Hardware Trojan Attacks on the Reconfigurable Interconnections of Field-Programmable Gate Array-Based Convolutional Neural Network Accelerators and a Physically Unclonable Function-Based Countermeasure Detection Technique
Abstract
1. Introduction
- (1)
- An attack method is designed to exploit a hardware Trojan on the reconfigurable interconnection network of an FPGA-based CNN accelerator. The objective of this attack is to manipulate the data path once the hardware Trojan is activated. Through this manipulation, the consequences become evident, as the PE array becomes incapable of performing the required calculations.
- (2)
- A detection technique based on physical unclonable functions (PUFs) is proposed as a countermeasure to protect the reconfigurable interconnection network of an FPGA-based CNN accelerator against hardware Trojan attacks. The designed PUF serves a dual purpose: it can detect the presence of hardware Trojans and identify their specific locations within the system.
- (3)
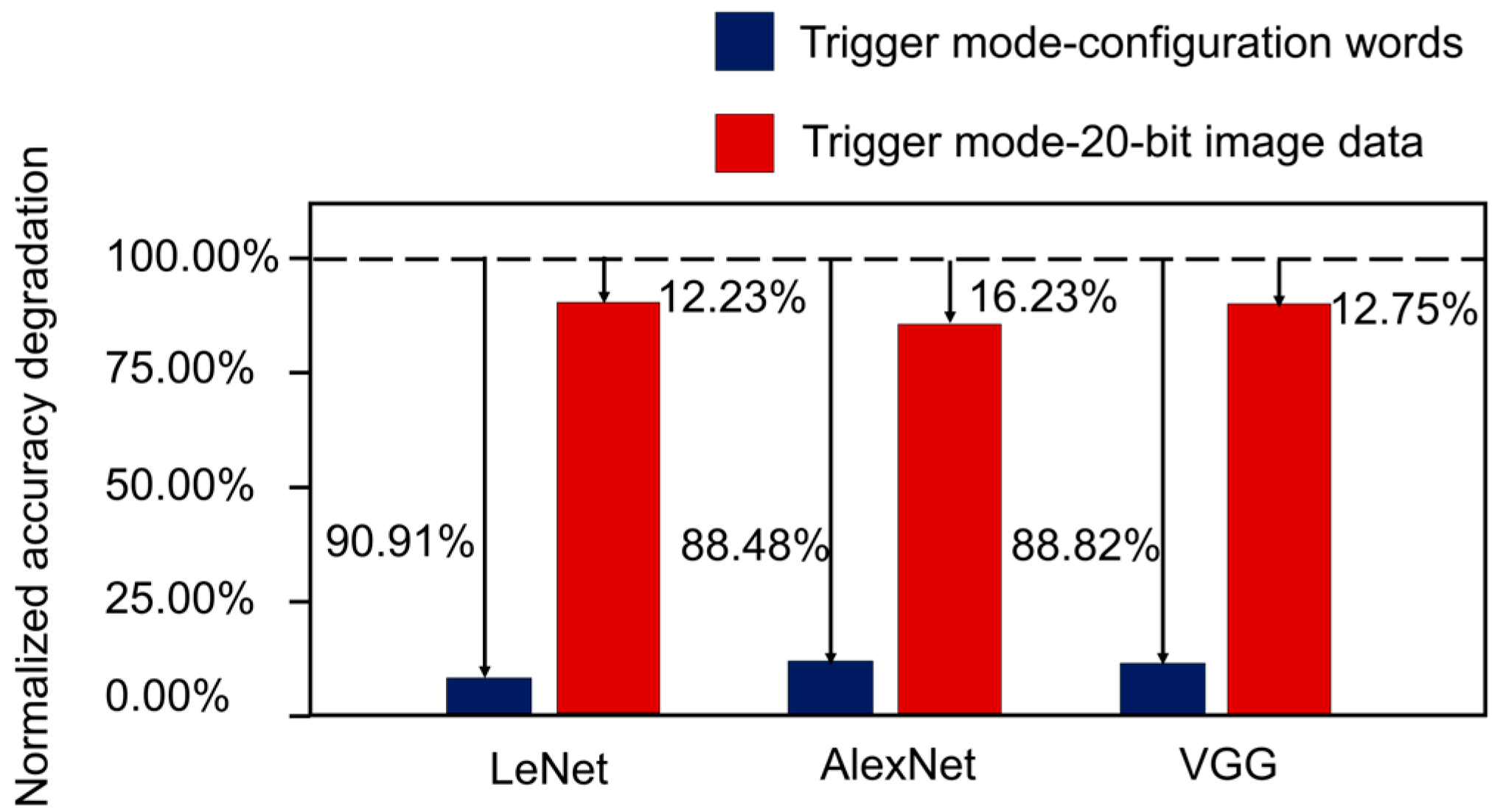
- The implemented hardware Trojan is embedded within the interconnection network of an in-house reconfigurable CNN accelerator. To evaluate its effectiveness, the Trojan attack was carried out on popular CNN architectures such as LeNet, AlexNet, and VGG. The experimental results reveal a significant degradation in accuracy for the CNN accelerator, ranging from 8.93% to 86.20% once the Trojan is activated. Furthermore, a detection technique based on an arbiter-based PUF is implemented on a Xilinx Zynq XC7Z100 platform. This PUF serves to detect hardware Trojans within the reconfigurable interconnection network. The effectiveness of the proposed detection technique is validated through these experimental implementations.
2. Related Work and Motivation
2.1. Related Work
2.2. Motivation
3. Methods
3.1. Hardware Trojan against Reconfigurable Interconnection Network
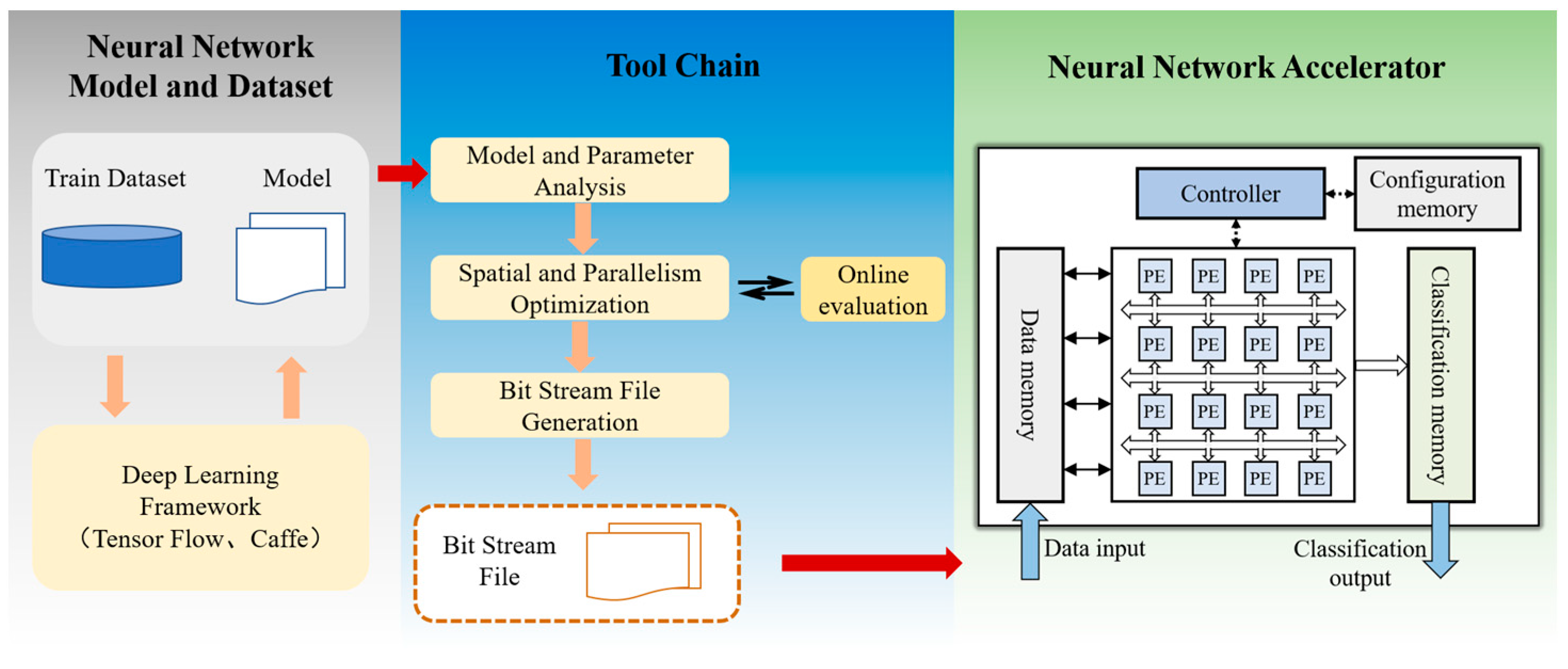
3.1.1. FPGA-Based CNN Accelerator and Reconfigurable Interconnection Network
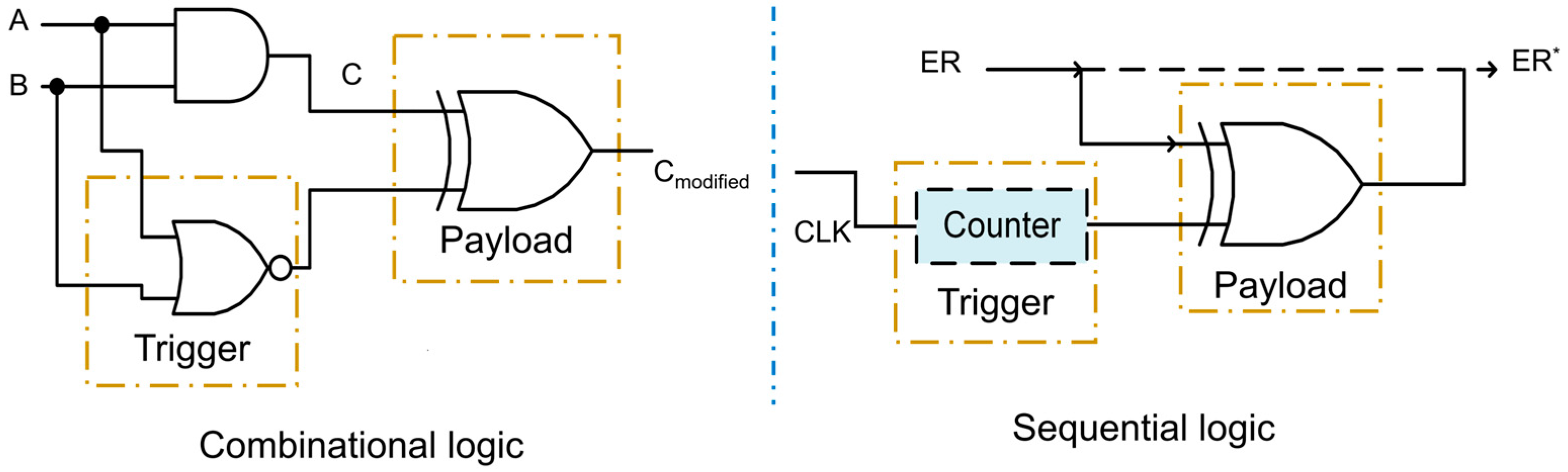
3.1.2. The Presence of Hardware Trojans in the Interconnection Network
3.1.3. Threat Model for Hardware Trojans against the Interconnection Network
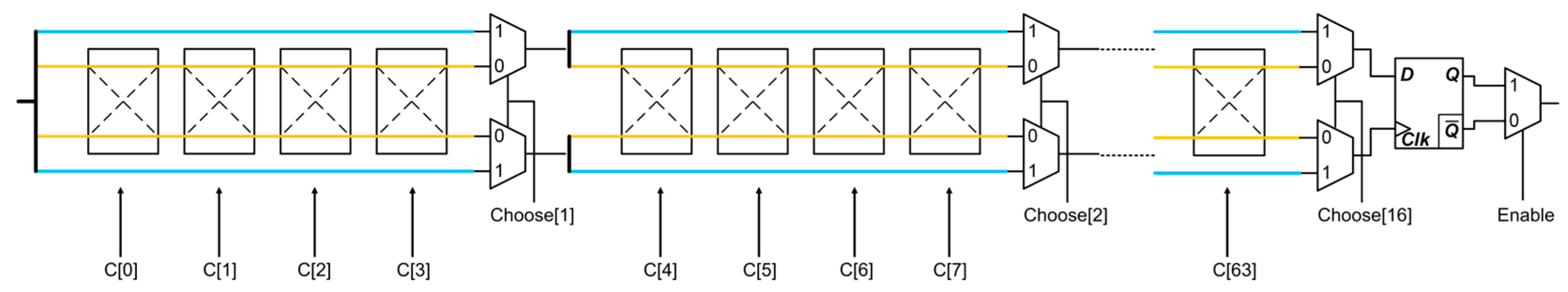
3.2. Corresponding Countermeasure of PUF-Based Detection Technique
3.2.1. Arbiter-Based PUF
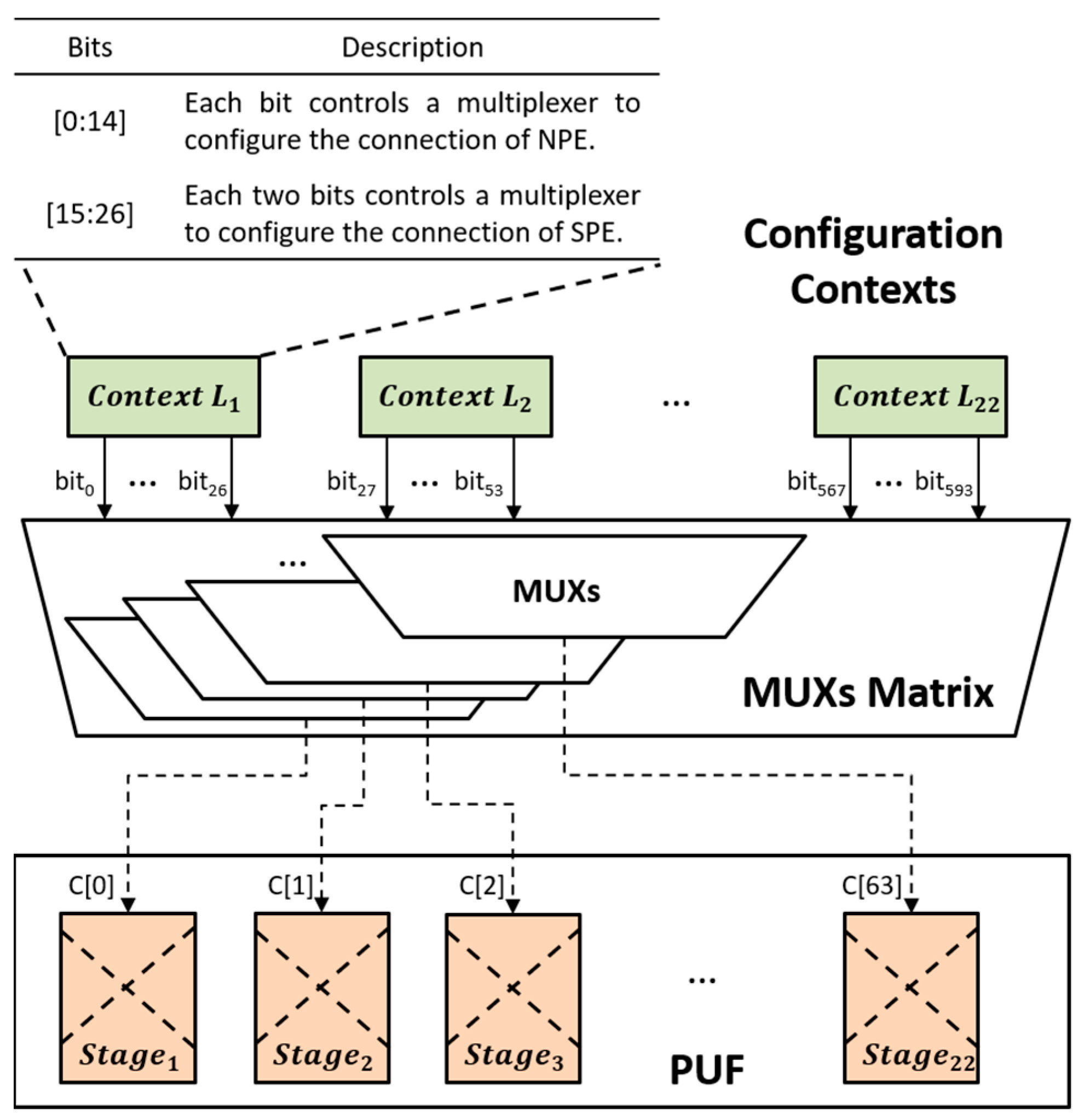
3.2.2. PUF-Based Countermeasure against Hardware Trojans Attack
4. Results
4.1. Experimental Setup
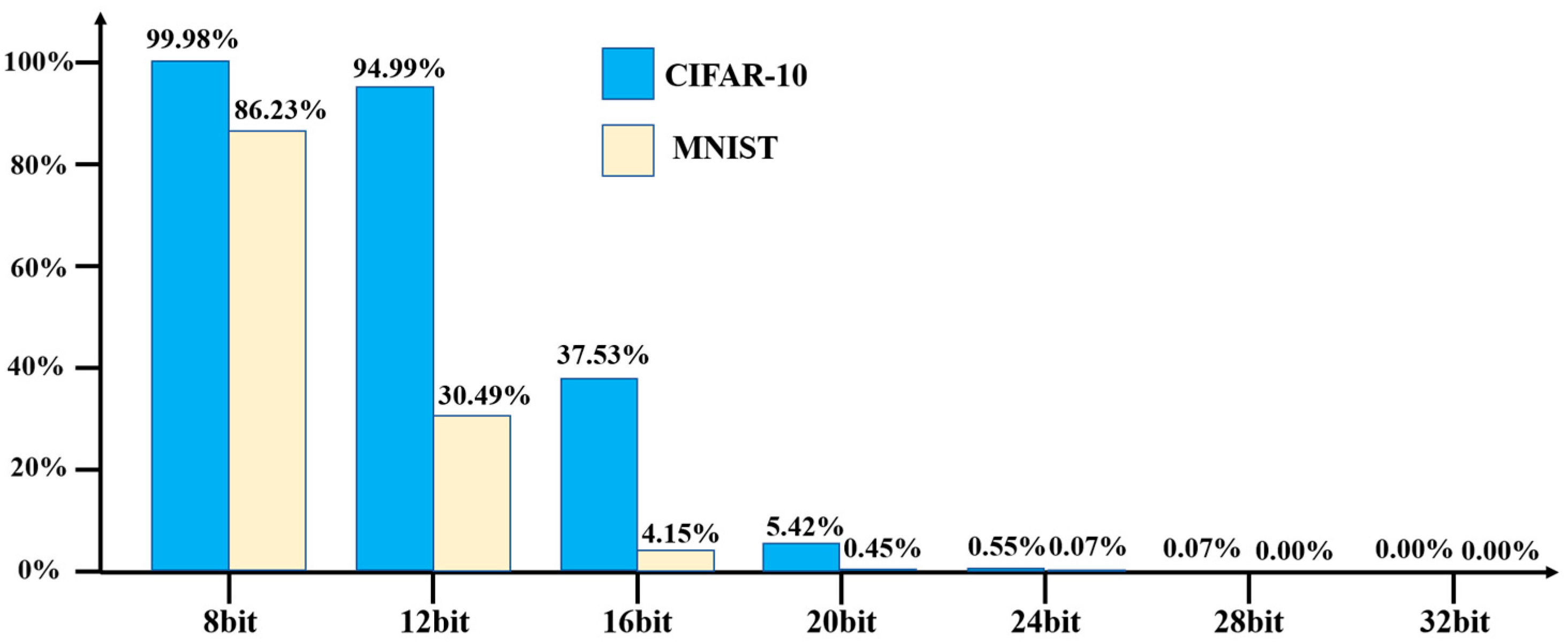
4.2. Hardware Trojan Attack Evaluation
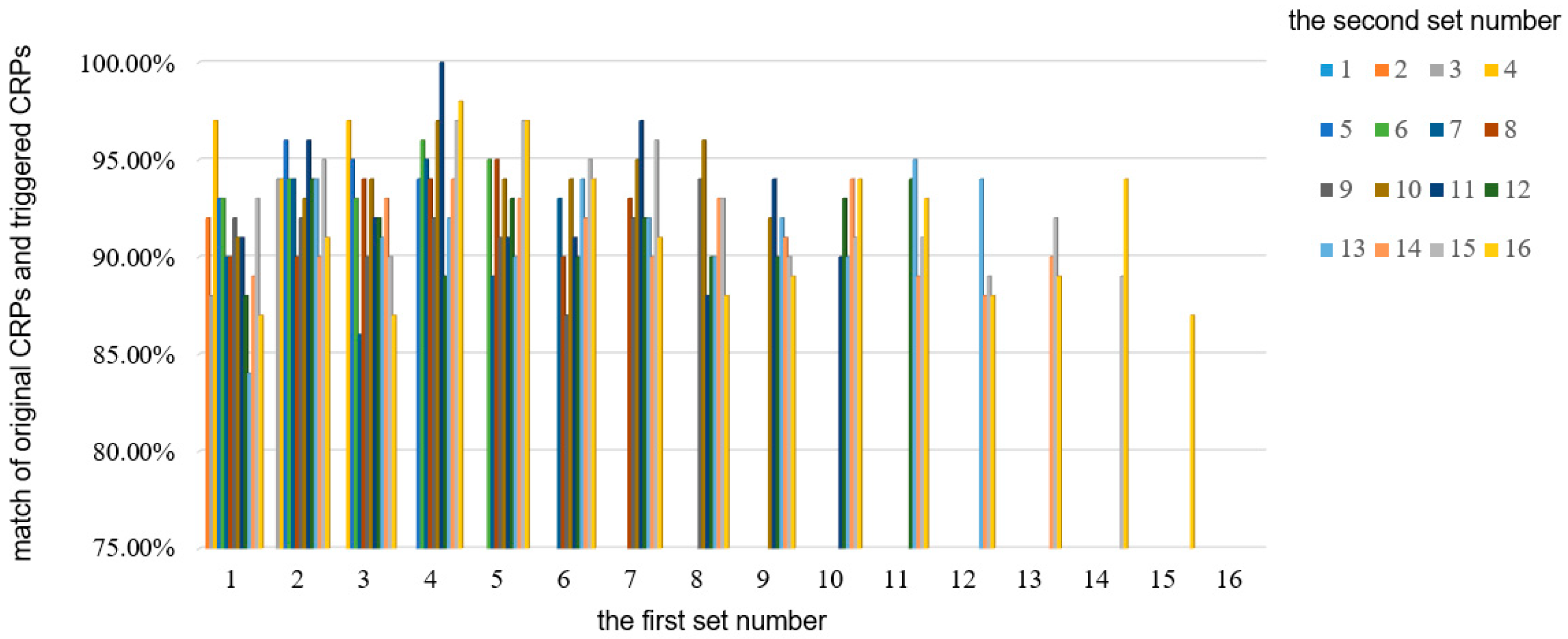
4.3. Detection Effectiveness
5. Discussion
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Okamoto, T.; Odagawa, M.; Koide, T.; Tanaka, S.; Tamaki, T.; Raytchev, B.; Kaneda, K.; Yoshida, S.; Mieno, H. Feature Extraction of Colorectal Endoscopic Images for Computer-Aided Diagnosis with CNN. In Proceedings of the 2019 2nd International Symposium on Devices, Circuits and Systems (ISDCS), Sapporo, Japan, 26–29 May 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Kido, S.; Hirano, Y.; Hashimoto, N. Detection and classification of lung abnormalities by use of convolutional neural network (CNN) and regions with CNN features (R-CNN). In Proceedings of the 2018 Interndational Workshop on Advanced Image Technology (IWAIT), Chiang Mai, Thailand, 7–9 January 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Eapen, J.; Bein, D.; Verma, A. Novel Deep Learning Model with CNN and Bi-Directional LSTM for Improved Stock Market Index Prediction. In Proceedings of the 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 7–9 January 2019; Institute of Electrical and Electronics Engineers (IEEE): New York, NY, USA, 2019; pp. 264–270. [Google Scholar] [CrossRef]
- Shin, H.-G.; Ra, I.; Choi, Y.-H. A Deep Multimodal Reinforcement Learning System Combined with CNN and LSTM for Stock Trading. In Proceedings of the 2019 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 16–18 October 2019; pp. 7–11. [Google Scholar] [CrossRef]
- He, R.; Wu, X.; Sun, Z.; Tan, T. Wasserstein CNN: Learning Invariant Features for NIR-VIS Face Recognition. IEEE Trans. Pattern Anal. Mach. Intell. 2018, 41, 1761–1773. [Google Scholar] [CrossRef]
- Qu, D.; Huang, Z.; Gao, Z.; Zhao, Y.; Zhao, X.; Song, G. An Automatic System for Smile Recognition Based on CNN and Face Detection. In Proceedings of the 2018 IEEE International Conference on Robotics and Biomimetics (ROBIO), Kuala Lumpur, Malaysia, 12–15 December 2018; pp. 243–247. [Google Scholar] [CrossRef]
- Girshick, R.; Donahue, J.; Darrell, T.; Malik, J. Rich Feature Hierarchies for Accurate Object Detection and Semantic Segmentation. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, Columbus, OH, USA, 23–28 June 2014; pp. 580–587. [Google Scholar] [CrossRef]
- Noh, H.; Hong, S.; Han, B. Learning deconvolution network for semantic segmentation. In Proceedings of the IEEE International Conference on Computer Vision, Santiago, Chile, 7–13 December 2015; pp. 1520–1528. [Google Scholar] [CrossRef]
- Liu, L.; Zhu, J.; Li, Z.; Lu, Y.; Deng, Y.; Han, J.; Yin, S.; Wei, S. A Survey of Coarse-Grained Reconfigurable Architecture and Design. ACM Comput. Surv. 2019, 52, 1–39. [Google Scholar] [CrossRef]
- Chen, Y.-H.; Krishna, T.; Emer, J.; Sze, V. 14.5 Eyeriss: An energy-efficient reconfigurable accelerator for deep convolutional neural networks. In Proceedings of the 2016 IEEE International Solid-State Circuits Conference (ISSCC), San Francisco, CA, USA, 31 January–4 February 2016; pp. 262–263. [Google Scholar] [CrossRef]
- Yin, S.; Ouyang, P.; Tang, S.; Tu, F.; Li, X.; Zheng, S.; Lu, T.; Gu, J.; Liu, L.; Wei, S. A High Energy Efficient Reconfigurable Hybrid Neural Network Processor for Deep Learning Applications. IEEE J. Solid-State Circuits 2017, 53, 968–982. [Google Scholar] [CrossRef]
- Yang, C.; Wang, Y.; Zhang, H.; Wang, X.; Geng, L. A Reconfigurable CNN Accelerator using Tile-by-Tile Computing and Dynamic Adaptive Data Truncation. In Proceedings of the 2019 IEEE International Conference on Integrated Circuits, Technologies and Applications (ICTA), Chengdu, China, 13–15 November 2019; pp. 73–74. [Google Scholar] [CrossRef]
- Yang, C.; Wang, Y.; Wang, X.; Geng, L. WRA: A 2.2-to-6.3 TOPS Highly Unified Dynamically Reconfigurable Accelerator Using a Novel Winograd Decomposition Algorithm for Convolutional Neural Networks. IEEE Trans. Circuits Syst. I Regul. Pap. 2019, 66, 3480–3493. [Google Scholar] [CrossRef]
- Fujii, T.; Toi, T.; Tanaka, T.; Togawa, K.; Kitaoka, T.; Nishino, K.; Nakamura, N.; Nakahara, H.; Motomura, M. New Generation Dynamically Reconfigurable Processor Technology for Accelerating Embedded AI Applications. In Proceedings of the 2018 IEEE Symposium on VLSI Circuits, Honolulu, HI, USA, 18–22 June 2018; pp. 41–42. [Google Scholar] [CrossRef]
- Liu, L.; Li, Z.; Yang, C.; Deng, C.; Yin, S.; Wei, S. HReA: An Energy-Efficient Embedded Dynamically Reconfigurable Fabric for 13-Dwarfs Processing. IEEE Trans. Circuits Syst. II Express Briefs 2017, 65, 381–385. [Google Scholar] [CrossRef]
- Guo, K.; Sui, L.; Qiu, J.; Yao, S.; Han, S.; Wang, Y.; Yang, H. From model to FPGA: Software-hardware co-design for efficient neural network acceleration. In Proceedings of the 2016 IEEE Hot Chips 28 Symposium (HCS), Cupertino, CA, USA, 21–23 August 2016; pp. 1–27. [Google Scholar] [CrossRef]
- Zhang, J.; Li, C. Adversarial Examples: Opportunities and Challenges. IEEE Trans. Neural Netw. Learn. Syst. 2019, 31, 2578–2593. [Google Scholar] [CrossRef] [PubMed]
- Alfeld, S.; Zhu, X.; Barford, P. Data poisoning attacks against autoregressive models. In Proceedings of the Association for the Advance of Artificial Intelligence (AAAI), Phoenix, AZ, USA, 12–17 February 2016; pp. 1452–1458. [Google Scholar]
- Liu, Y.; Wei, L.; Luo, B.; Xu, Q. Fault injection attack on deep neural network. In Proceedings of the 2017 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Irvine, CA, USA, 13–16 November 2017; pp. 131–138. [Google Scholar] [CrossRef]
- Hua, W.; Zhang, Z.; Suh, G.E. Reverse Engineering Convolutional Neural Networks Through Side-channel Information Leaks. In Proceedings of the 2018 55th ACM/ESDA/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 24–29 June 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Ye, J.; Hu, Y.; Li, X. Hardware Trojan in FPGA CNN Accelerator. In Proceedings of the 2018 IEEE 27th Asian Test Symposium (ATS), Hefei, China, 15–18 October 2018; pp. 68–73. [Google Scholar] [CrossRef]
- Clements, J.; Lao, Y. Hardware Trojan Design on Neural Networks. In Proceedings of the 2019 IEEE International Symposium on Circuits and Systems (ISCAS), Sapporo, Japan, 26–29 May 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Zhao, Y.; Hu, X.; Li, S.; Ye, J.; Deng, L.; Ji, Y.; Xu, J.; Wu, D.; Xie, Y. Memory Trojan Attack on Neural Network Accelerators. In Proceedings of the 2019 Design, Automation & Test in Europe Conference & Exhibition (DATE), Florence, Italy, 25–29 March 2019; pp. 1415–1420. [Google Scholar] [CrossRef]
- Hu, X.; Zhao, Y.; Deng, L.; Liang, L.; Zuo, P.; Ye, J.; Lin, Y.; Xie, Y. Practical Attacks on Deep Neural Networks by Memory Trojaning. IEEE Trans. Comput. Des. Integr. Circuits Syst. 2020, 40, 1230–1243. [Google Scholar] [CrossRef]
- Liu, Z.; Ye, J.; Hu, X.; Li, H.; Li, X.; Hu, Y. Sequence Triggered Hardware Trojan in Neural Network Accelerator. In Proceedings of the 2020 IEEE 38th VLSI Test Symposium (VTS), San Diego, CA, USA, 5–8 April 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Li, P.; Hou, R. Int-Monitor: A model triggered hardware trojan in deep learning accelerators. J. Supercomput. 2022, 79, 3095–3111. [Google Scholar] [CrossRef]
- Mukherjee, R.; Chakraborty, R.S. Novel Hardware Trojan Attack on Activation Parameters of FPGA-Based DNN Accelerators. IEEE Embed. Syst. Lett. 2022, 14, 131–134. [Google Scholar] [CrossRef]
- Zou, M.; Cui, X.; Shi, L.; Wu, K. Potential Trigger Detection for Hardware Trojans. IEEE Trans. Comput. Des. Integr. Circuits Syst. 2017, 37, 1384–1395. [Google Scholar] [CrossRef]
- Liu, L.; Zhou, Z.; Wei, S.; Zhu, M.; Yin, S.; Mao, S. DRMaSV: Enhanced Capability Against Hardware Trojans in Coarse Grained Reconfigurable Architectures. IEEE Trans. Comput. Des. Integr. Circuits Syst. 2017, 37, 782–795. [Google Scholar] [CrossRef]
- De, A.; Khan, M.N.I.; Nagarajan, K.; Ghosh, S. HarTBleed: Using Hardware Trojans for Data Leakage Exploits. IEEE Trans. Very Large Scale Integr. Syst. 2020, 28, 968–979. [Google Scholar] [CrossRef]
- Chen, X.; Liu, Q.; Yao, S.; Wang, J.; Xu, Q.; Wang, Y.; Liu, Y.; Yang, H. Hardware Trojan Detection in Third-Party Digital Intellectual Property Cores by Multilevel Feature Analysis. IEEE Trans. Comput. Des. Integr. Circuits Syst. 2017, 37, 1370–1383. [Google Scholar] [CrossRef]
- Mal-Sarkar, S.; Karam, R.; Narasimhan, S.; Ghosh, A.; Krishna, A.; Bhunia, S. Design and Validation for FPGA Trust under Hardware Trojan Attacks. IEEE Trans. Multi-Scale Comput. Syst. 2016, 2, 186–198. [Google Scholar] [CrossRef]
- Jyothi, V.; Thoonoli, M.; Stern, R.; Karri, R. FPGA Trust Zone: Incorporating trust and reliability into FPGA designs. In Proceedings of the 2016 IEEE 34th International Conference on Computer Design (ICCD), Phoenix, AZ, USA, 2–5 October 2016; pp. 600–605. [Google Scholar] [CrossRef]
- Pino, Y.; Jyothi, V.; French, M. Intra-die process variation aware anomaly detection in FPGAs. In Proceedings of the 2014 IEEE International Test Conference (ITC), Seattle, WA, USA, 20–23 October 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Krieg, C.; Wolf, C.; Jantsch, A. Malicious LUT: A stealthy FPGA Trojan injected and triggered by the design flow. In Proceedings of the 2016 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Austin, TX, USA, 7–10 November 2016; pp. 1–8. [Google Scholar] [CrossRef]
- Roy, J.A.; Koushanfar, F.; Markov, I.L. Extended abstract: Circuit CAD tools as a security threat. In Proceedings of the 2008 IEEE International Workshop on Hardware-Oriented Security and Trust (HOST), Anaheim, CA, USA, 9 June 2008; pp. 65–66. [Google Scholar] [CrossRef]
- Thompson, K. Reflections on trusting trust. Commun. ACM 1984, 27, 761–763. [Google Scholar] [CrossRef]
- Agrawal, D.; Baktir, S.; Karakoyunlu, D.; Rohatgi, P.; Sunar, B. Trojan Detection using IC Fingerprinting. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP ‘07), Berkeley, CA, USA, 20–23 May 2007; pp. 296–310. [Google Scholar] [CrossRef]
- Bhunia, S.; Hsiao, M.S.; Banga, M.; Narasimhan, S. Hardware Trojan Attacks: Threat Analysis and Countermeasures. Proc. IEEE 2014, 102, 1229–1247. [Google Scholar] [CrossRef]
- Xiao, K.; Forte, D.; Jin, Y.; Karri, R.; Bhunia, S.; Tehranipoor, M. Hardware Trojans: Lessons Learned after One Decade of Re-search. ACM Trans. Des. Autom. Electron. Syst. 2016, 22, 1–23. [Google Scholar] [CrossRef]
- Dunbar, C.; Qu, G. Designing Trusted Embedded Systems from Finite State Machines. ACM Trans. Embed. Comput. Syst. 2014, 13, 1–20. [Google Scholar] [CrossRef]
- Lin, L.; Burleson, W.; Paar, C. MOLES: Malicious off-chip leakage enabled by side-channels. In Proceedings of the IEEE/ACM International Conference on Computer-Aided Design, 2009 (ICCAD’09), San Jose, CA, USA, 2–5 November 2009; pp. 117–122. [Google Scholar]
- Cha, B.; Gupta, S.K. A Resizing Method to Minimize Effects of Hardware Trojans. In Proceedings of the 2014 IEEE 23rd Asian Test Symposium (ATS), Hangzhou, China, 16–19 November 2014; pp. 192–199. [Google Scholar] [CrossRef]
- Tsoutsos, N.G.; Maniatakos, M. Fabrication Attacks: Zero-Overhead Malicious Modifications Enabling Modern Microprocessor Privilege Escalation. IEEE Trans. Emerg. Top. Comput. 2013, 2, 81–93. [Google Scholar] [CrossRef]
- Chakraborty, R.S.; Saha, I.; Palchaudhuri, A.; Naik, G.K. Hardware Trojan Insertion by Direct Modification of FPGA Configuration Bitstream. IEEE Des. Test 2013, 30, 45–54. [Google Scholar] [CrossRef]
- Narasimhan, S.; Du, D.; Chakraborty, R.S.; Paul, S.; Wolff, F.G.; Papachristou, C.A.; Roy, K.; Bhunia, S. Hardware Trojan Detection by Multiple-Parameter Side-Channel Analysis. IEEE Trans. Comput. 2012, 62, 2183–2195. [Google Scholar] [CrossRef]
- Bhunia, S.; Abramovici, M.; Agrawal, D.; Bradley, P.; Hsiao, M.S.; Plusquellic, J.; Tehranipoor, M. Protection Against Hardware Trojan Attacks: Towards a Comprehensive Solution. IEEE Des. Test 2013, 30, 6–17. [Google Scholar] [CrossRef]
- Kulkarni, A.; Pino, Y.; Mohsenin, T. Adaptive real-time Trojan detection framework through machine learning. In Proceedings of the 2016 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, VA, USA, 3–5 May 2016; pp. 120–123. [Google Scholar] [CrossRef]
- Elnaggar, R.; Chakrabarty, K.; Tahoori, M.B. Hardware Trojan Detection Using Changepoint-Based Anomaly Detection Techniques. IEEE Trans. VLSI 2019, 27, 2706–2719. [Google Scholar] [CrossRef]
- Nguyen, L.N.; Cheng, C.-L.; Prvulovic, M.; Zajic, A. Creating a Backscattering Side Channel to Enable Detection of Dormant Hardware Trojans. IEEE Trans. Very Large Scale Integr. Syst. 2019, 27, 1561–1574. [Google Scholar] [CrossRef]
- Pappu, R.; Recht, B.; Taylor, J.; Gershenfeld, N. Physical One-Way Functions. Science 2002, 297, 2026–2030. [Google Scholar] [CrossRef] [PubMed]
- Yang, C.; Hou, J.; Wu, M.; Mei, K.; Geng, L. Hardware Trojan Attacks on the Reconfigurable Interconnections of Convolutional Neural Networks Accelerators. In Proceedings of the 2020 IEEE 15th International Conference on Solid-State & Integrated Circuit Technology (ICSICT), Kunming, China, 3–6 November 2020; pp. 1–3. [Google Scholar] [CrossRef]
- Yang, C.; Hou, J.; Wang, Y.; Zhang, H.; Wang, X.; Geng, L. RNA: A Flexible and Efficient Accelerator Based on Dynamically Reconfigurable Computing for Multiple Convolutional Neural Networks. J. Circuits Syst. Comput. 2022, 31, 1–32. [Google Scholar] [CrossRef]
- Lim, D.; Lee, J.; Gassend, B.; Suh, G.; van Dijk, M.; Devadas, S. Extracting secret keys from integrated circuits. IEEE Trans. Very Large Scale Integr. Syst. 2005, 13, 1200–1205. [Google Scholar] [CrossRef]

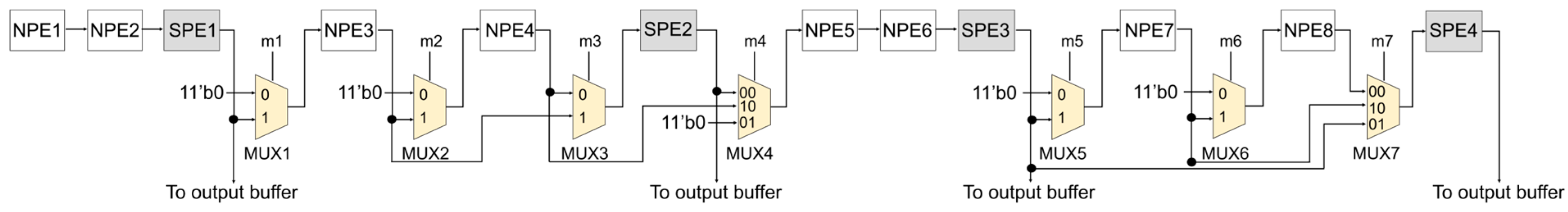




| Kernel Size | MUX1 | MUX2 | MUX3 | MUX4 | MUX5 | MUX6 | MUX7 |
|---|---|---|---|---|---|---|---|
| 3 × 3 | 0 | 1 | 0 | 01 | 0 | 1 | 00 |
| 5 × 5 | 1 | 0 | 1 | 01 | 0 | 1 | 10 |
| 11 × 11 | 1 | 1 | 0 | 00 | 1 | 0 | 01 |
| Kernel Size | m1 | m2 | m3 | m5 | m6 |
|---|---|---|---|---|---|
| 3 × 3 | S’2 = S2 + S1 | S’2 = S2 − N3 | S’2 = S2 − N3 − N4 | S’4 = S4 + S3 | S’4 = S4 − N7 |
| 5 × 5 | S’1 = S1 − N1 − N2 − SP1 | S’1 = S1 | S’1 = S1 − N1 − N2 − SP1 − N3 | S’2 = S2 − N5 − N6 − SP3 | S’2 = S2 |
| 11 × 11 | S’1 = S1 − N1 − N2 − SP1 | S’1 = S1 − N1 − N2 − SP1 − N3 | S’1 = S1 − N1 − N2 − SP1 − N3 − N4 | S’1 = S1 − N1 − N2 − SP1 − N3 − N4 − SP2 − N5 − N6 − SP3 | S’1 = S1 |
| The State of Choose Signal | Comparison of CRPs |
|---|---|
| choose[1] = 1, choose[2] = 1 | = |
| choose[1] = 1, choose[2] = 0 | ≠ |
| choose[1] = 0, choose[2] = 1 | ≠ |
| choose[1] = 0, choose[2] = 0 | ≠ |
| CNN Model | Accuracy | ||
|---|---|---|---|
| Normal Mode | Triggered Mode | ||
| Configuration Words | 20-Bit Image Data | ||
| LeNet | 98.21% | 8.93% | 86.20% |
| AlexNet | 86.82% | 10.00% | 72.73% |
| VGG | 90.26% | 10.00% | 78.75% |
| Original Accelerator | Malicious Accelerator | Comparison | |
|---|---|---|---|
| Overhead (LUT) | 84.350 K | 84.578 K | 0.27% ↑ * |
| Skipping Set Number | Match | Skipping Set Number | Match |
|---|---|---|---|
| 1 | 100% | 9 | 98% |
| 2 | 97% | 10 | 96% |
| 3 | 98% | 11 | 95% |
| 4 | 95% | 12 | 97% |
| 5 | 95% | 13 | 95% |
| 6 | 98% | 14 | 96% |
| 7 | 91% | 15 | 93% |
| 8 | 97% | 16 | 91% |
| The Accelerator without PUF | The Accelerator with PUF | Comparison | |
|---|---|---|---|
| Overhead (LUT) | 84.350 K | 84.834 K | 0.57% ↑ * |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hou, J.; Liu, Z.; Yang, Z.; Yang, C. Hardware Trojan Attacks on the Reconfigurable Interconnections of Field-Programmable Gate Array-Based Convolutional Neural Network Accelerators and a Physically Unclonable Function-Based Countermeasure Detection Technique. Micromachines 2024, 15, 149. https://doi.org/10.3390/mi15010149
Hou J, Liu Z, Yang Z, Yang C. Hardware Trojan Attacks on the Reconfigurable Interconnections of Field-Programmable Gate Array-Based Convolutional Neural Network Accelerators and a Physically Unclonable Function-Based Countermeasure Detection Technique. Micromachines. 2024; 15(1):149. https://doi.org/10.3390/mi15010149
Chicago/Turabian StyleHou, Jia, Zichu Liu, Zepeng Yang, and Chen Yang. 2024. "Hardware Trojan Attacks on the Reconfigurable Interconnections of Field-Programmable Gate Array-Based Convolutional Neural Network Accelerators and a Physically Unclonable Function-Based Countermeasure Detection Technique" Micromachines 15, no. 1: 149. https://doi.org/10.3390/mi15010149
APA StyleHou, J., Liu, Z., Yang, Z., & Yang, C. (2024). Hardware Trojan Attacks on the Reconfigurable Interconnections of Field-Programmable Gate Array-Based Convolutional Neural Network Accelerators and a Physically Unclonable Function-Based Countermeasure Detection Technique. Micromachines, 15(1), 149. https://doi.org/10.3390/mi15010149







