1. Introduction
The extreme consumption of the Internet in numerous fields is motivating technologists and researchers [
1]. Moreover, the usage of intelligent systems can assist users and various applications, ensuring proficient computation, and maintaining the quality of service throughout the networks [
2]. The conventional techniques were less efficient, providing average performance and time consumption, and were not suitable for offering solutions in complex, multi-purpose, or real-time difficulties [
3]. Consequently, the requirement of a proficient attack identification system can decrease the destructive special effects of cyber threats [
4]. Cyber security involves security mechanisms and combinations of different technological developments to protect information, destruction of data and networks, and programs against dissimilar attack activities like modification of information, unauthorized access, and robbery through the network or Internet [
5]. Components of cybersecurity consider mostly network security systems and host protection. Presently, it is utilized for protecting various fields, namely the Internet of Things (IoTs), cloud computing (CC), and wireless sensor networks (WSNs) [
6]. Several security estimations are obtainable for providing that security to the networks or models, like firewalls, IDS, and anti-virus software. Nevertheless, cyber threats are regularly harmful and interrupt internet services day by day. This encourages numerous researchers to provide their broad offers to pattern security systems [
7].
Effective cyber attack detection and prevention contribute to sustainability by minimizing economic losses, reducing electronic waste, maintaining trust, improving energy efficiency, promoting responsible digital transformation, ensuring supply chain resilience, and preventing potential environmental damage [
8]. Cyber attack detection and sustainability share common principles of proactive risk management, ethical responsibility, resilience, and the well-being of individuals, organizations, and the planet. By integrating robust cybersecurity practices into the fabric of sustainable initiatives, society can work toward a safer, more secure, and environmentally responsible future [
9]. In addition, sustainable businesses prioritize long-term viability, and cyber attack detection plays a vital role in maintaining operational continuity. By preventing and swiftly responding to cyber threats, organizations can avoid costly disruptions, financial losses, and reputational damage [
10]. Furthermore, detecting and mitigating attacks promptly can reduce resource consumption, including energy, time, and human effort. By conserving resources, both within organizations and in the broader context, cyber attack detection aligns with principles of environmental sustainability. Moreover, detecting and preventing attacks reduces unnecessary network and system activity, contributing to lower carbon emissions and a smaller environmental footprint [
11]. Finally, sustainable practices include ethical considerations, and protecting user data and privacy is a fundamental ethical responsibility. Cyber attack detection helps safeguard personal information, fostering trust between businesses and their customers. This trust is crucial for sustaining healthy relationships and long-term business success.
The widely different techniques applied for detecting attacks extensively are classified into three main kinds, such as misuse-based, hybrid-based, and anomaly-based identification [
12]. In the detection technique of misuse-based cyber attacks, they can be examined with pre-recorded attack signatures, and the technique is utilized significantly for detecting the identified attacks. It is helpful to identify the well-known attacks with the fewest false alerts or alarms. The technique needs a few conversions of the rules of attacks and signatures on the datasets [
7]. Researchers have been encouraged to use decentralized IDSs that incorporate various machine learning (ML) methods comprising optimization algorithms, deep learning (DL), and artificial neural networks (ANNs), on account of current developments in intelligent machines. Generally, ANNs are limited in their capability to handle the complexities of IDS systems [
13]. DL is a subcategory of ML that contains the unsupervised and supervised learning approaches, and it is based on the number of layers of ANNs [
14]. Every layer consists of certain neurons with activated functions that are applied to generate non-linear results. The technology is motivated by the biological neuron structures of the brain, but it is broadly relevant to communication models and data processing in the natural nervous system [
15]. DL algorithms acquire crucial abstract illustrations from the original information over the usage of the multiple-level learning technique hierarchically.
This study develops blockchain-assisted hybrid metaheuristics with machine learning-based cyber attack detection and a classification (BHMML-CADC) algorithm. The objective of the BHMML-CADC method lies in its accurate detection and classification of cyber attacks. To accomplish this, the BHMML-CADC method employs BC technology using the Ethereum blockchain for attack detection. In addition, a hybrid-enhanced glowworm swarm optimization (HEGSO) system was used for feature selection (FS). Moreover, cyber attacks can be identified by the design of a quasi-recurrent neural network (QRNN) model. Finally, a hunter–prey optimization (HPO) method can be employed for the optimum selection of the QRNN parameters, which has a rapid convergence rate and a considerable optimization capacity. The experimental outcome of the BHMML-CADC method was validated on benchmark datasets.
2. Related Research
This section briefly examines existing studies related to cyber attack detection techniques using ML and DL models. Babu et al. [
16] introduced a permission-based BC technology that exploits the arbiter PUF model for protecting the key pair of IoT devices through a lightweight technique. An integrated detection technique is used for identifying the DDoS on IoT via an ML-based ensemble algorithm. Then, a BC technique was integrated that safely shares the alarm signals to every single node of the IoT, with secure authentication. The authors in [
17] performed a BC on cluster head (CH) and base station (BS) for registering the node using authorizations, and to address security challenges. Furthermore, ML classifiers called histogram gradient boost (HGB), were applied on the BS to categorize the node as legitimate or malicious. In addition, a wide range of experiments were conducted by the WSN. Dehghani et al. [
18] introduced a selective ensemble DL algorithm using gray wolf optimization (GWO) technique for identifying the FDIA in DC-MG. Initially, to collect adequate information within the typical performance needed for model training, load change was considered to identify datasets for load variation schemes and cyber attacks during the data generation process.
Bhayo et al. [
19] devised an ML-based algorithm for the recognition of DDoS attacks in SDN-WISE IoT controllers. The study incorporated ML-based detection techniques into the controller, and set up testbed environments for stimulating the traffic generation of DDoS attacks. Saheed and Arowolo [
20] introduced a deep RNN (DRNN) and supervised ML techniques (KNN, RF, DT, and ridge classifiers) that are used to design an effective IDS in IoMT environments for the classification and prediction of unexpected cyber threats. Normalization and pre-processing of data were implemented. Later, we enhanced features through the biologically simulated PSO model. Khan et al. [
21] improved the accuracy of UAVs with a decentralized ML structure based on BC. The presented method framework is able to considerably increase the storage and reliability of information for intelligent decision-making amongst different UAVs.
The authors in [
22] developed a cyber attack detection technique for IoMT-based network, utilizing ensemble learning and a fog-cloud platform for addressing security challenges. The ensemble method exploits an LSTM network as individual learners, and stacks DTs on top of them to categorize normal events and attacks. Reddy and Shyam [
23] developed a new architecture for the mitigation of attack nodes using secured SaaS architecture. The important role of this study was to provide an attack detection system that is performed in DBN, where the weight and the activation function are fine-tuned by the Median Fitness-oriented Sea Lion Optimizer technique (MFSLnO). Once the DBN recognizes the attack nodes, then control is transported to the lightweight bait method that consistently alleviates the attack node without disturbing the connection. Ashraf et al. [
24] developed an SDN-based IoT anomaly detection technique that identifies attacks and abnormal behaviors. Three ML approaches, SVM, KNN, and MLP, are utilized to develop an IDS, which is employed at the SDN controller to learn and monitor the behaviors of IoT gadgets, and any other deviations from the behaviors can be considered as an attack. After examining the existing research, it was noticed that the current methods do not focus on the hyperparameter selection method, which largely affects the accuracy of the classification algorithm. In particular, the hyperparameters involving learning rate selection, epoch count, and batch size are important to obtain effective outcomes. A metaheuristic algorithm is applied, since the trial-and-error technique for hyperparameter tuning is an erroneous and difficult process. Thus, the HPO technique is used for the parameter selection of the QRNN model in this research.
3. The Proposed Model
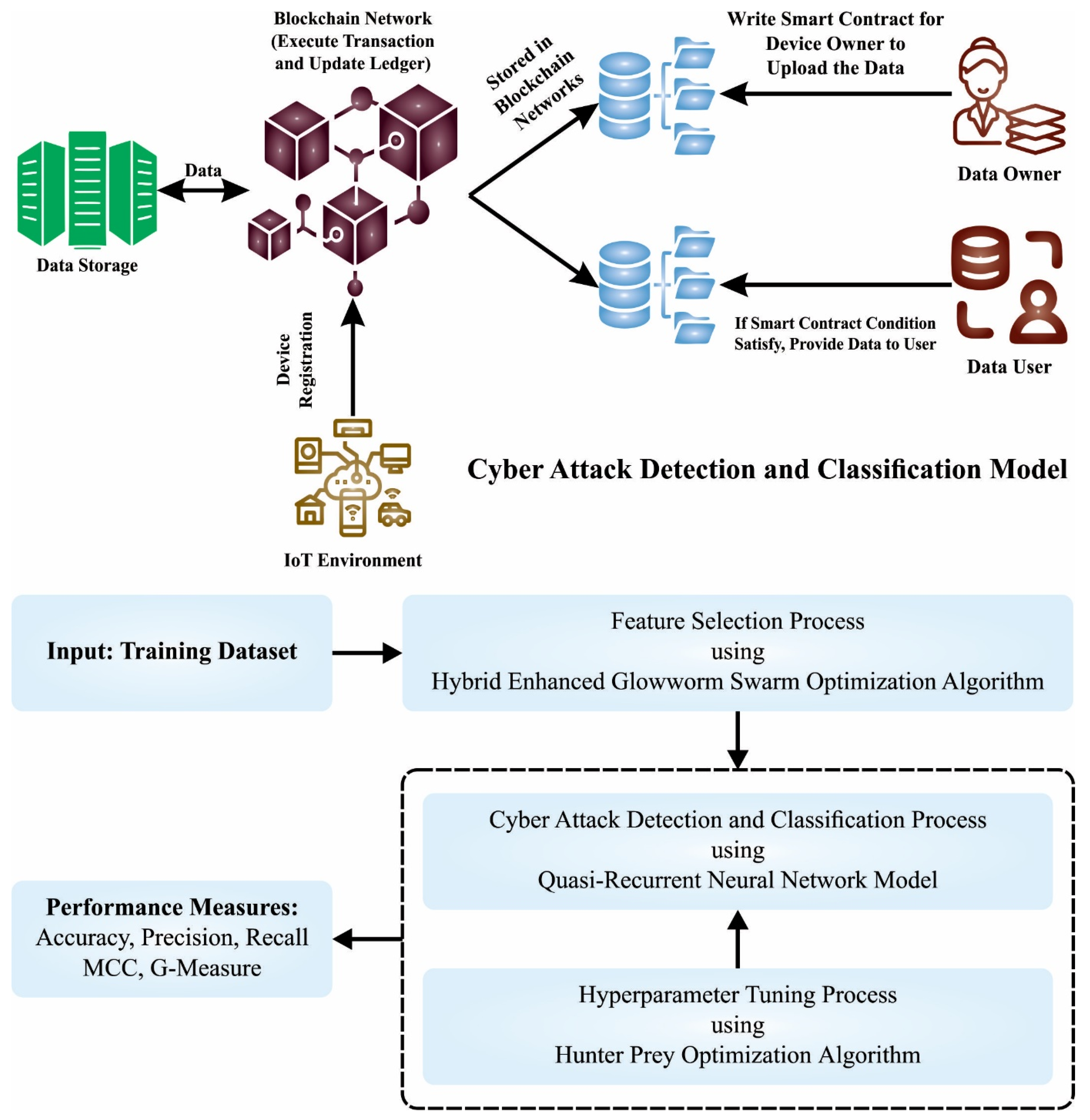
In this study, the BHMML-CADC method was introduced for the detection and classification of cyber attacks. The purpose of the BHMML-CADC technique is to exploit BC technology with FS and an optimal DL model for cyber attack recognition. To accomplish this, the BHMML-CADC technique follows several stages of operations, namely BC technology, pre-processing, HPO-based hyperparameter tuning, QRNN-based detection, and HEGSO-based FS.
Figure 1 demonstrates the overall work flow of the BHMML-CADC algorithm.
3.1. BC Technology for Cyber Attack Detection
BC is a list of records represented by the Merkle tree related to the cryptographic norm, but all the blocks hold the cryptographic hash of their previous block [
25]. BC resists all forms of data modification; meanwhile, modification of data in a single block should modify the subsequent block. Validation of a new block occurs before adding in the chain, and BC is considered more secure than the traditional distributed system, as it displays higher Byzantine fault tolerance despite not being un-modifiable. The distributed ledger records the transaction between both entities in a verifiable and permanent manner, and also aids in increasing trust in social and economic activities.
The development tools such as Oraclize API, truffle suite, and web3.js API were exploited, and smart contract (SC) was introduced in solid language to carry out the necessary transactions among each participant for the implementation of Ethereum BC. The initial activity implemented in the SC is about beginning the attack detection by identifying the financial deals, and the input and output accuracy. InterPlanetory File System (IPFS) is utilized as decentralized storage after learning the local data pattern, which records the parameter related to the attack detection as a hash value that is distributed to decentralized applications (DApp). The assessment of off-chain is implemented, and the result is declared in the DApp. The next action performs the retrieval of assessment in the single node by Web3.js API, within the predetermined threshold by the minimum acceptable fitness rate (MAFR). The analysis, which is superior to MAFR, then interacts with the processing agent through the payable function, which can be performed through BC.
3.2. Pre-Processing
Primarily, the BHMML-CADC technique undergoes preprocessing using min–max normalization [
26]. For all the features, the maximum values are changed to
, the minimum values are changed to
, and each value is converted to a decimal between [0, 1]. The succeeding formula was utilized for normalizing the feature.
In Equation (1), represents the group of feature values attained, and show the maximal and minimal values in , respectively.
3.3. Feature Selection Using HEGSO Algorithm
The HEGSO method is exploited for the optimum selection of features. The classical GSO method is based on the natural behaviors of the glowworm during nighttime [
27]. Based on the luciferin, the glowworm displays a type of interaction with other glowworms in the population. If the light discharged through the glowworm is greater, then the luciferin is greater. There exist three dissimilar stages, namely luciferin update, movement, and the update and neighborhood stage. The number of luciferins is equivalent to the fitness of their existing location on the objective function. Next is the movement phase. Using the HEGSO technique, optimization can be carried out. The optimization technique initiates once the path is found between the beginning and ending points of the vehicle nodes. The steps for the HEGSO technique are shown as follows:
Step1: Initialize the Search Agents (SA), viz., the size of population
an initial value of radial gamut of SA
individual glowworm
;
shows the step size, iteration counter
, luciferin’s initial value
and time instance
.
Step2: Evaluate the fitness function (FF) based on Equation (3):
where
denotes the average speed of vehicles on the road,
indicates the vehicle, and
shows the overall length of the road segments.
Step3: This phase is the luciferin phase. Here, the new SA can be evaluated using the subsequent equation:
In Equation (4), shows the luciferin decay constant within [], implies the luciferin values of the SA at time, is the luciferin value of the SA at time, and indicates the FF.
Step4: The objective function of the new SA is evaluated according to similar fitness.
Step5: Based on the brightness, the SA moves towards the adjacent glowworm. The movement of SA can be determined by the EDs among the glowworms. During the movement phase, the SA heads for the computed neighborhood based on probabilistic means. It can be mathematically modelled by Equation (5):
where
denotes the step size.
Step6: The decision range and neighborhood range of the SA are updated in this step. The decision rules are used based on the following expression:
In Equation (6), shows the prior value of the neighborhood range, represents the SA with a higher luciferin value from the decision range, shows the upgrade values of the neighborhood range, denotes the constant, and indicates the maximum sensing radius of the glowworms.
Step7: If the termination criteria are satisfied, then the fittest solution can be attained. If they are not satisfied, then the mutation and crossover operators can be used. The two-point crossover is exploited.
The FF used in the HEGSO technique is developed to take a balance between the classification accuracy (maximal) and the amount of feature selections (minimal) attained; Equation (10) signifies the FF to evaluate the solution.
In Equation (7), refers to the cardinality of the selected subset, indicates the classification error rate, symbolizes the overall feature count, and parameters and are respective to the importance of classification quality and subset length. ∈ [1,0] and
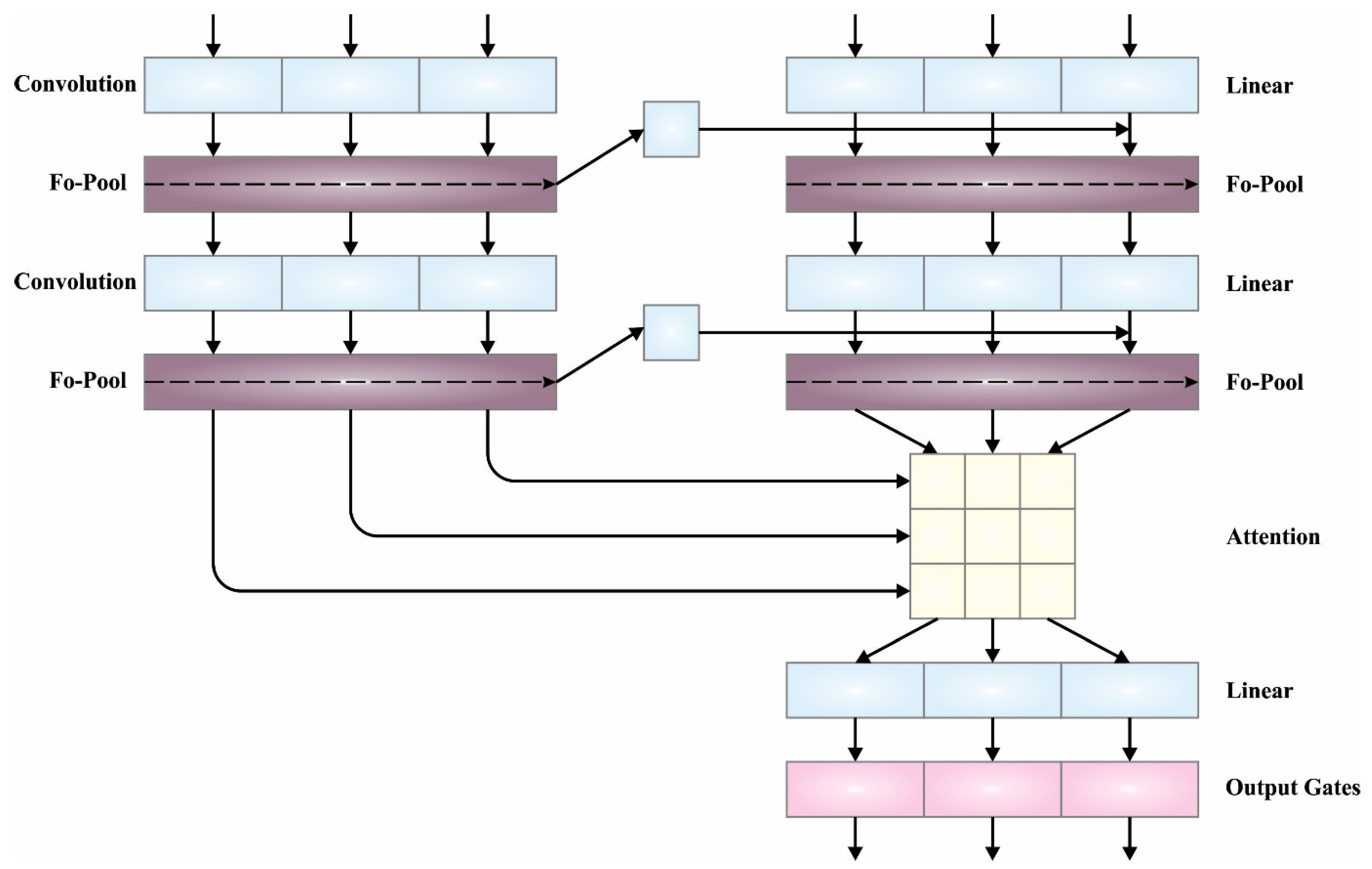
3.4. QRNN-Based Cyber Attack Detection
At this stage, the QRNN architecture is used for the detection and classification of cyber attacks. QRNN is a hybrid NN inspired by the LSTM, which brings the benefits of CNN and LSTM together [
28]. CNN is fast and extremely parallelizable, while LSTM has the potential to model long-range dependency. However, LSTMs and RNNs have a slower recurrent step. Actually,
relies on
, which relies in its turn on
, etc., thereby generating an execution bottleneck.
Figure 2 depicts the infrastructure of QRNN.
The hidden-hidden matrix multiplication of LSTM is eliminated, and the convolution size of
over input
is provided to diminish the computation effort needed for the recurrent step, t. Furthermore, the forget and input gates are connected, which produces output gate
and forget gate
. The QRNN with
-pooling can be described by the subsequent expression:
Subsequently, the recurrent step is a weighted or gated sum, thus effectuating faster implementation. This provides a probability for the unbounded activation function, including the ReLu function, considering that the hidden layer cannot exponentially grow anymore.
3.5. Hyperparameter Tuning Using HPO Algorithm
Finally, the HPO algorithm optimally chooses the hyperparameters related to the QRNN models, including the learning rate, number of epochs, and batch size. The HPO algorithm is a new swarm-based optimization technique that mimics the behaviors between the prey and predators. The HPO imitates the predictor behaviors during hunting the prey; in the meantime, the prey moves towards the safer region to escape from the predator. Consequently, based on the modified site of the safer region, the safer region is updated dynamically, and the predator must update its position. In HPO, Iraj et al. [
29] explored the safer region corresponding to the better objective values. As HPO is a metaheuristic algorithm, it begins with the collection of random solutions that are calculated using Equation (12):
where
and
denote the upper and lower boundaries of the searching field
vector form with dimension
, and
shows the uniformly distributed random value. The
and
symbols are the numbers of the problem variables and the overall population size, respectively.
The primary group of solutions for detecting the bad and good solutions can calculate the FF. Next, the primary phase of the solution can be updated using the key stages of the HPA method through the set of independent runs. In the HPO, the search process comprises two different stages, the exploitation and exploration phases. During the exploration phase, the agent explores with higher randomness to find the local and global points in the searching space. On the other hand, the exploitation stage repossesses minimal randomization for circulating the potential solution. In this context, Iraj et al. developed the subsequent equation to model the exploration and exploitation stages of the model:
In Equation (13),
refers to the corresponding present and future locations of the
ith hunter. The prey location can be represented as
; the
, and
symbols are the balancing parameters, adaptive parameters, and mean of each location, respectively. This parameter is calculated with the following expression:
where
refers to the index number of the vector
that meets the criteria of
and
;
, and
denote the random vector within
.
denotes the maximal number of iterations. The balance parameter
is calculated with Equation (15), whose value drops from 1 to 0.02 through the number of iterations. As previously stated, HPO aims to catch the prey; thus, the prey upgrades the place through the average of each location (
) using Equation (14), and later calculates the distance of all the searching agents from the mean position [
30].
Based on the Euclidean distance, the distance can be evaluated as follows:
The searching agent with a maximum distance in the mean of placement is assumed to be the prey
.
In Equation (18),
,
denotes the number of solutions. Once the prey are attacked, they attempt to escape toward the safer region. Iraj et al. supposed the optimal safer place is the global optimal location, and the hunter may upgrade the current location to choose another prey via the subsequent equation:
In Equation (19),
denotes the safe place (global optimal location) and
shows the random integer. Iraj et al. considered the subsequent Equation (8) to differentiate between the hunters and prey.
In Equation (20),
denotes a random number that lies in [
], and
shows the regulatory parameter set as
. The HPO approach develops an FF to obtain a greater classifier solution. It defines a positive integer to indicate the fittest solution for candidate performances. In this case, the decline in the classifier error rate could be regarded to be FF.
4. Results and Discussion
The proposed model was simulated using Python 3.6.5 tool on a PC i5-8600k, GeForce 1050Ti 4 GB, 250 GB SSD, 1 TB HDD, with 16 GB RAM. The followingparameter settings were provided: batch size: 5, dropout: 0.5, learning rate: 0.01, epoch count: 50, and activation: ReLU.
In this section, the cyber attack detection performance of the BHMML-CADC algorithm is tested on the BOT-IoT dataset [
31,
32], comprising 4500 samples and 9 classes, as represented in
Table 1.
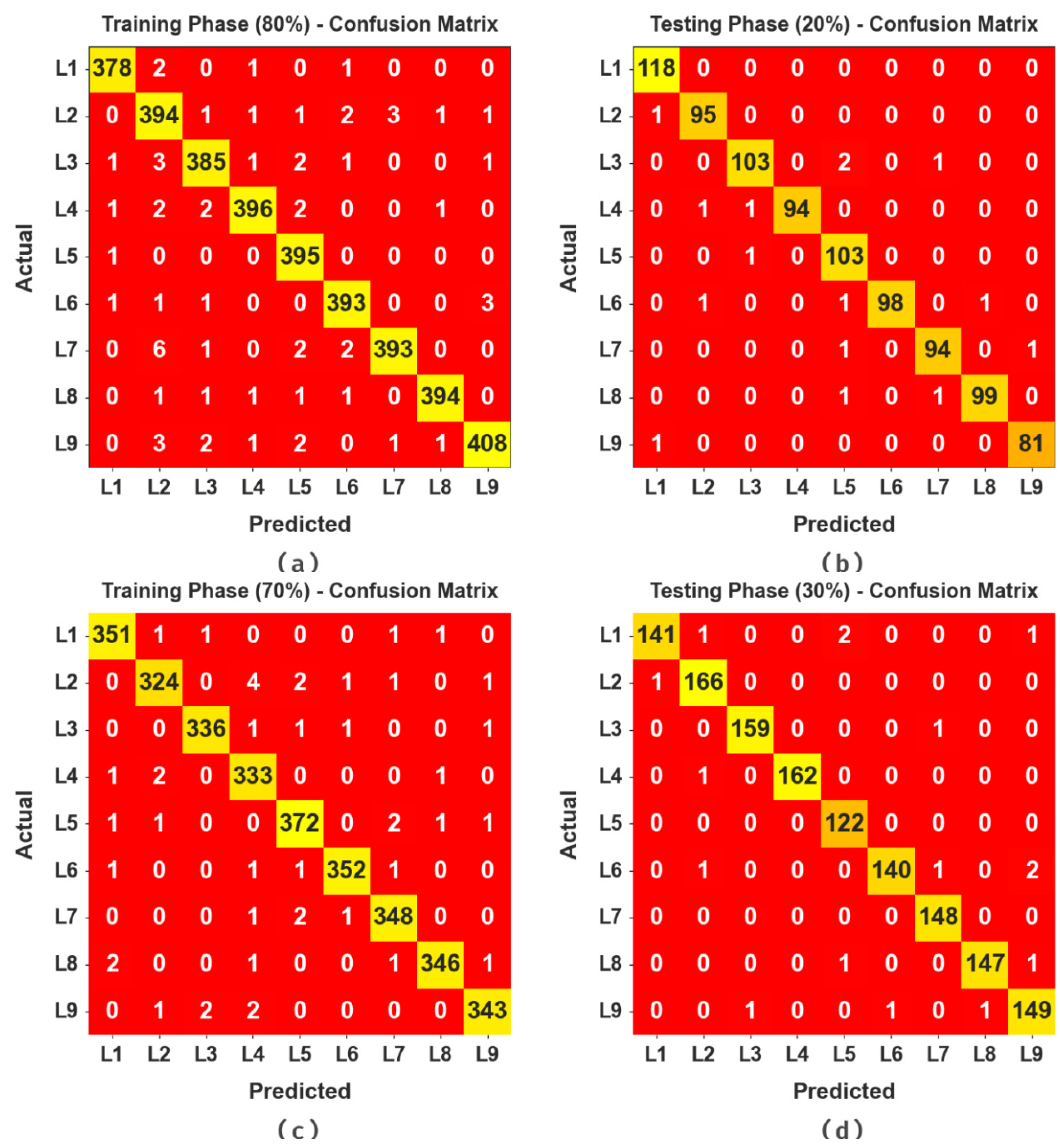
The cyber attack classification outcomes of the BHMML-CADC technique are demonstrated in
Figure 3. The experimental outcome was that the BHMML-CADC method achieved effective outcomes, with the distinct categorization of the class labels.
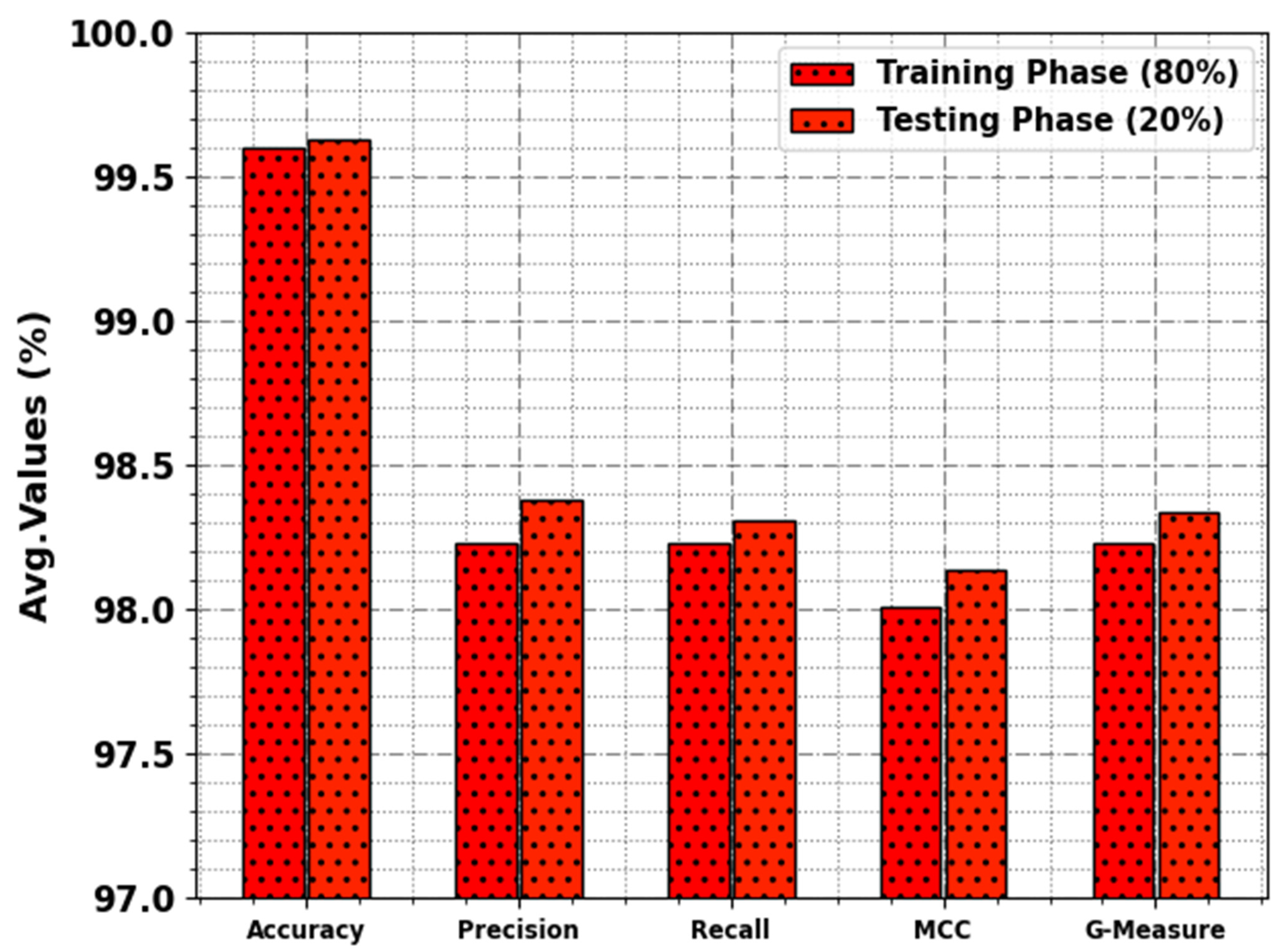
In
Table 2 and
Figure 4, the overall cyber attack detection outcome of the BHMML-CADC method is highlighted at 80:20 of the TR set/TS set. The outcomes shows that the BHMML-CADC method categorizes different kinds of attacks proficiently.
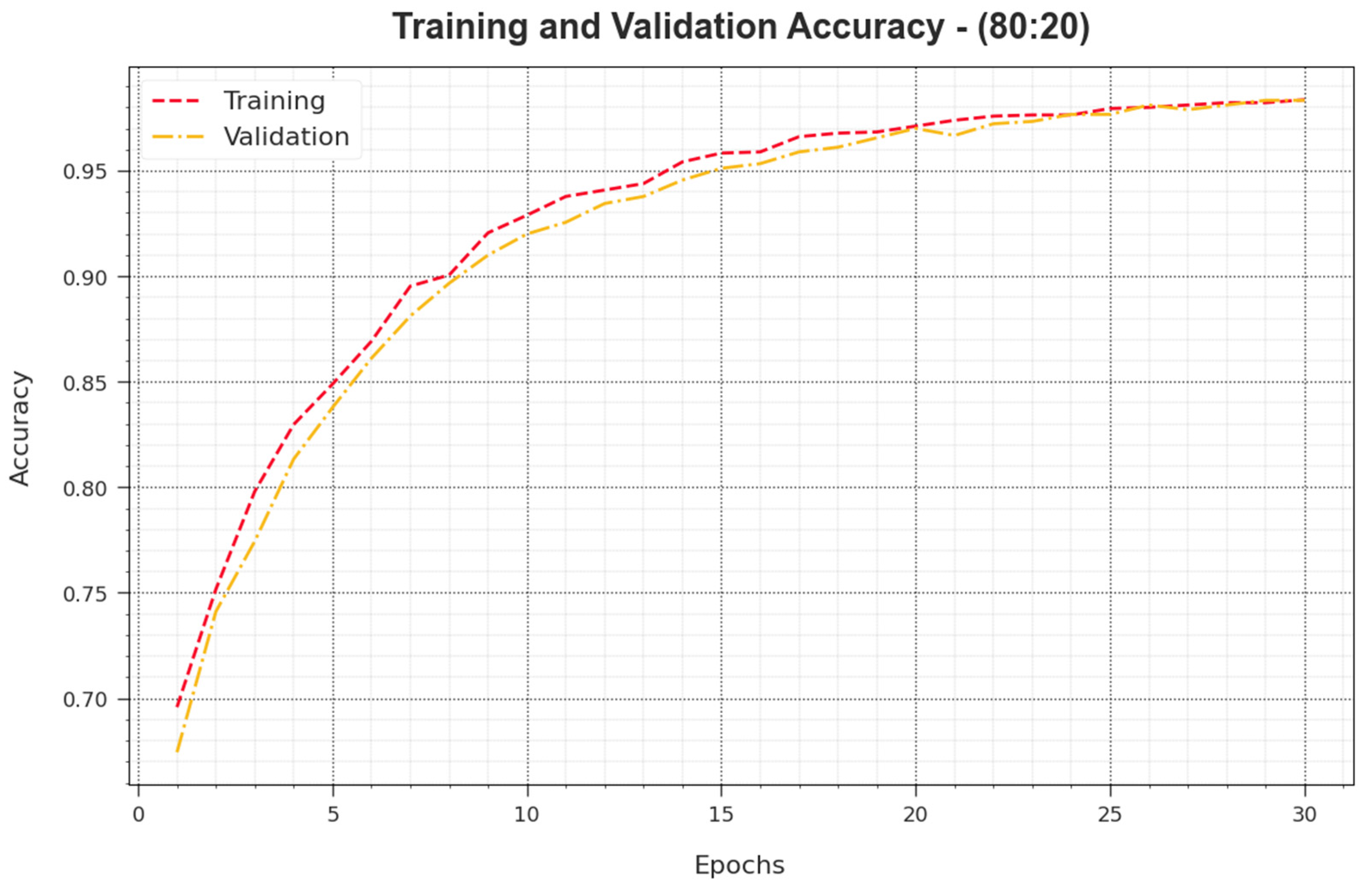
Figure 5 presents the training accuracies
and
of the BHMML-CADC method for the 80:20 TR set/TS set. The
can be defined by the approximation of the BHMML-CADC method on the TR database, whereas the
is calculated by estimating the performance of the different testing databases. The experimental outcomes demonstrated that
and
increase with an increase in epochs. Consequently, the performance of the BHMML-CADC method improves to enhance the TR and TS databases with upsurges in many epochs.
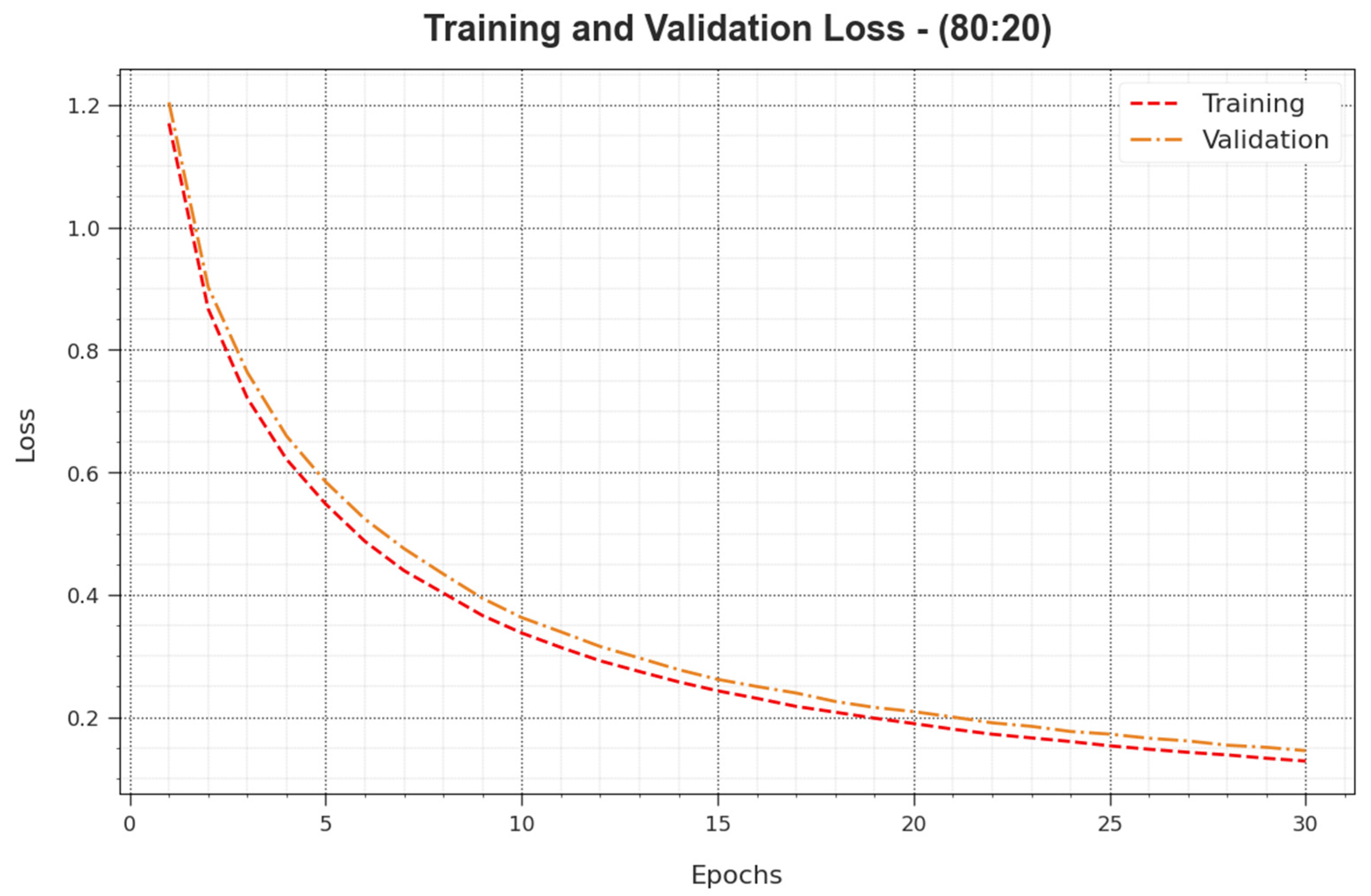
In
Figure 6, examination of the
and
of the BHMML-CADC algorithm for the 80:20 TR set/TS set is presented. The
defines the error between the predicted performance and original values on the TR database. The
indicates the measured performance of the BHMML-CADC method on the validation data. The outcomes show that the
and
tend to decrease with maximum epochs. This depicts the superior performance of the BHMML-CADC approach, and its capability to produce an accurate classification. The reduced values of the
and
show the maximum performance of the BHMML-CADC method in obtaining the patterns and relationships.
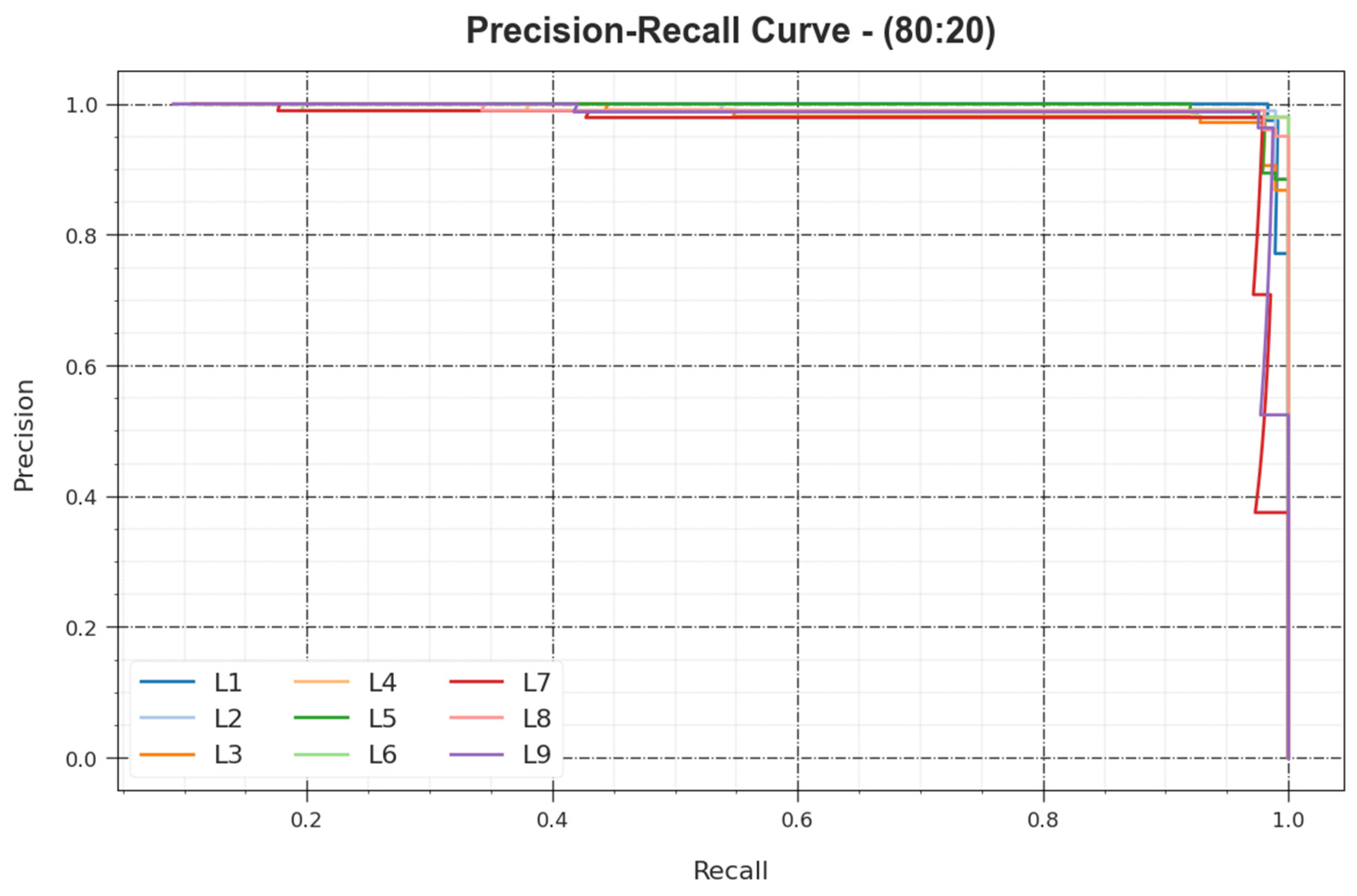
A summary precision–recall (PR) curve of the BHMML-CADC approach is shown for the 80:20 TR set/TS set in
Figure 7. The analysis shows the BHMML-CADC method outcomes in raising the PR values. Moreover, it was observed that the BHMML-CADC method achieved superior PR values on all of the class labels.
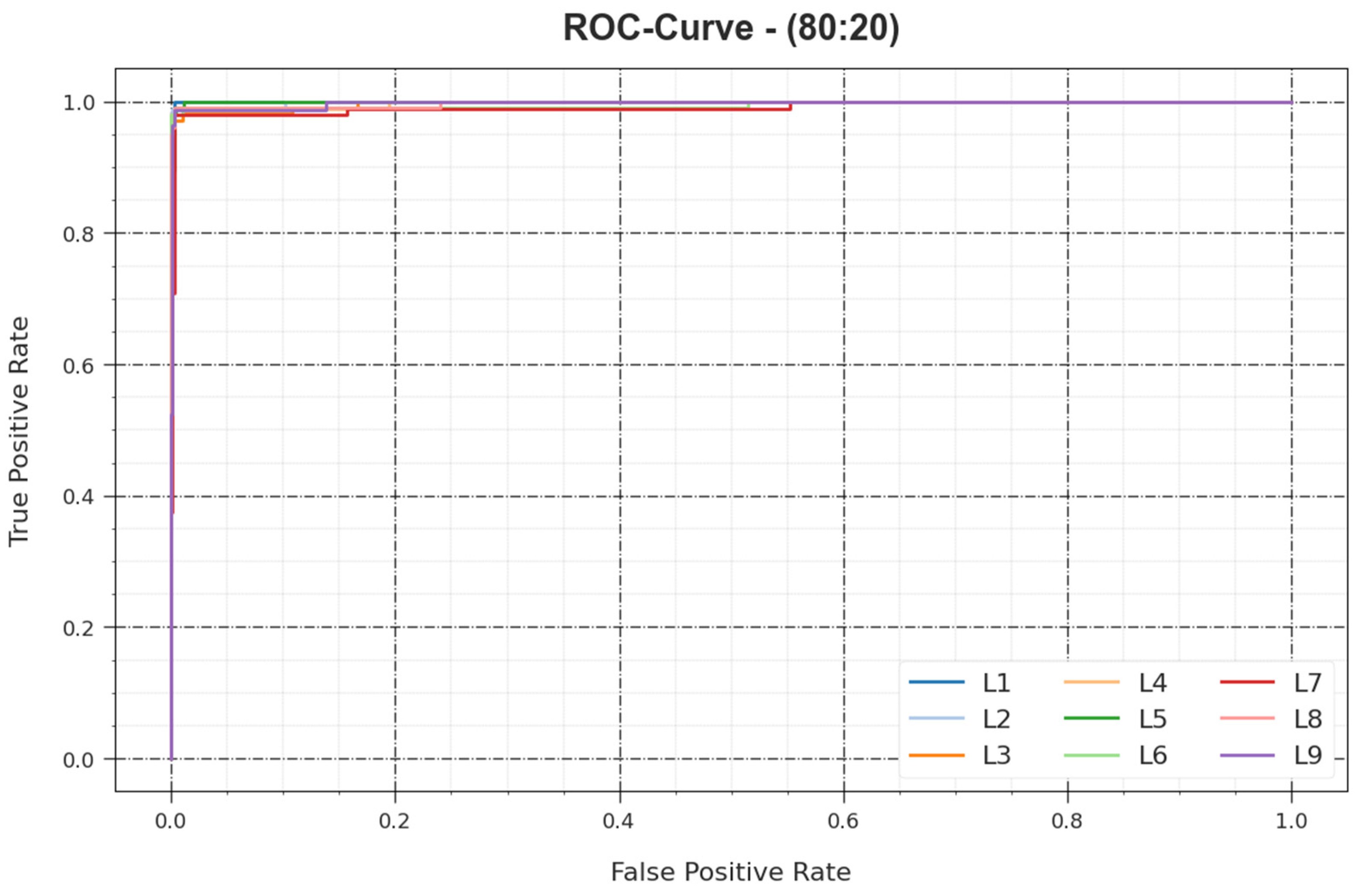
In
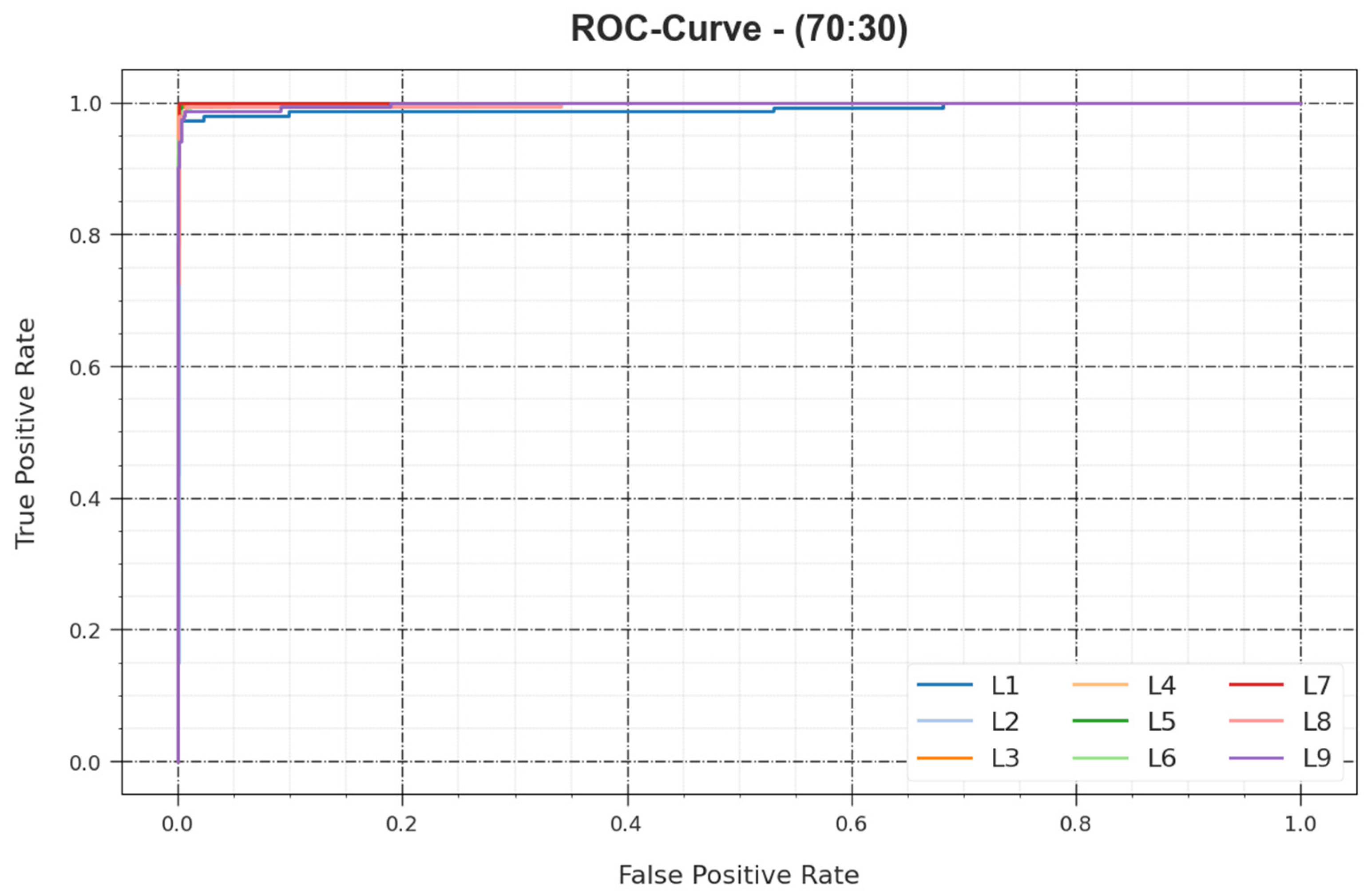
Figure 8, an ROC investigation of the BHMML-CADC method is shown for the 80:20 TR set/TS set. The figure portrays that the BHMML-CADC method yielded increased ROC values. Moreover, the BHMML-CADC method can be extended for the enhancement of ROC values on all class labels.
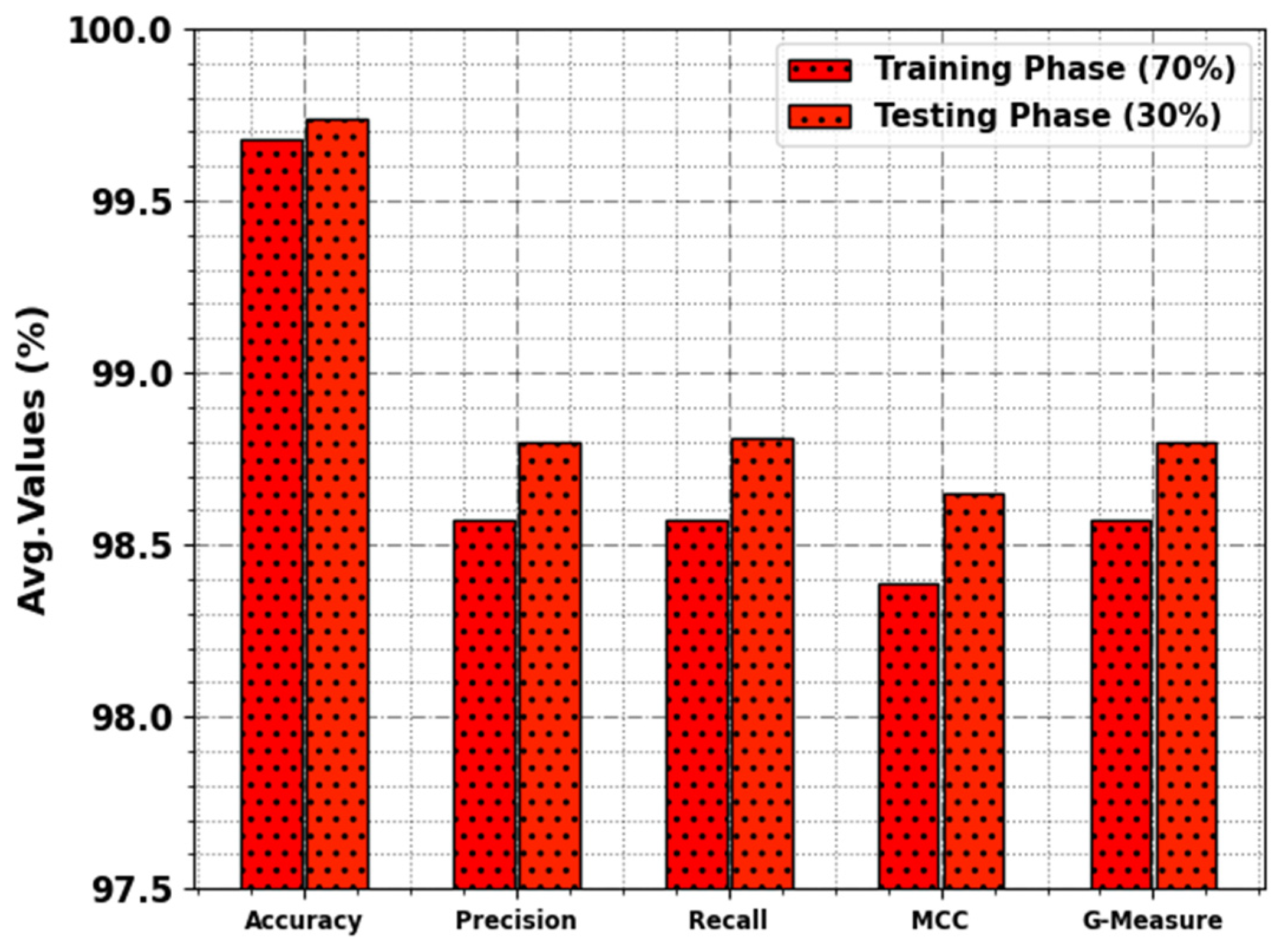
In
Table 3 and
Figure 9, the overall cyber attack identification performance of the BHMML-CADC method is evaluated for the 70:30 TR set/TS set. The outcomes denote that the BHMML-CADC method classifies various types of attacks efficiently. For instance, for the 70% TR set, the BHMML-CADC method provides average
,
,
, MCC, and
of 99.68%, 98.57%, 98.57%, 98.39%, and 98.57%, respectively. Therefore, for the 30% TS set, the BHMML-CADC approach appropriately provides average
,
,
, MCC, and
of 99.74%, 98.80%, 98.81%, 98.65%, and 98.80%, respectively.
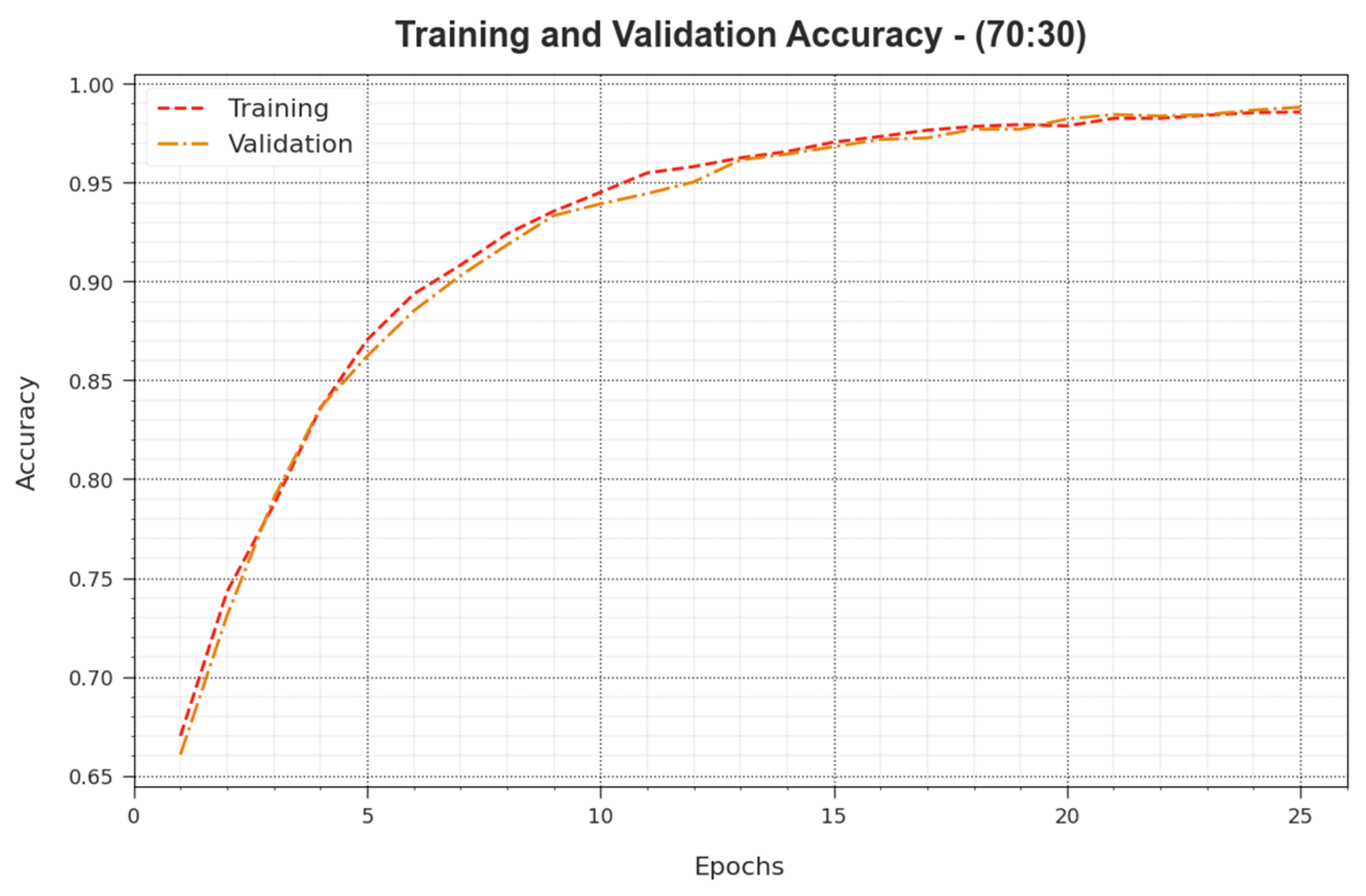
Figure 10 demonstrates the training accuracies
and
of the BHMML-CADC approach for the 70:30 TR set/TS set. The
is defined by the estimation of the BHMML-CADC method on the TR database, whereas the
is calculated by approximating the performance on the individual testing dataset. The outcomes show that
and
increase with increasing epochs. As an outcome, the performance of the BHMML-CADC method was required to enhance the TR and TS databases with upsurges in many epochs.
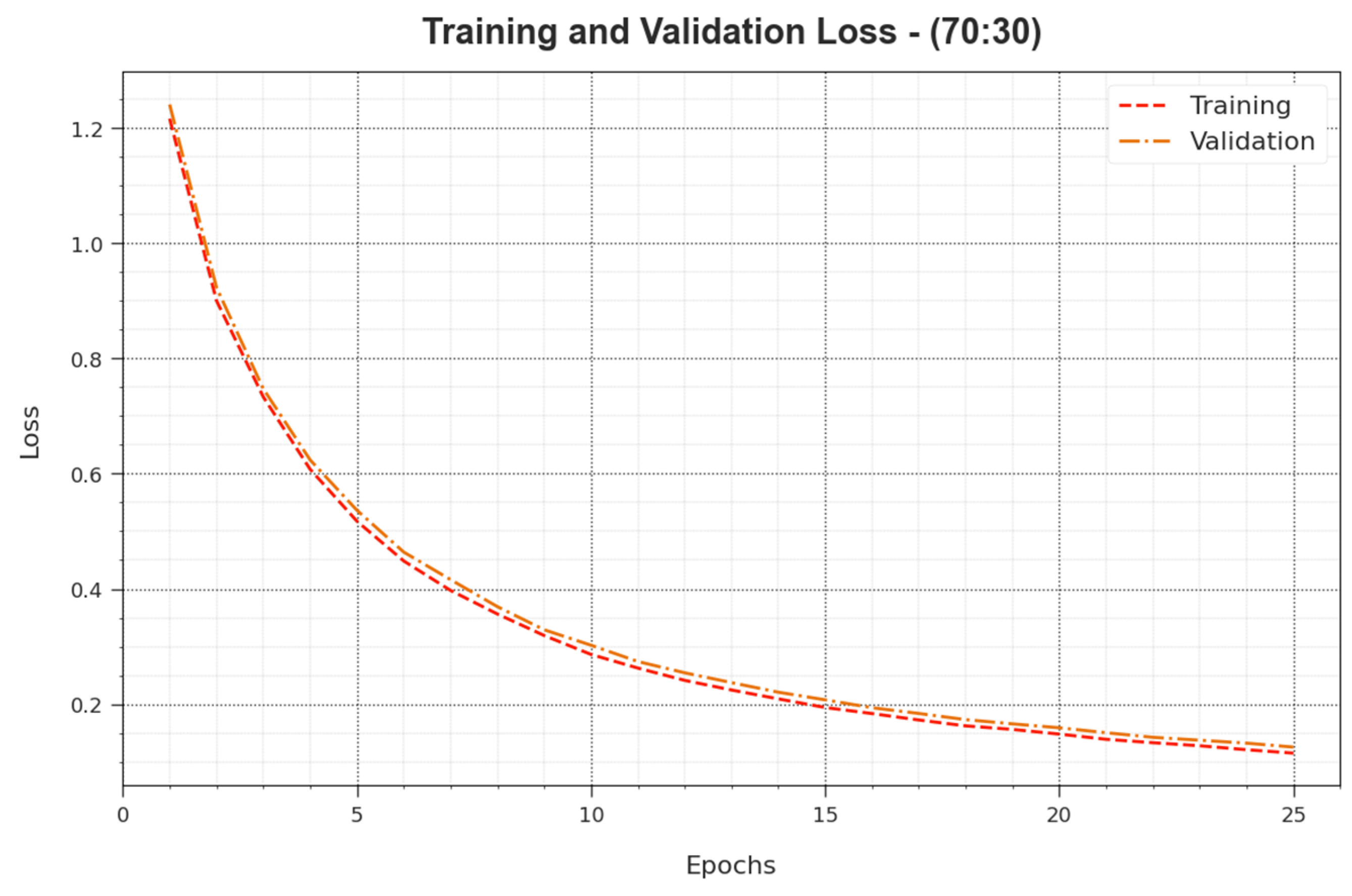
In
Figure 11, the
and
outcomes of the BHMML-CADC system for the 70:30 TR set/TS set are revealed. The
defines the error between the predicted performance and original values on the TR data. The
illustrates the measured performance of the BHMML-CADC method on separate validation data. The outcomes indicate that the
and
tend to decrease with growing epochs. These represent the enhanced outcomes of the BHMML-CADC method and its capability to produce an accurate classification. The reduced values of the
and
exhibit the greater performance of the BHMML-CADC approach on catching patterns and relationships.
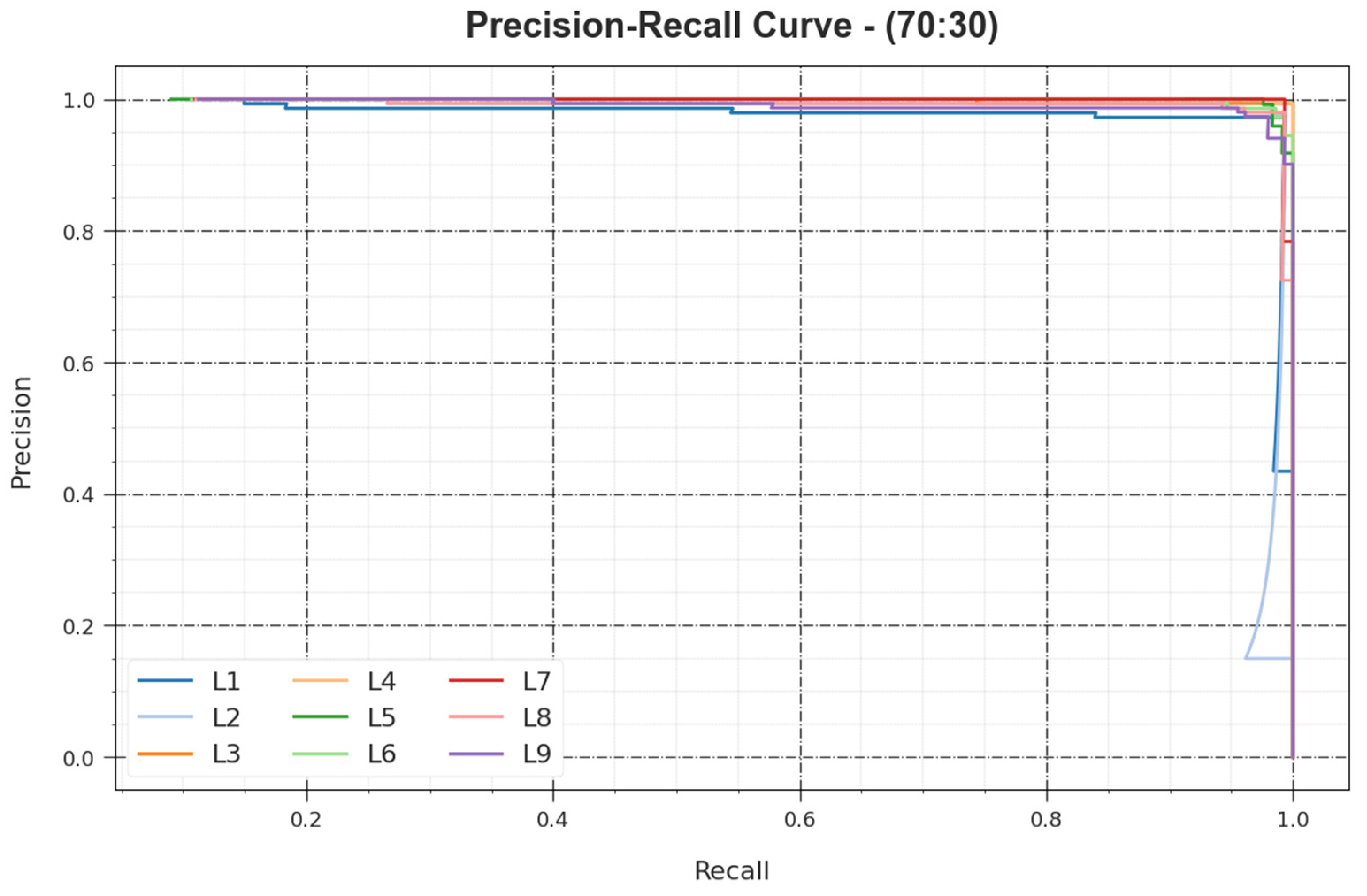
A summary of the analysis of the PR curve of the BHMML-CADC approach is shown for the 70:30 TR set/TS set in
Figure 12. The analysis illustrates that the BHMML-CADC methodology raises the PR values. Moreover, it can be seen that the BHMML-CADC method can obtain better PR values on all class labels.
In
Figure 13, an ROC investigation of the BHMML-CADC method is demonstrated for the 70:30 TR set/TS set. The figure shows that the BHMML-CADC method enhanced the ROC values. Additionally, the BHMML-CADC method can be extended for the enhancement of ROC values on all class labels.
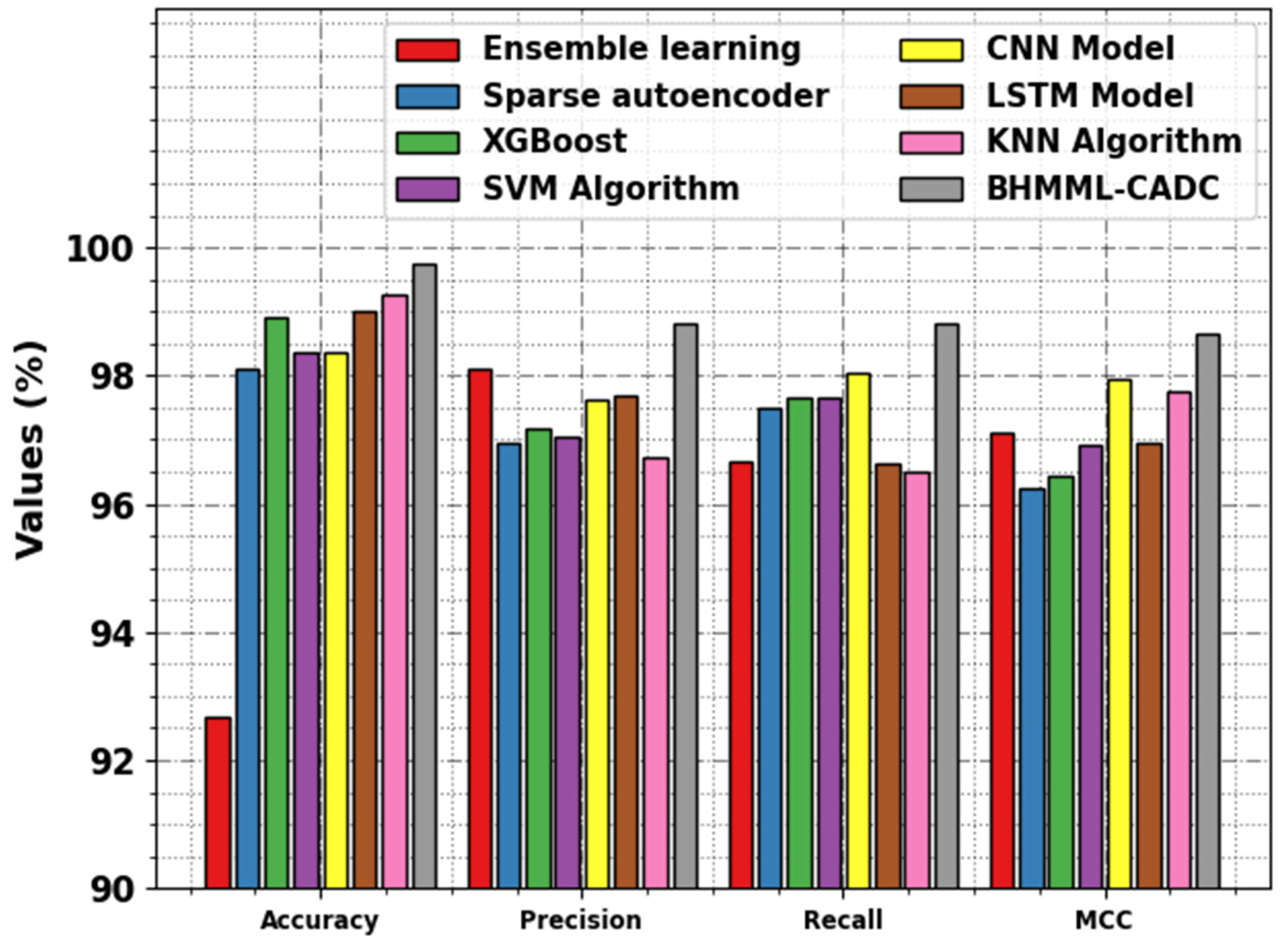
In
Table 4 and
Figure 14, detailed classification results of the BHMML-CADC technique are clearly illustrated [
33,
34,
35]. The experimental values highlight that the ensemble learning model achieves worse results. Simultaneously, the SAE, XGBoost, SVM, and CNN models show slightly boosted results. Along with that, the KNN model reported considerable performance with
,
,
, and MCC values of 99.26%, 96.74%, 95.60%, and 97.75%, respectively. Nevertheless, the BHMML-CADC technique accomplished improved performance with maximum
,
,
, and MCC values of 99.74%, 98.80%, 98.81%, and 98.65%, respectively. Therefore, the BHMML-CADC technique is an effective tool for the automated cyber attack detection process.
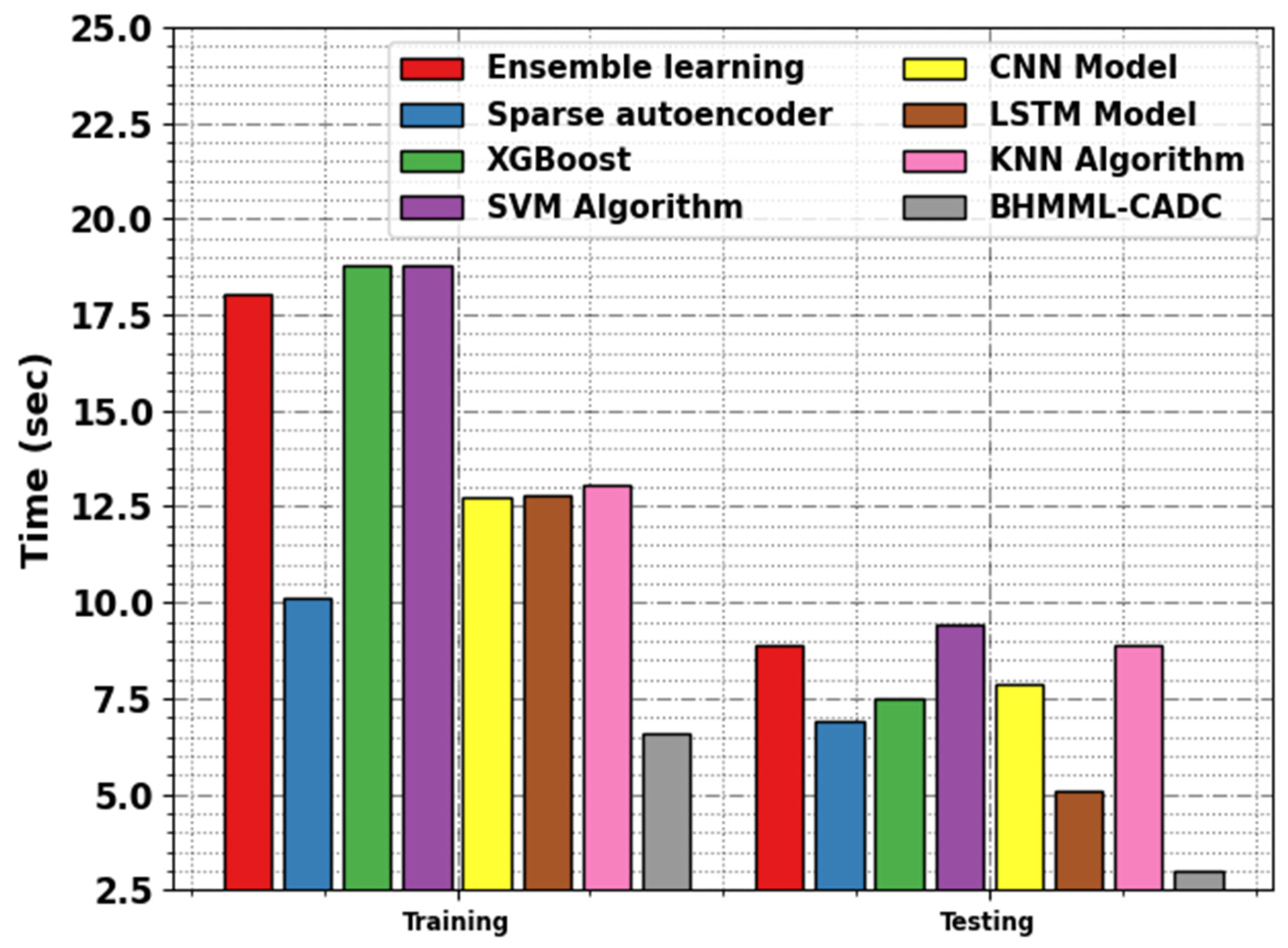
Table 5 and
Figure 15 demonstrate the comparative TRT and TST investigations of the BHMML-CADC method with other current algorithms. The outcomes highlight that the BHMML-CADC system achieves superior performance over the other models.
Based on the TRT outcomes, the BHMML-CADC technique demonstrates a reduced TRT of 6.60 s, while the Ensemble learning, Sparse autoencoder, XGBoost, SVM, CNN, LSTM, and KNN approaches obtained higher TRTs of 18.06 s, 10.14 s, 18.78 s, 18.78 s, 12.73 s, 12.82 s, and 13.05 s, respectively. Afterwards, based on the TST, the BHMML-CADC approach achieved a minimized TST of 3.01 s, whereas the XGBoost, Ensemble learning, Sparse autoencoder, LSTM, KNN, SVM, and CNN techniques achieved greater TST values of 8.86 s, 6.88 s, 7.52 s, 9.44 s, 7.87 s, 5.10 s, and 8.88 s, respectively.
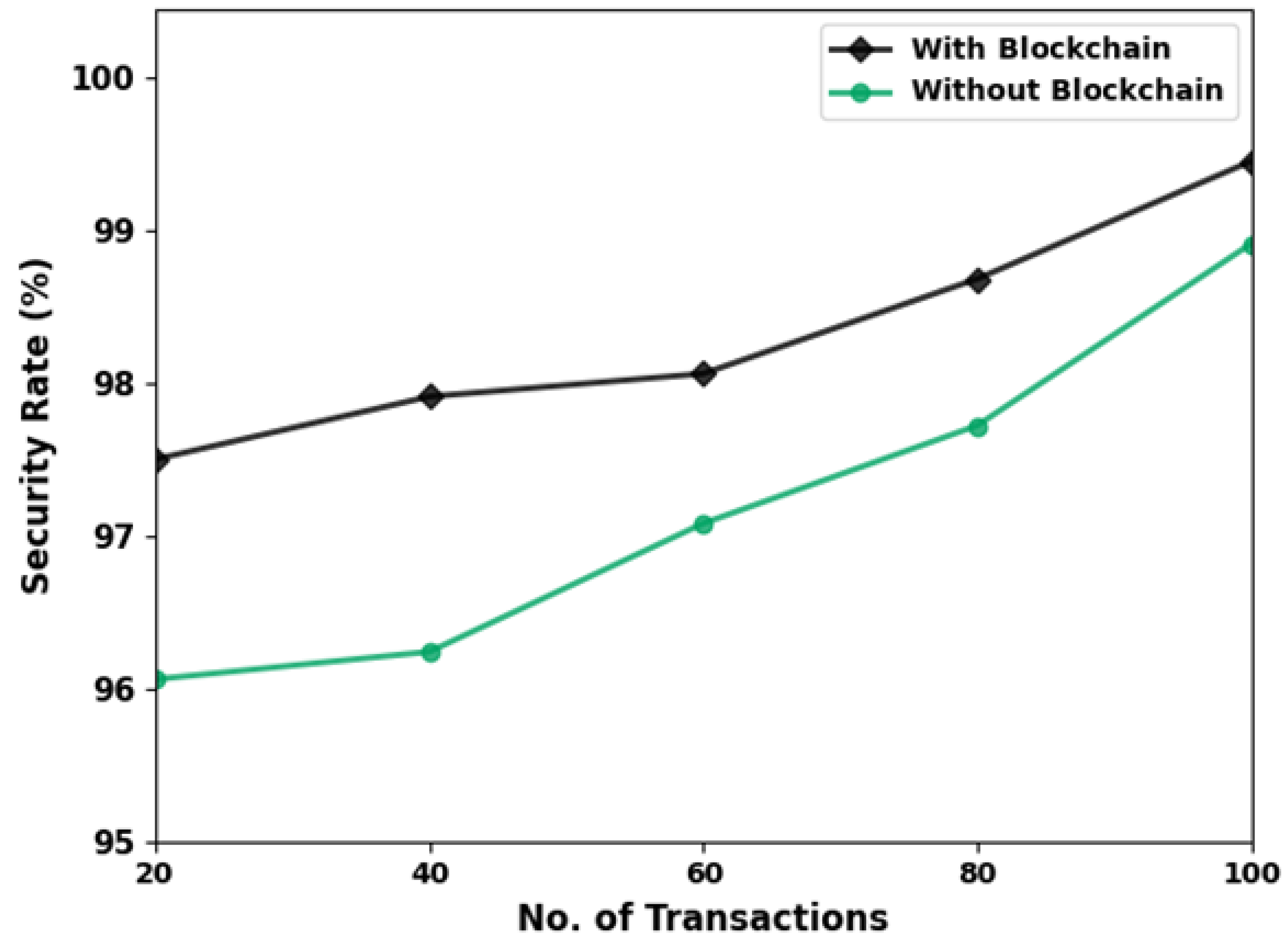
Figure 16 illustrates the security rate of the proposed model with and without BC technology. The security rate of the proposed model with BC was found to be higher than that of the proposed model without BC. The use of BC technology helps to achieve an enhanced security rate of the proposed model. It was also observed that the security rate increases with an increase in the number of transactions (
Table 6).
In summary, the proposed model shows improved performance over the other techniques, which is due to the integration of the HEGSO-based FS and HPO-based hyperparameter tuning. The HEGSO technique chooses the related and useful features from the available set of features. With the removal of irrelevant features, the BHMML-CADC technique can focus on crucial factors that contribute to the classification process. This leads to an increase in classification performance. Simultaneously, the HPO optimizer chooses the optimal value for the hyperparameter of the given QRNN model. Hyperparameters are settings that are not learned during training, but must be set before training. They may have a considerable effect on system performance, and selecting the optimum values can result in better accuracy. By combining HPO optimizer-based hyperparameter tuning and the HEGSO algorithm, the BHMML-CADC model achieved the best outcomes by focusing on the most relevant features and selecting the optimum settings for the model. These outcomes ensured superior performance of the BHMML-CADC method over the other current approaches.