Quality of Service (QoS) Management for Local Area Network (LAN) Using Traffic Policy Technique to Secure Congestion
Abstract
1. Introduction
2. Related Works
2.1. QoS and Network Convergence through Throughput
2.2. QoS Based on Bandwidth Utilization
2.3. Online Sequential Extreme Learning Machine
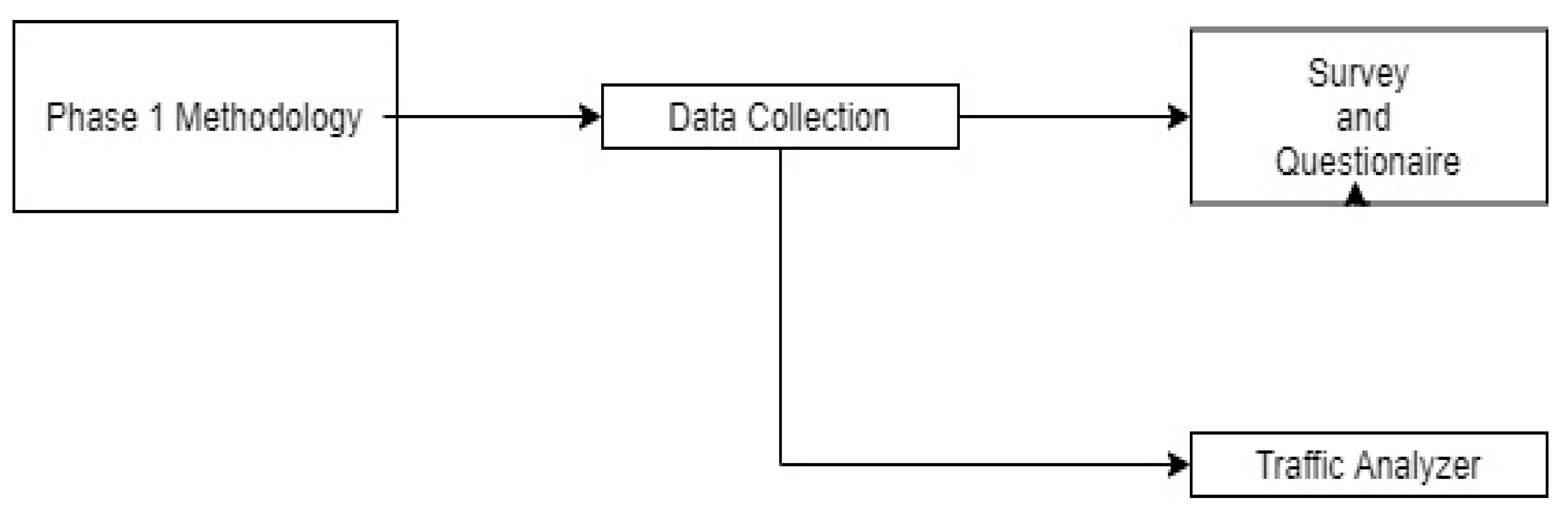
3. Methodology
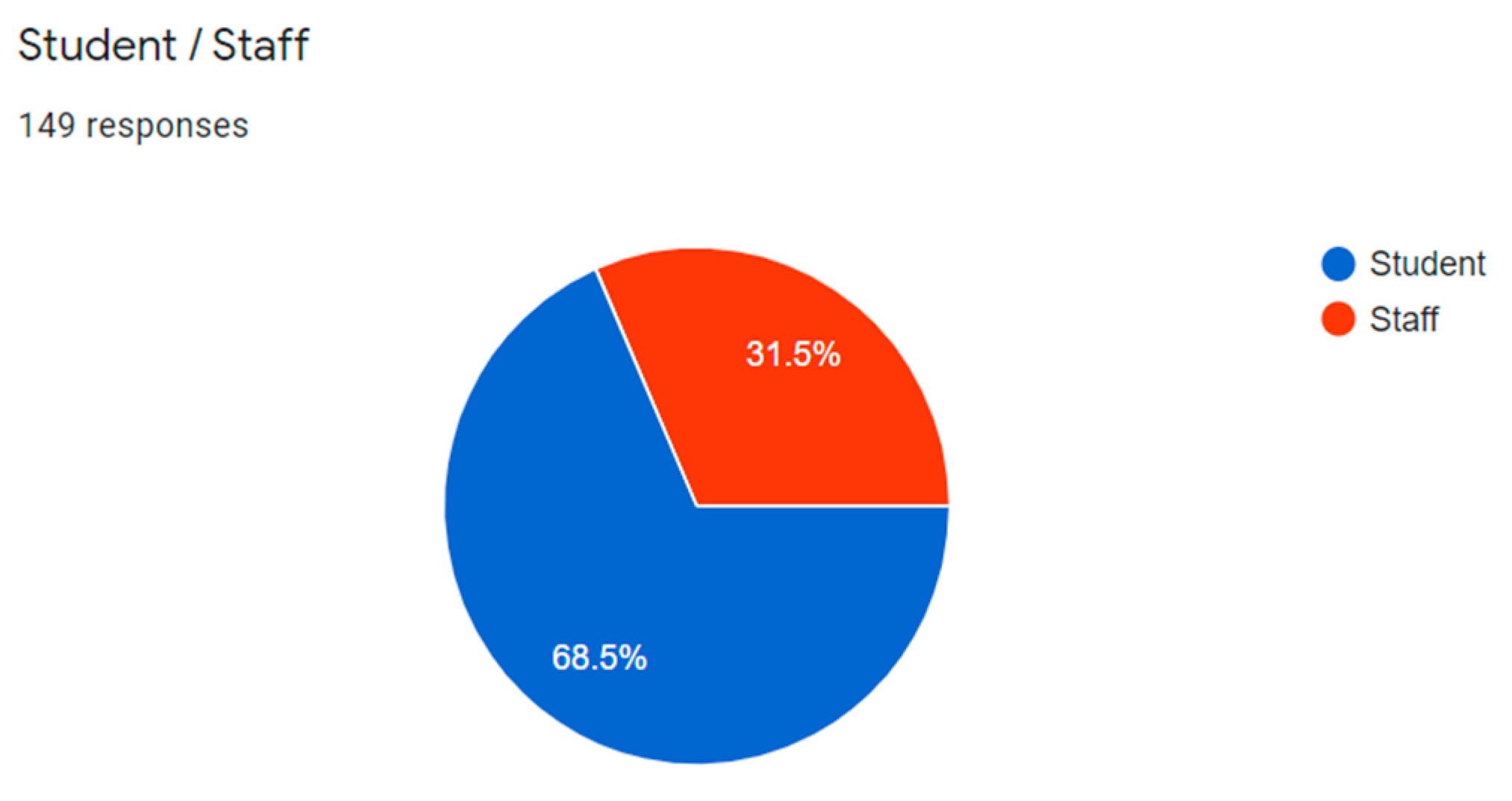
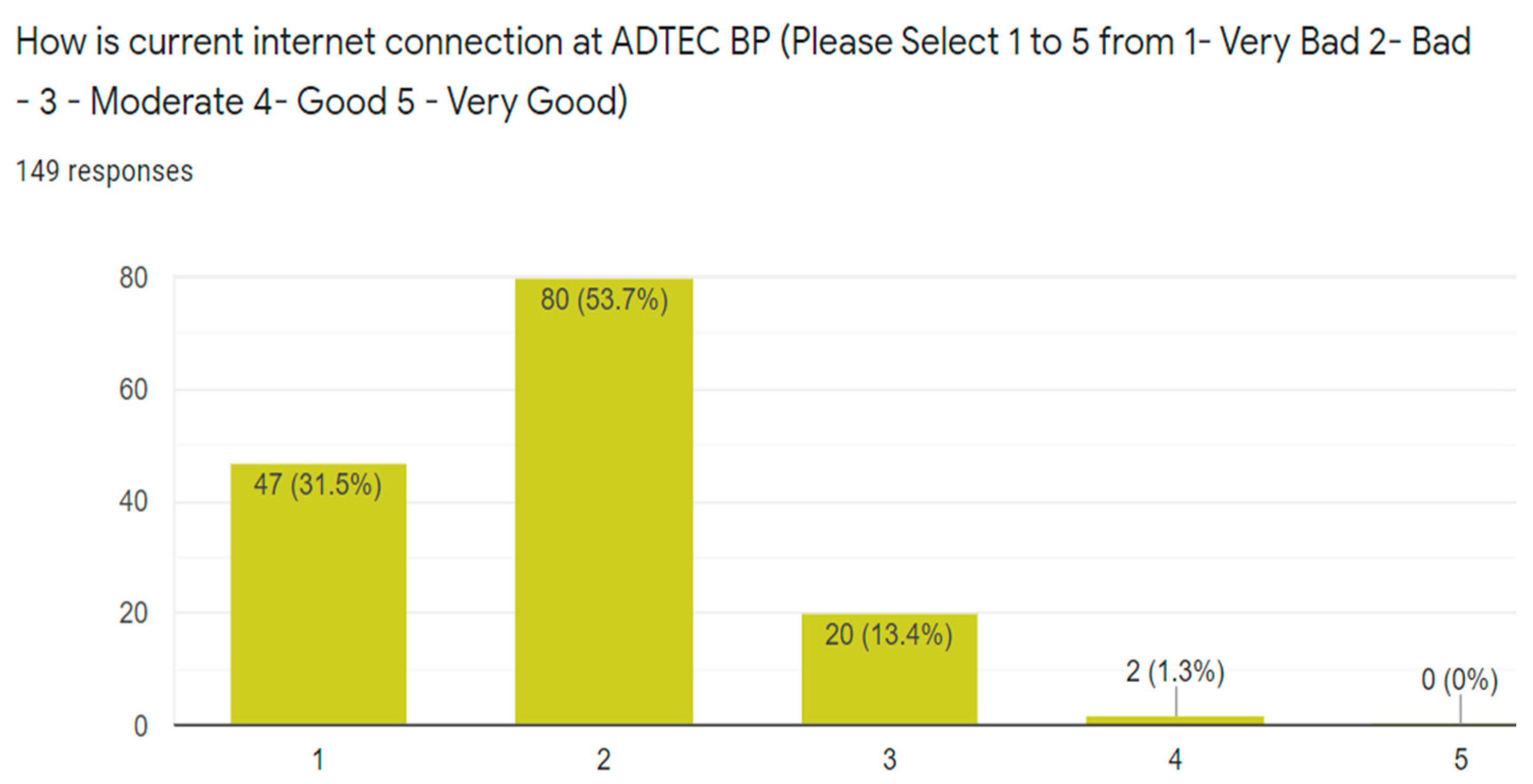
3.1. Phase 1—Data Collection and Survey
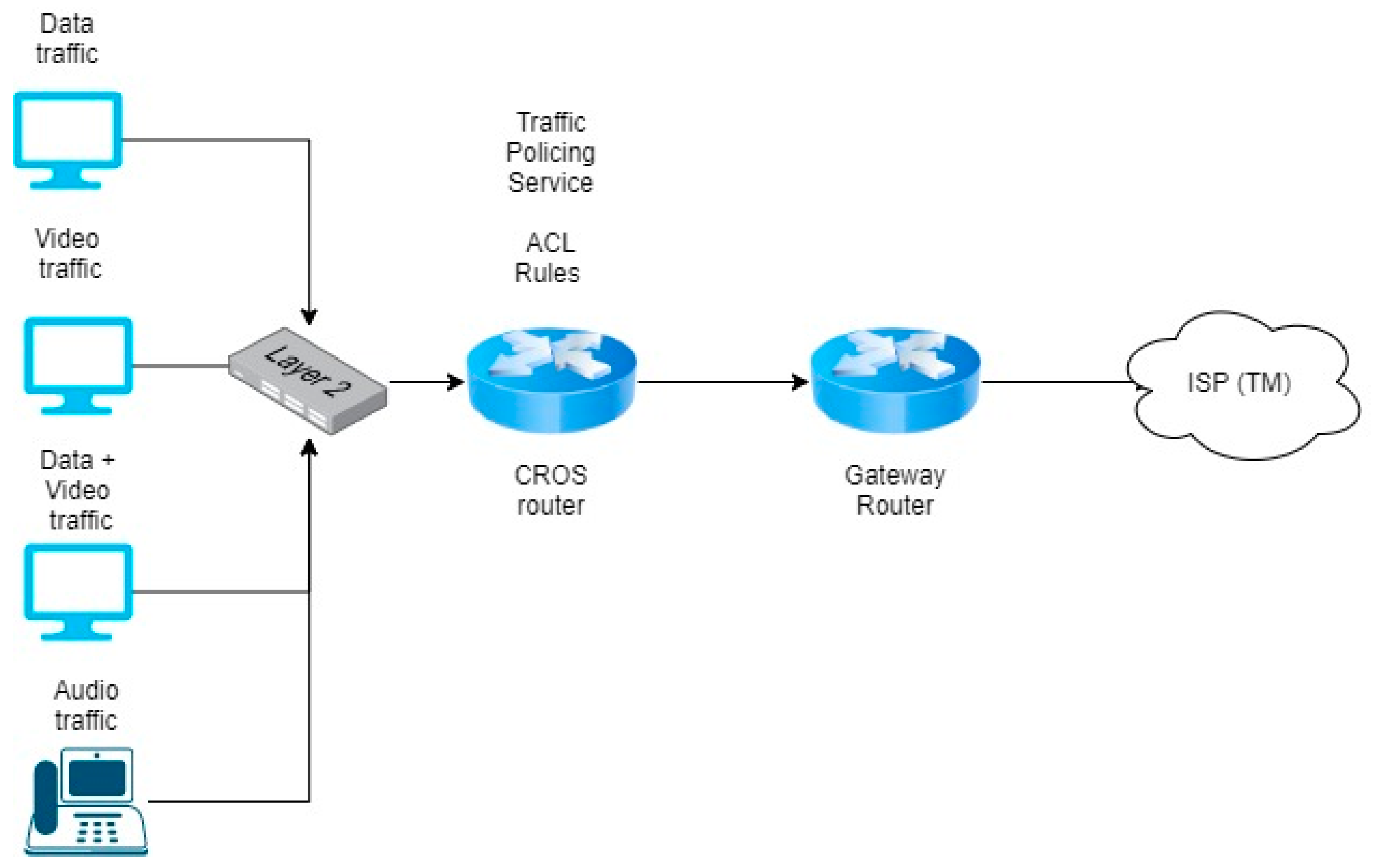
3.2. Phase 2—CISCO Router-on-a-stick Cross-Origin Resource Sharing (CORS) Development
- (a)
- Test 1: No classification and policy. The FIFO queuing discipline without any rules on the router configuration is used for all incoming packet data. This discipline is the baseline for comparing transmission control protocol (TCP) and user datagram protocol (UDP) testing. None of the traffic is classified or remarked with any policy.
- (b)
- Test 2: Traffic classification method. This second methodology is based on the classification of the packets at the ingress router, which are categorized on the basis of their service classes. After grouping, the packets are differentiated depending on their values; packets that contain streaming data after the classification received high priority transmission. This testing, which mainly focuses on the classification of the packet, can be applied only by using a single TCP stream of a packet.
- (c)
- Test 3: Traffic policing method. This step aims to inspect, classify, and categorize the packets that arrive at the incoming port of the router to ensure that they will have unique differentiated services code point values. The remarking process is executed after the categorization at the egress router and each packet obtained is assigned its corresponding ToS value. Although the packet has been remarked, it can still obtain an agreement to enter the neighboring router. After exiting the egress router, all packets are remarked on the basis of the information that has been previously agreed on.
3.3. CROS Analysis
4. Results and Discussion
4.1. Test 1: Benchmark Testing
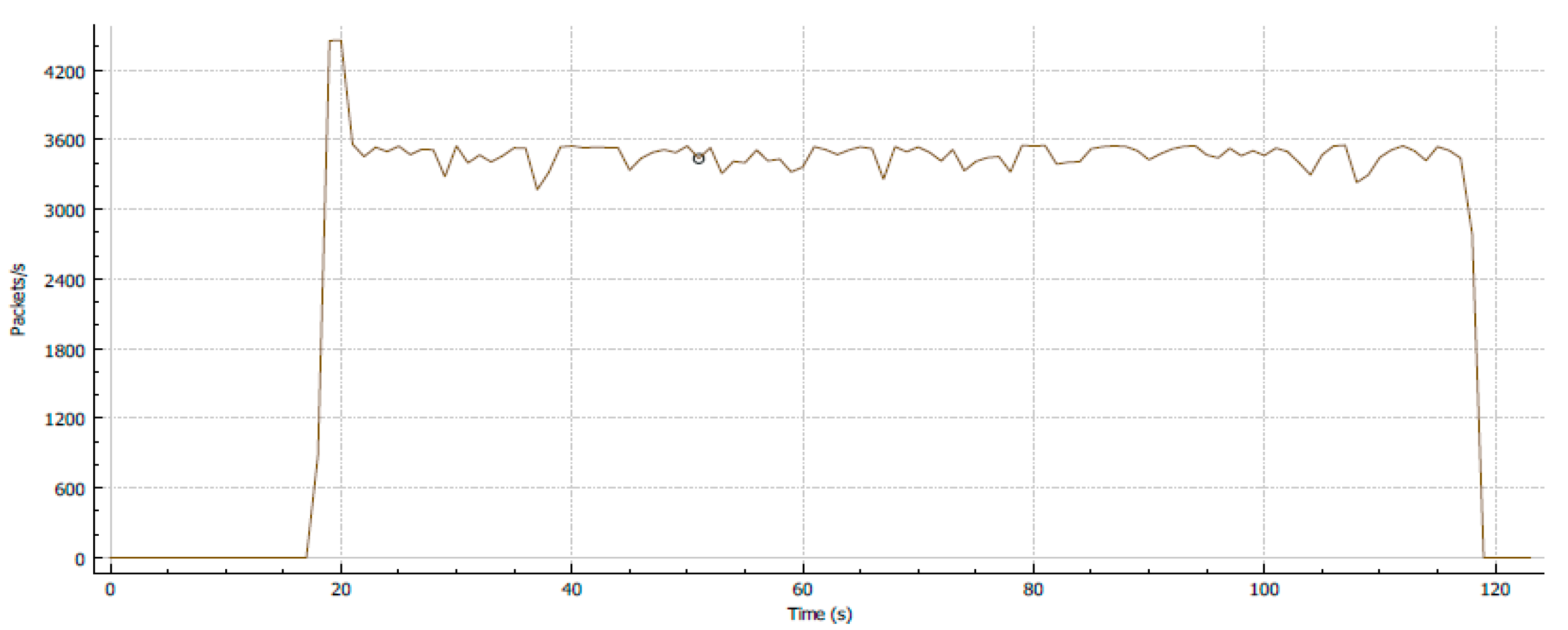
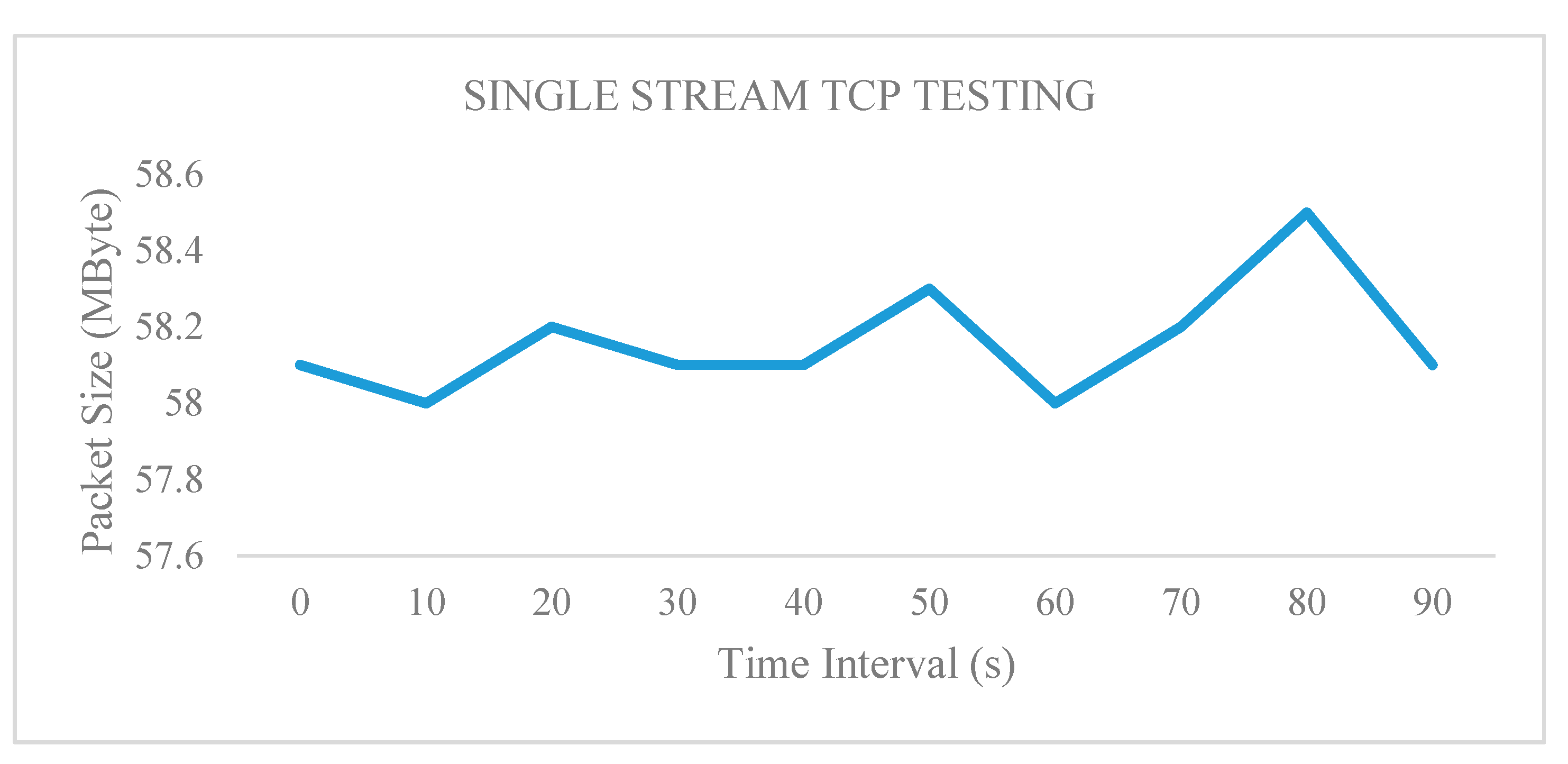
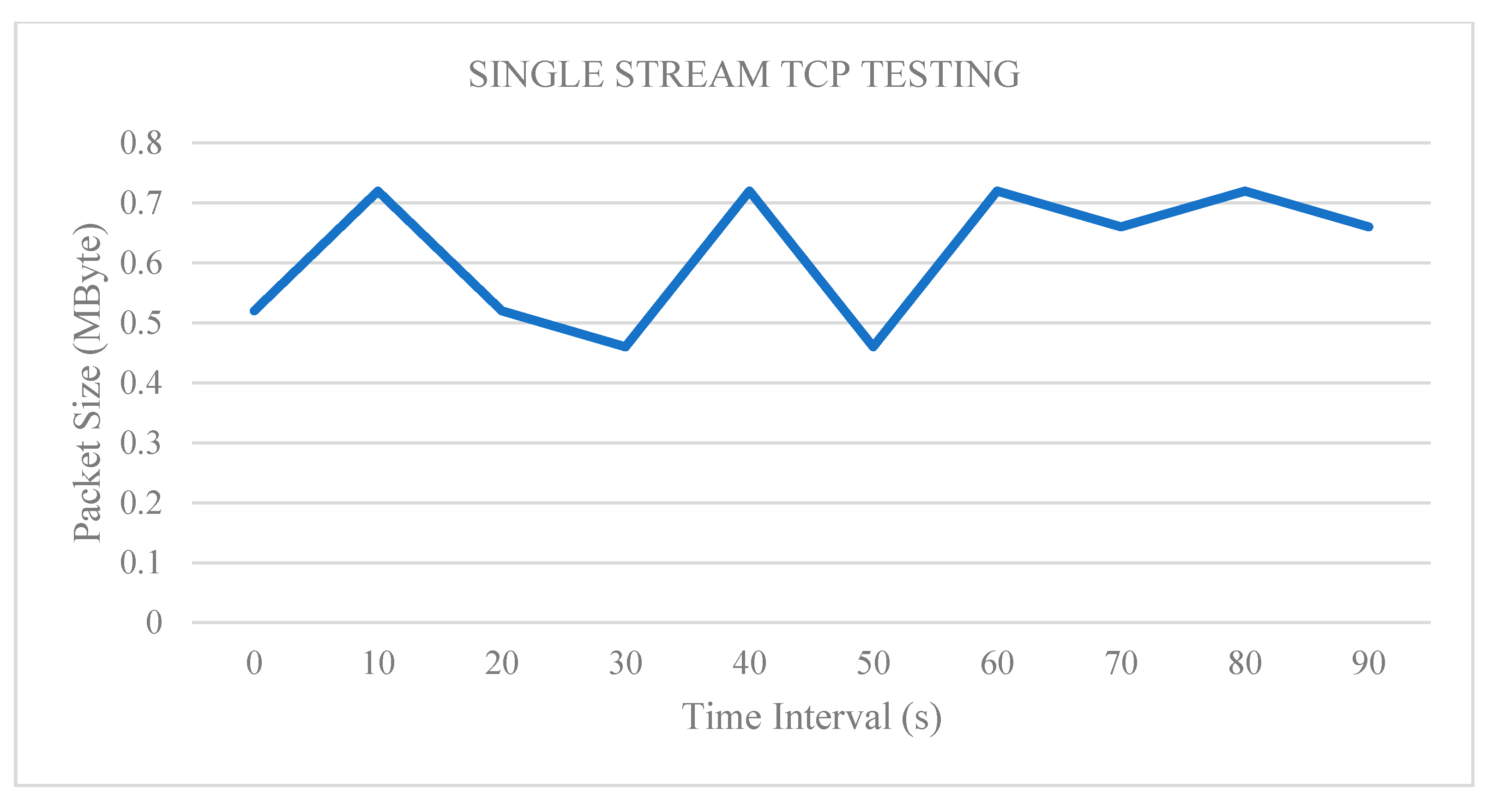
4.1.1. Test 1: Single Parallel Stream Implementation
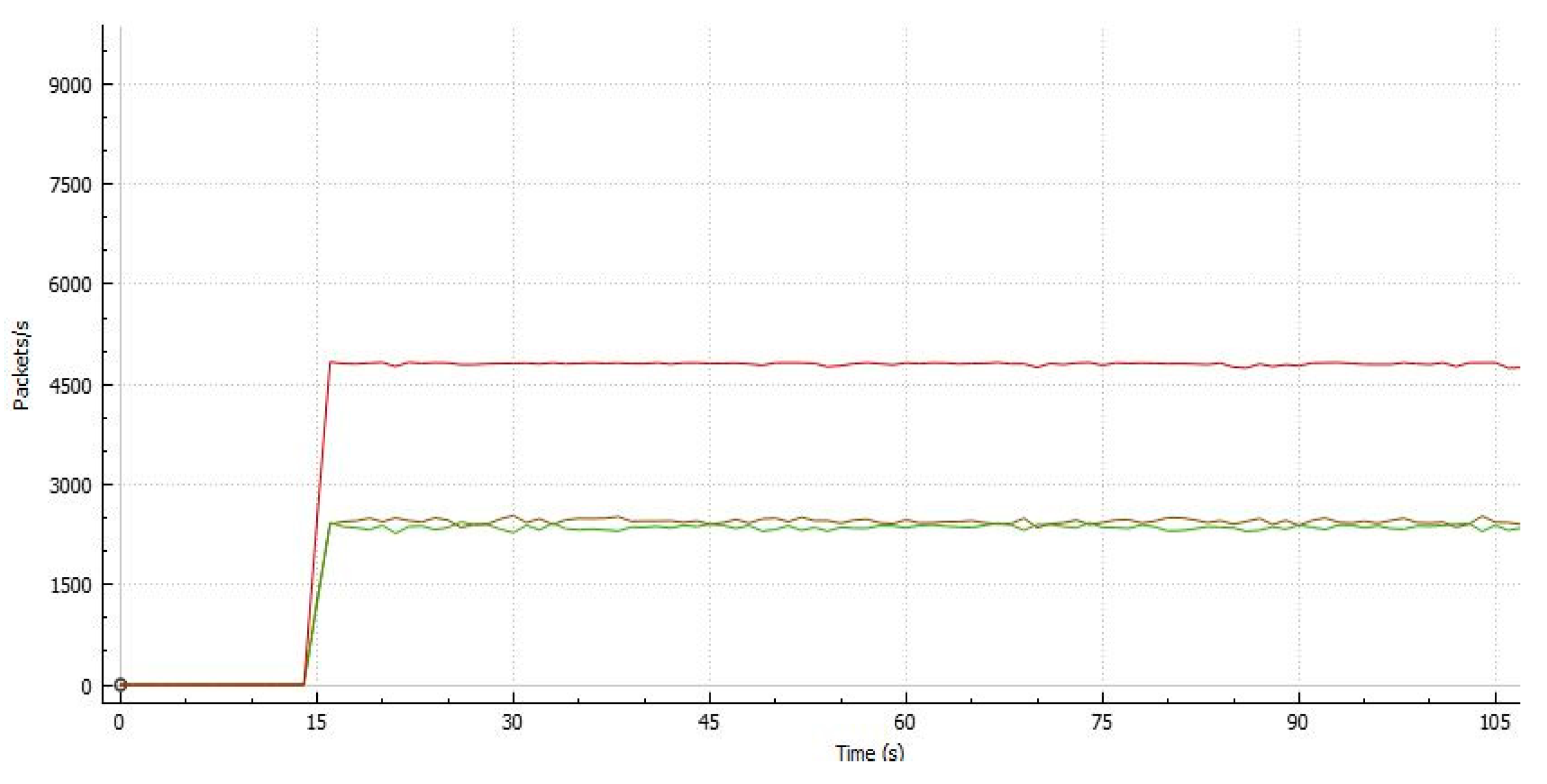
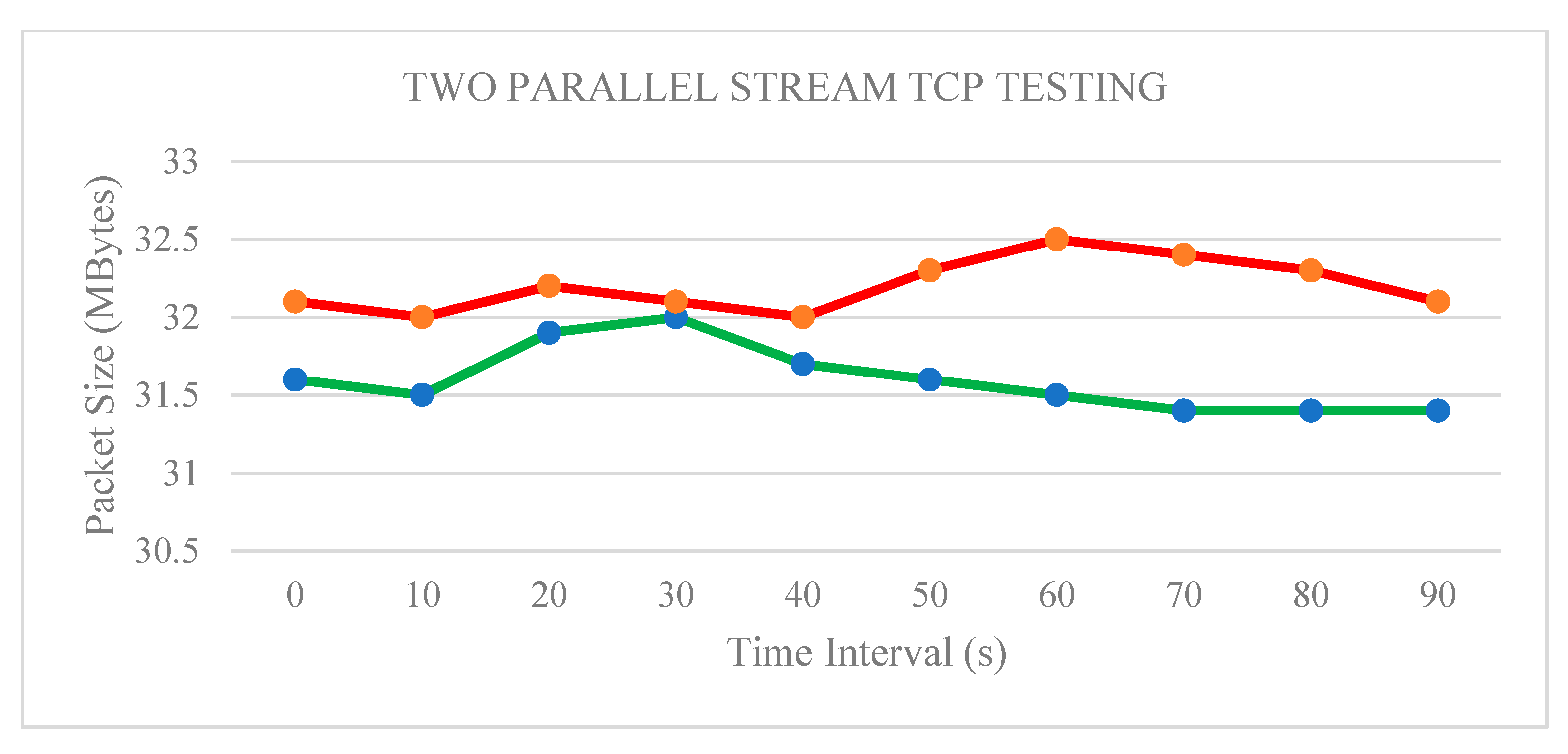
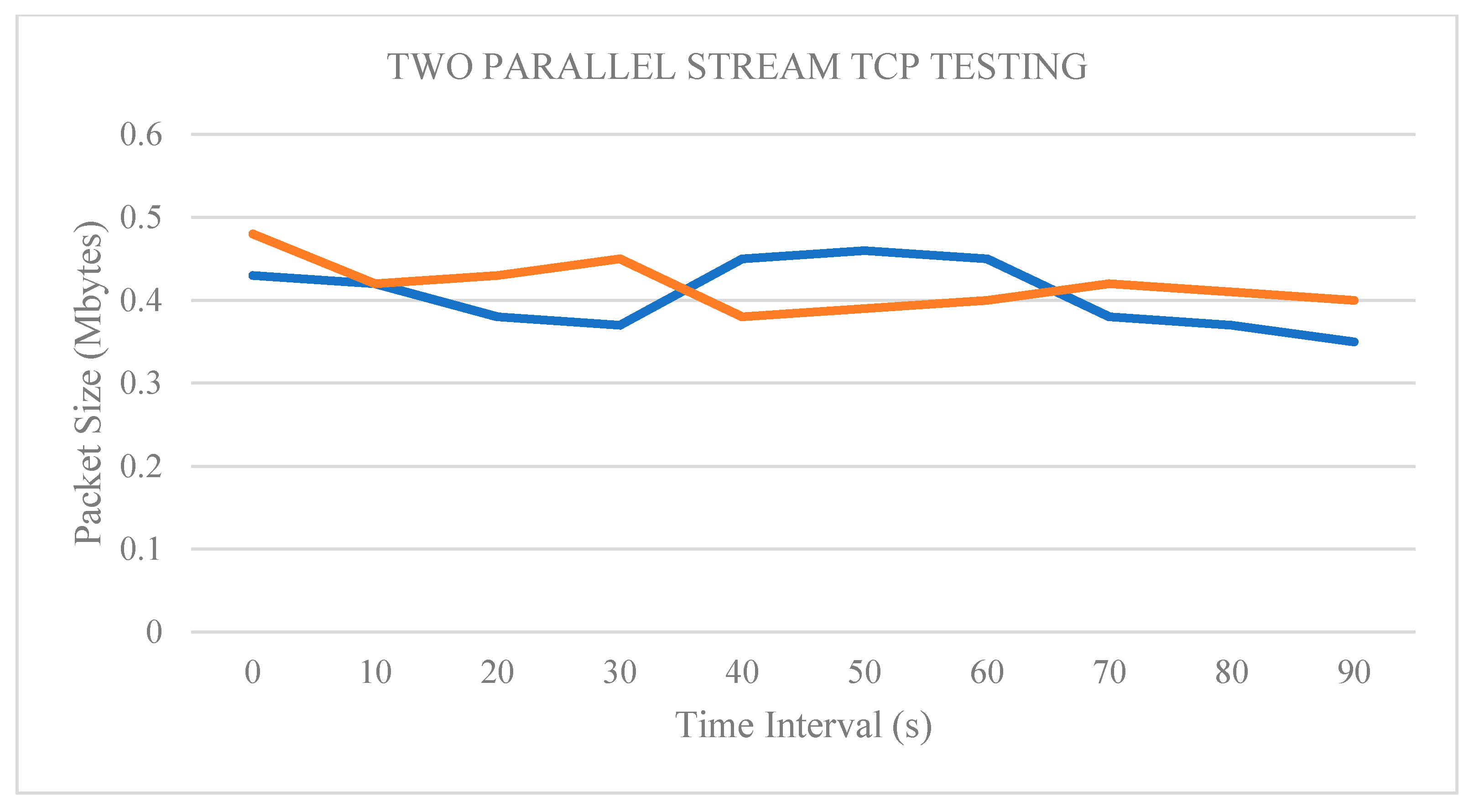
4.1.2. Two Parallel Stream Implementation
4.1.3. Three Parallel Stream Implementation
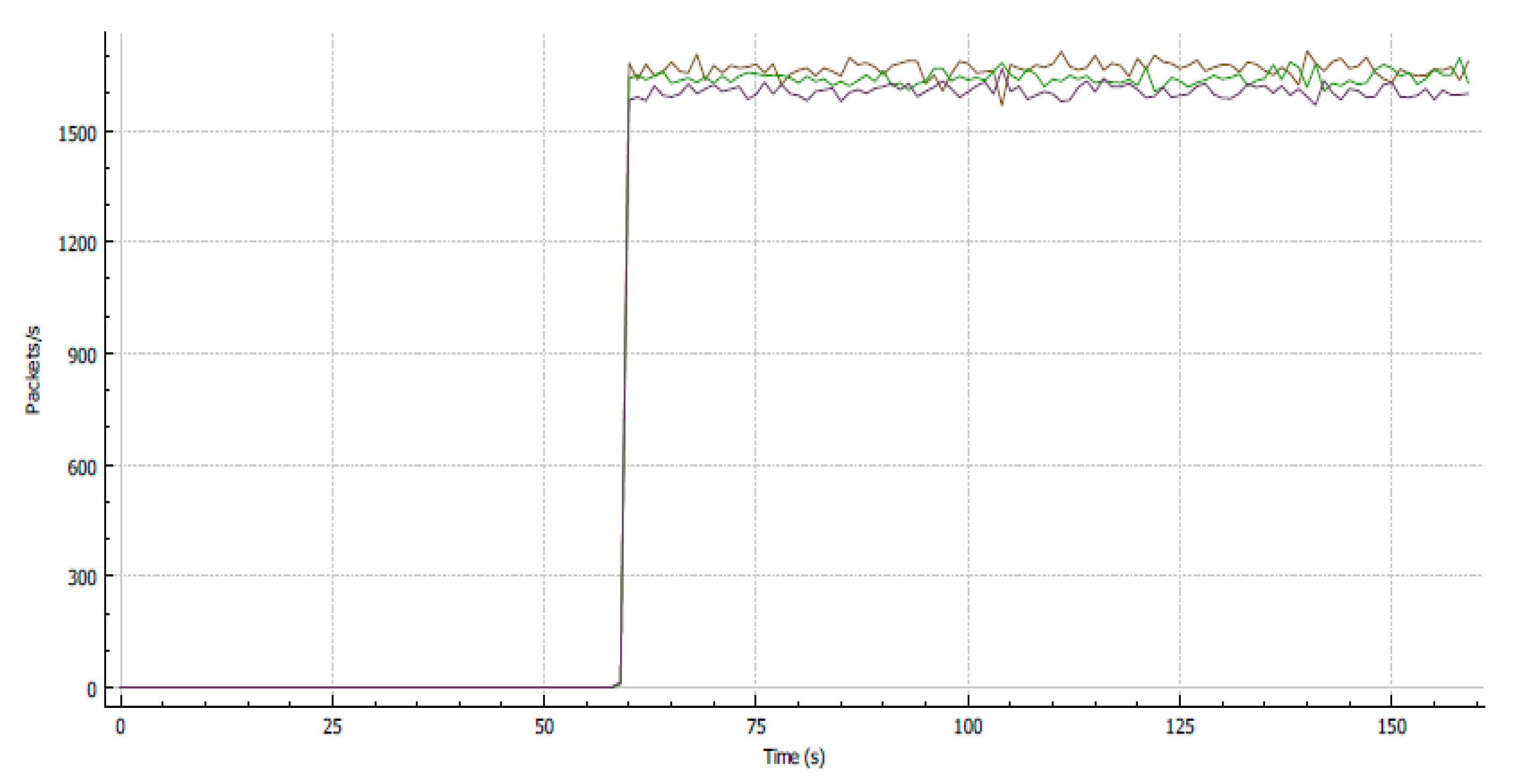
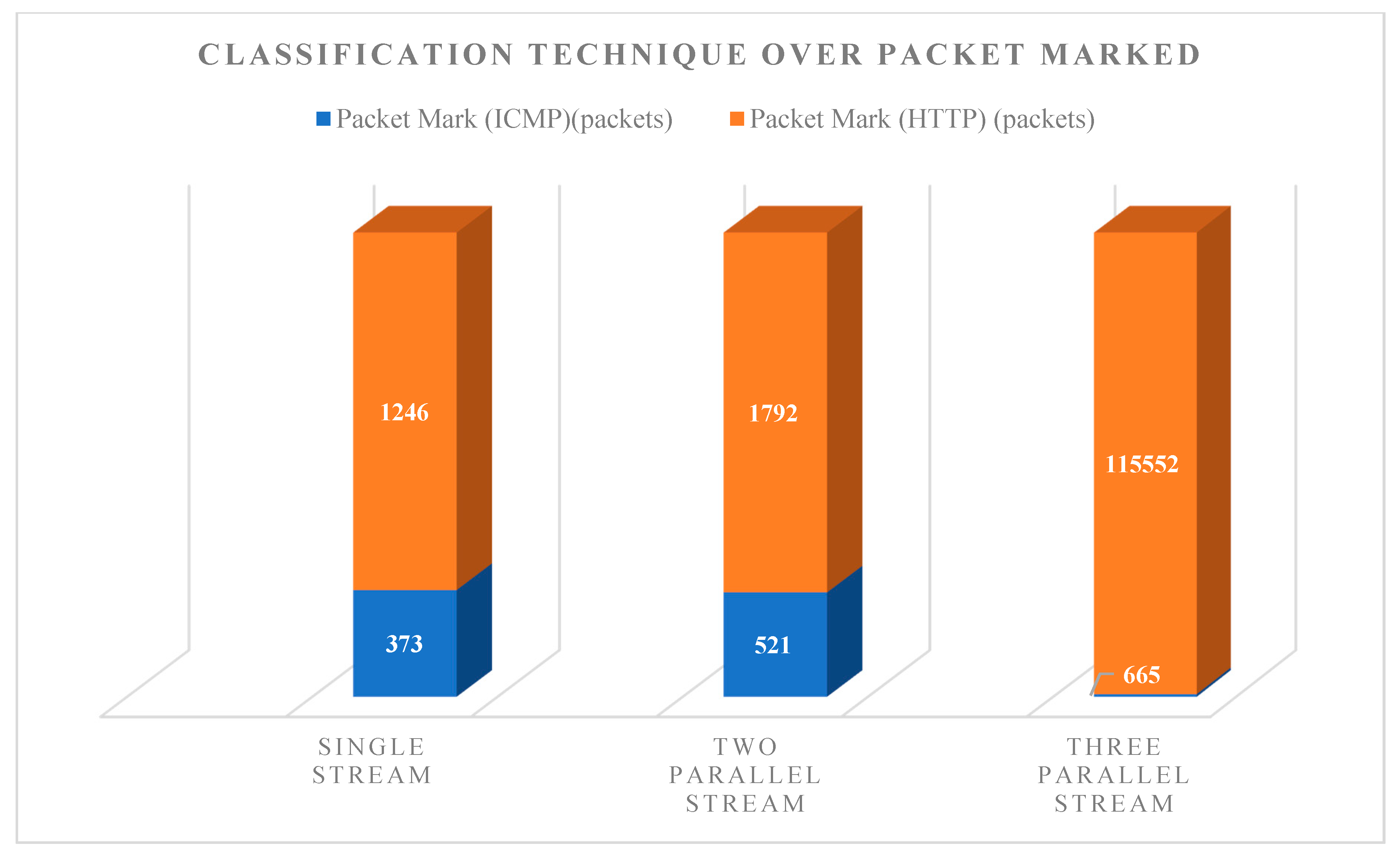
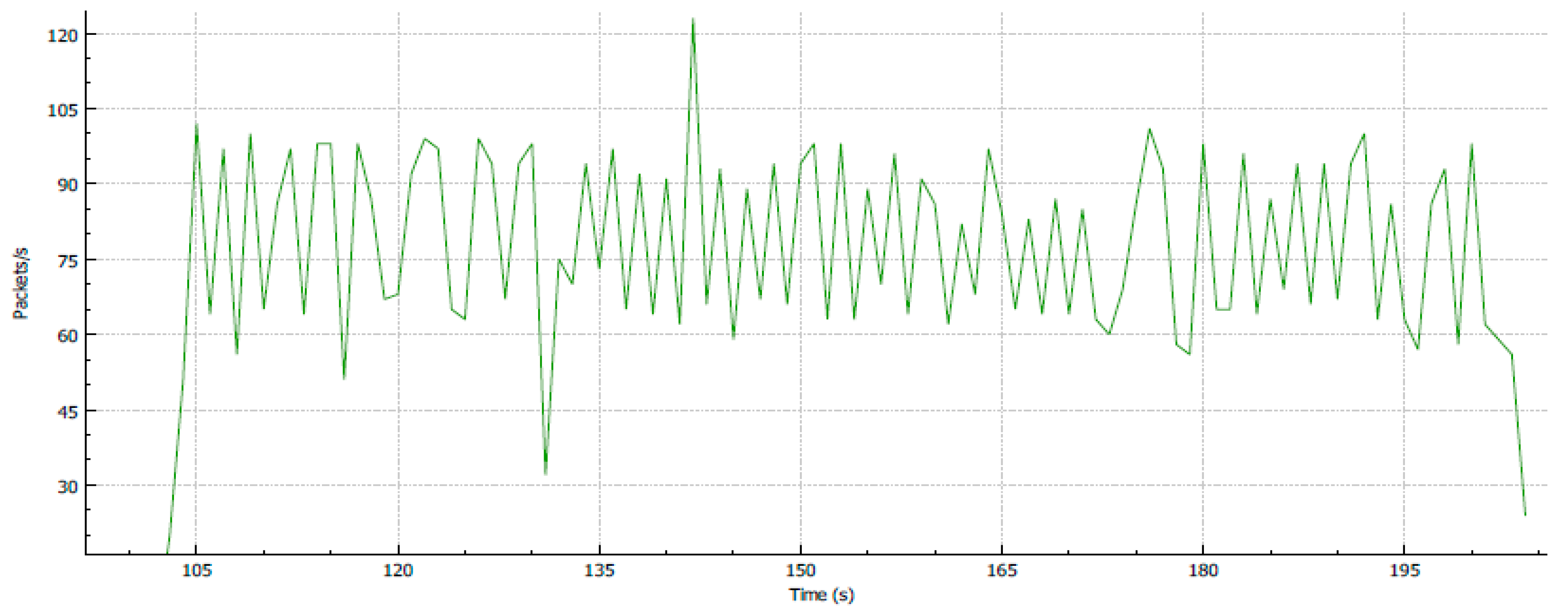
4.2. Test 2: Traffic Classification Method
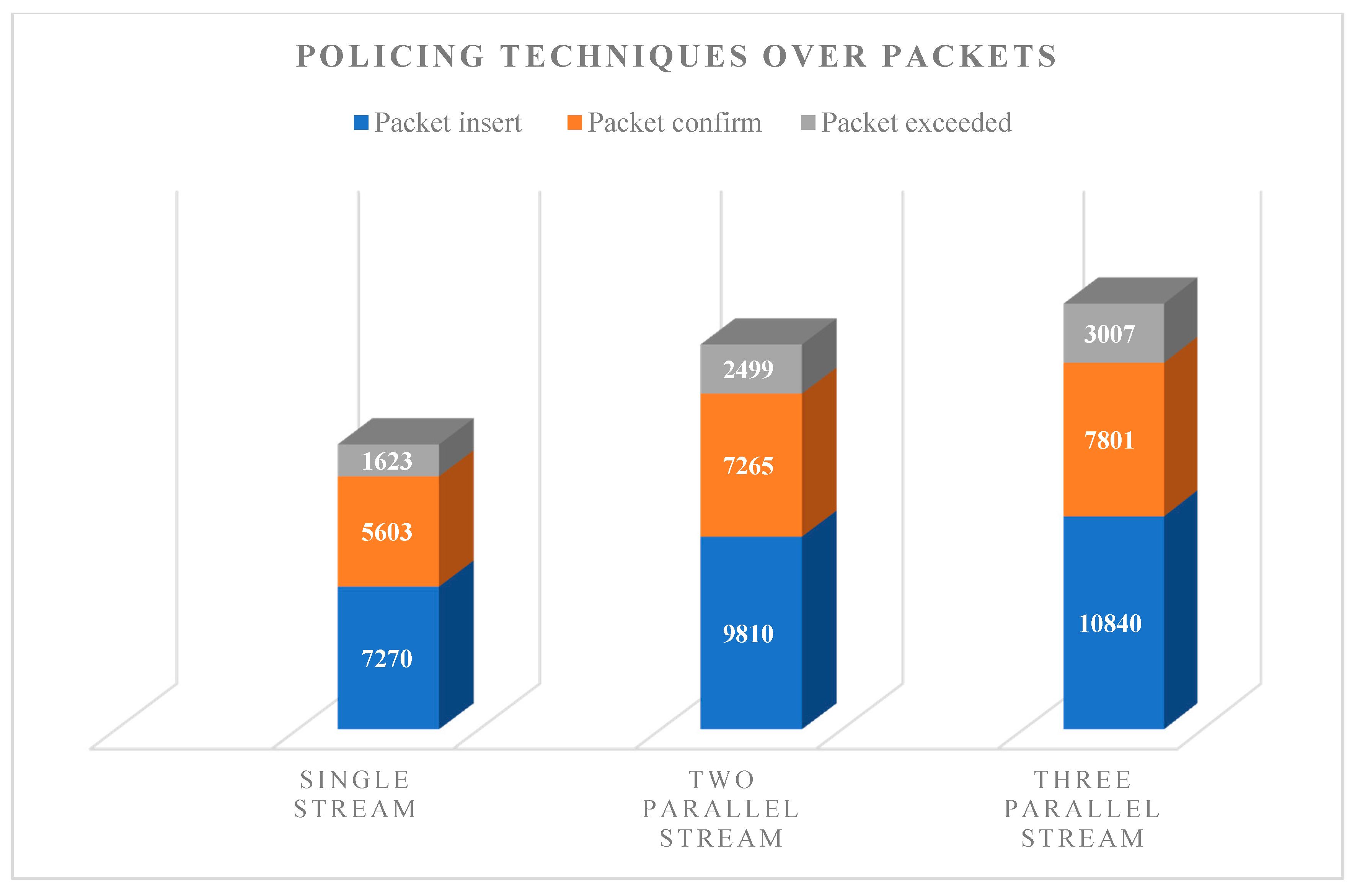
4.3. Test 3: Traffic Policing Method
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Dey, P.K.; Canbaz, M.A.; Yuksel, M.; Gunes, M.H. On correlating ISP topologies to their businesses. In Proceedings of the IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–7. [Google Scholar]
- Marcon, M.; Dischinger, M.; Gummadi, K.P.; Vahdat, A. The local and global effects of traffic shaping in the internet. In Proceedings of the Third International Conference on Communication Systems and Networks (COMSNETS 2011), Bangalore, India, 4–8 January 2011; pp. 1–10. [Google Scholar]
- AL-Khaleefa, A.S.; Ahmad, M.R.; Muniyandi, R.C.; Malik, R.F.; Isa, A.A.M. Optimized authentication for wireless body area network. J. Telecommun. Electron. Comput. Eng. 2018, 10, 137–142. [Google Scholar]
- Jubair, M.A.; Mostafa, S.A.; Muniyandi, R.C.; Mahdin, H.; Mustapha, A.; Hassan, M.H.; Mahmoud, M.; Al-Jawhar, Y.; Salih, A.; Mahmood, A. Bat optimized link state routing protocol for energy-aware mobile ad-hoc networks. Symmetry 2019, 11, 1409. [Google Scholar] [CrossRef]
- Bolla, R.; Carrega, A.; Repetto, M.; Robino, G. Improving efficiency of edge computing infrastructures through orchestration models †. Computers 2018, 7, 36. [Google Scholar] [CrossRef]
- Zakariyya, I.; A Rahman, M.N. Bandwidth guarantee using Class Based Weighted Fair Queue (CBWFQ) scheduling algorithm. Int. J. Digit. Inf. Wirel. Commun. 2015, 5, 152–157. [Google Scholar] [CrossRef]
- Kassim, M.; Ismail, M.; Yusof, M.I. A new adaptive throughput policy algorithm on campus ip-based network internet traffic. J. Theor. Appl. Inf. Technol. 2015, 71, 205–214. [Google Scholar]
- Slavata, O.; Holub, J. Impact of the codec and various QoS methods on the final quality of the transferred voice in an IP network. J. Phys. Conf. Ser. 2015, 588, 012011. [Google Scholar] [CrossRef]
- Aman, A.H.M.; Hassan, R.; Hashim, A.-H.A.; Ramli, H.A.M. Investigation of internet of things handover process for information centric networking and proxy mobile internet protocol. Res. J. Eng. Technol. 2019, 38, 867–874. [Google Scholar] [CrossRef]
- Ahmed, A.S.; Hassan, R.; Othman, N.E.; Ahmad, N.I.; Kenish, Y. Impacts evaluation of DoS attacks over ipv6 neighbor discovery protocol. J. Comput. Sci. 2019, 15, 702–727. [Google Scholar] [CrossRef]
- Amato, F.; Moscato, V.; Picariello, A.; Sperli, G. Recommendation in social media networks. In Proceedings of the IEEE Third International Conference on Multimedia Big Data (BigMM), Laguna Hills, CA, USA, 19–21 April 2017; pp. 213–216. [Google Scholar]
- Amato, F.; Castiglione, A.; Mercorio, F.; Mezzanzanica, M.; Moscato, V.; Picariello, A.; Sperlí, G. Multimedia story creation on social networks. Future Gener. Comput. Syst. 2018, 86, 412–420. [Google Scholar] [CrossRef]
- Ali, Z.; Aman, A.H.B.M.; Hassan, R. Cloud Query Processing Analysis: Encryption and Decryption. 3C Tecnologia. Glosas de innovación aplicadas a la pyme. Special Issue 2019, 65–75. [Google Scholar] [CrossRef]
- Mojib, G.; Aman, A.H.M.; Khalaf, M.; Hassan, R. Simulation Analysis for QoS in Internet of Things Wireless Network. 3C Tecnologia. Glosas de innovación aplicadas a la pyme. Special Issue 2019, 77–83. [Google Scholar] [CrossRef]
- Kaur, S. Implementation of differential services based on priority, token bucket, round robin algorithms. Int. J. Comput. Sci. Mob. Comput. 2015, 4, 810–818. [Google Scholar]
- AL-Khaleefa, A.S.; Ahmad, M.R.; Isa, A.A.M.; AL-Saffar, A.; Esa, M.R.M.; Malik, R.F. MFA-OSELM Algorithm for WiFi-Based Indoor Positioning System. Information 2019, 10, 146. [Google Scholar] [CrossRef]
- AL-Saiagh, W.; Tiun, S.; AL-Saffar, A.; Awang, S.; Al-khaleefa, A.S. Word sense disambiguation using hybrid swarm intelligence approach. PLoS ONE 2018, 13, e0208695. [Google Scholar] [CrossRef] [PubMed]
- AL-Khaleefa, A.S.; Ahmad, M.R.; Isa, A.A.M.; Esa, M.R.M.; Aljeroudi, Y.; Jubair, M.A.; Malik, R.F. Knowledge Preserving OSELM Model for Wi-Fi-Based Indoor Localization. Sensors 2019, 19, 2397. [Google Scholar] [CrossRef] [PubMed]



| Test | Description |
|---|---|
| Test 1 | No classification and policy |
| Test 2 | With classification but no policy |
| Test 3 | With classification and policy |
| Interval (sec) | Transfer (Mbytes) | Throughput (Mbps) |
|---|---|---|
| 0.0–10.0 | 69.40 | 58.10 |
| 10.0–20.0 | 69.20 | 58.00 |
| 20.0–30.0 | 69.50 | 58.20 |
| 30.0–40.0 | 69.30 | 58.10 |
| 40.0–50.0 | 69.10 | 58.10 |
| 50.0–60.0 | 69.70 | 58.30 |
| 60.0–70.0 | 69.30 | 58.00 |
| 70.0–80.0 | 69.60 | 58.20 |
| 80.0–90.0 | 69.50 | 58.50 |
| 90.0–100 | 69.40 | 58.10 |
| Interval (sec). | Stream 1 (Mbytes) | Stream 2 (Mbytes) | Throughput 1 (Mbps) | Throughput 2 (Mbps) |
|---|---|---|---|---|
| 0.0–10.0 | 52.70 | 58.40 | 46.30 | 47.80 |
| 10.0–20.0 | 52.80 | 58.50 | 45.50 | 48.50 |
| 20.0–30.0 | 52.60 | 58.20 | 44.60 | 47.60 |
| 30.0–40.0 | 52.90 | 58.30 | 45.40 | 49.00 |
| 40.0–50.0 | 52.90 | 58.40 | 46.70 | 48.80 |
| 50.0–60.0 | 52.60 | 58.70 | 45.80 | 45.60 |
| 60.0–70.0 | 52.90 | 58.40 | 45.90 | 49.70 |
| 70.0–80.0 | 52.90 | 58.30 | 46.50 | 47.80 |
| 80.0–90.0 | 52.80 | 58.40 | 44.70 | 49.20 |
| 90.0–100 | 52.90 | 58.40 | 44.10 | 49.10 |
| Total | 1112.0 | 93.3 | ||
| Traffic classfication class map Setting class map Match-all ICMP match access-group 101 class-map match-all HTTP match access-group 105 class-map match-all VOICE match precedence 3 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Azamuddin, W.M.H.; Hassan, R.; Aman, A.H.M.; Hasan, M.K.; Al-Khaleefa, A.S. Quality of Service (QoS) Management for Local Area Network (LAN) Using Traffic Policy Technique to Secure Congestion. Computers 2020, 9, 39. https://doi.org/10.3390/computers9020039
Azamuddin WMH, Hassan R, Aman AHM, Hasan MK, Al-Khaleefa AS. Quality of Service (QoS) Management for Local Area Network (LAN) Using Traffic Policy Technique to Secure Congestion. Computers. 2020; 9(2):39. https://doi.org/10.3390/computers9020039
Chicago/Turabian StyleAzamuddin, Wan Muhd Hazwan, Rosilah Hassan, Azana Hafizah Mohd Aman, Mohammad Kamrul Hasan, and Ahmed Salih Al-Khaleefa. 2020. "Quality of Service (QoS) Management for Local Area Network (LAN) Using Traffic Policy Technique to Secure Congestion" Computers 9, no. 2: 39. https://doi.org/10.3390/computers9020039
APA StyleAzamuddin, W. M. H., Hassan, R., Aman, A. H. M., Hasan, M. K., & Al-Khaleefa, A. S. (2020). Quality of Service (QoS) Management for Local Area Network (LAN) Using Traffic Policy Technique to Secure Congestion. Computers, 9(2), 39. https://doi.org/10.3390/computers9020039







