Exploring Knowledge Domain of Intelligent Safety and Security Studies by Bibliometric Analysis
Abstract
1. Introduction
2. Data and Methodology
2.1. Data Collection
2.2. Research Methods and Tools
3. Results
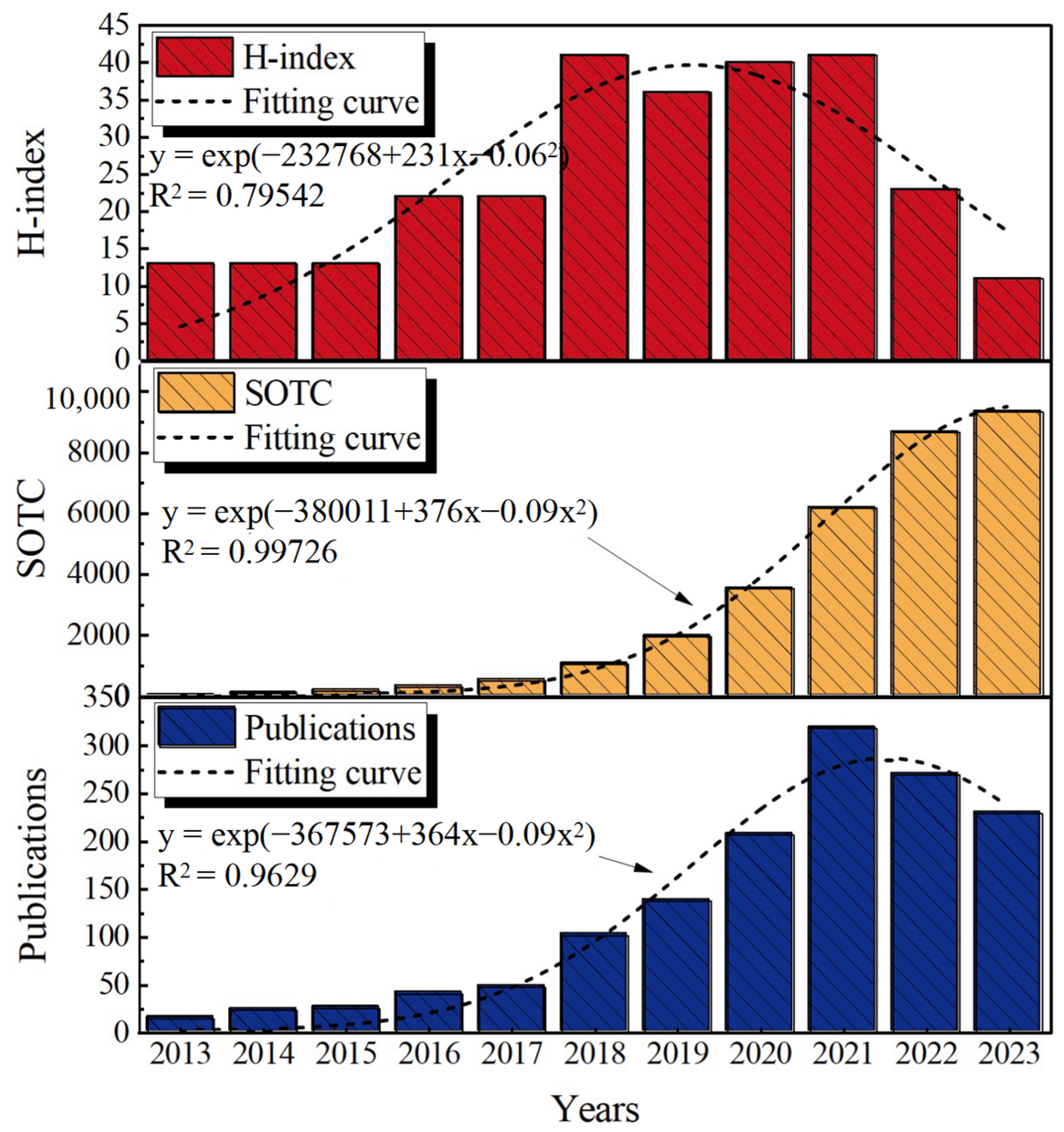
3.1. Trends in Literature Publications
3.1.1. Temporal Distribution Analysis
3.1.2. Country/Region Distribution Analysis
3.2. Academic Cooperation and Major Research Bases
3.2.1. Key Institutions and Cooperation Analysis
3.2.2. Major Authors and Cooperation Analysis
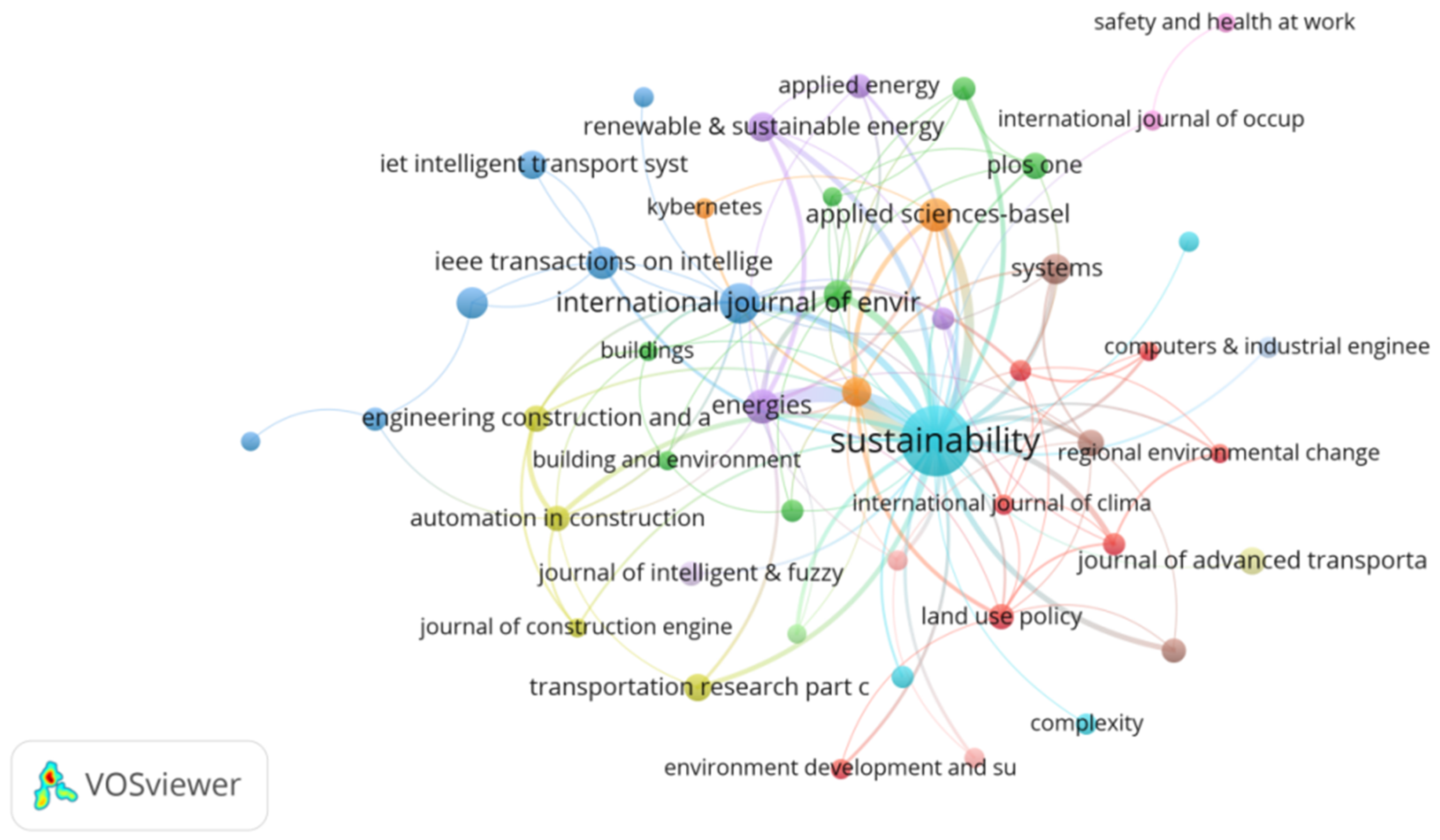
3.2.3. Journal Distribution Analysis
3.3. Current Situation and Basic Knowledge of Research Field
3.3.1. Highly Cited Journals Analysis
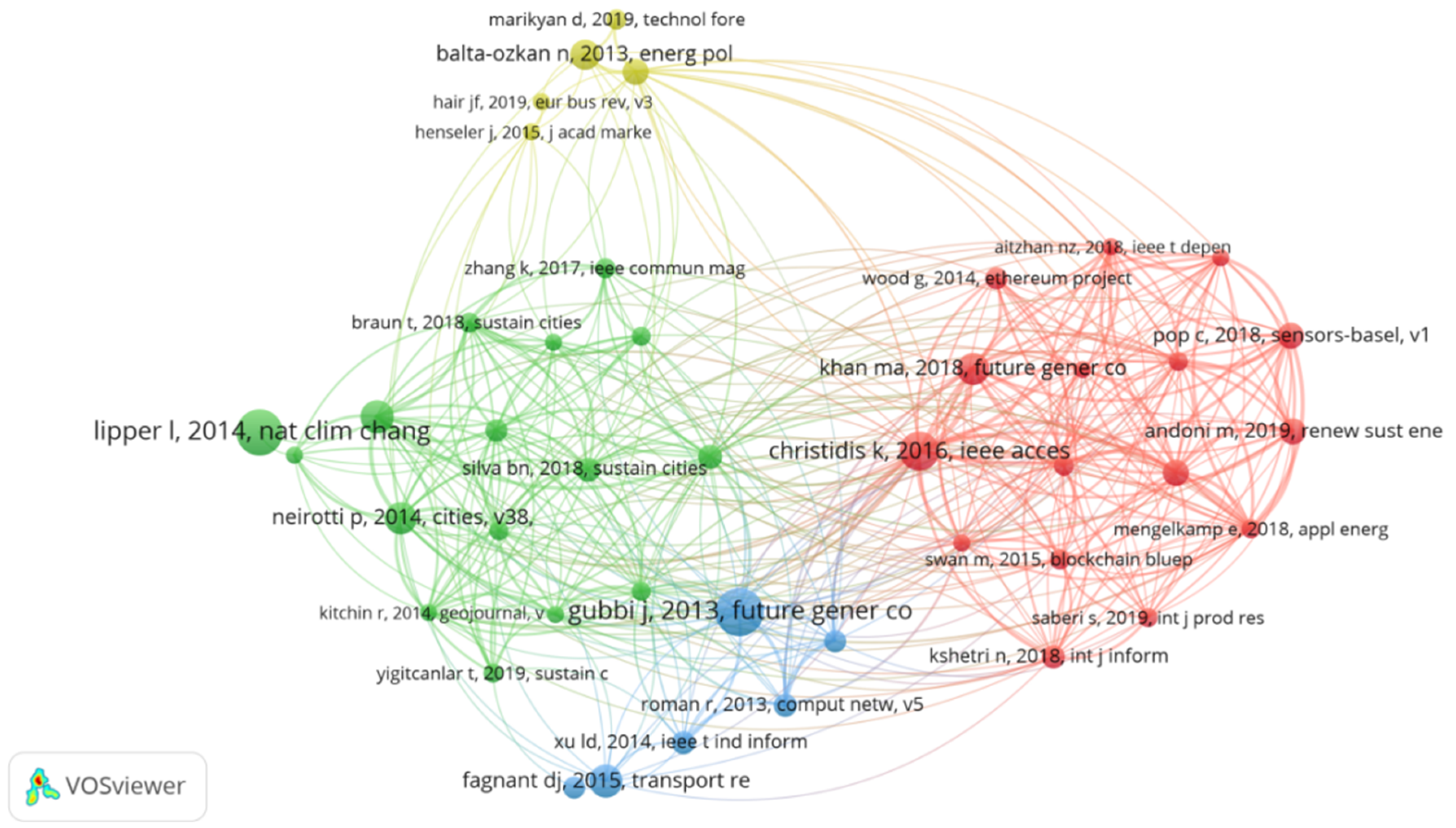
3.3.2. Core Literature Analysis
3.3.3. Knowledge Base Analysis
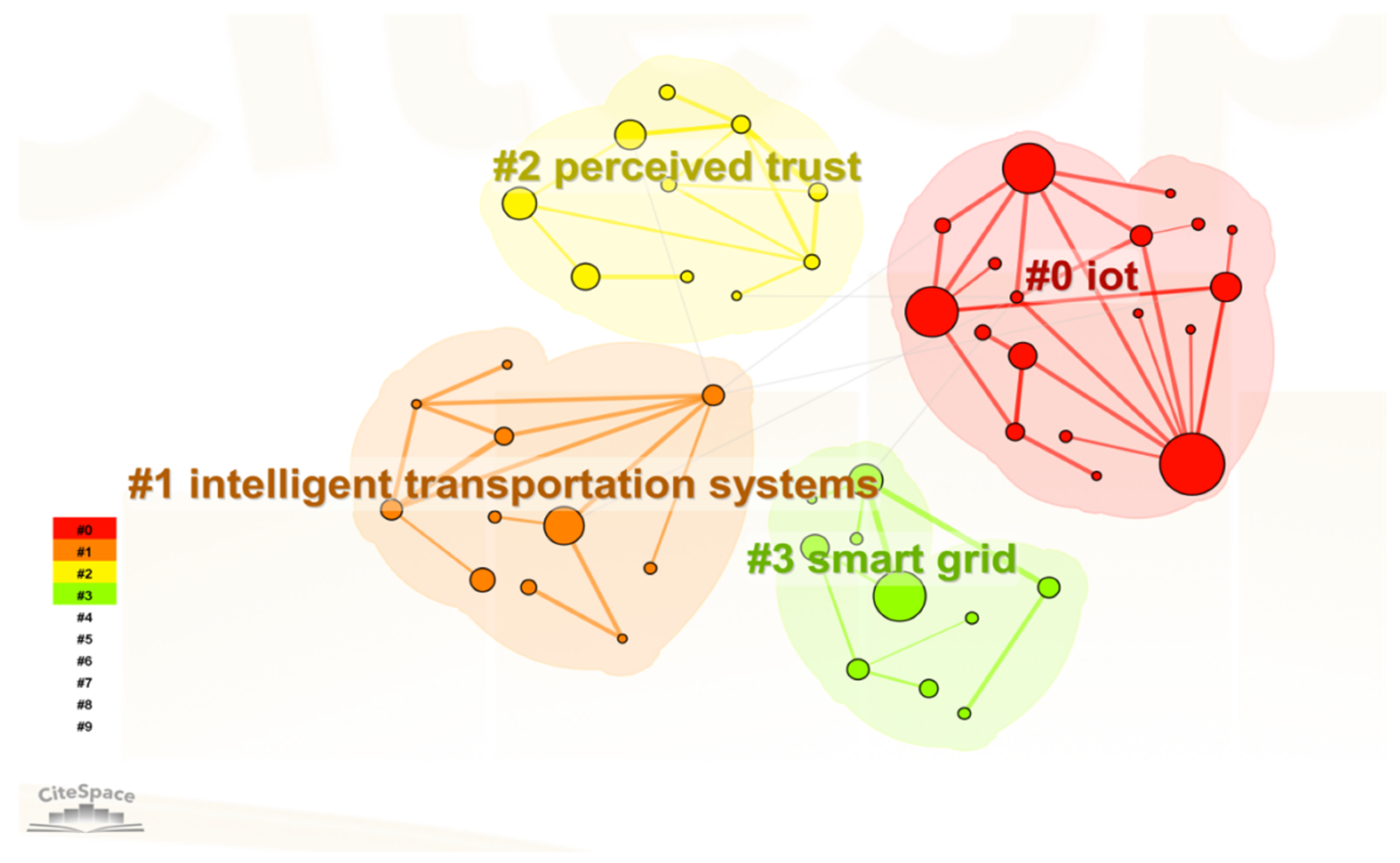
3.4. Research Hotspots and Frontier
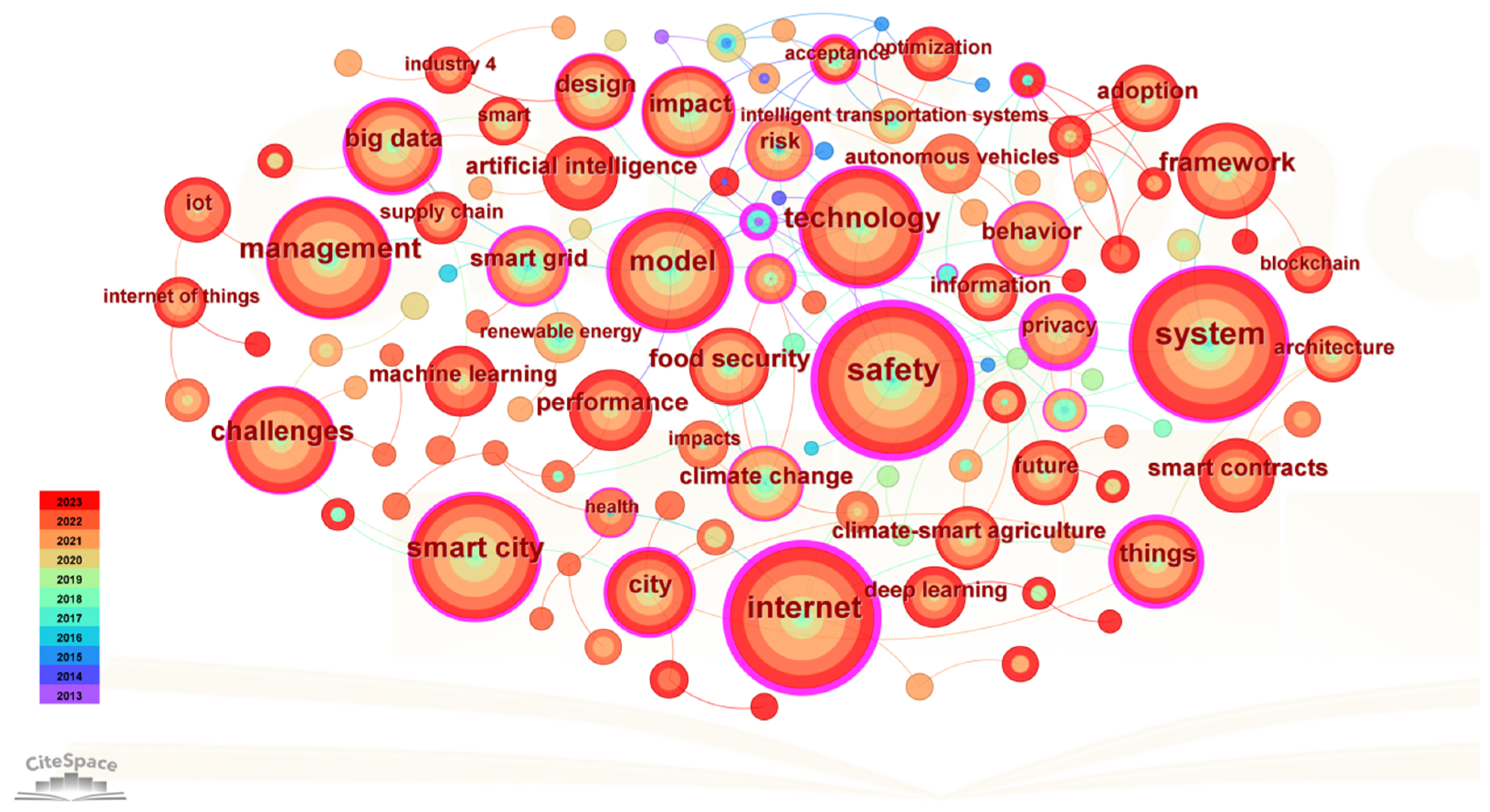
3.4.1. Research Hotspot Analysis
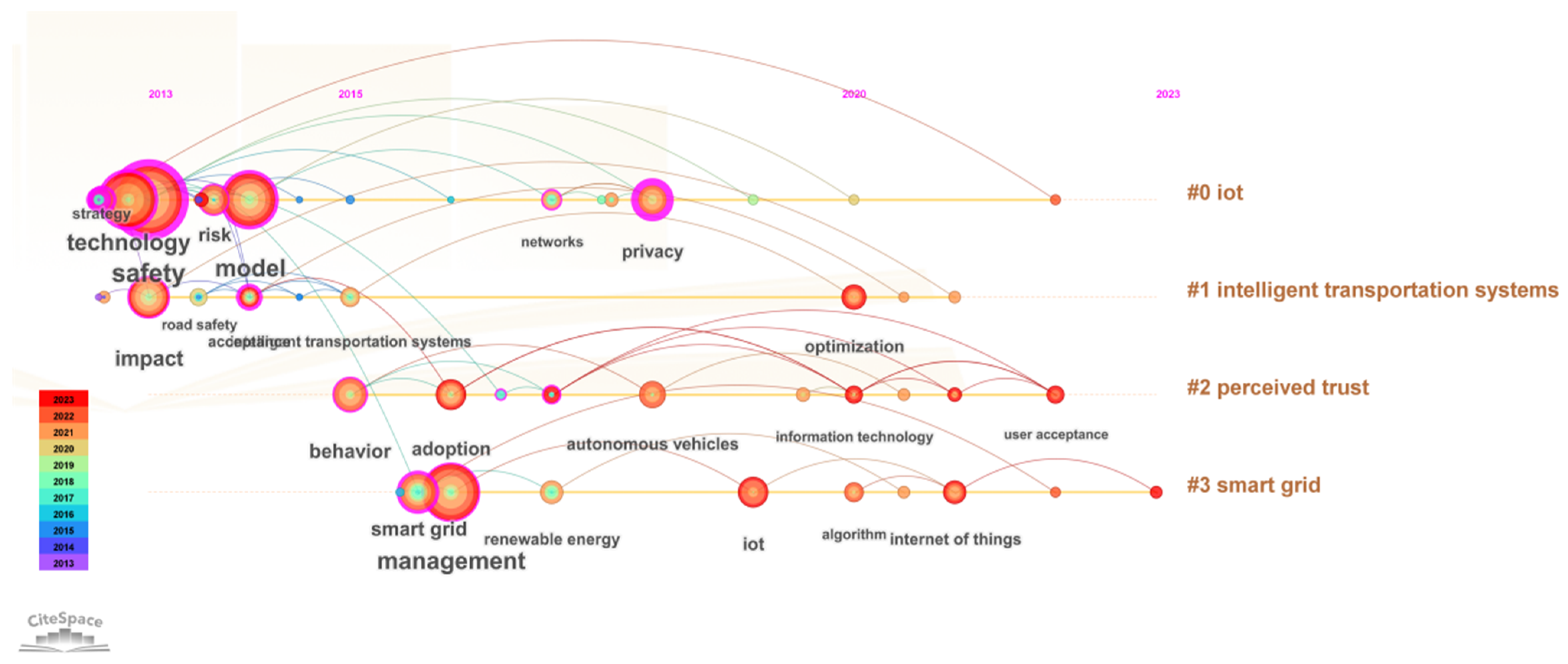
3.4.2. Research Frontiers Exploration
4. Discussion
4.1. Challenges for Future Research
4.2. Theoretical and Practical Contributions
4.3. Future Prospects
5. Conclusions
- (1)
- Research in intelligent safety and security can be categorized into three phases: steady development from 2013 to 2016, stable growth from 2017 to 2020, and rapid expansion from 2021 to 2023. Geographically, significant collaboration has been established between China, the United States, the United Kingdom, and South Korea, with China emerging as the core of this collaboration due to its significant status and influence. Looking ahead, Chinese institutions and scholars are expected to play a pivotal role in further advancing research in this field, owing to their substantial contributions.
- (2)
- China has shown substantial research strength, with four Chinese institutions ranking among the top 10 in terms of the number of published papers. Notably, King Saud University, The Hong Kong Polytechnic University, and Tongji University have been particularly active, with extensive academic collaborations established by scholars from these institutions. Research in this field is marked by multidisciplinary integration, primarily focusing on environmental protection and sustainable development. The most frequently cited journals include Renewable and Sustainable Energy Reviews, Sustainable Cities and Society, and Energies. Co-cited journals can be broadly categorized into four main areas: intelligent transportation systems, Environmental Ecology, and Chemical and Engineering Technology, with Renewable and Sustainable Energy Reviews, Sustainable Cities and Society, and IEEE Transactions on Intelligent Transportation Systems being the core journals.
- (3)
- The research hotspots in intelligent safety and security can be summarized into four core categories. The first is IoT security, focusing on ensuring the stable operation of IoT devices and systems, preventing security threats and attacks, and safeguarding data integrity and confidentiality. The second is intelligent transportation systems, which aim to improve traffic efficiency and safety through intelligent technologies, with real-time data processing and intelligent decision-making being crucial for enhancing traffic conditions. Research also emphasizes traffic safety, addressing not only accident prevention and response but also the long-term social, economic, and environmental implications. Additionally, smart grids and renewable energy are gaining attention for their role in the intelligent monitoring and optimization of power systems through advanced information and communication technologies, with renewable energy serving as a key component of sustainable development.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Latif, S.; Idrees, Z.; Huma, Z.E.; Ahmad, J. Blockchain technology for the industrial internet of things: A comprehensive survey on security challenges, architectures, applications, and future research directions. Trans. Emerg. Telecommun. Technol. 2021, 32, e433737. [Google Scholar] [CrossRef]
- Sharma, M.; Pant, S.; Sharma, D.K.; Gupta, K.D.; Vashishth, V.; Chhabra, A. Enabling security for the industrial internet of things using deep learning, blockchain, and coalitions. Trans. Emerg. Telecommun. Technol. 2021, 32, e4137. [Google Scholar] [CrossRef]
- Oumaima, F.; Karim, Z.; Abdellatif, E.; Mohammed, B. A survey on blockchain and artificial intelligence technologies for enhancing security and privacy in smart environments. IEEE Access 2022, 10, 93168–93186. [Google Scholar] [CrossRef]
- Mishra, P.; Vidyarthi, A.; Siano, P. Guest editorial: Security and privacy for cloud-assisted internet of things (iot) and smart grid. IEEE Trans. Ind. Inform. 2022, 18, 4966–4968. [Google Scholar] [CrossRef]
- Li, B.B.; Xiao, G.X.; Lu, R.X.; Deng, R.L.; Bao, H.Y. On feasibility and limitations of detecting false data injection attacks on power grid state estimation using d-facts devices. IEEE Trans. Ind. Inform. 2020, 16, 854–864. [Google Scholar] [CrossRef]
- Wang, Z.W.; Zhang, B.; Xu, X.N.; Usman; Li, L. Research on cyber-physical system control strategy under false data injection attack perception. Trans. Inst. Meas. Control 2022. [Google Scholar] [CrossRef]
- Qin, J.H.; Li, M.L.; Shi, L.; Yu, X.H. Optimal denial-of-service attack scheduling with energy constraint over packet-dropping networks. IEEE Trans. Autom. Control 2018, 63, 1648–1663. [Google Scholar] [CrossRef]
- Chen, W.; Wang, X.Z. Coal mine safety intelligent monitoring based on wireless sensor network. IEEE Sens. J. 2021, 21, 25465–25471. [Google Scholar] [CrossRef]
- Bing, W.; Chao, W.U. Study on the innovation research of safety science based on the safety big data. Sci. Technol. Manag. Res. 2017, 37, 37–43. [Google Scholar] [CrossRef]
- Ayhan, B.U.; Tokdemir, O.B. Accident analysis for construction safety using latent class clustering and artificial neural networks. J. Constr. Eng. Manag. 2020, 146, 04019114. [Google Scholar] [CrossRef]
- Su, Y.; Mao, C.; Jiang, R.; Liu, G.W.; Wang, J. Data-driven fire safety management at building construction sites: Leveraging cnn. J. Manag. Eng. 2021, 37, 04020108. [Google Scholar] [CrossRef]
- Diem, A.; Wolter, S.C. The use of bibliometrics to measure research performance in education sciences. Res. High. Educ. 2013, 54, 86–114. [Google Scholar] [CrossRef]
- van Eck, N.J.; Waltman, L. Software survey: Vosviewer, a computer program for bibliometric mapping. Scientometrics 2010, 84, 523–538. [Google Scholar] [CrossRef]
- Liu, D.; Che, S.Q.; Zhu, W.Z. Visualizing the knowledge domain of academic mobility research from 2010 to 2020: A bibliometric analysis using citespace. SAGE Open 2022, 12, 21582440211068510. [Google Scholar] [CrossRef]
- Falagas, M.E.; Kouranos, V.D.; Arencibia-Jorge, R.; Karageorgopoulos, D.E. Comparison of scimago journal rank indicator with journal impact factor. FASEB J. 2008, 22, 2623–2628. [Google Scholar] [CrossRef] [PubMed]
- Liu, H.; Chen, H.L.; Hong, R.; Liu, H.G.; You, W.J. Mapping knowledge structure and research trends of emergency evacuation studies. Saf. Sci. 2020, 121, 348–361. [Google Scholar] [CrossRef]
- Lang, Z.H.; Liu, H.; Meng, N.; Wang, H.N.; Wang, H.; Kong, F.Y. Mapping the knowledge domains of research on fire safety—An informetrics analysis. Tunn. Undergr. Space Technol. 2021, 108, 103676. [Google Scholar] [CrossRef]
- Chen, C. Citespace ii: Detecting and visualizing emerging trends. J. Am. Soc. Inf. Sci. Tec. 2006, 57, 359–377. [Google Scholar] [CrossRef]
- Shiffrin, R.M.; Borner, K. Mapping knowledge domains. Proc. Natl. Acad. Sci. USA 2004, 101 (Suppl. S1), 5183–5185. [Google Scholar] [CrossRef]
- Chen, C.M.; Hu, Z.G.; Liu, S.B.; Tseng, H. Emerging trends in regenerative medicine: A scientometric analysis in citespace. Expert Opin. Biol. Ther. 2012, 12, 593–608. [Google Scholar] [CrossRef] [PubMed]
- Zhu, J.; Hua, W.J. Visualizing the knowledge domain of sustainable development research between 1987 and 2015: A bibliometric analysis. Scientometrics 2017, 110, 893–914. [Google Scholar] [CrossRef]
- Hong, R.; Xiang, C.; Liu, H.; Glowacz, A.; Pan, W. Visualizing the knowledge structure and research evolution of infrared detection technology studies. Information 2019, 10, 227. [Google Scholar] [CrossRef]
- Li, J.; Reniers, G.; Cozzani, V.; Khan, F. A bibliometric analysis of peer-reviewed publications on domino effects in the process industry. J. Loss Prev. Process Ind. 2017, 49, 103–110. [Google Scholar] [CrossRef]
- Liu, H.; Yu, Z.H.; Chen, C.; Hong, R.; Jin, K.; Yang, C. Visualization and bibliometric analysis of research trends on human fatigue assessment. J. Med. Syst. 2018, 42, 179. [Google Scholar] [CrossRef]
- Wang, H.; Liu, H.; Yao, J.Y.; Ye, D.; Lang, Z.H.; Glowacz, A. Mapping the knowledge domains of new energy vehicle safety: Informetrics analysis-based studies. J. Energy Storage 2021, 35, 102275. [Google Scholar] [CrossRef]
- Small, H. Co-citation in the scientific literature: A new measure of the relationship between two documents. J. Am. Soc. Inf. Sci. Tec. 1973, 24, 265–269. [Google Scholar] [CrossRef]
- Chen, C.; Li, C.J.; Reniers, G.; Yang, F.Q. Safety and security of oil and gas pipeline transportation: A systematic analysis of research trends and future needs using wos. J. Clean. Prod. 2021, 279, 123583. [Google Scholar] [CrossRef]
- Lang, Z.H.; Wang, D.G.; Liu, H.; Gou, X.Q. Mapping the knowledge domains of research on corrosion of petrochemical equipment: An informetrics analysis-based study. Eng. Fail. Anal. 2021, 129, 105716. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of things (iot): A vision, architectural elements, and future directions. Futur. Gener. Comp. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Albino, V.; Berardi, U.; Dangelico, R.M. Smart cities: Definitions, dimensions, performance, and initiatives. J. Urban. Technol. 2015, 22, 3–21. [Google Scholar] [CrossRef]
- Neirotti, P.; De Marco, A.; Cagliano, A.C.; Mangano, G.; Scorrano, F. Current trends in smart city initiatives: Some stylised facts. Cities 2014, 38, 25–36. [Google Scholar] [CrossRef]
- Lipper, L.; Thornton, P.; Campbell, B.M.; Baedeker, T.; Braimoh, A.; Bwalya, M.; Caron, P.; Cattaneo, A.; Garrity, D.; Henry, K.; et al. Climate-smart agriculture for food security. Nat. Clim. Chang. 2014, 4, 1068–1072. [Google Scholar] [CrossRef]
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Fagnant, D.J.; Kockelman, K. Preparing a nation for autonomous vehicles: Opportunities, barriers and policy recommendations. Transp. Res. Pt. A-Policy Pract. 2015, 77, 167–181. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. Iot security: Review, blockchain solutions, and open challenges. Futur. Gener. Comp. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Balta-Ozkan, N.; Davidson, R.; Bicket, M.; Whitmarsh, L. Social barriers to the adoption of smart homes. Energy Policy 2013, 63, 363–374. [Google Scholar] [CrossRef]
- Pop, C.; Cioara, T.; Antal, M.; Anghel, I.; Salomie, I.; Bertoncini, M. Blockchain based decentralized management of demand response programs in smart energy grids. Sensors 2018, 18, 162. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Patsakis, C. A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telemat. Inform. 2019, 36, 55–81. [Google Scholar] [CrossRef]
- Aitzhan, N.Z.; Svetinovic, D. Security and privacy in decentralized energy trading through multi-signatures, blockchain and anonymous messaging streams. IEEE Trans. Dependable Secur. Comput. 2018, 15, 840–852. [Google Scholar] [CrossRef]
- Andoni, M.; Robu, V.; Flynn, D.; Abram, S.; Geach, D.; Jenkins, D.; McCallum, P.; Peacock, A. Blockchain technology in the energy sector: A systematic review of challenges and opportunities. Renew. Sust. Energ. Rev. 2019, 100, 143–174. [Google Scholar] [CrossRef]
- Bhutta, M.N.M.; Khwaja, A.A.; Nadeem, A.; Ahmad, H.F.; Khan, M.K.; Hanif, M.A.; Song, H.B.; Alshamari, M.; Cao, Y. A survey on blockchain technology: Evolution, architecture and security. IEEE Access 2021, 9, 61048–61073. [Google Scholar] [CrossRef]
- Xie, J.F.; Tang, H.E.; Huang, T.; Yu, F.R.; Xie, R.C.; Liu, J.; Liu, Y.J. A survey of blockchain technology applied to smart cities: Research issues and challenges. IEEE Commun. Surv. Tutor. 2019, 21, 2794–2830. [Google Scholar] [CrossRef]
- Hu, Q.W.; Dai, Y.Y.; Li, S.; Jiang, T. Enhancing Account Privacy in Blockchain-Based IoT Access Control via Zero Knowledge Proof. IEEE Netw. 2023, 37, 117–123. [Google Scholar] [CrossRef]
- Roman, R.; Zhou, J.Y.; Lopez, J. On the features and challenges of security and privacy in distributed internet of things. Comput. Netw. 2013, 57, 2266–2279. [Google Scholar] [CrossRef]
- Xu, L.D.; He, W.; Li, S.C. Internet of things in industries: A survey. IEEE Trans. Ind. Inform. 2014, 10, 2233–2243. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in internet of things: The road ahead. Comput. Netw. 2015, 76, 146–164. [Google Scholar] [CrossRef]
- Li, X.; Xuan, Z.; Wen, L. Research on the Architecture of Trusted Security System Based on the Internet of Things. IEEE 2011, 2, 1171–1175. [Google Scholar] [CrossRef]
- Zanella, A.; Bui, N.; Castellani, A.; Vangelista, L.; Zorzi, M. Internet of things for smart cities. IEEE Internet Things J. 2014, 1, 22–32. [Google Scholar] [CrossRef]
- Zheng, X.; Cai, Z.P.; Li, Y.S. Data linkage in smart internet of things systems: A consideration from a privacy perspective. IEEE Commun. Mag. 2018, 56, 55–61. [Google Scholar] [CrossRef]
- Hu, Q.W.; Zheng, G.P.; Jiang, T. Joint Content and Radio Access for the Internet of Things: A Smart-Contract-Based Trusted Framework. IEEE Internet Things J. 2022, 9, 18142–18152. [Google Scholar] [CrossRef]
- Allam, Z.; Dhunny, Z.A. On big data, artificial intelligence and smart cities. Cities 2019, 89, 80–91. [Google Scholar] [CrossRef]
- Braun, T.; Fung, B.C.M.; Iqbal, F.; Shah, B. Security and privacy challenges in smart cities. Sust. Cities Soc. 2018, 39, 499–507. [Google Scholar] [CrossRef]
- Zhang, K.; Ni, J.B.; Yang, K.; Liang, X.H.; Ren, J.; Shen, X.M. Security and privacy in smart city applications: Challenges and solutions. IEEE Commun. Mag. 2017, 55, 122–129. [Google Scholar] [CrossRef]
- Silva, B.N.; Khan, M.; Han, K. Towards sustainable smart cities: A review of trends, architectures, components, and open challenges in smart cities. Sust. Cities Soc. 2018, 38, 697–713. [Google Scholar] [CrossRef]
- Abbas, K.; Tawalbeh, L.A.; Rafiq, A.; Muthanna, A.; Elgendy, I.A.; Abd El-Latif, A.A. Convergence of blockchain and iot for secure transportation systems in smart cities. Secur. Commun. Netw. 2021, 2021, 5597679. [Google Scholar] [CrossRef]
- Marikyan, D.; Papagiannidis, S.; Alamanos, E. A systematic review of the smart home literature: A user perspective. Technol. Forecast. Soc. Chang. 2019, 138, 139–154. [Google Scholar] [CrossRef]
- Solaimani, S.; Keijzer-Broers, W.; Bouwman, H. What we do—And don’t—Know about the smart home: An analysis of the smart home literature. Indoor Built Environ. 2015, 24, 370–383. [Google Scholar] [CrossRef]
- Stojkoska, B.L.R.; Trivodaliev, K.V. A review of internet of things for smart home: Challenges and solutions. J. Clean. Prod. 2017, 140, 1454–1464. [Google Scholar] [CrossRef]
- Hu, H.K.; Xue, W.D.; Jiang, P.; Li, Y. Polyimide-based materials for lithium-ion battery separator applications: A bibliometric study. Int. J. Polym. Sci. 2022, 2022, 6740710. [Google Scholar] [CrossRef]
- Xie, K.F.; Yu, S.C.; Wang, P.; Chen, P. Polyethylene terephthalate-based materials for lithium-ion battery separator applications: A review based on knowledge domain analysis. Int. J. Polym. Sci. 2021, 2021, 6694105. [Google Scholar] [CrossRef]
- Sabe, M.; Chen, C.M.; Sentissi, O.; Deenik, J.; Vancampfort, D.; Firth, J.; Smith, L.; Stubbs, B.; Rosenbaum, S.; Schuch, F.B.; et al. Thirty years of research on physical activity, mental health, and wellbeing: A scientometric analysis of hotspots and trends. Front. Public Health 2022, 10, 943435. [Google Scholar] [CrossRef] [PubMed]
- Jing, Q.; Vasilakos, A.V.; Wan, J.F.; Lu, J.W.; Qiu, D.C. Security of the internet of things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Granjal, J.; Monteiro, E.; Silva, J.S. Security for the internet of things: A survey of existing protocols and open research issues. IEEE Commun. Surv. Tutor. 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Roman, R.; Alcaraz, C.; Lopez, J.; Sklavos, N. Key management systems for sensor networks in the context of the internet of things. Comput. Electr. Eng. 2011, 37, 147–159. [Google Scholar] [CrossRef]
- Hoffmann, L.; Diffie, W.; Hellman, M. Finding new directions in cryptography. Commun. ACM 2016, 59, 112-111. [Google Scholar] [CrossRef]
- Faisal, M.; Ali, I.; Khan, M.S.; Kim, J.; Kim, S.M. Cyber security and key management issues for internet of things: Techniques, requirements, and challenges. Complexity 2020, 2020, 6619498. [Google Scholar] [CrossRef]
- Feng, S.; Sun, H.W.; Yan, X.T.; Zhu, H.J.; Zou, Z.X.; Shen, S.Y.; Liu, H.X. Dense reinforcement learning for safety validation of autonomous vehicles. Nature 2023, 615, 620–627. [Google Scholar] [CrossRef] [PubMed]
- Lian, Y.Q.; Zhang, G.Q.; Lee, J.; Huang, H.L. Review on big data applications in safety research of intelligent transportation systems and connected/automated vehicles. Accid. Anal. Prev. 2020, 146, 105711. [Google Scholar] [CrossRef]
- Kaffash, S.; Nguyen, A.T.; Zhu, J. Big data algorithms and applications in intelligent transportation system: A review and bibliometric analysis. Int. J. Prod. Econ. 2021, 231, 107868. [Google Scholar] [CrossRef]
- Zhu, L.; Yu, F.R.; Wang, Y.G.; Ning, B.; Tang, T. Big data analytics in intelligent transportation systems: A survey. IEEE Trans. Intell. Transp. Syst. 2019, 20, 383–398. [Google Scholar] [CrossRef]
- Sun, X.Q.; Yu, F.R.; Zhang, P. A survey on cyber-security of connected and autonomous vehicles (cavs). IEEE Trans. Intell. Transp. Syst. 2022, 23, 6240–6259. [Google Scholar] [CrossRef]
- Cui, J.; Liew, L.S.; Sabaliauskaite, G.; Zhou, F.J. A review on safety failures, security attacks, and available countermeasures for autonomous vehicles. Ad Hoc Netw. 2019, 90, 101823. [Google Scholar] [CrossRef]
- Khan, F.; Kumar, R.L.; Kadry, S.; Meqdad, M.N.; Nam, Y. Autonomous vehicles: A study of implementation and security. Int. J. Electr. Comput. 2021, 11, 3013–3021. [Google Scholar] [CrossRef]
- Berrada, J.; Mouhoubi, I.; Christoforou, Z. Factors of successful implementation and diffusion of services based on autonomous vehicles: Users’ acceptance and operators’ profitability. Res. Transp. Econ. 2020, 83, 100902. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, L.; Huang, Y.J.; Zhao, J. Safety of Autonomous Vehicles. J. Adv. Transp. 2020, 2020, 13. [Google Scholar] [CrossRef]
- Tu, H.Z.; Wang, M.; Li, H.; Sun, L.J. Safety risk assessment for autonomous vehicle road testing. Traffic Inj. Prev. 2023, 24, 652–661. [Google Scholar] [CrossRef] [PubMed]
- Gungor, V.C.; Sahin, D.; Kocak, T.; Ergut, S.; Buccella, C.; Cecati, C.; Hancke, G.P. A survey on smart grid potential applications and communication requirements. IEEE Trans. Ind. Inform. 2013, 9, 28–42. [Google Scholar] [CrossRef]
- Hossain, M.S.; Madlool, N.A.; Rahim, N.A.; Selvaraj, J.; Pandey, A.K.; Khan, A.F. Role of smart grid in renewable energy: An overview. Renew. Sust. Energ. Rev. 2016, 60, 1168–1184. [Google Scholar] [CrossRef]
- Aloul, F.; Al-Ali, A.R.; Al-Dalky, R.; Al-Mardini, M.; El-Hajj, W. Smart grid security: Threats, vulnerabilities and solutions. Int. J. Smart Grid Clean. Energy 2012, 1, 1–6. [Google Scholar] [CrossRef]
- Metke, A.R.; Ekl, R.L. Security technology for smart grid networks. IEEE T Smart Grid 2010, 1, 99–107. [Google Scholar] [CrossRef]
- Wang, W.Y.; Lu, Z. Cyber security in the smart grid: Survey and challenges. Comput. Netw. 2013, 57, 1344–1371. [Google Scholar] [CrossRef]
- Aggarwal, S.; Kumar, N.; Tanwar, S.; Alazab, M. A survey on energy trading in the smart grid: Taxonomy, research challenges and solutions. IEEE Access 2021, 9, 116231–116253. [Google Scholar] [CrossRef]





| NO. | Type of Literature | Total Publications | Percentage/% |
|---|---|---|---|
| 1 | Article | 1157 | 82.64 |
| 2 | Review | 212 | 15.14 |
| 3 | Early Access | 16 | 1.14 |
| 4 | Others | 15 | 1.07 |
| Rank | Country | Quantity | Percentage/% | SOTC | Total Link Strength |
|---|---|---|---|---|---|
| 1 | China | 401 | 28.64 | 7362 | 219 |
| 2 | USA | 201 | 14.36 | 6185 | 196 |
| 3 | UK | 120 | 8.57 | 5884 | 147 |
| 4 | South Korea | 114 | 8.14 | 2601 | 90 |
| 5 | India | 101 | 7.21 | 2471 | 139 |
| 6 | Saudi Arabia | 100 | 7.14 | 1473 | 157 |
| 7 | Australia | 98 | 7.00 | 3604 | 118 |
| 8 | Italy | 94 | 6.71 | 2033 | 75 |
| 9 | Paskistan | 66 | 4.71 | 1111 | 122 |
| 10 | Spain | 55 | 3.93 | 1358 | 66 |
| Rank | Institution | Country | Quantity | ACI | Total Link Strength |
|---|---|---|---|---|---|
| 1 | King Saud University | Saudi Arabia | 21 | 10.24 | 17 |
| 2 | The Hong Kong Polytechnic University | China | 19 | 27.58 | 16 |
| 3 | Tongji University | China | 18 | 16.89 | 8 |
| 4 | Tsinghua University | China | 18 | 42.17 | 2 |
| 5 | Southeast University | China | 16 | 16.69 | 2 |
| 6 | Princess Nourah Bint Abdulrahman University | Saudi Arabia | 14 | 4.36 | 18 |
| 7 | Queensland University of Technology | Australia | 14 | 47.29 | 6 |
| 8 | Delft University of Technology | Netherlands | 14 | 36.86 | 4 |
| 9 | Islamabad University of Communications | Pakistan | 11 | 25.73 | 8 |
| 10 | King Abdulaziz University | Saudi Arabia | 11 | 23.27 | 7 |
| Rank | Author | Country | Institute | Quantities | ACI | Links |
|---|---|---|---|---|---|---|
| 1 | Li Heng | China | Tongji University | 7 | 32.29 | 4 |
| 2 | Yigitcanlar Tan | Australia | Queensland University of Technology | 6 | 58.17 | 4 |
| 3 | Huh Jun-Ho | South Korea | Korea Maritime and Ocean University | 5 | 14.2 | 4 |
| 4 | Liu Yang | China | Tsinghua University | 5 | 2.2 | 3 |
| 5 | Azadeh A | Iran | College of Engineering University of Tehran | 5 | 13.4 | 0 |
| 6 | Park Jong Hyuk | South Korea | Seoul National University of Science and Technology | 5 | 14 | 0 |
| 7 | Almongren Ahmad | Saudi Arabia | King Saud University | 4 | 13 | 8 |
| 8 | Shah Munam Ali | Pakistan | Comsats University Islamabad | 4 | 18 | 7 |
| 9 | Yu. Yamtao | China | The Hong Kong Polytechnic University | 4 | 26.75 | 4 |
| 10 | Buller David B. | America | The Hong Kong Polytechnic University | 4 | 12.75 | 6 |
| Rank | Journal Title | Quantity | ACI | Impact Factor (2022) |
|---|---|---|---|---|
| 1 | Sustainability | 551 | 11.76 | 3.9 |
| 2 | International Journal of Environmental Research and Public Health | 66 | 12.36 | 4.614 |
| 3 | Energies | 37 | 37.19 | 3.2 |
| 4 | Applied Sciences | 34 | 17.41 | 2.7 |
| 5 | IEEE Transactions on Intelligent Transportation Systems | 29 | 34.66 | 9.55 |
| 6 | International Journal of Human–Computer Interaction | 25 | 16.12 | 4.7 |
| 7 | Systems | 22 | 3.23 | 1.9 |
| 8 | Sustainable Cities and Society | 19 | 63 | 11.7 |
| 9 | Renewable and Sustainable Energy Reviews | 19 | 93.47 | 15.9 |
| 10 | Energy Research and Social Science | 18 | 30.89 | 8.514 |
| Rank | Source | SOTC | Total Link Strength |
|---|---|---|---|
| 1 | Sustainability | 1415 | 34,768 |
| 2 | IEEE Access | 1287 | 43,358 |
| 3 | Accident Analysis and Prevention | 924 | 19,580 |
| 4 | Sensors | 808 | 25,714 |
| 5 | Automation in Construction | 780 | 22,576 |
| 6 | Journal of Cleaner Production | 775 | 26,953 |
| 7 | Renewable and Sustainable Energy Reviews | 760 | 30,870 |
| 8 | IEEE Transactions on Intelligent Transportation Systems | 712 | 16,894 |
| 9 | Energy Policy | 638 | 19,461 |
| 10 | Safety Science | 578 | 16,750 |
| NO. | Title | Journal | Author | Year | IN | CN | Cations |
|---|---|---|---|---|---|---|---|
| 1 | Internet of Things (IoT): a vision, architectural elements, and future directions | Future Generation Computer Systems—The International Journal of Escience | Gubbi, J et al. [29] | 2013 | 1 | 1 | 33 |
| 2 | Climate-smart agriculture for food security | Chemical Engineering Journal | lipper L et al. [32] | 2014 | 18 | 11 | 32 |
| 3 | Blockchains and smart contracts for the internet of things | IEEE Access | Christidis, K et al. [33] | 2016 | 1 | 1 | 27 |
| 4 | Smart cities: definitions, dimensions, performance, and initiatives | Journal of Urban Technology | Albino, V et al. [30] | 2015 | 3 | 2 | 23 |
| 5 | Preparing a nation for autonomous vehicles: opportunities, barriers and policy recommendations | Transportation Research Part A: Policy and Practice | Fagnant, DJ et al. [34] | 2015 | 2 | 1 | 23 |
| 6 | Current trends in smart city initiatives: some stylised facts | Cities | Neirotti, P et al. [31] | 2014 | 1 | 1 | 22 |
| 7 | Iot security: review, blockchain solutions, and open challenges | Future Generation Computer Systems | Khan, MA et al. [35] | 2018 | 2 | 2 | 22 |
| 8 | Social barriers to the adoption of smart homes | Energy Policy | Balta-Ozkan, N et al. [36] | 2013 | 9 | 2 | 21 |
| 9 | Blockchain based decentralized management of demand response programs in smart energy grids | Sensors | Pop, C et al. [37] | 2018 | 2 | 2 | 18 |
| 10 | A systematic literature review of blockchain-based applications: current status, classification and open issues | Telematics and Informatics | Casino, F et al. [38] | 2019 | 6 | 1 | 18 |
| Rank | Keywords | Occurrences | Centrality |
|---|---|---|---|
| 1 | Safety | 208 | 0.74 |
| 2 | System | 208 | 0.20 |
| 3 | Internet | 191 | 0.73 |
| 4 | Smart city | 140 | 0.22 |
| 5 | Management | 137 | 0.13 |
| 6 | Model | 136 | 0.37 |
| 7 | Technology | 128 | 0.32 |
| 8 | Challenges | 99 | 0.16 |
| 9 | Framework | 88 | 0.07 |
| 10 | Big data | 75 | 0.23 |
| Rank | Keywords | Begin | End | Strength | Year |
|---|---|---|---|---|---|
| 1 | Smart grid | 2016 | 2018 | 7.77 | 2016 |
| 2 | Climate change | 2016 | 2019 | 6.46 | 2016 |
| 3 | Renewable energy | 2017 | 2019 | 6.27 | 2017 |
| 4 | Risk | 2014 | 2017 | 5.89 | 2014 |
| 5 | Road safety | 2014 | 2020 | 5.25 | 2014 |
| 6 | Networks | 2017 | 2018 | 4.87 | 2017 |
| 7 | Intelligent transportation systems | 2015 | 2020 | 4.39 | 2015 |
| 8 | Communication | 2019 | 2020 | 4.28 | 2019 |
| 9 | Management | 2017 | 2018 | 4.1 | 2017 |
| 10 | Systerm | 2016 | 2017 | 3.32 | 2016 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mei, T.; Liu, H.; Tong, B.; Tong, C.; Zhu, J.; Wang, Y.; Kou, M. Exploring Knowledge Domain of Intelligent Safety and Security Studies by Bibliometric Analysis. Sustainability 2025, 17, 1475. https://doi.org/10.3390/su17041475
Mei T, Liu H, Tong B, Tong C, Zhu J, Wang Y, Kou M. Exploring Knowledge Domain of Intelligent Safety and Security Studies by Bibliometric Analysis. Sustainability. 2025; 17(4):1475. https://doi.org/10.3390/su17041475
Chicago/Turabian StyleMei, Ting, Hui Liu, Bingrui Tong, Chaozhen Tong, Junjie Zhu, Yuxuan Wang, and Mengyao Kou. 2025. "Exploring Knowledge Domain of Intelligent Safety and Security Studies by Bibliometric Analysis" Sustainability 17, no. 4: 1475. https://doi.org/10.3390/su17041475
APA StyleMei, T., Liu, H., Tong, B., Tong, C., Zhu, J., Wang, Y., & Kou, M. (2025). Exploring Knowledge Domain of Intelligent Safety and Security Studies by Bibliometric Analysis. Sustainability, 17(4), 1475. https://doi.org/10.3390/su17041475







