Overview of Radar Jamming Waveform Design
Abstract
1. Introduction
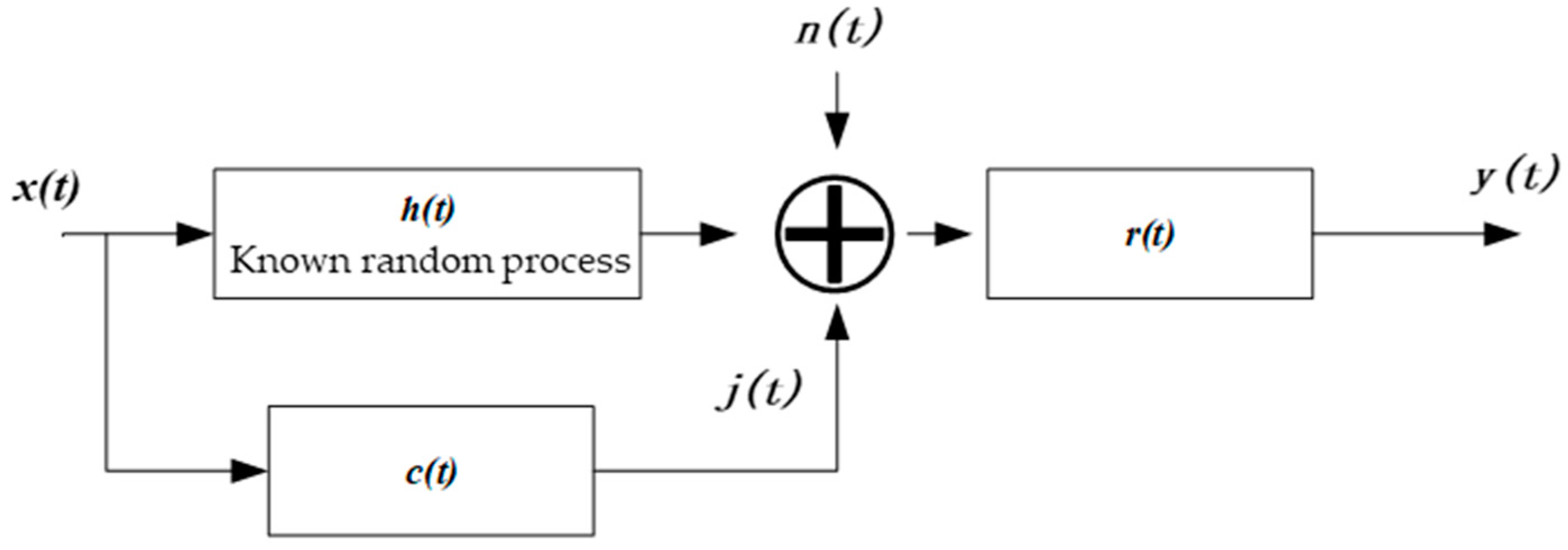
2. General Formula for Jamming
3. Classification Based on Jamming Effects
3.1. Barrage Jamming
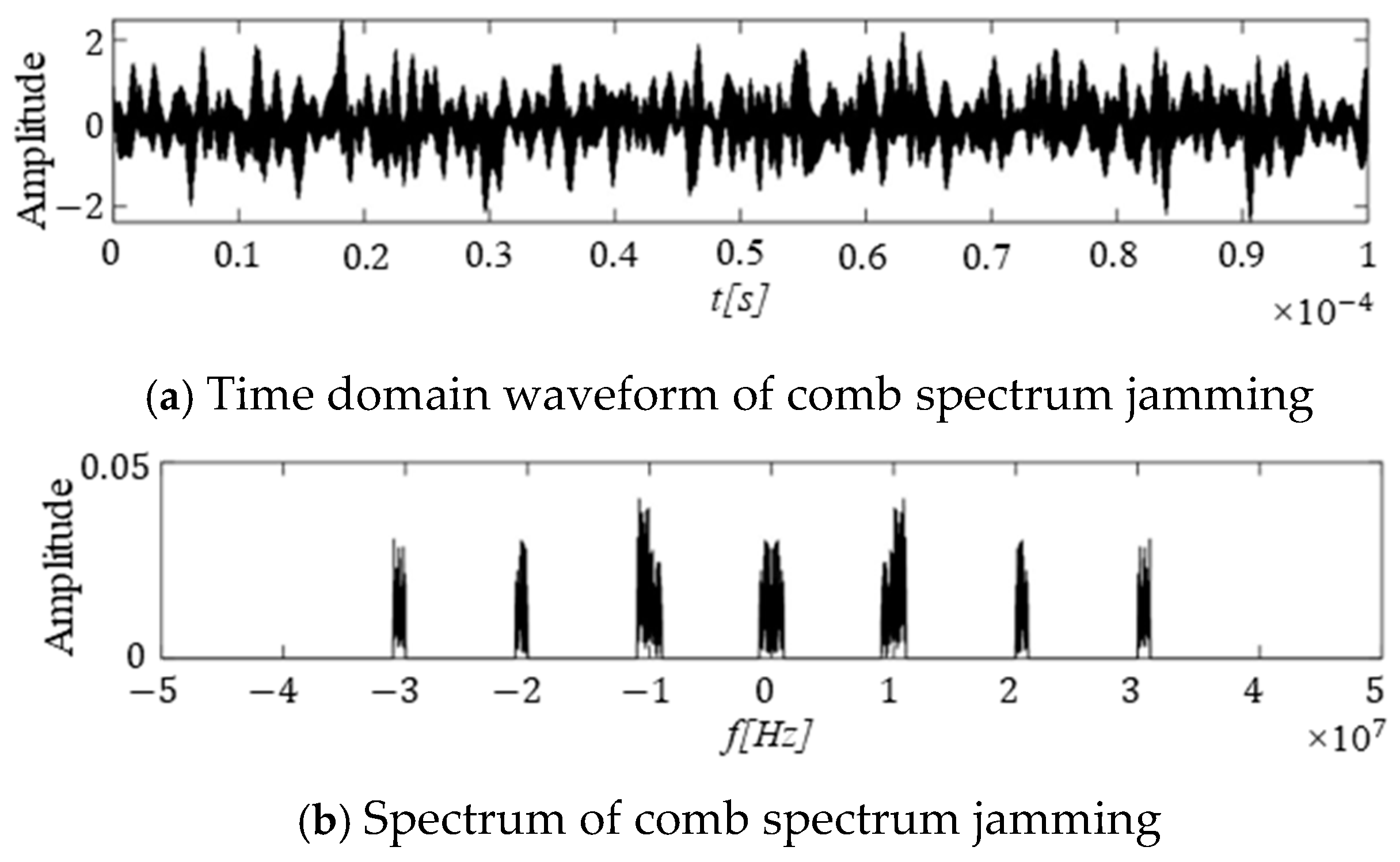
3.1.1. Single-Band Jamming
3.1.2. Multi-Band Jamming
3.2. Deceptive Jamming
3.2.1. Full-Pulse Repetition Jamming
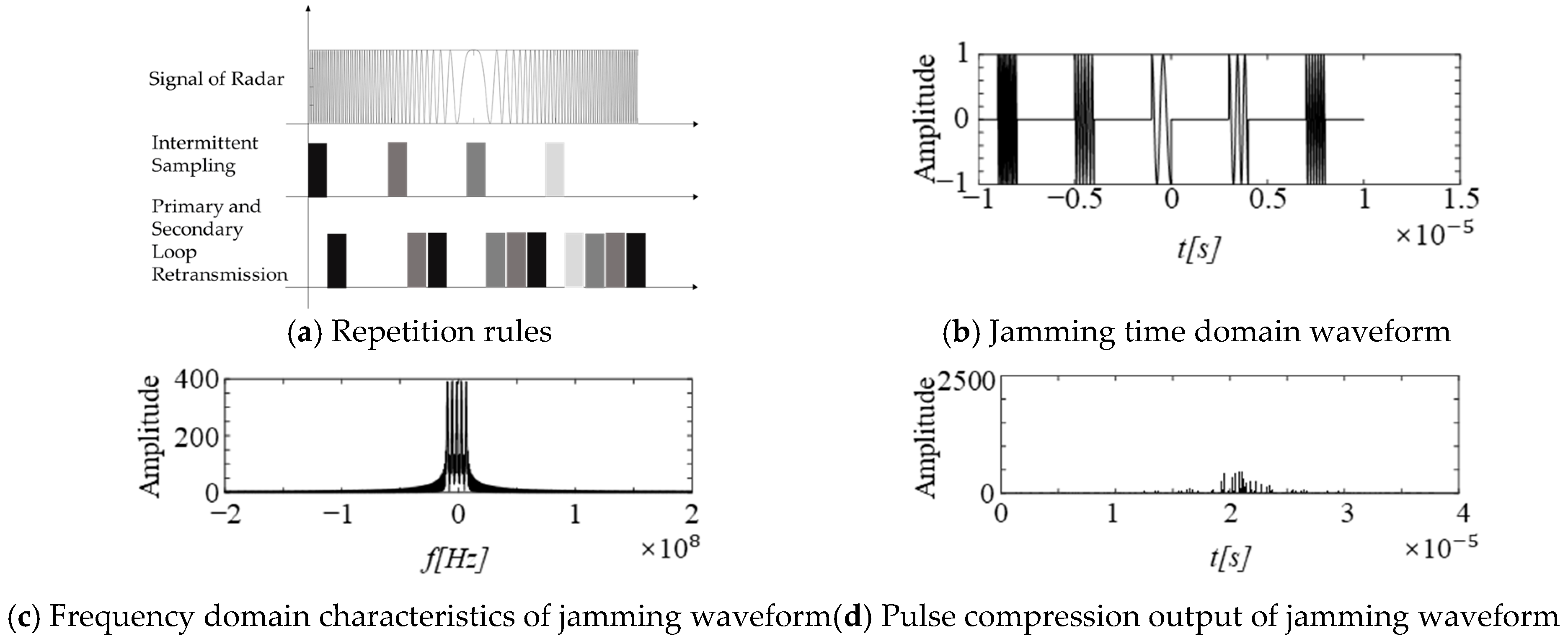
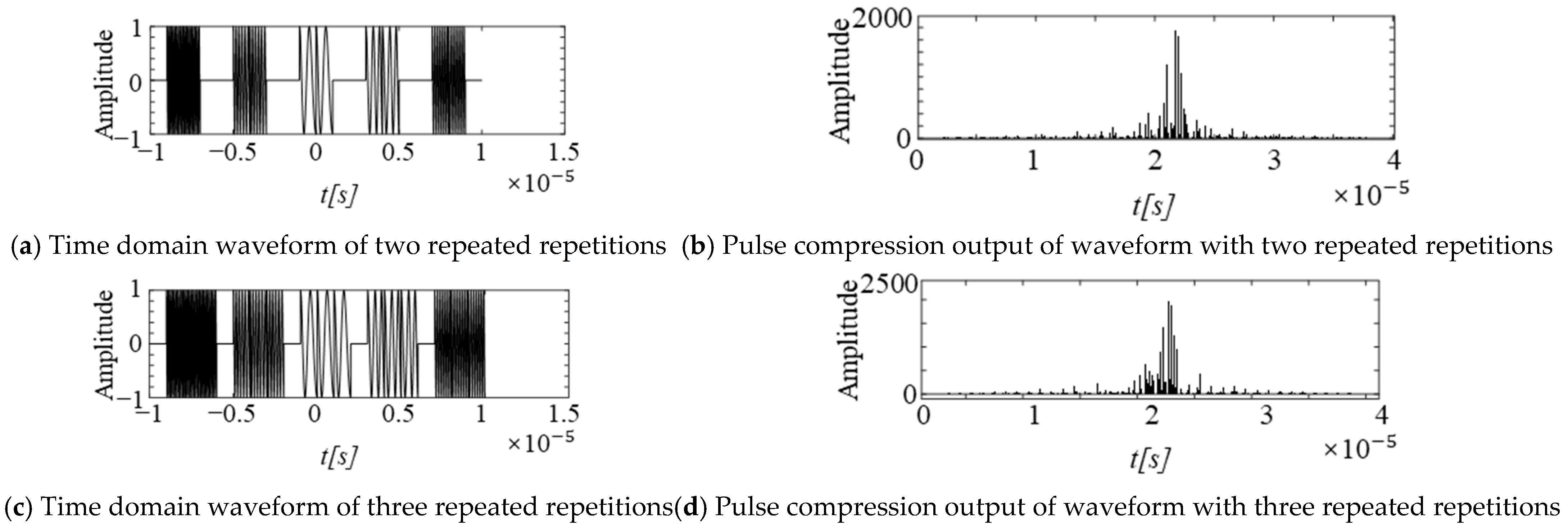
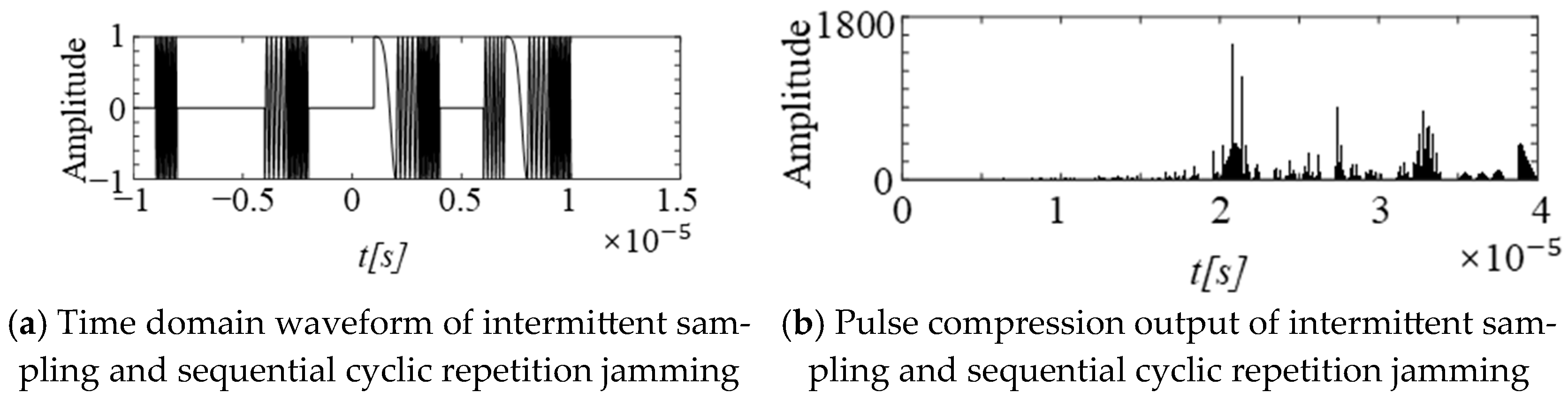
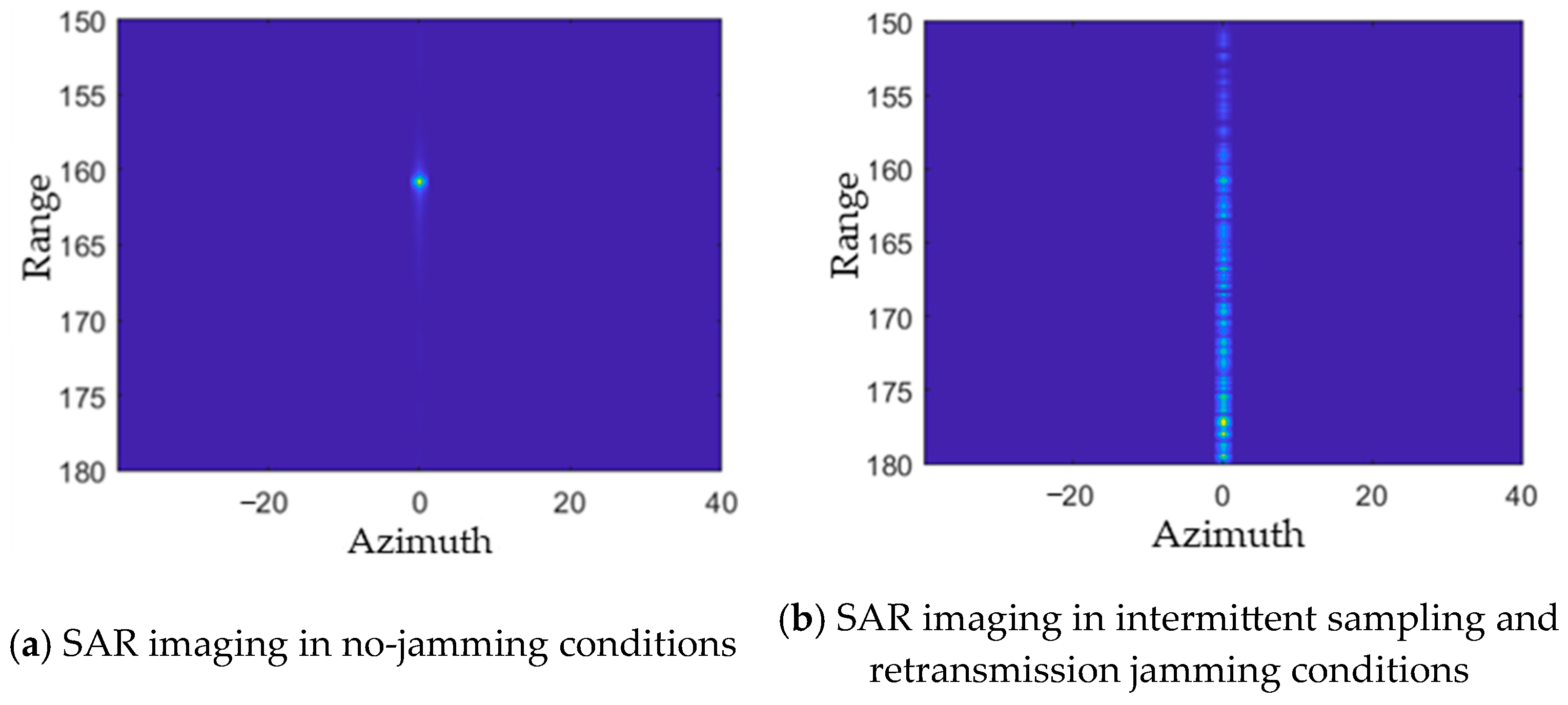
3.2.2. Intermittent Sampling and Repetition Jamming
3.3. Smart Noise Jamming
3.3.1. Jamming by Modulating Complete Pulses
3.3.2. Jamming by Modulating Pulse Segments
3.4. Comparative Analysis
4. Classification Based on Jamming Targets
4.1. Jamming Against Pulse Compression Radars
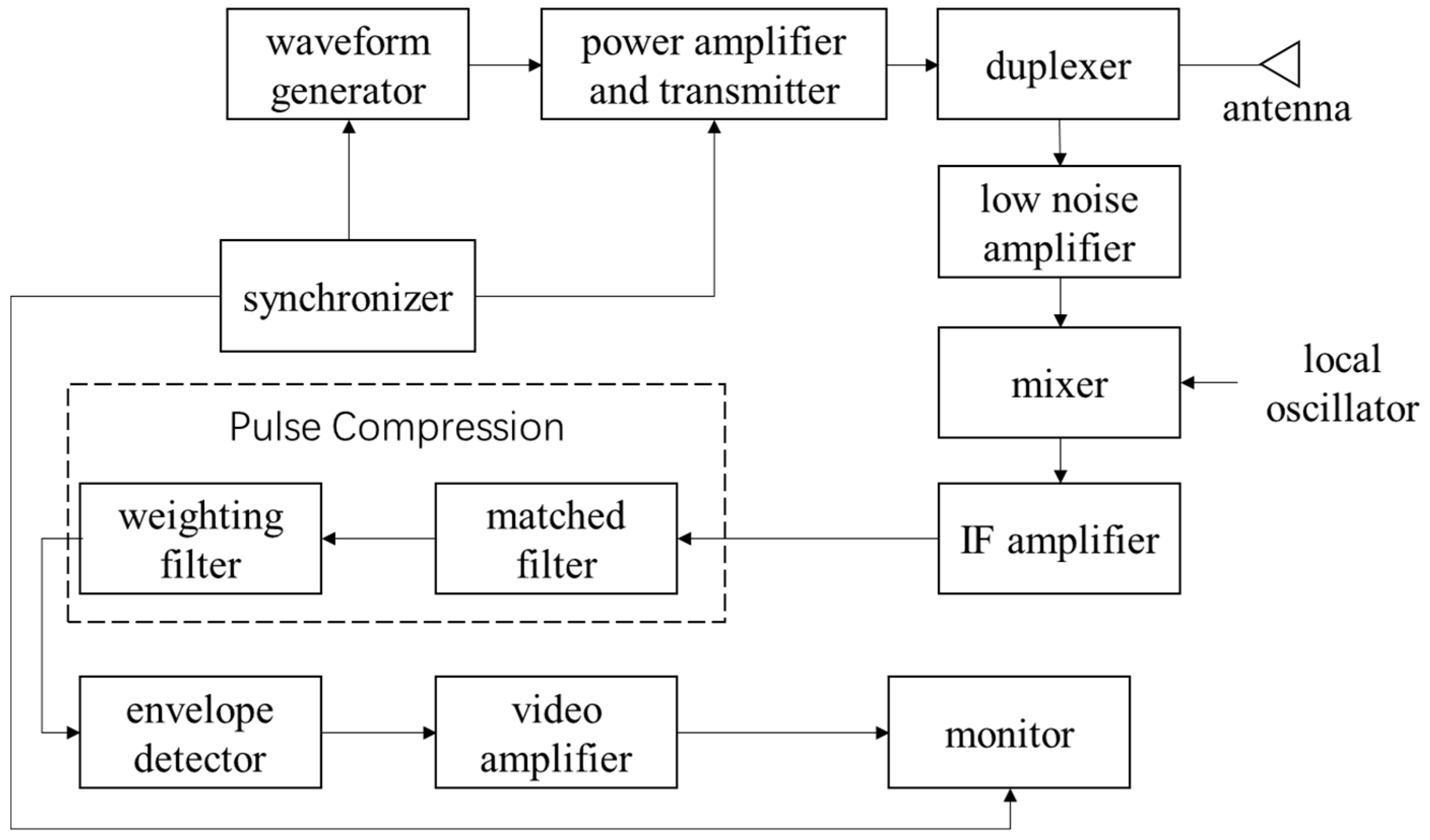
4.1.1. Principle of Pulse Compression Radars
4.1.2. Jamming
4.2. Jamming Against PD Radars
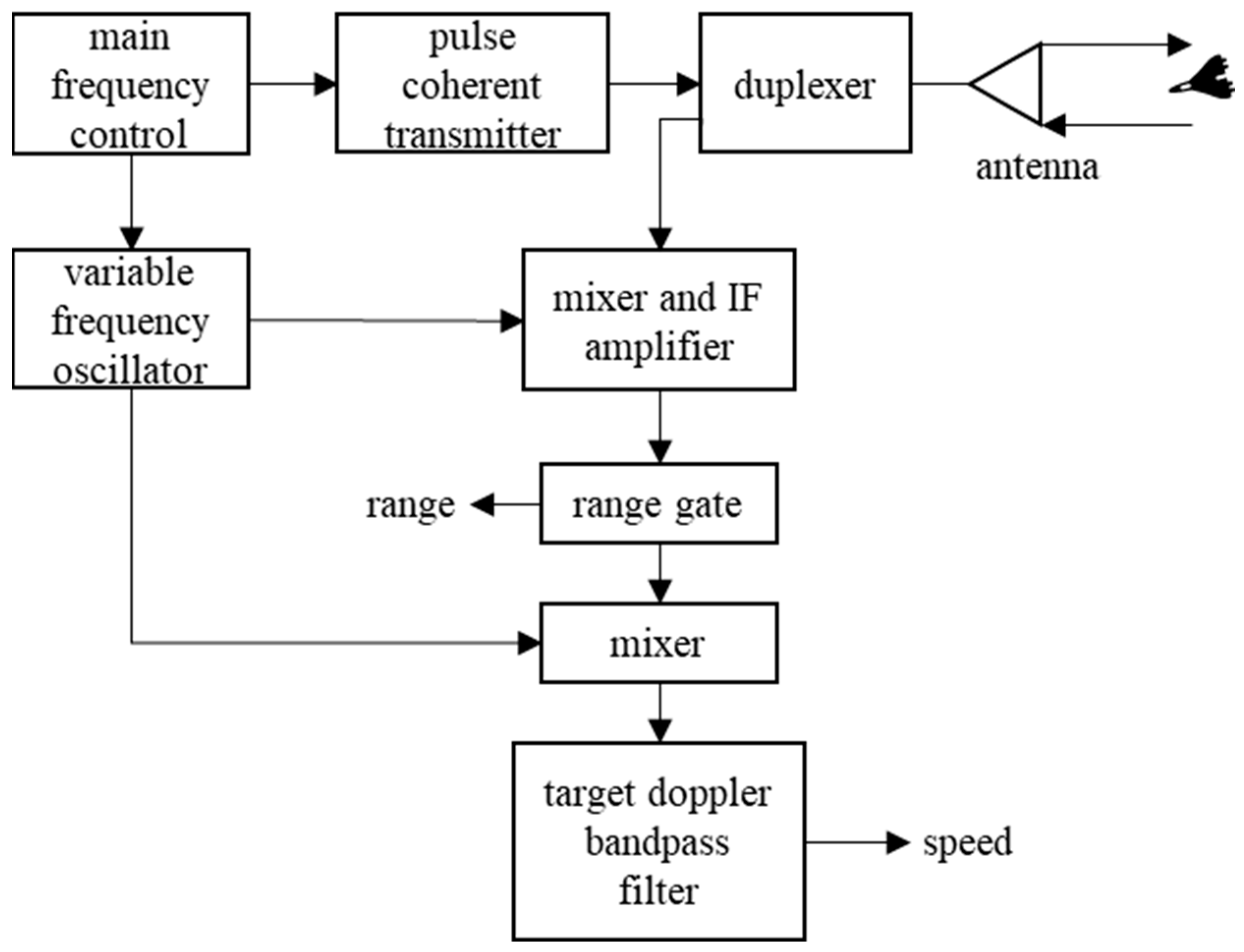
4.2.1. Principle of PD Radars
4.2.2. Jamming
4.3. Jamming Against SAR
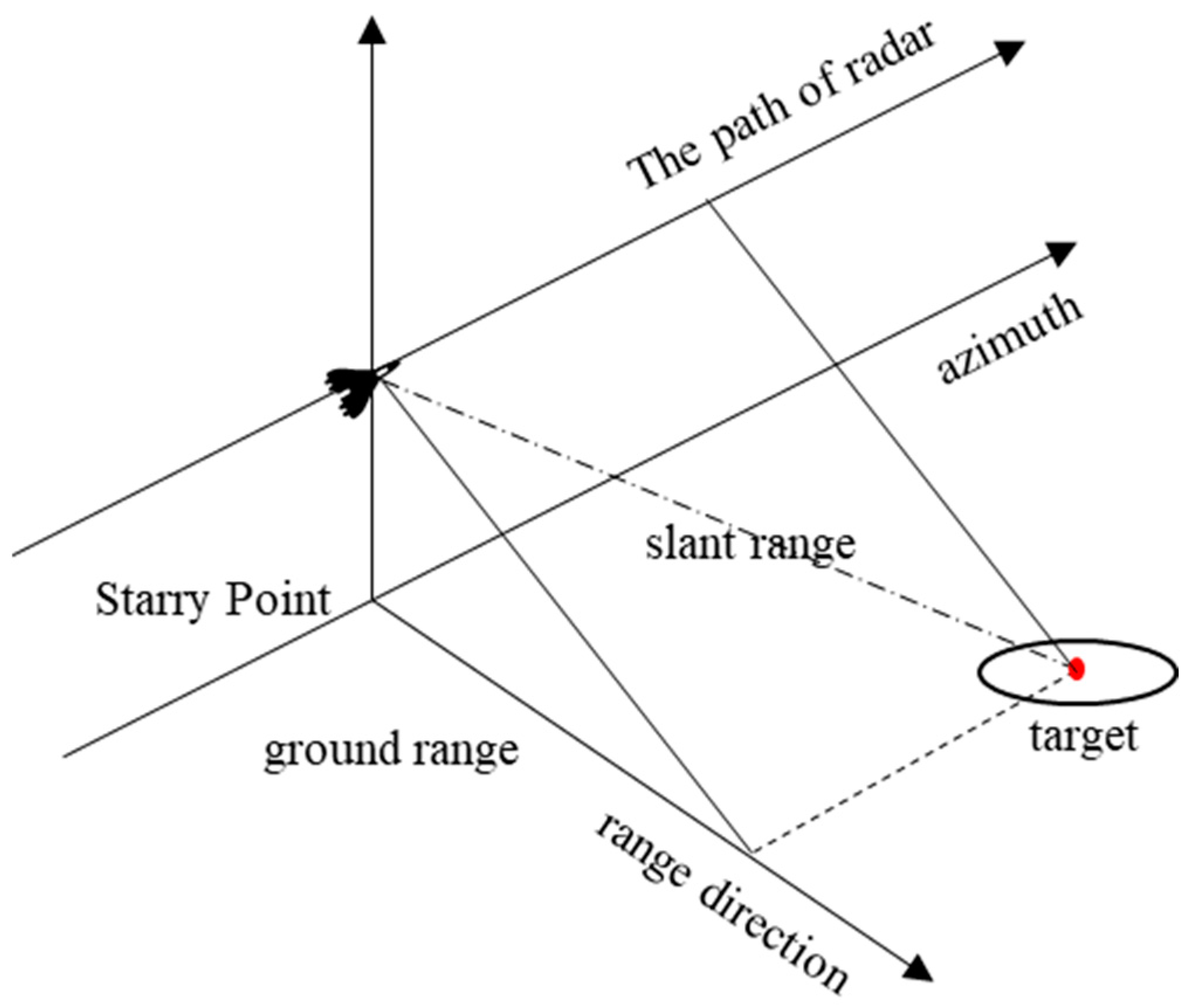
4.3.1. Principle of SAR
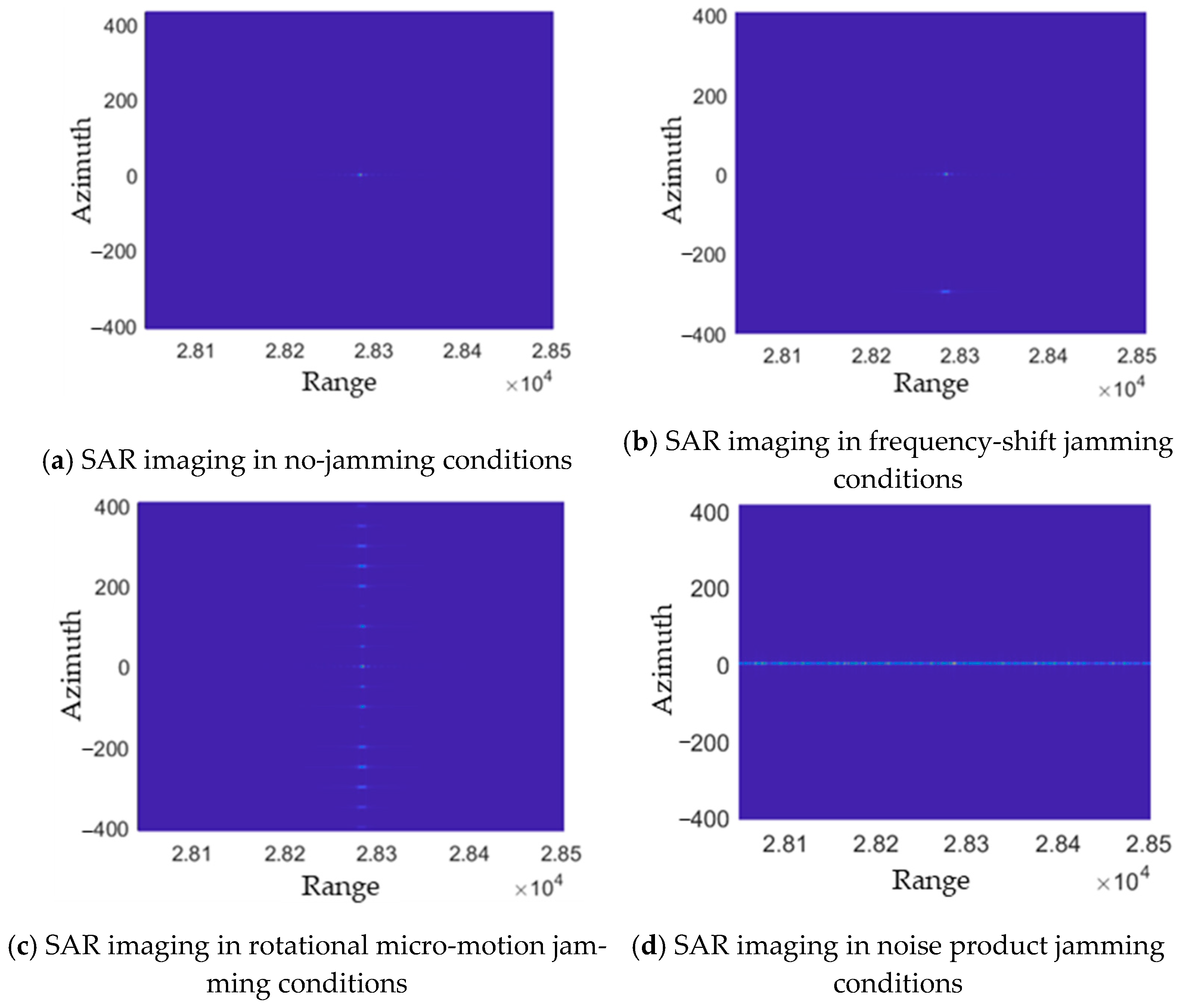
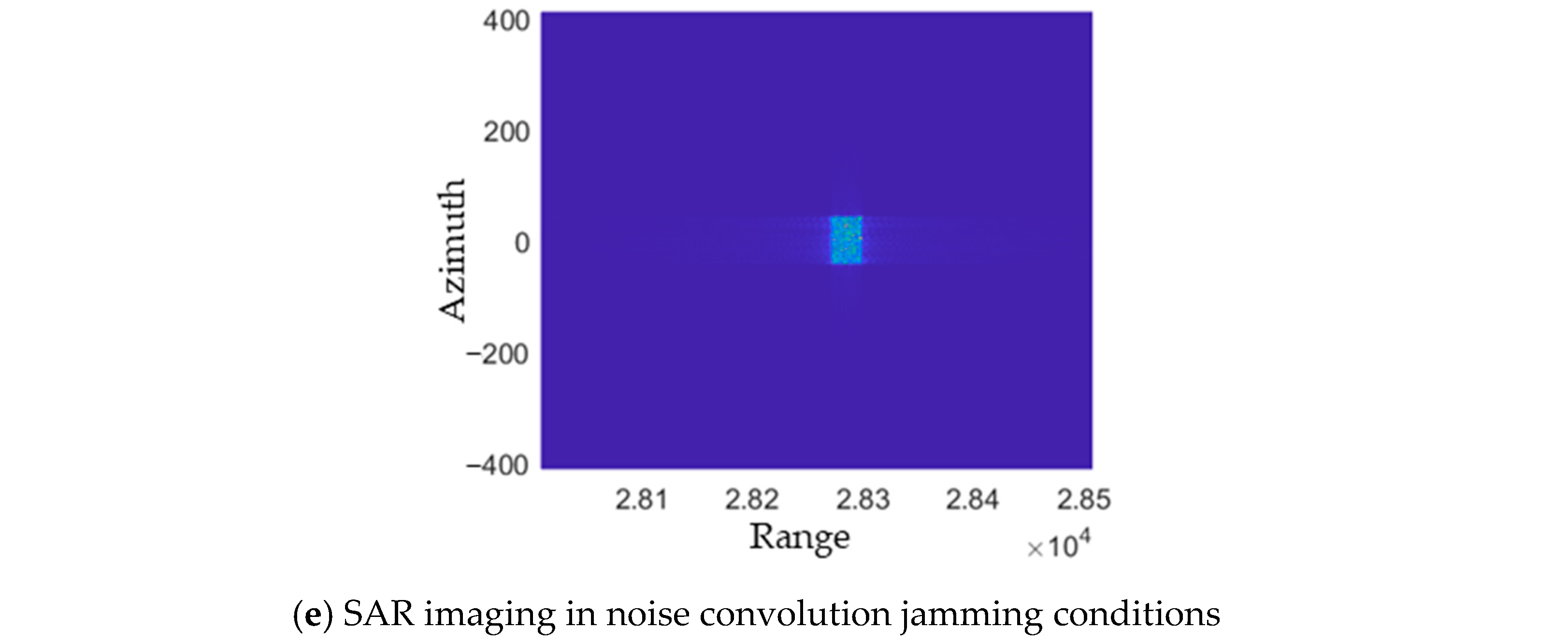
4.3.2. Jamming
4.4. Comparative Analysis
5. Classification Based on the Stage of Jamming Action
6. Summary
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Joint Chiefs of Staff. Electronic Warfare. 2023, JP 3-13.1. Available online: https://edocs.nps.edu/dodpubs/topic/jointpubs/JP3/JP3_13_1_070125.pdf (accessed on 31 January 2024).
- Skolnik, M.I. Radar Handbook, 3rd ed.; McGraw-Hill: New York, NY, USA, 2008. [Google Scholar]
- Haykin, S. Cognitive radar: A way of the future. IEEE Signal Process. Mag. 2006, 23, 30–40. [Google Scholar]
- Wang, L. Adaptive Waveform Design Based on Information Theory. Ph.D. Thesis, National University of Defense Technology, Changsha, China, 2015. [Google Scholar]
- Bell, M.R. Information theory and radar waveform design. IEEE Trans. Inf. Theory 1993, 39, 1578–1597. [Google Scholar] [CrossRef]
- Romero, R.A.; Bae, J.; Goodman, N.A. Theory and application of SNR and mutual information matched illumination waveforms. IEEE Trans. Aerosp. Electron. Syst. 2011, 47, 912–927. [Google Scholar]
- He, P.; Zhao, L.; Zhou, S.; Niu, Z. Water-filling: A geometric approach and its application to solve generalized radio resource allocation problems. IEEE Trans. Wirel. Commun. 2013, 12, 3637–3647. [Google Scholar] [CrossRef]
- Zhu, Z.; Kay, S.; Raghavan, R.S. Information-theoretic optimal radar waveform design. IEEE Signal Process. Lett. 2017, 24, 274–278. [Google Scholar]
- Chen, J.; Wang, F.; Zhou, J. Information content based optimal radar waveform design: LPI’s purpose. Entropy 2017, 19, 210. [Google Scholar] [CrossRef]
- Yan, Z.; Wu, C.; Chen, X.; Zeng, X.; Chen, Y. Research on coherent multi-false-target jamming technology based on comb spectrum modulation. Mod. Radar 2017, 39, 85–88. [Google Scholar]
- Zhang, M.; Zhang, W.; Lu, M. Design of random phase multi-frequency point cyclic superposition comb spectrum jamming waveform. Aerosp. Def. 2023, 6, 74–79. [Google Scholar]
- Shen, A.; Jiang, Q. Comb spectrum jamming technology for ultra-wideband radar without carrier frequency. Syst. Eng. Electron. 2009, 1, 66–68. [Google Scholar]
- Shen, A.; Jiang, Q. Broadband SAR subband pulse modulation comb spectrum jamming technology. Mod. Radar 2014, 1, 6–10. [Google Scholar]
- An, K.; Yang, T. Neural network-based optimization technology for peak-to-average power ratio of comb spectrum signals. J. Acad. Electron. Inf. Eng. 2020, 15, 566–572. [Google Scholar]
- Spector, S.C. A Coherent Microwave Memory Using Digital Storage: The Loopless Memory Loop; Electronic Warfare: New York, NY, USA, 1975. [Google Scholar]
- Tang, L.; Huang, J. Research on smart noise jamming for linear frequency-modulated pulse compression radar. Electron. Countermeas. 2008, 1, 14–17. [Google Scholar]
- Huang, D.; Xing, S.; Li, Y.; Liu, Y.; Xiao, S. SAR smart jamming method based on product modulation. Syst. Eng. Electron. 2021, 43, 3160–3168. [Google Scholar]
- Zhu, Y.; Zhao, G. Effect analysis of range target image deception jamming. J. Electromagn. Waves Appl. 2006, 1, 131–134. [Google Scholar]
- Zhang, W.; Zhou, X.; Tan, Y. Effect analysis of range false target deception jamming for fire control radar. Sichuan Ordnance J. 2007, 4, 40–42. [Google Scholar]
- Zhang, Y.; Gao, M.; Li, Y.; Yuan, Q. Digital implementation of multi-false-target jamming in velocity domain. J. Beijing Inst. Technol. 2009, 29, 59–62. [Google Scholar]
- Wei, S. Research on Active Efficient Deception Jamming Mechanism and Method for MIMO Radar. Master’s Thesis, University of Electronic Science and Technology of China, Sichuan, China, 2013. [Google Scholar]
- Gan, D.; Meng, L.; Guo, H. Brief analysis of range-Doppler false target jamming based on DRFM. Spacecr. Electron. Countermeas. 2005, 1, 25–27. [Google Scholar]
- Shi, C.; Wen, W.; Song, H.; Tian, D.; Zhou, J. Research on Delay Error of UAV Swarm Repeater Deception Jamming against Networked Radar. Aero Weapon. 2024, 31, 131–137. [Google Scholar]
- Wang, X.; Liu, J.; Zhang, W. Mathematical principles of intermittent sampling and retransmission jamming. Chin. Sci. Bull. 2006, 36, 891–901. [Google Scholar]
- Liu, J.; Wang, X.; Liu, Z.; Yang, J.; Wang, G. Leading false target group jamming for linear frequency-modulated pulse compression radar. J. Electron. Inf. Technol. 2008, 30, 1350–1353. [Google Scholar] [CrossRef]
- Liu, Z.; Liu, J.; Wang, X.; Wang, G. Analysis of intermittent sampling and retransmission jamming signals. Electron. Countermeas. 2007, 6, 19–23. [Google Scholar]
- Pan, X.; Liu, X.; Chen, J.; Feng, X.; Gu, Z.; Xiao, S. Review of Intermittent Sampling and Retransmission Jamming Technology. Syst. Eng. Electron. 2024, 46, 2887–2901. [Google Scholar]
- Luan, L. Simulation and Modeling Study of Smart Noise Jamming. Master’s Thesis, Xidian University, Xi’an, China, 2009. [Google Scholar]
- Yun, J.; Zhu, Y.; Jin, X. Peak-to-average power ratio improvement method for dense false target jamming. Shipborne Electron. Countermeas. 2012, 2, 54–57. [Google Scholar]
- Shen, H.; Wang, X.; Rong, J. Research on smart noise jamming waveform based on DRFM. Spacecr. Electron. Countermeas. 2007, 1, 62–64. [Google Scholar]
- Lu, K.; Wang, Y.; Liu, J. Research and simulation of smart noise waveform design. Piezoelectrics Acoustooptics 2009, 31, 757–759. [Google Scholar]
- Chen, Q. Simulation Study of Smart Noise Jamming. Master’s Thesis, Nanjing University of Science and Technology, Nanjing, China, 2007. [Google Scholar]
- Zhou, Y.; Zhang, J.; He, P. A radar jamming technology—smart noise jamming. Radar Countermeas. 2002, 1, 12–16. [Google Scholar]
- Tang, L.; Huang, J.; Xu, X. A smart noise jamming method for LFM pulse compression radar. Spacecr. Electron. Countermeas. 2008, 2, 34–37. [Google Scholar]
- Li, W.; Liang, D.; Dong, Z. Research on SAR jamming technology based on deceptive moving targets. Remote Sens. 2006, 1, 71–75. [Google Scholar]
- Liu, G.; Zhang, Q.; Huang, Z.; Chen, T.; Mu, B.; Guo, H. SAR Imaging of Dense False Target Jamming Based on Phase Modulation. IEEE Geosci. Remote Sens. Lett. 2025, 22, 1–5. [Google Scholar]
- Pan, X.; Wang, W.; Feng, D.; Fu, Q.; Wang, G. LFM radar jamming method based on full pulse segmentation and retransmission. J. Natl. Univ. Def. Technol. 2013, 3, 119–125. [Google Scholar]
- Wang, Y.; Zhao, G. N-order SSC blind frequency-shift jamming algorithm for LFM radar. J. Circuits Syst. 2011, 16, 70–74. [Google Scholar]
- Xiao, J.; Wei, X.; Sun, J. Interrupted-sampling multi-strategy forwarding jamming with amplitude constraints based on simultaneous transmission and reception technology. Digital Signal Process. 2024, 147, 104416. [Google Scholar] [CrossRef]
- Zhang, Y. Waveform Optimization Design of Intermittent Sampling and Retransmission Jamming. Master’s Thesis, Harbin Engineering University, Harbin, China, 2022. [Google Scholar]
- Chen, T.; Zhang, Y.; Hu, X.; Xiao, Y. Waveform optimization design for detection and jamming integration based on DQN. Syst. Eng. Electron. 2023, 45, 638–646. [Google Scholar]
- Chen, T.; Zhang, Y.; Huang, X. Adaptive jamming waveform design based on reinforcement learning. Aerosp. Def. 2021, 4, 59–66. [Google Scholar]
- Hao, W.; Zhang, J.; Chen, J. Research on a non-uniform combined intermittent sampling and retransmission jamming method. Fire Control Radar Technol. 2023, 52, 87–91. [Google Scholar]
- Zhang, J.; Li, W.; Sun, W.; Wang, H. Optimization of phase-coded radar jamming waveform based on particle swarm optimization algorithm. Mod. Electron. Technol. 2023, 46, 27–32. [Google Scholar]
- Zhang, L. Research on New Jamming Technology for Phase-Coded Radar. Master’s Thesis, National University of Defense Technology, Changsha, China, 2008. [Google Scholar]
- Xu, L.; Feng, D.; Zhao, J.; Zhang, W. Leading false target jamming for phase-coded radar systems. J. Astronaut. 2013, 1, 133–138. [Google Scholar]
- Lai, Z.; Gao, Y.; Wan, J.; Zhou, Y. Research on dense false target jamming for phase-coded radar. J. Air Force Early Warn. Acad. 2016, 4, 267–270. [Google Scholar]
- Zhang, X.; Xiao, K.; Gu, J. New System Radar Confrontation Theory; Beijing Institute of Technology Press: Beijing, China, 2020. [Google Scholar]
- Lv, B.; Feng, Q.; Zhang, X.; Yuan, N. Research on random pulse convolution jamming for SAR. J. Acad. Electron. Inf. Eng. 2008, 3, 276–279. [Google Scholar]
- Lu, J.; Li, J.; Huang, G. Noise jamming research for pulse Doppler radar. Shipborne Electron. Countermeas. 2010, 33, 15–19. [Google Scholar]
- Cheng, L.; Xie, D.; Jiang, D.; Zhang, Y. Simulation study of pulse Doppler radar jamming based on SystemVue. Shipborne Electron. Countermeas. 2017, 50, 72–77. [Google Scholar]
- Lu, M. Research on Pulse Doppler Radar Jamming Technology. Master’s Thesis, Xidian University, Xi’an, China, 2005. [Google Scholar]
- Yang, H.; Cheng, Q.; Jiang, S.; Wang, J. Research on pulse Doppler radar jamming modulation technology. Electron. Compon. 2023, 46, 1225–1229. [Google Scholar]
- Yang, Z. Research on Pseudo-Code Phase Modulation Pulse Doppler Fuze Jamming Technology. Master’s Thesis, Xidian University, Xi’an, China, 2023. [Google Scholar]
- Goj, G. Synthetic-Aperture Radar and Electronic Warfare; Artech House: Boston, MA, USA, 1993. [Google Scholar]
- Condley, C. Some system considerations for electronic countermeasures to synthetic aperture radar. In Proceedings of the IEE Colloquium on Electronic Warfare Systems, London, UK, 14 January 1991. [Google Scholar]
- Liang, B. NMD-GBR radar jamming waveform design. Spacecr. Electron. Countermeas. 2007, 23, 5–7. [Google Scholar]
- Liang, B. Jamming for synthetic aperture radar. Shanghai Aerosp. 1995, 1, 37–42+47. [Google Scholar]
- Wu, X.; Dai, D.; Wang, X.; Lu, H. SAR azimuth Doppler modulation jamming. Mod. Radar 2010, 1, 55–60. [Google Scholar]
- Bo, Z.; Lei, H.; Bing, L.; Shi, L.; Wei, B. One-bit splitting deceptive jamming against SAR. Def. Technol. 2022, 18, 1760–1777. [Google Scholar]
- Wang, S.; Yu, L.; Ni, J.; Zhang, G. Research on active deception jamming methods for synthetic aperture radar. Acta Electron. Sin. 2003, 2, 1900–1903. [Google Scholar]
- Ji, P.; Xing, S.; Dai, D.; Xu, W.; Pang, B.; Feng, D. SAR convolution deception jamming method based on inverse chirp scaling. J. Electromagn. Waves Appl. 2023, 38, 1029–1039. [Google Scholar]
- Ji, P.; Xing, S.; Dai, D.; Pang, B.; Feng, D. SAR range convolution azimuth product modulation scene deception jamming method. J. Aeronaut. 2023, 44, 242–259. [Google Scholar]
- Huang, D.; Xing, S.; Liu, Y.; Li, Y.; Xiao, S. New method for generating false signals in SAR based on noise convolution modulation. J. Radars 2020, 9, 898–907. [Google Scholar]
- Wu, X.; Wang, X.; Liang, J. High-fidelity uniform motion false target modulation jamming method for SAR-GMTI. J. Astronaut. 2012, 10, 1472–1479. [Google Scholar]
- Wu, X.; Dai, D.; Wang, X.; Lu, H. A novel active jamming method for SAR based on micro-motion modulation. Acta Electron. Sin. 2010, 4, 954–959. [Google Scholar]
- Wu, X.; Wang, X.; Lu, H. Research on intermittent sampling and retransmission jamming for SAR. J. Astronaut. 2009, 5, 2043–2048, 2072. [Google Scholar]
- Wu, X.; Bai, Z.; Dai, D.; Wang, X. Azimuth intermittent sampling and retransmission jamming for SAR. Signal Process. 2010, 1, 1–6. [Google Scholar]
- Zhou, Y.; Bi, D.; Shen, A. Large-area masking active-passive coordinated jamming method for SAR-GMTI. Syst. Eng. Electron. 2018, 40, 1004–1011. [Google Scholar]
- Song, J.; Zhang, H.; Zheng, F. Micro-motion modulation-based comb spectrum smart noise suppression jamming. Radar Sci. Technol. 2020, 18, 531–538+545. [Google Scholar]
- Wu, J.; Ji, X.; Wang, X.; Xiong, B.; Li, B. A practical noise jamming method for pulse compression Doppler radar. Electron. Inf. Countermeas. Technol. 2022, 37, 55–59. [Google Scholar]
- Wu, Z. Cognitive Electronic Countermeasure Jamming Waveform Design. Master’s Thesis, Xidian University, Xi’an, China, 2018. [Google Scholar]
- Huang, H.; Huang, Z.; Zhou, Y. Research on frequency-shift jamming for synthetic aperture radar. J. Astronaut. 2006, 3, 463–469. [Google Scholar]


| Jamming Technique | Parameters | Target | ||||||
|---|---|---|---|---|---|---|---|---|
| Colored Noise | 0 | 0 | 0 | 1 | / | 0 | / | No specific target |
| Comb Spectrum Jamming | 0 | 0 | 0 | 1 | / | Comb spectrum frequency shift formula | / | No specific target |
| Trailing Range False Target Jamming | 0 | 0 | 1 | 0 | / | Doppler coupling | Increasing Time Delay | PD radar |
| Non-Trailing Range False Target Jamming | 0 | 0 | 1 | 0 | / | / | Fixed Time Delay | No specific target |
| Velocity False Target Jamming | 0 | 0 | 1 | 0 | / | Doppler frequency shift (including velocity trailing, jitter, rotational micro-movement jamming, etc.) | Range Coupling | PD radar |
| Azimuth False Target Jamming | 0 | 0 | 1 | 0 | / | Slow-time frequency shift can achieve false targets in the azimuth direction of Synthetic Aperture Radar (SAR) | Time Alignment | SAR |
| Intermittent Sampling and Repetition Jamming | 0 | 0 | 1 | 0 | Sampling width (variable when non-uniform sampling is used) | / | Transmission Timing | No specific target |
| Convolutional Jamming | 0 | 1 | 0 | 0 | / | / | Time Alignment | No specific target |
| Multiplicative Jamming | 1 | 0 | 0 | 0 | / | / | Time Alignment | No specific target |
| Jamming Type | Jamming Technique | Jamming Effect | Required Prior Parameters | Advantages | Disadvantages |
|---|---|---|---|---|---|
| Barrage Jamming | Narrowband Colored Noise [4] | Reduces SNR, uses colored noise to overwhelm echoes, and decreases detection probability. | 1. Radar Carrier Frequency 2. Radar Bandwidth 3. Radar Signal Power Spectral Distribution | 1. In terms of frequency, the jamming energy is more concentrated than in blocking jamming. 2. Fewer prior parameters are required, and the jamming signal is easy to generate. | 1. The generated jamming signal is non-coherent. 2. When targeting fixed frequency points, it is not flexible. |
| Comb Spectrum Jamming [12,13,14] | Targets multiple frequency points, reduces SNR, uses colored noise to overwhelm echoes, and decreases detection probability. | 1. Multiple Frequency Points of Radar Operation 2. Signal Bandwidth 3. Power Spectral Characteristics | Can release colored noise targeting radar signal frequency hopping or multiple frequency points operating simultaneously. | 1. Requires the jammer’s transmitter and receiver bandwidth to be relatively large. 2. The superposition of signals interfering with multiple frequency points may result in an excessively high PAPR, affecting engineering implementations. | |
| Deceptive Jamming | Deceptive Jamming with Complete Pulses [16,17,18,19,20,21,22,23] | Generates false targets in terms of range, azimuth, or velocity. | 1. Carrier Frequency 2. Intercepted Radar Pulse 3. Pulse Repetition Interval 4. Frequency Modulation Slope 5. Distance and Relative Motion Relationship between Radar, Jammer, and False Target | 1. Can produce deceptive jamming signals highly similar to real target echoes. 2. The azimuth and velocity of false targets are controllable. 3. The jamming signal is highly coherent with the radar signal, requiring low jamming power. | 1. Requires high-quality intercepted pulses. 2. Requires many prior parameters. 3. When designing multiple false targets with different distributions and motion patterns, the parameters need to be adjusted one by one, the calculation is complex, and the PAPR is difficult to control. 4. When using modulation, such as rotation and micro-motion, the distribution pattern of multiple false targets is impacted. |
| Intermittent Sampling and Repetition Jamming [24,25,26,27] | Forms a series of regularly distributed false targets in regard to range direction. | Intercepted Radar Pulse | 1. Requires fewer parameters. 2. Can quickly generate multiple false targets, with strong real-time performance. 3. The jamming signal is coherent, requiring low jamming power. 4. Solves the antenna transmitter and receiver isolation problem of the jammer, with a low PAPR. | 1. The distribution pattern of false targets is regular and easily recognizable. 2. The utilization rate of the jamming time is low, and the jamming effect is easily affected by the sampling and retransmission rules and duty cycle. | |
| Smart Noise Jamming | Smart Noise Jamming by Modulating Complete Pulses [16,28,29,30,31,32,33,34,35] | Generates suppressive jamming in the range or imaging area. | 1. Carrier Frequency 2. Intercepted Radar Pulse 3. Pulse Repetition Interval 4. Distance and Relative Motion Relationship between Radar, Jammer, and False Target | Can produce highly realistic points, area deception, or suppression jamming. | It depends on many parameters, has a large computational load, and has poor real-time performance. |
| Smart Noise Jamming by Modulating Pulse Segments [40,41,42,43,44,45,46,47] | Produces suppressive jamming in range or specific imaging areas. | 1. Carrier Frequency 2. Intercepted Radar Pulse 3. Pulse Repetition Interval 4. Distance and Relative Motion Relationship between Radar, Jammer, and False Target | It can produce highly realistic point, area deception, or suppression jamming (intermittent sampling and retransmission jamming can only produce range jamming). | 1. The signals generated by equidistant sampling and pulse sampling methods mean that it is difficult to address the antenna transmitter and receiver isolation problem and high PAPR issues. 2. In regard to intermittent sampling and retransmission jamming, it is difficult to interfere in the azimuth direction, and the utilization rate of the jamming time is low. |
| Jamming Type | Jamming Technique | Jamming Effect | Required Prior Parameters | Advantages | Disadvantages |
|---|---|---|---|---|---|
| Pulse Compression Radar | Noise Jamming [4] | Suppresses the energy of the target echo, increases the SNR, and affects target detection. | 1. Signal Carrier Frequency 2. Signal Bandwidth | Less dependent on reconnaissance parameters | High power requirements, prone to revealing the jammer’s location. |
| Intermittent Sampling and Repetition Jamming [24,25,26,27] | Forms a series of evenly spaced false point targets. | 1. Intercepted Radar Pulse 2. Pulse Width | 1. Less dependent on parameters 2. Good real-time performance 3. Flexible and variable number and spacing of false targets 4. Solves the problem of transmitter–receiver isolation for the jammer’s antenna | 1. The distribution pattern of false targets is regular and easily identifiable. 2. Low utilization rate of jamming time. 3. Prone to being affected by the duty cycle. | |
| Smart Noise Jamming [30,31,32] | Can create suppressive dense false targets. | 1. Intercepted Radar Pulse 2. Pulse Width 3. Pulse Bandwidth 4. Relative Position Relationship between the Jammer and the Radar | 1. Flexible modulation methods 2. The jamming signal is coherent with the radar signal, combining deception and suppression | Some modulation methods require a high computational load or have difficulty in suppressing the PAPR. | |
| PD Radar | Noise Jamming [50,51] | Suppresses the energy of the target echo, increases the SNR, and affects target detection. | 1. Signal Carrier Frequency 2. Signal Bandwidth | Less dependent on reconnaissance parameters | 1. High power requirements. 2. Prone to revealing the jammer’s location. |
| Range–Velocity Deceptive Jamming [52] | Can create highly realistic single or multiple range, velocity, or range–velocity false targets for deception. | 1. Intercepted Radar Pulse 2. Signal Carrier Frequency 3. Signal Pulse Width 4. Signal Bandwidth 5. Pulse Repetition Interval (PRI) | 1. Can generate velocity and range false targets, and can also interfere with both velocity and range simultaneously, offering flexible jamming effects 2. Can generate multiple false targets at the same time | 1. The current methods for generating multiple false targets in deceptive jamming have a strong regularity, making them easily identifiable. 2. If false target signals are designed individually to create multiple false targets for deception, the computational load is high, and it is difficult to suppress the PAPR. 3. High dependence on parameters. | |
| Intermittent Sampling and Repetition Jamming [54] | Forms a series of evenly spaced false point targets in the range direction. | 1. Intercepted Radar Pulse 2. Pulse Width | 1. Less dependent on parameters 2. Good real-time performance 3. The number and spacing of false targets are flexible and variable 4. Solves the problem of transmitter–receiver isolation for the jammer’s antenna | 1. The distribution pattern of false targets is regular and easily identifiable. 2. Low utilization rate of jamming time. 3. Prone to being affected by the duty cycle. 4. Difficult to create velocity deception. | |
| Smart Noise Jamming [53,54] | Can form dense false targets for suppressive purposes. | 1. Intercepted Radar Pulse 2. Pulse Width 3. Pulse Bandwidth 4. Relative Position and Velocity Relationship between the Jammer and the Radar | 1. Flexible modulation methods 2. The jamming signal is coherent with the radar signal, balancing deception and suppression | 1. Some modulation methods have a high computational load, or it is difficult to suppress the PAPR. 2. It is challenging to design the process for different target motions. | |
| SAR | Noise Jamming [55,56,57,58] | Suppresses the energy of the target echo but degrades the image quality. | 1. Carrier Frequency 2. Bandwidth | 1. Less dependent on reconnaissance parameters 2. Wide application range | 1. High power requirements. 2. Prone to revealing the jammer’s location. |
| Convolutional Deceptive Jamming [61] | False targets or scenarios. | 1. Intercepted Radar Pulse 2. Relative Position and Velocity Relationship between the Jammer and the Radar 3. Pulse Repetition Interval (PRI) 4. Carrier Frequency | Generates point, surface, and scenario deception | 1. High computational load, and poor real-time performance. 2. High dependency on reconnaissance parameters. | |
| Intermittent Sampling and Repetition Jamming [67,68] | Evenly spaced false point target strings in the range direction. | Intercept Radar Signal | 1. Less dependent on reconnaissance parameters, with strong real-time capabilities 2. The number and spacing of false targets are flexible and variable 3. Solves the problem of transmitter–receiver isolation for the jammer’s antenna | 1. The regularity of the false targets is strong, making them easily identifiable. 2. The utilization rate of the jamming time is relatively low. 3. Prone to being affected by duty cycle. | |
| Frequency-Shift Jamming [66] | Forms false point targets, strings of point targets, suppression bands, or suppression areas in the azimuth direction. | 1. Intercepted Radar Pulse 2. Pulse Width 3. Signal Bandwidth | 1. Can create a variety of jamming effects 2. Can cover distributed surface targets and large-scale scenarios | High dependency on reconnaissance parameters. | |
| Motion Modulation Jamming [65,66] | Azimuth false targets or suppression stripes. | 1. Intercepted Radar Pulse 2. Signal Carrier Frequency 3. Relative Position and Velocity Relationship between the Jammer and the Radar | 1. The length of the suppression line is variable 2. The spacing and number of false point targets are variable | 1. The suppression area is small, making it difficult to cover surface targets. 2. The false targets have a strong regularity, making them easily identifiable. | |
| Smart Noise Jamming [62,63,64] | Suppression bands, suppression areas. | 1. Intercepted Radar Pulse 2. Relative Position and Velocity Relationship between the Jammer and the Radar 3. Signal Carrier Frequency 4. Pulse Width 5. Bandwidth | 1. Flexible modulation methods 2. Diverse jamming effects | High computational load, and poor real-time performance for some methods. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pan, Y.; Xie, D.; Zhao, Y.; Wang, X.; Huang, Z. Overview of Radar Jamming Waveform Design. Remote Sens. 2025, 17, 1218. https://doi.org/10.3390/rs17071218
Pan Y, Xie D, Zhao Y, Wang X, Huang Z. Overview of Radar Jamming Waveform Design. Remote Sensing. 2025; 17(7):1218. https://doi.org/10.3390/rs17071218
Chicago/Turabian StylePan, Yu, Didi Xie, Yurui Zhao, Xiang Wang, and Zhitao Huang. 2025. "Overview of Radar Jamming Waveform Design" Remote Sensing 17, no. 7: 1218. https://doi.org/10.3390/rs17071218
APA StylePan, Y., Xie, D., Zhao, Y., Wang, X., & Huang, Z. (2025). Overview of Radar Jamming Waveform Design. Remote Sensing, 17(7), 1218. https://doi.org/10.3390/rs17071218










