An Improvement on Remote User Authentication Schemes Using Smart Cards
Abstract
:1. Introduction
2. Cryptanalysis of Yeh et al.’s Schemes
2.1. Review of Yeh et al.’s Timestamp Based Scheme
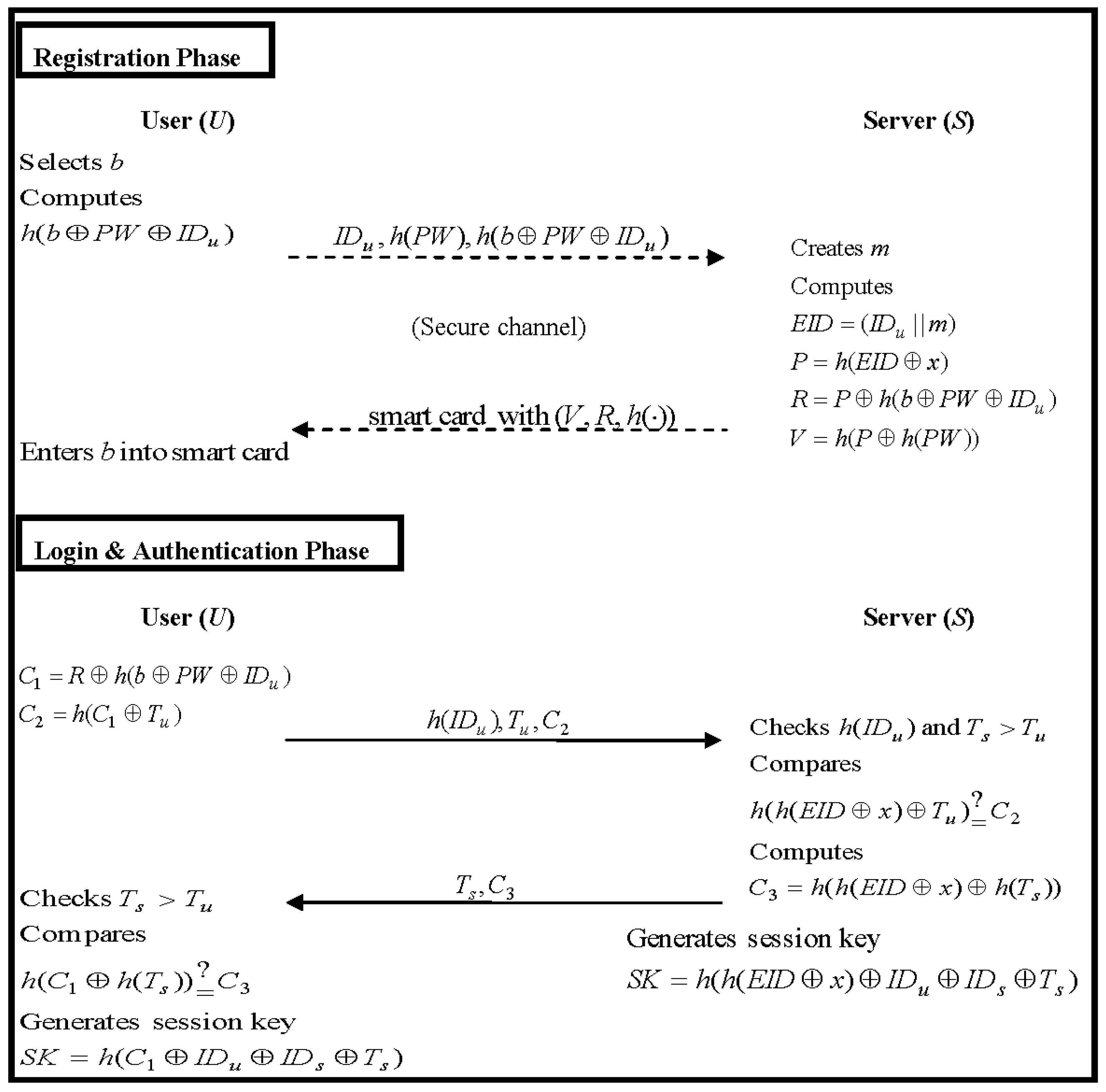
2.1.1. Registration Phase
- U selects a random number b and computes h(b ⊕ PW ⊕ IDu). He or she then securely send IDu, h(PW) and h(b ⊕ PW ⊕ IDu) to S.
- S creates a new entry with a value m = 0 for U in the database or sets m = m + 1 in the existing entry. Here, m denotes the number of times of re-registering to S for each user U. Next, S computes EID, P, R and V:Then, S securely issues a smart card containing V, R, h(·) to U.
- Finally, U enters a random number b into his or her smart card.
2.1.2. Login Phase
- U inserts his or her smart card into the card reader and then enters the IDu and PW.
- U’s smart card computes C1, C2 and sends the authentication request messages (h(IDu), Tu, C2) to S:
2.1.3. Authentication Phase
- S first checks the validity of h(IDu) and Ts > Tu. If it does not hold, S rejects U’s login request; otherwise, S computes h(h(EID ⊕ x) ⊕ Tu) and compares it with C2:If the Equation (7) holds, S accepts U’s login request and computes C3:otherwise, S rejects it. Continuously, S sends the response messages (Ts, C3) to U and generates a session key SK for later secure communication:
- According the received messages (Ts, C3), U’s smart card checks the validity of Ts > Tu. If it does not hold, U terminates the session; otherwise, U computes h(C1 ⊕ h(Ts)) and compares it with C3:If the Equation (10) holds, U successfully authenticates S. Finally, U computes the same session key SK:and then, U and S can use the session key SK to securely communicate with each other.
2.1.4. Password Change Phase
- U inserts his or her smart card into the card reader, enters IDu and PW and then requests a password change.
- U’s smart card computes P*, V* and compares V* with the stored V:If Equation (14) does not hold, the smart card rejects the request; if the number of login failures exceeds a predefined value, the smart card is locked immediately to prevent exhaustive password guessing attacks; otherwise, U inputs the new password PWnew. Afterward, U’s smart card computes Rnew and Vnew as follows:then, replaces with Rnew, Vnew, respectively.
2.2. Weakness of Yeh et al.’s Timestamp Based Scheme
2.2.1. ID-Theft Attack
- A guesses an identity IDA, computes a hashed value h(IDA) and compares it with the intercepted h(IDu).
- If the guessed hashed value is equal to h(IDu), this indicates that A guessed the correct identity (i.e., h(IDA) = h(IDu)); otherwise, A retries Steps 1 and 2.
2.2.2. Off-Line Password Guessing Attacks
- Following Section 2.2.1, the attacker A can obtain the real identity of U. Afterward, A guesses a password PWA.
- A computes counterfeit messages CA1 and CA2 for comparison with the intercepted messages C2 or C3, as follows:or
- Since IDu is revealed following Section 2.2.1, A can guess the correct IDu and PW to change the user’s password. Refer to the password change phase of Section 2.1.4.
2.2.3. On-line Password Guessing Attacks
- A guesses a possible password PWA and computes a value following Equation (17) CA1 with a timestamp TA. A then computes counterfeit messages (h(IDA), TA, CA1) to send to the server S.
- After receiving the messages, S first checks the timestamp Ts > Tu. Continuously, S computes h(h(EID ⊕ x) ⊕ TA) to compare the received value CA1. If both of them are equal, then PWA is U’s correct password.
- Then, S accepts this login request and sends the messages (Ts, C3) to A.
- According to the received messages, A can recognize that the correct password has been guessed; otherwise, A retries the above attack procedures until obtaining the correct password.
2.3. Review of Yeh et al.’s Nonce Based Scheme
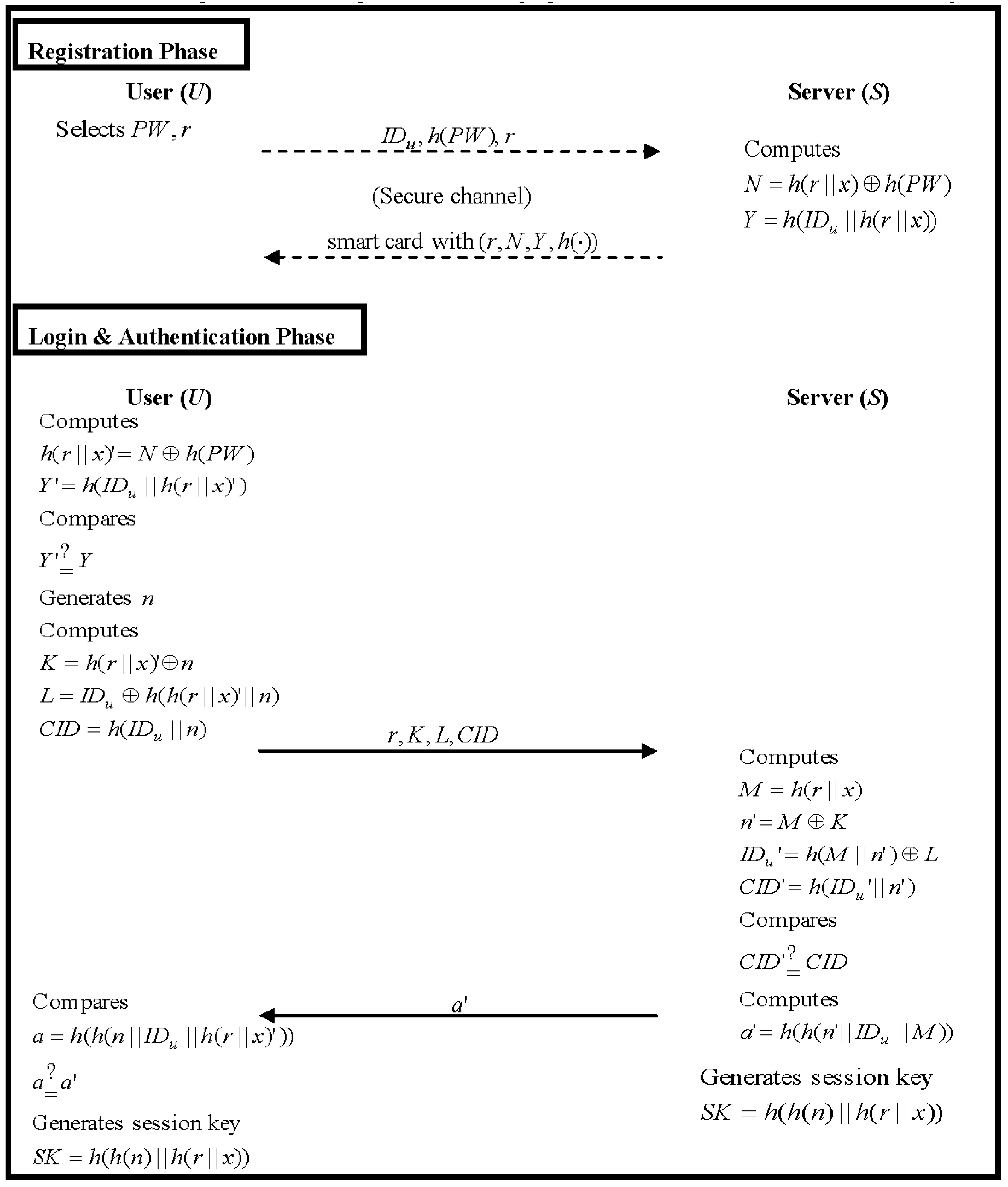
2.3.1. Registration Phase
- The user U first selects a password PW and a random number r. Then, U submits IDu, h(PW) to the remote server S through a secure channel.
- When receiving the registration request messages from U, S first computes a hash value h(r||x). With h(r||x), IDu and h(PW), S computes N and Y:Next, S initializes the smart card with r, N, Y, h(·) and sends it to U via a secure channel.
2.3.2. Login Phase
- First, the smart card uses PW and N to derive the value h(r||x). Next, the smart card computes :and compares Y′ with the stored Y; otherwise, the login request is rejected.
- Second, the smart card generates a nonce n and computes K, L and CID:
- Third, the smart card sends login request messages (r, K, L, CID) to S.
2.3.3. Authentication Phase
- S uses the received value r and its secret x to compute the hashed value M:Next, S computes n′, IDu′ and CID′:After that, S checks whether CID′ is equal to CID or not. If it holds, S confirms that U is valid and replies a message a′ to U:otherwise, S rejects the login request.
- Upon receiving message a′, U first calculates value a:and compares it with the received value a′. If both of these two values are identical, U confirms that S is valid. Since they already possess the current secret values h(r||x) and n, the session key SK will be securely agreed upon by S and U:
2.3.4. Password Change Phase
- U first inserts his or her smart card into a card reader or the terminal and keys in the identity IDu and the original password PW.
- Next, according to Equations (23) and (24), the smart card examines the validity of IDu and PW and checks to see if Y′ = Y. If the verification holds, U is allowed to enter a new password PWnew; otherwise, the smart card rejects the password change request.
- Finally, the smart card calculates N′:and replaces the old value N with the new one N′. Now, the password has been successfully changed without the participation of S.
2.4. Weakness of Yeh et al.’s Nonce Based Scheme
User Impersonation Attack
- A uses his or her own PW and N to compute the hashed value h(r||x)′ (see Equation (23)).Continuously, A selects a nonce n and the same format of identity IDi to compute the authentication message K, L and CID:and then A sends (r, K, L, CID) to S.
- S uses the received value r and its secret x to compute the hashed value M (Refer to Equation (28)):Next, S computes n′ (Refer to Equation (29), IDi′ and CID′:After that, S checks whether CID′ is equal to CID or not. If it holds, S confirms that A is valid and replies a message a′ to A:
- After receiving message a′, A can confirm that he or she pass the authentication to impersonate the User i.
3. The Improved Scheme
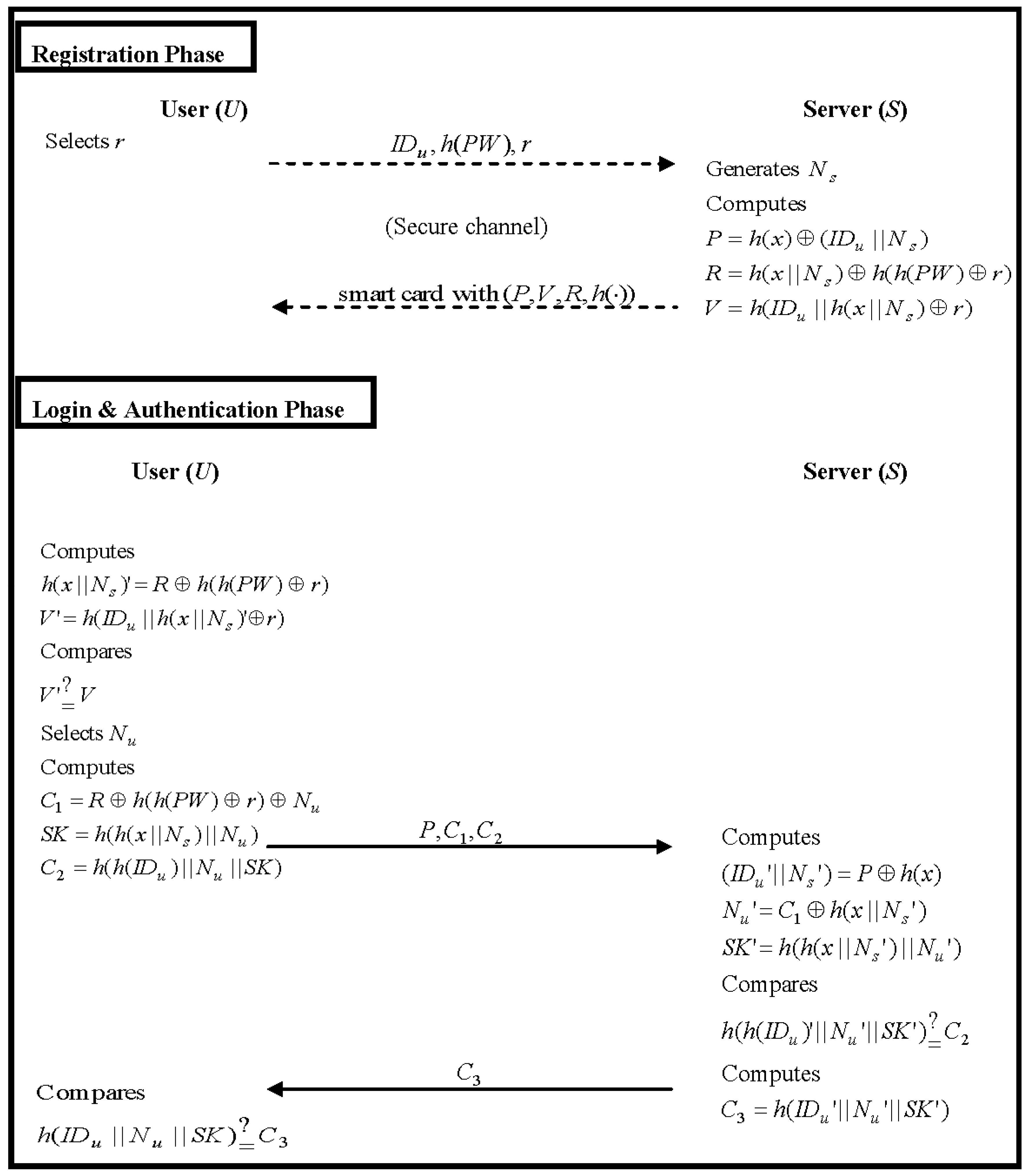
3.1. Registration Phase
- The user U chooses a password and selects a random number r, then submits the registration messages (IDu, h(PW), r) to the remote server S via a secure channel.
- When S receives the registration messages from U, S first generates a nonce Ns and uses IDu and h(PW) to compute three values P, R and V:Afterward, S issues the smart card with parameters P, R, V and h(·) to U through a secure channel.
3.2. Login Phase
- The smart card uses random number r, PW and R to compute a value h(x||Ns)′ and calculate V′ to compare with V:If Equation (47) holds, the smart card generates a nonce Nu and computes messages C1, SK and C2; otherwise, the login request is rejected:
- Finally, the smart card sends login request messages (P, C1, C2) to S.
3.3. Authentication Phase
- S uses the received value P and its secret key x to obtain (IDu′ and Ns′):Afterward, S computes Nu′ and SK′ to check if the authentication message C2 is valid or not:If Equation (54) holds, S confirms that U is a legal user and responds a message C3 to U:Otherwise, S rejects the login request.
- When receiving the response C3, U first verifies whether the message is valid or not:If the Equation (56) holds, U confirms that S is valid. Afterward, U and S can use the same session key SK to securely communicate with each other.
3.4. Password Change Phase
- First, U inserts his or her smart card into a card reader or the terminal and enters the IDu and the original PW.
- Second, according to Equations (46) and (47), the smart card examines the validity of IDu and PW and compares V′ with the stored V. If this holds, U is allowed to key in a new password PWnew; otherwise, the smart card rejects the password change request.
- Third, the smart card calculates :and replaces the old value R with the new R′. Thus, the password has been successfully changed without the participation of remote server S.
4. Security Analysis
4.1. Mutual Authentication
| P sees X. Someone has sent a message containing X to P, who can read and repeat X. |
| P once said X. P at some time sent a message including X. |
| P has jurisdiction over X. P is an authority on X and should be trusted on this matter. |
| This represents X combined with Y. |
| The formula X is fresh, that is, X has not been sent in a message at any time before the current run of the protocol. |
| P and Q may use the shared key K to communicate. |
| The formula S is a secret known only to P and Q and possibly to principals trusted by them. |
| G1 |
| M1 |
| A1 |
- Server S authenticates user U.By M1 and the seeing rule, we can derive:By A2 and the freshness rule, we can derive:By (Statement 1), A4 and the message meaning rule, we can derive:By (Statement 2), (Statement 3) and the nonce verification rule, we can derive:By (Statement 4) and the belief rule, we can derive:By (Statement 5), A6 and the jurisdiction rule, we can derive:By (Statement 6) and the belief rule, we can derive:By (Statement 7), A7 and the jurisdiction rule, we can derive:
- User U authenticates server S.By M2 and the seeing rule, we can derive:By A1 and the freshness rule, we can derive:By (Statement 9), A3 and the message meaning rule, we can derive:By (Statement 10), (Statement 11) and the message meaning rule, we can derive:By (Statement 12), A5 and the jurisdiction rule, we can derive:
- Scenario:
- A malicious attacker uses an illegal server to authenticate a legal user.
- Analysis:
- The attacker will not succeed because the legal user has not been registered to the illegal server and the illegal server cannot calculate the correct session key SK. Thus, it will fail when the legal user attempts to authenticate the illegal server. In the proposed scheme, the attacker cannot achieve their purpose using an illegal server. In the same scenario, the proposed scheme can also defend against a malicious attack using an illegal user to connect to a legal server. This is why the illegal user has not been registered to the legal server and the illegal user cannot calculate the correct session key SK. Thus, the attack will fail when the legal server attempts to authenticate the illegal user.
4.2. Lost Smart Card
4.3. ID-Theft Attack
4.4. Password Guessing Attacks
4.5. Server Counterfeit Attack and User Impersonation Attack
4.6. Replay Attack
- Scenario:
- A malicious attacker intercepts the transmitted message between the user and the server and sends the same message again to the user or the server.
- Analysis:
- The attacker will not succeed because the legal user uses the nonce value Nu in each session. The attacker cannot get the correct nonce value Nu. Thus, the attack will fail when the legal server authenticates the received message. In the proposed scheme, the attackers cannot achieve their purpose by sending the same message again to the user or to the server. Therefore, attackers cannot achieve their purpose by replay attack.
5. Performance Analysis
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Lamport, L. Password authentication with insecure communication. ACM Commun. 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Argyroudis, P.G.; Verma, R.; Tewari, H.; O’Mahony, D. Performance analysis of cryptographic protocols on handheld devices. In Proceedings of the 3rd International Symposium on Network Computing and Applications, Cambridge, MA, USA, 30 August–1 September 2004; pp. 169–174. [Google Scholar]
- Awasthi, A.K.; Lal, S. A remote user authentication scheme using smart cards with forward secrecy. IEEE Trans. Consum. Electron. 2003, 49, 1246–1248. [Google Scholar] [CrossRef]
- Bellare, M.; Rogaway, P. Entity authentication and key distribution. In Advances in Cryptology—CRYPTO’93, LNCS; Springer: Berlin, Germany, 1993; Volume 773, pp. 232–249. [Google Scholar]
- Chien, H.Y.; Chen, C.H. A remote authentication scheme preserving user anonymity. In Proceedings of the 19th International Conference on Advanced Information Networking and Applications, Taipei, Taiwan, 28–30 March 2005; pp. 245–248. [Google Scholar]
- Das, M.L.; Saxena, A.; Gulati, V.P. A dynamic ID-based remote user authentication scheme. IEEE Trans. Consum. Electron. 2004, 50, 629–631. [Google Scholar] [CrossRef]
- Ding, Y.; Horster, P. Undetectable on-line password guessing attacks. ACM SIGOPS Oper. Syst. Rev. 1995, 29, 77–86. [Google Scholar] [CrossRef]
- Duan, X.; Liu, J.W.; Zhang, Q. Security improvement on Chien et al.’s remote user authentication scheme using smart cards. In Proceedings of the IEEE International Conference on Computational Intelligence and Security, Guangzhou, China, 3–6 November 2006; pp. 1133–1135. [Google Scholar]
- Gao, Z.X.; Tu, Y.Q. An improvement of dynamic ID-based remote user authentication scheme with smart cards. In Proceedings of the 7th World Congress on Intelligent Control and Automation, Chongqing, China, 25–27 June 2008; pp. 4562–4567. [Google Scholar]
- Gong, L. A security risk of depending on synchronized clocks. ACM Oper. Syst. Rev. 1992, 26, 49–53. [Google Scholar] [CrossRef]
- Hsiang, H.C.; Shih, W.K. Weaknesses and improvements of the Yoon-Ryu-Yoo remote user authentication scheme using smart cards. Comput. Commun. 2009, 32, 649–652. [Google Scholar] [CrossRef]
- Hwang, T.; Chen, Y.; Laih, C.S. Non-interactive password authentication without password tables. In Proceedings of the IEEE Region 10 Conference on Computer and Communication Systems, Hong Kong, China, 24–27 September 1990; pp. 429–431. [Google Scholar]
- Hwang, M.S.; Chong, S.K.; Chen, T.Y. DoS-resistant ID-based password authentication scheme using smart cards. J. Syst. Softw. 2010, 83, 163–172. [Google Scholar] [CrossRef]
- Hwang, M.S.; Li, L.H. A new remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 2000, 46, 28–30. [Google Scholar] [CrossRef]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Advances in Cryptology: Proceedings of CRYPTO 99, LNCS; Springer: Berlin, Germany, 1999; Volume 1666, pp. 388–397. [Google Scholar]
- Ku, W.C.; Chang, S.T. Impersonation attack on a dynamic ID-based remote user authentication scheme using smart cards. IEICE Trans. Commun. 2005, E88-B, 2165–2167. [Google Scholar] [CrossRef]
- Lee, C.C.; Hwang, M.S.; Yang, W.P. A flexible remote user authentication scheme using smart cards. ACM Oper. Syst. Rev. 2002, 36, 46–52. [Google Scholar] [CrossRef]
- Lee, C.C.; Li, L.H.; Hwang, M.S. A remote user authentication scheme using hash functions. ACM Oper. Syst. Rev. 2002, 36, 23–29. [Google Scholar] [CrossRef]
- Liao, I.E.; Lee, C.C.; Hwang, M.S. Security enhancement for a dynamic ID-based remote user authentication scheme. In Proceedings of the IEEE International Conference on Next Generation Web Services Practices, Seoul, Korea, 22–26 August 2005; pp. 437–440. [Google Scholar]
- Lo, N.W.; Yeh, K.H. Cryptanalysis of two three-party encrypted key exchange protocols. Comput. Stand. Interfaces 2009, 31, 1167–1174. [Google Scholar] [CrossRef]
- Messerges, T.S.; Dabbish, E.A.; Sloan, R.H. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 51, 541–552. [Google Scholar] [CrossRef]
- Misbahuddin, M.; Ahmed, M.A.; Shastri, M.H. A simple and efficient solution to remote user authentication using smart cards. In Proceedings of the Innovations in Information Technology, Dubai, UAE, 19–21 November 2006; pp. 1–5. [Google Scholar]
- Sun, H.M. An efficient remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 2000, 46, 958–961. [Google Scholar]
- Shen, J.J.; Lin, C.W.; Hwang, M.S. A modified remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 2003, 49, 414–416. [Google Scholar] [CrossRef]
- Wang, Y.Y.; Liu, J.Y.; Xiao, F.X.; Dan, J. A more efficient and secure dynamic ID-based remote user authentication scheme. Comput. Commun. 2009, 32, 583–585. [Google Scholar] [CrossRef]
- Xie, Q.; Wang, J.L.; Chen, D.R.; Yu, X.Y. A novel user authentication scheme using smart cards. In Proceedings of the 2008 International Conference on Computer Science and Software Engineering, Hubei, China, 12–14 December 2008; pp. 834–836. [Google Scholar]
- Yeh, K.H.; Su, C.; Lo, N.W.; Li, Y.; Hung, Y.X. Two robust remote user authentication protocols using smart cards. J. Syst. Softw. 2010, 83, 2556–2565. [Google Scholar] [CrossRef]
- Yoon, E.J.; Ryu, E.K.; Yoo, K.Y. Further improvement of an efficient password based remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 2004, 50, 612–614. [Google Scholar] [CrossRef]
- Zhang, X.; Feng, Q.Y.; Li, M. A modified dynamic ID-based remote user authentication scheme. In Proceedings of the International Conference on Communications, Circuits and Systems, Guilin, China, 25–28 June 2006; pp. 1602–1604. [Google Scholar]
- Chang, C.; Hwang, K.F. Some forgery attacks on a remote user authentication scheme using smart cards. Informatics 2003, 14, 289–294. [Google Scholar]
- Hwang, M.S.; Lee, C.C.; Tang, Y.L. A simple remote user authentication scheme. Math. Comput. Model. 2002, 36, 103–107. [Google Scholar] [CrossRef]
- Hwang, T.; Ku, W.C. Reparable key distribution protocols for Internet environments. IEEE Trans. Consum. Electron. 1995, 43, 1947–1949. [Google Scholar]
- Ku, W.C.; Chen, S.M. Weaknesses and improvements of an efficient password based remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 2004, 50, 204–207. [Google Scholar]
- Das, A.K.; Goswami, A. A robust anonymous biometric-based remote user authentication scheme using smart cards. J. King Saud Univ. Comput. Inf. Sci. 2015, 27, 193–210. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Goswami, A. An efficient ECC-based privacy-preserving client authentication protocol with key agreement using smart card. J. Inf. Secur. Appl. 2015, 21, 1–19. [Google Scholar] [CrossRef]
- Mishra, D.; Chaturvedi, A.; Mukhopadhyay, S. Design of a lightweight two-factor authentication scheme with smart card revocation. J. Inf. Secur. Appl. 2015, 23, 44–53. [Google Scholar] [CrossRef]
- Chaturvedi, A.; Das, A.K.; Mishra, D.; Mukhopadhyay, S. Design of a secure smart card-based multi-server authentication scheme. J. Inf. Secur. Appl. 2016, 30, 64–80. [Google Scholar] [CrossRef]
- Madhusudhan, R.; Hegde, M. Security bound enhancement of remote user authentication using smart card. J. Inf. Secur. Appl. 2017, 36, 59–68. [Google Scholar] [CrossRef]
- Jeon, J.C.; Kang, B.H.; Kim, S.M.; Lee, W.S.; Yoo, K.Y. An improvement of remote user authentication scheme using smart cards. In Proceedings of the International Conference on Mobile Ad-Hoc and Sensor Networks, Vancouver, BC, Canada, 9–12 October 2006; pp. 416–423. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Chang, C.C.; Lee, C.Y.; Chiu, Y.C. Enhanced authentication scheme with anonymity for roaming service in global mobility networks. Comput. Commun. 2009, 32, 611–618. [Google Scholar] [CrossRef]
- Ren, K.; Lout, W.; Kim, K.; Deng, R. A novel privacy preserving authentication and access control scheme for pervasive computing environments. IEEE Trans. Veh. Technol. 2006, 55, 1373–1384. [Google Scholar] [CrossRef]
- Yeh, L.Y.; Chen, Y.C.; Huang, J.L. PPACP: A portable privacy-preserving authentication and access control protocol in vehicular ad hoc networks. Comput. Commun. 2011, 34, 447–456. [Google Scholar] [CrossRef]
| Hsiang and Shih’s Scheme (2009) | Wang et al.’s Scheme (2009) | Yeh et al.’s Timestamp-Based Scheme (2010) | Yeh et al.’s Nonce-Based Scheme (2010) | Ours | |
|---|---|---|---|---|---|
| Mutual authentication | Yes | Yes | Yes | Yes | Yes |
| Freely change password | Yes | Yes | Yes | Yes | Yes |
| Solve clock synchronization problem | No | No | No | Yes | Yes |
| Lost smart card | No | No | No | Yes | Yes |
| Prevention of ID-theft attack | No | No | No | Yes | Yes |
| Prevention of undetectable on-line password guessing attacks | No | No | No | Yes | Yes |
| Prevention of off-line password guessing attacks | No | No | No | Yes | Yes |
| Prevention of user impersonation attack | No | No | Yes | No | Yes |
| Prevention of server counterfeit attack | No | No | Yes | Yes | Yes |
| Prevention of man-in-the-middle attack | No | No | Yes | Yes | Yes |
| Prevention of replay attack | No | No | Yes | Yes | Yes |
| Prevention of session parallel attack | Yes | Yes | Yes | Yes | Yes |
| Hsiang and Shih’s Scheme (2009) | Wang et al.’s Scheme (2009) | Yeh et al.’s Timestamp-Based Scheme (2010) | Yeh et al.’s Nonce-Based Scheme (2010) | Ours | |
|---|---|---|---|---|---|
| Registration phase | 4H + 4Xor | 2H + 2Xor | 4H + 5Xor | 3H + 1Xor | 4H + 2Xor |
| Login & authentication phase | 8H + 7Xor | 6H + 13Xor | 11H + 14Xor | 15H + 5Xor | 12H + 4Xor |
| Password change phase | 6H + 6Xor | 2H + 2Xor | 6H + 6Xor | 3H + 2Xor | 3H + 2Xor |
| Total | 18H + 17Xor | 10H + 17Xor | 21H + 25Xor | 21H + 8Xor | 19H + 8Xor |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, C.-L.; Deng, Y.-Y.; Tang, Y.-W.; Chen, J.-H.; Lin, Y.-F. An Improvement on Remote User Authentication Schemes Using Smart Cards. Computers 2018, 7, 9. https://doi.org/10.3390/computers7010009
Chen C-L, Deng Y-Y, Tang Y-W, Chen J-H, Lin Y-F. An Improvement on Remote User Authentication Schemes Using Smart Cards. Computers. 2018; 7(1):9. https://doi.org/10.3390/computers7010009
Chicago/Turabian StyleChen, Chin-Ling, Yong-Yuan Deng, Yung-Wen Tang, Jung-Hsuan Chen, and Yu-Fan Lin. 2018. "An Improvement on Remote User Authentication Schemes Using Smart Cards" Computers 7, no. 1: 9. https://doi.org/10.3390/computers7010009
APA StyleChen, C.-L., Deng, Y.-Y., Tang, Y.-W., Chen, J.-H., & Lin, Y.-F. (2018). An Improvement on Remote User Authentication Schemes Using Smart Cards. Computers, 7(1), 9. https://doi.org/10.3390/computers7010009





