Enhanced Detection of Intrusion Detection System in Cloud Networks Using Time-Aware and Deep Learning Techniques
Abstract
1. Introduction
2. Literature Review
3. Materials and Methods
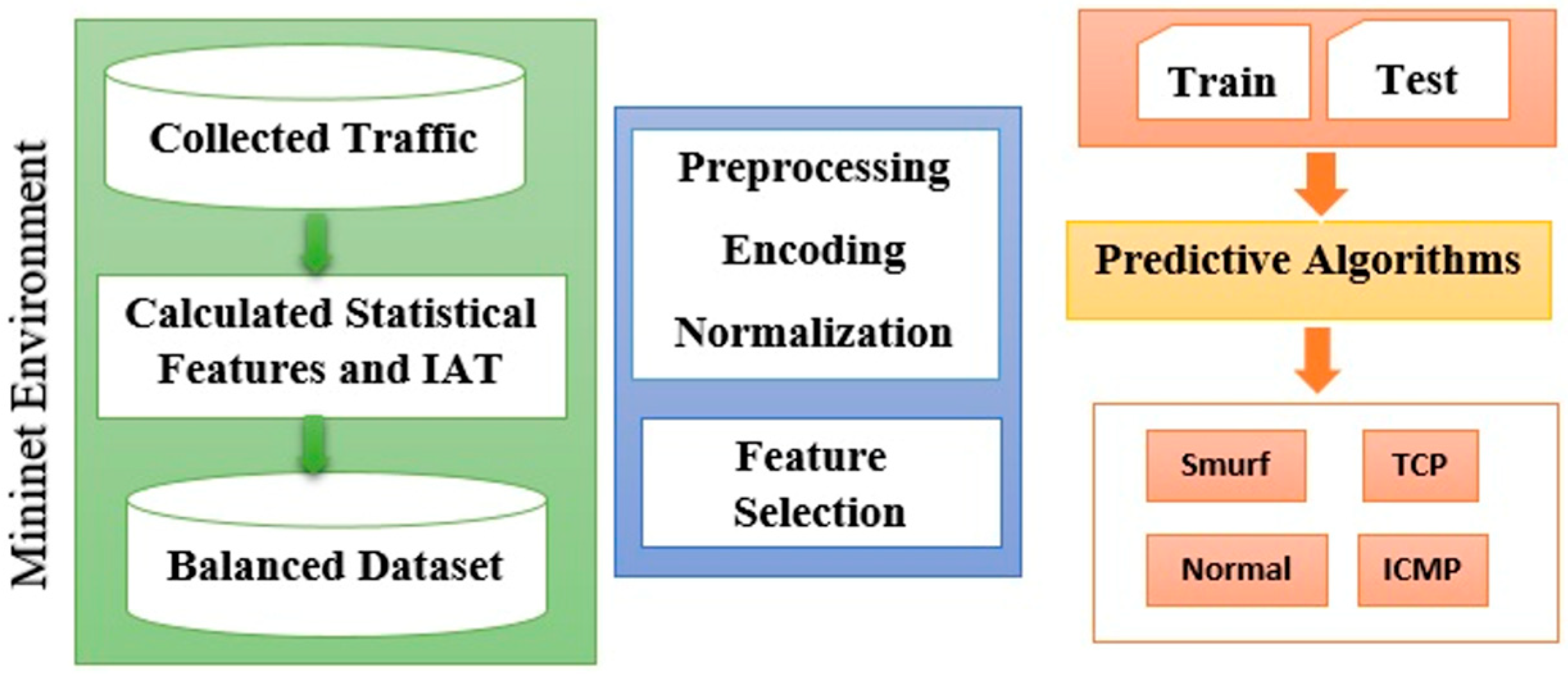
3.1. Mininet Implementation
3.2. Dataset Description
3.3. Statistical-Based Approach
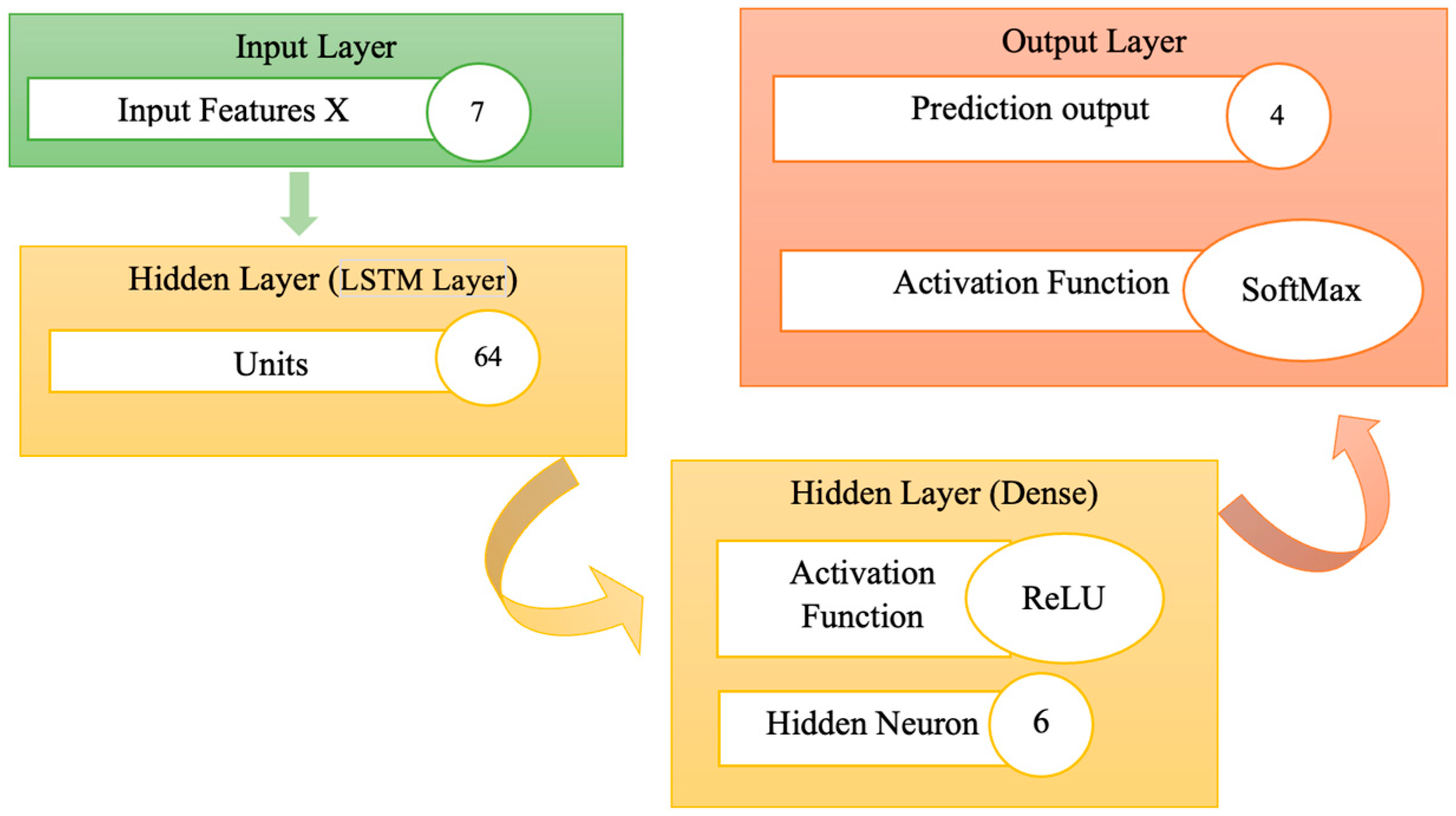
3.4. Predictive Algorithms
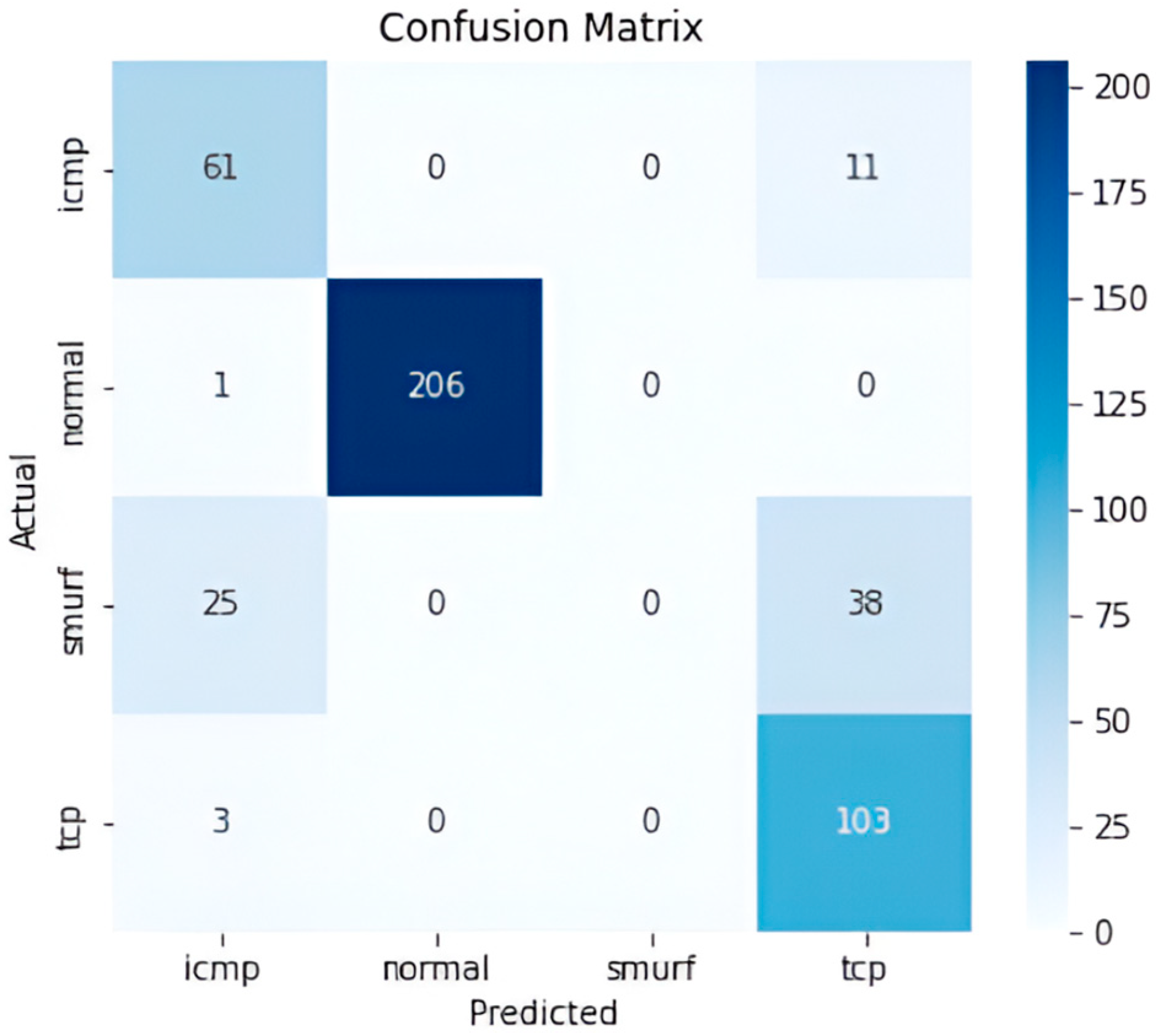
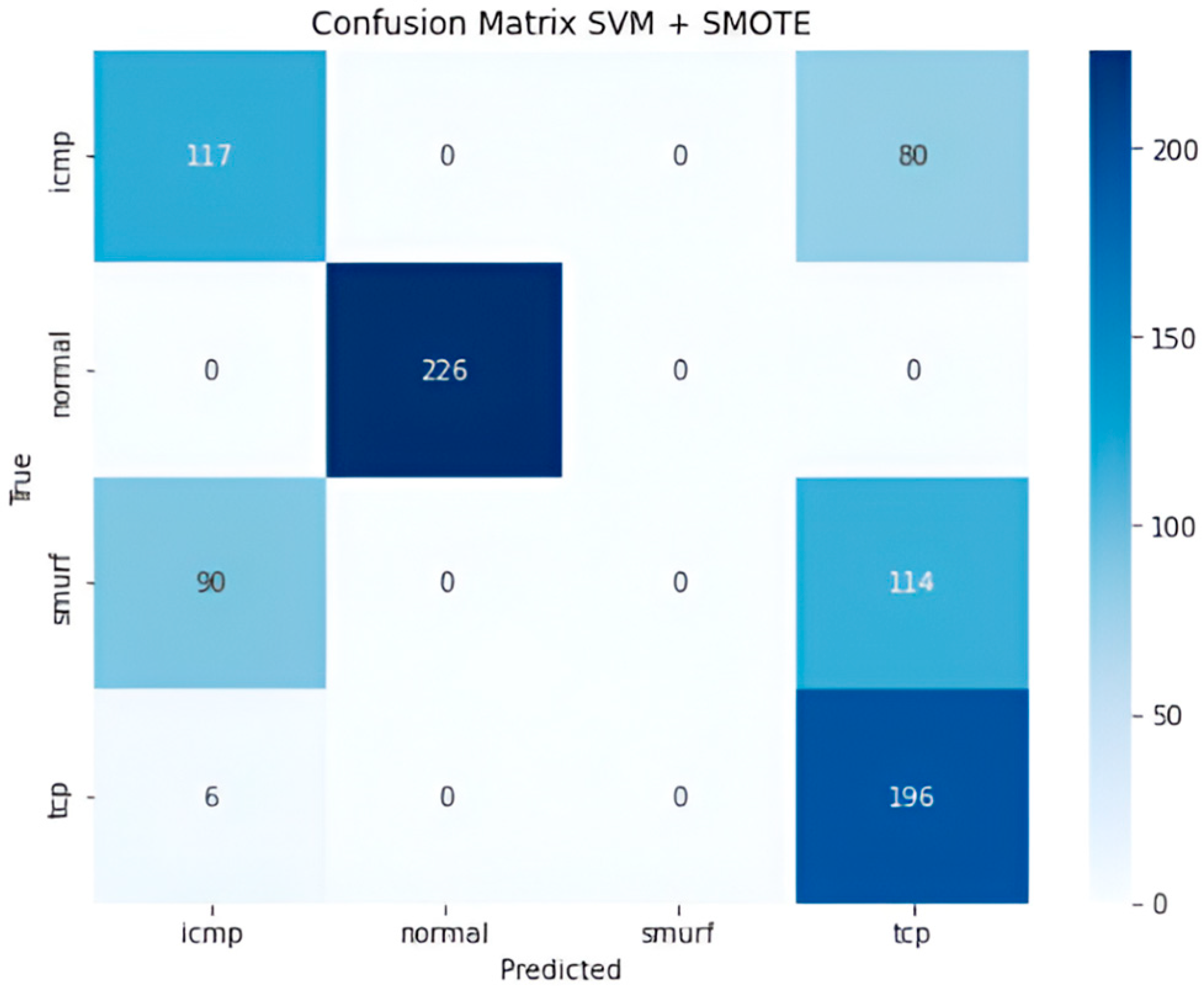
4. Results
4.1. Experiment Settings
4.2. Traditional Machine Learning Results
4.3. Deep Learning Results
4.4. Transferability and Applicability
5. Discussion and Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Tashtoush, Y.M.; Darweesh, D.A.; Husari, G.; Darwish, O.A.; Darwish, Y.; Issa, L.B.; Ashqar, H.I. Agile approaches for cybersecurity systems, iot and intelligent transportation. IEEE Access 2021, 10, 1360–1375. [Google Scholar] [CrossRef]
- Aleesa, A.; Younis, M.; Mohammed, A.A.; Sahar, N. Deep-intrusion detection system with enhanced unswnb15 dataset based on deep learning techniques. J. Eng. Sci. Technol. 2021, 16, 711–727. [Google Scholar]
- Hussain, F.A.-A.; Nashat, D. Time series similarity for detecting ddos flooding attack. Assiut Univ. J. Multidiscip. Sci. Res. 2022, 51, 229–241. [Google Scholar] [CrossRef]
- Catak, F.O.; Mustacoglu, A.F. Distributed denial of service attack detection using autoencoder and deep neural networks. J. Intell. Fuzzy Syst. 2019, 37, 3969–3979. [Google Scholar] [CrossRef]
- Abu-Helo, H.; Ashqar, H. Early ransomware detection system based on network behavior. In International Conference on Advanced Information Networking and Applications; Springer: Berlin/Heidelberg, Germany, 2024; pp. 447–458. [Google Scholar]
- Naveed, M.; Arif, F.; Usman, S.M.; Anwar, A.; Hadjouni, M.; Elmannai, H.; Hussain, S.; Ullah, S.S.; Umar, F. A deep learning-based framework for feature extraction and classification of intrusion detection in networks. Wirel. Commun. Mob. Comput. 2022, 2022, 2215852. [Google Scholar] [CrossRef]
- Hamarshe, A.; Ashqar, H.I.; Hamarsheh, M. Detection of ddos attacks in software defined networking using machine learning models. In International Conference on Advances in Computing Research; Springer: Berlin/Heidelberg, Germany, 2023; pp. 640–651. [Google Scholar]
- Weshahi, A.; Dwaik, F.; Khouli, M.; Ashqar, H.I.; Shatnawi, A.; ElKhodr, M. Iot-enhanced malicious url detection using machine learning. In International Conference on Advanced Information Networking and Applications; Springer: Berlin/Heidelberg, Germany, 2024; pp. 470–482. [Google Scholar]
- Aburbeian, A.M.; Ashqar, H.I. Credit card fraud detection using enhanced random forest classifier for imbalanced data. In International Conference on Advances in Computing Research; Springer: Berlin/Heidelberg, Germany, 2023; pp. 605–616. [Google Scholar]
- Ullah, F.; Ullah, S.; Srivastava, G.; Lin, J.C.-W. Idsint: Intrusion detection system using transformer-based transfer learning for imbalanced network traffic. Digit. Commun. Netw. 2023, 10, 190–204. [Google Scholar] [CrossRef]
- Liu, Y.; Tang, S.; Liu, R.; Zhang, L.; Ma, Z. Secure and robust digital image watermarking scheme using logistic and rsa encryption. Expert Syst. Appl. 2018, 97, 95–105. [Google Scholar] [CrossRef]
- Alghawli, A.S. Complex methods detect anomalies in real time based on time series analysis. Alex. Eng. J. 2022, 61, 549–561. [Google Scholar] [CrossRef]
- Baldini, G.; Amerini, I. Online distributed denial of service (ddos) intrusion detection based on adaptive sliding window and morphological fractal dimension. Comput. Netw. 2022, 210, 108923. [Google Scholar] [CrossRef]
- Gao, L.; Li, Y.; Zhang, L.; Lin, F.; Ma, M. Research on detection and defense mechanisms of dos attacks based on bp neural network and game theory. IEEE Access 2019, 7, 43018–43030. [Google Scholar] [CrossRef]
- Bouyeddou, B.; Kadri, B.; Harrou, F.; Sun, Y. Nonparametric kullback-leibler distance-based method for networks intrusion detection. In Proceedings of the 2020 International Conference on Data Analytics for Business and Industry: Way Towards a Sustainable Economy (ICDABI), Sakheer, Bahrain, 26–27 October 2020; pp. 1–5. [Google Scholar]
- Almorabea, O.M.; Khanzada, T.J.S.; Aslam, M.A.; Hendi, F.A.; Almorabea, A.M. Iot network-based intrusion detection framework: A solution to process ping floods originating from embedded devices. IEEE Access 2023, 11, 119118–119145. [Google Scholar] [CrossRef]
- Pei, J.; Chen, Y.; Ji, W. A ddos attack detection method based on machine learning. J. Phys. Conf. Ser. 2019, 1237, 032040. [Google Scholar] [CrossRef]
- Fernando, G.-P.; Brayan, A.-A.H.; Florina, A.M.; Liliana, C.-B.; Hector-Gabriel, A.-M.; Reinel, T.-S. Enhancing intrusion detection in iot communications through ml model generalization with a new dataset (idsai). IEEE Access 2023, 11, 70542–70559. [Google Scholar] [CrossRef]
- Panigrahi, R.; Borah, S. A detailed analysis of cicids2017 dataset for designing intrusion detection systems. Int. J. Eng. Technol. 2018, 7, 479–482. [Google Scholar]
- Nichelini, A.; Pozzoli, C.A.; Longari, S.; Carminati, M.; Zanero, S. Canova: A hybrid intrusion detection framework based on automatic signal classification for can. Comput. Secur. 2023, 128, 103166. [Google Scholar] [CrossRef]
- Sharafaldin, I.; Lashkari, A.H.; Hakak, S.; Ghorbani, A.A. Developing realistic distributed denial of service (ddos) attack dataset and taxonomy. In Proceedings of the 2019 International Carnahan Conference on Security Technology (ICCST), Chennai, India, 1–3 October 2019; pp. 1–8. [Google Scholar]
- Jilcha, L.A.; Kim, D.-H.; Kwak, J. Temporal Decay Loss for Adaptive Log Anomaly Detection in Cloud Environments. Sensors 2025, 25, 2649. [Google Scholar] [CrossRef] [PubMed]
- Wang, Y.; Wu, Y.; Xu, Y.; Zhang, K.; Xu, Y. Research on Network Intrusion Detection Based on Weighted Histogram Algorithm for In-Vehicle Ethernet. Sensors 2025, 25, 3541. [Google Scholar] [CrossRef]

| Study | DoS | Dataset | Algorithm | Accuracy |
|---|---|---|---|---|
| [14] | M-Dos | IIoT | Support Vector Machine (SVM) | 96 |
| [15] | ICMP | DARPA99 | SVM | 93 |
| [16] | TCP UDP ICMP | collected | Random Forest (RF) SVM | 89 |
| [17] | ARP ICMP TCP | IDSAI Bot-IoT | RF | 94 |
| [18] | UDP Smurf http SID DOS | collected | RF Naïve Bayesian (NB) Multilayer Perceptron (MLP) | 98 |
| No. | Feature | Explanation |
|---|---|---|
| 1 | Stream | We aggregated the packets with different sizes in a stream (8 packet/128 packet/1024 packet). |
| 2 | Inter-Arrival Time (IAT) | Refers to the time elapsed between the arrivals of consecutive packets or data units. |
| 3 | Mean | Offers insight into the central tendency of the data. |
| 4 | Median | Indicates the typical behavior or size of the network traffic. |
| 5 | Standard Deviation | Measures the dispersion or variability of the data points around the mean, helping to gauge the level of fluctuation or stability in the traffic patterns. |
| 6 | Entropy | High entropy may indicate a lack of clear structure, potentially reflecting attack attempts that aim to obscure their patterns. |
| 7 | Min | The min value in each stream. |
| 8 | Max | The max value in each stream. |
| Model | Class | P | R | F1 | A |
|---|---|---|---|---|---|
| LR | ICMP | 66 | 79 | 72 | 79 |
| Normal | 100 | 100 | 100 | 100 | |
| Smurf | 21 | 11 | 14 | 10 | |
| TCP | 74 | 84 | 79 | 84 | |
| Overall | 65 | 69 | 66 | 80 | |
| SVM-GS | ICMP | 68 | 85 | 75 | 84 |
| Normal | 100 | 100 | 100 | 100 | |
| Smurf | 0 | 0 | 0 | 0 | |
| TCP | 68 | 80 | 97 | 97 | |
| Overall | 59 | 66 | 68 | 70 | |
| SVM-SMOTE | ICMP | 57 | 59 | 54 | 78 |
| Normal | 100 | 100 | 100 | 100 | |
| Smurf | 0 | 0 | 0 | 0 | |
| TCP | 50 | 97 | 66 | 75 | |
| Overall | 52 | 65 | 58 | 65 |
| Model | Class | P | R | F1 | A |
|---|---|---|---|---|---|
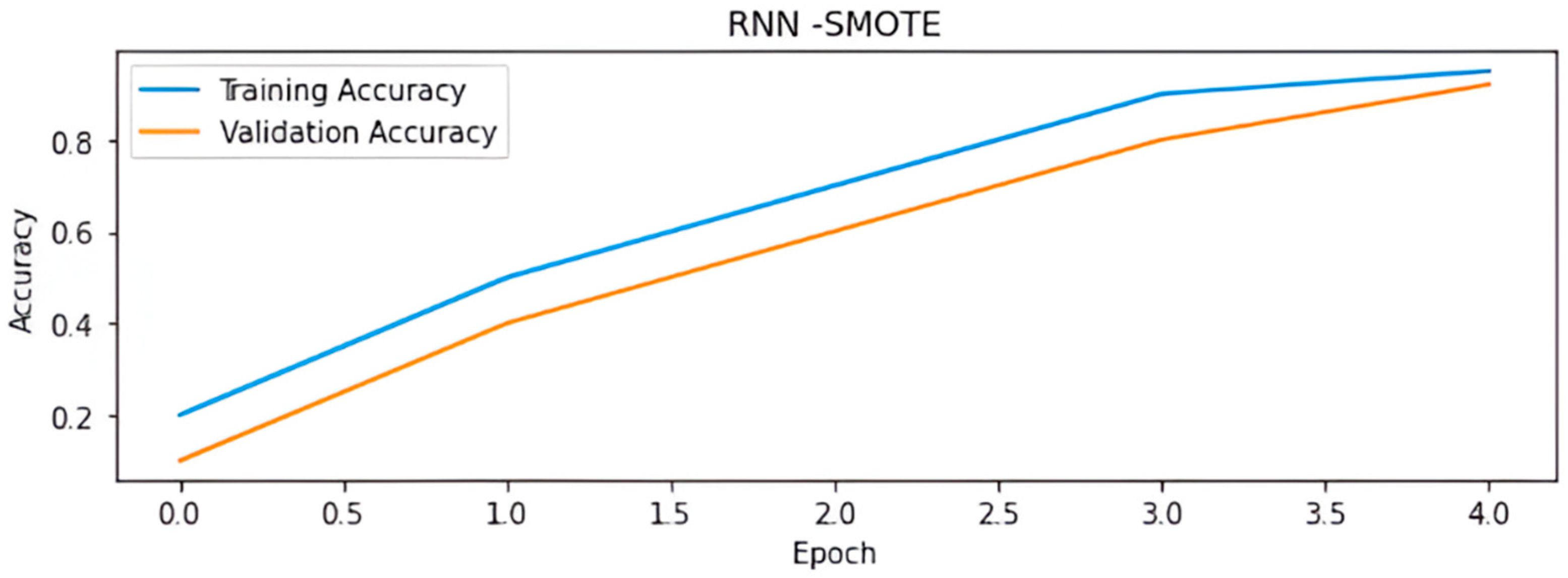
| RNN- SMOTE | ICMP | 95 | 93 | 94 | 90 |
| Normal | 88 | 91 | 89 | 85 | |
| Smurf | 92 | 94 | 93 | 88 | |
| TCP | 84 | 88 | 86 | 82 | |
| Overall | 89 | 91 | 90 | 86 | |
| RNN- SMOTEGS | ICMP | 94 | 89 | 92 | 97 |
| Normal | 100 | 99 | 100 | 97 | |
| Smurf | 92 | 95 | 93 | 97 | |
| TCP | 97 | 100 | 99 | 97 | |
| Overall | 96 | 96 | 96 | 97 | |
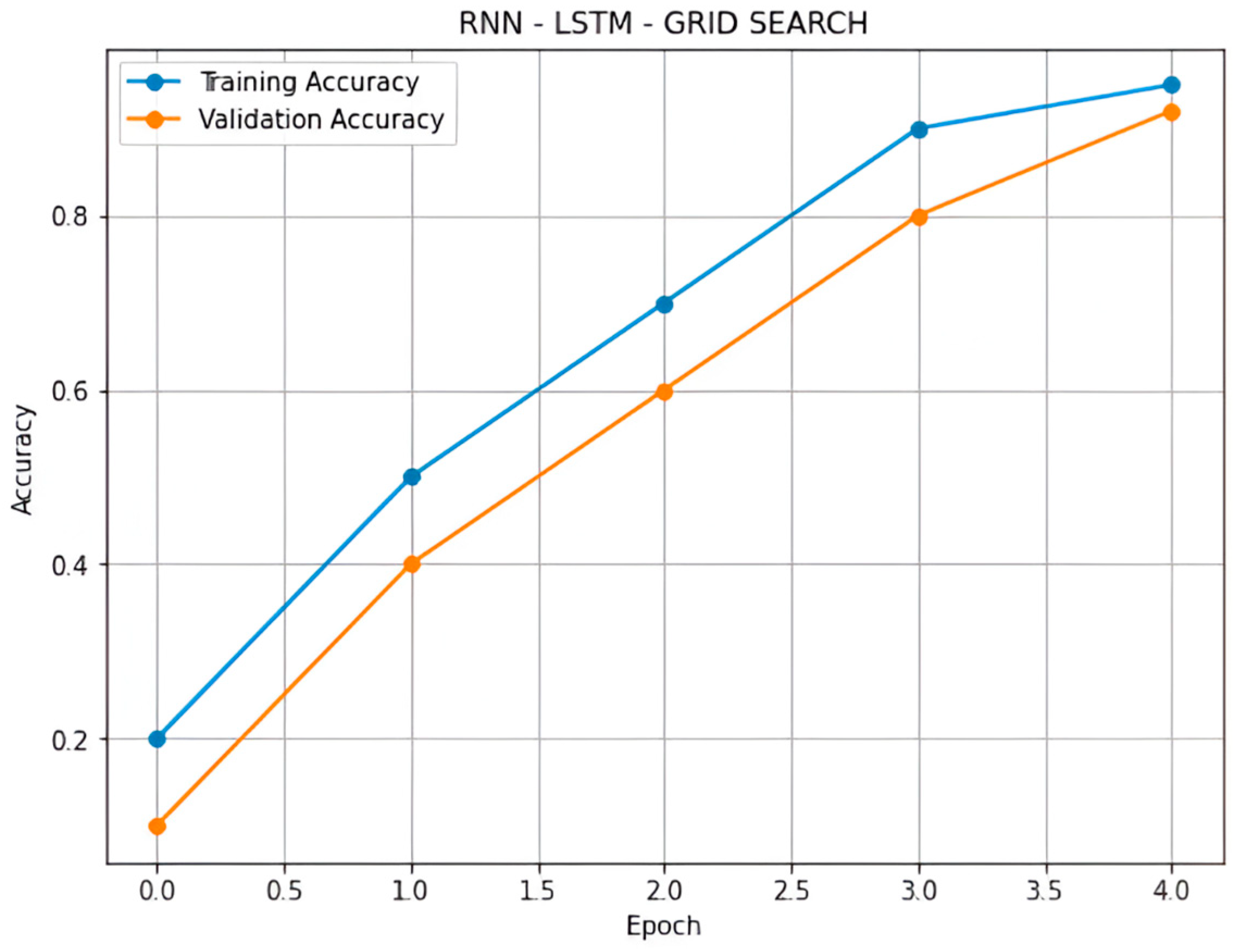
| RNN- LSTMGS | ICMP | 49 | 89 | 63 | 81 |
| Normal | 100 | 99 | 99 | 81 | |
| Smurf | 0 | 0 | 0 | 81 | |
| TCP | 82 | 100 | 90 | 81 | |
| Overall | 57 | 72 | 63 | 81 |
| Model | Class | P | R | F1 | A |
|---|---|---|---|---|---|
| DNN | ICMP | 33 | 33 | 27 | 71 |
| Normal | 100 | 100 | 100 | 100 | |
| Smurf | 33 | 6 | 10 | 18 | |
| TCP | 33 | 29 | 31 | 89 | |
| Overall | 50 | 39 | 42 | 71 | |
| DNN- SMOTE | ICMP | 53 | 89 | 67 | 89 |
| Normal | 100 | 99 | 99 | 99 | |
| Smurf | 72 | 22 | 33 | 22 | |
| TCP | 93 | 100 | 96 | 100 | |
| Overall | 86 | 85 | 83 | 85 | |
| DNNGS | ICMP | 64 | 85 | 73 | 89 |
| Normal | 100 | 99 | 99 | 89 | |
| Smurf | 82 | 54 | 65 | 89 | |
| TCP | 95 | 100 | 97 | 89 | |
| Overall | 85 | 84 | 84 | 89 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Terawi, N.; Ashqar, H.I.; Darwish, O.; Alsobeh, A.; Zahariev, P.; Tashtoush, Y. Enhanced Detection of Intrusion Detection System in Cloud Networks Using Time-Aware and Deep Learning Techniques. Computers 2025, 14, 282. https://doi.org/10.3390/computers14070282
Terawi N, Ashqar HI, Darwish O, Alsobeh A, Zahariev P, Tashtoush Y. Enhanced Detection of Intrusion Detection System in Cloud Networks Using Time-Aware and Deep Learning Techniques. Computers. 2025; 14(7):282. https://doi.org/10.3390/computers14070282
Chicago/Turabian StyleTerawi, Nima, Huthaifa I. Ashqar, Omar Darwish, Anas Alsobeh, Plamen Zahariev, and Yahya Tashtoush. 2025. "Enhanced Detection of Intrusion Detection System in Cloud Networks Using Time-Aware and Deep Learning Techniques" Computers 14, no. 7: 282. https://doi.org/10.3390/computers14070282
APA StyleTerawi, N., Ashqar, H. I., Darwish, O., Alsobeh, A., Zahariev, P., & Tashtoush, Y. (2025). Enhanced Detection of Intrusion Detection System in Cloud Networks Using Time-Aware and Deep Learning Techniques. Computers, 14(7), 282. https://doi.org/10.3390/computers14070282











