Abstract
In order to address the issues of unclear risk grading control, lack of safety management, and hidden danger investigation and management processes, this paper used a mining enterprise as the backdrop for an engineering example. The “evaluation model of the overall construction level of the enterprise safety management system” is constructed from four aspects: “preliminary infrastructure”, “risk grading and control”, “hidden danger investigation and management processes”, and “Post-support work”. The safety evaluation level is divided into five levels, and the evaluation model is combined weighted by using the combined ordered weighted averaging (COWA) algorithm and the criteria importance through intercriteria correlation (CRITIC) method. In addition, the cloud model, the extension cloud model, and the grey clustering evaluation method are used for a thorough evaluation. Finally, the enterprise safety management system’s overall construction level is determined to be good. In order to effectively strengthen the enterprise safety management capability and prevent the occurrence of production safety accidents, this study provides a practical and thorough evaluation method for the evaluation of the enterprise safety management system. This method makes it easier to identify system weaknesses and provides a safety guarantee for the sustainable development of enterprises.
1. Introduction
Every nation and government in the world has placed a strong emphasis on safety management, and they all view it as one of the key goals of sustainable development. Simultaneously, effective safety management is a critical tool that businesses may utilize to achieve safe production and protect the lives, health, and property of employees. It is also a critical component that businesses need to attain sustainable and long-term growth. In China, safety management is seen as a key priority. Over the years, the state has released a number of laws, rules, and policies to help businesses set up standardized safety management systems and perform well in terms of safety management, and it has seen some success. According to Figure 1, the number of fatalities brought on by various production safety accidents in China declined from 69,434 in 2013 to 20,963 in 2022, with a general trend of nearly 70%. As the nation pays more and more attention to safety management, it can be seen that production safety accidents have been effectively controlled. However, because production safety accidents continue to result in a high number of fatalities each year, the outlook for production safety is still not good. According to industry statistics, there were up to 407 safety incidents in China’s non-coal mines in total in 2017, as a result of which 484 people died; there were up to 170 fatal incidents in China’s mines in 2019, with 1 fatal incident happening on average every 2.1 days; and there were 356 safety incidents in China’s mines in total in 2021, of which 265 fatal incidents occurred in China’s non-coal mines, resulting in 503 and 325 deaths, respectively. The root causes lie in the fact that the enterprise safety management method is incorrect, the safety management system is imperfect, safety management measures are not put into practice, etc. These problems will increase the likelihood of production safety accidents, which pose a serious threat to the operating personnel’s life, health, and property safety.
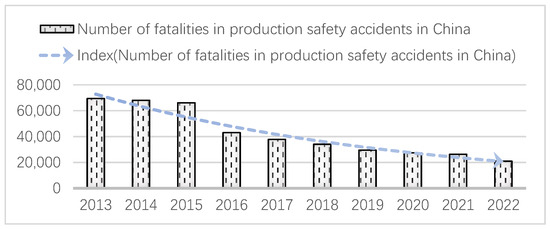
Figure 1.
Number of fatalities in production safety accidents in China.
Currently, experts and academics from both home and abroad are conducting research using the safety management idea. The notion of safety management has been the subject of research performed by specialists and academics both domestically and internationally. According to Aven et al. [1], enterprise risk management (ERM) should concentrate on the connection between risk, uncertainty, knowledge, and performance. Additionally, Álvarez-Santos et al. [2] showed how businesses in the context of total quality and safety management can help to facilitate the development of safety management systems.
Meanwhile, experts and scholars have explored and tried various methods of safety evaluation, including the analytic hierarchy process (AHP), the entropy weight method, SCL (Safety Check List), the cloud model, extenics, the grey clustering evaluation method, etc. You et al. [3] combined the triangular fuzzy number method, the entropy weight method, the criteria importance through intercriteria correlation (CRITIC) method, and three rough set methods; simultaneously, they combined these six subjective and objective weight calculation methods based on Euclidean distance of information entropy and rough set to assign weights into comprehensive weights. After performing this, they evaluated the safety management status of four coal mining enterprises and confirmed the viability of this evaluation method. Guo et al. [4] combined the matter-element extension evaluation model with the cloud model to form the analytic network process (ANP) extension cloud comprehensive evaluation model and applied it to the safety management evaluation of subway construction sites. Jiskani et al. [5] established a thorough evaluation model using the entropy weighting approach and grey clustering to assess the safety status of 27 safety evaluation indicators in mines. They then suggested implementing treatment measures in the order they were recommended. Peng and Zhang [6] used the extension cloud model to assess the safety level of construction sites based on the weights established by the hierarchical analysis method and game theory; they began by considering the psychological factors in the organization of construction sites, which are frequently overlooked when building the safety level evaluation model. By using the extension cloud theory and the optimal cloud entropy method, Chen et al. [7] developed a safety evaluation system with four secondary indicators and fifteen tertiary indicators to assess the safety level of buildings in karst areas, ultimately achieving a safety evaluation level that is in line with the project’s actual safety condition. Li and Gong [8] built a safety evaluation model for a power grid data management system and used expert consultation methods and AHP to better ensure the safety of smart grid data. Guo et al. [9] evaluate the safety management capacities of construction sites by utilizing video surveillance inspections rather than on-site inspections, creating safety checklists, and finally, applying safety checklist analysis (SCA). Maihemuti et al. [10] offered eight improvement solutions to maintain the safe and stable functioning of power systems after using SWOT (Strengths, Weaknesses, Opportunities, Threats) analysis to develop 24 internal and external evaluation variables for the safety of new energy power systems.
In addition, some scholars have conducted research on security risk evaluation. A semi-deterministic risk assessment method based on the fuzzy analytic hierarchy process (FAHP) was created by Mahdinia et al. [11], with the probability of impact and severity of consequences as two useful parameters for lowering safety risks in construction projects. In order to identify each type of risk, Klinke and Renn [12] proposed nine risk assessment criteria, six risk categories, and three risk management categories. They also created a decision tree to categorize each type of risk and matched a risk response strategy to each category, which significantly increased the feasibility and timeliness of the safety risk management procedure. Ju et al. [13] created a construction safety risk level evaluation model based on game theory and the extension cloud model. In order to undertake a thorough evaluation of the choice of wind farm address based on the ideal matter element extension evaluation model and the grey clustering evaluation model, Tan et al. [14] built a weight model integrating subjective and objective weights. Qiao et al. [15] combined the fuzzy comprehensive evaluation method with the clustering evaluation method to form a fuzzy grey clustering triangular function comprehensive evaluation model to evaluate the investment risk of wind power projects.
It is evident that current research is more concentrated on the evaluation of safety and risk levels during project construction or production operations and that there is little research on the evaluation of overall safety management levels in the context of mining enterprises. Most studies only use one evaluation method, which makes it challenging to guarantee the accuracy and reliability of evaluation results. When determining the weights of evaluation indicators, they do not take into account the issue of inaccurate weights due to complex levels and too many evaluation indicators, nor do they take into account the gaps and correlations between the indicators. Meanwhile, the existing safety evaluation methods include the analytic hierarchy process, matter-element extension theory, cloud model, fuzzy comprehensive evaluation method, BP neural network, extension cloud model, and grey clustering evaluation method. These evaluation techniques do, however, inevitably have some drawbacks and restrictions, such as the analytic hierarchy process’s excessive reliance on subjective factors, the matter-element extension theory’s correlation function’s overly objective nature, the fuzzy comprehensive evaluation’s insufficient consideration of the correlation between the evaluation indicators, and the BP neural network’s high data requirements and poor accuracy. It is also challenging to guarantee the correctness and dependability of the evaluation outcomes because the majority of studies only use one evaluation method.
Consequently, the COWA algorithm and the CRITIC method are combined and weighted in this research. Then, based on the weights obtained, it uses the cloud model, the extension cloud model, and the grey clustering evaluation method to form a comprehensive evaluation model. Finally, it uses the overall construction level of the enterprise safety management system to perform a comprehensive evaluation and reach a consistent evaluation level. The inadequacies of the pass evaluation model can be remedied by using this comprehensive evaluation model, which does a good job of accounting for the influence of subjective and objective criteria: the COWA algorithm can rearrange and combine data according to importance, rank objective data into priority positions, and assign weights first, which can well overcome the problem of too many information elements and get more objective weights. The CRITIC method can reflect the gap and correlation between indicators by calculating the contrast and conflict intensity of the indicators. The advantage of the extension cloud model over the matter-element extension theory is that it can rely on the benefits of randomness and vagueness of the cloud model to make up for the shortcomings of the randomness and vagueness of the characteristic values of things in the matter-element extension theory that have been ignored, combining the qualitative and quantitative advantages of matter-element extension theory. The grey clustering evaluation method, which has the benefits of the fuzzy comprehensive evaluation method and can also effectively handle the gray information of the evaluation object, is relatively easy to calculate and does not require a significant quantity of beginning data. The application of this comprehensive evaluation model may very well guarantee the accuracy and reliability of the evaluation results, offering a rigorous assurance for the accurate assessment of the company’s safety management level.
2. Methodology
2.1. Calculating Combined Weights
2.1.1. COWA Algorithm for Calculating Weight
By combining the number of improved weight vectors to determine the indicator weights, Chinese researchers were able to create the COWA algorithm, which was based on the ordered weighted averaging (OWA) algorithm proposed by Professor Yager [16] in the United States. The COWA algorithm is calculated as follows [17,18]:
- (1)
- Establishing the Scoring Dataset
Based on the aforementioned scoring results for each level of indicators, the initial data set (a1, a2, …, aj, …, an) is created. The initial data are then sorted in descending order starting at number 0 to obtain the restructured data set (b0, b1, b2, …, bj, …, bn−1), where b0 ≥ b1 ≥ b2 ≥ …≥ bj ≥ …≥ bn−1.
- (2)
- Calculating the Weighted Vector
The sorted reorganized data bj are assigned using the combinatorial number, and the weighted vector is also computed using Equation (1).
where , denotes the number of combinations after removing j data from n−1 data.
- (3)
- Calculation of Absolute and Relative Weight
The weighting vector is used to weight the data bj in the restructured data set. Following that, the absolute weight of each evaluation indicator is then calculated using Equation (2), and the relative weight of each indication is determined using Equation (3).
where , and m denotes the number of indicators.
2.1.2. CRITIC Method for Calculating Weight
The CRITIC method is a comprehensive weighting method put forth by Diakoulaki [19] in 1995 for the evaluation of multi-indicators. It reflects the objective weights of the indicators by assessing the degree of contrast and conflict between the indicators [20], which is able to simplify the complex correlation data between the indicators and obtain a more precise weight. The strength of the contrast is expressed in terms of standard deviation; the larger the standard deviation, the more unstable the data are and the higher the weight obtained. The conflict is expressed in terms of the correlation coefficient. The larger the correlation coefficient, the smaller the conflict will be; on the other hand, the smaller the correlation coefficient, the lower the weight obtained. The CRITIC method is calculated as follows [21,22]:
- (1)
- Establishing the Initial Scoring Matrix
The above scoring matrices B1, B2, B3, and B4 are used as the initial data matrix X, respectively, and Xnp is the value of the scoring by expert n on the indicator p.
- (2)
- Dimensionless Processing Indicator
The CRITIC method of dimensionless processing usually includes forward and reverse processing [23], as shown in Equations (5) and (6).
Positive indicators:
Negative indicators:
- (3)
- Calculation of Indicator Variability and Conflict
Indicator variability is usually reflected by calculating the standard deviation Sj with Equation (7); the higher the Sj value, the more information the indicator can convey and the more significant it is. Indicator conflict is usually reflected by calculating the Rj with Equation (8); the smaller the Rj, signifying a higher degree of information overlap, the indicator and other indicators of the conflict will be less and obtain a lower degree of importance [24].
where rij denotes the correlation coefficient of evaluation indicators i and j.
- (4)
- Calculation of Information Volume and Indicator Weight
The amount of information in the indicator is usually reflected by calculating the standard deviation Cj with Equation (9); the higher Cj, the more significant it is and it obtains a bigger weight.
Finally, the objective weight of the jth evaluation indicator is calculated by Equation (10).
2.1.3. Combined Weighting
The multiplicative combination weighting method can combine the weights determined by two different methods well, so the multiplicative combination weighting method Equation (11) is used to combine the weights determined by the COWA algorithm and the CRITIC method [25] and the value of the combined weighting ω is obtained.
2.2. Construction of Extension Cloud Evaluation Model
The extension cloud model is formed by combining the matter-element extension theory with a cloud model and replacing the eigenvalues of objects in the matter-element extension theory with the numerical eigenvalues of the cloud model [26]. The following are the steps in the evaluation of the extension cloud model [27,28].
2.2.1. Construction of Matter-Element to Be Evaluated and Standard Cloud
- (1)
- Construction of matter-element to be evaluated
The extension cloud model creates the object element R to be evaluated in the extension cloud model by replacing the eigenvalues V of objects in the matter-element extension theory with three numerical eigenvalues from the standard cloud model: expectation Ex, entropy En, and hyper entropy He [29].
where N is the matter-element to be evaluated, Cn is the evaluation object, and (Exn, Enn, Hen) is the cloud eigenvalue of the matter-element to be evaluated for Cn.
- (2)
- Determine the Standard Cloud
The calculation of the digital eigenvalues of the standard cloud parameters includes bilateral constraints and unilateral constraints, and the three digital eigenvalues (Ex, En, He) of the comment set are usually calculated and determined using the bilateral constraints [Xmin, Xmax] [30], and the calculation formula is shown in Equation (13).
where Xmax and Xmin denote the upper and lower limits of the score range corresponding to the evaluation level. The value of He reflects the randomness of the indicator, and k = 0.1 is taken to reflect realism.
2.2.2. Calculating Cloud Correlation
- (1)
- Calculating Indicator Layer Correlation
Let the score value of each indicator in the evaluation system be cloud drop x, and then generate a random number En′, which is subject to normal distribution with the expectation of En and the standard deviation of He. Then, the cloud correlation μ between the scoring value x of each indicator and the standard cloud is computed by Equation (14). Finally, the correlation obtained from the computation of each indicator is composed into a comprehensive judgment matrix Mi.
where μmn is the cloud correlation of evaluation indicator m under evaluation level n, m is the number of evaluation indicators, and n is the evaluation level.
- (2)
- Calculating Target Layer Correlation
Equation (16) is used to calculate the criterion layer correlation UB, while Equation (17) is used to calculate the target layer correlation U.
where WC is the indicator weight of the indicator layer and WB is the indicator weight of the criterion layer.
2.2.3. Determination of Evaluation Levels
The principle of maximum affiliation is typically used to determine the evaluation level. The evaluation grade of the evaluation object N is j if Uj(N) = maxj=(1,2,…,n)Uj(N) in the evaluation vector U [31]. However, the use of the principle of maximum affiliation in determining the comprehensive evaluation grade can lead to situations where information is lost [32], so the comprehensive evaluation grade is determined by calculating the variable eigenvalue j′ through Equation (18) and the evaluation grade that is closest to the variable eigenvalue is the final comprehensive evaluation grade.
2.3. Construction of Grey Clustering Evaluation Model
Grey clustering evaluation method is an evaluation method that divides the evaluation level into grey categories and corresponds to a whitening weight function, respectively, and then calculates the whitening weights of each evaluation object at different grey categories, thus determining the grey category of the evaluation object. The following are the evaluation steps for the grey clustering evaluation method [33,34].
2.3.1. Constructing a Grey Clustering Evaluation Matrix
The grey clustering evaluation matrix X was created by using the scoring matrix.
where i is the number of indicators in the indicator layer, and p is the number of experts.
2.3.2. Determine the Evaluation Level and Construct the Whitening Weight Function
According to the determined evaluation grade, the evaluation grade is divided into Based on the determined evaluation level, the evaluation level is divided into a corresponding number of grey categories. For the upper limit grey category, use the upper limit measure whitening weight function. For the lower limit grey category, use the lower limit measure whitening weight function. For the intermediate grey category, use the intermediate measure whitening weight function [35].
2.3.3. Constructing the Grey Clustering Weight Matrix
When the evaluation index xij belongs to grey category e, the clustering coefficient , the total clustering coefficient , and the grey clustering weight vector . Finally, the grey clustering weight vector is used to form the grey clustering weight matrix Ri.
2.3.4. Construction of a Comprehensive Evaluation Matrix and Calculation of Evaluation Values
Firstly, the clustering evaluation matrix Zi of each indicator in the criterion layer is calculated by Equation (21), the comprehensive evaluation matrix is obtained, and then the clustering evaluation is carried out to obtain the comprehensive evaluation vector M.
where ω is the combined weight of each indicator in each layer.
Determine the evaluation grade of each indicator based on the principle of maximum affiliation. And, in order to reduce the loss of information due to the use of the principle of maximum affiliation when determining the comprehensive evaluation grade, the comprehensive evaluation value W was obtained by multiplying the comprehensive evaluation vector M with the grey category centroid vector U through Equation (23), thus determining the comprehensive evaluation grade.
3. Case Analysis
3.1. Establishing the Evaluation Structure and Scoring
3.1.1. Establishing a Hierarchical Evaluation Structure
In this study, a mining enterprise is used as the engineering example background, and a hierarchical evaluation structure consisting of a target layer, criterion layer, and indicator layer is built in accordance with the actual situation of the enterprise, and the pertinent literature is reviewed [36,37,38]. The target layer A is set to be the “evaluation of the overall construction level of safety management system”, and the criterion layer B is set to be the “construction of preliminary infrastructure”, “risk grading and control”, “hidden danger investigation and management”, and “post-support work”. The indication layer C, which comprises 7, 10, 7, and 6 indicators, are set up. Table 1 displays the final hierarchical evaluation structure that has been built.

Table 1.
Security management hierarchy evaluation structure.
3.1.2. Scoring Dataset Acquisition
The evaluation levels have been classified into five categories after taking into account professional perspectives and examining the pertinent literature: “excellent”, “good”, “qualified”, “poor”, and “very poor”, which correspond to score ranges of [100,90], (90, 75], (75, 60], (60, 30], and (30, 0], respectively.
By distributing questionnaires to pertinent researchers and on-site managers of businesses, the results of ten surveys were gathered, and the scoring matrices B1, B2, B3, and B4 for each indicator were constructed. In the matrix, the columns stand in for evaluators, while the rows represent assessment indications.
The scoring matrix A for a criterion level indicator is obtained by calculating the average score of each expert regarding each indicator of the indicator level under a criterion level.
The Cronbach’s alpha coefficient [39] was used to assess the validity and dependability of the score data. Higher values denote more reliable data when α ≥ 0.9 denotes very reliable data, when 0.9 > α ≥ 0.8 denotes relatively reliable data, when 0.8 > α ≥ 0.7 denotes acceptable data, when 0.7 > α ≥ 0.6 denotes doubtful data, when 0.6 > α ≥ 0.5 denotes bad data, and when 0.5 > α denotes unacceptable data.
The estimated alpha coefficients for B1 are 0.959 > 0.9, B2 is 0.968 > 0.9, B3 is 0.954 > 0.9, B4 is 0.921 > 0.9, and A is 0.979 > 0.9. The scoring information was highly reliable. Therefore, the scoring data had high reliability.
3.2. Calculating Combined Weights
3.2.1. COWA Algorithm for Calculating Weight
Firstly, take the first column score of indicator C11 as an example. The reorganization data set is obtained as (98, 96, 91, 90, 88, 88, 85, 85, 80, 77), and similarly, the overall reorganization data matrix of indicator C11 and other indicators can be obtained. Then, Equation (1) is applied to calculate the weighting vector, as shown in Table 2. Finally, Equations (2) and (3) are applied to calculate the absolute and relative weights of the indicators, respectively, as shown in Table 3.

Table 2.
Indicator weighting vectors.

Table 3.
COWA, CRITIC weight, and combined weight.
In the table, S1–S10 denote raters; B1–4 denote guideline layers B1–B4; C1–7 denote indicator layers C1–C7; C2–10 denote indicator layers C2–C10; C3–7 denote indicator layers C3–C7; and C4–6 denote indicator layers C4–C6.
3.2.2. CRITIC Method for Calculating Weight
First, the aforementioned scoring matrices B1, B2, B3, and B4 are utilized as the initial data matrix X, and because the scoring data are all positive indicators, Equation (5) is employed for the normalization procedure. Following the computation of the indicator variability, conflict, and information, the indicator objective weights are eventually determined. The calculation results are shown in Table 3.
3.2.3. Combined Weighting
The multiplicative combination assignment method is applied to obtain the combination assignment weight values ω is shown in Table 3.
3.3. Construction of Extension Cloud Evaluation Model
3.3.1. Evaluation of Extension Cloud Model
Firstly, the digital eigenvalues of the standard cloud comment set are obtained by applying Equation (13) as follows: excellent (95, 1.6667, 0.1), good (82.5, 2.5, 0.1), qualified (67.5, 2.5, 0.1), poor (47.5, 4.1667, 0.1), and very poor (17.5, 5.8333, 0.1). Then, the cloud correlation of each indicator is obtained from Equation (14), which obtains the cloud correlation matrix between the scoring values of the evaluation indicators of the indicator layer and the standard cloud, M1, M2, M3, and M4.
Finally, Equation (16) is used to calculate the criterion layer correlation UB, while Equation (17) is used to calculate the target layer correlation U.
Based on the principle of maximum affiliation, the evaluation grades of “preliminary infrastructure construction B1”, “risk grading and control B2”, “hidden danger investigation and management B3”, and “post-support work B4” are all good. Meanwhile, in order to reduce the information loss caused by the application of the principle of maximum affiliation, Equation (18) was calculated to obtain , and the degree of the comprehensive evaluation grade of relevance of j′ = 2.1357, which is the closest to level 2.
3.3.2. Comparison and Validation of Cloud Model
In order to verify the accuracy of the evaluation results, the evaluation results obtained from the extension cloud model are compared with the cloud diagram generated by the cloud model. According to the numerical eigenvalues (Ex, En, He) calculated for each indicator and the number of operations set to 3000, we finally obtained the cloud diagrams: Figure 2, Figure 3, Figure 4, Figure 5 and Figure 6.
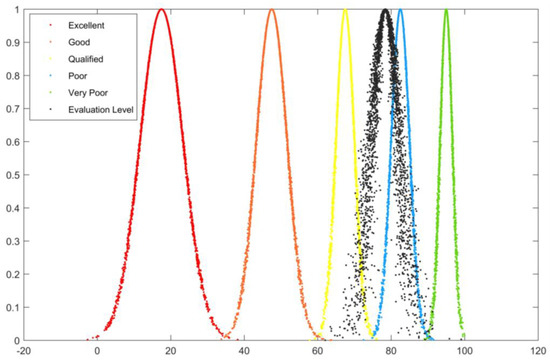
Figure 2.
Preliminary infrastructure construction B1 cloud diagram.
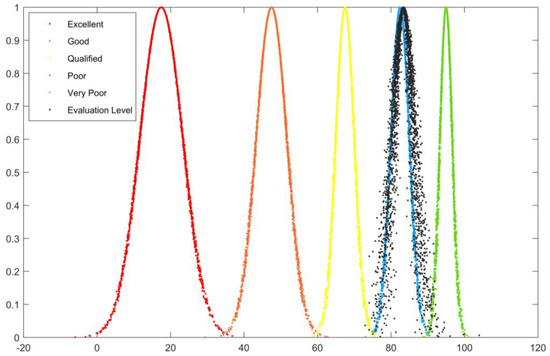
Figure 3.
Risk grading and control B2 cloud diagram.
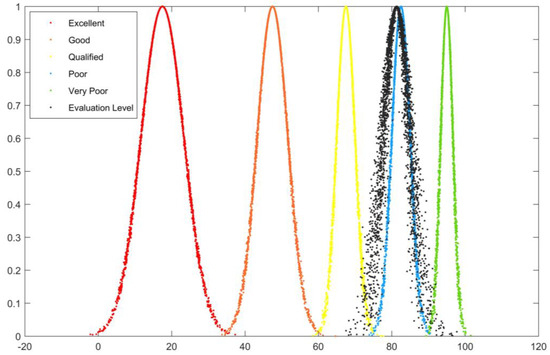
Figure 4.
Hidden danger investigation and management B3 cloud diagram.
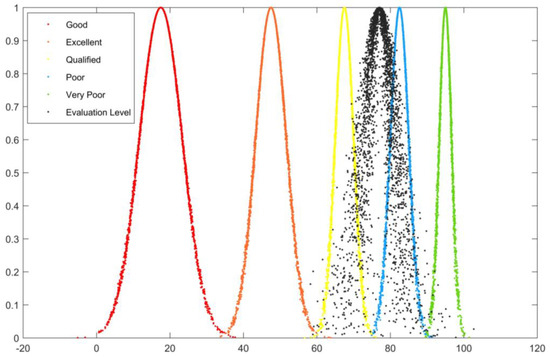
Figure 5.
Post-support work B4 cloud diagram.
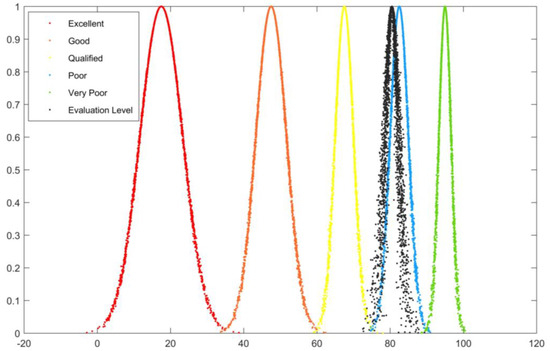
Figure 6.
Evaluation of overall construction level of safety management system A cloud diagram.
In Figure 2, Figure 3, Figure 4, Figure 5 and Figure 6, the horizontal axis represents the rating value, and the vertical axis represents the cloud correlation degree. The red, orange, yellow, blue, and green cloud maps correspond to five evaluation levels, while the black cloud map corresponds to the cloud evaluation level of the evaluation object.
It can be seen that the evaluation result of the “Preliminary infrastructure construction B1” cloud diagram is between qualified and good but leans more toward good, so the evaluation grade is good. The results of the “Risk classification and control B2” cloud diagram evaluation are highly overlapped with good results, so the evaluation grade is good. The results of the “Hidden danger investigation and management B3” cloud diagram evaluation mostly overlap with good, but with a slight bias toward the pass, so the evaluation grade is good. The results of the “Post-support work B4” cloud diagram evaluation are very close to the deviation between qualified and good but lean more toward good, so the evaluation grade is good. The results of the comprehensive evaluation cloud diagram “Evaluation of the overall construction level of safety management system A” are very close to good, only with a slight bias in favor of qualified, so the evaluation grade is good.
3.4. Construction of Grey Clustering Evaluation Model
Firstly, the grey clustering evaluation matrix X was created by combining the scoring matrices B1, B2, B3, and B4 for each of the aforementioned indicators. Meanwhile, according to the determined evaluation grade, the evaluation grade is divided into five grey categories e = 1, 2, 3, 4, 5, corresponding to “excellent”, “good”, “qualified”, “poor”, “very poor”, and the middle value of each grey category is taken as the center point of the grey category U = (95,82.5,67.5,47.5,17.5). Construct whitening weight functions based on the grey category, as shown in Table 4.

Table 4.
Grey category whitening weight function.
Constructing the Grey Clustering Weight Matrix
Then, the clustering coefficients, total clustering coefficient, and the grey clustering weight vector of evaluation indicators B1, B2, B3, and B4 at each grey category are calculated, respectively, and the gray clustering weight vectors comprise the grey clustering weight matrices of each evaluation indicator in the index layer R1, R2, R3, and R4. The clustering weight vectors are the columns of the matrix, while the rows of the matrix are the metrics in the metrics layer.
Finally, the clustering evaluation matrix Zi of each indicator in the criterion layer is calculated by Equation (21), the comprehensive evaluation matrix Z0 is obtained, and then the clustering evaluation is carried out to obtain the comprehensive evaluation vector M .
According to the principle of maximum affiliation, the grey category of “Preliminary infrastructure construction B1”, “Risk grading and control B2”, “Hidden danger investigation and management B3”, and “Post-support work B4” is e = 2, so the evaluation grade is good. Meanwhile, in order to reduce the loss of information due to the use of the principle of maximum affiliation when determining the comprehensive evaluation grade, the comprehensive evaluation value W = 78.3525 was obtained through Equation (23).
Therefore, the comprehensive evaluation value of the target level “Evaluation of the overall construction level of safety management system A” is 78.3525, which belongs to the score range of (90,75], and the comprehensive evaluation grade is good.
4. Results and Discussion
Based on the comprehensive evaluation results of three evaluation methods: the extension cloud model, the cloud model, and the grey clustering evaluation method, it can be seen that the evaluation results of the criterion layer are consistent with those of the target layer, and both are classified as good. In the indicator layer, the evaluation results of “Importance level of leadership”, “Choice of risk identification methods”, “Choice of risk evaluation methods”, and “Risk level classification” are good in the extension cloud model, while the evaluation results are excellent in the grey clustering evaluation method. All other indications are good, with the exception of those that qualify: “Safety production standardization construction level”, “Overall cultural level of employees”, “Internal and external communication mechanism”, and “Publicity and education of the system”.
As a result, although the enterprise’s overall construction level of the safety management system is fairly good, there is still potential for further optimization, which can be begun from the indicators with lower evaluation levels. For the “Safety production standardization construction level”, we can check and rectify each deduction in line with the demands of the work safety standardization evaluation in order to raise the level. For the “Overall cultural level of employees”, remedial action can be taken to compensate for the low literacy level of employees by enhancing professional knowledge and skills education after joining the workforce or by appropriately raising the threshold of academic qualifications for joining the workforce. The “Internal and external communication mechanism” can be improved by enhancing communication feedback, expanding communication methods, setting up suggestion rewards, and other measures so as to motivate employees to participate in communication. The “Publicity and education of the system” can be improved through the regular organization of the safety management system publicity and education conference, the organization of the safety system knowledge contests, and other forms to enhance the staff’s understanding of the enterprise’s safety system.
5. Limitations and Further Research
The scoring data will inevitably be influenced by some degree of subjective factors because the scoring data are obtained in the form of questionnaires, even though this study has minimized the degree of influence of subjective factors in determining the weights of the indicators by combining the COWA operator with the CRITIC method of assigning weights. Second, in determining the structure of the evaluation indicators, although this study has maximized the consideration of various factors in a variety of ways, it is inevitable that there will be cases of ill-consideration. To reduce the impact of subjective factors and ensure the reliability of the data, future studies should further optimize the collection of evaluation data and look for better reliability and validity tests for the gathered scoring data. In addition, since the comprehensive assessment approach can be effectively applied to the field of safety evaluation, future studies can focus on using the method in a variety of other fields to increase its applicability.
Some more sophisticated advanced optimization algorithms have been developed, including self-adaptive algorithms, polyploid algorithms, metaheuristics, hybrid heuristics, hyper-heuristics, and island algorithms. The problems of large-scale black-box optimization, CDT truck operation planning, vehicle transportation routing decision-making, accident prevention countermeasures at road junctions, and pheromone maps applications can now be effectively solved using these algorithms in the fields of reinforcement learning [40], scheduling [41], transportation [42], decision-making [43], and hyper-heuristics [44], respectively. In order to improve safety evaluation outcomes, further study can be directed toward applying these algorithms to safety management evaluation or combining them with conventional evaluation techniques.
6. Conclusions
The COWA algorithm and the CRITIC method were combined in this paper, and using the multiplier weighting method to combine the weights will result in comprehensive weights that can address the problem of having too many components in the indicators as well as comprehensively account for gaps and correlations between them. Meanwhile, the overall construction level of the mining enterprise’s safety management system was evaluated by using the extension cloud model, cloud model, and grey clustering evaluation method, and it was finally determined the evaluation level of the enterprise’s overall construction level of safety management system is good, and the evaluation level of each evaluation indicator of the criterion layer is good. This method overcomes the problem of the inaccuracy and unreliability of the evaluation results caused by the use of a single evaluation method.
According to the evaluation grade of indicator level that was determined by the extension cloud model and grey clustering evaluation method, the evaluation grade of the four evaluation indicators, namely, “Safety production standardization construction level”, “Overall cultural level of employees”, “Internal and external communication mechanism”, and “Publicity and education of the system”, are only qualified. This method may effectively improve the enterprise safety management capability and achieve the sustainable development of enterprise safety by identifying the weak points in the enterprise safety management system and suggesting appropriate improvement actions.
Author Contributions
Conceptualization, S.D. and X.L.; methodology, S.D.; investigation, Y.Y., X.H., H.D. and W.X.; data curation, S.D.; visualization, S.D. and X.J.; writing—original draft preparation, S.D.; writing—review and editing S.D. and X.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data used to support the findings of this study are available from the corresponding author upon request.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Aven, T.; Thekdi, S. Enterprise Risk Management; Taylor and Francis: New York, NY, USA, 2020. [Google Scholar]
- Álvarez-Santos, J.; Miguel-Dávila, J.; Herrera, L.; Nieto, M. Safety Management System in TQM environments. Saf. Sci. 2018, 101, 135–143. [Google Scholar] [CrossRef]
- You, Q.; Yao, Q.; Song, R.; Yu, K.; Xu, C.; Cao, H. Multi-dimensional safety risk assessment on coal mines under the profitability dilemma. Sci. Rep. 2023, 13, 2687. [Google Scholar] [CrossRef] [PubMed]
- Guo, Q.; Amin, S.; Hao, Q.; Haas, O. Resilience assessment of safety system at subway construction sites applying analytic network process and extension cloud models. Reliab. Eng. Syst. Saf. 2020, 201, 106956. [Google Scholar] [CrossRef]
- Jiskani, I.M.; Han, S.; Rehman, A.U.; Shahani, N.M.; Tariq, M.; Brohi, M.A. An Integrated Entropy Weight and Grey Clustering Method-Based Evaluation to Improve Safety in Mines. Min. Metall. Explor. 2021, 38, 1773–1787. [Google Scholar] [CrossRef]
- Peng, J.; Zhang, Q. Safety Performance Assessment of Construction Sites under the Influence of Psychological Factors: An Analysis Based on the Extension Cloud Model. Int. J. Env. Res. Pub. He. 2022, 19, 15378. [Google Scholar] [CrossRef] [PubMed]
- Chen, H.; Yang, S.; Feng, Z.; Liu, Y.; Qin, Y. Safety evaluation of buildings adjacent to shield construction in karst areas: An improved extension cloud approach. Eng. Appl. Artif. Intel. 2023, 124, 106386. [Google Scholar] [CrossRef]
- Li, D.; Gong, Y. The design of power grid data management system based on blockchain technology and construction of system security evaluation model. Energy Rep. 2022, 8, 466–479. [Google Scholar] [CrossRef]
- Guo, S.; Li, J.; Liang, K.; Tang, B. Improved safety checklist analysis approach using intelligent video surveillance in the construction industry: A case study. Int. J. Occup. Saf. Ergo. 2021, 27, 1064–1075. [Google Scholar] [CrossRef]
- Maihemuti, S.; Wang, W.; Wu, J.; Wang, H. New energy power system operation security evaluation based on the SWOT analysis. Sci. Rep. 2022, 12, 12680. [Google Scholar] [CrossRef]
- Mahdinia, M.; Yarandi, M.S.; Jafarinia, E.; Soltanzadeh, A. Development of a New Technique for Safety Risk Assessment in Construction Projects Based on Fuzzy Analytic Hierarchy Process. ASCE-ASME J. Risk Uncertain. Eng. Syst. Part A Civ. Eng. 2021, 7, 04021037. [Google Scholar] [CrossRef]
- Klinke, A.; Renn, O. A new approach to risk evaluation and management: Risk-based, precaution-based, and discourse-based strategies. Risk Anal. 2002, 22, 1071–1094. [Google Scholar] [CrossRef] [PubMed]
- Ju, W.; Wu, J.; Kang, Q.; Jiang, J.; Xing, Z. A method based on the theories of game and extension cloud for risk assessment of construction safety: A case study considering disaster-inducing factors in the construction process. J. Build. Eng. 2022, 62, 105317. [Google Scholar] [CrossRef]
- Tan, Q.; Wei, T.; Peng, W.; Yu, Z.; Wu, C. Comprehensive evaluation model of wind farm site selection based on ideal matter element and grey clustering. J. Clean. Prod. 2020, 272, 122658. [Google Scholar] [CrossRef]
- Qiao, H.; Wen, S.; Wu, L.; Zeng, B. Research on wind power project investment risk evaluation based on fuzzy-gray clustering trigonometric function. Energy Rep. 2022, 8, 1191–1199. [Google Scholar] [CrossRef]
- Yager, R.R. On Ordered Weighted Averaging Aggregation Operators in Multicriteria Decisionmaking. In Readings in Fuzzy Sets for Intelligent Systems; Dubois, D., Prade, H., Yager, R.R., Eds.; Morgan Kaufmann: Cambridgem, MA, USA, 1993; pp. 80–87. [Google Scholar]
- Su, G.; Jia, B.; Wang, P.; Zhang, R.; Shen, Z. Risk identification of coal spontaneous combustion based on COWA modified G1 combination weighting cloud model. Sci. Rep. 2022, 12, 2992. [Google Scholar] [CrossRef]
- Zhang, J.; Lang, X.; Jing, Y.; Kang, J.; You, Q.; Shang, Z.; Shi, M.; Dai, H. Vulnerability assessment of hydrogen stations based on cloud center of gravity theory. Int. J. Hydrogen. Energy 2023, 5, 295. [Google Scholar] [CrossRef]
- Diakoulaki, D.; Mavrotas, G.; Papayannakis, L. Determining objective weights in multiple criteria problems: The critic method. Comput. Oper. Res. 1995, 22, 763–770. [Google Scholar] [CrossRef]
- Abdel-Basset, M.; Mohamed, R. A novel plithogenic TOPSIS- CRITIC model for sustainable supply chain risk management. J. Clean. Prod. 2020, 247, 119586. [Google Scholar] [CrossRef]
- Khargotra, R.; Kumar, R.; András, K.; Fekete, G.; Singh, T. Thermo-hydraulic characterization and design optimization of delta-shaped obstacles in solar water heating system using CRITIC-COPRAS approach. Energy 2022, 261, 125236. [Google Scholar] [CrossRef]
- Ye, F.; Sun, J.; Wang, Y.; Nedjah, N.; Bu, W. A novel method for the performance evaluation of institutionalized collaborative innovation using an improved G1-CRITIC comprehensive evaluation model. J. Innov. Knowl. 2023, 8, 100289. [Google Scholar] [CrossRef]
- Zhang, L.; Cheng, Q.; Qu, S. Evaluation of Railway Transportation Performance Based on CRITIC-Relative Entropy Method in China. J. Adv. Transp. 2023, 2023, 5257482. [Google Scholar] [CrossRef]
- Zhong, S.; Chen, Y.; Miao, Y. Using improved CRITIC method to evaluate thermal coal suppliers. Sci. Rep. 2023, 13, 195. [Google Scholar] [CrossRef] [PubMed]
- Du, Y.; Zheng, Y.; Wu, G.; Tang, Y. Decision-making method of heavy-duty machine tool remanufacturing based on AHP-entropy weight and extension theory. J. Clean. Prod. 2020, 252, 119607. [Google Scholar] [CrossRef]
- Li, Q.; Wang, Z.; Lu, L.; Ma, Q. Construction Risk Evaluation of Poor Geological Channels Based on Cloud Model-Improved AHP-Matter-Element Theory. Sustainability 2021, 13, 9632. [Google Scholar] [CrossRef]
- Dong, J.; Liu, D.; Liu, Y.; Huo, H.; Dou, X.; Bao, A. Trading performance evaluation for traditional power generation group based on an integrated matter-element extension cloud model. Energy Rep. 2021, 7, 3074–3089. [Google Scholar] [CrossRef]
- Lu, Y.; Zhang, G.; Qi, J.; Huang, Y. Operational state assessment of cross-linked polyethylene power cable on the basis of an optimized cloud matter-element theory. Sustain. Energy Techn. 2021, 48, 101584. [Google Scholar] [CrossRef]
- Zou, Y.; Zhang, Y.; Ma, Z. Emergency Situation Safety Evaluation of Marine Ship Collision Accident Based on Extension Cloud Model. J. Mar. Sci. Eng. 2021, 9, 1370. [Google Scholar] [CrossRef]
- Wu, T.; Gao, Y.; Zhou, Y.; Sun, H. A novel comprehensive quantitative method for various geological disaster evaluations in underground engineering: Multidimensional finite interval cloud model (MFICM ). Environ. Earth Sci. 2021, 80, 1–18. [Google Scholar] [CrossRef]
- Yao, X.; Deng, H.; Zhang, T.; Qin, Y. Multistage fuzzy comprehensive evaluation of landslide hazards based on a cloud model. PLoS ONE 2019, 14, e0224312. [Google Scholar] [CrossRef]
- Gu, H.; Fu, X.; Zhu, Y.; Chen, Y.; Huang, L. Analysis of Social and Environmental Impact of Earth-Rock Dam Breaks Based on a Fuzzy Comprehensive Evaluation Method. Sustainability 2020, 12, 6239. [Google Scholar] [CrossRef]
- Karakoç, Ö.; Avni Es, H.; Fırat, S.Ü. Evaluation of the development level of provinces by grey cluster analysis. Procedia Comput. Sci. 2019, 158, 135–144. [Google Scholar] [CrossRef]
- Zhao, B.; Ren, Y.; Gao, D.; Xu, L. Performance ratio prediction of photovoltaic pumping system based on grey clustering and second curvelet neural network. Energy 2019, 171, 360–371. [Google Scholar] [CrossRef]
- Xie, N.M.; Su, B.T.; Chen, N.L. Construction mechanism of whitenization weight function and its application in grey clustering evaluation. J. Syst. Eng. Electron. 2019, 30, 121–131. [Google Scholar]
- Khalid, U.; Sagoo, A.; Benachir, M. Safety Management System (SMS) framework development—Mitigating the critical safety factors affecting Health and Safety performance in construction projects. Saf. Sci. 2021, 143, 105402. [Google Scholar] [CrossRef]
- Pilanawithana, N.M.; Feng, Y.; London, K.; Zhang, P. Framework for measuring resilience of safety management systems in Australian building repair and maintenance companies. J. Saf. Res. 2023, 85, 405–418. [Google Scholar] [CrossRef] [PubMed]
- Yang, W.; He, S. Coal mine safety management index system and environmental risk model based on sustainable operation. Sustain. Energy Techn. 2022, 53, 102721. [Google Scholar] [CrossRef]
- Lee, J.C. Coefficient alpha and the internal structure of tests. Psychometrika 1951, 16, 297–334. [Google Scholar]
- Chen, M.; Tan, Y. SF-FWA: A Self-Adaptive Fast Fireworks Algorithm for effective large-scale optimization. Swarm. Evol. Comput. 2023, 80, 101314. [Google Scholar] [CrossRef]
- Dulebenets, M.A. An Adaptive Polyploid Memetic Algorithm for scheduling trucks at a cross-docking terminal. Inform. Sci. 2021, 565, 390–421. [Google Scholar] [CrossRef]
- Pasha, J.; Nwodu, A.L.; Fathollahi-Fard, A.M.; Tian, G.; Li, Z.; Wang, H.; Dulebenets, M.A. Exact and metaheuristic algorithms for the vehicle routing problem with a factory-in-a-box in multi-objective settings. Adv. Eng. Inform. 2022, 52, 101623. [Google Scholar] [CrossRef]
- Singh, P.; Pasha, J.; Moses, R.; Sobanjo, J.; Ozguven, E.E.; Dulebenets, M.A. Development of exact and heuristic optimization methods for safety improvement projects at level crossings under conflicting objectives. Reliab. Eng. Syst. Saf. 2022, 220, 108296. [Google Scholar] [CrossRef]
- Singh, E.; Pillay, N. A study of ant-based pheromone spaces for generation constructive hyper-heuristics. Swarm. Evol. Comput. 2022, 72, 101095. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).