theory and deterrence. In Netherlands Annual Review of Military Studies 2020, 1st ed.; Osinga, F., Sweijs, T., Eds.; Springer: Berlin, Germany, 2020; pp. 437–454. [Google Scholar]
- Kahneman, D.; Tversky, A. Prospect theory: An analysis of decision under risk. Econometrica 1979, 47, 263–291. [Google Scholar] [CrossRef] [Green Version]
- Tversky, A.; Kahneman, D. Loss aversion in riskless choice: A reference-dependent model. Q. J. Econ. 1991, 106, 1039–1061. [Google Scholar] [CrossRef]
- Tversky, A.; Kahneman, D. Advances in prospect theory: Cumulative representation of uncertainty. J. Risk Uncertain. 1992, 5, 297–323. [Google Scholar] [CrossRef]
- Heath, C.; Larrick, R.P.; Wu, G. Goals as reference points. Cogn. Psychol. 1991, 38, 79–109. [Google Scholar] [CrossRef]
- Berejikian, J.D.; Early, B.R. Loss aversion and foreign policy resolve. Political Psychol. 2013, 34, 649–671. [Google Scholar] [CrossRef]
- Litt, A.; Eliasmith, C.; Thagard, P. Neural affective decision theory: Choices, brains and emotions. Cogn. Syst. Res. 2008, 9, 252–273. [Google Scholar] [CrossRef]
- Farnham, B. Roosevelt and the Munich crisis: Insights from prospect theory. Political Psychol. 1991, 13, 205–235. [Google Scholar] [CrossRef]
- Richardson, L. Avoiding and incurring losses: Decision-making in the Suez crisis. Int. J. 1992, 47, 370–401. [Google Scholar] [CrossRef]
- McDermott, R. Prospect theory in international relations: The Iranian hostage rescue mission. Political Psychol. 1992, 13, 237–263. [Google Scholar] [CrossRef]
- Haas, M.L. Prospect theory and the Cuban missile crisis. Int. Stud. Q. 2001, 45, 241–270. [Google Scholar] [CrossRef]
- Berejikian, J.D. A cognitive theory of deterrence. J. Peace Res. 2002, 39, 165–183. [Google Scholar] [CrossRef] [Green Version]
- Berejikian, J.D. Model building with prospect theory: A cognitive approach to International Relations. Political Psychol. 2002, 23, 759–786. [Google Scholar] [CrossRef]
- Tessman, B.F.; Chan, S. Power cycles, risk propensity and great power deterrence. J. Confl. Resolut. 2004, 48, 131–153. [Google Scholar] [CrossRef]
- Carlson, L.J.; Dacey, R. Sequential analysis of deterrence games with a declining status quo. Confl. Manag. Peace Sci. 2006, 23, 181–198. [Google Scholar] [CrossRef]
- Butler, C.K. Prospect theory and coercive bargaining. J. Confl. Resolut. 2007, 51, 227–250. [Google Scholar] [CrossRef] [Green Version]
- Tversky, A.; Kahneman, D. The framing of decisions and the psychology of choice. Science 1981, 211, 453–458. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Balcaen, P.; Du Bois, C.; Buts, C. A game-theoretic analysis of hybrid threats. Def. Peace Econ. 2021, 1–16. [Google Scholar] [CrossRef]
- Boettcher, W.A. The prospects for prospect theory: An empirical evaluation of international relations applications of framing and loss aversion. Political Psychol. 2004, 25, 331–362. [Google Scholar] [CrossRef]
- Stein, J.G. The micro-foundations of international relations theory: Psychology and behavioral economics. Int. Organ. 2017, 71, S249–S263. [Google Scholar] [CrossRef]
- Zagare, F.C.; Kilgour, M.D. Asymmetric deterrence. Int. Stud. Q. 1993, 37, 1–27. [Google Scholar] [CrossRef]
- Roth, A.; Harding, L. Russia to Pull Back Troops from Crimea and Ukraine Border. The Guardian. Available online: https://www.theguardian.com/world/2021/apr/22/russia-to-pull-back-troops-from-crimea-and-ukraine-border (accessed on 10 June 2021).
- Schelling, T. The Strategy of Conflict; Harvard University Press: Cambridge, UK, 1960. [Google Scholar]
- Nalebuff, B. Rational deterrence in an imperfect world. World Politics 1991, 43, 313–335. [Google Scholar] [CrossRef]
- Levy, J.S. Loss aversion, framing, and bargaining: The implications of prospect theory for international conflict. Int. Political Sci. Rev. 1996, 17, 179–195. [Google Scholar] [CrossRef] [Green Version]
- Levy, J.S.; Whyte, G. A cross-cultural exploration of crucial decisions under risk: Japan’s 1941 decision for war. J. Confl. Resolut. 1997, 41, 792–813. [Google Scholar] [CrossRef]
- Alliance for Securing Democracy. The Authoritarian Interference Tracker. Available online: https://securingdemocracy.gmfus.org/hamilton-dashboard/ (accessed on 20 June 2021).
- NATO. Speech by NATO Secretary General Jens Stoltenberg at the Cyber Defence Pledge Conference. Available online: https://www.nato.int/cps/en/natohq/opinions_154462.htm?selectedLocale=ru (accessed on 15 March 2021).
- Leuprecht, C.; Szeman, J.; Skillicorn, D.B. The damoclean sword of offensive cyber: Policy uncertainty and collective insecurity. Contemp. Secur. Policy 2019, 40, 382–407. [Google Scholar] [CrossRef]
- US Department of Defense. US Defense Budget Overview. Available online: https://comptroller.defense.gov/Budget-Materials/ (accessed on 10 June 2021).
- Stockholm International Peace Research Institute (SIPRI). Military Expenditures Database 2020. Available online: https://www.sipri.org/databases/milex (accessed on 28 June 2021).
- Cami, G.; Shea, J.; Mikaela d’Angelo, M.; Huerta, G.; André, L.; Arenella, R.; Lów, E. Hybrid and Transnational Threats; Friends of Europe: Brussels, Belgium, 2018; Available online: https://www.friendsofeurope.org/wp/wp-content/uploads/2019/04/FoE_SEC_PUB_Hybrid_DP_WEB.pdf (accessed on 15 March 2021).
- Hybrid Centre of Excellence. What Is the Hybrid CoE? Available online: https://www.hybridcoe.fi/about-us/ (accessed on 18 March 2021).
- Council on Foreign Relations. Cyber Operations Tracker. Available online: https://www.cfr.org/blog/new-entries-cfr-cyber-operations-tracker-q4-2020 (accessed on 1 July 2021).
- Mission Critical. The Dark Web: DDoS Attacks Sell for as Low as $10 Per Hour. 2020. Available online: https://www.missioncriticalmagazine.com/articles/93185-the-dark-web-ddos-attacks-sell-for-as-low-as-10-per-hour (accessed on 2 July 2021).
- Kertzer, J.D. Resolve, time and risk. Int. Organ. 2017, 71, S109–S136. [Google Scholar] [CrossRef]


Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Balcaen, P.; Du Bois, C.; Buts, C. The Hybridisation of Conflict: A Prospect Theoretic Analysis. Games 2021, 12, 81. https://doi.org/10.3390/g12040081
Balcaen P, Du Bois C, Buts C. The Hybridisation of Conflict: A Prospect Theoretic Analysis. Games. 2021; 12(4):81. https://doi.org/10.3390/g12040081
Chicago/Turabian StyleBalcaen, Pieter, Cind Du Bois, and Caroline Buts. 2021. "The Hybridisation of Conflict: A Prospect Theoretic Analysis" Games 12, no. 4: 81. https://doi.org/10.3390/g12040081
APA StyleBalcaen, P., Du Bois, C., & Buts, C. (2021). The Hybridisation of Conflict: A Prospect Theoretic Analysis. Games, 12(4), 81. https://doi.org/10.3390/g12040081




