Abstract
Mastermind is famous two-player game. The first player (codemaker) chooses a secret code which the second player (codebreaker) is supposed to crack within a minimum number of code guesses (queries). Therefore, the codemaker’s duty is to help the codebreaker by providing a well-defined error measure between the secret code and the guessed code after each query. We consider a variant, called Yes-No AB-Mastermind, where both secret code and queries must be repetition-free and the provided information by the codemaker only indicates if a query contains any correct position at all. For this Mastermind version with n positions and colors and , we prove a lower bound of and an upper bound of on the number of queries necessary to break the secret code. For the important case , where both secret code and queries represent permutations, our results imply an exact asymptotic complexity of queries.
MSC:
91A46
1. Introduction
Mastermind is a popular two-player board game invented by Mordecai Meirowitz and released in 1971 [1,2]. Its idea is that a codemaker chooses a secret code of fixed length n, where each position is selected from a set of k colors. The second player, codebreaker, has to identify the secret code by a finite sequence of corresponding code guesses (queries), each of which is replied with the number of matching positions and the number of further correct colors. The original game is played by picking pegs of different colors and placing them into rows with holes, where the number of rows (allowed queries) for the codebreaker is limited.
Generalizing the situation to arbitrarily many positions and colors, the codemaker selects a vector and the codebreaker gives in each iteration a query in form of a vector . In the original setting, the codemaker’s reply is the so called black-white error measure, consisting of a pair of numbers, where the first number, , is the number of positions in which x and y coincide and the second number, , is the number of additional colors which appear in both x and y, but at different positions. In this paper, we consider a variant, called Yes-No AB-Mastermind, which is defined by the following properties
- Both secret code and queries must be repetition-free. This property is indicated by the prefix AB and stems from the AB game, better known as “Bulls and Cows” (cf. [1]), which was even known prior to the commercial version of Mastermind with color repetitions.
- The provided information by the codemaker only answers the question whether or not a query contains any correct position at all. This property is introduced by us and referred to by the term “Yes-No”.
Related Works: Mastermind and its variants have been analyzed under different aspects. One of the first analyses of the commercial version with positions and colors is by Knuth [3] and shows that each code can be cracked in at most 5 queries. Even before the appearance of Mastermind as a commercial game, Erdős and Rényi [4] analyzed the asymptotic query complexity of a similar problem with two colors in 1963 to be . After Knuth’s analysis of the commercial game, many different variants of Mastermind with arbitrary code length n and number of colors k have been investigated. For example, Black-Peg Mastermind restricts its error measure between two codes x and y to the single value (i.e., the exact number of positions where both codes coincide). This version was introduced in 1983 by Chvátal [5] for the case , who provides a deterministic adaptive strategy using queries. Improved upper bounds for this variant and arbitrary n and k where given by Goodrich [6] () and later by Jäger and Peczarski [7] ( for and for ) but remained in the order of . Doerr et al. [8] provided a randomized codebreaker strategy that only needs queries in expectation and showed that this asymptotic order even holds for up to colors, if both black and white information is allowed. A first upper bound for AB Mastermind was given by Ker-I Ko and Shia-Chung Teng [9] for the case , i.e., secret code and queries represent permutations of . Their non-constructive strategy yields an upper bound of queries. A constructive strategy by El Ouali and Sauerland [10] reduced this upper bound by a factor of almost 2 and also included the case of Black-Peg AB-Mastermind. The term Black-Peg labels the situation that the error measure between secret code and queries is only “black” information, i.e., the number of coinciding positions, while the “white” information (see above) is omitted. El Ouali et al. [11] combined their upper bound of queries for and ) queries for with a lower bound of n queries, which is implied by a codemaker strategy. It improved the lower bound of by Berger et al [12]. However, a gap between and remains for this Mastermind variant. Some facts indicate that closing this gap means to improve both bounds. On the one hand, a careful consideration of the partition of the remaining searchspace with respect to all possible codemaker replies might yield a refined codemaker strategy and possibly increase the lower bound. On the other hand, overcoming the sequential learning process of the codebreaker’s binary search strategy might decrease the upper bound. The latter presumption is reinforced by the results of Afshani et al. [13], who consider another permutation-based variant of Mastermind. There, the secret code is a combination of a binary string and a permutation, (both of length n), queries are binary strings of length n, and the error measure returns the number of leading coincidences in the binary string with respect to the order of the permutation. For this setting, which is also a generalization of the popular leading ones test problem in black box optimization, the authors prove an exact asymptotic query complexity of for deterministic strategies but a randomized query complexity of .
One of the ultimate goals in the analysis of Mastermind variants is to prove the exact asymptotic query complexity. As mentioned above, closing the asymptotic gap between the lower bound and the upper bound is an unsolved problem for Black-Peg AB Mastermind. A related open question is whether the same asymptotic number of queries is required for both (Black-Peg) Mastermind with color repetition and (Black-Peg) AB Mastermind.
Our Contribution: We consider a new variant of AB-Mastermind which is more difficult to play for the codebreaker since the error-measure provided by the codemaker is less informative. Here, for a secret code y the answer to a query is “yes” if some of its positions coincide with the secret code, otherwise the answer is “no”. We first analyze the worst-case performance of query strategies for this Mastermind variant and give a lower bound of queries for , which becomes in the case . The lower bound even holds if the codebreaker is allowed to use repeated colors in his queries. We further present a deterministic polynomial-time algorithm that identifies the secret code. This algorithm is a modification of the constructive strategy of El Ouali et al. [11]. It returns the secret code in at most queries in the case and in less than queries in the case . For the important case , our results imply the exact asymptotic query complexity of . Since the considered “Yes-No” error measure implies a new variant of AB-Mastermind, there is no previous reference to compare our results to.
2. Results
2.1. Lower Bound on the Number of Queries
To simulate the worst case, we allow the codemaker to “cheat” in a way that after every query he may decide for a new secret code that is still in agreement with all information he gave so far.
Theorem 1.
Let , and . Every strategy for Yes-No AB-Mastermind needs at least queries in the worst case.
Proof.
We give a codemaker strategy that implies the lower bound. For let denote the set of secrets that are still possible after the i-th query has been answered, starting with . Let be the set of secrets that lead to a yes-answer to the -th query and the set of secrets that lead to a no-answer. The strategy of the codemaker in round is as follows:
- If , pick a secret from (and give the answer yes)
- Otherwise pick a secret from (and give the answer no)
By using this strategy, the codemaker achieves for every round i that
This implies . So, for any we have
which means that there are still at least two possible secrets left. Since
we obtain the claimed lower bound. □
Corollary 1.
Every strategy for Yes-No Permutation-Mastermind (the case ) needs at least
queries in the worst case.
We also note that the lower bound on the query complexity of Yes-No AB-Mastermind remains of the asymptotic order if the number of colors is polynomial in the number of positions (, P a polynomial).
2.2. Upper Bound on the Number of Queries
Theorem 2.
Let , and . For , there is a strategy for Yes-No AB-Mastermind that identifies every secret code in at most queries and for , there is a strategy that identifies every secret code in less than queries.
Corollary 2.
The exact asymptotic query complexity of Yes-No Permutation-Mastermind is .
The proof of Theorem 2 resembles the proof of a corresponding result concerning Black-Peg AB-Mastermind [11], except that the information whether a given query contains a correct but unidentified position is not derived directly but requires special querying outlined by Algorithm 1 below. In a nutshell (including both cases and ), the strategy consists of k distinct initial queries, each of which consists of the first n positions of a circularly shifted version of the vector . From the answers of the initial queries, we will be able to learn the secret code position-wise, keeping record about the positions that have already been identified. As long as there are consecutive initial queries a and b with the property that a coincides with the secret code in at least one yet unidentified position but b does not, we can apply a binary search for the next unidentified position in a, using further queries. Such initial queries a and b exist ever after one (usually after zero) but not all positions of the secret code have been identified.
Proof of Theorem 2.
The case : We give a constructive strategy that identifies the positions of the secret code one-by-one. In order to keep record about identified positions of the secret code we deal with a partial solution vector x that satisfies for all . We call the non-zero positions of x fixed and the zero-positions of x open. The fixed positions of x are the identified positions of the secret code. Remember, that for a query we denote by
the information if there is some position in which coincides with the secret code y. For Yes-No AB-Mastermind the related information whether a query contains a correct but unidentified position cannot always be derived directly but must be obtained by guessing one or two modifications of , rearranging those positions that coincide with the partial solution x. The required query procedure is summarized as Algorithm 1.
Example 1.
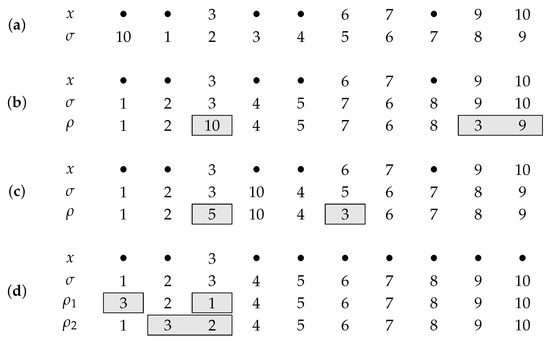
Figure 1 illustrates the four distinct cases that are considered by . In the first and easiest case (panel (a)) the actual query σ does not coincide with the partial solution x. Thus, σ contains a correct unidentified position if and only if it contains a correct position at all, i.e., . In the second case (panel (b)), σ and x coincide in more than one position, namely the positions with colors 3, 9 and 10. The modified query ρ is obtained from σ by rearranging these positions in a way that all identified positions get a wrong color while leaving all open positions of σ unchanged. This implies that . Panels (c) and (d) deal with the case that σ and x coincide in exactly one position, say i. If x already contains a further non-zero position j, we obtain ρ from σ by swapping positions i and j in σ (the positions with colors 3 and 5 in panel (c)). Again, we obtain that . Finally, if position i is the only yet identified position of the secret code we have to ask two different modified queries to derive (panel (d)). We obtain the two queries and , each by swapping the identified position (here 3) with another position in σ, (here with 1 and 2, respectively). While the color of the identified position is wrong in both modifications and , every other position of σ coincides with the corresponding position of at least one modification. Therefore, if and only if .

Figure 1.
Illustrating the cases considered by . Panel (a): query does not coincide with the partial solution x; . Panel (b): and x coincide in more than one position; rearranges these positions of ; . Panel (c): and x coincide in exactly one position i, but more positions are identified already; is obtained from by swapping position i with another identified position j; . Panel (d): Exactly one position is identified and appears to be correct in ; two modified queries and must be defined, each by swapping the identified position with another one; if and only if .
| Algorithm 1: Function infoP |
 |
The codebreaker strategy that identifies the secret code y has two phases. In the first phase the codebreaker guesses an initial sequence of n queries that has a predefined structure. In the second phase, the structure of the initial sequence and the corresponding information by the codemaker enable us to identify correct positions of the secret code one after another, each by using a binary search. We denote the vector x restricted to the set with , .
Phase 1 Consider the n queries, , that are defined as follows: represents the identity map and for , we obtain from by a circular shift to the right. For example, if , we have , , and . The codebreaker guesses .
Phase 2. Now, the codebreaker identifies the values of y one after another, using a binary search procedure, that we call findNext. The idea is to exploit the information that for we have , , and . findNext is used to identify the second correct position to the last correct position in the main loop of the algorithm.
After the first position of y has been found and fixed in x, there exists a such that . As long as we have open positions in x, we can either find a with but and set , or we have but and set and . We call such an index j an active index. Let j be an active index and r its related index. Let c be the color of some position of y that is already identified and fixed in the partial solution x. With and we denote the position of color c in and , respectively. The color c serves as a pivot color for identifying a correct position m in that is not fixed, yet. There are two possible modes for the binary search that depend on the fact if . The mode is indicated by a Boolean variable and determined by lines 5–9 of findNext. Clearly, if . Otherwise, the codebreaker guesses
By the information we obtain that . We further know that every open color has a wrong position in . For that reason, implies that . The binary search for the exact value of m is done in the interval , where m is initialized as n and as
(lines 10–15 of findNext). In order to determine if there is an open correct position on the left side of the current center ℓ of in we can define a case dependent query:
In the first case, the first positions of coincide with those of . The remaining positions of cannot coincide with the corresponding positions of the secret code if they have not been fixed, yet. This is because the ℓ-th position of has the already fixed value c, positions to coincide with the corresponding positions of which satisfies and the remaining positions have been checked to be wrong in this case (cf. former definition of in line 5 and line 9, respectively). Thus, there is a correct open position on the left side of ℓ in , if and only if . In the second case, the same holds for similar arguments. Now, if there is a correct open position to the left of ℓ, we update the binary search interval by . Otherwise, we update by .
| Algorithm 2: Function findNext |
 |
Example 2.
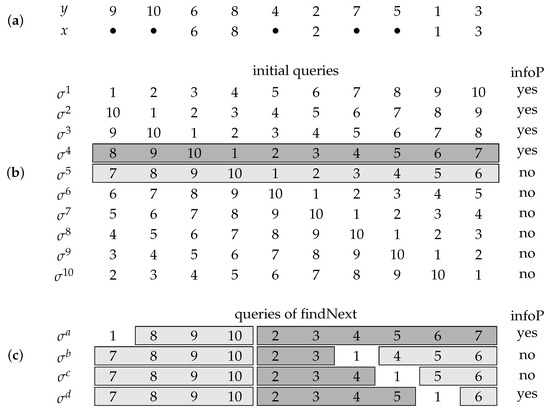
Suppose, that for the secret code y and the partial solution x are given as in the top panel of Figure 2 and that we have first identified the position with color 1, such that 1 is our pivot color. The initial 10 queries together with their current measures are given in the mid panel of Figure 2. We see that the highlighted queries, and , can be used for the binary search with findNext, since has a correct not yet identified position but has not. So the active indices are and and the corresponding pivot color positions in and are and . The first query of findNext (cf. lower panel of Figure 2) is . It begins with the pivot color, followed by the first 3 positions of (positions 2 to 4 of ) and positions 5 to 10 of (cf. line 7 of findNext). Since , the left most correct but unidentified position in is none of its first 4 positions. Thus, the binary search is continued in the interval . It is realized by queries , , and , which are composed according to line 20 of findNext (in this case), and finally identifies position 8 with color 5 of the secret code (generally the position left to the left most pivot color position that receives the answer “yes” in the binary search).

Figure 2.
Panel (a): secret code y and partial solution vector x. Panel (b): the initial queries and their responses , indicating if a query and the secret code coincide in any position that has not been identified, yet (i.e., in any 0-position of x). Panel (c): binary search queries to identify the next secret position. The highlighted subsequences correspond to the subsequences of the initial queries that have been selected to apply the binary search.
The Main Algorithm. The main algorithm is outlined as Algorithm 3.
It starts with an empty partial solution and finds the positions of the secret code y one-by-one. The vector v keeps record about which of the initial queries coincides with the secret code y in some open position. Thus, v is initialized by , . The main loop always requires an active index. For that reason, if for all in the beginning, we first identify the correct position in (which is unique in this case) by queries (each swapping two positions of ) and update x and v, correspondingly. After this step, there will always exist an active index. Every call of findNext in the main loop augments x by a correct solution value. One call of findNext requires at most queries if the partial solution x contains more than one non-zero position, and at most queries (two queries for each call of infoP) if x has exactly one non-zero position. Thus, Algorithm 3 does not need more than queries to break the secret code inclusive the initial queries, queries to find the first correct position, calls of findNext and 2 final queries.
| Algorithm 3: Codebreaker Strategy for Permutations |
 |
The case : Let be the code that must be found. We use the same notations as above.
Phase 1. Consider the k queries , where represents the identity map on and for , we obtain from by a circular shift to the right. We define k codes by , . For example, if and , we have , , , and . Within those k codes, every color appears exactly once at every position and, thus, there are at least initial queries that do not contain any correct position. Since , this implies
Lemma 1.
There is a with .
Phase 2. Having more colors than positions, we can perform our binary search for a next correct position without using a pivot color. The corresponding simplified version of findNext is outlined as Algorithm 4.
| Algorithm 4: Function findNext for k > n |
 |
Using that version of findNext also allows to simplify our main algorithm (Algorithm 3) by adapting lines 2 and 3, and, due to Lemma 1, skipping lines 4–7, as findNext can be already applied to find the first correct position. Thus, for the required number of queries to break the secret code we have: the initial queries, a call of the modified findNext for every but the last two positions and one or two final queries. This yields that the modified Mastermind Algorithm breaks the secret code in at most queries. □
3. Conclusions
We showed that deterministic algorithms for the identification of a secret code in Black-Peg AB-Mastermind can be modified and applied to Yes-No AB-Mastermind. The latter is a new variant of AB-Mastermind which is harder to play for the codebreaker since a less informative error measure is provided. The Yes-No measure only returns the information whether a query and the secret code coincide in any position, while the Black-Peg measure is the number of positions in which both codes coincide. Nevertheless, we proved that the best known asymptotic upper bound for Black-Peg AB-Mastermind does also apply to Yes-No AB-Mastermind, by adapting the corresponding constructive querying strategy. Utilizing a simple codemaker strategy, we further derived corresponding lower bounds for Yes-No AB-Mastermind. Another challenge with AB-Mastermind is that no color repetition is allowed in a query whereas most strategies for other Mastermind variants exploit the property of color repetition. While for most Mastermind variants there is a gap between lower and upper bounds on the worst case number of queries to break the secret code, our results imply that this number is for the most popular case of Yes-No AB-Mastermind, which is also referred to as Yes-No Permutation-Mastermind. The same is true for the case with constant c. To our knowledge, this result is a first exact asymptotic query complexity proof for a multicolor Mastermind variant, where both secret code and queries are chosen from the same set, here .
A future challenge will be studying the static variant of Yes-No AB-Mastermind (where the codebreaker must give all but one queries in advance of codemaker’s answers). Lower and upper bounds for static Black-Peg AB-Mastermind were provided as and , respectively [14].
Codeavailability
We provide Matlab/Octave implementations of the codebreaker strategy via GitHub, a permanent version of which is archived in a public zenodo repository [15].
Author Contributions
Conceptualization, M.E.O. and V.S.; methodology, M.E.O.; software, V.S.; validation, M.E.O. and V.S; writing—original draft preparation, M.E.O. and V.S.; writing—review and editing, M.E.O. and V.S.; visualization, V.S.; All authors have read and agreed to the published version of the manuscript.
Funding
This research received financial support by DFG within the funding programme Open Access Publizieren.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Wikipedia Website about Mastermind. Available online: https://en.wikipedia.org/wiki/Mastermind_(board_game) (accessed on 27 March 2020).
- Wikipedia Website about Mordecai Meirowitz. Available online: https://en.wikipedia.org/wiki/Mordecai_Meirowitz (accessed on 27 March 2020).
- Knuth, D.E. The computer as a master mind. J. Recreat. Math. 1977, 9, 1–5. [Google Scholar]
- Erdős, P.; Rényi, C. On Two Problems in Information Theory. Publ. Math. Inst. Hung. Acad. Sci. 1963, 8, 229–242. [Google Scholar]
- Chvátal, V. Mastermind. Combinatorica 1983, 3, 325–329. [Google Scholar] [CrossRef]
- Goodrich, M.T. On the algorithmic complexity of the Mastermind game with black-peg results. Inf. Process. Lett. 2009, 109, 675–678. [Google Scholar] [CrossRef]
- Jäger, G.; Peczarski, M. The number of pessimistic guesses in Generalized Black-peg Mastermind. Inf. Process. Lett. 2011, 111, 933–940. [Google Scholar] [CrossRef]
- Doerr, B.; Doerr, C.; Spöhel, R.; Thomas, H. Playing Mastermind with Many Colors. J. ACM 2016, 63, 1–23. [Google Scholar] [CrossRef]
- Ko, K.; Teng, S. On the Number of Queries Necessary to Identify a Permutation. J. Algorithms 1986, 7, 449–462. [Google Scholar] [CrossRef]
- El Ouali, M.; Sauerland, V. Improved Approximation Algorithm for the Number of Queries Necessary to Identify a Permutation. In Proceedings of the 24th International Workshop on Combinatorial Algorithms (IWOCA 2013), Rouen, France, 10–12 July 2013; Lecroq, T., Mouchard, L., Eds.; Number 8288 in Lecture Notes in Computer Science. Springer: Berlin, Germany, 2013; pp. 443–447. [Google Scholar]
- El Ouali, M.; Glazik, C.; Sauerland, V.; Srivastav, A. On the Query Complexity of Black-Peg AB-Mastermind. Games 2018, 9, 2. [Google Scholar] [CrossRef]
- Berger, A.; Chute, C.; Stone, M. Query Complexity of Mastermind Variants. arXiv 2016, arXiv:1607.04597. [Google Scholar] [CrossRef]
- Afshani, P.; Agrawal, M.; Doerr, B.; Doerr, C.; Larsen, K.G.; Mehlhorn, K. The query complexity of a permutation-based variant of Mastermind. Discret. Appl. Math. 2019, 260, 28–50. [Google Scholar] [CrossRef]
- Glazik, C.; Jäger, G.; Schiemann, J.; Srivastav, A. Bounds for Static Black-Peg AB Mastermind. In Proceedings of the 11th International Conference on Combinatorial Optimization and Applications (COCOA 2017), Part II, Shanghai, China, 16–18 December 2017; Gao, X., Du, H., Han, M., Eds.; Number 10628 in Lecture Notes in Computer Science. Springer: Berlin, Germany, 2017; pp. 409–424. [Google Scholar] [CrossRef]
- El Ouali, M.; Sauerland, V. GitHub repositry yn-ab-mastermindv1.0: Codebreaker strategies for Yes-No AB-Mastermind (Matlab/Octave). arXiv 2020, arXiv:2003.11538. [Google Scholar] [CrossRef]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).