Development of an Application-Based Framework for Information Security Management in SMEs
Abstract
1. Introduction
2. Theoretical Background
2.1. Information Security
2.2. Risk Management and Information Security
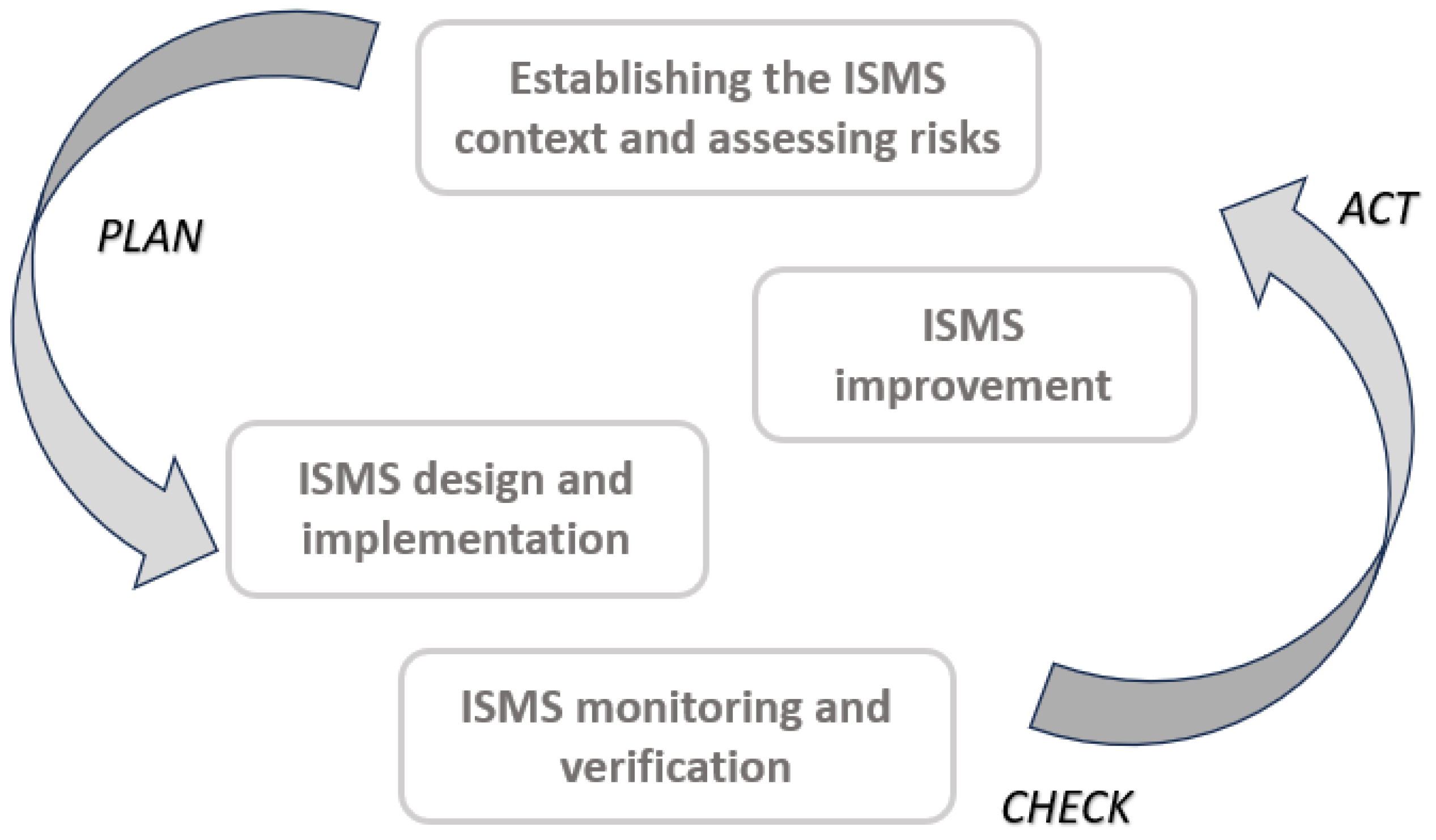
2.3. Information Security Management Systems (ISMS)
3. Research
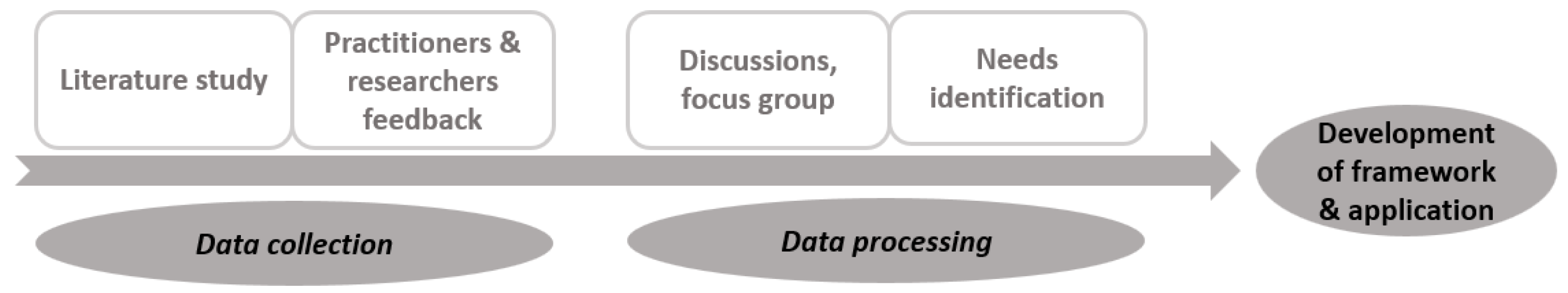
3.1. Research Methodology
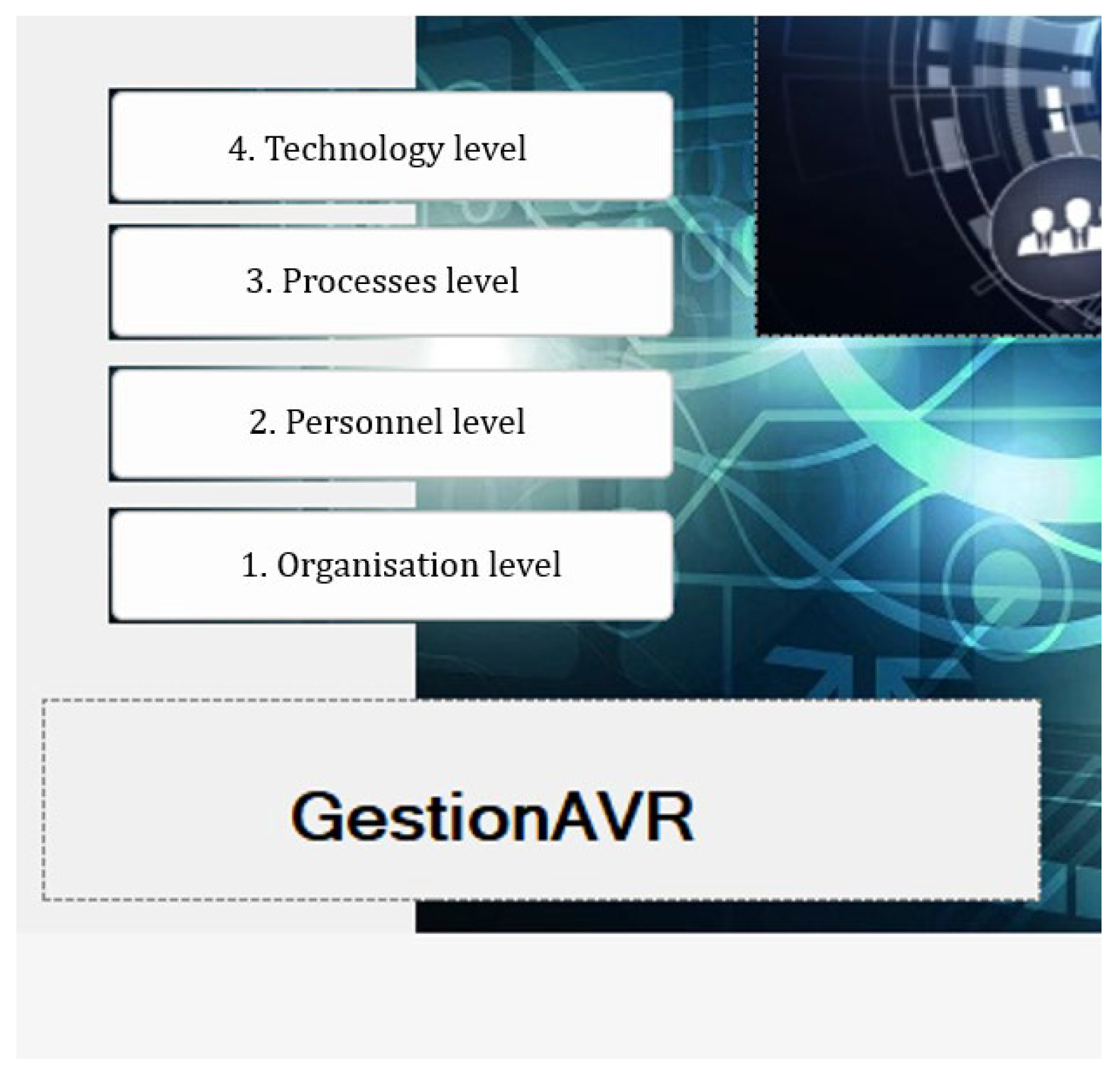
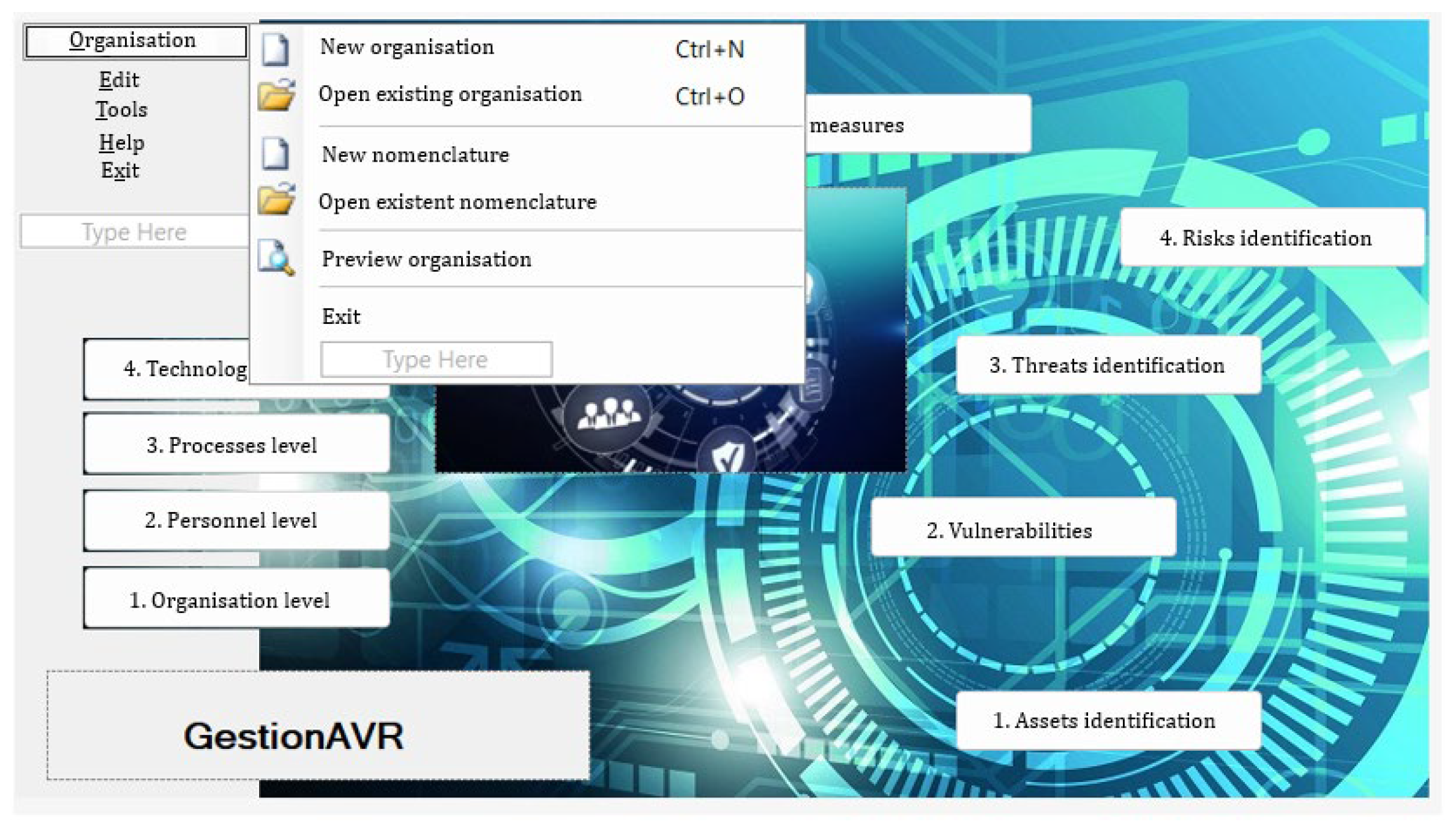
3.2. Framework Description
- The ongoing importance of security for the organization;
- The fact that they are responsible for their actions;
- The possible consequences that may arise from a violation of existing and applicable policies, standards or procedures at the organization level.
- Theoretical research conducted to define relevant security concepts and models.
- Discussions with internal stakeholders such as managers, operators, and employees to collect key information regarding
- -
- The current security system and organizational structure;
- -
- IT systems in use;
- -
- Previously encountered risks, threats, and incidents.
- Describing the architecture of the IT environment.
- Documenting system components, data flows, and technical dependencies.
- Laying the groundwork for identifying potential threats and mitigation strategies.
- Employing qualitative methods such as brainstorming sessions, focus groups with staff, employee surveys, and structured interviews [43];
- Systematically categorizing and analyzing the collected data with the involvement of the research team and working groups.
- Understanding how systems are used in practice;
- Assessing how operational practices influence security risks and potential impacts on the organization.
- Providing the tool GestionAVR and training to employees for its use.
- Gathering feedback from users;
- Evaluating the effectiveness of the applied measures;
- Identifying lessons learned and refining the approach for continuous improvement.
3.3. Case Study
3.3.1. Organizational Structure
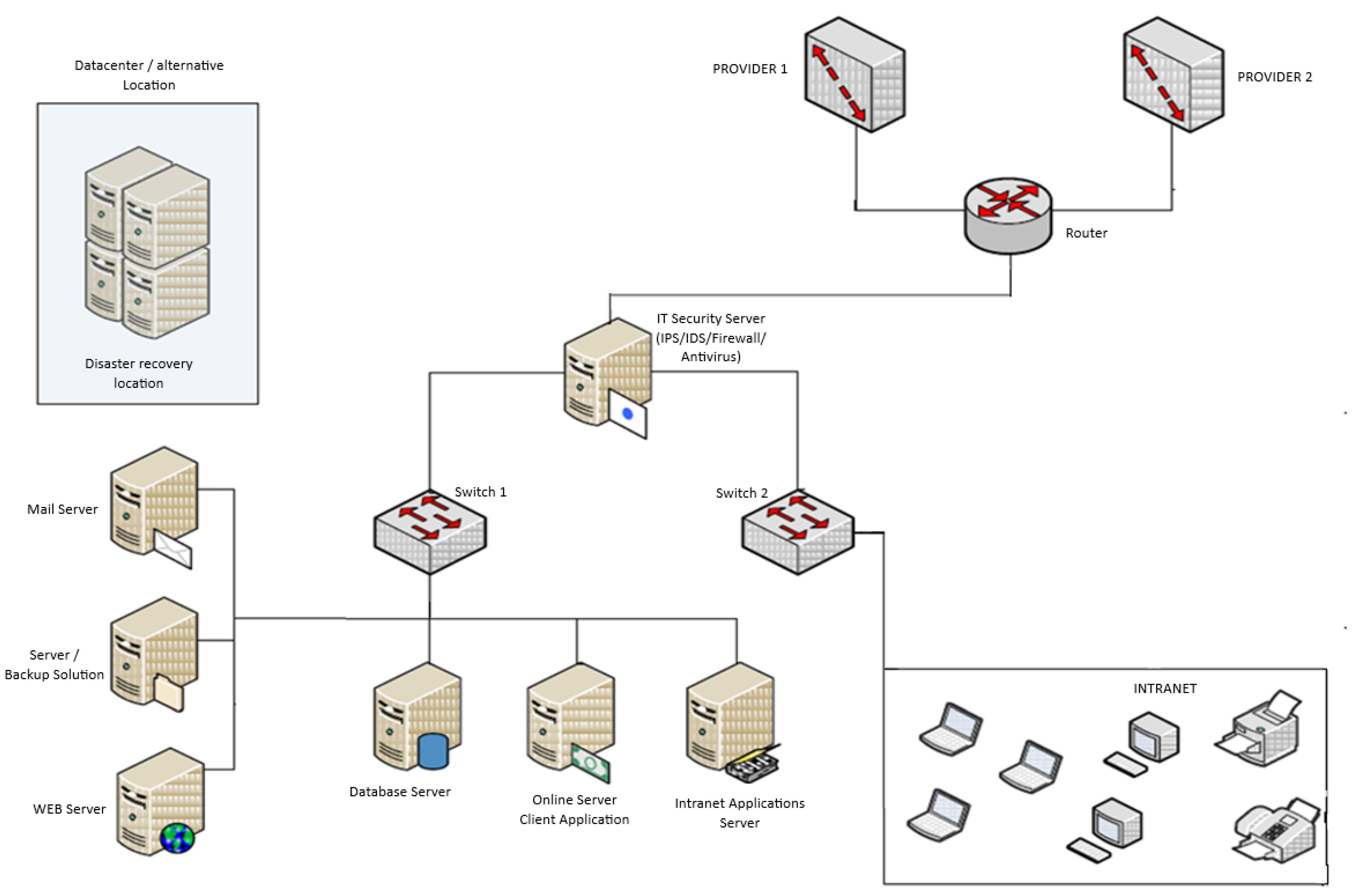
3.3.2. IT Infrastructure Architecture
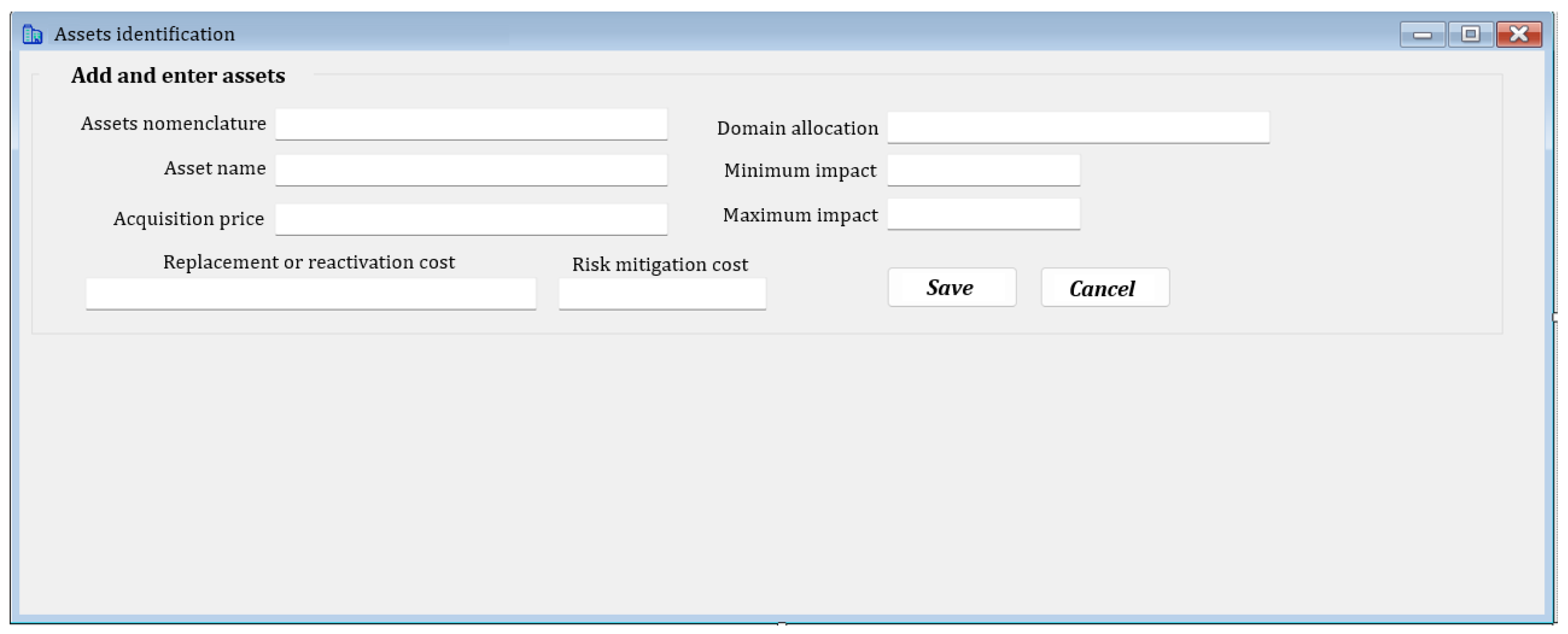
- The identification of critical applications whose replication is necessary within the recovery center;
- The description of the IT infrastructure within the organization;
- The description of the disaster recovery system implemented;
- The description of the personnel available within the organization;
- The analysis of risks and their impact;
- The definition of guidelines for concluding Service Level Agreements (SLA), in order to ensure QoS (Quality of Service) both with equipment suppliers and with communication system suppliers;
- The description of the method of monitoring the disaster recovery system in current operation;
- The definition of critical disaster-type events;
- Defining the activities, steps and procedures that make up the BCP;
- The existence of an alternative data processing location;
- Performing back-ups according to existing procedures;
- The existence of an information security policy with the following objectives:
- -
- Information security management: Information security management measures will be implemented and enforced in accordance with the information security objectives, statements, policies, standards and procedures established by the organization’s management.
- -
- Classification of information, systems and resources: Information, systems and resources will be classified according to the level and type of protection required.
- -
- Identification and authentication: all information and systems with which the institution enforces its own identification and authentication of employees, other users, third parties and systems.
- -
- Confidentiality: the confidentiality of all data, information, systems, documents and software that is enforced.
- -
- Integrity: The integrity of data, information, systems, documents and software that is implemented, depending on how critical the resource is to the organization’s activity.
- -
- Accountability: Accountability and responsibility for user actions must be clearly defined and permanently implemented.
- -
- Availability: All information and systems must be available to authorized users, when needed. They are considered timely, complete and accurate with the recovery of any data, information, software or systems lost due to unwanted and unexpected events (e.g., system interruption in the event of a disaster).
- -
- Nonrepudiation: It is a concept for ensuring that an injured party in a dispute cannot be repudiated, or challenged by a statement of validity. Systems must ensure that an information transaction cannot be subsequently rejected (rejected) by that injured party.
- -
- Physical and logical access control: All information and systems will be appropriately and rigorously secured with physical and logical access controls.
- -
- Risk assessment: The assessment of threats, impacts and vulnerabilities of information processing utilities and the probability of their occurrence.
- -
- Risk management: The process of identifying, reviewing and reducing or eliminating security risks that may affect information systems at an acceptable cost.
- -
- Information security training and awareness: All employees will undergo information security training and awareness programs.
- -
- Roles and responsibilities: The roles, responsibilities and decision-making rights for all parties who have access to information resources are clearly defined and communicated.
- -
- Compliance: Staff as well as other users must be familiar with and comply with the information security procedures and policies.
- -
- Information security monitoring and reporting: Monitoring and reporting of information security measures will be established to detect and report actual and suspected breaches and ensure remedial actions are taken.
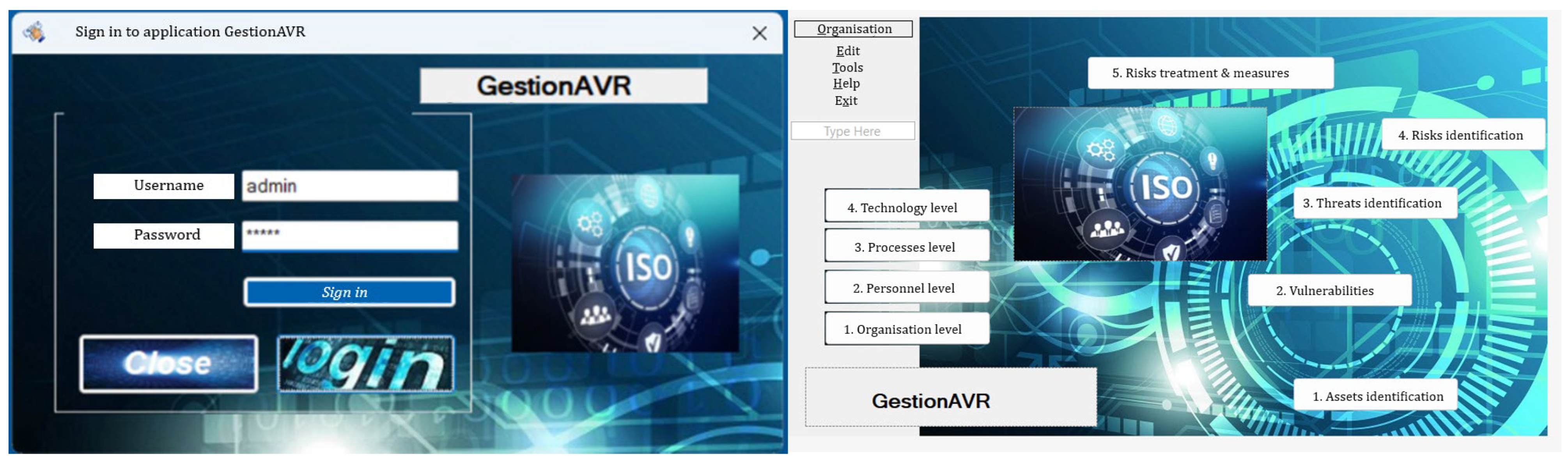
3.3.3. Risk Identification
- External/Organization;
- People/HR Personnel;
- Physical/Processes;
- Systems/Technology
3.3.4. Application GestionAVR
- The risks persisted;
- New risks have emerged;
- The impact and probability of risks have undergone changes, in which case the risk levels are revised;
- New risk control measures and deadlines for their implementation are necessary;
- Risks need to be reprioritized.
3.4. Results and Limitations
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Ahmadi-Gh, Z.; Bello-Pintado, A. Towards sustainable manufacturing: How does digitalization and development affect sustainability barriers? J. Clean. Prod. 2021, 476, 143792. [Google Scholar] [CrossRef]
- Lyu, J. How does digital leadership improve organizational sustainability: Theory and evidence. J. Clean. Prod. 2024, 434, 140148. [Google Scholar] [CrossRef]
- Bendovschi, A. Cyber-Attacks–Trends, Patterns and Security Countermeasures. Procedia Econ. Financ. 2015, 28, 24–31. [Google Scholar] [CrossRef]
- Al Zaidy, A. What are Cyber-Threats, Cyber-Attacks and how to defend our Systems; Research Proposal; Full Sail University: Winter Park, FL, USA, 2014. [Google Scholar] [CrossRef]
- Sajko, M.; Rabuzin, K.; Bača, M. How to calculate information value for effective security risk assessment. J. Inf. Organ. Sci. 2006, 30, 263–278. [Google Scholar]
- Du Toit, A.; Saloojee, R.; Groenewald, D. Investigating the business value of information management. S. Afr. J. Inf. Manag. 2007, 9, a17. [Google Scholar] [CrossRef]
- Bodendorf, F.; Franke, J. What is the business value of your data? A multi-perspective empirical study on monetary valuation factors and methods for data governance. Data Knowl. Eng. 2024, 149, 102242. [Google Scholar] [CrossRef]
- Aleksandrov, M.N.; Vasiliev, V.A.; Aleksandrova, S.V. Implementation of the Risk-based Approach Methodology in Information Security Management Systems. In Proceedings of the 2021 International Conference on Quality Management, Transport and Information Security, Information Technologies (IT&QM&IS), Yaroslavl, Russia, 6–10 September 2021; pp. 137–139. [Google Scholar] [CrossRef]
- Marhad, S.S.; Goni, S.Z.A.; Sani, M.K.J.A. Implementation of Information Security Management Systems for Data Protection in Organizations: A systematic literature review. Environ. Behav. Proc. J. 2023, 9, 197–203. [Google Scholar] [CrossRef]
- Christiawan, E. The Importance of Information Security Management in Small Medium Enterprises. Ph.D. Thesis, Murdoch University Singapore, Singapore, 2015. [Google Scholar]
- Ng, Z.X.; Ahmad, A.; Maynard, S.B. Information Security Management: Factors that influence Security Investments in SMEs. In Proceedings of the 11th Australian Information Security Management Conference, Perth, Australia, 2–4 December 2013; pp. 60–74. [Google Scholar]
- Park, J.-Y.; Robles, R.; Hong, C.-H.; Yeo, S.-S.; Kim, T. IT Security Strategies for SME’s. Int. J. Softw. Eng. Its Appl. 2008, 2, 3. [Google Scholar]
- Whitman, M.E.; Mattord, H. Roadmap to Information Security: For IT and Infosec Managers; Cengage Learning: Boston, MA, USA, 2011. [Google Scholar]
- Brunner, M.; Sauerwein, C.; Felderer, M.; Breu, R. Risk management practices in information security: Exploring the status quo in the DACH region. Comput. Secur. 2020, 92, 101776. [Google Scholar] [CrossRef]
- Blakley, B.; McDermott, E.; Geer, D. Information security is information risk management. In Proceedings of the New Security Paradigms Workshop, Cloudcroft, NM, USA, 10–13 September 2001; p. 97. [Google Scholar] [CrossRef]
- Wangen, G.B. An initial insight into Information Security Risk Assessment practices. In Proceedings of the Federated Conference on Computer Science and Information Systems, Gdansk, Poland, 11–14 September 2016; pp. 999–1008. [Google Scholar] [CrossRef]
- ISO/IEC 27001:2022; Information Security, Cybersecurity and Privacy Protection—Information Security Management Systems—Requirements. International Organization for Standardization: Geneva, Switzerland, 2022.
- BSI 100-1; Information Security Management Systems (ISMS). BSI: Bonn, Germany, 2005.
- Asosheh, A.; Hajinazari, P.; Khodkari, H. A practical implementation of ISMS. In Proceedings of the 7th International Conference on e-Commerce in Developing Countries: With Focus on e-Security, Kish Island, Iran, 17–18 April 2013; pp. 1–17. [Google Scholar] [CrossRef]
- Burggräf, P.; Adlon, T.; Schupp, S.; Salzwedel, J. Risk Management in Factory Planning–A Literature Review. Procedia CIRP 2021, 104, 1191–1196. [Google Scholar] [CrossRef]
- Crovini, C.; Ossola, G.; Britzelmaier, B. How to reconsider risk management in SMEs? An Advanced, Reasoned and Organised Literature Review. Eur. Manag. J. 2021, 39, 118–134. [Google Scholar] [CrossRef]
- Qiu, S.; Tong, Y.; Zhang, X.; Huang, C.; Guo, F. Construction and Practice of Enterprise Information Security Management System of Intrusion Detection Technology. Procedia Comput. Sci. 2024, 243, 340–347. [Google Scholar] [CrossRef]
- Katsikas, S.K. Health care management and information systems security: Awareness, training or education? Int. J. Med. Inform. 2000, 60, 129–135. [Google Scholar] [CrossRef]
- Fitzgerald, T. What You Told Us: A CISO Survey. In CISO Leadership; Auerbach Publications: Boca Raton, FL, USA, 2007; pp. 37–62. [Google Scholar]
- Hooper, V.; McKissack, J. The emerging role of the ciso. Bus. Horiz. 2016, 59, 585–591. [Google Scholar] [CrossRef]
- Haufe, K.; Dzombeta, S.; Brandis, K. Proposal for a Security Management in Cloud Computing for Health Care. Sci. World J. 2014, 19, 146970. [Google Scholar] [CrossRef]
- Aftabi, N.; Moradi, N.; Mahroo, F.; Kianfar, F. SD-ABM-ISM: An integrated system dynamics and agent-based modeling framework for information security management in complex information systems with multi-actor threat dynamics. Expert Syst. Appl. 2024, 263, 125681. [Google Scholar] [CrossRef]
- Aleksandrova, S.; Vasiliev, V.; Aleksandrov, M. Problems of Implementing Information Security Management Systems. In Proceedings of the International Conference on Quality Management, Transport and Information Security, Information Technologies, Yaroslavl, Russia, 7–11 September 2020; pp. 78–81. [Google Scholar] [CrossRef]
- Andrzejewski, K. Security information management systems. Manag. Sci. 2019, 24, 1–9. [Google Scholar] [CrossRef]
- Sanchez, L.E.; Villafranca, D.; Fernandez-Medina, E.; Piattini, M. Developing a model and a tool to manage the information security in Small and Medium Enterprises. In Proceedings of the SECRYPT 2007–International Conference on Security and Cryptography, Barcelona, Spain, 13–28 July 2007; pp. 355–362. [Google Scholar]
- Brunner, M.; Mussmann, A.; Breu, R. Introduction of a Tool-based Continuous Information Security Management System: An Exploratory Case Study. In Proceedings of the 2018 IEEE International Conference on Software Quality, Reliability and Security Companion, Lisbon, Portugal, 16–20 July 2018. [Google Scholar] [CrossRef]
- Valdevit, T.; Mayer, N.; Barafort, B. Tailoring ISO/IEC 27001 for SMEs–A Guide to Implement an Information Security Management System in Small Settings. In Software Process Improvement. EuroSPI 2009. Communications in Computer and Information Science; Springer: Berlin/Heidelberg, Germany, 2009; Volume 42, pp. 201–212. [Google Scholar]
- Mthiyane, Z.Z.F.; van der Poll, H.M.; Tshehla, M.F. A Framework for Risk Management in Small Medium Enterprises in Developing Countries. Risks 2022, 10, 173. [Google Scholar] [CrossRef]
- Peltier, T.R. Preparing for ISO 17799. Inf. Syst. Secur. 2003, 11, 21–28. [Google Scholar] [CrossRef]
- Garigue, R.; Stefaniu, M. Information Security Governance Reporting. Inf. Syst. Secur. 2003, 12, 36–40. [Google Scholar] [CrossRef]
- Boyes, H.; Higgins, M.D. An Overview of Information and Cyber Security Standards. J. ICT Stand. 2024, 12, 95–134. [Google Scholar] [CrossRef]
- Barlette, Y.; Fomin, V.V. The adoption of information security management standards: A literature review. In Information Resources Management: Concepts, Methodologies, Tools and Applications; Information Resource Management Association, Ed.; IGI Global: Hershey, PA, USA, 2010; pp. 69–90. [Google Scholar] [CrossRef]
- Sanchez, L.E.; Villafranca, D.; Fernandez-Medina, E.; Piattini, M. Practical Application of a Security Management Maturity Model for SMEs Based on Predefined Schemas. In Proceedings of the International Conference on Security and Cryptography (SECRYPT08), Porto, Portugal, 26–29 July 2008; pp. 391–398. [Google Scholar]
- Brunner, M.; Sillaber, C.; Breu, R. Towards Automation in Information Security Management Systems. In Proceedings of the 2017 IEEE International Conference on Software Quality, Reliability and Security (QRS), Prague, Czech Republic, 25–29 July 2017; pp. 160–167. [Google Scholar]
- Pipkin, D.L. Information Security; Prentice Hall: Saddle River, NJ, USA, 2000. [Google Scholar]
- Wirtz, R.; Heisel, M. Risk Treatment: An Iterative Method for Identifying Controls. In Evaluation of Novel Approaches to Software Engineering; Springer: Cham, Switzerland, 2021; pp. 283–310. [Google Scholar] [CrossRef]
- Carlson, S.E.; Lewis, D.G.R.; Maliakal, L.V.; Gerber, E.M.; Easterday, M.W. The design risks framework: Understanding metacognition for iteration. Des. Stud. 2020, 70, 100961. [Google Scholar] [CrossRef]
- ISO/IEC 27005:2022; Information Security, Cybersecurity and Privacy Protection–Guidelines for Information Security Risk Management. International Organization for Standardization: Geneva, Switzerland, 2022.
- Hidayatullah, D.E.R.; Kunthi, R.; Harwahyu, R. Design and Analysis of Information Security Risk Management Based on ISO 27005: Case Study on Audit Management System (AMS) XYZ Internal Audit Department. Int. J. Electr. Comput. Biomed. Eng. 2024, 2, 395–413. [Google Scholar] [CrossRef]
- Moraru, R.I.; Băbuț, G.B.; Cioca, L.I. Rationale and criteria development for risk assessment tool selection in work environments. Environ. Eng. Manag. J. 2014, 13, 1371–1376. [Google Scholar] [CrossRef]
- Whitman, M.E.; Mattord, H.J. Management of Information Security; Cengage Learning: Stamford, CT, USA, 2014. [Google Scholar]
- Zhang, X.; Cui, L.; Shen, W.; Wang, Y. Design and Implementation of Intelligent Data Security Risk Assessment and Management System. Procedia Comput. Sci. 2024, 243, 148–155. [Google Scholar] [CrossRef]
- DeLange, S. Vanta. Integrating Climate Change Considerations into Your ISMS Following the ISO 27001 2024 Amendment. Available online: https://help.vanta.com/en/articles/11345801-integrating-climate-change-considerations-into-your-isms-following-the-iso-27001-2024-amendment (accessed on 22 May 2025).
| Risks Related to Organization’s External Environment |
| losses due to catastrophic events/natural disasters |
| losses generated by factors outside the organization |
| interruptions in the provision of services contracted with external suppliers |
| external fraud and criminal activities |
| exposures to external factors of system security |
| terrorist or cyber attacks |
| economic and/or cyber crime |
| power outages |
| disaster recovery risks |
| external back-up location |
| inadequate testing of disaster recovery |
| Risks related to organization’s personnel |
| lack of a clear delimitation between the roles of the people who access/manage/develop the information systems |
| data alteration |
| changes in information or data in reports, without appropriate documentation |
| failure to comply with processes, procedures or work instructions |
| errors in manual entry or inappropriate use of information systems |
| conflict of interest between the personnel who develops and administrates the information systems or between their users |
| insufficient staff |
| dependence on key employees |
| lack of communication and cooperation between employees |
| failure to report errors or mistakes related to information systems |
| complacency of personnel |
| fraud |
| money laundering and financing of terrorism |
| non-compliance with the international sanctions’ regime |
| Risks related to physical level and the processes |
| Model risks |
| lack of organizational processes (at least regarding change management, incidents, problems, service levels, various versions, capacity, availability and projects) |
| methodological or model errors |
| evaluation errors |
| availability of reserves to cover losses |
| complexity of models |
| inadequate process control |
| software inappropriate to the business objectives |
| insufficient corporate governance in this area |
| Transactional risks |
| execution errors |
| recording errors |
| inadequate data and information management |
| machine errors |
| product complexity |
| capacity risks |
| evaluation risks |
| confidentiality risks |
| fraud |
| Risks related to the control of operations |
| lack of separation of rights and duties (segregation) |
| exceeding limits |
| volume risks |
| security risks |
| reporting risks |
| risks of inadequate accounting records |
| inadequate control of outsourced activities |
| disruption of service provision |
| misidentification of operations in question based on risk indicators and predefined analytical variables |
| Risks related to locations |
| miscommunication |
| supply chain disruptions |
| quality control issues |
| cultural risks |
| workforce management and coordination |
| Risks related to systems/technology |
| inadequate technology and security management system |
| lack of development and testing methodologies |
| insufficient processing capacity |
| system outages (hardware, software, storage, telecommunications) |
| network outages |
| interruptions in the provision of services provided by external providers |
| inadequate systems |
| inadequate protection against malware |
| compatibility risks |
| risks generated by suppliers/vendors |
| inadequate technology update system |
| outdated systems |
| inadequate system support services |
| programming errors |
| data corruption |
| Grade | 1 | 2 | 3 |
|---|---|---|---|
| Probability | Negligible | Low | High |
| Description | Practically impossible to occur under normal conditions. No historical records have been made. | It may occur under normal conditions, but the frequency of occurrence is rare. | It is likely to occur. This risk is reasonable to occur in the immediate future. |
| VULNERABILITY | HIGH | Medium Risk | High Risk | High Risk |
| MEDIUM | Low Risk | Medium Risk | High Risk | |
| NEGLIGIBLE | Low Risk | Low Risk | Medium Risk | |
| NEGLIGIBLE | LOW | HIGH | ||
| PROBABILITY | ||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rusu, D.; Mantulescu, M. Development of an Application-Based Framework for Information Security Management in SMEs. Sustainability 2025, 17, 8314. https://doi.org/10.3390/su17188314
Rusu D, Mantulescu M. Development of an Application-Based Framework for Information Security Management in SMEs. Sustainability. 2025; 17(18):8314. https://doi.org/10.3390/su17188314
Chicago/Turabian StyleRusu, Diana, and Marius Mantulescu. 2025. "Development of an Application-Based Framework for Information Security Management in SMEs" Sustainability 17, no. 18: 8314. https://doi.org/10.3390/su17188314
APA StyleRusu, D., & Mantulescu, M. (2025). Development of an Application-Based Framework for Information Security Management in SMEs. Sustainability, 17(18), 8314. https://doi.org/10.3390/su17188314









