Conceptual Model of Key Aspects of Security and Privacy Protection in a Smart City in Slovakia
Abstract
1. Introduction
1.1. Research Questions
- What are the general security and privacy aspects of a smart city and how can we categorise them?
- Which of these aspects are critical for the development of a conceptual model of security and privacy in a smart city with respect to the possibilities, assumptions, problems, and factors of its feasibility in the Slovak Republic?
1.2. Literature Review
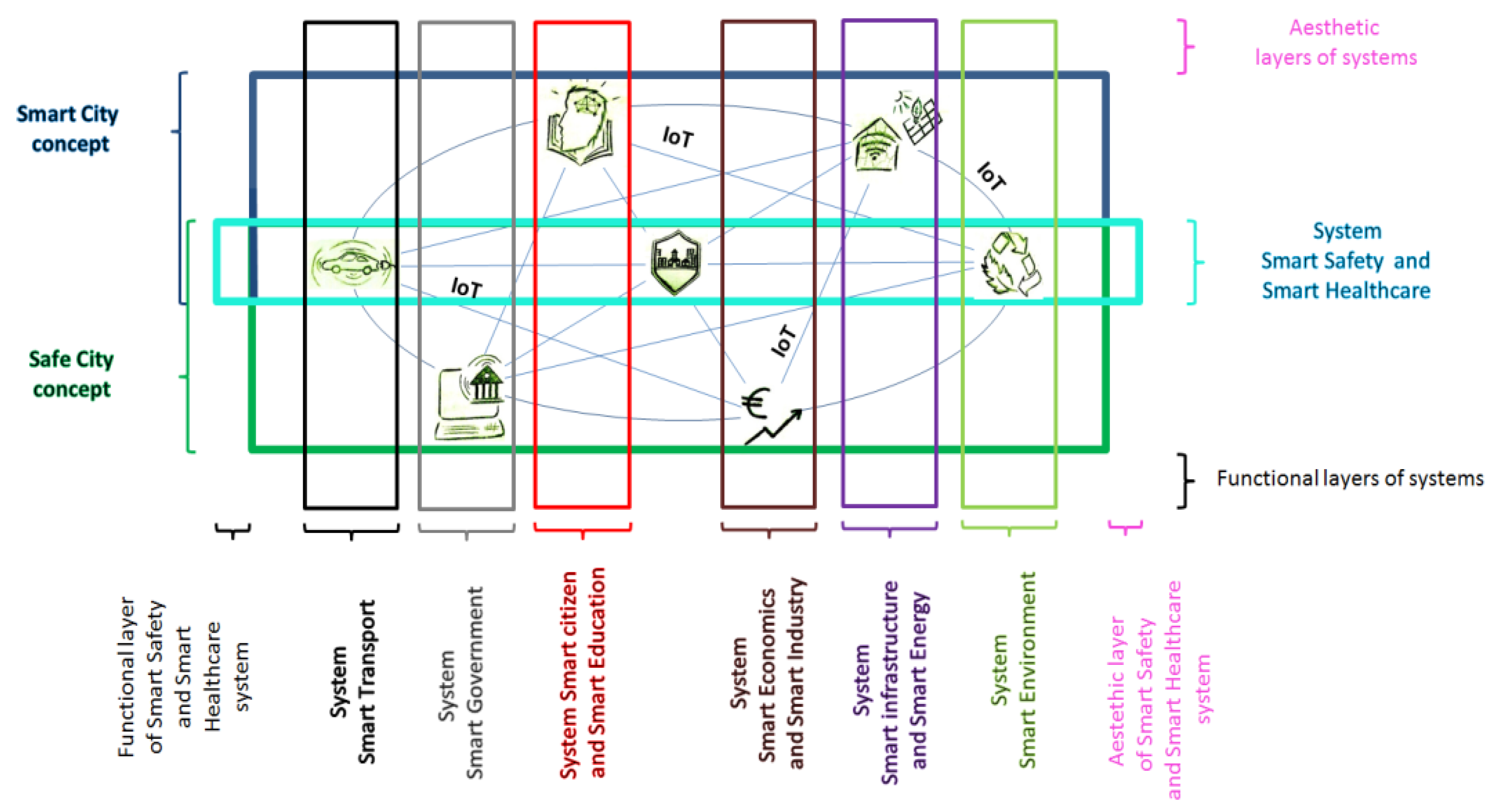
- Smart City Governance: This system primarily relates to municipal politics and citizen participation in public decision-making, management of municipal enterprises, and general services for smart city residents [25]. For instance, digitalisation of local elections, public consultations, referendums, voting, monitoring of residents’ sentiment about public affairs or local policies, and others [26]. In the Slovak Republic, municipalities are constitutionally obliged to appropriately inform residents about their activities. Without more detailed elaboration of the means, this obligation is further specified in Act No. 211/2000 Coll. on free access to information.
- Smart Residents: The system mainly relates to the level of competence and education of residents in the use of technological artefacts and participation in the smart city ecosystem, but also to the ability of residents to actively perceive social interactions and public life and react to emerging changes [27]. Responsible residents who know how to securely handle and share their data are a good example. The principal methods of residential participation in Slovak municipal governance are specified in the Act on the Municipal System no. 369/1990 Coll. The voluntary contribution relies on the municipality’s independent initiative [27]. A national programme for development of education as well as a programme of school informatisation with an outlook until 2030 seek to increase competence of the society in the field of ICT and digital services.
- Smart Economy: This system is mainly linked with competition, entrepreneurship, continuous innovation cycle, flexibility, and labour market productivity [28]. The focus is on how technology is applied rather than how many technological artefacts are available [29]. Examples include special industrial zones or the circular economy. The Smart Industry Concept for Slovakia defines the vision and some domains of a smart economy, while a follow-up action plan is limited to the framing of general tasks that would enable favourable conditions for the development of the Slovak IoT-based economy. The Research and Innovation Strategy for Intelligent Specialisation Slovak Republic 2021–2027 increases the potential for such transformation.
- Smart Housing: The system encompasses a number of intelligent services designed to improve general quality of life or provide convenient home better management of home appliances [30]. These range from optimisation of residential zones, cultural and social facilities, educational facilities, tourism, and security to remote monitoring [31,32].
- Smart Healthcare: A connected, intelligent, and human-centred healthcare system is best represented by the integration of personal, environment, and infrastructure data via algorithms to create actionable insights or personalised care experience for smart city residents [33]. Digitalisation and informatisation of the Slovak healthcare system was enabled by Act No. 53/2013 Coll. on the national health information system, which established the National Centre for Health Information responsible for the implementation of informatisation and computerisation of healthcare in the Slovak Republic [34]. This paradigm was further accelerated by the COVID-19 pandemic.
- Smart Transportation: This system is primarily tied to a sustainable transportation system and the continuous improvement of urban transport efficiency, smart parking, and traffic management in relation to planning and demographic trends [35]. A suitable example are the smart interfaces for public transportation. Act No. 317/2012 Coll. on Intelligent Transport Systems in Road Transport regulates the use of smart transport systems in Slovakia for road transport only. Data collection and analysing are somewhat decentralised and take place at several levels, e.g., the Slovak Road Administration through the National Traffic Information System [36]. This strategy for smart and sustainable mobility in Slovakia provides a vision for the future direction of this system.
- Smart Infrastructure: This system relates to the monitoring of urban environments and management of limited resources, raw materials, and energy networks in order to ensure their optimal usage [37]. Some examples are smart grid, electricity storage or decentralisation of energy production, and consumption [38]. Providing access to information and communication networks and technologies also falls into this category. The topic of smart energy is one of the priorities of the Energy Union and according to the Ministry of Economy, Slovakia is significantly lagging behind. Act No. 251/2012 Coll. on Energy does not take into account the dynamically changing environment and contemporary trends such as decentralisation [39].
- Smart Urban Environment: This system comprises monitoring of key ecological indexes and their analyses to adequate responses from authorities. It is an essential link between city management and environmental protection [40]. Examples include, but are not limited to, carbon and harmful gas management, construction of green spaces and buildings, waste recycling, and sanitation management. The vague vision is conveyed by the Strategy of Environmental Policy of the Slovak Republic to 2030. Act No. 17/1992 Coll. on the Environment as well as the forthcoming Act No. 27/2022 Coll. on Air Protection defines sufficient environmental parameters, but there is a lack of legislation framing the means of achieving the desired state.
- Sustainable Finance: The Slovak Government approved the Programme Slovakia 2021–2027, on the basis of which the Slovak Republic will be able to draw European resources in the amount of almost EUR 13 billion in the new programming period. The package also includes EUR 106.3 million allocated for the building of smart cities and regions, in accordance with the Programme Declaration of the Slovak Government and other relevant focus materials, including the upcoming Action Plan for Smart Cities and Regions for 2023–2025. The National Investment Plan for 2018–2030 elaborates on the current funding basis and specifies financial instruments at the national level.
- A.
- An active participation of residents is the backbone of a smart city because the concept itself is based on the premise that technology serves the needs of residents and a smart city is not merely about advanced technology and infrastructure. The participation of residents and their devices is essential due to their ability to generate data for the development of technologies, applications and systems as well as human factors such as innovation [13].
- B.
- Meaningful human control of systems and subsystems. Given the ubiquity of systems in a smart city, it is necessary to take into consideration ethical implications and user values to ensure their socio-technical resilience [42]. Meaningful human control as part of the design ensures sustainable engagement of residents.
- C.
- Onnectivity enables the connection of technological artefacts and their clusters to the intelligent ecosystem represented by IoT [43]. Thus, connectivity is the most fundamental prerequisite for a technically functioning smart city and a guarantor of competitive advantage over conventional cities. Connectivity, through the provision of communication solutions, causes a significant spillover effect to other domains.
- D.
- Scalability complements connectivity, as each IoT system or component should be scalable according to the needs of a smart city. Assuming that smart cities evolve from small to larger, from technologically simpler to more complex, an exponential increase in system complexity as well as data quantity can be expected [44]. A smart city cannot function properly without scalable systems and mechanisms. Connectivity and scalability are directly related to the generation and management of big data (Big Data).
- E.
- Big Data are the result of the application of IoT. As outlined in the introduction, for the operation of a smart city, it is necessary to manage large amounts of sensitive and personal information that may pose a security risk or a vulnerable part of the system.
- F.
- Heterogeneity is another requirement that is related to IoT. Heterogeneity can be defined as the plurality and independence of systems, technological artefacts, users, diversity of networks, protocols and communication technologies, tools, and platforms that lack a common security framework [45]. Homogeneity is in direct conflict with the dynamic concept of the evolving smart city.
- G.
- Constrained resources, or in other words, devices that are a part of IoT are limited by physical parameters such as memory, battery capacity and quality, radio standards or network interfaces [46]. For better security, it is necessary to balance the use of cheaper, smaller, and less energy-intensive devices with their expensive counterparts. Data minimisation and avoiding recording of irrelevant data are also part of effective resource management [47]. Unique security challenges require specific security measures.
- H.
- Autonomy provides rapid response, cost savings, and adaptive configuration of systems as they operate. Autonomy is closely linked to the artificial intelligence (AI) that enables it. Devices involved in IoT, unlike traditional technological artefacts, should be able to configure themselves automatically.
- I.
- Vulnerability or susceptibility of complex systems to coordinated physical attacks and natural disasters is the Achilles heel of IoT [48]. Due to their number, sensors are usually small and do not have robust physical protection. This means that they can be easily destroyed, stolen, moved, or tampered with.
1.3. Literature Gap
2. Materials and Methods
Summary of the Research Process
- Define the research questions as well as inclusion and exclusion criteria for various privacy and security aspects.
- Search for relevant academic articles in electronic databases such as JSTOR, ScienceDirect, Scopus, EBSCO, ProQuest.
- Select highly cited articles with respect to the defined research method, criteria, and timeliness.
- Filter research articles by title, keywords, and abstract with respect to various aspects of smart city security and privacy.
- Evaluate bias and extract relevant data from the articles.
- Analyse and classify key aspects.
- Reduce and extract key aspects.
- Categorise key aspects.
- Assess the quality of evidence and interpretation of categories to achieve a more comprehensive view.
- Draw generalised conclusions to the aspects beyond their individual elements.
- Address retrieved conclusions that differ from the literature review and unpack in the discussion.
3. Results
3.1. Security
3.2. Privacy
- Identification: The threat of identification is related to the association of a person with private data. Authentication based on personal data minimisation limits the ability of sensors to collect data in the IoT, thus maintaining control over data disclosure [67].
- Localisation: The threat of recording location or tracking a person’s movement in space and time relates to the availability of spatio-temporal data in the IoT, where technological artefacts continuously record a user’s identity, location, and activity [68].
- Profiling: The threat of collecting and analysing data about the activities of individuals or groups in space and time, in order to identify their behaviours based on specific characteristics. The threat is exacerbated by identifying or combining it with other personal information [69].
- Information fusion: The threat of creating accurate information as a result of combining independent data from different systems. The integration of different types of information about an individual that reveals new facts [70].
- Exploitation: The threat of malicious use of personal information, leakage of personal data, creation of fake profiles, identity spoofing attacks, and misuse of facial recognition. Illegal collection of information about the existence and characteristics of specific persons and things. Unauthorised access to personal data that may be disclosed or leaked. Data that are subject to unprotected smart city infrastructure may provide information that facilitates the theft of personal data and its use for subversive activities.
- Insecurity: The threat of not securing the sensors, technological artefacts, and software that are the starting point of any attack. If the hardware is not sufficiently tested, it poses a significant threat to the entire system. The lack of certification and standardisation of devices and software creates a vulnerability in the system, as an attack on one device can compromise the entire network [71]. Due to the large set of technological devices, a simple software bug can affect an entire system.
- Extortion: A psychological threat that is compounded by the frequent interaction of smart city residents in the digital environment. Extortion can be perpetrated against individuals, but especially against children and adolescents. Such threats include child harassment, high-risk behaviour on social media, and communication with strangers [72].
- Alteration of ownership: A threat based on a legal process in which a new person becomes the official owner of a technological artefact, sensor, system, or network that was previously used by another person. For example, an attacker could use hijacked smart metres to run ransomware on systems [73].
- Influencing: Within the context of this study, this threat can be defined as a set of soft power instruments of influence that aim to obtain data or exploit system vulnerabilities to disrupt the processes of a smart city [74]. This can be achieved not only by social engineering, but also by arousing negative sentiment, eroding residents’ trust in governing institutions, or challenging core values of the concept [75].
- Composite attacks: A combined threat consisting of multiple distributed attacks with a synergistic effect and a greater impact.
3.3. Cyber Threats
- Short development cycle of new techniques and attack methods: The possibilities for attackers to use innovative tools are constantly improving. Therefore, the development of appropriate cybersecurity tools or the degree of their availability in specific markets may come too late or be of insufficient potency in some instances [81]. Attackers customarily react to emerging vulnerabilities in products and services in real time, while security measures can be subject to long development cycles. The development of emerging technologies such as applications of AI, quantum computing, and encryption further enables attackers to execute their attacks more efficiently. As vulnerability rates increase in direct proportion to the evolution of technology and the digitisation of society, accelerating development cycles exerts pressure on security requirements. This creates an asymmetry between dynamic development and the emphasis on security requirements, especially if the developer prioritises functionality and design over security. A similar problem arises in software technology upgrades, where improved functionality does not necessarily equate to better security, unless the very reason for the upgrade is security. Short development cycles also imply quicker loss of manufacturer support and infrequent updates for outdated products and services.
- 2.
- Lack of expertise and low level of user awareness: Technological advances are not the only determinant of security; the human factor is equally important. Unless the individuals who handle technology and participate in the smart city ecosystem are competent or experienced enough to manage risks and apply security measures, the human factor will be a weak link in security [84]. Defining processes and implementing security measures require aware individuals as well as sufficient awareness in society to facilitate funding for security activities and ensure leadership support. For example, the detection of cyber incidents, i.e., attempted or successful attacks, is a challenging process, requiring a high level of expertise and technical capacity. Awareness of the pitfalls and risks in cyberspace affects not only the company but also the users’ attitude towards their own security. Individuals lacking knowledge and experience in cybersecurity can become ideal targets for attackers.
- 3.
- There is a slow implementation of legislative measures and standards. The topic of security is not commonly considered a priority, but mostly just an obligation that must be fulfilled by law; implementing regulations or non-legislative standards defines the status quo of measures across all levels of security. Moreover, legislative cycles are usually much longer than the cycle of innovation and application of new methods and technologies in the cybercrime field [86].
4. Discussion
4.1. Data-Centric Approach
4.2. Resident-Centric Approach
4.3. Policy-Centric Approach
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Picon, A. Opinions, Smart Cities, Privacy and the Pulverisation/Reconstruction of Individuals. Eur. Data Prot. Law Rev. 2019, 5, 154–155. [Google Scholar] [CrossRef]
- Komninos, N. What Makes Cities Intelligent? In Smart Cities: Governing, Modelling and Analysing the Transition; Deakin, M., Ed.; Taylor and Francis: Abingdon, UK, 2013; p. 77. [Google Scholar]
- Alter, S. Making Sense of Smartness in the Context of Smart Devices and Smart Systems. Inf. Syst. Front. 2020, 22, 381–393. [Google Scholar] [CrossRef]
- Seta, F.; Sen, J.; Biswas, A.; Khare, A. From Poverty, Inequality to Smart City Proceedings of the National Conference on Sustainable Built Environment 2015, 1st ed.; Seta, F., Sen, J., Biswas, A., Khare, A., Eds.; Springer: Singapore, 2017. [Google Scholar]
- Yeh, H. The effects of successful ICT-based smart city services: From citizens’ perspectives. Gov. Inf. Q. 2017, 34, 556–565. [Google Scholar] [CrossRef]
- McLaren, D.; Agyeman, J. Sharing Cities: A Case for Truly Smart and Sustainable Cities/Duncan McLaren and Julian Agyeman; MIT Press: Cambridge, MA, USA, 2015. [Google Scholar]
- Vinod Kumar, T.M. (Ed.) Smart Living for Smart Cities Case Studies, 1st ed.; Springer: Singapore, 2020. [Google Scholar]
- AI-Turjman, F.; Imran, M. (Eds.) IoT Technologies in Smart Cities from Sensors to Big Data, Security and Trust; IET: Stevenage, UK, 2020. [Google Scholar]
- Ejaz, W.; Anpalagan, A. (Eds.) Internet of Things for Smart Cities Technologies, Big Data and Security, 1st ed.; Springer International Publishing: Cham, Switzerland, 2019. [Google Scholar]
- Orlowski, C. Management of IOT Open Data Projects in Smart Cities; Elsevier Science & Technology: San Diego, CA, USA, 2020. [Google Scholar]
- Ju, J.; Liu, L.; Feng, Y. Citizen-centered big data analysis-driven governance intelligence framework for smart cities. Telecommun. Policy 2018, 42, 881–896. [Google Scholar] [CrossRef]
- Lai, C.S.; Jia, Y.; Dong, Z.; Wang, D.; Tao, Y.; Lai, Q.H.; Wong, R.T.K.; Zobaa, A.F.; Wu, R.; Lai, L.L. A Review of Technical Standards for Smart Cities. Clean Technol. 2020, 2, 290–310. [Google Scholar] [CrossRef]
- Rizi MH, P.; Seno SA, H. A systematic review of technologies and solutions to improve security and privacy protection of citizens in the smart city. Internet Things 2022, 20, 100584. [Google Scholar] [CrossRef]
- Orłowski, C. Management of IoT Open Data Projects in Smart Cities Cezary Orlowski; Academic Press: London, UK, 2021. [Google Scholar]
- Popkova, E.G.; Polukhin, A.A.; Ragulina, J.V. Towards an Increased Security: Green Innovations, Intellectual Property Protection and Information Security; Springer International Publishing: Cham, Switzerland, 2022; Volume 372. [Google Scholar]
- Srebalová, M.; Peráček, T. Effective Public Administration as a Tool for Building Smart Cities: The Experience of the Slovak Republic. Laws 2022, 11, 67. [Google Scholar] [CrossRef]
- Cagáňová, D. Smart Technology Trends in Industrial and Business Management Edited by Dagmar Cagáňová, Michal Balog, 1st ed.; Knapčíková, L., Soviar, J., Mezarcıöz, S., Cagáňová, D., Eds.; Springer International Publishing: Cham, Switzerland, 2019. [Google Scholar]
- Yigitcanlar, T.; Yigitcanlar, T. Reviews and Perspectives on Smart and Sustainable Metropolitan and Regional Cities; MDPI—Multidisciplinary Digital Publishing Institute: Basel, Switzerland, 2021. [Google Scholar]
- Lacinák, M.; Ristvej, J. Smart City, Safety and Security. Procedia Eng. 2017, 192, 522–527. [Google Scholar] [CrossRef]
- Fabrègue, B.F.G.; Bogoni, A. Privacy and Security Concerns in the Smart City. Smart Cities 2023, 6, 586–613. [Google Scholar] [CrossRef]
- Sicari, S.; Rizzardi, A.; Grieco, L.A.; Coen-Porisini, A. Security, privacy and trust in Internet of Things: The road ahead. Comput. Netw. 2015, 1999, 76146–76164. [Google Scholar] [CrossRef]
- Gharaibeh, A.; Salahuddin, M.A.; Hussini, S.J.; Khreishah, A.; Khalil, I.; Guizani, M.; Al-Fuqaha, A. Smart Cities: A Survey on Data Management, Security, and Enabling Technologies. IEEE Commun. Surv. Tutor. 2017, 19, 2456–2501. [Google Scholar] [CrossRef]
- Zhang, K.; Ni, J.; Yang, K.; Liang, X.; Ren, J.; Shen, X.S. Security and Privacy in Smart City Applications: Challenges and Solutions. IEEE Commun. Mag. 2017, 55, 122–129. [Google Scholar] [CrossRef]
- Eckhoff, D.; Wagner, I. Privacy in the Smart City-Applications, Technologies, Challenges, and Solutions. IEEE Commun. Surv. Tutor. 2018, 20, 489–516. [Google Scholar] [CrossRef]
- Bolivar, M.P.R.; Meijer, A.J. Smart Governance: Using a Literature Review and Empirical Analysis to Build a Research Model. Soc. Sci. Comput. Rev. 2016, 34, 673–692. [Google Scholar] [CrossRef]
- Vitálišová, K.; Vaňová, A.; Borseková, K.; Nagyová, Ľ.; Cagáňová, D. Tools of Smart Governance in Cities of the Slovak Republic. In Science and Technologies for Smart Cities; Springer International Publishing: Cham, Switzerland, 2019; pp. 369–387. [Google Scholar]
- Shaw, S.-L.; Sui, D. Human Dynamics Research in Smart and Connected Communities; Springer International Publishing AG: Cham, Switzerland, 2018. [Google Scholar]
- Vinod Kumar, T.M. (Ed.) Smart Economy in Smart Cities: International Collaborative Research: Ottawa, St. Louis, Stuttgart, Bologna, Cape Town, Nairobi, Dakar, Lagos, New Delhi, Varanasi, Vijayawada, Kozhikode, Hong Kong, 1st ed.; Springer: Singapore, 2017. [Google Scholar]
- Mboup, G.; Oyelaran-Oyeyinka, B. (Eds.) Smart Economy in Smart African Cities Sustainable, Inclusive, Resilient and Prosperous, 1st ed.; Springer: Singapore, 2019. [Google Scholar]
- Li, X.; Lu, R.; Liang, X.; Shen, X.; Chen, J.; Lin, X. Smart community: An internet of things application. IEEE Commun. Mag. 2011, 49, 68–75. [Google Scholar] [CrossRef]
- Sheina, S.; Fedorovskaya, A.; Yudina, K. Smart City: Comfortable Living Environment. IOP Conf. Ser. Mater. Sci. Eng. 2018, 463, 32095. [Google Scholar] [CrossRef]
- Cui, L.; Xie, G.; Qu, Y.; Gao, L.; Yang, Y. Security and Privacy in Smart Cities: Challenges and Opportunities. IEEE Access 2018, 6, 46134–46145. [Google Scholar] [CrossRef]
- Zhao, W.; Luo, X.; Qiu, T. (Eds.) Recent Developments in Smart Healthcare; MDPI—Multidisciplinary Digital Publishing Institute: Basel, Switzerland, 2018. [Google Scholar]
- Ševcová, K. Digitalization of the Health Care System in the Slovak Republic. Rev. Int. Jurídica Empresarial 2020, 3, 45–60. [Google Scholar] [CrossRef]
- Kostakos, V.; Ojala, T.; Juntunen, T. Traffic in the Smart City: Exploring City—Wide Sensing for Traffic Control Center Augmentation. IEEE Internet Comput. 2013, 17, 22–29. [Google Scholar] [CrossRef]
- Golej, J.; Pánik, M.; Špirková, D.; Adamuscin, A. Smart Mobility in Urban Development. In Advances in Human Factors in Architecture, Sustainable Urban Planning and Infrastructure; Springer International Publishing: Cham, Switzerland, 2020; pp. 192–198. [Google Scholar]
- Ristvej, J.; Lacinák, M.; Ondrejka, R. On Smart City and Safe City Concepts. Mobile Networks and Applications. Mob. Netw. Appl. 2020, 25, 2020. [Google Scholar] [CrossRef]
- Rehak, D.; Hromada, M.; Lovecek, T. Personnel Threats in an Electric Power Critical Infrastructure Sector and Their Impacts on Dependent Sectors. Saf. Sci. 2020, 127, 104698. [Google Scholar] [CrossRef]
- Janíček, F.; Perný, M.; Šály, V.; Váry, M.; Breza, J.; Chochol, P. The role of smart grid in integrating the renewable energies in Slovakia. Energy Environ. 2018, 29, 300–312. [Google Scholar] [CrossRef]
- Shen, Z.; Huang, L.; Peng, K.H.; Pai, J. (Eds.) Green City Planning and Practices in Asian Cities Sustainable Development and Smart Growth in Urban Environments, 1st ed.; Springer International Publishing: Cham, Switzerland, 2018. [Google Scholar]
- Brezula, J. Aspects of cyber security in Slovakia and in the world. Krízový Manažment 2017, 16, 83–88. [Google Scholar] [CrossRef]
- Ahram, T.; Taiar, R. Human Interaction, Emerging Technologies and Future Applications III. In Proceedings of the 3rd International Conference on Human Interaction and Emerging Technologies: Future Applications (IHIET 2020), Paris, France, 27–29 August 2020; Ahram, T., Taiar, R., Langlois, K., Choplin, A., Eds.; Springer International Publishing: Cham, Switzerland, 2021. [Google Scholar]
- Yarali, A. (Ed.) Intelligent Connectivity: AI, IoT, and 5G; Wiley: Hoboken, NJ, USA, 2022. [Google Scholar]
- Dogra, R.; Rani, S.; Sharma, B.; Verma, S. Essence of Scalability in Wireless Sensor Network for Smart City Applications. IOP Conf. Ser. Mater. Sci. Eng. 2021, 1022, 12094. [Google Scholar] [CrossRef]
- Haj Qasem, M.; AlMobaideen, W. Heterogeneity in IoT-based Smart Cities Designs. Int. J. Interact. Mob. Technol. 2019, 13, 210–225. [Google Scholar] [CrossRef]
- Šulyová, D.; Kubina, M. Integrated management of limited water resources in Smart Cities. IOP Conf. Ser. Earth Environ. Sci. 2022, 1077, 012003. [Google Scholar] [CrossRef]
- Kulhari, S. (Ed.) Building-Blocks of a Data Protection Revolution: The Uneasy Case for Blockchain Technology to Secure Privacy and Identity, 1st ed.; Nomos Verlagsgesellschaft mbH & Co. KG: Baden-Baden, Germany, 2018. [Google Scholar]
- Kampova, K.; Lovecek, T.; Rehak, D. Quantitative approach to physical protection systems assessment of critical infrastructure elements: Use case in the Slovak Republic. Int. J. Crit. Infrastruct. Prot. 2020, 30, 100376. [Google Scholar] [CrossRef]
- Sheng, Z.; Yang, S.; Yu, Y.; Vasilakos, A.V.; McCann, J.A.; Leung, K.K. A survey on the ietf protocol suite for the internet of things: Standards, challenges, and opportunities. IEEE Wirel. Commun. 2013, 20, 91–98. [Google Scholar] [CrossRef]
- Xu, K.; Wang, X.; Wei, W.; Song, H.; Mao, B. Toward software defined smart home. IEEE Commun. Mag. 2016, 54, 116–122. [Google Scholar] [CrossRef]
- Biswas, K.; Muthukkumarasamy, V. Securing Smart Cities Using Blockchain Technology. In Proceedings of the 2016 IEEE 18th International Conference on High Performance Computing and Communications; IEEE 14th International Conference on Smart City; IEEE 2nd International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Sydney, Australia, 12–14 December 2016; pp. 1392–1393. [Google Scholar]
- Kasaraneni, P.P.; Yellapragada, V.P.K.; Moganti, G.L.K.; Flah, A. Analytical Enumeration of Redundant Data Anomalies in Energy Consumption Readings of Smart Buildings with a Case Study of Darmstadt Smart City in Germany. Sustainability 2022, 14, 10842. [Google Scholar] [CrossRef]
- Visvizi, A.; Lytras, M.D. (Eds.) Sustainable Smart Cities and Smart Villages Research; MDPI—Multidisciplinary Digital Publishing Institute: Basel, Switzerland, 2018. [Google Scholar]
- Yigitcanlar, T.; Han, H.; Kamruzzaman, M. Approaches, Advances and Applications in Sustainable Development of Smart Cities; MDPI—Multidisciplinary Digital Publishing Institute: Basel, Switzerland, 2020. [Google Scholar]
- Kitchenham, B.A. Procedures for Performing Systematic Reviews. Joint Technical Report, Computer Science Department, Keele University (TR/SE0401) and National ICT Australia Ltd. (0400011T.1). 2004. Available online: http://www.inf.ufsc.br/~aldo.vw/kitchenham.pdf (accessed on 27 February 2020).
- Moher, D.; Liberati, A.; Tetzlaff, J.; Altman, D.G. Preferred Reporting Items for Systematic Reviews and Meta-Analyses: The PRISMA Statement. Ann. Intern. Med. 2009, 151, 264–269. [Google Scholar] [CrossRef] [PubMed]
- O’Brien, A.M.; Mc Guckin, C. The Systematic Literature Review Method: Trials and Tribulations of Electronic Database Searching at Doctoral Level; O’Brien, A.M., Ed.; SAGE Publications: London, UK, 2016. [Google Scholar]
- Boland, A.; Cherry, G.; Dickson, R. (Eds.) Doing a Systematic Review: A Student’s Guide, 2nd ed.; SAGE: Los Angeles, CA, USA, 2017. [Google Scholar]
- Hesse-Biber, S.N.; Johnson, B. (Eds.) The Oxford Handbook of Multimethod and Mixed Methods Research Inquiry; Oxford University Press: New York, NY, USA, 2016. [Google Scholar]
- Heyvaert, M.; Hannes, K.; Onghena, P. (Eds.) Using Mixed Methods Research Synthesis for Literature Reviews; SAGE: Los Angeles, CA, USA, 2017. [Google Scholar]
- Singh, S.; Sharma, P.K.; Moon, S.Y.; Moon, D.; Park, J.H. A comprehensive study on APT attacks and countermeasures for future networks and communications: Challenges and solutions. J. Supercomput. 2019, 75, 4543–4574. [Google Scholar] [CrossRef]
- Alandjani, G. Features and Potential Security Challenges for IoT Enabled Devices in Smart City Environment. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 8. [Google Scholar] [CrossRef]
- Belous, A.; Saladukha, V. (Eds.) Viruses, Hardware and Software Trojans Attacks and Countermeasures, 1st ed.; Springer International Publishing: Cham, Switzerland, 2020. [Google Scholar]
- da Costa, K.A.P.; Papa, J.P.; Lisboa, C.O. Internet of Things: A survey on machine learning-based intrusion detection approaches. Comput. Netw. 1999, 151, 147–157. [Google Scholar] [CrossRef]
- Siman, B. Hybrid Warfare Is Not Synonymous with Cyber: The Threat of Influence Operations; EGMONT Royal Institute for International Relations: Brussels, Belgium, 2022. [Google Scholar]
- Ying, B. Privacy preserving broadcast message authentication protocol for VANETs. J. Netw. Comput. Appl. 2013, 36, 1352–1364. [Google Scholar] [CrossRef]
- Al-Dhubhani, R.; Mehmood, R.; Katib, I.; Algarni, A. Location Privacy in Smart Cities Era. In Smart Societies, Infrastructure, Technologies and Applications; Springer International Publishing: Cham, Switzerland, 2018; pp. 123–138. [Google Scholar]
- Antonopoulos, K.; Petropoulos, C.; Antonopoulos, C.P.; Voros, N. Security Data Management Process and Its Impact on Smart Cities’ Wireless Sensor Networks. In Proceedings of the 2017 South Eastern European Design Automation, Computer Engineering, Computer Networks and Social Media Conference (SEEDA-CECNSM) 2017, Preveza, Greece, 23–25 September 2017; pp. 1–8. [Google Scholar]
- Beltran, V.; Martinez, J.A.; Skarmeta, A. User-Centric Access Control for Efficient Security in Smart Cities. In Proceedings of the 2017 Global Internet of Things Summit (GIoTS), Geneva, Switzerland, 6–9 June 2017; IEEE: Piscataway, NJ, USA; pp. 1–6. [Google Scholar]
- Ali, H.; Elzeki, O.M.; Elmougy, S. Smart Attacks Learning Machine Advisor System for Protecting Smart Cities from Smart Threats. Appl. Sci. 2022, 12, 6473. [Google Scholar] [CrossRef]
- Huang, Q.; Wang, L.; Yang, Y. Secure and Privacy-Preserving Data Sharing and Collaboration in Mobile Healthcare Social Networks of Smart Cities. Secur. Commun. Netw. 2017, 2017, 6426495. [Google Scholar] [CrossRef]
- Gheisari, M.; Wang, G.; Khan, W.Z.; Fernández-Campusano, C. A context-aware privacy-preserving method for IoT-based smart city using Software Defined Networking. Comput. Secur. 2019, 87, 101470. [Google Scholar] [CrossRef]
- Alromaihi, S.; Elmedany, W.; Balakrishna, C. Cyber Security Challenges of Deploying IoT in Smart Cities for Healthcare Applications. In Proceedings of the 2018 6th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Barcelona, Spain, 6–8 August 2018; pp. 140–145. [Google Scholar]
- Gressel, G. Protecting Europe against Hybrid Threats; European Council on Foreign Relations: Berlin, Germany, 2022. [Google Scholar]
- Sweijs, T. Framework for Cross-Domain Strategies Against Hybrid Threats; Hague Centre for Strategic Studies: The Haag, The Netherlands, 2022. [Google Scholar]
- Sarri, A.; Kyranoudi, P. Good Practices in Innovation on Cybersecurity under the NCSS: Good Practices in Innovation on Cybersecurity under the National Cyber Security Strategies; ENISA_2: Heraklion, Greece, 2019. [Google Scholar]
- Nicholson, D. Advances in Human Factors in Cybersecurity. In Proceedings of the AHFE 2017 International Conference on Human Factors in Cybersecurity, Los Angeles, CA, USA, 17−21 July 2017, 1st ed.; Nicholson, D., Ed.; Springer International Publishing: Cham, Switzerland, 2018. [Google Scholar]
- Poehlmann, N.; Caramancion, K.M.; Tatar, I.; Merz, T. The Organizational Cybersecurity Success Factors: An Exhaustive Literature Review. In Advances in Security, Networks, and Internet of Things; Springer International Publishing: Cham, Switzerland, 2021; pp. 377–395. [Google Scholar]
- Kalyani, G.; Chaudhari, S. An efficient approach for enhancing security in Internet of Things using the optimum authentication key. Int. J. Comput. Appl. 2020, 42, 306–314. [Google Scholar] [CrossRef]
- Chatterjee, S.; Kar, A.K.; Gupta, M.P. Alignment of IT Authority and Citizens of Proposed Smart Cities in India: System Security and Privacy Perspective. Glob. J. Flex. Syst. Manag. 2018, 19, 95–107. [Google Scholar] [CrossRef]
- Sengan, S.; Subramaniyaswamy, V.; Nair, S.K.; Indragandhi, V.; Manikandan, J.; Ravi, L. Enhancing cyber–physical systems with hybrid smart city cyber security architecture for secure public data-smart network. Future Gener. Comput. Syst. 2020, 112724–112737. [Google Scholar] [CrossRef]
- National Security Authority. National Cyber Strategy Security for the Years 2021 to 2025. Available online: https://www.nbu.gov.sk/wp-content/uploads/cyber-security/National_cybersecurity_strategy_2021.pdf (accessed on 12 December 2022).
- Kamil, H.; Burita, L.; Kozak, P. Overview of Cyber Threats in Central European Countries. In Proceedings of the 2021 Communication and Information Technologies (KIT), Vysoke Tatry, Slovakia, 13–15 October 2021; pp. 1–6. [Google Scholar]
- Sharma, A.; Singh, Y. On Security of Opportunistic Routing Protocol in Wireless Sensor Networks. In Proceedings of ICRIC 2019; Springer International Publishing: Cham, Switzerland, 2019; pp. 407–419. [Google Scholar]
- Nagy, M. Cyber Security Strategies of the Visegrád Group States and Romania. Acta Univ. Sapientiae Eur. Reg. Stud. 2021, 19, 72–87. [Google Scholar] [CrossRef]
- Fadlullah, Z.M.; Khan Pathan, A.-S. (Eds.) Combating Security Challenges in the Age of Big Data Powered by State-of-the-Art Artificial Intelligence Techniques, 1st ed.; Springer International Publishing: Cham, Switzerland, 2020. [Google Scholar]
- Viano, E.C. (Ed.) Cybercrime, Organized Crime, and Societal Responses International Approaches, 1st ed.; Springer International Publishing: Cham, Switzerland, 2017. [Google Scholar]
- Vitunskaite, M.; He, Y.; Brandstetter, T.; Janicke, H. Smart cities and cyber security: Are we there yet? A comparative study on the role of standards, third party risk management and security ownership. Comput. Secur. 2019, 83, 313–331. [Google Scholar] [CrossRef]
- Sanduleac, M. Energy ecosystem in smart cities—Privacy and security solutions for citizen’s engagement in a multi-stream environment. In Proceedings of the 2016 IEEE International Smart Cities Conference (ISC2), Trento, Italy, 12–15 September 2016; pp. 1–4. [Google Scholar]
- Van den Broek, T.; van Veenstra, A.F. Governance of big data collaborations: How to balance regulatory compliance and disruptive innovation. Technol. Forecast. Soc. Change 2018, 129, 330–338. [Google Scholar] [CrossRef]

| Layer | Threat | Countermeasure |
|---|---|---|
| sensors | physical attacks on heterogeneous devices, hacking | robustness, monitoring, ubiquity |
| data | unauthorised access, eavesdropping, spoofing *, physical threats caused by environment and people | multi-factor verification and authentication, encryption, cryptography |
| network | malicious code insertion, signal jamming, wide range of hacking and cyber attacks, spoofing, sniffing ° | data encryption, antivirus |
| computing | denial of service, unauthorised access, insider threat, insecure software services | monitoring |
| services | DDoS, malicious code insertion, phishing, social engineering, spyware, cache overflow, backdoor, botnet | antiviruses, filters, user education, anti-DDoS measures |
| acceptance | influencing, lack of explainability, trust or meaningful control over systems | communication, training and education, user interfaces |
| System | Threat | Security Trends | Challenges |
|---|---|---|---|
| governance | combined attacks, extortion, insecurity, abuse | blockchain, cloudification, increase in computing capacity | Data immutability in blockchain depends on the distribution of nodes in a network. No entity shall own more than half. |
| residents | extortion, insecurity, abuse, information fusion, profiling, localisation, impersonation | biometrics, encryption, cryptography, data minimisation, anonymisation | Biometric databases represent a single point of failure. Biometrics are inherently publicly accessible. |
| economy | combined attacks, change of ownership, insecurity | blockchain, cloudification, artificial intelligence, machine learning | Cloudification increases latency, limits scalability, and creates a single point of failure. |
| housing | change of ownership, insecurity, profiling, localisation, identification | encryption, cryptography, security standards, attestation, authentication and validation | Cryptography is efficient but computationally intensive for personal devices. |
| healthcare | malware, phishing, insecurity, hacking, bioterrorism, ransomware | biometrics, robust artificial intelligence and machine learning models | Regulating adaptive AI algorithms. Periodically updating and configuring devices. |
| transportation | change of ownership, insecurity, profiling, localisation, identification | robust artificial intelligence and machine learning models, advanced mathematical models | The robustness of AI-based models depends on the amount of annotated and raw data used to train them. |
| environment | combined attacks, insecurity | sensorisation, artificial intelligence, machine learning | Periodically updating and configuring sensors. Standardisation and quality control. |
| finance | ransomware, phishing, spoofing, fraud, social engineering | multi-form authentication | Deploying digital currencies and modernising payment systems. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kollarova, M.; Granak, T.; Strelcova, S.; Ristvej, J. Conceptual Model of Key Aspects of Security and Privacy Protection in a Smart City in Slovakia. Sustainability 2023, 15, 6926. https://doi.org/10.3390/su15086926
Kollarova M, Granak T, Strelcova S, Ristvej J. Conceptual Model of Key Aspects of Security and Privacy Protection in a Smart City in Slovakia. Sustainability. 2023; 15(8):6926. https://doi.org/10.3390/su15086926
Chicago/Turabian StyleKollarova, Michaela, Tomas Granak, Stanislava Strelcova, and Jozef Ristvej. 2023. "Conceptual Model of Key Aspects of Security and Privacy Protection in a Smart City in Slovakia" Sustainability 15, no. 8: 6926. https://doi.org/10.3390/su15086926
APA StyleKollarova, M., Granak, T., Strelcova, S., & Ristvej, J. (2023). Conceptual Model of Key Aspects of Security and Privacy Protection in a Smart City in Slovakia. Sustainability, 15(8), 6926. https://doi.org/10.3390/su15086926










