From Mean Time to Failure to Mean Time to Attack/Compromise: Incorporating Reliability into Cybersecurity
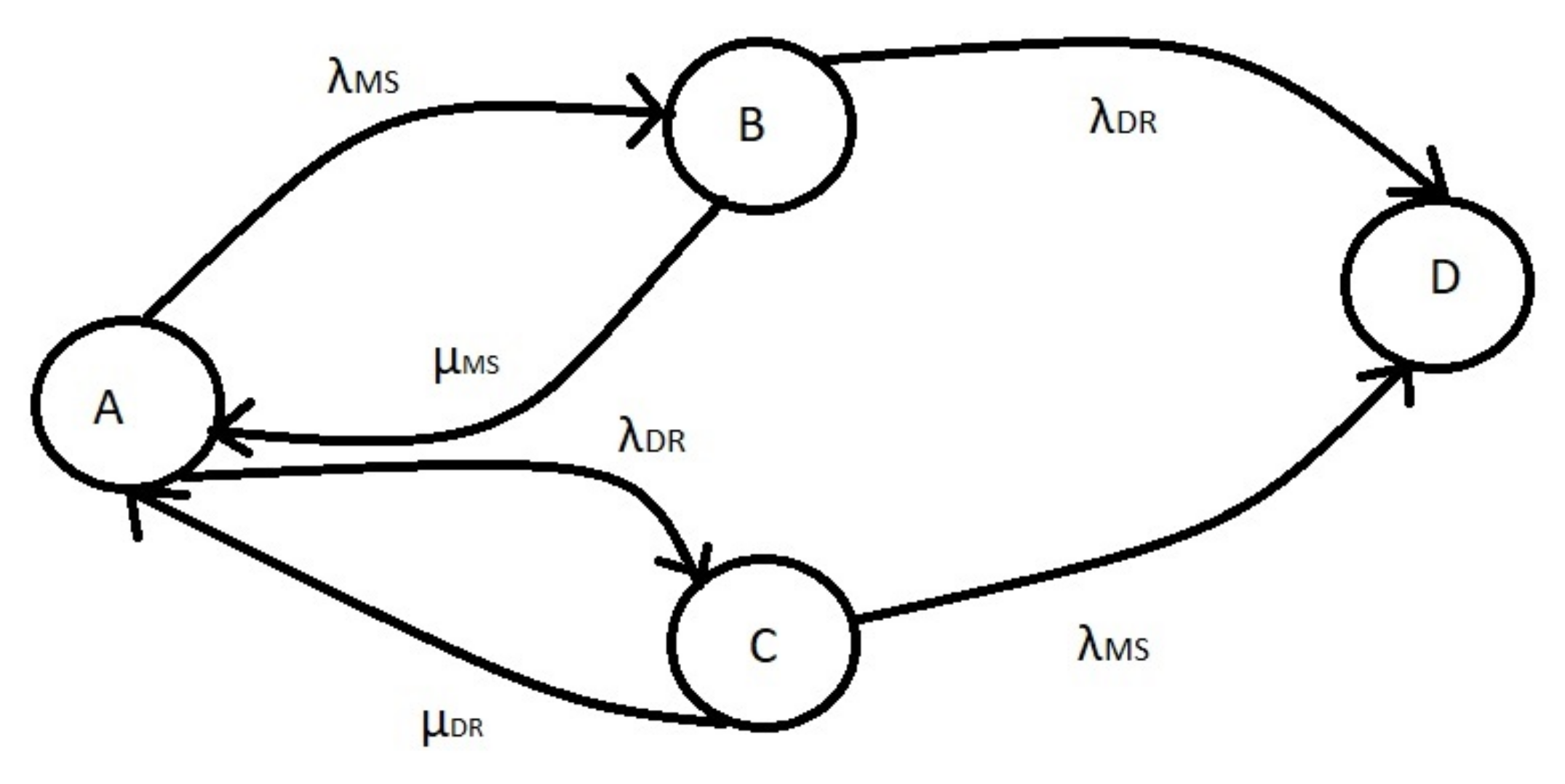
- State A is when both the system and the DR site are operating normally.
- State B is when the system is down due to a malfunction or attack.
- State C is when the DR site is off.
- State D is when both S and DR are off.
- λMS is the failure rate of the system, and
- λDR is the error rate of the Disaster Recovery Site.
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Shenglin, B.; Simonelli, F.; Ruidong, Z.; Bosc, R.; Wenwei, L. Digital infrastructure: Overcoming the digital divide in emerging economies. G20 Insights 2017, 3, 1–36. [Google Scholar]
- Corallo, A.; Lazoi, M.; Lezzi, M. Cybersecurity in the context of industry 4.0: A structured classification of critical assets and business impacts. Comput. Ind. 2020, 114, 103165. [Google Scholar] [CrossRef]
- Pranggono, B.; Arabo, A. COVID-19 pandemic cybersecurity issues. Internet Technol. Lett. 2021, 4, e247. [Google Scholar] [CrossRef]
- Norris, D.F.; Mateczun, L.; Joshi, A.; Finin, T. Cyberattacks at the grass roots: American local governments and the need for high levels of cybersecurity. Public Adm. Rev. 2019, 79, 895–904. [Google Scholar] [CrossRef]
- Sulistyowati, D.; Handayani, F.; Suryanto, Y. Comparative analysis and design of cybersecurity maturity assessment methodology using nist csf, cobit, iso/iec 27002 and pci dss. JOIV Int. J. Inform. Vis. 2020, 4, 225–230. [Google Scholar] [CrossRef]
- Chouliaras, N.; Kittes, G.; Kantzavelou, I.; Maglaras, L.; Pantziou, G.; Ferrag, M.A. Cyber ranges and testbeds for education, training, and research. Appl. Sci. 2021, 11, 1809. [Google Scholar] [CrossRef]
- Karagiannis, S.; Ntantogian, C.; Magkos, E.; Ribeiro, L.L.; Campos, L. PocketCTF: A fully featured approach for hosting portable attack and defense cybersecurity exercises. Information 2021, 12, 318. [Google Scholar] [CrossRef]
- Zwilling, M.; Klien, G.; Lesjak, D.; Wiechetek, Ł.; Cetin, F.; Basim, H.N. Cyber security awareness, knowledge and behavior: A comparative study. J. Comput. Inf. Syst. 2022, 62, 82–97. [Google Scholar]
- He, Y.; Camacho, R.S.; Soygazi, H.; Luo, C. Attacking and defence pathways for intelligent medical diagnosis system (IMDS). Int. J. Med. Inform. 2021, 148, 104415. [Google Scholar] [CrossRef]
- Kioskli, K.; Polemi, N. Estimating Attackers’ Profiles Results in More Realistic Vulnerability Severity Scores 2022. In Proceedings of the 13th International Conference on Applied Human Factors and Ergonomics (AHFE 2022), San Francisco, CA, USA, 20–24 July 2022. [Google Scholar]
- Boullauazan, Y.; Sys, C.; Vanelslander, T. Developing and demonstrating a maturity model for smart ports. Marit. Policy Manag. 2022, 1–19. [Google Scholar] [CrossRef]
- Papastergiou, S.; Polemi, D. Securing maritime logistics and supply chain: The medusa and mitigate approaches. Marit. Interdiction Oper. J. 2017, 14, 42–48. [Google Scholar]
- Aliyu, A.; Maglaras, L.; He, Y.; Yevseyeva, I.; Boiten, E.; Cook, A.; Janicke, H. A holistic cybersecurity maturity assessment framework for higher education institutions in the United Kingdom. Appl. Sci. 2020, 10, 3660. [Google Scholar] [CrossRef]
- Drivas, G.; Chatzopoulou, A.; Maglaras, L.; Lambrinoudakis, C.; Cook, A.; Janicke, H. A nis directive compliant cybersecurity maturity assessment framework. In Proceedings of the 2020 IEEE 44th Annual Computers, Software, and Applications Conference (COMPSAC), Madrid, Spain, 13–17 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1641–1646. [Google Scholar]
- Janicke, H.; Nicholson, A.; Webber, S.; Cau, A. Runtime-monitoring for industrial control systems. Electronics 2015, 4, 995–1017. [Google Scholar] [CrossRef] [Green Version]
- Kour, R.; Karim, R.; Thaduri, A. Cybersecurity for railways—A maturity model. Proc. Inst. Mech. Eng. Part F J. Rail Rapid Transit 2020, 234, 1129–1148. [Google Scholar] [CrossRef]
- Dube, D.P.; Mohanty, R. The application of cyber security capability maturity model to identify the impact of internal efficiency factors on the external effectiveness of cyber security. Int. J. Bus. Inf. Syst. 2021, 38, 367–392. [Google Scholar] [CrossRef]
- Rajawat, A.S.; Bedi, P.; Goyal, S.; Shaw, R.N.; Ghosh, A. Reliability Analysis in Cyber-Physical System Using Deep Learning for Smart Cities Industrial IoT Network Node. In AI and IoT for Smart City Applications; Springer: Berlin/Heidelberg, Germany, 2022; pp. 157–169. [Google Scholar]
- Buckley, I.A.; Fernandez, E.B.; Larrondo-Petrie, M.M. Patterns combining reliability and security. In Proceedings of the International Conferences on Pervasive Patterns and Applications, IARIA Conferences, XPS (Xpert Publishing Services), Rome, Italy, 25–30 September 2011; pp. 144–150. [Google Scholar]
- Maglaras, L.A.; Ferrag, M.A.; Janicke, H.; Ayres, N.; Tassiulas, L. Reliability, Security, and Privacy in Power Grids. Computer 2022, 55, 85–88. [Google Scholar] [CrossRef]
- Holgado, P.; Villagrá, V.A.; Vazquez, L. Real-time multistep attack prediction based on hidden markov models. IEEE Trans. Dependable Secur. Comput. 2017, 17, 134–147. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, L.; Xiang, Y.; Ten, C.W. Power system reliability evaluation with SCADA cybersecurity considerations. IEEE Trans. Smart Grid 2015, 6, 1707–1721. [Google Scholar] [CrossRef]
- Stamp, J.; McIntyre, A.; Ricardson, B. Reliability impacts from cyber attack on electric power systems. In Proceedings of the 2009 IEEE/PES Power Systems Conference and Exposition, Seattle, WA, USA, 15–18 March 2009; IEEE: Piscataway, NJ, USA, 2009; pp. 1–8. [Google Scholar]
- Leversage, D.J.; Byres, E.J. Estimating a system’s mean time-to-compromise. IEEE Secur. Priv. 2008, 6, 52–60. [Google Scholar] [CrossRef]
- Kharchenko, V.; Ponochovnyi, Y.; Ivanchenko, O.; Fesenko, H.; Illiashenko, O. Combining Markov and Semi-Markov Modelling for Assessing Availability and Cybersecurity of Cloud and IoT Systems. Cryptography 2022, 6, 44. [Google Scholar] [CrossRef]
- Ali, K.E.; Mazen, S.A.; Hassanein, E. A proposed hybrid model for adopting cloud computing in e-government. Future Comput. Inform. J. 2018, 3, 286–295. [Google Scholar] [CrossRef]
- Marotta, A. Cybersecurity Dynamics: Mapping Multiple Interdependencies 2021. Available online: ttps://pure.southwales.ac.uk/en/studentTheses/cybersecurity-dynamics-mapping-multiple-interdependencies (accessed on 10 October 2022).
- Endharta, A.J.; Yun, W.Y.; Ko, Y.M. Reliability evaluation of circular k-out-of-n: G balanced systems through minimal path sets. Reliab. Eng. Syst. Saf. 2018, 180, 226–236. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Maglaras, L. From Mean Time to Failure to Mean Time to Attack/Compromise: Incorporating Reliability into Cybersecurity. Computers 2022, 11, 159. https://doi.org/10.3390/computers11110159
Maglaras L. From Mean Time to Failure to Mean Time to Attack/Compromise: Incorporating Reliability into Cybersecurity. Computers. 2022; 11(11):159. https://doi.org/10.3390/computers11110159
Chicago/Turabian StyleMaglaras, Leandros. 2022. "From Mean Time to Failure to Mean Time to Attack/Compromise: Incorporating Reliability into Cybersecurity" Computers 11, no. 11: 159. https://doi.org/10.3390/computers11110159
APA StyleMaglaras, L. (2022). From Mean Time to Failure to Mean Time to Attack/Compromise: Incorporating Reliability into Cybersecurity. Computers, 11(11), 159. https://doi.org/10.3390/computers11110159




