2.2. Upper Bound on the Number of Queries
Theorem 2. Let , and . For , there is a strategy for Yes-No AB-Mastermind that identifies every secret code in at most queries and for , there is a strategy that identifies every secret code in less than queries.
Corollary 2. The exact asymptotic query complexity of Yes-No Permutation-Mastermind is .
The proof of Theorem 2 resembles the proof of a corresponding result concerning Black-Peg AB-Mastermind [
11], except that the information whether a given query contains a
correct but unidentified position is not derived directly but requires special querying outlined by Algorithm 1 below. In a nutshell (including both cases
and
), the strategy consists of
k distinct initial queries, each of which consists of the first
n positions of a circularly shifted version of the vector
. From the answers of the initial queries, we will be able to learn the secret code position-wise, keeping record about the positions that have already been identified. As long as there are consecutive initial queries
a and
b with the property that
a coincides with the secret code in at least one yet unidentified position but
b does not, we can apply a binary search for the next unidentified position in
a, using
further queries. Such initial queries
a and
b exist ever after one (usually after zero) but not all positions of the secret code have been identified.
Proof of Theorem 2. The case : We give a constructive strategy that identifies the positions of the secret code
one-by-one. In order to keep record about identified positions of the secret code we deal with a partial solution vector
x that satisfies
for all
. We call the non-zero positions of
x fixed and the zero-positions of
x open. The fixed positions of
x are the identified positions of the secret code. Remember, that for a query
we denote by
the information if there is some position in which
coincides with the secret code
y. For Yes-No AB-Mastermind the related information whether a query
contains a
correct but unidentified position cannot always be derived directly but must be obtained by guessing one or two modifications of
, rearranging those positions that coincide with the partial solution
x. The required query procedure is summarized as Algorithm 1.
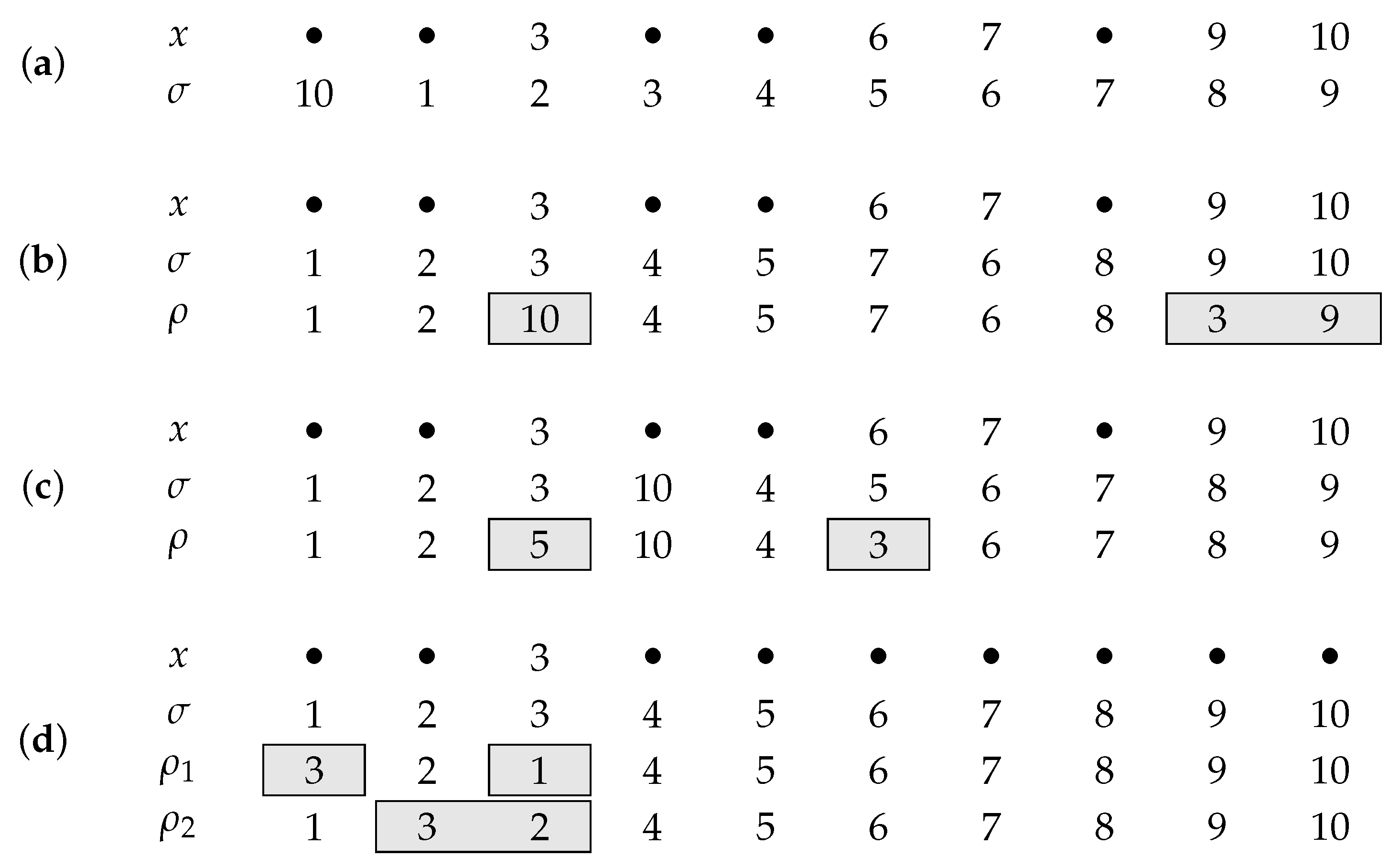
Example 1. Figure 1 illustrates the four distinct cases that are considered by . In the first and easiest case (panel (a)) the actual query σ does not coincide with the partial solution x. Thus, σ contains a correct unidentified position if and only if it contains a correct position at all, i.e., . In the second case (panel (b)), σ and x coincide in more than one position, namely the positions with colors 3, 9 and 10. The modified query ρ is obtained from σ by rearranging these positions in a way that all identified positions get a wrong color while leaving all open positions of σ unchanged. This implies that . Panels (c) and (d) deal with the case that σ and x coincide in exactly one position, say i. If x already contains a further non-zero position j, we obtain ρ from σ by swapping positions i and j in σ (the positions with colors 3 and 5 in panel (c)). Again, we obtain that . Finally, if position i is the only yet identified position of the secret code we have to ask two different modified queries to derive (panel (d)). We obtain the two queries and , each by swapping the identified position (here 3) with another position in σ, (here with 1 and 2, respectively). While the color of the identified position is wrong in both modifications and , every other position of σ coincides with the corresponding position of at least one modification. Therefore, if and only if . | Algorithm 1: Function infoP |
![Games 11 00019 i001 Games 11 00019 i001]() |
The codebreaker strategy that identifies the secret code y has two phases. In the first phase the codebreaker guesses an initial sequence of n queries that has a predefined structure. In the second phase, the structure of the initial sequence and the corresponding information by the codemaker enable us to identify correct positions of the secret code one after another, each by using a binary search. We denote the vector x restricted to the set with , .
Phase 1 Consider the n queries, , that are defined as follows: represents the identity map and for , we obtain from by a circular shift to the right. For example, if , we have , , and . The codebreaker guesses .
Phase 2. Now, the codebreaker identifies the values of y one after another, using a binary search procedure, that we call findNext. The idea is to exploit the information that for we have , , and . findNext is used to identify the second correct position to the last correct position in the main loop of the algorithm.
After the first position of
y has been found and fixed in
x, there exists a
such that
. As long as we have open positions in
x, we can either find a
with
but
and set
, or we have
but
and set
and
. We call such an index
j an
active index. Let
j be an active index and
r its related index. Let
c be the color of some position of
y that is already identified and fixed in the partial solution
x. With
and
we denote the position of color
c in
and
, respectively. The color
c serves as a pivot color for identifying a correct position
m in
that is not fixed, yet. There are two possible modes for the binary search that depend on the fact if
. The mode is indicated by a Boolean variable
and determined by lines 5–9 of findNext. Clearly,
if
. Otherwise, the codebreaker guesses
By the information
we obtain that
. We further know that every open color has a wrong position in
. For that reason,
implies that
. The binary search for the exact value of
m is done in the interval
, where
m is initialized as
n and
as
(lines 10–15 of findNext). In order to determine if there is an open correct position on the left side of the current center
ℓ of
in
we can define a case dependent query:
In the first case, the first positions of coincide with those of . The remaining positions of cannot coincide with the corresponding positions of the secret code if they have not been fixed, yet. This is because the ℓ-th position of has the already fixed value c, positions to coincide with the corresponding positions of which satisfies and the remaining positions have been checked to be wrong in this case (cf. former definition of in line 5 and line 9, respectively). Thus, there is a correct open position on the left side of ℓ in , if and only if . In the second case, the same holds for similar arguments. Now, if there is a correct open position to the left of ℓ, we update the binary search interval by . Otherwise, we update by .
| Algorithm 2: Function findNext |
![Games 11 00019 i002 Games 11 00019 i002]() |
Example 2. Suppose, that for the secret code y and the partial solution x are given as in the top panel of Figure 2 and that we have first identified the position with color 1, such that 1 is our pivot color. The initial 10 queries together with their current measures are given in the mid panel of Figure 2. We see that the highlighted queries, and , can be used for the binary search with findNext, since has a correct not yet identified position but has not. So the active indices are and and the corresponding pivot color positions in and are and . The first query of findNext (cf. lower panel of Figure 2) is . It begins with the pivot color, followed by the first 3 positions of (positions 2 to 4 of ) and positions 5 to 10 of (cf. line 7 of findNext). Since , the left most correct but unidentified position in is none of its first 4
positions. Thus, the binary search is continued in the interval . It is realized by queries , , and , which are composed according to line 20 of findNext (in this case), and finally identifies position 8
with color 5
of the secret code (generally the position left to the left most pivot color position that receives the answer “yes” in the binary search). The Main Algorithm. The main algorithm is outlined as Algorithm 3.
It starts with an empty partial solution and finds the positions of the secret code y one-by-one. The vector v keeps record about which of the initial queries coincides with the secret code y in some open position. Thus, v is initialized by , . The main loop always requires an active index. For that reason, if for all in the beginning, we first identify the correct position in (which is unique in this case) by queries (each swapping two positions of ) and update x and v, correspondingly. After this step, there will always exist an active index. Every call of findNext in the main loop augments x by a correct solution value. One call of findNext requires at most queries if the partial solution x contains more than one non-zero position, and at most queries (two queries for each call of infoP) if x has exactly one non-zero position. Thus, Algorithm 3 does not need more than queries to break the secret code inclusive the initial queries, queries to find the first correct position, calls of findNext and 2 final queries.
| Algorithm 3: Codebreaker Strategy for Permutations |
![Games 11 00019 i003 Games 11 00019 i003]() |
The case : Let be the code that must be found. We use the same notations as above.
Phase 1. Consider the k queries , where represents the identity map on and for , we obtain from by a circular shift to the right. We define k codes by , . For example, if and , we have , , , and . Within those k codes, every color appears exactly once at every position and, thus, there are at least initial queries that do not contain any correct position. Since , this implies
Lemma 1. There is a with .
Phase 2. Having more colors than positions, we can perform our binary search for a next correct position without using a pivot color. The corresponding simplified version of findNext is outlined as Algorithm 4.
| Algorithm 4: Function findNext for k > n |
![Games 11 00019 i004 Games 11 00019 i004]() |
Using that version of findNext also allows to simplify our main algorithm (Algorithm 3) by adapting lines 2 and 3, and, due to Lemma 1, skipping lines 4–7, as findNext can be already applied to find the first correct position. Thus, for the required number of queries to break the secret code we have: the initial queries, a call of the modified findNext for every but the last two positions and one or two final queries. This yields that the modified Mastermind Algorithm breaks the secret code in at most queries. □