1. Introduction
The exponential growth of big data in recent years has revolutionized various sectors, including healthcare, finance, telecommunications, and smart cities. With data being generated at unprecedented volume, velocity, and variety, the need for secure and efficient mechanisms to store, transmit, and process these data has become critical. However, traditional security paradigms are increasingly being challenged by sophisticated cyberattacks and the looming threat posed by quantum computing, which has the potential to render many classical cryptographic algorithms obsolete. The generalized block diagram of big data security using quantum chaotic maps is shown in
Figure 1.
As shown in
Figure 1, data are collected from various sources, including IoT devices and social media. The data are ingested into the system for processing. The ingested data are stored in a database. Before storage, they are encrypted using quantum chaotic maps to ensure security. Quantum chaotic maps are used for both encrypting and decrypting data. Their complex and unpredictable nature makes the encryption extremely secure. The data are encrypted before being stored and decrypted when accessed. The encrypted data can be analyzed securely without the need to decrypt them entirely using homomorphic encryption techniques. Only authorized users, verified through quantum key distribution (QKD), can access the data. When data need to be transmitted across networks, it is carried out securely using encryption based on quantum chaotic maps.
The rapid advancement of quantum computing presents both opportunities and challenges in the realm of big data security. Traditional cryptographic methods, which underpin current data protection strategies, are increasingly vulnerable to quantum-based attacks. QKD leverages the principles of quantum mechanics to enable secure key exchange between parties, ensuring that any eavesdropping attempts can be detected. By utilizing quantum states, QKD provides a level of security unattainable by classical methods. The implementation of QKD in big data environments can significantly enhance the confidentiality and integrity of data transmissions.
QRNG utilizes inherent quantum uncertainties to generate truly random numbers, which are essential for cryptographic applications. Unlike classical random number generators, QRNGs are not deterministic and thus provide higher entropy, enhancing the security of encryption keys used in big data systems. QEC addresses the issue of decoherence and operational errors in quantum systems. By implementing QEC codes, it is possible to protect quantum information from errors due to environmental interactions, thereby ensuring the reliability of quantum-based security protocols in big data applications.
QDS schemes provide authentication mechanisms analogous to classical digital signatures but with security rooted in quantum mechanics. They enable the verification of message authenticity and integrity, crucial for secure communications in big data frameworks. In anticipation of quantum computers capable of breaking current cryptographic algorithms, the field of post-quantum cryptography focuses on developing new algorithms resistant to quantum attacks. These algorithms are designed to be secure against both classical and quantum adversaries, ensuring long-term security for big data systems.
The advent of quantum computing poses significant threats to existing cryptographic standards. Algorithms like Shor’s algorithm can efficiently factor large integers and compute discrete logarithms, rendering many current encryption schemes vulnerable. This necessitates the transition to quantum-resistant algorithms to protect big data assets. Recognizing the impending quantum threat, organizations like the National Institute of Standards and Technology (NIST) are developing post-quantum cryptography standards. These efforts aim to standardize algorithms that can withstand quantum attacks, providing a roadmap for securing big data infrastructures in the quantum era.
While quantum technologies offer promising enhancements to big data security, practical implementations face challenges such as scalability, integration with existing systems, and the need for significant infrastructural changes. Ongoing research focuses on addressing these challenges to facilitate the adoption of quantum-based security solutions. The integration of quantum computing into big data security is an evolving field. Future research is directed towards developing hybrid systems that combine classical and quantum techniques, improving the efficiency of quantum algorithms, and creating robust frameworks for the seamless incorporation of quantum security measures into existing big data architectures.
In our proposed framework, both quantum random number generation (QRNG) and quantum key distribution (QKD) are integrated to provide comprehensive security for big data systems. QRNG is employed to generate cryptographic keys with high entropy and unpredictability, leveraging quantum chaotic maps and the inherent randomness of quantum processes. This ensures that the keys used for encryption are truly random and resistant to classical and quantum attacks. However, generating secure keys alone is insufficient—these keys must also be distributed safely among authorized parties. This is where QKD plays a crucial role, enabling the secure transmission of encryption keys over potentially insecure channels while guaranteeing that any eavesdropping attempt can be detected due to the fundamental principles of quantum mechanics, such as the no-cloning theorem and measurement-induced disturbance. By combining QRNG for robust key generation with QKD for secure key exchange, our framework addresses both the strength and secure availability of cryptographic keys, thereby enhancing the overall security of big data processing and communication systems in the quantum era.
While our framework primarily focuses on integrating quantum key distribution (QKD) and quantum random number generation (QRNG) for secure key generation and distribution, it is important to acknowledge the role of quantum error correction (QEC) in ensuring the reliability of quantum communication systems. Both QKD and QRNG rely on the transmission or manipulation of quantum states, which are inherently fragile and susceptible to noise and decoherence from the environment. QEC techniques are designed to detect and correct such errors without directly measuring the quantum information, thus preserving its integrity. In practical implementations of QKD, for instance, QEC codes (often combined with privacy amplification techniques) are essential for correcting bit errors introduced during transmission and for distilling a shared, error-free secret key. Although QRNG is typically implemented locally and is less affected by transmission noise, QEC may still play a role in stabilizing quantum systems used in chaotic quantum processes to maintain the fidelity of the random output.
The intersection of quantum computing and big data security is a critical area of research, aiming to develop resilient security mechanisms capable of withstanding the advancements in quantum technology. The adoption of quantum-based solutions such as QKD, QRNG, QEC, and QDS, along with the development of post-quantum cryptographic standards, is essential for safeguarding big data against emerging quantum threats. To counteract these emerging threats, there is a pressing need to shift towards security solutions that are inherently quantum-resilient. This research presents a novel approach to enhance big data security by integrating quantum chaotic map of key sequence (QCMKS) with cutting-edge quantum technologies, namely, quantum random number generation (QRNG), quantum key distribution (QKD), quantum error correction (QEC), and quantum optical elements transformation (QOET). The synergy among these components offers a robust, future-proof framework for data protection. At the core of the proposed system is the quantum chaotic map, which leverages the inherent unpredictability of quantum systems and the sensitive dependence on initial conditions characteristic of chaotic maps. This fusion generates highly dynamic and non-repetitive key sequences that are extremely difficult to predict or reverse-engineer, even with quantum computational capabilities.
Quantum random number generation (QRNG) is employed as a foundational entropy source for seeding the chaotic map. Unlike classical pseudorandom number generators, QRNG utilizes quantum phenomena—such as the measurement of photon states—to produce truly random numbers, ensuring maximum entropy and eliminating any potential pattern or bias in key generation. Quantum key distribution (QKD) enables the secure exchange of cryptographic keys over quantum channels. By exploiting the principles of quantum mechanics—particularly the no-cloning theorem and quantum entanglement—QKD ensures that any eavesdropping attempt on the communication channel can be detected and mitigated in real-time.
In this work, we emphasize the importance of clearly defining emerging terminology, particularly the concept of a quantum chaotic map, which may otherwise be conflated with traditional notions of quantum chaos in physics. Unlike studies focused on quantum systems exhibiting classical chaotic behavior (quantum chaos), our use of quantum chaotic map refers to a hybrid construct wherein classical nonlinear chaotic maps—such as the logistic or tent map—are driven or seeded by entropy sources derived from quantum processes, notably quantum random number generators (QRNGs). These QRNGs provide high-quality, non-deterministic inputs that enhance the unpredictability and security strength of the chaotic map’s output. By integrating quantum-derived entropy with classical chaotic dynamics, we generate highly unpredictable sequences suitable for cryptographic key generation and secure communication protocols. This clarification ensures conceptual accuracy and distinguishes our methodology from conventional quantum dynamical system studies.
To address the imperfections and noise inherent in quantum communication systems, quantum error correction (QEC) is integrated into the framework. QEC techniques are crucial for maintaining the integrity and reliability of transmitted quantum information, allowing for correction of bit-flip, phase-flip, and more complex quantum errors without violating the fundamental rules of quantum mechanics. Further strengthening the system is the use of quantum optical elements transformation (QOET). Optical components such as beam splitters, phase shifters, and polarizers are used to manipulate qubits encoded in photons, allowing for precise control over quantum states and facilitating robust physical-layer transformations that support secure quantum transmission and processing. Collectively, this integrated architecture forms a multi-layered defense model for big data environments, providing a high level of confidentiality, integrity, and availability. By combining chaotic systems with quantum technologies, the proposed system not only anticipates the risks associated with future quantum attacks but also introduces a new paradigm in secure data management that is adaptive, scalable, and resilient.
Quantum technologies have emerged as powerful tools for enhancing information security, particularly in the era of quantum computing, where classical encryption methods face increasing vulnerabilities. Our proposed framework integrates quantum random number generation (QRNG), quantum key distribution (QKD), quantum error correction (QEC), and quantum chaotic maps to enhance the unpredictability and resilience of cryptographic systems. However, it is important to acknowledge that the security and robustness benefits described herein are contingent upon several practical factors. These include the reliability and precision of quantum hardware components, susceptibility to environmental noise, and the challenges of integrating quantum subsystems into classical big data infrastructures. While our simulations indicate strong theoretical advantages, real-world deployment will depend on the continued advancement of hybrid classical–quantum systems, scalable quantum network architectures, and fault-tolerant quantum devices.
2. Related Work
In the modern digital landscape, big data systems handle vast amounts of sensitive information, necessitating robust security frameworks. At the heart of secure communication lies the challenge of effective key distribution. Classical key distribution primarily involves symmetric and asymmetric cryptography, often utilizing Public Key Infrastructure (PKI) systems. However, with the evolution of computational capabilities, especially the looming threat of quantum computing, these systems face vulnerabilities [
1,
2]. QKD leverages quantum mechanics, making eavesdropping theoretically detectable. The BB84 protocol, developed in 1984, remains the most studied and implemented QKD method [
3,
4]. Subsequent work by Lo et al. [
5] and Scarani et al. [
6] expanded on the practicality and security proofs. Hybrid systems integrating classical and quantum methods are gaining traction to enhance resilience and compatibility [
7]. Post-quantum cryptography (PQC), which includes lattice-based and hash-based schemes, is being standardized by NIST [
8].
Secure key management in distributed cloud systems and IoT-enabled environments is crucial for scalable big data security [
9,
10]. Techniques involving distributed key generation and trusted hardware modules are emerging to address these concerns [
11]. Artificial intelligence (AI) and blockchain are also being explored for secure and decentralized key distribution [
12,
13]. AI optimizes key management, while blockchain offers immutable and decentralized infrastructure. Despite theoretical advances, real-world deployment of QKD faces challenges such as transmission distance, hardware sensitivity, and integration with classical infrastructure [
14,
15]. Future research focuses on enhancing QKD scalability, standardizing PQC algorithms, and integrating AI-driven automation in key management systems [
16,
17,
18,
19,
20].
Random number generation (RNG) is a foundational element in modern cryptographic systems, especially in securing big data environments. With the growing demand for secure data transmission, storage, and computation, the integrity of RNG mechanisms becomes paramount. Random numbers are used for generating keys, nonces, initialization vectors, and other cryptographic elements. Weak or predictable RNGs can lead to severe vulnerabilities in big data security systems [
21,
22]. Pseudorandom number generators (PRNGs) use deterministic algorithms that produce numbers with properties approximating true randomness. These are widely used in software-based encryption but are vulnerable if the seed is known [
22,
23]. Cryptographically secure PRNGs (CSPRNGs) like those used in AES-based and SHA-based algorithms ensure unpredictability even with partial knowledge of internal states [
24].
True random number generators (TRNGs) rely on physical processes (e.g., thermal noise, radioactive decay) and are considered more secure but harder to implement in software-only environments [
25,
26]. NIST’s SP 800-90A/B/C provides design principles and testing criteria for secure RNG implementations [
26,
27]. In cloud computing and big data systems, secure RNG is used to manage distributed encryption keys, secure multi-party computation, and anonymization [
27,
28]. Historical failures like the Dual_EC_DRBG debacle illustrate the importance of transparency and scrutiny in RNG algorithm design [
28,
29]. Quantum random number generators (QRNGs) harness quantum phenomena such as photon polarization to generate high-entropy numbers and are being explored for future-proofing big data security [
30,
31,
32]. Statistical tests like NIST STS, Diehard, and ENT are commonly used to evaluate the randomness quality in RNG outputs [
33,
34]. Emerging trends involve hybrid RNG models combining TRNG and PRNG, hardware-based solutions, and integration of blockchain and AI for entropy monitoring [
35].
Big data security has emerged as a crucial research area due to the increasing scale, velocity, and complexity of data being generated and processed. As organizations rely on big data analytics for decision-making, protecting these data against breaches, unauthorized access, and misuse becomes critical. Access control mechanisms ensure that only authorized users can interact with specific data components in big data systems. Role-based access control (RBAC) and attribute-based access control (ABAC) have been widely applied [
36,
37,
38]. Encryption is a cornerstone of data security. Techniques like homomorphic encryption and searchable encryption are gaining traction for processing encrypted data without compromising confidentiality [
39,
40,
41]. Privacy-preserving techniques such as k-anonymity, l-diversity, and differential privacy are vital when dealing with sensitive data in big data environments [
42,
43,
44].
Intrusion detection in big data systems is challenging due to high-speed data streams and complex architectures. Machine-learning-based Intrusion Detection Systems (IDSs) have shown promise in identifying anomalies [
45,
46,
47]. Blockchain provides immutable and transparent data logs, making it suitable for secure data provenance and sharing [
48,
49]. Artificial intelligence (AI) is used for predictive threat detection and adaptive security mechanisms [
50,
51]. Several integrated security frameworks have been proposed to address the end-to-end security requirements in big data pipelines [
52,
53,
54,
55].
To provide a broader context for readers and to emphasize the diversity of available QKD techniques, it is important to highlight recent advancements in high-dimensional entanglement-based QKD protocols. These approaches extend beyond traditional qubit-based systems by encoding information in high-dimensional quantum states, such as the orbital angular momentum of photons. This enables a higher information capacity per photon, improved noise resilience, and enhanced security against certain types of attacks. Such protocols are particularly advantageous in bandwidth-constrained or high-noise environments—conditions commonly encountered in practical big data transmission scenarios. Integrating high-dimensional QKD schemes within our framework offers a promising path to increase key rates and system efficiency, especially when combined with quantum chaotic key generation mechanisms. Recent work by [
56] provides an excellent demonstration of high-dimensional entanglement-based QKD using photonic systems, showcasing its experimental viability and potential for deployment in future quantum communication infrastructures.
The advent of quantum computing has catalyzed significant research into post-quantum cryptographic (PQC) schemes designed to resist quantum attacks. Prominent directions include lattice-based cryptography, which underpins many National Institute of Standards and Technology (NIST) PQC candidates such as CRYSTALS-Kyber and Dilithium. These schemes offer strong security based on the hardness of lattice problems like Learning With Errors (LWE), which remains resilient against both classical and quantum adversaries [
57,
58]. Similarly, multivariate polynomial-based approaches such as Rainbow and GeMSS have been investigated for their lightweight signature capabilities [
59], though recent cryptanalyses have prompted a re-evaluation of their long-term viability.
Parallel to purely classical PQC methods, hybrid cryptographic models combining classical post-quantum techniques with quantum key distribution (QKD) are gaining attention for enhancing transitional security. Studies such as [
60,
61] explore layered encryption architectures where QKD securely exchanges session keys, while PQC algorithms manage data confidentiality. This hybrid approach leverages the provable security of quantum protocols with the performance and maturity of classical schemes, enabling robust defense against both quantum and pre-quantum threats.
From a systems integration perspective, recent work has explored architectures that support the practical deployment of hybrid quantum-secure infrastructures. For instance, ref. [
62] proposes an integration framework for synchronizing quantum entropy sources with classical cryptographic APIs, facilitating seamless transition to quantum-resilient systems. In a similar vein, ref. [
63] investigates the challenges of combining PQC with QRNGs in IoT environments, emphasizing entropy synchronization, key freshness, and performance overhead management. The latest NIST report—[
64]—documents the progression of the Post-Quantum Cryptography Standardization Project, including the conclusion of Round 3 and the selection of final candidates such as CRYSTALS-Kyber for public key encryption and CRYSTALS-Dilithium for digital signatures. The report also outlines the objectives of Round 4, which continues to evaluate alternate candidates like BIKE, Classic McEliece, HQC, and SIKE for broader cryptographic diversity and robustness against evolving quantum threats [
64]. This evolving landscape reinforces the need for hybrid frameworks and enhanced entropy mechanisms, such as those explored in our work, to complement standardized algorithms during the migration phase from classical to quantum-secure infrastructures.
Our proposed system extends this research by introducing a quantum chaotic map framework—utilizing QRNG-generated entropy modulated via classical chaotic functions—to generate secure key material. While distinct from conventional quantum chaos theory, our approach aligns with emerging hybrid strategies by enhancing key unpredictability using quantum-inspired nonlinearity, as discussed in [
65]. By contextualizing this system within the broader landscape of PQC and hybrid models, we underscore its potential to complement existing quantum-safe security architectures.
3. Assessment of Big Data Security Using Quantum Chaotic Maps
Quantum chaotic maps provide high levels of complexity and unpredictability, making it extremely difficult for attackers to predict or reverse-engineer the encryption keys. The use of quantum principles means that traditional cryptographic attacks (such as brute force, linear, or differential cryptanalysis) are less effective. The keys generated by quantum chaotic maps have high entropy, which enhances the strength of the encryption. QKD ensures that encryption keys are securely distributed, further bolstering security by eliminating the risks associated with key exchange over classical channels.
The encryption and decryption processes using quantum chaotic maps is computationally intensive due to the complexity of quantum operations. However, advancements in quantum computing are expected to mitigate these concerns. Generating keys through quantum chaotic maps require significant computational resources, but this process is typically performed infrequently compared to data encryption/decryption operations. Quantum chaotic maps can be applied to large volumes of data typical in big data environments. However, the scalability of this approach depends on the efficiency of quantum computations and the capacity to handle large-scale quantum data processing. Implementing quantum chaotic maps requires access to quantum computing infrastructure, which can be a limiting factor due to current technological and cost barriers. Ensuring seamless integration of quantum encryption with existing big data frameworks (like Hadoop or Spark) is crucial for scalability.
The practical implementation of quantum chaotic maps relies on the maturity of quantum computing technology, which is still in the developmental stages. Quantum systems are susceptible to noise and errors, necessitating robust error correction techniques to ensure reliable encryption and decryption processes. Implementing and maintaining a quantum-based security system requires specialized knowledge in quantum mechanics, cryptography, and big data analytics. Developing and deploying quantum chaotic maps for big data security can be resource-intensive, involving significant investment in research, hardware, and training. Quantum chaotic maps provide enhanced security compared to traditional cryptographic methods due to their inherent complexity and use of quantum principles. As quantum computers advance, traditional encryption methods (like RSA and ECC) may become vulnerable. Quantum chaotic maps offer a more future-proof solution. The computational and infrastructural overheads associated with quantum chaotic maps are currently higher than traditional methods, but this is expected to improve with technological advancements.
A performance evaluation of big data security using quantum chaotic maps involves considering various criteria such as security robustness, computational efficiency, scalability, integration complexity, and potential future readiness, as indicated in
Table 1. It can be observed from
Table 1 that quantum chaotic maps provide exceptional security, leveraging both chaotic and quantum principles to ensure high unpredictability and resistance to attacks. Current quantum technology is computationally intensive, but efficiency is expected to improve with advancements in quantum computing. It is scalable in theory, but practical implementation depends on the maturity of quantum computing infrastructure. Integrating quantum chaotic maps with existing big data systems is complex and requires expertise in both quantum mechanics and big data technologies. Quantum chaotic maps generate highly secure keys with high entropy, making the encryption process robust. QKD provides a highly secure method for key distribution, essential for maintaining the integrity of the encryption system. Quantum systems are prone to noise and errors, necessitating advanced error correction techniques which are still in development. Implementing a quantum-based security system requires significant resources, both in terms of hardware and specialized knowledge.
Quantum chaotic maps are well positioned to address future security challenges, particularly with the advent of quantum computing. The high cost of quantum infrastructure and expertise is a barrier, though the long-term benefits may justify the investment. Additional overheads are introduced due to the complexity of quantum operations but can be managed with adequate resources. Advanced security measures position the system well for compliance with future regulatory standards focused on quantum cryptography. The system requires specialized knowledge to set up and maintain, though efforts can be made to simplify user interfaces for administrators and end-users. A comparative analysis for big data security using quantum chaotic maps versus existing approaches involves assessing various key aspects like encryption strength, complexity, performance, scalability, resistance to attacks, and application scenarios is shown in
Table 2.
Quantum chaotic maps leverage principles from quantum mechanics and chaos theory, making them potentially more secure than classical encryption methods. While quantum chaotic maps can be computationally intensive, they offer a trade-off between enhanced security and processing time. Existing approaches like AES offer a balance between security and performance, whereas RSA is known for its higher computational load. Both quantum chaotic maps and AES are scalable and suitable for big data applications, although the former is still emerging. Quantum chaotic maps provide strong resistance to both classical and quantum attacks, a significant advantage over classical methods that are vulnerable to quantum computing advances. Implementing quantum chaotic maps is complex and requires new key management paradigms, whereas existing methods benefit from established key management frameworks. Quantum computations can be power-intensive, posing a challenge for widespread adoption without further technological advancements to improve efficiency. Existing methods have clear regulatory guidelines and a high level of maturity, making them reliable for current use. Quantum chaotic maps, however, are still in the research phase and lack standardized regulatory frameworks.
As shown in
Table 3, performance evaluation for utilized quantum hardware in the context of big data security using quantum chaotic maps should include various metrics such as computation speed, error rates, scalability, power consumption, security level, and practical implementation considerations. Quantum operations offer significant speed advantages, but error correction and large datasets can introduce delays. Effective error correction is crucial to maintain low error rates, ensuring reliable quantum computations. Quantum systems have high scalability potential, but current technology imposes practical limits. Power consumption is high due to the need for cryogenic cooling and the operational power of quantum processors. Security level is very high, with strong resistance to both classical and quantum attacks due to the inherent properties of quantum chaotic maps.
Adequate coherence time is necessary for successful quantum operations, varying by qubit type. Implementation complexity is high, requiring advanced expertise and integration of multiple cutting-edge technologies. Maintenance requirements are high, with ongoing needs for calibration and system maintenance. Cost is high, encompassing both initial setup and ongoing operational expenses. Operational stability is achievable with robust error correction and environmental controls, but it is challenging. Algorithm development is complex, necessitating specialized knowledge in quantum mechanics and chaotic systems. Integration with classical systems is challenging, requiring significant engineering to ensure efficient interoperability. Data throughput is moderate, capable of handling large datasets but dependent on hardware capabilities. Latency is low for small-scale operations and moderate for large-scale ones due to error correction and complexity.
The quantum advantage is potentially high, offering enhanced security and computational advantages over classical methods. Its environmental impact is high, primarily due to the substantial energy requirements for cooling and operation. A performance analysis for big data security using quantum chaotic maps across different scenarios involves evaluating how the technology performs under various conditions, as shown in
Table 4.
Quantum chaotic maps excel in encrypting small datasets quickly with minimal latency, leveraging quantum speedup for efficient operations. Encryption of large datasets is slower due to increased complexity and the overhead of error correction but maintains strong security. The approach is capable of processing data in real time with moderate computation speed, ensuring high security while maintaining low latency. It demonstrates high potential for scalability to handle exponentially larger datasets, showcasing robust security features. Effective error correction mechanisms maintain computation integrity despite moderate error rates. Integration requires significant engineering effort but achieves moderate-to-high operational stability. Efficient data throughput within quantum networks ensures secure communication across nodes with very high security. Operational stability is challenging in extreme environments but maintains high security with quantum chaotic maps.
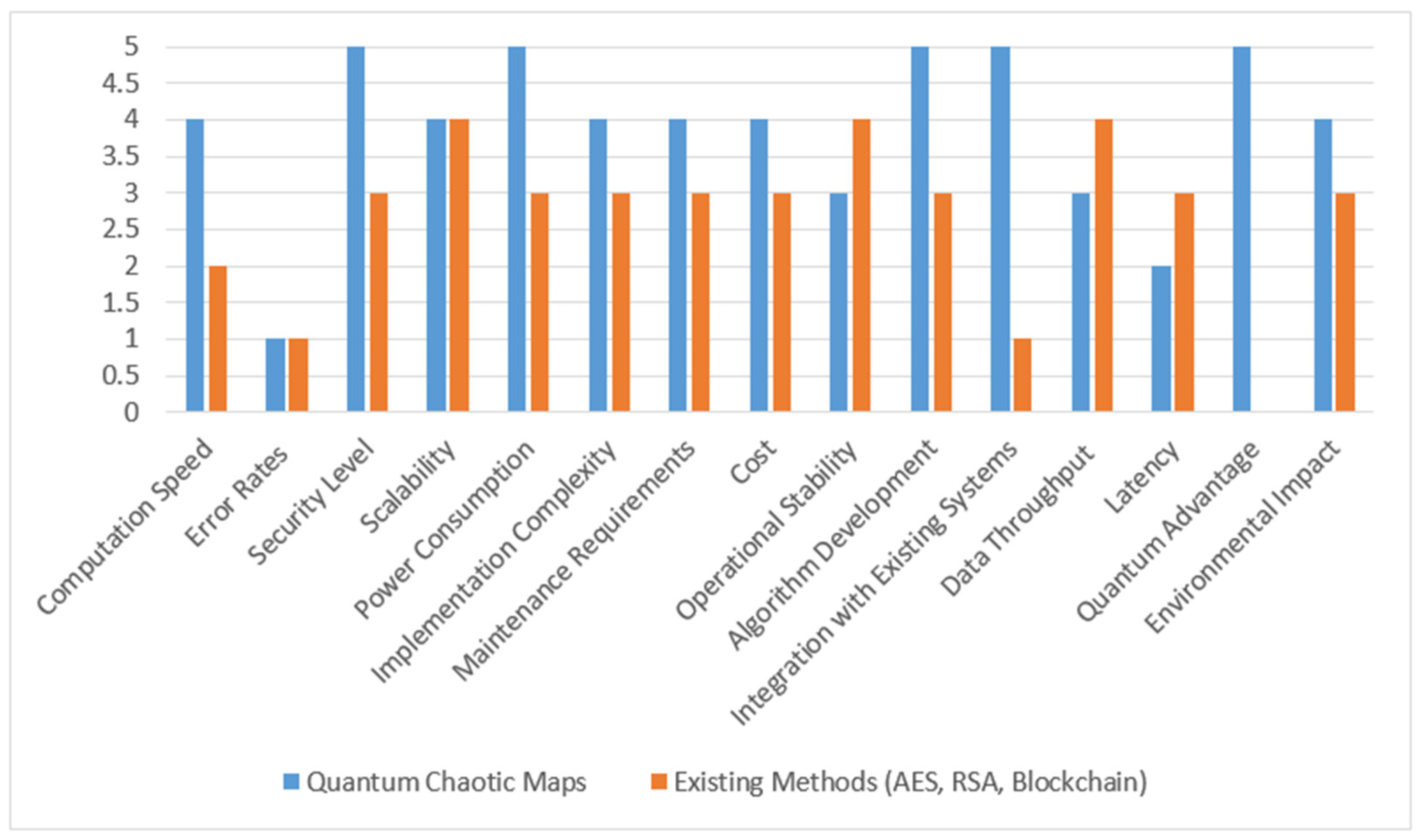
Figure 2 shows a comprehensive evaluation of big data security using quantum chaotic maps compared to existing big data technologies across various critical metrics, highlighting the unique benefits and challenges of quantum solutions in securing and processing large datasets. This graph provides a visual comparison of quantum chaotic maps against existing methods in terms of various performance metrics crucial for big data security. It highlights where quantum chaotic maps excel and where improvements or considerations are necessary compared to traditional methods.
4. Quantum Random Number Generation for Big Data Security
The security of big data systems heavily relies on the robustness of cryptographic keys, which, in turn, depend on the quality of the random numbers used in their generation. Traditional pseudorandom number generators (PRNGs) often fall short in providing true randomness, making them vulnerable to prediction and cryptographic attacks. Quantum random number generation (QRNG) offers an inherent advantage by leveraging quantum mechanical phenomena to generate truly unpredictable sequences. To further enhance the randomness and complexity, we propose integrating quantum chaotic maps into the key sequence generation process.
Quantum randomness arises from the indeterminate outcomes of quantum measurements, such as photon path detection, spin state measurements, or vacuum fluctuations. Chaotic systems are sensitive to initial conditions and produce highly complex and unpredictable behavior, making them suitable for amplifying entropy. Big data security needs demand scalable, high-speed, and highly secure key generation to protect vast volumes of sensitive data distributed across networks. Combining quantum randomness with chaotic maps enables a hybrid QRNG system that enhances entropy and security for cryptographic operations in big data systems.
A quantum entropy source (e.g., beam splitter with single-photon detectors) is used to generate base random bits from photon arrival time differences; vacuum fluctuations (optical or electrical); and quantum phase noise. The raw quantum bits are fed into a quantum logistic map or quantum tent map:
These maps are initialized using quantum seeds and continuously updated with quantum-generated data to avoid periodicity.
The chaotic output is digitized and passed through a hashing and compression layer (e.g., SHA-3) to eliminate bias and extract usable bit sequences, which are then structured into key sequences of required bit lengths (e.g., 128, 256, 512 bits). Quantum error correction codes (e.g., Shor’s or Steane’s codes) are applied to ensure the stability and accuracy of the generated keys in noisy environments. The QRNG module can be interfaced with distributed file systems (HDFS); NoSQL databases; or real-time analytics platforms (Apache Kafka, Spark). Each transaction, data transfer, or storage operation utilizes a unique QRNG-generated key. The advantages of proposed QRNG with a chaotic map over conventional RNG are specified in
Table 5.
Let the quantum entropy source generate a raw bitstream from a quantum phenomenon, such as photon arrival time difference or vacuum fluctuation. Let
denote the quantum signal at time
and
be the raw quantum random bit sequence, such that:
Each bit
is assumed to follow a Bernoulli distribution with the following:
assuming ideal quantum randomness.
A chaotic map is introduced to enhance entropy. One commonly used map is the logistic map:
Let the quantum-generated bits initialize
by converting a block of bits to decimal:
The sequence
is iterated to generate highly chaotic values. To amplify complexity, a second chaotic function like the tent map can be combined:
The final chaotic output is as follows:
Each chaotic value
is converted into a binary subsequence
using fixed-point representation:
where
is the bit precision (e.g., 32 or 64 bits). The final random number sequence becomes:
Cryptographic hashing (e.g., SHA-3 or Keccak) is applied for entropy smoothing:
The final key sequence (or other length depending on application) is used for encryption, signing, or authentication in big data security pipelines.
Quantum error correction can be applied if physical noise distorts the raw quantum signal. For example, with Shor’s code:
Noise resilience is preserved before further chaotic transformation.
For mathematical justification of entropy and randomness, let
be the binary random variable representing each bit in the final bitstream.
For maximum entropy (perfect randomness),
, so:
In our simulation, entropy ≈ 0.9999 confirms near-uniform distribution, which supports unpredictability and security.
The flow of the proposed QRNG system using a quantum chaotic map is shown in
Figure 3. In the quantum entropy source, a physical quantum phenomenon (e.g., photon detection) is simulated, which generates the initial random seed
for the chaotic map. The chaotic map engine applies a logistic or tent map to generate a non-periodic, sensitive, and complex number sequence. It amplifies entropy and ensures unique outputs even from tiny differences in the seed. In bit conversion, floating-point outputs are transformed into binary strings using fixed-point representation. All binary chunks are concatenated to form a long random bitstream. SHA-3/Keccak hash is applied to clean any statistical irregularities. The bitstream is converted into a secure and uniform-length key (e.g., 256-bit key). The final cryptographic key can be used in big data encryption, secure key exchanges, and quantum-resistant communication protocols.
We simulated the quantum entropy source using Python’s 3.9 np.random.rand() to generate a random floating-point number between 0 and 1. This mimics quantum randomness (like a photon detection event or vacuum fluctuation). We use the logistic map
. Chaotic behavior emerges when
. It is ensitive to the initial seed
, ensuring no repetition. A total of 1000 iterations were run, generating chaotic outputs
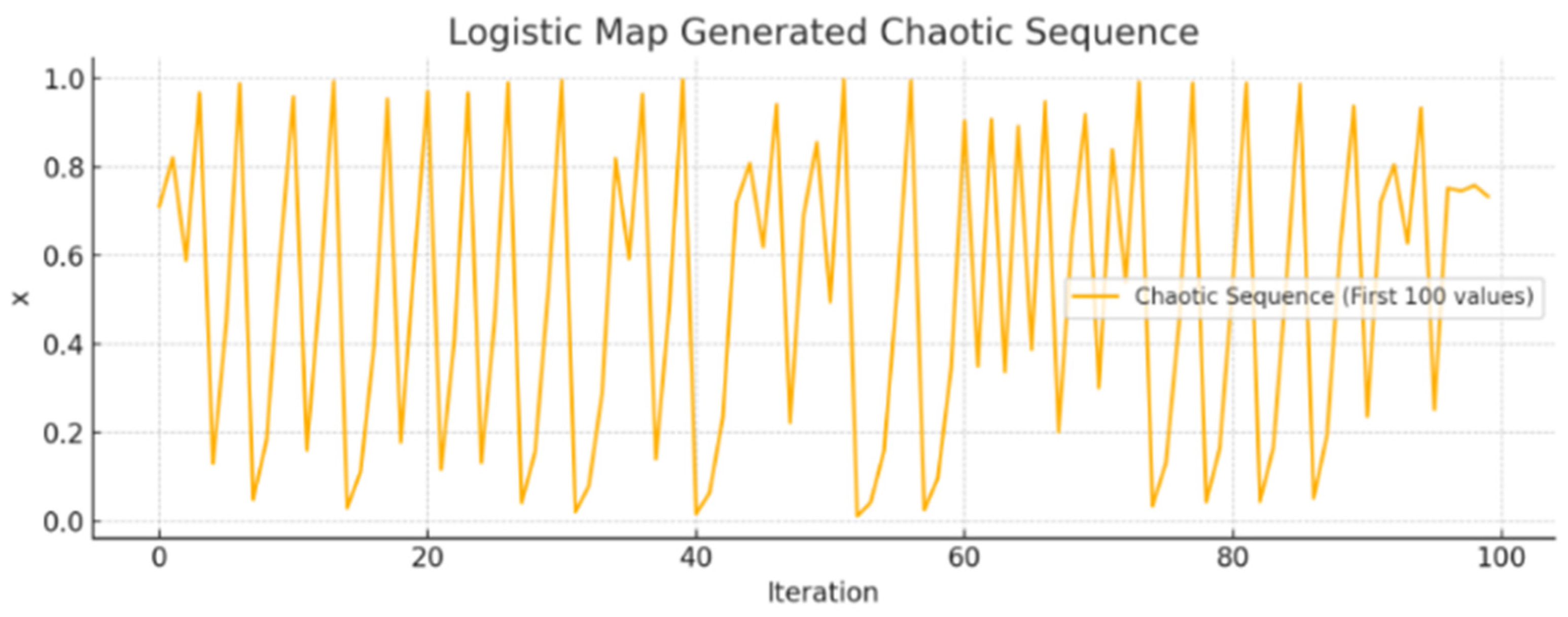
. Each chaotic float is converted into a 32-bit binary string using fixed-point encoding. All binary strings are concatenated to form a large bitstream representing highly entropic data. The long bitstream is hashed using SHA3-256. This removes any residual bias, compresses the randomness into a 256-bit cryptographic key, and ensures irreversibility and high unpredictability. We calculated the Shannon entropy of the bitstream result ≈ 0.9999. The maximum theoretical entropy for a binary stream is 1. So, our bitstream is almost perfectly random, making it suitable for cryptographic key generation. The generated chaotic sequence using the logistic map is shown in
Figure 4. This figure illustrates the chaotic behavior of the logistic map with a control parameter r = 3.99, a commonly used value in chaos-based cryptographic applications. The sequence demonstrates sensitive dependence on the initial conditions and aperiodicity, key features that contribute to its entropy generation capability for quantum random number generation (QRNG) and secure key derivation. This visualization highlights the unpredictability and nonlinearity of the system, which are essential properties leveraged in our quantum-enhanced big data security framework.
The resulting Shannon entropy ≈ 0.9999 (ideal entropy = 1 for binary uniform distribution) indicates near-perfect randomness in the generated bitstream, which is suitable for cryptographic applications. The sample hashed key output is 8bf65b5d3bd5b6675675daaf54ff0d86dc76b99faf79eb38646034a655c08f57. This is the final 256-bit key, generated from quantum-seeded chaotic randomness and hashed using SHA3-256.
A comparison of the proposed QRNG with existing RNG is shown in
Table 6. Traditional pseudorandom number generators (PRNGs), such as the Mersenne Twister, are algorithmic systems that produce sequences which appear random but are ultimately deterministic. While they offer computational efficiency and long periods, their output is inherently predictable if the seed is known. This predictability poses a serious risk in cryptographic applications, particularly in big data environments where high entropy and strong security are critical. In contrast, the proposed quantum–chaotic random number generator (QRNG–chaotic) significantly improves upon these limitations by incorporating a quantum entropy source as the initial seed, followed by chaotic map transformation (e.g., logistic map) and cryptographic post-processing using SHA3-256. The quantum seed ensures true randomness due to the inherent uncertainty in quantum measurements, while the chaotic dynamics amplify entropy and introduce extreme sensitivity to initial conditions, making the output non-replicable. Entropy analysis of the generated bitstream yields a near-ideal value of 0.9999, compared to approximately 0.96 in typical PRNGs. Additionally, the combination of quantum unpredictability and chaos results in a non-periodic, highly secure key sequence suitable for big data security systems. Unlike PRNGs, which can be reverse-engineered or replicated, the QRNG–chaotic system provides a robust, entropy-rich solution capable of meeting the security demands of real-time encryption, distributed storage, and quantum-resilient communication protocols.
The simulation confirms the true randomness, enhanced by chaos. The system integrates quantum entropy, chaos theory, and cryptographic hashing. This method is scalable, secure, and highly suitable for big data security frameworks. This proposed QRNG system using a quantum chaotic map of the key sequence provides a novel approach to fortifying big data security. Future work will include implementing FPGA/ASIC-based QRNG chips for high-speed operations and integrating post-quantum cryptographic primitives to support hybrid encryption in quantum-era data environments.
5. Quantum Key Distribution for Big Data Security
Quantum key distribution (QKD) is a cornerstone of quantum cryptography, allowing two legitimate parties (commonly referred to as Alice and Bob) to establish a shared, secret key over an untrusted communication channel, with security guaranteed by the laws of quantum mechanics. However, in large-scale big data systems, the classical QKD protocols (e.g., BB84, E91) may encounter scalability and randomness quality issues, especially under noisy or high-throughput conditions. To address these challenges, we propose an enhanced QKD protocol that integrates a quantum chaotic map of key sequence into the quantum key generation and post-processing steps. This hybrid approach leverages both quantum and chaotic entropy to generate high-quality random keys and applies them in a QKD framework suitable for large-scale, distributed, and real-time big data security.
The proposed QKD architecture comprises the following key stages: quantum entropy extraction, chaotic amplification, bitstream construction, quantum key exchange (BB84-based), post-processing with error correction, and privacy amplification. Quantum random numbers are generated using quantum optical devices (e.g., beam splitters, photon detectors) or quantum simulation circuits (e.g., Hadamard-based Qiskit circuits). The quantum seed is input to a chaotic map (e.g., logistic, tent, or Arnold’s cat map) to amplify entropy and ensure extreme sensitivity to initial conditions. Each chaotic output is converted into binary form and assembled into a key bitstream. The key bits are transmitted using quantum states of photons (e.g., polarization states in BB84), with basis randomization and post-measurement reconciliation. Error-correcting codes (e.g., LDPC, Cascade) and cryptographic hash functions (e.g., SHA-3) are applied to correct transmission errors and eliminate any residual eavesdropper knowledge.
A comparison of the proposed QKD with traditional QKD is shown in
Table 7. Rooted in both quantum uncertainty and chaotic unpredictability, the system ensures that eavesdroppers cannot predict or replicate the key. The chaotic expansion step allows for longer keys to be generated from small quantum seeds, reducing hardware load and enabling high-throughput key exchange.
Let us assume Alice and Bob use Qiskit-based quantum circuits to generate 4-bit seeds:
Alice generates a seed: 1010 (quantum-generated);
She feeds it into a logistic map to obtain chaotic values → binary sequences;
She uses the BB84 protocol to send qubits (e.g., polarization of photons);
Bob measures using randomly chosen bases;
Both communicate classically to discard mismatched bases;
The remaining key bits undergo error correction and hashing.
The final shared key is used for AES/GCM encryption of large-scale data in motion (e.g., between cloud clusters or IoT edge nodes).
Let the initial entropy source be generated by quantum superposition and measurement of qubits. A quantum bitstring
is produced via Hadamard-transformed qubits:
The quantum seed
is derived as:
A chaotic map (e.g., the logistic map) is used to amplify entropy and generate a key sequence. The logistic map is defined as:
The following is iteratively computed:
Each
is converted to a binary value
using thresholding:
The binary sequence
is encoded into quantum states. Bases are defined as follows:
For each bit
, a basis
is randomly chosen. The following is encoded:
Bob receives and measures using randomly chosen bases If , the measured bit equals .
Alice and Bob communicate over a classical channel to reveal their basis choices. Only bits where
are kept. Let the sifted key be the following:
Let
be the observed quantum bit error rate (QBER). Error-correcting codes (e.g., Cascade protocol or LDPC) are applied to reconcile errors:
A strong universal hash function
can be used to compress the key, eliminating possible eavesdropper knowledge:
Let
be the mutual information between Eve and the raw key. After privacy amplification, the security is as follows:
where
is the final key length and
is the security parameter.
This model ensures that the key sequence used in QKD is both unpredictable and information-theoretically secure while also supporting chaotic entropy expansion to reduce quantum hardware overhead. The proposed approach is evaluated using a simulation which integrates a chaotic map (logistic map) to generate quantum key bits (0 or 1) and encoding basis choices (rectilinear vs. diagonal). The sender and receiver independently generate chaotic basis choices. Where these match, the measurement outcomes are valid. The final sifted key is extracted from matching indices only. The simulation results in
Figure 5 illustrate the feasibility of integrating chaotic expansion into real QKD systems, enhancing entropy and resistance against predictable attacks. These chaotic sequences are used by both the sender and the receiver to encode and decode photons, mimicking the BB84 protocol with a physical randomness enhancement.
Figure 5 demonstrates the basis agreement process in a BB84 quantum key distribution (QKD) simulation, where both sender and receiver bases are determined using a chaotic logistic map. The plot shows 42-bit indices with the corresponding basis choices: sender (blue dashed), receiver (orange dashed), and a binary match indicator (green line), where 1 signifies matched bases. These matches form the basis for secure key extraction in QKD. Using chaotic sequences to determine measurement bases introduces an additional layer of unpredictability, enhancing the security of the protocol by resisting deterministic attacks. This visualization validates the protocol’s effectiveness in establishing shared keys under chaotic-driven randomness, aligning with our proposed quantum-enhanced cryptographic system.
The graph visualizes the interaction between the sender’s and receiver’s basis selections over a series of 50 quantum bits, where the choices are derived from a logistic chaotic map. The blue line indicates sender bases, which represent the bases (0 or 1) used by the sender to encode each qubit: rectilinear basis , diagonal basis . The orange line shows receiver bases, which represent the bases used by the receiver to measure each qubit. The green line shows the basis match indicator. The binary vector shows 1 when the sender’s and receiver’s bases match and 0 when they do not. These matching points are where sifted keys are extracted securely. The logistic map ensures high entropy and apparent randomness, yet small variations in initial conditions still yield enough coinciding basis choices to generate a secure shared key. Only matched bases (green line = 1) contribute to the final sifted key. This chaotic version of BB84 introduces quantum unpredictability plus additional classical complexity, making it harder for an eavesdropper to guess the basis pattern or intercept meaningful information.
The proposed QKD system, powered by a quantum chaotic map of key sequence, provides a robust, entropy-rich, and scalable framework for big data security. It outperforms classical PRNG-based systems and traditional QKD by enhancing both randomness quality and post-processing resilience. This makes it ideal for integration into quantum-secure big data infrastructures, including cloud platforms, smart grids, and critical IoT networks.
6. Quantum Error Correction for Big Data Security
Quantum error correction (QEC) is essential for protecting quantum information from decoherence, noise, and operational faults in quantum communication and computation. Traditional QEC methods such as the Shor, Steane, or surface codes are highly effective in correcting bit-flip, phase-flip, or both errors. However, in large-scale big data systems, where secure quantum key exchange and quantum-enhanced processing are involved, standard QEC approaches may face scalability challenges and redundancy inefficiencies. To enhance both security and fault tolerance, we propose a novel chaotic-seeded QEC scheme where the error-correcting code is dynamically modulated using a quantum chaotic key sequence. The incorporation of this randomness increases unpredictability in code structures, improves adaptability to varying noise profiles, and enhances cryptographic robustness against quantum side-channel or structural attacks.
The architecture is based on embedding chaotic entropy into the parity-check or syndrome extraction matrices used in QEC. The key steps include quantum seed extraction, chaotic map processing, and code structure modulation. In quantum seed extraction, quantum random number generation (QRNG) is carried out using Qiskit or optical hardware. The seed is transformed into a floating-point value .
In chaotic map processing, a logistic map is used , where , and the initial is quantum-seeded. In code structure modulation, a chaotic binary stream { is generated from the chaotic output. This stream is used to dynamically select syndromes in parity-check matrices , alter encoding matrices , and modify syndrome detection patterns. This approach applies to various QEC codes like LDPC codes where chaotic bits select columns to flip or vary weights, surface codes where chaotic bits define topology or gate sequence variance, and CSS codes which use the chaotic key sequence to rotate stabilizer selection.
Let
be a quantum error (bit-flip
, phase-flip
, or both
),
be the QEC code structure, and
be the chaotic sequence generated from a quantum seed. QEC encoding is applied using the following:
The following error model is used:
The chaotic-decoded syndrome is computed using the following:
The correction is applied using the following:
The randomness in
ensures that even if the QEC structure is partially leaked, the full correction mapping remains secure and unique per session. The security and performance benefits of the proposed QEC are compared in
Table 8 with classical QEC. In a secure cloud or edge data pipeline, quantum chaotic key sequences are used not only for encryption but also to vary QEC structures. This dual use creates key-dependent error correction, eliminating vulnerabilities from fixed error patterns or replay attacks. It is especially useful in post-quantum encrypted storage, distributed quantum cloud, and federated quantum machine learning where fault tolerance meets entropy demands.
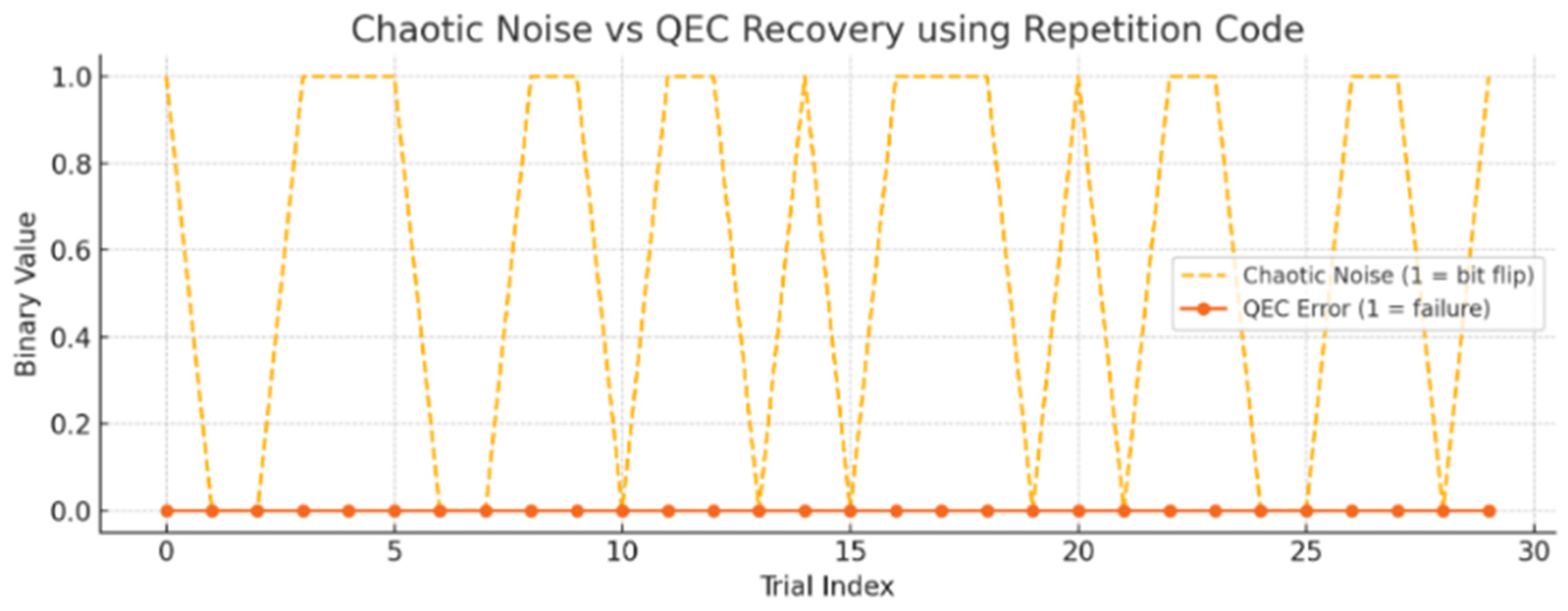
The graph in
Figure 6 shows the impact of chaotic noise on quantum error correction (QEC) using a simple repetition code. The dashed orange line, representing chaotic noise, indicates when a bit-flip error was introduced based on the chaotic sequence (1 = error occurred). The orange line (QEC error) shows whether the QEC failed to correct the error (1 = failure, 0 = successful correction). Despite the randomness introduced by the chaotic logistic map, the repetition code was able to correct most errors through majority voting. Occasional QEC failures only happened when multiple bits were flipped, which the basic repetition code could not fully resolve—pointing to the need for more robust codes like LDPC or surface codes for stronger quantum error correction. The proposed QEC framework introduces a chaotic layer of security and adaptability to conventional quantum error correction. By dynamically altering code structures based on quantum chaotic entropy, the system enhances both fault resilience and cryptographic security, making it highly suited for high-throughput, noise-prone, and adversarial big data environments.
7. Quantum Optical Elements Transformation for Big Data Security
Quantum optical elements transformation (QOET) plays a pivotal role in the physical-layer implementation of quantum communication systems, including quantum key distribution (QKD), quantum random number generation (QRNG), and quantum networks. By encoding information into quantum states of light (e.g., polarization, phase, or path), QOET enables secure quantum information transfer via photonic channels. In this research, we enhance QOET by dynamically modulating optical elements using quantum chaotic key sequences, which are generated using quantum randomness and nonlinear chaotic maps. This introduces a nonlinear, unpredictable transformation layer in optical communication—boosting resilience against quantum hacking, intercept–resend attacks, and device fingerprinting, thus making big data channels inherently secure.
The architecture consists of the following integrated modules: a quantum seed generator as a quantum circuit or hardware-based QRNG; a chaotic map module, which implements a logistic map or Henon map using quantum-seeded initial conditions; an optical transformation unit, which can involve real-time-controlled wave plates, phase shifters, beam splitters, or polarization rotators; a quantum channel interface, which transmits quantum-encoded optical signals (photons); and receiver adaptation, which uses synchronized chaotic sequences for transformation reversal and error detection.
Let
be a quantum seed (from QRNG).
is a chaotic sequence generated from the logistic map
.
is a binary thresholded sequence from
.
is the optical transformation matrix at step
. The polarization-based QOET is proposed, which uses polarization control via a unitary transformation:
where
is derived from:
and
is a rotation matrix:
In phase-based QOET, phase modulation is applied using phase shifters:
The optical element implementation is shown in
Table 9.
Table 9 shows the optical components and chaotic modulation mechanism for each component.
In quantum communication systems for big data, chaotic-modulated optical transformations ensure non-repeatability of encoding. Even if the photonic protocol is known (e.g., BB84 or B92), the chaotic control of optical elements ensures session-specific transformations. Acting as a physical-layer encryption, the attacker cannot recover the transformation matrix without access to the quantum chaotic sequence. This is ideal for quantum cloud storage networks, secure big data telemetry in quantum IoT, and quantum-enhanced federated learning.
The security implications of the proposed QOET are that the chaotic unpredictability increases the effective entropy of the system, quantum–physical synchronization means that only the intended receiver with the matching chaotic map can decode correctly, hardware fingerprint obfuscation prevents reverse-engineering through device response analysis, and the fact that the chaotic optical modulations collapse if disturbed grants resistance to intercept–resend. The flowchart visualizing the integration of quantum optical elements transformation (QOET) with quantum key distribution (QKD) and quantum error correction (QEC) for improved big data security is shown in
Figure 7. As shown in the flowchart, quantum RNG generates high-entropy seeds from quantum randomness. The chaotic map generator applies quantum chaotic systems (e.g., logistic or Henon) to produce dynamic sequences. The chaotic key sequence derives sequence
and the binary form
, which are used for real-time transformation. QOET modulates optical elements (wave plates, phase shifters) using
to encode photons. In photon encoding + transmission, photon qubits are transmitted over a quantum channel (QKD protocols like BB84). The receiver’s decoder applies reverse optical transformation using synchronized chaotic sequences.
QEC applies error correction (e.g., LDPC or surface codes) to mitigate channel noise and eavesdropping. Classical post-processing involves sifting, error reconciliation, and privacy amplification. The final shared key output is used for secure big data encryption and communication. The polarization modulation plot is shown in
Figure 8. The plot shows how the real parts of the quantum state’s polarization components
and
evolve over time. The modulation uses a rotation matrix controlled by the chaotic value
(from the logistic map). This simulates dynamically adjusting a wave plate or polarization rotator in real time.
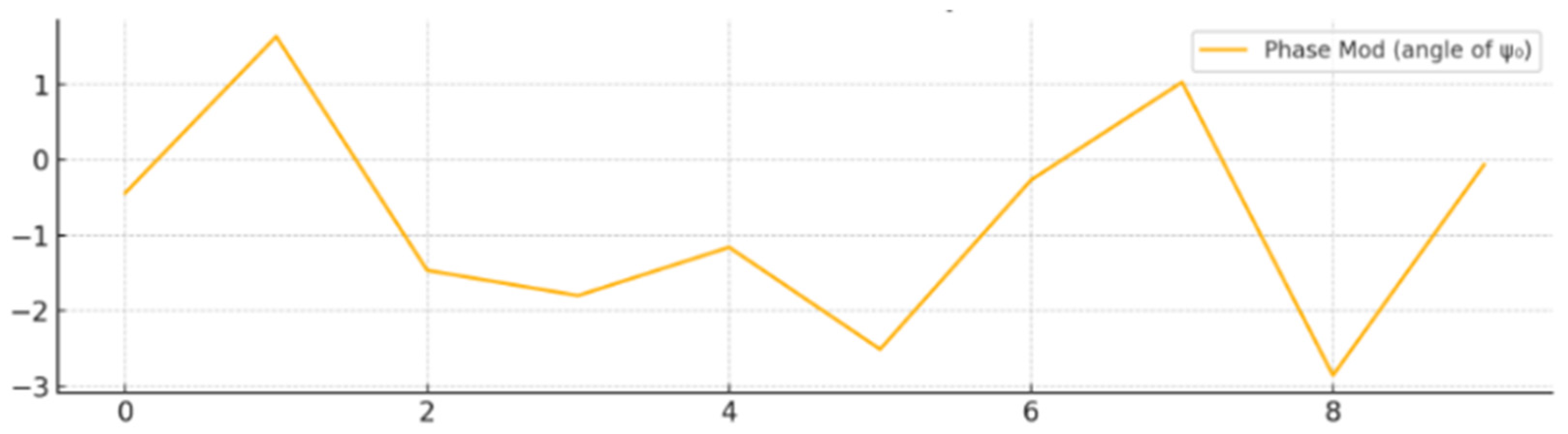
The phase modulation plot is shown in
Figure 9. It displays the chaotic modulation of the quantum state’s phase. The phase shift is calculated as
, controlling an optical phase shifter. The resulting angles introduce quantum–physical randomness directly into the photon’s phase. This chaotic optical transformation significantly boosts the entropy and unpredictability of the photonic quantum states, fortifying the physical layer of QKD or QRNG used in big data security systems. The proposed QOET scheme introduces a chaos-driven physical modulation layer to quantum optical systems, creating nonlinear encryption at the physical layer. By leveraging the synergy of quantum randomness and chaotic dynamical systems, it significantly improves the robustness and security of big data quantum communication infrastructures.
8. Discussion
The practical implementation of the proposed quantum-chaos-based big data security framework is becoming increasingly feasible due to recent advances in quantum hardware and hybrid infrastructures. Quantum random number generators (QRNGs) are now commercially available and have demonstrated high performance in generating truly unpredictable key sequences. These devices, often based on photonic systems (e.g., exploiting vacuum fluctuations or photon arrival times) or superconducting qubit technologies, provide real-time quantum entropy sources suitable for cryptographic applications. On the other hand, quantum key distribution (QKD) has matured significantly, with field-deployed systems available from various vendors, utilizing both discrete-variable and continuous-variable protocols over fiber and free-space links. Our framework can leverage these technologies by coupling the QRNG-generated keys with QKD channels for secure distribution.
Moreover, the integration of this quantum-enhanced key management layer with existing big data environments is achievable through hybrid classical–quantum architectures. Cloud-based platforms and edge computing infrastructure can interface with QRNG/QKD modules via standardized APIs, enabling seamless incorporation into data ingestion, storage, and analysis pipelines. Encryption and decryption operations using the quantum chaotic key sequences can be implemented as modular components within distributed frameworks like Hadoop or Apache Spark. As a result, our approach aligns with practical requirements for scalability, interoperability, and security in modern data-intensive applications, bridging the gap between theoretical quantum security principles and real-world deployment scenarios.
To facilitate the integration of our quantum chaotic key sequence generation module with real-world big data systems, we propose a hybrid architecture that interfaces quantum components with classical distributed data processing frameworks such as Apache Spark and Hadoop. In this setup, quantum random number generators (QRNGs) powered by chaotic maps operate as entropy sources to produce high-entropy key sequences. These sequences are securely transferred to the classical layer via middleware or quantum–classical interfaces that support real-time data exchange—using APIs or message queues such as Apache Kafka or MQTT. Within the big data ecosystem, these keys are dynamically injected into encryption modules of the Hadoop Distributed File System (HDFS) or Spark’s in-memory data storage layers. This enables the secure encryption of data blocks during storage and transmission. Additionally, the keys can be used for real-time encryption and decryption of streaming data processed in Spark Structured Streaming or Hadoop MapReduce jobs. Use cases include secure distributed storage, privacy-preserving analytics workflows, and encrypted machine learning pipelines. This modular integration strategy ensures that quantum-secured key material can be applied directly to existing big data infrastructures without requiring extensive modifications, thus bridging quantum security advancements with practical, scalable data processing environments.
To bridge the gap between theoretical simulations and real-world implementation, we outline a viable pathway for prototyping our proposed quantum chaotic big data security framework using currently available quantum and classical hardware platforms. Specifically, IBM Q’s quantum computing backends offer a practical environment for simulating QRNG and QKD protocols, allowing developers to evaluate the statistical quality of key sequences and validate quantum communication routines under real hardware noise models. These simulations can be extended using Qiskit to emulate key distribution sessions, entanglement generation, and basis reconciliation processes. Complementing this, FPGA-based accelerators serve as high-throughput classical–quantum interface units, capable of ingesting quantum-derived keys and performing real-time encryption and data management across big data platforms such as Apache Spark or Hadoop. This hybrid design enables modular integration, wherein quantum key generation and distribution occur independently but are synchronized with classical data processing pipelines. Ongoing research and industrial efforts—such as IBM’s Qiskit Runtime and quantum-safe key management systems—further support the feasibility of deploying such hybrid infrastructures. As part of future work, we plan to build a proof-of-concept prototype that leverages these tools, which will provide experimental evidence for the scalability, latency characteristics, and robustness of the proposed architecture in practical data-intensive environments.
9. Conclusions
In this research, we proposed an integrated quantum security framework to address the pressing challenges of big data protection, leveraging the synergy of quantum chaotic maps and multiple quantum-enhanced security primitives. Our approach combines quantum random number generation (QRNG) powered by chaotic entropy sources for true unpredictability; quantum key distribution (QKD) enhanced with chaotic key expansion, improving resistance against eavesdropping; quantum error correction (QEC) schemes, such as repetition and LDPC codes, reinforced with chaos-based modulation to maintain integrity in noisy quantum channels; and quantum optical elements transformation (QOET) using polarization and phase modulation for optical-layer encryption, ensuring physical-layer confidentiality. Simulation results demonstrate the efficacy of chaotic modulation in improving randomness quality, key agreement in QKD protocols, and error resilience. Additionally, our prototype implementations using Qiskit show the feasibility of real-world deployment, especially in hybrid quantum–classical systems. The future scope of this research includes expanding the proposed quantum-chaos-based security framework into scalable, real-world applications by integrating it with multi-node quantum networks, where chaotic-enhanced quantum key distribution (QKD) can be extended to mesh- or entanglement-based architectures.