A Robust Fuzzy Equilibrium Optimization-Based ROI Selection and DWT-Based Multi-Watermarking Model for Medical Images
Abstract
1. Introduction
Motivation and Contribution
- The fuzzy equilibrium optimization (FEO) algorithm is proposed to provide secure, reliable and unbreakable watermarking for medical images.
- The medical image dataset is selected, which includes magnetic resonance imaging (MRI) images, computed tomography (CT) images and ultrasound (US) images for analysing the image quality.
- For determining the performance rate, a few performance evaluation measures such as embedding rate, embedding time, extraction time, coefficient index and entropy index are utilized.
2. Literature Survey
3. Basic Concepts
3.1. Fuzzy Logic
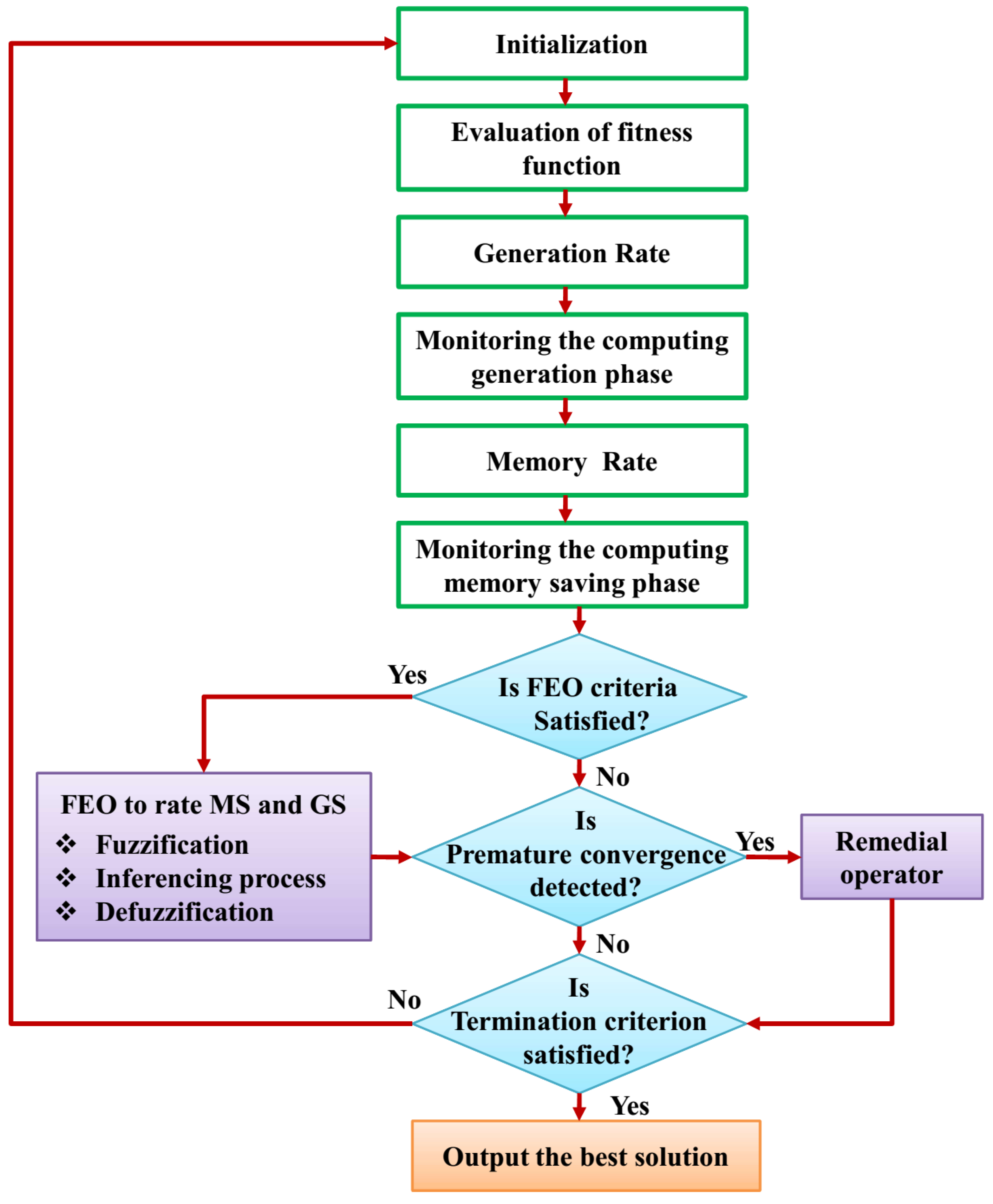
3.2. Equilibrium Optimizer (EO)
- i.
- B1 rules the algorithm’s exploration ability and determines the potentiality of the equilibrium candidate’s new position. As the value of B1 increases, the exploration capability also increases. Moreover, the performance of the exploration is degraded by a number greater than three. B1 is large enough in expanding the exploration ability because of its ability in magnifying the concentration variable. The sum of the cognitive and social parameters must be less than or equal to four in PSO.
- ii.
- Sign (q − 0.5): The direction of exploration is controlled by sign. There is an equal possibility of positive and negative signs because of q in the range of [0, 1] along with uniform distribution.
- iii.
- Generation Probability (GP = 1): The generation rate updated the concentration’s participation probability, which is already controlled by GP. In the process of optimization, no participation of the generation rate term is represented as GP = 1. This condition reveals the greater ability of exploration and results in inaccurate solutions. Moreover, the participation of the generation rate term in the optimization process is denoted as GP = 1. It maximizes the stagnation probability in local optima. A good balance between exploitation and exploration is offered by GP = 0.5, on the basis of empirical testing.
- iv.
- Equilibrium Pool: The five particle is contained in this vector and the choosing of these particles is based on empirical testing. The distance between the candidates is very far from each other in the initial iterations. On the basis of these candidates, the concentrations are updated and enhance the ability of the algorithm in order to discover the space. In the initial iterations, the unknown search is discovered with the help of the average particle, as the particles are distant from each other.
- a.
- B2 is the same as B1 that rules the exploitation feature and determines the exploitation’s magnitude by obtaining the best solution around.
- b.
- The r − 0.5 rules regarding the quality of exploitation and the local search direction are specified.
- c.
- Memory saving: The best particles which very far are saved by the memory saving and replaced by the worse particles. Moreover, these features enhance the ability of EO for exploitation.
- d.
- Equilibrium pool: The fade in of exploitation and fade out of exploration happens in the iteration lapse. Finally, the equilibrium candidates are very near each other in the final iteration and the concentration updating process helps the candidates around in the local search, resulting in exploitation.
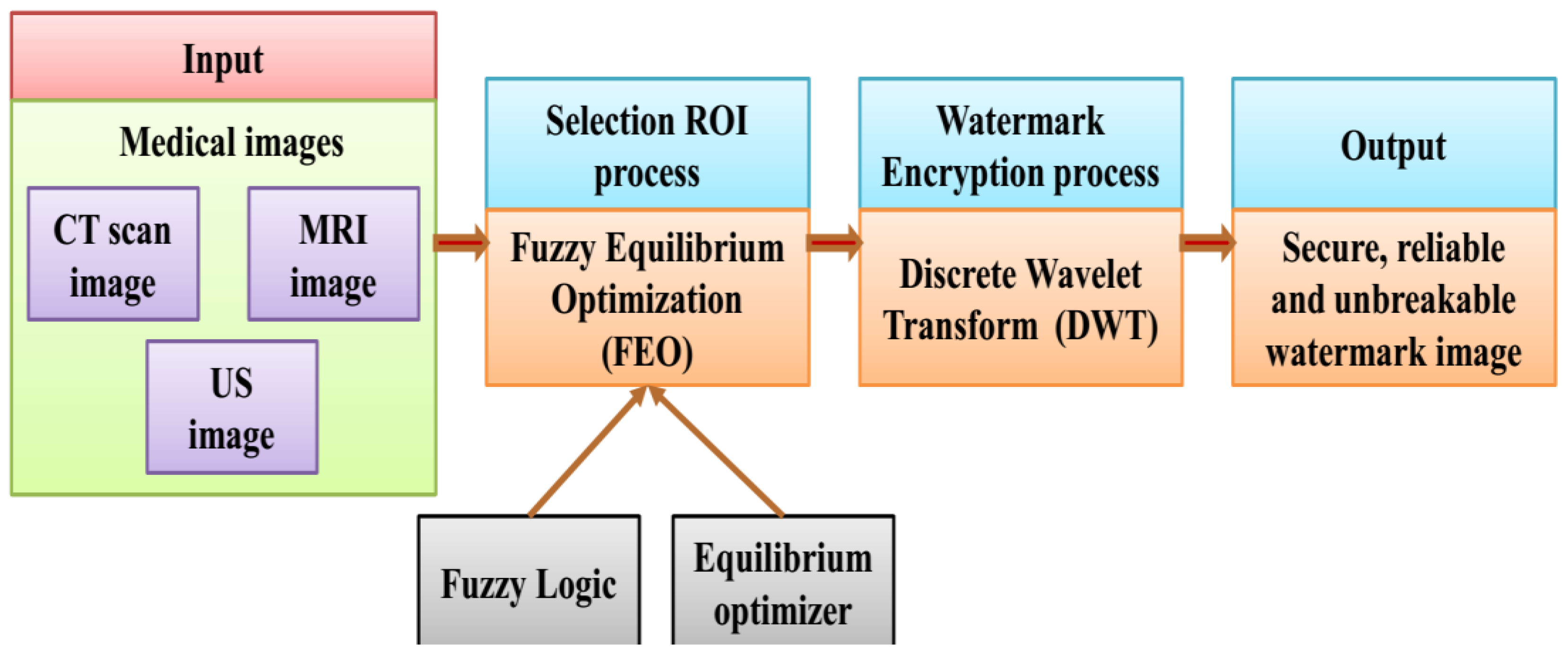
4. Proposed Methodology
4.1. Fuzzy Equilibrium-Based Region of Interest (ROI) Selection
- I.
- The movement of the bar is neutral when the success rate of the memory rate and generation rate is low.
- II.
- The movement of the bar is left, when the success rate of the generation rate and memory rate is low and medium.
- III.
- The bar movement is far-left if the success rate of the generation rate and memory rate is low and high.
- IV.
- The bar movement is right, as the generation rate and memory rate are medium and low.
- V.
- The movement of the bar is neutral when the generation rate and memory rate are medium.
- VI.
- The movement of the bar is left, when the generation rate and memory rate are medium and high.
- VII.
- The bar movement is right, as the generation rate and memory rate are high and low.
- VIII.
- The bar movement is right, as the generation rate and memory rate are high and medium.
- IX.
- If the success rate of memory rate and generation rate is high, then the movement of the bar is neutral.
4.2. Discrete Wavelet Transform (DWT) Based Watermark Encryption Process
4.3. Embedded and Extracted Method of the Watermarking
Watermark Extraction
5. Experimental Analysis and Discussions
5.1. Experimental Setup
5.2. Dataset Description
5.3. Parameter Settings
5.4. Performance Evaluation Measures
5.5. Performance Evaluation
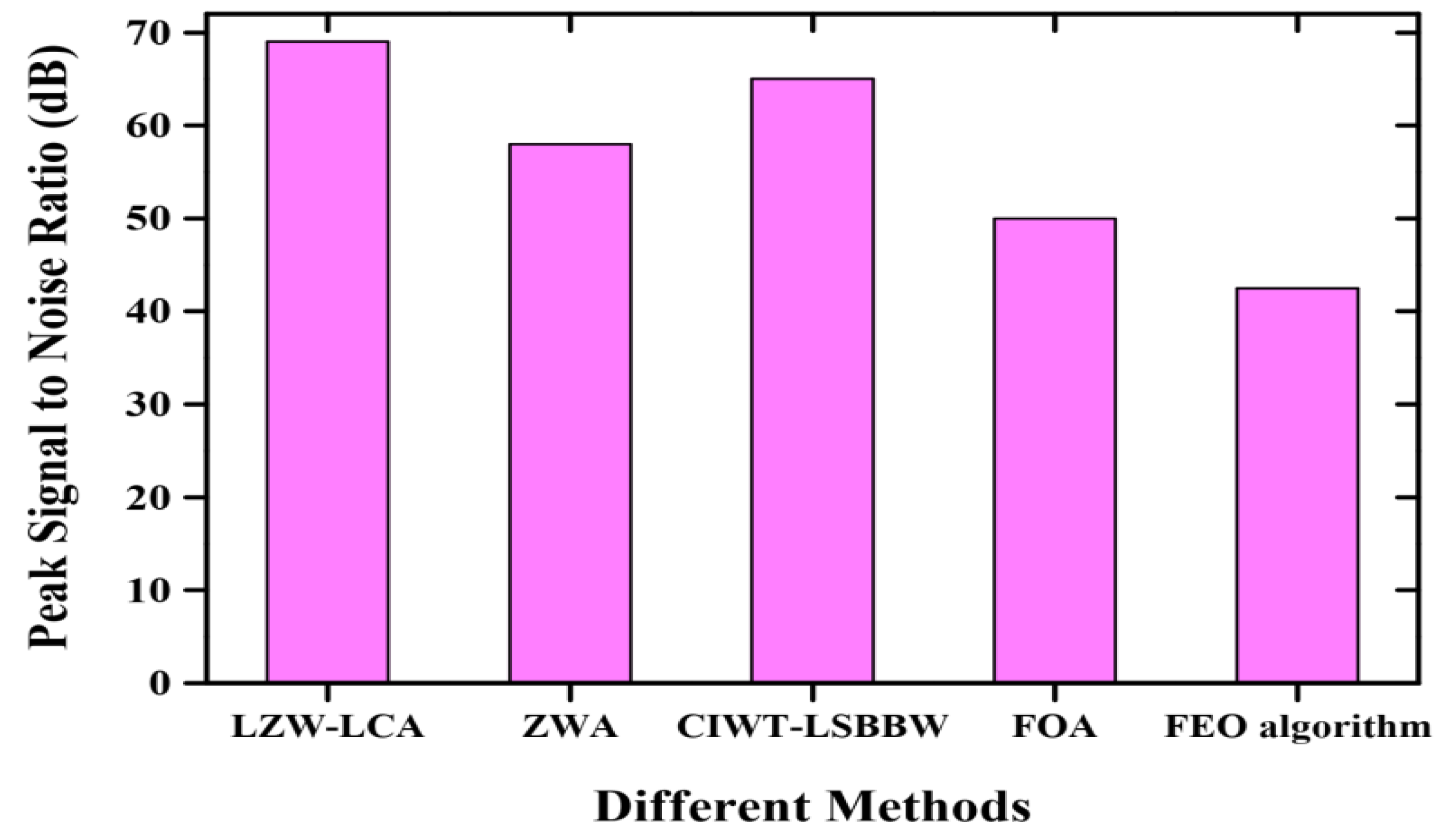
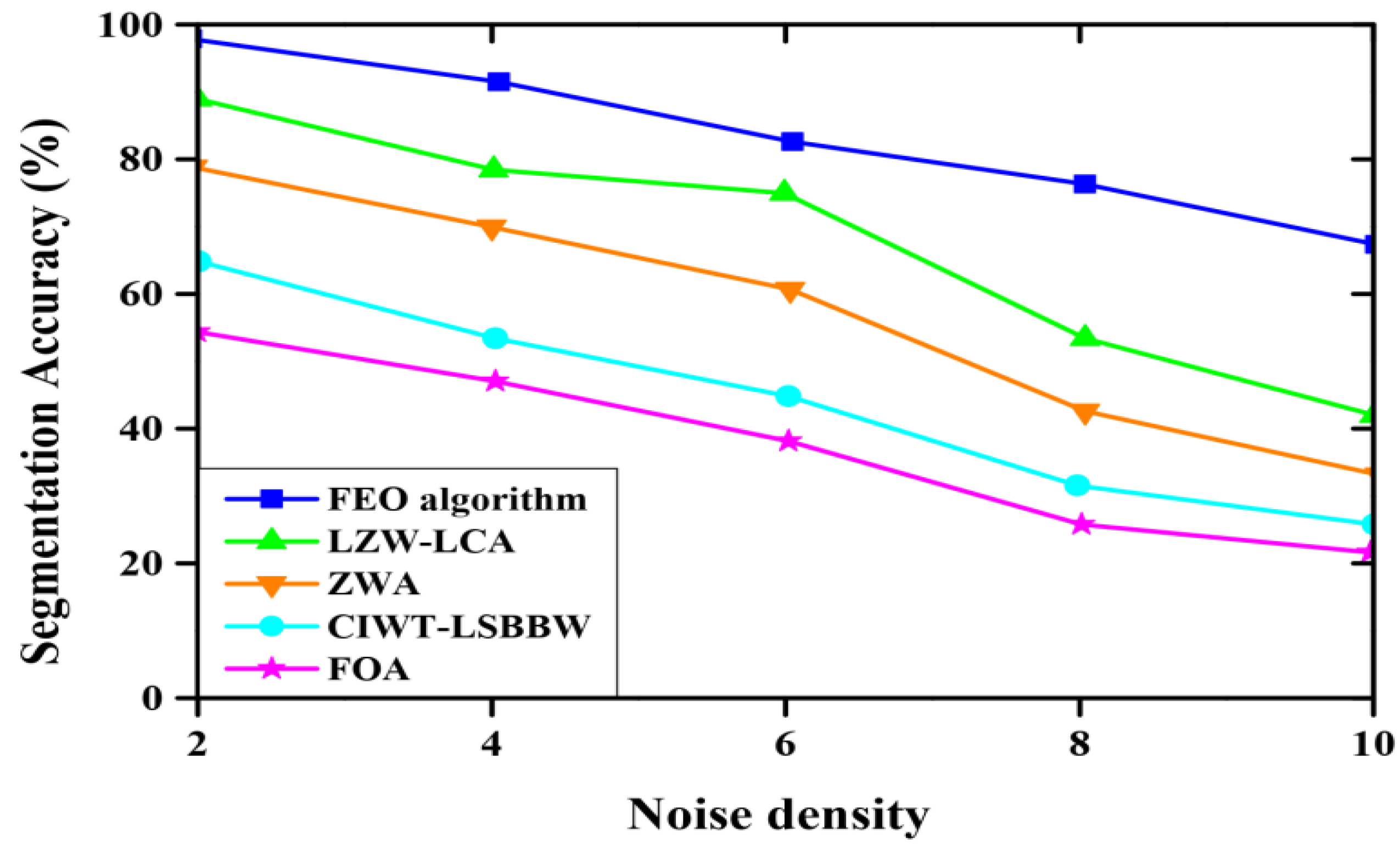
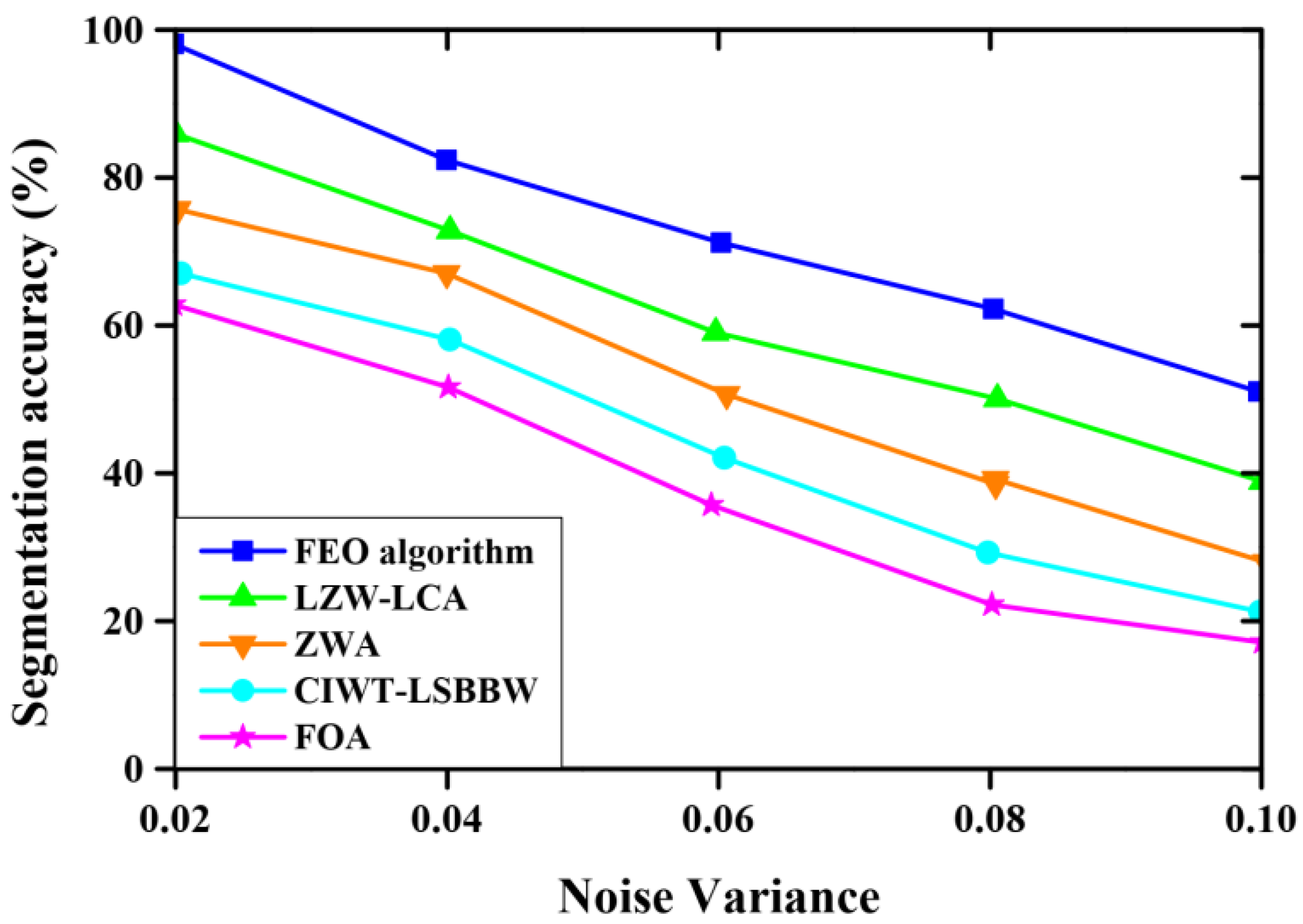
5.6. Comparative Analysis
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Balasamy, K.; Suganyadevi, S. A fuzzy based ROI selection for encryption and watermarking in medical image using DWT and SVD. Multimed. Tools Appl. 2021, 80, 7167–7186. [Google Scholar]
- Sinhal, R.; Sharma, S.; Ansari, I.A.; Bajaj, V. Multipurpose medical image watermarking for effective security solutions. Multimed. Tools Appl. 2022, 81, 14045–14063. [Google Scholar] [CrossRef]
- Ravichandran, D.; Praveenkumar, P.; Rajagopalan, S.; Rayappan, J.B.B.; Amirtharajan, R. ROI-based medical image watermarking for accurate tamper detection, localisation and recovery. Med. Biol. Eng. Comput. 2021, 59, 1355–1372. [Google Scholar] [CrossRef] [PubMed]
- Dai, Z.; Lian, C.; He, Z.; Jiang, H.; Wang, Y. A novel hybrid reversible-zero watermarking scheme to protect medical image. IEEE Access 2022, 10, 58005–58016. [Google Scholar] [CrossRef]
- Borra, S.; Thanki, R. Crypto-watermarking scheme for tamper detection of medical images. Comput. Methods Biomech. Biomed. Eng. Imaging Vis. 2020, 8, 345–355. [Google Scholar] [CrossRef]
- Iwendi, C.; Jalil, Z.; Javed, A.R.; Reddy, T.; Kaluri, R.; Srivastava, G.; Jo, O. Keysplitwatermark: Zero watermarking algorithm for software protection against cyber-attacks. IEEE Access 2020, 8, 72650–72660. [Google Scholar] [CrossRef]
- Cedillo-Hernandez, M.; Cedillo-Hernandez, A.; Nakano-Miyatake, M.; Perez-Meana, H. Improving the management of medical imaging by using robust and secure dual watermarking. Biomed. Signal Process. Control 2020, 56, 101695. [Google Scholar] [CrossRef]
- Wang, W.; Xu, H.; Alazab, M.; Gadekallu, T.R.; Han, Z.; Su, C. Blockchain-based reliable and efficient certificateless signature for IIoT devices. IEEE Trans. Ind. Inform. 2021, 18, 7059–7067. [Google Scholar] [CrossRef]
- Alshanbari, H.S. Medical image watermarking for ownership & tamper detection. Multimed. Tools Appl. 2021, 80, 16549–16564. [Google Scholar]
- Thakur, S.; Singh, A.K.; Ghrera, S.P. NSCT domain–based secure multiple-watermarking technique through lightweight encryption for medical images. Concurr. Comput. Pract. Exp. 2021, 33, e5108. [Google Scholar] [CrossRef]
- Swaraja, K.; Meenakshi, K.; Kora, P. An optimized blind dual medical image watermarking framework for tamper localization and content authentication in secured telemedicine. Biomed. Signal Process. Control 2020, 55, 101665. [Google Scholar]
- Liu, X.; Lou, J.; Fang, H.; Chen, Y.; Ouyang, P.; Wang, Y.; Zou, B.; Wang, L. A novel robust reversible watermarking scheme for protecting authenticity and integrity of medical images. IEEE Access 2019, 7, 76580–76598. [Google Scholar] [CrossRef]
- Zeng, C.; Liu, J.; Li, J.; Cheng, J.; Zhou, J.; Nawaz, S.A.; Xiao, X.; Bhatti, U.A. Multi-watermarking algorithm for medical image based on KAZE-DCT. J. Ambient. Intell. Humaniz. Comput. 2022, 1–9. [Google Scholar] [CrossRef]
- Patel, N.; Dwivedi, V.V.; Kothari, A. Hybrid Dct-Dwt Based Roi Medical Image Compression for Telemedicine Application. Image 2020, 8, 8. [Google Scholar] [CrossRef]
- Hu, K.; Wang, X.; Hu, J.; Wang, H.; Qin, H. A novel robust zero-watermarking algorithm for medical images. Vis. Comput. 2021, 37, 2841–2853. [Google Scholar] [CrossRef]
- Nazari, M.; Mehrabian, M. A novel chaotic IWT-LSB blind watermarking approach with flexible capacity for secure transmission of authenticated medical images. Multimed. Tools Appl. 2021, 80, 10615–10655. [Google Scholar] [CrossRef]
- Gong, C.; Li, J.; Bhatti, U.A.; Gong, M.; Ma, J.; Huang, M. Robust and secure zero-watermarking algorithm for medical images based on Harris-SURF-DCT and chaotic map. Secur. Commun. Netw. 2021, 2021, 3084153. [Google Scholar] [CrossRef]
- Dhall, S.; Gupta, S. Multilayered highly secure authentic watermarking mechanism for medical applications. Multimed. Tools Appl. 2021, 80, 18069–18105. [Google Scholar] [CrossRef]
- Song, Q.; Zhao, Q.; Wang, S.; Liu, Q.; Chen, X. Dynamic path planning for unmanned vehicles based on fuzzy logic and improved ant colony optimization. IEEE Access 2020, 8, 62107–62115. [Google Scholar] [CrossRef]
- Faramarzi, A.; Heidarinejad, M.; Stephens, B.; Mirjalili, S. Equilibrium optimizer: A novel optimization algorithm. Knowl.-Based Syst. 2020, 191, 105190. [Google Scholar] [CrossRef]
- Cheng, M.Y.; Prayogo, D. A novel fuzzy adaptive teaching–learning-based optimization (FATLBO) for solving structural optimization problems. Eng. Comput. 2017, 33, 55–69. [Google Scholar] [CrossRef]
- Rejeesh, M.R. Interest point based face recognition using adaptive neuro fuzzy inference system. Multimed. Tools Appl. 2019, 78, 22691–22710. [Google Scholar] [CrossRef]
- Liu, Y.; Guan, L.; Hou, C.; Han, H.; Liu, Z.; Sun, Y.; Zheng, M. Wind power short-term prediction based on LSTM and discrete wavelet transform. Appl. Sci. 2019, 9, 1108. [Google Scholar] [CrossRef]
- Clark, K.; Vendt, B.; Smith, K.; Freymann, J.; Kirby, J.; Koppel, P.; Moore, S.; Phillips, S.; Maffitt, D.; Pringle, M.; et al. The Cancer Imaging Archive (TCIA): Maintaining and Operating a Public Information Repository. J. Digit. Imaging 2013, 26, 1045–1057. [Google Scholar] [CrossRef] [PubMed]
- Anand, A.; Singh, A.K. RDWT-SVD-firefly based dual watermarking technique for medical images (workshop paper). In Proceedings of the 2020 IEEE Sixth International Conference on Multimedia Big Data (BigMM), New Delhi, India, 24–26 September 2020; pp. 366–372. [Google Scholar]
| Different Approaches | Optimal Parameters | Optimal Parameter Values |
|---|---|---|
| DWT | Number of epochs | 100 |
| Number of neurons in the hidden layer | 10 | |
| Name of the optimizer | Adam | |
| FEO | Variable probability | 0.5 |
| Learning rate | 0.8 | |
| 0.11 | ||
| 5 | ||
| Arc rate | 1.4 | |
| Population size | 50 | |
| Number of iterations | 100 |
| Different Performance Metrics | Performance Rate |
|---|---|
| Peak signal to noise ratio | 42.5 dB |
| Segmentation accuracy with respect to noise density | 98.1% |
| Segmentation accuracy with respect to noise variance | 98.3% |
| 0.985 | |
| 0.3827 | |
| Embedding rate | 0.021 |
| Embedding time | 3.2 s |
| Extraction time | 2.1 s |
| Types | Original Image | Embedded Image | Noise Image | Output |
|---|---|---|---|---|
| CT |  |  |  |  |
 |  |  |  | |
| MRI |  |  |  |  |
 |  |  |  | |
| US |  |  |  |  |
 |  |  |  |
| Different Performance Metrics | Comparison Methods | ||||
|---|---|---|---|---|---|
| CIWT-LSBBW | LZW-LCA | FOA | ZWA | Proposed FEO Algorithm | |
| Embedding rate (bpp) | 0.0018 | 0.0051 | 0.0097 | 0.0150 | 0.021 |
| Embedding time (s) | 5.2 | 4.9 | 6.3 | 4.5 | 3.2 s |
| Extraction time (s) | 7 | 5.7 | 6.2 | 3.8 | 2.1 s |
| 0.904 | 0.956 | 0.897 | 0.962 | 0.985 | |
| 0.258 | 0.3154 | 0.3381 | 0.2197 | 0.3827 | |
| Coefficient index | 0.875 | 0.927 | 0.891 | 0.952 | 0.979 |
| Entropy index | 0.0789 | 0.0563 | 0.0617 | 0.0454 | 0.0310 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bhatia, S.; Almutairi, A. A Robust Fuzzy Equilibrium Optimization-Based ROI Selection and DWT-Based Multi-Watermarking Model for Medical Images. Sustainability 2023, 15, 6189. https://doi.org/10.3390/su15076189
Bhatia S, Almutairi A. A Robust Fuzzy Equilibrium Optimization-Based ROI Selection and DWT-Based Multi-Watermarking Model for Medical Images. Sustainability. 2023; 15(7):6189. https://doi.org/10.3390/su15076189
Chicago/Turabian StyleBhatia, Surbhi, and Alhanof Almutairi. 2023. "A Robust Fuzzy Equilibrium Optimization-Based ROI Selection and DWT-Based Multi-Watermarking Model for Medical Images" Sustainability 15, no. 7: 6189. https://doi.org/10.3390/su15076189
APA StyleBhatia, S., & Almutairi, A. (2023). A Robust Fuzzy Equilibrium Optimization-Based ROI Selection and DWT-Based Multi-Watermarking Model for Medical Images. Sustainability, 15(7), 6189. https://doi.org/10.3390/su15076189






