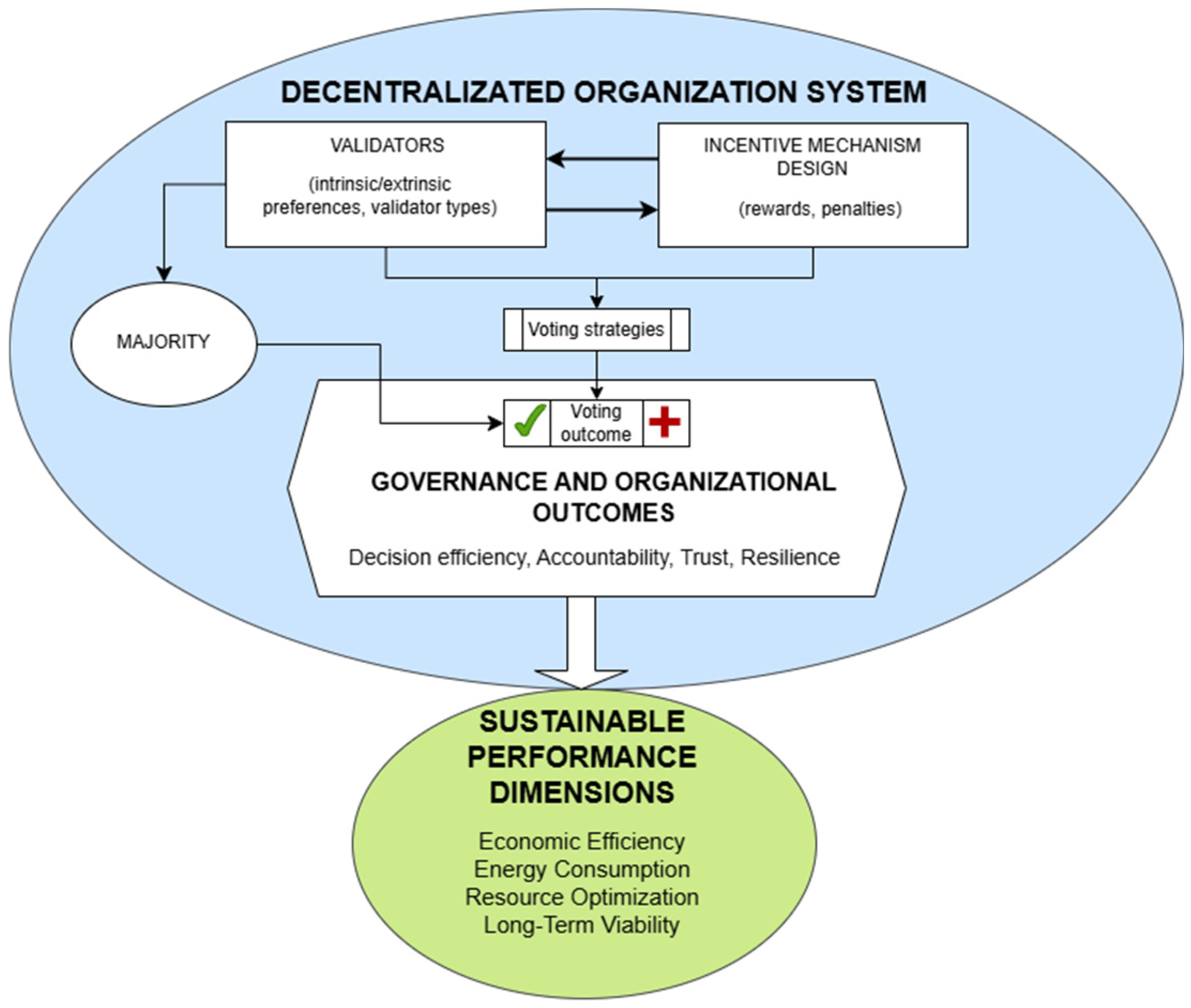
When coming to a non-crypto blockchain, the binary choice may be a true/false alternative. Consider the use of non-cryptocurrency blockchains for certifying competencies, property rights, or other individual characteristics. Agents acting as faulty or malicious nodes may obtain private gains by certifying false information. Consequently, the malicious agent may be externally incentivized to certify features that are not true and to broadcast messages that differ from the ones received. This is an opportunist behavior, adopted by a self-interested validator. In contrast, the honest node always broadcasts the message received. In what follows, it will be assumed that honest and malicious nodes (agents) have different utility functions. Different incentive compatibility constraints and the dominant strategies (when they exist) for each type of agent will be consequently derived. The objective is to show how an optimal reward scheme can be designed. This could be a prominent feature to ensure a reliable application of blockchain technologies for commercial, institutional, and industrial uses.
4.1. Theoretical Model
The base model considers a blockchain with
n = 3
k + 1 validators. The PBFT protocol assumes that a block is accepted if at least 2
k + 1 validators agree on its acceptance. Each validator
i agrees upon the block acceptance through a
vi vote (
i = 1, …,
n), which can take two values:
The block is accepted if . The block is rejected if .
This scenario is a simple representation of a PBFT protocol, where validators receive a block proposal message
M = (
x,
y), where x is the content and y is the result of the voting process on the message. In detail:
In the blockchain validation process, validators may receive a positive reward (wi > 0).
The following behavioral hypotheses will be adopted:
H1. Validators can read the message and comprehend whether it is either valid or invalid.
H2. Honest validators gain increasing utility from the acceptance of valid blocks and the rejection of false blocks (with the same satisfaction gain). Faulty validators gain increasing utility from the acceptance of invalid blocks and the rejection of valid blocks (with the same satisfaction gain).
H3. Both types of validators have increasing utility in positive wi.
The utility functions of the faulty (F) and honest (H) agents, as
can be accordingly described in their functional forms.
Accordingly, honest validators gain increasing utility both from the acceptance of valid blocks and from the rejection of false ones. This represents the intrinsic satisfaction derived from contributing to the proper functioning of the blockchain or the involvement in community [
41]. Faulty validators, by contrast, aim to accept invalid blocks and reject valid ones (H2); their intrinsic satisfaction is thus associated with the attempt to disrupt the system. In both cases, utility also increases with the extrinsic reward (H3).
To simplify the notations without losing generality, let a = denote the ratio between intrinsic and extrinsic marginal satisfaction for honest nodes, and let b = represent the corresponding ratio for faulty nodes.
Based on these behavioral assumptions, the analysis will compare two remuneration schemes to verify the final payoffs for both types of validators. The two schemes can be summarized as follows:
Scheme A. If the vote is vi = 1 and the block is accepted, the validator receives a positive wi. If the vote is vi = 0, no reward is provided.
Scheme B. If the vote is vi = 1 and the block is accepted, the validator receives a positive wi. If the vote is vi = 0, and the block is rejected, the validator receives a positive wi.
The difference between the two schemes lies in the treatment of rejection votes, which becomes critical in aligning individual incentives with collective objectives. By comparing payoffs (see
Table A1,
Table A2,
Table A3 and
Table A4 in the
Appendix A), it emerges that, in Scheme A, the agreement vote (
vi = 1) is a dominant strategy for both honest and faulty nodes since only validators who agree on the block are rewarded. In Scheme B, no dominant strategy emerges for either type of node.
Nevertheless, payoffs depend on the voting outcome. Validators make their choices based on whether the message content is valid or invalid, without knowing if it will ultimately be accepted. The final payoffs must be expressed as expected value, conditional on the probability of block acceptance or rejection.
To compute the expected results y
e, we assume expectations follow on the PBFT distribution between honest and faulty nodes. Recalling that the PBFT protocol assumes that 2
k + 1 validators are honest, the probability of block acceptance/rejection follows Equations (8) and (9).
Using these probabilities, the expected payoffs for the honest (EV
H) and faulty (EV
F) nodes in Scheme A can be computed (see Equations (A1)–(A4) in the
Appendix A).
By comparing the expected payoffs, it emerges that, for honest validators, vi = 1 is a dominant strategy when facing valid blocks. Conversely, for false blocks, vi = 0 becomes dominant only if . In this framework, rejection of false blocks depends on the validator’s preference for honest behavior and on the network size. The balance between intrinsic and extrinsic satisfaction is crucial in determining dominant strategies.
For faulty nodes, vi = 1 is a dominant strategy for false blocks, while, for valid block they vote vi = 0 if . Hence, even malicious behavior is influenced by the relative strength of intrinsic versus extrinsic satisfaction.
The expected payoffs for Scheme B are displayed in Equations (A5)–(A8) in the
Appendix A. This scheme awards both positive votes for accepted blocks and negative votes for rejected blocks. For honest nodes,
vi = 1 is a dominant strategy with valid blocks and
vi = 0 with false ones. Faulty nodes vote 0 for a valid block if
and
vi = 1 for false block if the same condition holds.
The honest validator is incentivized to behave correctly, as they will agree on the valid blocks and reject the false ones. On the other hand, the faulty nodes will be incentivized to behave maliciously only if their motivation is strong enough: that is, if .
Schemes A and B are compared in
Table 1, where the dominant strategies for each type of validator are displayed. Scheme B offers stronger incentives and is incentive-compatible for honest nodes, who have as dominant strategies both to accept valid blocks and reject false blocks. Scheme A is less reliable as it depends heavily on the intrinsic motivation of honest validators. At the same time, faulty nodes have a conditional dominant strategy under Scheme B for false blocks, which does not occur under Scheme A. The inclusion of extrinsic rewards in Scheme B reinforces the blockchain resistance to dishonest validation behavior.
4.2. Simulation Results
To assess the effectiveness of the proposed incentive schemes, some simulations were conducted under two main scenarios, defined by the relative weights of the coefficients a and b, and across four blockchain network sizes (n = 12, 120, 1200, and 12,000).
In the first scenario, the validators derive stronger intrinsic satisfaction from adhering to their individual objectives than from the extrinsic reward (labeled ‘Strong intrinsic satisfaction’ in
Table 2 and
Table 3). The second scenario assumes the opposite condition, where extrinsic satisfaction dominates (‘Weak intrinsic satisfaction’ in
Table 2 and
Table 3).
Additionally, two different voter compositions were tested.
Table 2 presents results assuming that two thirds of nodes are honest;
Table 3 considers a simple majority (one half plus one) of honest voters. For each configuration, the percentage of approval votes was recorded both for true and false blocks.
Comparing the results of Scheme A and Scheme B, both schemes clearly perform robustly when approving true blocks. When false blocks are proposed, however, Scheme A tends to approve them, whereas Scheme B consistently rejects them.
These outcomes highlight the greater robustness and reliability of Scheme B, particularly in maintaining consensus integrity against dishonest behaviors and suggest that the design of the reward mechanism plays a decisive role in sustaining the integrity and efficiency of decentralized systems. By ensuring that honest behavior is both individually rational and collectively beneficial, Scheme B provides a more sustainable equilibrium between autonomy and accountability within blockchain-based organizations. Moreover, the observed stability of the results across different network dimensions implies scalability, making the incentive structure potentially applicable to both small and large decentralized organizations, such as DAOs.