An Artificial Bee Colony-Based COPE Framework for Wireless Sensor Network
Abstract
:1. Introduction
2. Related Work
- Prolong snooping of the communication medium may quickly deplete node’s battery.
- Periodic broadcast of reception reports and the diversity of links may increase battery consumption and network traffic.
- COPE is a probabilistic approach. Therefore, the time complexity of the coding algorithm in COPE is less, but it may not be the best encoding solution each time.
3. Proposed Work
3.1. Self-Organization
- Positive feedback is the information generated by the system and again fed back to the system to create a better structure. It provides diversity and acceleration to the new stable state.
- Negative feedback helps to stabilize the system and compensates the effect of positive feedback.
- Fluctuation helps in finding a new solution by random change and avoids stagnation.
- Multiple interactions provide group intelligent behavior by learning from individuals of the society.
3.2. Division of Labor
- Employee bees are currently exploiting or employed at some food source. They share information of the food source with other members of the hive with a certain probability.
- Onlooker bees are waiting in the hive for new food sources. They evaluate the information communicated by employed bees to find the best one among those.
- Scout bees are unemployed bees and randomly explore the new food source near the hive.
| Algorithm 1 ABC algorithm. |
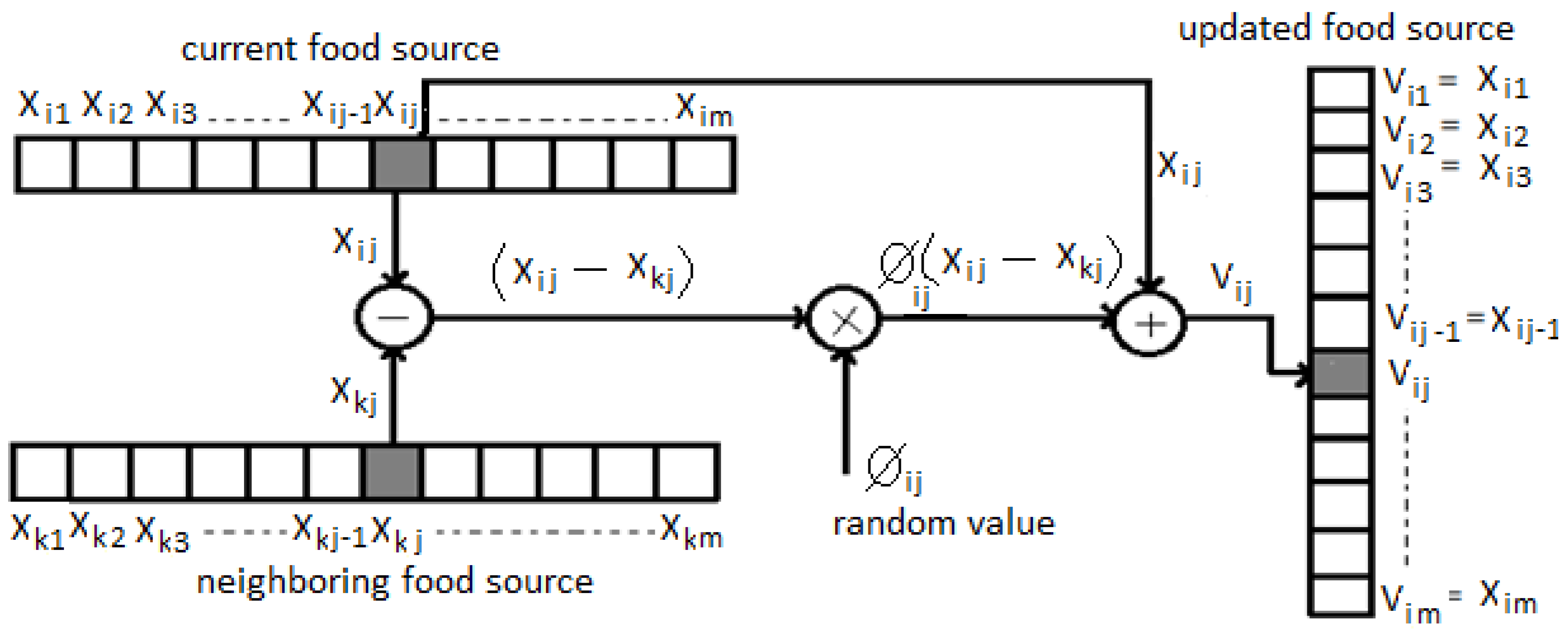
|
- = updated position value
- = current position value
- = neighboring position value
- = random value
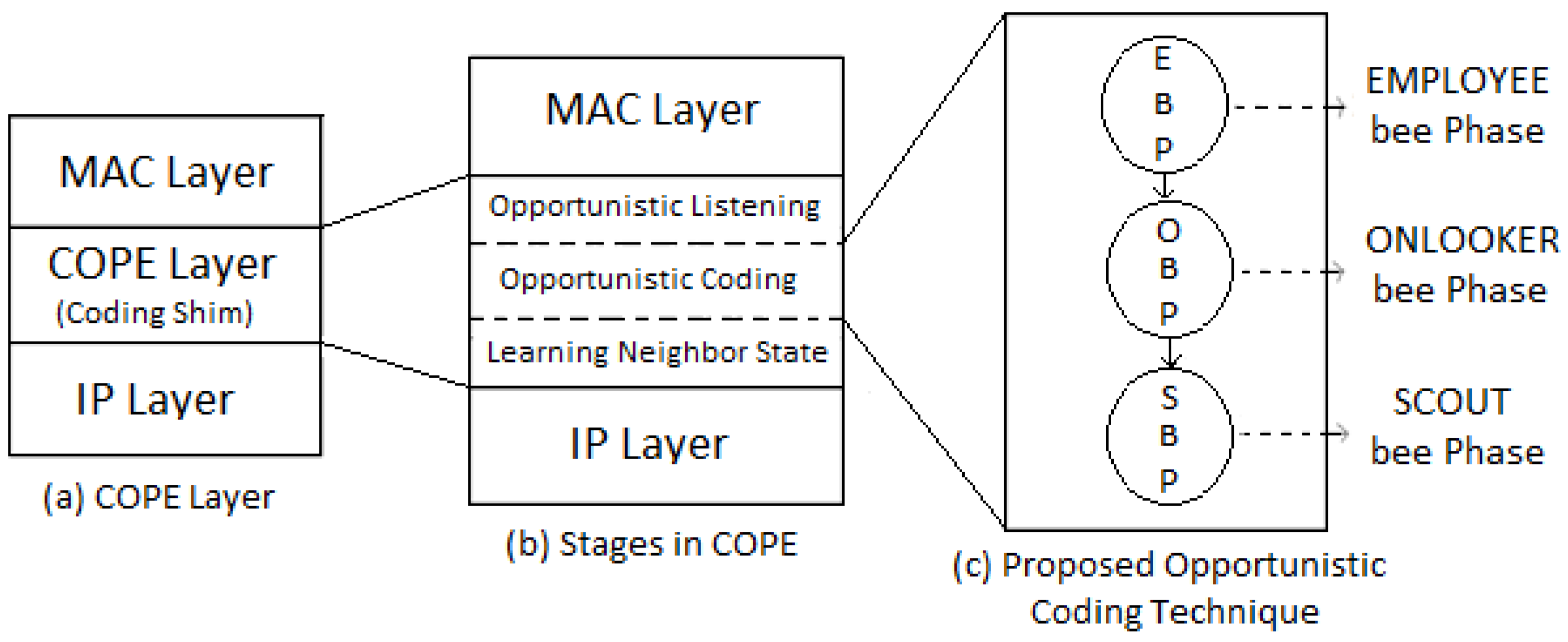
3.3. Opportunistic Listening
3.4. Opportunistic Coding
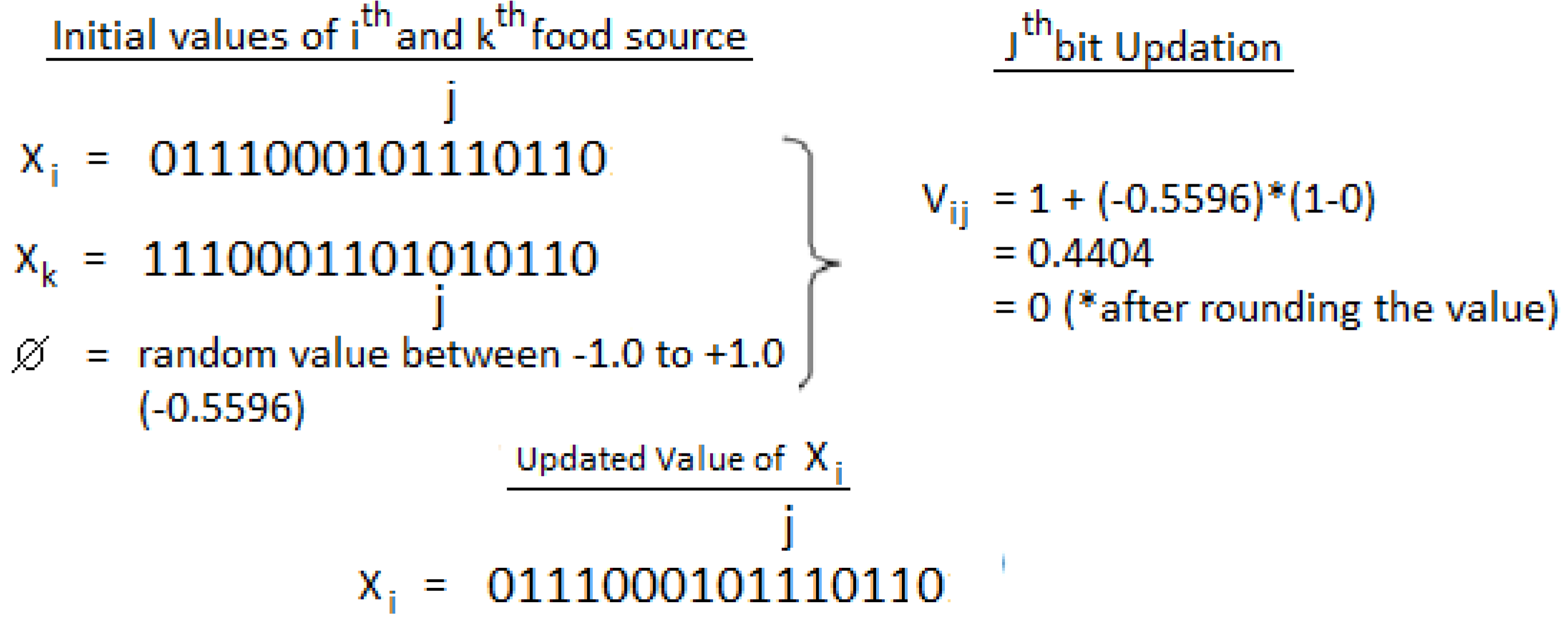
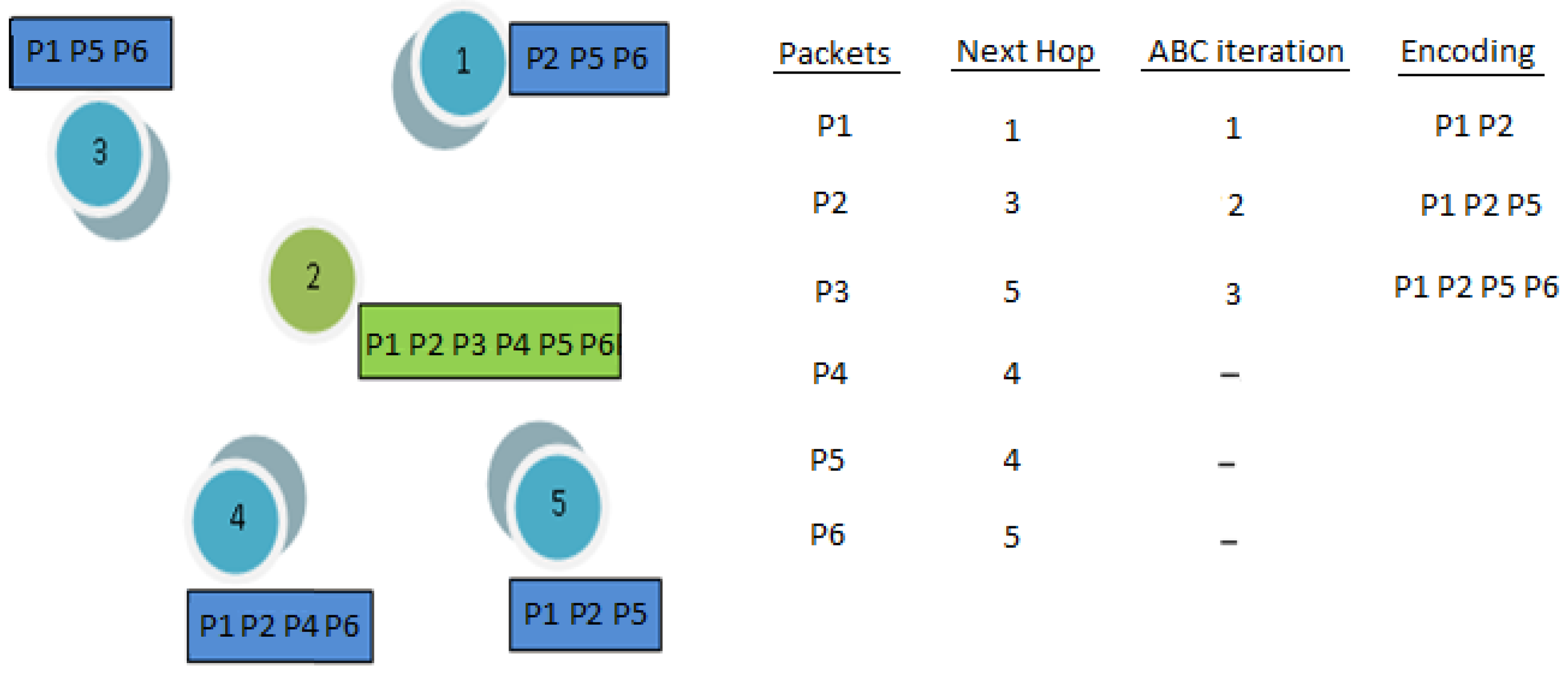
3.4.1. Packet Encoding
| Algorithm 2 ABC-COPE. |
|
| Algorithm 3 EMPLOYEE bee phase. |
|
| Algorithm 4 ONLOOKER bee phase. |
|
| Algorithm 5 SCOUT bee phase. |
|
3.4.2. Pocket Decoding
3.5. Learning Neighbor State
- ENCODED_NUM contains the information regarding the packets XORed together
- REPORT_NUM carries the reception report information
- ACK_NUM contains the cumulative acknowledgment information
- An output FIFO queue is used to store packets that need to relay to the next-hop
- The packet pool stores all packets heard in the last T unit of time
- Two virtual queues to store per neighbor information shared/computed by the reception report/deterministic probability
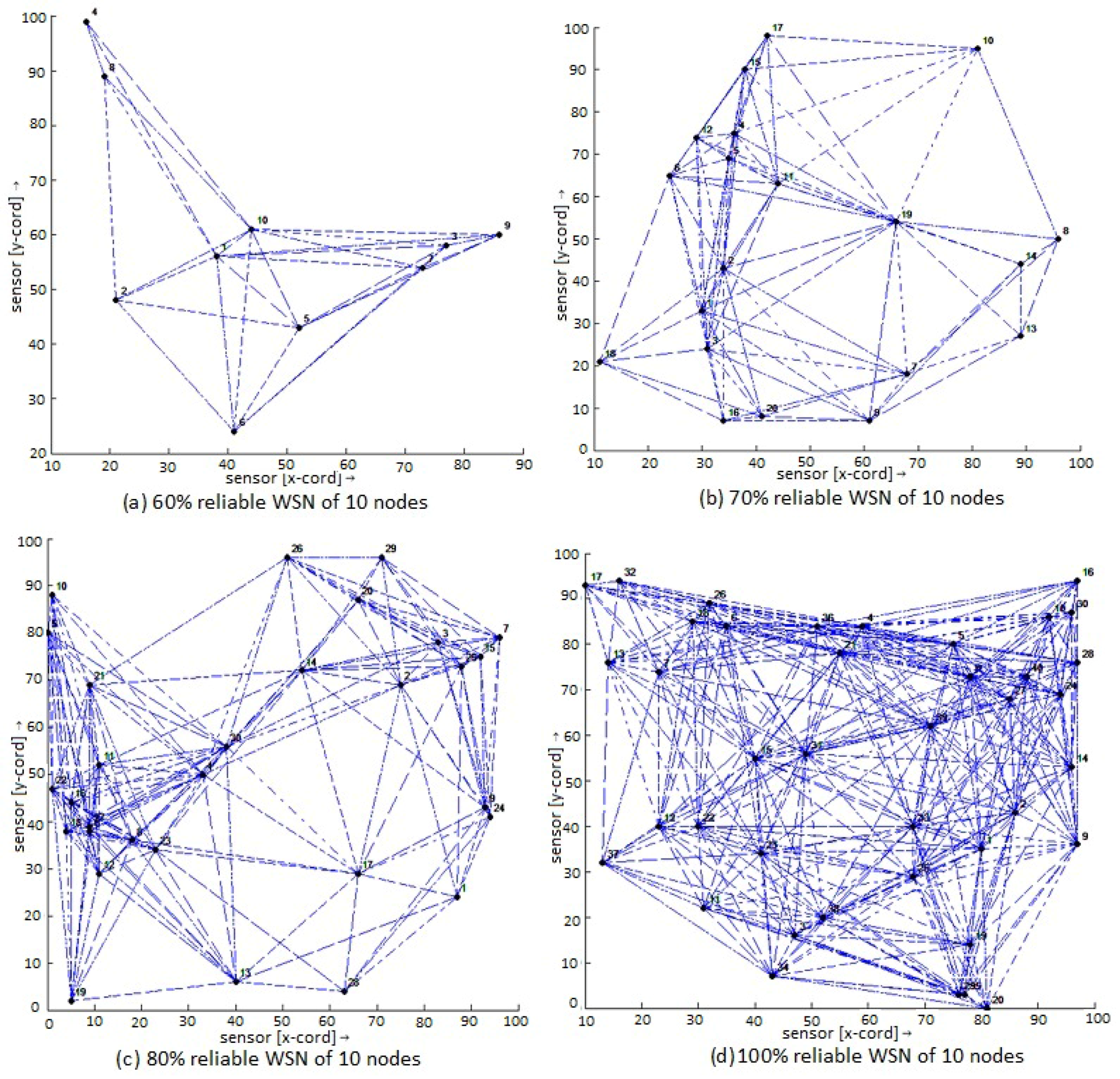
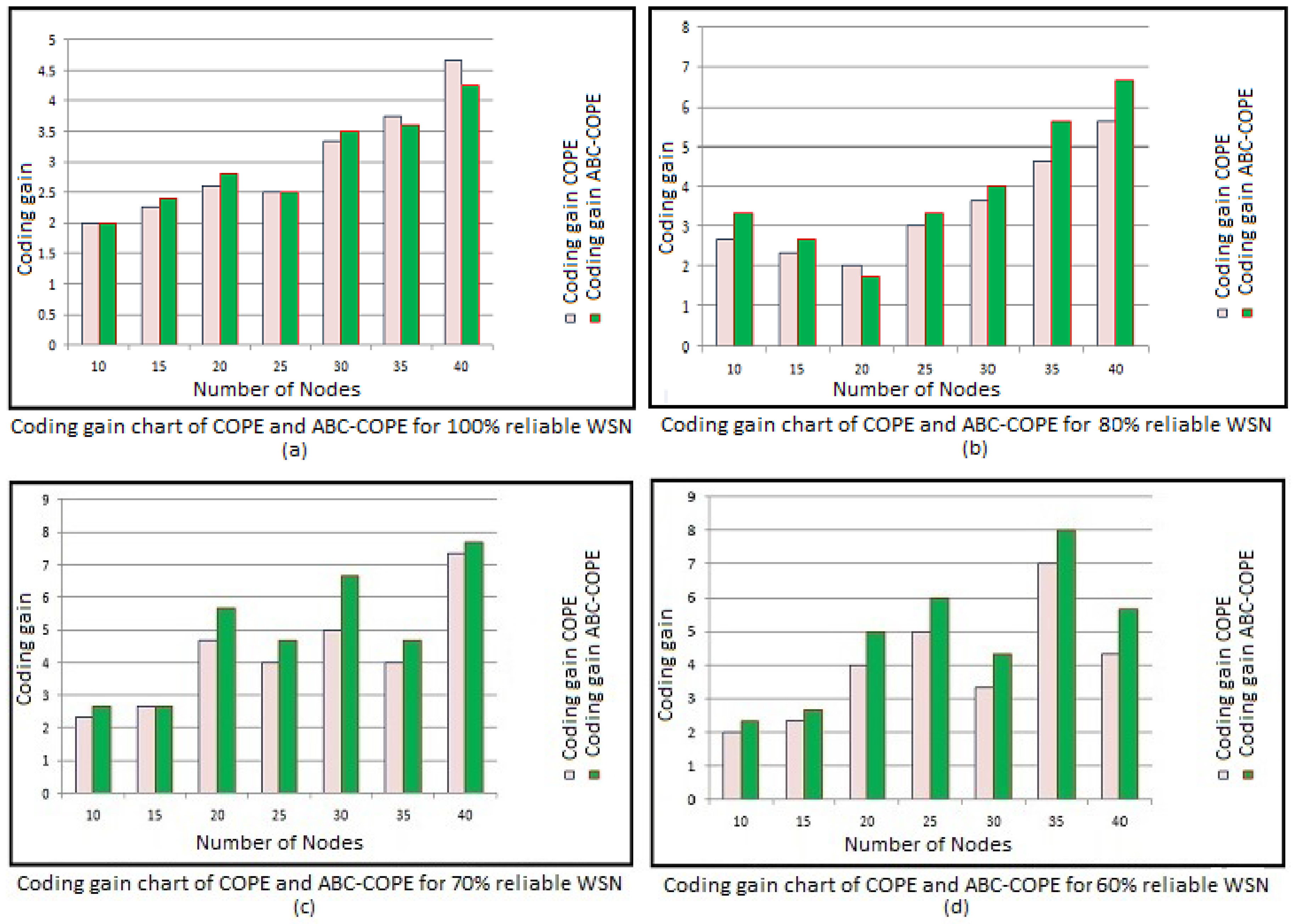
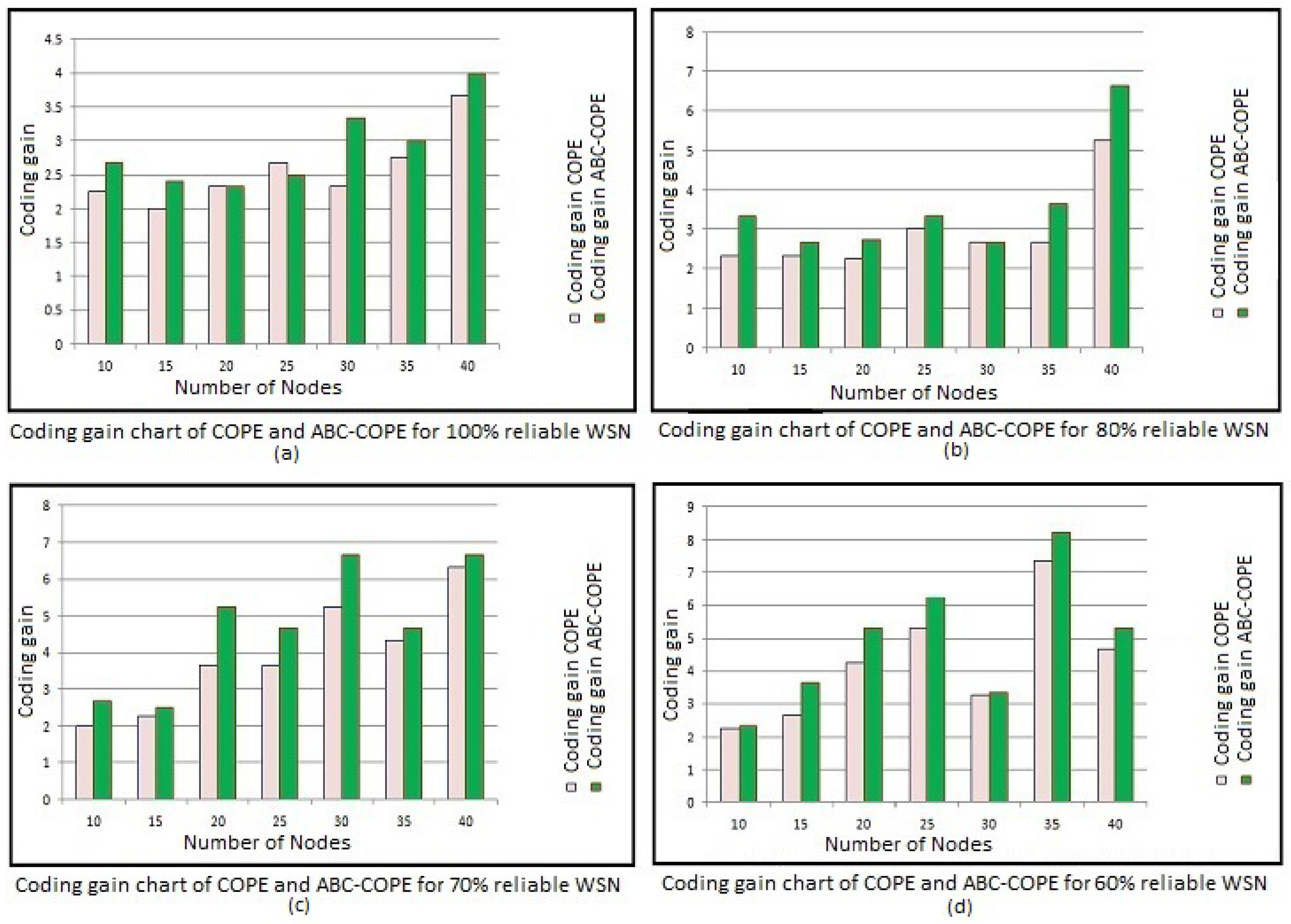
4. Results and Discussion
5. Conclusions and Future Work
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Aguayo, D.; Bicket, J.; Biswas, S.; Judd, G.; Morris, R. Link-level measurements from an 802.11b mesh network. In Proceedings of the 2004 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Portland, OR, USA, 30 August–3 September 2004; Volume 34, pp. 121–132.
- Katti, S.; Rahul, H.; Hu, W.; Katabi, D.; Médard, M.; Crowcroft, J. XORs in the air: Practical wireless network coding. IEEE/ACM Trans. Netw. 2008, 16, 497–510. [Google Scholar] [CrossRef]
- Liu, J.; Goeckel, D.; Towsley, D. Bounds on the gain of network coding and broadcasting in wireless networks. In Proceedings of the IEEE 26th International Conference on Computer Communications, INFOCOM, Anchorage, AK, USA, 6–12 May 2007; pp. 724–732.
- Glatz, P.M.; Hormann, L.B.; Steger, C.; Weiss, R. Opportunistic network coding for energy conservation in wireless sensor networks. In Proceedings of the IEEE Ninth Annual Communication Networks and Services Research Conference (CNSR), Ottawa, ON, USA, 2–5 May 2011; pp. 239–246.
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless sensor networks: A survey. Comput. Netw. 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Culler, D.; Estrin, D.; Srivastava, M. Guest editors’ introduction: Overview of sensor networks. Computer 2004, 37, 41–49. [Google Scholar] [CrossRef]
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Chang, F.-C.; Huang, H.-C. A survey on intelligent sensor network and its application. J. Netw. Intell. 2016, 1, 1–15. [Google Scholar]
- Akyildiz, I.F.; Xie, J.; Mohanty, S. A survey of mobility management in next-generation all-IP-based wireless systems. IEEE Wirel. Commun. 2004, 11, 16–28. [Google Scholar] [CrossRef]
- Jun, J.; Sichitiu, M.L. The nominal capacity of wireless mesh networks. IEEE Wirel. Commun. 2003, 10, 8–14. [Google Scholar]
- Akyildiz, I.F.; Wang, X.; Wang, W. Wireless mesh networks: A survey. Comput. Netw. 2005, 47, 445–487. [Google Scholar] [CrossRef]
- Dao, T.-K.; Pan, T.-S.; Nguyen, T.-T.; Chu, S.-C. A compact Artificial Bee Colony optimization for topology control scheme in Wireless Sensor Networks. J. Inf. Hiding and Multimed. Signal Process. 2015, 6, 297–310. [Google Scholar]
- Kaikai, C.H.; Jiang, X.; Horiguchi, S. A more efficient cope architecture for network coding in multihop wireless networks. IEICE Trans. Commun. 2009, 92, 766–775. [Google Scholar]
- Sengupta, S.; Rayanchu, S.; Banerjee, S. An analysis of wireless network coding for unicast sessions: The case for coding-aware routing. In Proceedings of the IEEE 26th International Conference on Computer Communications, INFOCOM, Anchorage, AK, USA, 6–12 May 2007; pp. 1028–1036.
- Cui, T.; Chen, L.; Ho, T. Energy efficient opportunistic network coding for wireless networks. In Proceedings of the IEEE 27th Conference on Computer Communications, INFOCOM, Phoenix, AZ, USA, 15–17 April 2008.
- Seferoglu, H.; Markopoulou, A. Network coding-aware queue management for unicast flows over coded wireless networks. In Proceedings of the IEEE International Symposium Network Coding (NetCod), Toronto, ON, Canada, 9–11 June 2010; pp. 1–6.
- Rayanchu, S.; Sen, S.; Wu, J.; Banerjee, S.; Sengupta, S. Loss-aware network coding for unicast wireless sessions: Design, implementation, and performance evaluation. In Proceedings of the ACM SIGMETRICS International Conference on Measurement and Modeling of Computer Systems, Annapolis, MD, USA, 2–6 June 2008; Volume 36, pp. 85–96.
- Khreishah, A.; Khalil, I.M.; Ostovari, P.; Wu, J. Flow-based xor network coding for lossy wireless networks. IEEE Trans. Wirel. Commun. 2012, 11, 2321–2329. [Google Scholar] [CrossRef]
- Keller, L.; Atsan, E.; Argyraki, K.; Fragouli, C. SenseCode: Network coding for reliable sensor networks. ACM Trans. Sens. Netw. 2013, 9. [Google Scholar] [CrossRef]
- Kasireddy, B.; Wang, Y.; Liu, J. Energy conservation using network coding in grid wireless sensor networks. In Proceedings of the 3rd IEEE International Workshop on Intelligent Systems and Applications (ISA), Wuhan, China, 28–29 May 2011; pp. 1–4.
- Biswas, S.; Morris, R. ExOR: Opportunistic multi-hop routing for wireless networks. In Proceedings of the ACM SIGCOMM 2004 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communication, Portland, OR, USA, 30 August–3 September 2004; Volume 35, pp. 133–144.
- Chachulski, S.; Jennings, M.; Katti, S.; Katabi, D. Trading structure for randomness in wireless opportunistic routing. In Proceedings of the ACM Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Kyoto, Japan, 27–31 August 2007.
- Zhang, X.; Li, B. Optimized multipath network coding in lossy wireless networks. IEEE J. Sel. Areas Commun. 2009, 27, 622–634. [Google Scholar] [CrossRef]
- Lin, Y.; Li, B.; Liang, B. CodeOR: Opportunistic routing in wireless mesh networks with segmented network coding. In Proceedings of the IEEE International Conference on Network Protocols (ICNP), Orlando, FL, USA, 19–22 October 2008; pp. 13–22.
- Koutsonikolas, D.; Wang, C.C.; Hu, Y.C. Efficient network-coding-based opportunistic routing through cumulative coded acknowledgments. IEEE/ACM Trans. Netw. 2011, 19, 1368–1381. [Google Scholar] [CrossRef]
- Khreishah, A.; Khalil, I.M.; Wu, J. Universal opportunistic routing scheme using network coding. In Proceedings of the 9th IEEE Annual Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks (SECON), Seoul, Korea, 18–21 June 2012; pp. 353–361.
- Katti, S.; Katabi, D.; Balakrishnan, H.; Medard, M. Symbol-level network coding for wireless mesh networks. In Proceedings of the ACM SIGCOMM Computer Communication Review, Seattle, WA, USA, 17–22 August 2008; Volume 38, pp. 401–412.
- Bonabeau, E.; Dorigo, M.; Theraulaz, G. Swarm Intelligence: From Natural to Artificial Systems; Oxford University Press: Oxford, UK, 1999. [Google Scholar]
- Jeanne, R.L. The evolution of the organization of work in social insects. Monit. Zool. Ital. Ital. J. Zool. 1986, 20, 119–133. [Google Scholar]
- Karaboga, D. An Idea Based on Honey Bee Swarm for Numerical Optimization; Technical Report-tr06; Engineering Faculty, Computer Engineering Department, Erciyes University: Kayseri, Turkey, 2005. [Google Scholar]
- Singh, A.; Nagaraju, A. Network coding: ABC based COPE in wireless sensor and Mesh network. In Proceedings of the IEEE Contemporary Computing and Informatics (IC3I), Mysore, India, 27–29 November 2014; pp. 320–325.

© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Singh, A.; Nagaraju, A. An Artificial Bee Colony-Based COPE Framework for Wireless Sensor Network. Computers 2016, 5, 8. https://doi.org/10.3390/computers5020008
Singh A, Nagaraju A. An Artificial Bee Colony-Based COPE Framework for Wireless Sensor Network. Computers. 2016; 5(2):8. https://doi.org/10.3390/computers5020008
Chicago/Turabian StyleSingh, Amit, and Aitha Nagaraju. 2016. "An Artificial Bee Colony-Based COPE Framework for Wireless Sensor Network" Computers 5, no. 2: 8. https://doi.org/10.3390/computers5020008
APA StyleSingh, A., & Nagaraju, A. (2016). An Artificial Bee Colony-Based COPE Framework for Wireless Sensor Network. Computers, 5(2), 8. https://doi.org/10.3390/computers5020008




