Abstract
This article proposes a scientifically grounded approach to risk assessment for infrastructural and functional systems that underpin the development of digitally transformed regional territories under conditions of high threat dynamics and sociotechnical instability. The core methodology is based on modeling of multifactorial threats through the application of fuzzy set theory and logic–linguistic analysis, enabling consideration of parameter uncertainty, fragmented expert input, and the lack of a unified risk landscape within complex infrastructure environments. A special emphasis is placed on components of technogenic, informational, and mobile infrastructure that ensure regional viability across planning, response, and recovery phases. The results confirm the relevance of the approach for assessing infrastructure resilience risks in regional spatial–functional systems, which demonstrates the potential integration into sustainable development strategies at the level of regional governance, cross-sectoral planning, and cultural reevaluation of the role of analytics as an ethically grounded practice for cultivating trust, transparency, and professional maturity.
1. Introduction
The challenges of sustainable development for smart regions require a rethinking of critical national infrastructure not only as a physical resource but also as the basis of digital sovereignty, regional resilience, and strategic trust. Smart regions are considered spatial–functional systems that integrate technological progress, environmental efficiency, and social integration. They need a reliable, adaptive, and cyber-resilient infrastructure that is capable of withstanding hybrid threats and protecting essential public services.
Critical infrastructure—including energy, communications, transportation, environmental, and informational systems—serves as a foundation for sustainable territorial development. Its cyber-resilience is not only a component of national security but also a prerequisite for achieving the UN Sustainable Development Goals, particularly Goal 9 (“Industry, Innovation, and Infrastructure”), Goal 11 (“Sustainable Cities and Communities”), Goal 13 (“Climate Action”), and Goal 16 (“Peace, Justice, and Strong Institutions”). This highlights the necessity for a comprehensive risk assessment approach that considers the functional, regulatory, and social interdependence of systems.
The multifaceted, adaptive, and dynamic nature of current threats demands models capable of operating with incomplete, contradictory, or ambiguous data. Fuzzy set theory and logical–linguistic modeling form the methodological foundation of this study. It allows the integration of expert judgement, linguistic rule sets, scenario variability, and structural–regulatory logic for management. These tools support the prioritization of threats and the development of adaptive solutions under conditions of uncertainty.
The study emphasizes mobile infrastructure components, particularly information-communication and technogenic systems that perform monitoring, logistics, ecological evaluation, and response functions. The integration of these elements into the broader architecture of risk management expands the spatial and functional boundaries of cyber-resilience, which is especially relevant for smart regions undergoing active reconstruction.
The aim of this work is to develop a fuzzy model for assessing risks to critical infrastructure within the sustainable development framework of smart regions. This model:
- Accommodates the multi-tier structure of technogenic, informational, and mobile components;
- Aligns with international standards and local governance contexts;
- Integrates indicators of infrastructural, social, and environmental resilience;
- Supports the development of ethically mature, strategically grounded, and culturally relevant analytics.
The research outcomes aim to enhance the capability of regional systems to adapt to emerging risks, build public trust in digital solutions, and ensure the sustainability of governance processes in complex spatial–social configurations.
2. State of the Art
The assessment of critical infrastructure risks under hybrid threat conditions is the subject of active interdisciplinary research. Several distinct directions have emerged in the literature that directly resonate with the topic of this paper: fuzzy risk management models, cyber-resilience of mobile and stationary infrastructure components, and the impact of digital security on the sustainability of territorial development.
A significant part of recent studies focuses on hybrid threats—both in the context of hybrid warfare and the perspective of risk management, response scenario development, and systems analysis. Works [1,2,3] explore approaches to threat identification, comparative evaluation methodologies, and administrative capacity building. Other authors [4,5] have proposed preventive frameworks to anticipate adversarial actions and enhance strategic resilience. The use of AI for cyber threat detection [6], game theory [7], and analysis of the role of intelligence and defense structures [8,9,10] demonstrates the inter-sectoral nature of the issue. Additional publications investigate administrative agency roles [11], regional actors [12,13,14,15], strategic communication, and the broader scientific role in countering hybrid threats [16,17].
Risk modeling increasingly leverages human-factor-based assessments [18,19], early warning scenarios [20,21], composite indicators [22], and classical management frameworks [23,24,25]. However, many of these models remain limited in addressing uncertainties, ambiguity, and subjective expert evaluations.
A growing interest surrounds fuzzy set theory (FST) applications in strategic planning, management, cognitive modeling [26,27,28,29,30,31], technical systems [32,33,34,35], and risk assessment [36,37,38,39,40,41], including hybrid FST–Monte Carlo methods [42], ontological uncertainty modeling [43], and dynamic system evaluation [44,45]. Studies such as [36,46,47,48] confirm the effectiveness of variable fuzzification in multidimensional risk analysis, strengthening system resilience to hybrid disruptions. Nevertheless, their use in civil critical infrastructure (CCI) systems remains fragmented and underdeveloped.
It is particularly important to highlight a set of studies addressing current challenges at the intersection of digital security and sustainable development. Specifically, recent analyses have examined the impact of cybersecurity measures in financial technology platforms on the sustainability of urban service systems [49], proposing the integration of risk management models into smart regional governance frameworks. Other research has focused on the protection of ADS-B data from unmanned aerial systems using spectral steganography [50], enabling consideration of mobile threat vectors within critical infrastructure architectures. Another contribution involves autonomous unmanned aerial vehicle (UAV) navigation, based on long short-term memory algorithms and reinforcement learning [51], directly linked to the implementation of Sustainable Development Goals, particularly Goals 9, 11, and 13. At the institutional level, the Organization for Economic Cooperation and Development (OECD) [52] provides frameworks for digital safety and instruments for resilient regional administration, which are especially pertinent to recovery and strategic modernization efforts.
Also promising are studies [53] that propose fuzzy risk assessment models for multifactor scenarios, utilizing geometric transformations and normalized indicators to enable comprehensive analytical architecture.
In summary, recent scientific literature demonstrates the following key trends:
- Expansion of the “critical infrastructure” concept to include mobile platforms for ecology, logistics, and finance.
- Institutionalization of cyber-resilience as a foundational element of sustainable development.
- Widespread application of fuzzy models as adaptive tools under uncertainty.
- Emergence of interdisciplinary approaches integrating engineering, economic, and legal dimensions of risk evaluation.
These findings form the conceptual and methodological foundation for the next stage: designing a fuzzy risk assessment framework that accounts for the structural, functional, and strategic role of critical infrastructure in the sustainable development of smart regions.
3. Materials and Methods
Systematic assessment of the risks of hybrid threats is a necessary prerequisite for ensuring the stability of the functioning of both individual information resources and state or critical systems in general. Successful integration of such an assessment into cybersecurity management processes allows the identification of threats, as well as the prevention of disruptions to the continuity of critical infrastructure operations in a timely manner. That is why this study proposes a method that ensures both the accuracy of the assessment and the determination of the impact on the stability of systems under the changing conditions of hybrid threats.
Based on the strategic analysis of hybrid threats performed in Ukraine in the civil security sector (CSS), an expert group developed a special questionnaire to assess the risk of threats related to the cybersecurity sphere in the state. Using the questionnaire, a survey of experts in the relevant subject area was completed to establish the values of the quantities “Possible consequences (Impact)” (PC) and “Probability (Assessment Level)” (L) of the occurrence of a hybrid threat [3]. The survey was completed with the participation of a certain number (SR) of expert respondents. To assess the corresponding hybrid threat, each expert (respondent) was offered a three-level scoring scale for L (15 points—high value, 10 points—medium value, 5 points—low value) and a four-level scale for PC (20 points—catastrophe, 15 points—critical condition, 10 points—severe condition, 5 points—minor consequences). In total, 298 respondents (SR = 298) were involved in the assessment process.
A risk assessment, taking into account the obtained judgments of each expert regarding the values of L and PC, is proposed to be carried out on the basis of a logical–linguistic approach using fuzzy set theory [3,36,46]. This allows consideration of the nature of expert assessment based on the judgments of specialists in the relevant subject area and makes it possible to reflect the characteristics of risk with extended indicators that allow determination of the affiliation of current data to a certain level. This, in contrast to the method based on average values [3], reduces the sensitivity to threshold values in the risk measurement scales and to the attribution of almost identical values, for example, 50% and 50.01% to different levels, due to the implementation of the fuzzification procedure. As a result, the application of urgent measures to reduce the risk of spreading threats according to certain indicators remains out of consideration. This approach makes it possible to perform rating, which ultimately will allow more effective allocation of resources to reduce risks, rather than directing core assets to one resource and ignoring another that is characterized by almost the same level.
The method is proposed for risk assessment, which consists of 9 stages: threat identification; expert threat assessment; interval fuzzification; expert judgment fuzzification; finding the average value; forming benchmarks for risk assessment; risk calculation; calculation of the generalized Hamming distance (GHD) [46]; determining the risk level; and interpreting the results.
3.1. Development Stages
Let us describe each stage in detail.
3.1.1. Stage 1—Threat Identification
Based on the strategic analysis in CSS, hybrid cybersecurity threats are identified, and a corresponding list is formed. An example of the implementation of this stage is given in Table 1, where the first column indicates the current number of the identified hybrid threat (, where is the number of threats), and the second column indicates its identifier.

Table 1.
Results of the analysis of hybrid threats (excerpt).
3.1.2. Stage 2—Expert Assessment of Threats
The assessment is carried out on the basis of a questionnaire of experts on the values of and for each hybrid threat identified a stage 1. An example of the implementation of this stage is given in Table 2, which shows the results of the assessment of the first threat (: Malware: “Virus”) by experts using a defined scoring scale for L and PC.

Table 2.
Example of survey results for threat 1: Malware: “Virus”.
3.1.3. Stage 3—Interval Fuzzification
The practice of solving problems in the field of information and cybersecurity [47,48] has shown that for processing expert data, it is the most effective to use fuzzy set theory. In this regard, linguistic variables (LV) “LIKELIHOOD” (L) and “CONSEQUENCES” (PC) are introduced, which are represented by the tuple [36] <L, L, XL> and <PC, PC, XPC>, where the basic term-sets are defined by and terms, respectively.
and
where is the threat number and is the respondent number.
Taking into account the intervals determined (for L and PC) based on the fuzzification method [47], the set of values of the LV L and PC at and , respectively, for trapezoidal LR numbers is formed:
and
Taking into account (3) and (4), Formulas (1) and (2) are written in the following form:
} = {{0/0; 1/0; 1/3.6; 0/6.9}, {0/3.6; 1/6.9; 1/9.9; 0/12.6}, {0/9.9; 1/12.6; 1/15; 0/15}} = {(0; 0; 3.6; 6.9)LR, (3.6; 6.9; 9.9; 12.6)LR, (9.9; 12.6; 15; 15)LR};
{ } = {{0/0; 1/0; 1/3.43; 0/6.57}, {0/3.43; 1/6.57; 1/9.43; 0/12.29}, {0/9.43; 1/12.29; 1/15.14; 0/17.71}, {0/15.14; 1/17.71; 1/20; 0/20}} = {(0; 0; 3.43; 6.57)LR, (3.43; 6.57; 9.43; 12.29)LR, (9.43; 12.29; 15.14; 17.71)LR, (15.14; 17.71; 20; 20)LR}, where and are the term-sets for L and PC, respectively. and denote their fuzzy numbers (FNs), and , .
The graphical interpretation of the fuzzy numbers L and PC formed on the basis of (5) and (6) is given in Figure 1 and Figure 2, respectively.
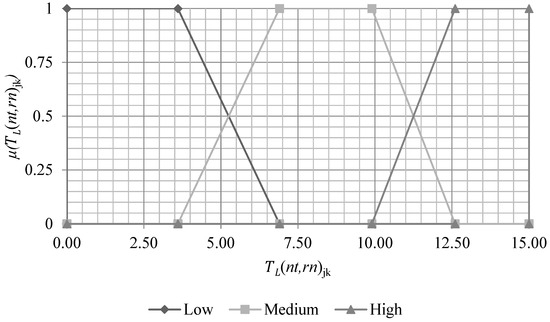
Figure 1.
Value terms for LV L.
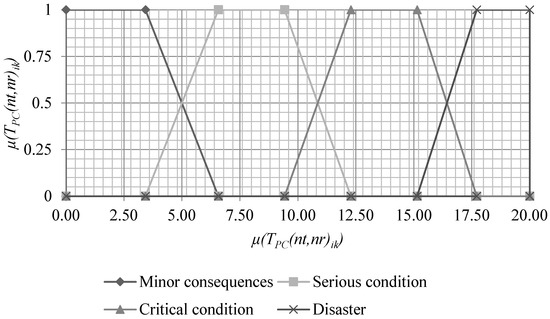
Figure 2.
Value terms for LV PC.
3.1.4. Stage 4—Expert Judgment Fuzzification
Taking into account [47], the fuzzification is implemented using the FNs obtained at stage 3. An example of the implementation of this stage is given in Table 3, where each interval corresponds to its FN determined at stage 4.

Table 3.
The result of the fuzzification of expert judgments for the first threat (): Malware: “Virus”.
3.1.5. Stage 5—Finding the Average Value
Using the linear approximation method by local maxima (LALM) [46], we find the average values of the survey results for the threat using the following formulas:
where , , is the sign of the fuzzy sum operation, is the respondent number, is the threat number, is the number of respondents, is the number of threats, and and are the average values of the FNs for L and PC, respectively.
Therefore, for example, for trapezoidal LR numbers, taking into account (3) ÷ (6) at and , Formulas (7) and (8) take the following form:
( … /298 = {0/6.8; 1/11.5; 1/12.2; 0/13.4} = (6.8; 11.5; 12.2; 13.4)LR,
( … /298 = {0/6.66; 1/11.66; 1/12.11; 0/14.49} = (6.66; 11.66; 12.11; 14.49)LR.
By analogy, using Formulas (9) and (10), the average values of the FNs and of the LV L and PC for all identified threats are calculated. The results are listed in Table 4.

Table 4.
Average values of FNs and and for all identified threats.
3.1.6. Stage 6—Forming the Benchmarks for Risk Assessment
The construction of the necessary standards was implemented on the basis of the introduced LV “RISK LEVEL” (RL), which is defined as a tuple [3, 36] <RL, , XRL>, where the basic term-set is formed on the basis of terms, for each of which
(,—the number of terms), accordingly, its intervals of values are formed, which lie within the limits and are denoted as . For example, for , the following intervals were defined for RL:
Further, using the interval transformation method [47], the corresponding mappings of the LV RL into the FNs are implemented (for), as a result of which the following term-values are obtained for trapezoidal LR numbers (see Figure 3), and, taking into account (5) and (6), Formula (11) takes the following form:
- {{ } = {{0/0; 1/0; 1/42.86; 0/85.71}, {0/42.86; 1/85.71; 1/128.57; 0/171.43}, {0/128.57; 1/174.43; 1/214.29; 0/257.14}, {0/214.29; 1/257.14; 1/300; 0/300}} = {(0; 0; 42.86; 85.71)LR, (42.86; 85.71; 128.57; 171.43)LR, (128.57; 174.43; 214.29; 257.14)LR, (214.29; 257.14; 300; 300)LR},
- where are term-sets of LV RL, and are values of their trapezoidal FNs (, ).
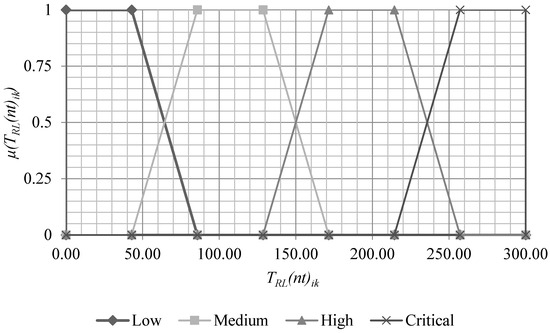
Figure 3.
Value terms for LV RL.
3.1.7. Stage 7—Risk Calculation
Since a risk in many standards and approaches is determined by the product of probability and possible consequences [54], on this basis, for example, using the LALM method [46], the risk calculation is implemented by multiplying the obtained FN values for and (see Table 4) using the following formula:
where , is the fuzzy multiplication sign, and ta are the average FN values for L and PC of the -th threat
Taking Formulas (7) and (8) into account, Expression (13) is presented as follows:
{ ; ; } { ; ; }.
So, for example, using (13) for the first threat (: Malware: “Virus”), = {0/6.8; 1/11.5; 1/12.2; 0/13.4} {0/6.66; 1/11.66; 1/12.11; 0/14.49} = {0/45.60; 1/139.73; 1/147.97; 0/194.75} = (45.60; 139.73; 147.97; 194.75)LR. The obtained results for are listed in Table 5.

Table 5.
Risk assessment results.
3.1.8. Stage 8—Calculation of the Generalized Hamming Distance
To determine the risk level for each threat, it is necessary to calculate the GHD [46] and compare the current results with their benchmarks formed at stage 6. To compare the indicated FNs, the GHD set is used:
where, for the -th threat, the minimum value of all
indicates the greatest proximity of the NF to the reference [46] (, where is the number of threats, and , where is the number of term-sets). So, for example, for and :
{399.47; 99.47; 243.38; 543.38}.
The obtained results for are listed in Table 6.

Table 6.
GHD calculation results.
3.1.9. Stage 9—Determining the Risk Level and Interpreting the Results
According to the properties of the method used in stage 8, and taking into account that the minimum of the values of indicates the greatest proximity of FN to the reference one, the minimum GHD of the values of , are calculated by Formula (14):
where = at .
Next, the basic pair of arguments and are formed to construct the associative rules necessary for determining risk, as follows:
which is closest to .
A normalizing coefficient is introduced regarding the belonging of the current value to the reference one, which is calculated using the following expression:
Next, indicators of the expert’s level of confidence regarding the belonging of current values to a certain level of risk are formed, which are calculated using the following expression:
For example, according to (14) for (: Malware: “Virus”):
= H 399.47 99.47 243.38 543.38 = 99.47, and , and according to (15):
then = .
Next, it is necessary to calculate the coefficient of belonging of the current value to the reference using Formula (16):
and according to (17), the indicator is formed:
Next, a template of rules is formed for interpreting the results: /; /), where is the risk level of the -th threat, are terms of values for LV . For this threat, at , = “Medium”, 0.71, = “High”, , the result is as follows:
The proposed nine-stage procedure for assessing hybrid threats formalizes the process of risk management under conditions of uncertainty. To enhance its cross-sector compatibility, it is advisable to show the correspondence of the stages of the method to the basic phases of risk management according to the international frameworks ISO 31000 and NIST CSF. Such correspondence demonstrates the applied integrativeness of the proposed approach in both the public and private regulatory environments.
Below is the summary table (see Table 7) showing the correspondence of the method stages to the ISO/NIST phases.

Table 7.
The correspondence of the method stages to the standard risk management phases.
The correspondence of individual stages to the procedures “Identify”, “Analyze”, “Respond”, etc., allows adapting the logic of risk assessment to existing frameworks without changing the mathematical basis of the method. This, in turn, paves the way for further integration into standardized cyber-resilience management models.
To enhance the comprehensiveness of the assessment, it is appropriate to incorporate additional parameters that combine the technical, regulatory, and social logic of cyber-resilience formation. The methodology of this study also includes the following:
- Analysis of mobile critical infrastructure, particularly systems based on unmanned aerial vehicles, which increasingly play a role in supporting civil safety, ecological monitoring, and crisis logistics. The risks associated with their deployment require dedicated modeling efforts that account for both physical threats and informational attacks.
In this context, the application of specialized risk management models focused on the dynamic behavior of mobile platforms in highly uncertain environments becomes especially relevant. UAV systems, as autonomous and remotely operated components of infrastructure, function at the intersection of several domains—aviation safety, telecommunications, navigation, sensor data acquisition, and algorithmic control. This necessitates the combination of techniques for assessing physical vulnerabilities (e.g., the impact of weather conditions, mechanical overloads, or loss of connectivity) with an analysis of cyber risks, including signal spoofing, command channel intrusion, falsification of navigational data, and algorithmic sabotage.
Within a fuzzy logic–linguistic framework, such risks can be represented through multidimensional evaluations characterized by high variability in input parameters, including a system’s adaptability to change, resilience against inaccurate or incomplete data, capacity for self-organization, and scenario-specific responsiveness. For instance, flight trajectory analysis in conjunction with GPS data loss assessment may serve as an indicator of technical cyber-resilience, while interaction with the smart region’s ecosystem reflects infrastructure-level integration.
Consequently, the analysis of mobile critical infrastructure requires a holistic approach that considers the hybrid nature of threats, which simultaneously encompass technical, informational, and societal dimensions of system functionality. This opens a pathway for designing specialized fuzzy risk scenarios that can be incorporated into the overarching cyber-resilience framework for smart regions.
- Integration with the Sustainable Development Goals (SDGs). Here, cyber-resilience is understood not merely as a technological attribute, but also as a determinant of social and ecological sustainability within regional systems. Particular emphasis is placed on Goals 9, 11, 16, and 17, which reinforce the interlinkages between infrastructure, governance, and partnership networks.
From this perspective, cyber-resilience analysis transcends technical audits and standard risk evaluations. It evolves into a strategic modeling tool for sustainable development, one that considers the interconnectedness of digital infrastructure, social cohesion, environmental stability, and institutional effectiveness.
Goal 9 (Industry, Innovation, and Infrastructure) supports the concept of digital infrastructure resilience, encompassing secure technologies not only for their ability to drive economic growth and service accessibility. Goal 11 (Sustainable Cities and Communities) calls for embedding cybersecurity into the management systems of urban critical infrastructure, especially amid hybrid threats and technological disruptions. Goal 16 (Peace, Justice, and Strong Institutions) emphasizes digital trust, personal data protection, and the role of analytics in enabling transparency, counteracting disinformation, and strengthening the rule of law. Goal 17 (Partnerships for the Goals) envisions cyber-resilience as a platform for multistakeholder collaboration across government, private, and civil sectors, including academic and technical communities.
This broadened analytical approach enables cyber-resilience to be viewed not as a reactionary function, but as a proactive regional capacity for adaptation, learning, innovation uptake, and ecosystem formation that is simultaneously technologically robust and socially inclusive. In turn, this reinforces the strategic foundations of digital sovereignty and creates a framework for “smart recovery” in post-crisis governance.
- Adaptation of international standards. This includes principles drawn from ISO/IEC 27005, NIST SP 800-30, and OECD guidance on public sector digital transformation. The methodology is localized, taking into account the specifics of the post-conflict period, the necessity of rebuilding institutional trust, and enhancing digital sovereignty.
Risk assessment and digital transformation based on adapted international standards become key instruments of strategic management, particularly in the context of comprehensive institutional recovery and reinforcement of digital autonomy. The localized context demands not mere implementation of global frameworks, but their deep transformation—aligned with local regulatory structures, resource limitations, digital ecosystem architecture, and societal expectations.
ISO/IEC 27005 offers a structured methodology for evaluating information security risks, which—in localized form—includes adjusting risk acceptance criteria to conditions of armed conflict and recovery, such as temporary access constraints, unstable supply chains, and the potential for technological innovation. NIST SP 800-30 underpins scenario-based risk modeling that accommodates not only conventional threats (external attacks, system vulnerabilities) but also emergent vectors such as fragmented digital services in disrupted regions. OECD guidelines on open governance, civic inclusion, and efficient digital public services are reframed within post-conflict recovery as a methodology for transparent community engagement in evaluating, monitoring, and reimagining institutional digital resilience.
This adaptation involves not only technical interpretation of standards but also their conceptual rethinking as part of a broader process of trust restoration, development of local competencies, and formulation of a strategic vision for digital sovereignty. The outcome is a flexible and contextually relevant analytical framework that can be scaled both to national policy and to regional implementation within the scope of smart recovery.
4. Results
According to the example, the final risk variant is interpreted by the associative rule as: “RISK LEVEL” of the threat implementation (: Malware: “Virus”) and is within the range between “Medium” with the expert confidence coefficient of 0.71 and “High” with the expert confidence coefficient of 0.29.
By analogy, rules have been calculated and formed for . For example, according to (14) for (: Malware: “Worm”): = H 346.88 60.11 295.98 595.98 = 60.11, and , and according to (15):
Next, using (16), the coefficient of belonging of the current value to the reference value has been calculated and according to (17) the indicator has been formed ta.
Further, to interpret the results, the has been formed. For this threat, at , = “Medium”, 0.83, = “High”, , the result is as follows: ) = IR .
Next, for (: Malware: “Ransomware”): = 338.52 53.39 304.34 604.34 = 53.39, = 2: = , and the coefficient of belonging of the current value to the reference is The indicator . Then at , = “Medium”, 0.85, = “High”, , the result is ) = IR
And for (: Malware: “Trojan”): = 130.59, = 2, then = . The coefficient of belonging of the current value to the reference is , and indicators are and . Then at , = “Medium”, 0.62, = “High”, , the result is ) = IR .
Figure 4 presents a graphical interpretation of the evaluation results for .
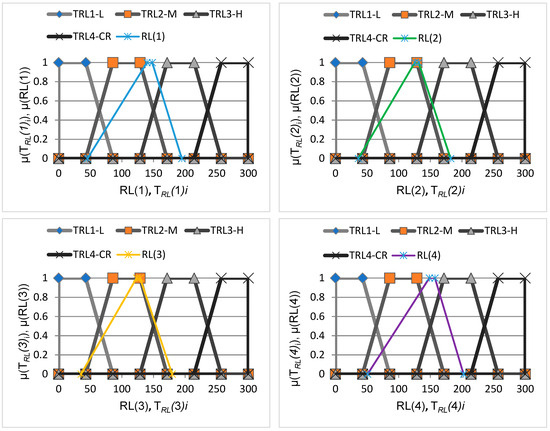
Figure 4.
Value terms for LV RL, where 1: L—risk level “Low”, 2: M—risk level “Medium”, 3: H—risk level “High”, 4: CR—risk level “Critical”, ÷ —risk levels obtained.
The proposed approach has applied significance not only for risk assessment but it can also directly affect their assessments the stability of the functioning of civil security systems. In particular, a clear ranking of hybrid cyber threats allows for timely identification of critical vulnerabilities, predicts the consequences of attacks, and ensures preventive strengthening of the critical infrastructure resilience. Due to the logical–linguistic approach and data fuzzification, the assessment system functions stably even under conditions of incomplete or contradictory data, which is key in crises. Thus, the proposed method directly contributes to reducing the risk of destabilization within the cyberspace of the state, which is one of the basic factors of its stable development.
Given the technical results obtained, it is relevant to expand the analytical framework for assessing the impact of decisions not only on security but also on the social and environmental parameters of sustainable development. The research results demonstrate that the implementation of fuzzy risk assessment models related to mobile components of critical infrastructure, in particular UAVs, enables effective identification of systemic vulnerabilities under conditions of limited information and dynamic threats.
These models can position their relevance in the context of the following:
- -
- Environmental monitoring (identification of potential zones of environmental degradation);
- -
- Safety of humanitarian aid operations (optimization of delivery routes and associated risks);
- -
- Information counteraction (identification of anomalies in UAV data flows).
Additional comparison of the results with relevant SDG indicators (Goals 9, 11, 16, and 17) allows for a broader evaluation of the proposed methodology’s impact on regional resilience, digital trust, and social integration. This points to the model’s potential use not only for security but also for strategic recovery planning.
At the same time, localized integration of international standards (ISO/NIST/OECD) ensures a high level of consistency between technical solutions and public expectations regarding resilience, trust, and transparency.
An important outcome of this approach is the possibility of implementing tangible measures based on the development of a structured roadmap for cyber-resilience implementation within the context of the state’s regional sustainable development strategies. It combines three key analytical frameworks (mobile infrastructure, SDGs, and standards) and transforms them into a logic of practical realization. This roadmap envisions a phased transformation of analytical approaches into practical management tools. Its structure is based on three key concepts: analysis of mobile critical infrastructure (in particular UAV systems), integration with Sustainable Development Goals (SDGs), and adaptation of international standards for risk assessment and digital transformation (ISO/IEC 27005, NIST SP 800-30, and OECD).
In the first phase, which lasts up to six months, strategic diagnostics are conducted. Focus is placed on identifying regional mobile infrastructure assets, analyzing their vulnerability to hybrid threats, and preliminary mapping of the digital capacity of territorial communities. In parallel, evaluation begins with compliance with international standards in the field of information security and the determination of relevant sustainable development benchmarks (particularly SDGs 9, 11, 16, and 17).
The second phase (6–12 months) involves localization of international standards according to the realities of the post-conflict period. This includes adapting risk criteria and scenario modeling to account for instability, fragmentation of digital services, and resource constraints. In addition to technical transformation of standards, digital indicators of social trust and environmental resilience are developed. A compatibility matrix between adapted standards and Sustainable Development Goals is formulated, laying the groundwork for integrated models of digital transformation.
The third phase (12–24 months) focuses on pilot implementation of regional cyber-resilience programs. Special attention is given to the creation of dashboards for risks and cyber incidents, the launch of educational campaigns on digital ethics, and the formation of cross-sectoral partnerships. Within this phase, program impact is verified through the system of SDG indicators, including infrastructure innovation (SDG 9), sustainability of urban governance (SDG 11), institutional transparency (SDG 16), and partnership effectiveness (SDG 17).
The fourth phase (24–36 months) involves interregional expansion of the developments and their integration into national frameworks for digital sovereignty. Cyber resilience is institutionalized as a component of regional sustainable development plans. An interregional platform is established for the exchange of risk models and innovations, and mechanisms are built for collaboration with international donors, analytical centers, and the academic community.
Overall, such a consistent roadmap structure allows not only for the integration of cyber-resilience concepts into sustainable development strategies but also for their adaptation to complex reality, forming the foundation for strategic modernization of public administration, infrastructure, and societal trust in the digital age.
5. Discussion
The work is devoted to the development of an approach to assessing the risks of hybrid threats in the civil security sector based on fuzzy set theory. This method consists of nine stages and takes into account the following aspects:
- Threat identification.
- Expert threat assessment.
- Fuzzification of intervals and expert judgments.
- Use of indicators of average values and benchmarks.
- Calculating risks and generalized Hamming distance.
This method allows taking into account the uncertainty and subjectivity of expert judgments, ensuring flexibility and adaptability in decision-making. This is especially important for systems that require stable and continuous operation even under conditions of external hybrid pressure.
The theoretical significance of this approach is that the approach demonstrates how the fuzzy set theory can be applied to the processing of weakly formalized, vaguely defined data in complex risk management systems. This makes it promising for research in areas where traditional approaches are ineffective. Thanks to the clearly defined nine stages, the process becomes not only understandable but also easily adaptable to different contexts, such as other aspects of hybrid threats (for example, information or physical security). The use of tools such as the generalized Hamming distance increases the accuracy of risk identification, reducing the risk of erroneous conclusions with minimal data discrepancies. This, in turn, allows maintaining the stability of the functioning of various systems, reducing the likelihood of failures or interruptions in critical processes.
The proposed assessment system has the potential to integrate with existing risk management frameworks such as ISO31000, NIST Cybersecurity Framework (CSF), and ENISA Risk Management Framework. Its logical–linguistic approach allows for the alignment of the identification, assessment, ranking, and response phases with risk management structures already in place in the public and private sectors. Such integration provides the dual effect of maintaining regulatory compliance and increasing assessment accuracy in conditions of data ambiguity.
The proposed stages form the basis for creating software that will significantly accelerate risk assessment, providing the ability to integrate with existing threat monitoring systems. In addition, this approach opens up opportunities for combination with artificial intelligence technologies (e.g., for risk forecasting) and Big Data to expand analytical potential. The mathematical structure of the method does not limit its application only to the Civil Security Sector. For example, in the financial sector, it is possible to classify hybrid threats as attacks on payment systems, cyber fraud, or data integrity violations. The linguistic variables “probability” and “consequences” retain semantic consistency, which allows for the formation of risk profiles similar to those described in the article, without changing the structure of the nine-stage assessment.
From a practical point of view, this method allows solving specific tasks of threat assessment and ranking, providing more informed decision-making on resource allocation and implementation of various preventive measures that will ensure the stability of critical infrastructures. This is of particular value for organizations that seek to maintain stable functioning even under complex hybrid influences. Using the method allows assessing critical threats (e.g., cyber espionage, data breach) and ensuring their ranking for priority response. This is key in preventing large-scale cyber incidents that can destabilize entire industries and negatively affect the sustainable development of the state.
The method allows you to adapt to the specific needs of organizations operating in different CSS. Its implementation contributes to increasing resilience to hybrid threats and ensuring the stability of key elements of the information infrastructure, which is a key aspect for modern cybersecurity of the state. For example, it can be used to protect critical infrastructure facilities, such as energy or financial systems. Taking into account a clear ranking of threats, it becomes possible to direct resources to handle the most significant risks, avoiding overspending on minor threats and at the same time maintaining the stability of the systems.
Moreover, the implementation of this approach is essential for increasing stability in the CSS. Clear structuring of risks and fuzzification mechanisms allows avoiding excessive dependence on individual sources of information, ensuring the stability of management decisions in conditions of limited time or data scarcity. The adaptability of the method to new threats contributes to the long-term stability of the functioning of critical infrastructure, which is especially important in conditions of hybrid aggression.
Thus, the method of assessing the risks of hybrid threats based on fuzzy set theory has significant theoretical and practical value as a tool for processing complex and uncertain data. It provides effective risk management in the face of modern challenges in the field of cybersecurity, especially for countries such as Ukraine, which are under the influence of multi-component hybrid threats. The implementation of this approach contributes to the creation of a more secure information space, reducing risks for both public and private structures.
In addition to technical efficiency, it is also relevant to comprehend the role of analytics in building trust, restoring regions, and shaping a culture of digital resilience.
The discussion of the research findings gains particular significance in the context where analytical tools perform technical and cultural–strategic functions. The fuzzy risk modeling related to mobile critical infrastructure and the integration of SDG indicators enables the formation of a new quality of managerial decisions based on flexibility, humanity, and evidence.
Analytics is regarded as an institutional practice that contributes to the following:
- the restoration of trust between citizens, the state, and technologies;
- the professionalization of cyber-resilience culture through coordinated actions, ethical transparency, and strategic thinking;
- the localization of global standards in a manner that preserves the dignity and autonomy of regions.
This shift toward analytics as a cultural process opens opportunities for transforming the role of a specialist from a technical executor to a strategic and trusted agent of change.
Such a rethinking of the methodology and results not only allows analytics to be seen as a response to threats but also as a proactive tool for shaping holistic regional policy based on principles of dignity, resilience, and social partnership.
6. Conclusions
According to the results obtained (see Table 1 and Table 6), the characteristic risk level of all the mentioned CSS hybrid threats in Ukraine is “Medium”. At the same time, taking into account the associative rules formed at stage 9 and the expert’s confidence coefficients, in order to more effectively use the necessary resources to ensure the appropriate level of cybersecurity in the state, the priority of cyber threats (using the example of the first four) was determined in terms of reducing their risk level: (1) : Malware: “Trojan”; (2) : Malware: “Virus”; (3) : Malware: “Worm”; (4) : Malware: “Ransomware”, since the values of their terms are closer to the “High” level with the expert confidence coefficients , , , and , respectively.
Thus, the method for assessing the level of risk has been developed, which, through the procedures of identifying threats, their expert assessment, forming linguistic variables, fuzzifying intervals and expert judgments, finding average values, forming standards, forming a set of characteristics of objects under review, the process of initial measurement, determining current values of the risk level, forming a generalized Hamming distance, and determining the risk level, which are formalized by the corresponding stages, allows implementing the process of assessing the level of cybersecurity risk of hybrid threats in the CSS of Ukraine and, based on the data obtained, rationally distributing the available resources to protect the critical infrastructure of the state.
Moreover, the implementation of this method contributes to increasing the stability of various systems, in particular the CSS, through timely response to priority threats, reducing the impact of uncertainty and enabling effective risk management. Adaptation to specific scenarios of hybrid aggression allows minimizing destabilizing effects, ensuring the stable functioning of state and infrastructure systems even in difficult security situations.
In the future, it is necessary to build an appropriate software system that will allow automating such an assessment process when forming a new survey or a list of new threats, as well as generating recommendations for rational resource allocation. The implementation of the proposed method also opens up the possibility of combining it with international risk assessment frameworks. For example, the calculated levels of hybrid impact risks can be used to form integrated cyber risk maps within the framework of ISO31000 or NIST CSF structures, including the “Protect” and “Respond” categories. This will not only contribute to the unification of approaches to risk management and ensure the stability of critical infrastructures at the cross-sectoral level, as well as reduce risks, but also generally increase the stability and reliability of the information environment in conditions of hybrid impact. It is advisable to use the proposed approach for regular monitoring of the stability of critical infrastructure facilities of the state as one of the tools for ensuring its sustainable development.
Moreover, it is advisable to expand the scope of the method to other segments of critical infrastructure, taking into account the specific threats of each sector. This will allow creating a universal platform for assessing the risks of hybrid impact with the ability to adapt to the requirements of a specific industry without the necessity to change the basic model.
According to the results obtained, the model demonstrates the potential for adaptation to various scenarios of digital risk management under conditions of uncertainty. The conclusions of this study go beyond purely technical analytics. They reveal the model’s potential as a tool for interdisciplinary transformation of practices in security, management, and sustainable development. The localized integration of international standards (ISO, NIST, OECD), taking into account challenges of digital sovereignty, post-conflict recovery, and institutional trust, enables the formation of a new culture of strategic analytics.
The ethical component of the model, particularly the emphasis on flexibility, transparency, and social responsibility, gives opportunities for building a professional community capable of acting not only as technical experts but also as strategic facilitators of change.
In the international context, the proposed solution demonstrates adaptability to polycentric scenarios of digital development, where cyber-resilience intersects with humanitarian security, environmental monitoring, and cultural integration of standards. The model is not only technically effective but also institutionally, strategically, and philosophically relevant.
Thus, analytics in this study is regarded as the fundamental component of modern governance that contributes to the construction of more dignified, mature, and resilient societies.
Author Contributions
Conceptualization, O.K. (Oleksandr Korystin); methodology, O.K. (Oleksandr Korystin), O.K. (Oleksandr Korchenko) and S.D.; software, V.S., S.K. and S.D.; validation, V.S., S.K., S.Z. and S.D.; formal analysis, O.K. (Oleksandr Korchenko), S.D. and S.K.; investigation, O.K. (Oleksandr Korchenko), S.D. and S.K.; resources, O.K. (Oleksandr Korchenko), V.S., S.D. and O.K. (Oleksandr Korystin); data curation, O.K. (Oleksandr Korystin), V.S. and S.K.; writing-original draft preparation, O.K. (Oleksandr Korchenko) and S.Z.; writing—review and editing, O.K. (Oleksandr Korystin) and S.Z.; visualization, O.K. (Oleksandr Korystin) and S.Z.; supervision, S.Z.; project administration, V.S. and S.K.; funding acquisition, O.K. (Oleksandr Korchenko), S.D. and O.K. (Oleksandr Korystin). All authors have read and agreed to the published version of the manuscript.
Funding
The funding for this study was provided by the research project of the University of the National Education Commission (Poland).
Informed Consent Statement
Informed consent was obtained from all subjects involved in the study.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors on request.
Acknowledgments
The authors express their gratitude to the University of the National Education Commission (Poland) for financial support of the research project, as well as to the Ministry of Internal Affairs of Ukraine for organizational and administrative support during the study. The study is the result of the respondents’ hard work in filling out a complex questionnaire and thus forming a reliable expert sample. At the same time, authors express their gratitude to colleagues who contributed to the implementation of the relevant scientific tools at all stages of the research project, as well as to the development of the final methodology. The authors have reviewed and edited the output and take full responsibility for the content of this publication.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Korystin, O.E.; Svyrydiuk, N.P. Assessment of hybrid threats and capabilities to counter them in the formation of strategic communications. Uzhhorod Natl. Univ. Her. Ser. Law 2023, 2, 66–74. [Google Scholar] [CrossRef]
- Horbulin, V. The World Hybrid War: Ukrainian Forefront: Monograph Abridged and Translated from Ukrainian; Folio: Kharkiv, Ukraine, 2017. Available online: https://niss.gov.ua/sites/default/files/2017-01/GW_engl_site.pdf (accessed on 1 August 2025).
- Korystin, O.E.; Korchenko, O.; Kazmirchuk, S.; Demediuk, S.; Korystin, O.O. Comparative Risk Assessment of Cyber Threats Based on Average and Fuzzy Sets Theory. Int. J. Comput. Netw. Inf. Secur. (IJCNIS) 2024, 16, 24–34. [Google Scholar] [CrossRef]
- Alefari, M.; Almanei, M.; Salonitis, K. A System Dynamics Model of Employees’ Performance. Sustainability 2020, 12, 6511. [Google Scholar] [CrossRef]
- Filipec, O. Preventing Hybrid Threats: From Identification to an Effective Response. Eur. Stud. 2021, 8, 17–38. [Google Scholar] [CrossRef]
- Liu, Y.; Li, S. Hybrid cyber threats detection using explainable AI in Industrial IoT. In Proceedings of the 2023 International Conference on Human-Centered Cognitive Systems (HCCS), Cardiff, UK, 16–17 December 2023. [Google Scholar] [CrossRef]
- Balcaen, P.; Bois, C.; Buts, C. A Game-theoretic Analysis of Hybrid Threats. Def. Peace Econ. 2021, 33, 26–41. [Google Scholar] [CrossRef]
- Countering Hybrid Threats: EU-NATO Cooperation. Available online: https://www.europarl.europa.eu/thinktank/en/document/EPRS_BRI(2017)599315 (accessed on 25 July 2025).
- Coldea, F. Intelligence Challenges in Countering Hybrid Threats. Natl. Secur. Future 2022, 23, 49–66. [Google Scholar] [CrossRef]
- Neag, M. Physiognomy of Military Operations Answer to Hybrid Threats. Int. Conf. Knowl.-Based Organ. 2018, 24, 163–170. [Google Scholar] [CrossRef]
- The Role of Public Administration in Countering Hybrid Threats in Cyberspace. Pak. J. Criminol. 2023, 16, 1037–1052. [CrossRef]
- Treverton, G.F.; Thvedt, A.; Chen, A.R.; Lee, K.; McCue, M. Addressing Hybrid Threats; Arkitektkopia AB: Bromma, Sweden, 2018; Available online: https://www.hybridcoe.fi/wp-content/uploads/2020/07/Treverton-AddressingHybridThreats.pdf (accessed on 25 July 2025).
- Harjanne, A.; Muilu, E.; Smith, H.; Pääkkönen, J. Helsinki in the Era of Hybrid Threats—Hybrid Influencing and the City; Publications of the Central Administration: Helsinki, Finland, 2018; Available online: https://www.hybridcoe.fi/wp-content/uploads/2020/07/Helsinki-in-the-era-of-hybrid-threats-%E2%80%93-Hybrid-influencing-and-the-city_ENG.pdf (accessed on 25 July 2025).
- Joint Report to the European Parliament and the Council on the Implementation of the Joint Framework on Countering Hybrid Threats—A European Union Response. EU Council. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A52016JC0018 (accessed on 25 July 2025).
- Bajarūnas, E.; Keršanskas, V. Hybrid Threats: Analysis of Content, Challenges Posed and Measures to Overcome. Lith. Annu. Strateg. Rev. 2018, 16, 123–170. [Google Scholar] [CrossRef]
- Sarjito, A. Countering Hybrid Threats: Challenges and the Role of Defense Science. J. Public Adm. Stud. 2024, 3, 101–111. [Google Scholar] [CrossRef]
- Khriapynskyi, A.; Khmyrov, I.; Svoboda, I.; Shevchuk, M.; Iastrebova, V. State information security strategies in conditions of hybrid threats. Amazon. Investig. 2023, 12, 84–93. [Google Scholar] [CrossRef]
- Zharikova, M.; Pickl, S. Human factors in hybrid threat risk assessment. Hum. Factors Softw. Syst. Eng. 2024, 140, 19–25. [Google Scholar] [CrossRef]
- Mazaraki, A.; Kalyuzhna, N.; Sarkisian, L. Multiplicative effects of hybrid threats. Balt. J. Econ. Stud. 2021, 7, 136–144. [Google Scholar] [CrossRef]
- Zharikova, M.; Pickl, S. A Framework for Hybrid Risk Analysis. In Proceedings of the 6th International Conference on Intelligent Human Systems Integration (IHSI 2023) Integrating People and Intelligent Systems, Venice, Italy, 22–24 February 2023. [Google Scholar] [CrossRef]
- Sherstjuk, V.; Zharikova, M.; Pickl, S.; Villota, M.; Dorovskaja, I.; Chornyi, D. Modeling Hybrid Attacks and Operations to Assess the Threats in Early Warning Systems. In Proceedings of the 12th International Conference on Advanced Computer Information Technologies (ACIT), Ruzomberok, Slovakia, 26–28 September 2022; pp. 39–44. [Google Scholar] [CrossRef]
- Apolzan, I.; Bănacu, C.S.; Andreica, M.; Ivan, L. Composite Indicators Used in Measuring Hybrid Threats. Proc. Int. Conf. Bus. Excell. 2023, 17, 882–894. [Google Scholar] [CrossRef]
- Joshi, C.; Singh, U.K. Information security risks management framework—A step towards mitigating security risks in university network. J. Inf. Secur. Appl. 2017, 35, 128–137. [Google Scholar] [CrossRef]
- Kaluarachchilage, P.K.H.; Attanayake, C.; Rajasooriya, S.; Tsokos, C.P. An Analytical Approach to Assess and Compare the Vulnerability Risk of Operating Systems. Int. J. Comput. Netw. Inf. Secur. (IJCNIS) 2020, 12, 1–10. [Google Scholar] [CrossRef]
- Lambrinoudakis, C.; Gritzalis, S.; Xenakis, C.; Katsikas, S.; Karyda, M.; Tsochou, A. Compendium of Risk Management Frameworks with Potential Interoperability: Supplement to the Interoperable EU Risk Management Framework Report; European Union Agency for Cybersecurity, ENISA: Attiki, Greece, 2022. [Google Scholar] [CrossRef]
- Zimmermann, H. Fuzzy Set Theory-and Its Applications. In Scimago Journal Rank Measures the Influence of Journals Within a Domain; Springer: Berlin/Heidelberg, Germany, 2022; pp. 1–399. [Google Scholar] [CrossRef]
- Smithson, M.; Oden, G. Fuzzy Set Theory and Applications in Psychology. In Practical Applications of Fuzzy Technologies; Springer: Berlin/Heidelberg, Germany, 2022; pp. 557–585. [Google Scholar] [CrossRef]
- Zimmermann, H. Applications of fuzzy set theory to mathematical programming. Inf. Sci. 1985, 36, 29–58. [Google Scholar] [CrossRef]
- Pavlidis, T. Fuzzy sets and their applications to cognitive and decision processes. IEEE Trans. Autom. Control 1977, 22, 999–1000. [Google Scholar] [CrossRef]
- Cagman, N.; Enginoglu, S.; Citak, F. Fuzzy soft set theory and its applications. Iran. J. Fuzzy Syst. 2011, 8, 137–147. [Google Scholar] [CrossRef]
- Kandel, A.; Byatt, W. Fuzzy sets, fuzzy algebra, and fuzzy statistics. Proc. IEEE 1978, 66, 1619–1639. [Google Scholar] [CrossRef]
- Maiers, J.; Sherif, Y. Applications of fuzzy set theory. IEEE Trans. Syst. Man Cybern. 1985, SMC-15, 175–189. [Google Scholar] [CrossRef]
- Schwartz, D.; Klir, G.; Lewis, H.; Ezawa, Y. Applications of fuzzy sets and approximate reasoning. Proc. IEEE 1994, 82, 482–498. [Google Scholar] [CrossRef]
- Wong, B.; Lai, V. A survey of the application of fuzzy set theory in production and operations management: 1998–2009. Int. J. Prod. Econ. 2011, 129, 157–168. [Google Scholar] [CrossRef]
- Gui, X.; Goering, C. Introduction to fuzzy set theory and applications. Trans. ASABE 1990, 33, 306–0313. [Google Scholar] [CrossRef]
- Korchenko, O.G.; Kazmirchuk, S.V.; Akhmetov, B.B. Applied Information Security Risk Assessment Systems; Comprint: Kyiv, Ukraine, 1990; Available online: https://er.nau.edu.ua/handle/NAU/40482 (accessed on 25 July 2025).
- Chang, L.Y.; Lee, Z.-J. Applying fuzzy expert system to information security risk Assessment—A case study on an attendance system. In Proceedings of the 2013 International Conference on Fuzzy Theory and Its Applications (IFUZZY), Taipei, Taiwan, 6–8 December 2013; pp. 346–351. [Google Scholar] [CrossRef]
- Abdymanapov, S.A.; Muratbekov, M.; Altynbek, S.; Barlybayev, A. Fuzzy Expert System of Information Security Risk Assessment on the Example of Analysis Learning Management Systems. IEEE Access 2013, 9, 156556–156565. [Google Scholar] [CrossRef]
- Gozon, F.Z.; Vaczi, D.; Toth-Laufer, E. Fuzzy-based Human Factor Centered Cybersecurity Risk Assessment. In Proceedings of the IEEE 19th International Symposium on Intelligent Systems and Informatics (SISY), Subotica, Serbia, 16–18 September 2021; pp. 83–88. [Google Scholar] [CrossRef]
- Duisebekova, K.S.; Duisebekov, T. Utilization of Fuzzy Mathematics for Security Model of a System. In Proceedings of the IEEE 12th International Conference on Application of Information and Communication Technologies (AICT), Almaty, Kazakhstan, 17–19 October 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Quelch, J.; Cameron, I. Uncertainty representation and propagation in quantified risk assessment using fuzzy sets. J. Loss Prev. Process Ind. 1994, 7, 463–473. [Google Scholar] [CrossRef]
- Li, W.; Zhou, J. Power System Risk Assessment Using a Hybrid Method of Fuzzy Set and Monte Carlo Simulation. IEEE Trans. Power Syst. 1994, 23, 336–343. [Google Scholar] [CrossRef]
- Georgescu, V. Joint propagation of ontological and epistemic uncertainty across risk assessment and fuzzy time series models. Comput. Sci. Inf. Syst. 2014, 11, 881–904. [Google Scholar] [CrossRef]
- Korvin, A.; Shipley, M.; Omer, K. Assessing risks due to threats to internal control in a computer-based accounting information system: A pragmatic approach based on fuzzy set theory. Intell. Syst. Account. Financ. Manag. 2004, 12, 139–152. [Google Scholar] [CrossRef]
- Abdo, H.; Flaus, J. A mixed fuzzy probabilistic approach for risk assessment of dynamic systems. IFAC-PapersOnLine 2004, 48, 960–965. [Google Scholar] [CrossRef]
- Korchenko, A.G. Construction of information protection systems on fuzzy sets. In Theory and Practical Solutions; MK-Press: Kiev, Ukraine, 2006. [Google Scholar]
- Morklyanik, B.; Korchenko, O.; Kubiv, S.; Kazmirchuk, S.; Teliushchenko, V. The method of phasification of intervals for solving cybersecurity assessment tasks at critical infrastructure facilities. Ukr. Sci. J. Inf. Secur. 2023, 29, 103–110. [Google Scholar]
- Korchenko, A.; Breslavskyi, V.; Yevseiev, S.; Zhumangalieva, N.; Zvarych, A.; Kazmirchuk, S.; Kurchenko, O.; Laptiev, O.; Sievierinov, O.; Tkachuk, S. Development of a method for constructing linguistic standards for multi-criteria assessment of honeypot efficiency. East.-Eur. J. Enterp. Technol. 2023, 111, 63–83. [Google Scholar] [CrossRef]
- Leroy, I.; Zolotaryova, I.; Semenov, S. Impact of Critical Infrastructure Cyber Security on the Sustainable Development of Smart Cities: Insights from Internal Specialists and External Information Security Auditors. Sustainability 2025, 17, 1188. [Google Scholar] [CrossRef]
- Semenov, S.; Krupska-Klimczak, M.; Mazurek, P.; Zhang, M.; Chernikh, O. Improving Unmanned Aerial Vehicle Security as a Factor in Sustainable Development of Smart City Infrastructure: Automatic Dependent Surveillance–Broadcast (ADS-B) Data Protection. Sustainability 2025, 17, 1553. [Google Scholar] [CrossRef]
- Semenov, S.; Krupska-Klimczak, M.; Wasiuta, O.; Krzaczek, B.; Mieczkowski, P.; Głowacki, L.; Yu, J.; He, J.; Chernykh, O. Intelligent Assurance of Resilient UAV Navigation Under Visual Data Deficiency for Sustainable Development of Smart Regions. Sustainability 2025, 17, 6030. [Google Scholar] [CrossRef]
- OECD. Rebuilding Ukraine by Reinforcing Regional and Municipal Governance; OECD Multi-level Governance Studies; OECD Publishing: Paris, France, 2022. [Google Scholar] [CrossRef]
- Forkan, M.; Rizvi, M.M.; Chowdhury, M.A.M. Optimal path planning of Unmanned Aerial Vehicles (UAVs) for targets touring: Geometric and arc parameterization approaches. PLoS ONE 2022, 17, e0276105. [Google Scholar] [CrossRef]
- ISO 31000:2018; Risk Management. ISO: Geneva, Switzerland, 2018. Available online: https://www.iso.org/ru/publication/PUB100464.html (accessed on 25 July 2025).
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).