Penetration Taxonomy: A Systematic Review on the Penetration Process, Framework, Standards, Tools, and Scoring Methods
Abstract
1. Introduction
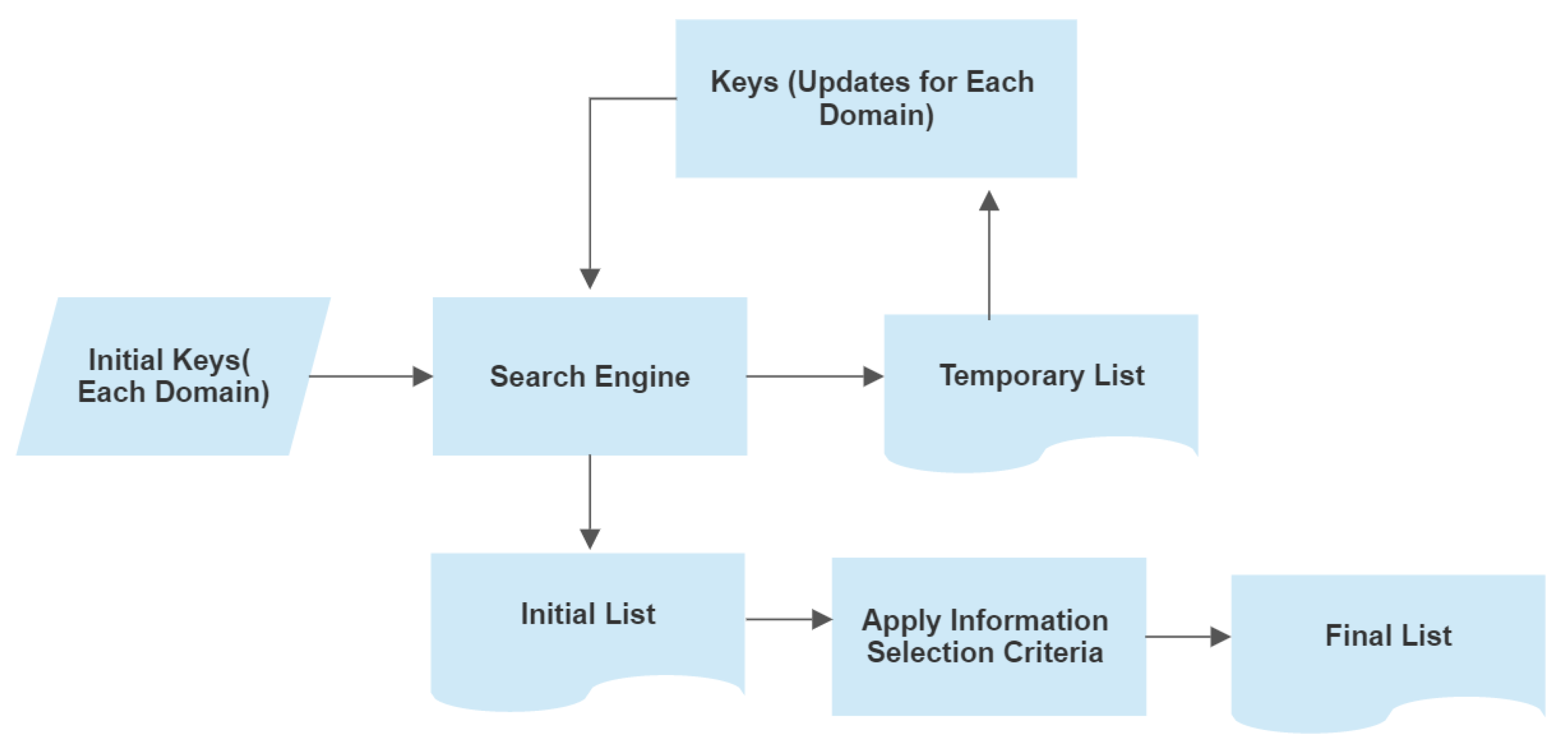
2. Methodology
3. Penetration
3.1. Penetration Overview
3.2. Penetration Phases
- Footprinting and reconnaissance: This is the first phase of the penetration process, which collects information about the target organization, its technical and physical infrastructure, and users’ contacts. Information is collected from users (maybe by tricking too), published documents, online scanning tools, third parties, stakeholders, etc. Attackers want to know as much as possible about the IT infrastructure and services to explore the attacking scope, methodology, and tools. Collected information also supports making an effective attacking strategy and plan. The main aim of this phase is to define the goal and scope of the test and collect relevant information for making an attacking strategy.
- Scanning: In this phase, the attacker will interact with the target to identify prospective vulnerabilities. Attackers make different attempts to scan the information, and their responses are recorded for further analysis. The existing exploitation strategy will be updated according to the results of the analysis. Different scanning applications, tools, and techniques are applied in this phase to scan networks, devices, and services. It identifies an open shared drive, open FTP ports, services that are running, etc. Scanning methods are divided into static scanning and dynamic scanning. Static scanning is aimed at identifying the vulnerable functions, libraries, and logic. On the other hand, in the case of dynamic scanning, a tester passes various inputs to the application and records their responses. Dynamic scanning is more practical and faster than static scanning.
- Enumeration: Attacks are performed in this phase based on the strategy and plan that was developed in the first phase, as well as scanning information from the previous phase. Special knowledge, skills, and experience are required for accessing loopholes to obtain access control. Skills and patience are important for applying a series of attempts to achieve an attacking target by using multiple tools and techniques. An attacker tries his best actions in this phase to extract targeted data, compromise the network’s security, and disturb services. The pen tester executes all possible attacks on the system and records all bugs in the applications, networks, memory, social engineering practices, user practices, physical security posture, Wi-Fi, zero-day-attacks, etc. [72].
- Analysis: Risk analysis is performed according to the exploitation evidence of the vulnerabilities in this phase. A tester should follow standard methods for risk measurement and impact mapping [73], with categories such as critical, high, medium, and low, which provide a priority for initiating the fixing of the required vulnerabilities [74]. The analysis report is comparatively short and simple, but it is easy for management to know the system’s weaknesses [75]. It also includes clean-up activities such as removing executable scripts and temporary files, reconfiguring the original setting that was used before exploitation, eliminating all installed rootkits, and removing the user accounts that are created by testers.
- Reporting: Usually, it is a formal document of the summary of the entire penetration testing that is submitted by the pen tester team to the organization with a recommendation guideline [74] to enhance the security of the organization. The report should consist of high-level documentation and be easy to understand, supporting further review. The findings (good or bad practices, strengths and weaknesses, etc.) [75] are explained properly so that internal security teams improve the significant security posture. Reporting is an art that reflects the activities, and a good report adds value to the work.
3.3. Importance of Penetration Testing
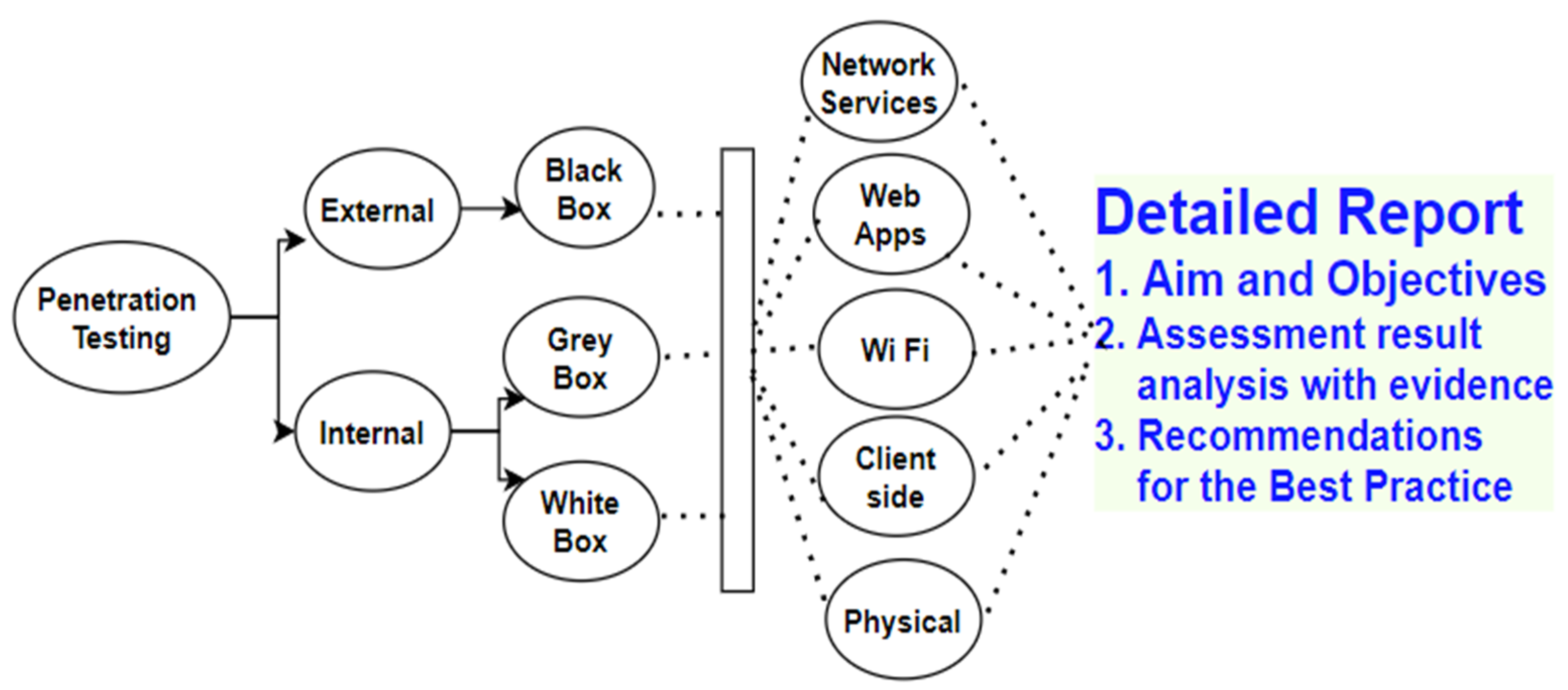
4. Penetration Taxonomy
4.1. Penetration Domains
4.2. Penetration for Common Vulnerabilities
5. Penetration Frameworks
6. Penetration Standards
7. Penetration Tools
- KaliLinux 2023.1: In most cases, it is considered as a default penetration. OS [59] is a reliable pen-testing tool on the platforms of desktops, mobile devices, virtual machines, Docker, and Windows or Linux-based subsystems [60]. It supports vulnerability scanning and digital forensics operations and can be used as a sniffing tool for LAN and WAN [61]. In addition, it is used for 16-bit brute force password cracking [61].
- Intruder: It is a common tool used in the banking and government sector to scan vulnerabilities of the system [58]. It performs auto analysis and develops a vulnerability list based on the risk priority [62]. It is supported by ISO 27001/27002 standards and SOC 2 compliance standards [62]. Moreover, it can work with cloud systems: AWS, Google Cloud, and Azure [62].
- NMAP: This is one of the most popular network scanning tools used for port scanning, network mapping, and creating inventory for network services [58]. Network administrators also use this as a regular testing tool for monitoring, inventory management, service management, and upgrading schedules [60]. In addition, legitimate organizations scan the entire IPv4 range and ports regularly for the IP map and ports’ status respectively [59].
- SQLmap: It is applied in automated penetration to detect SQL injection flaws [58] with Boolean, stack, union, and error injection methods [61]. It supports H2, Informix, MaxDB, SAP, Microsoft SQL Server, MySQL, Oracle, PostgreSQL, Microsoft Access, SQLite, IBM DB2, Firebird, and Sybase for security checking [59].
- Nikto 2.1.6: This is an open-source pluggable web server scanner that consists of 7000 scanning programs [58]. There are plenty of tests for both vulnerability and misconfiguration tests.
- Brup Suit 2023.4.4: It is an open-source tool that is incredibly effective for web traffic exploration and can fire when required [59]. It consists of a set of tools such as a web crawler, repeater, sequencer, and proxy to perform security tests on web applications [58]. It is also good for beginners to understand traffic exploitation in a computer network [59].
- Acunetix 15: It is an automatic pen testing tool that is capable of identifying out-of-band vulnerabilities [61] and is applicable for on-premises or cloud platforms [61]. It supports important standards such as PCI DSS, HIPPA, and ISO 27001 and is seamlessly integrated with the platforms: GitHub, Bugzilla, JIRA, Azure DevOps, and Mantis [62].
8. Penetration Scoring
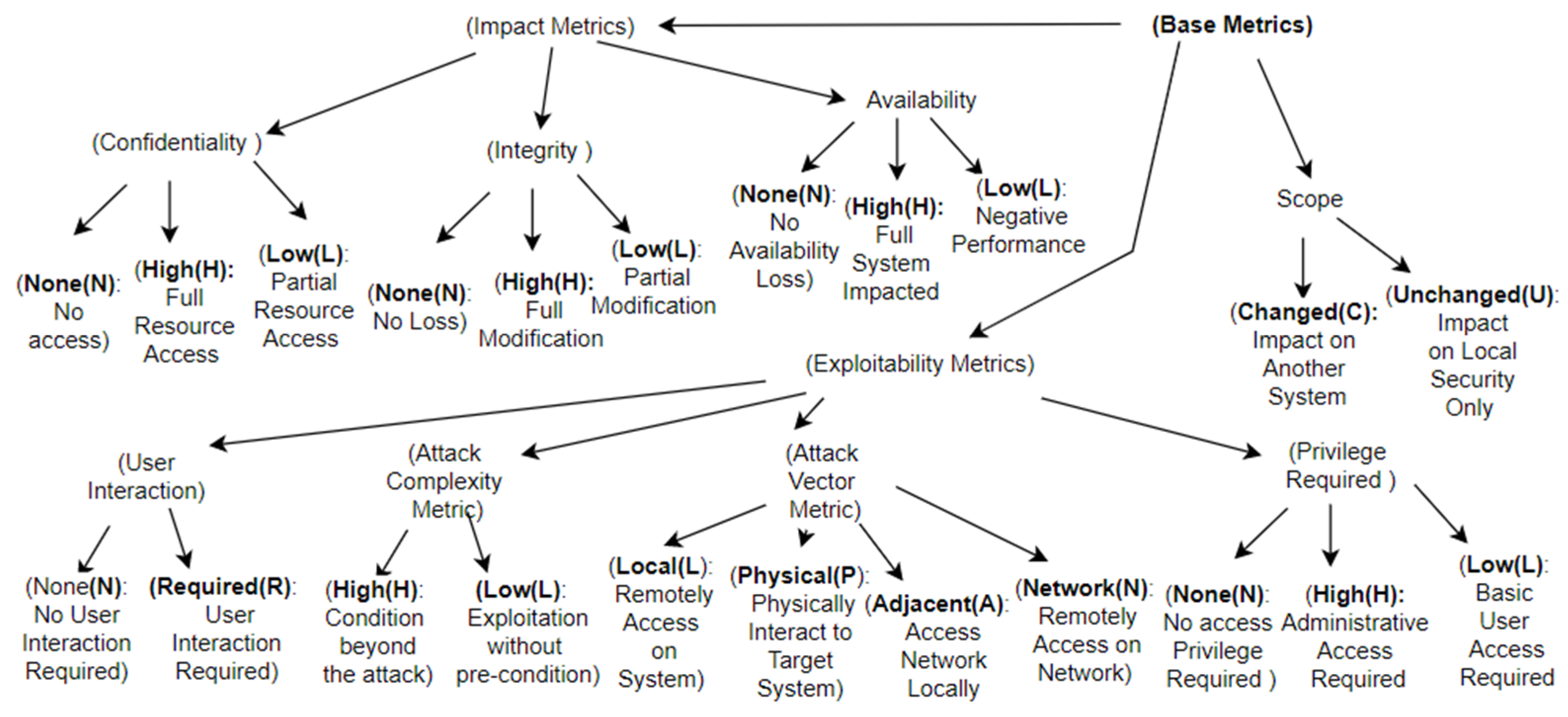
8.1. Base Matrix Taxonomy
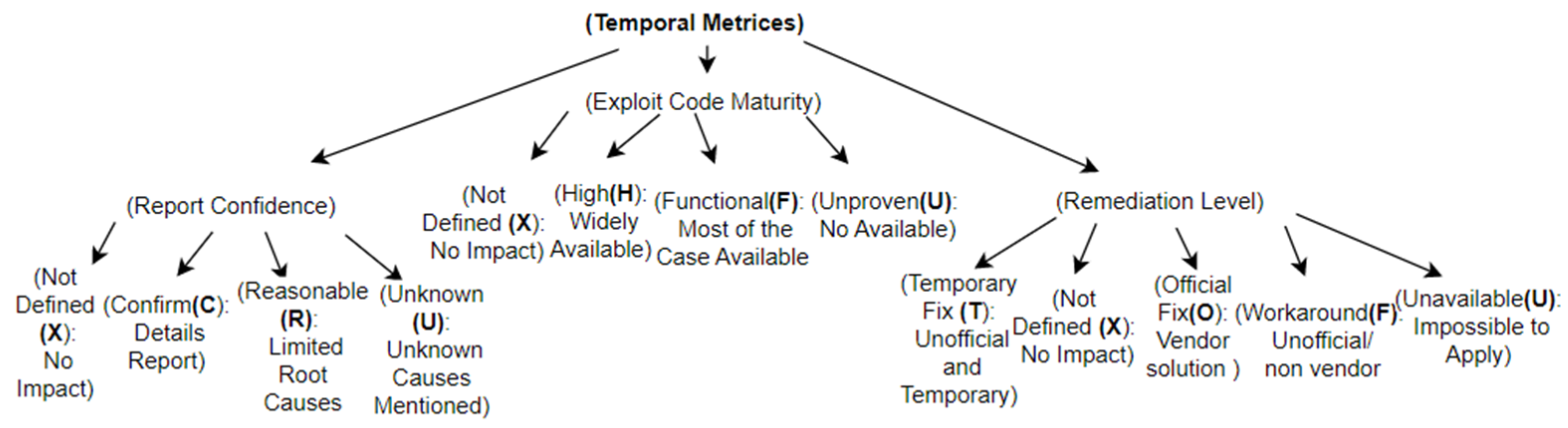
8.2. Temporal Matrix Taxonomy
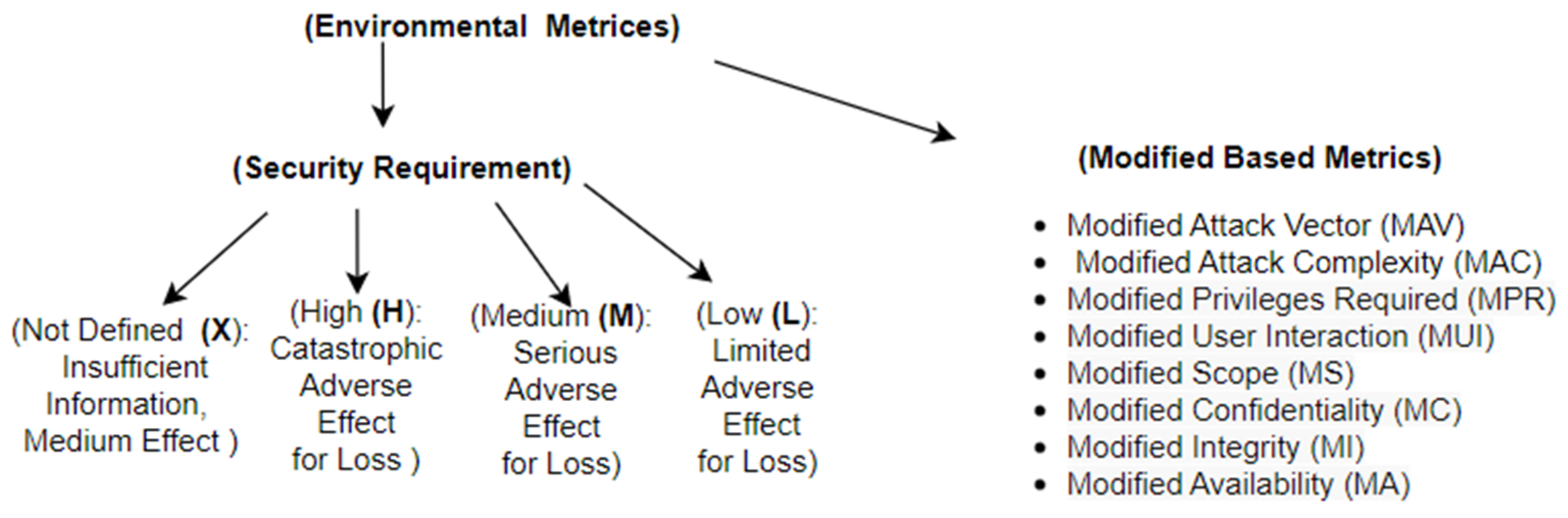
8.3. Environmental Matrix Taxonomy
9. Conclusions
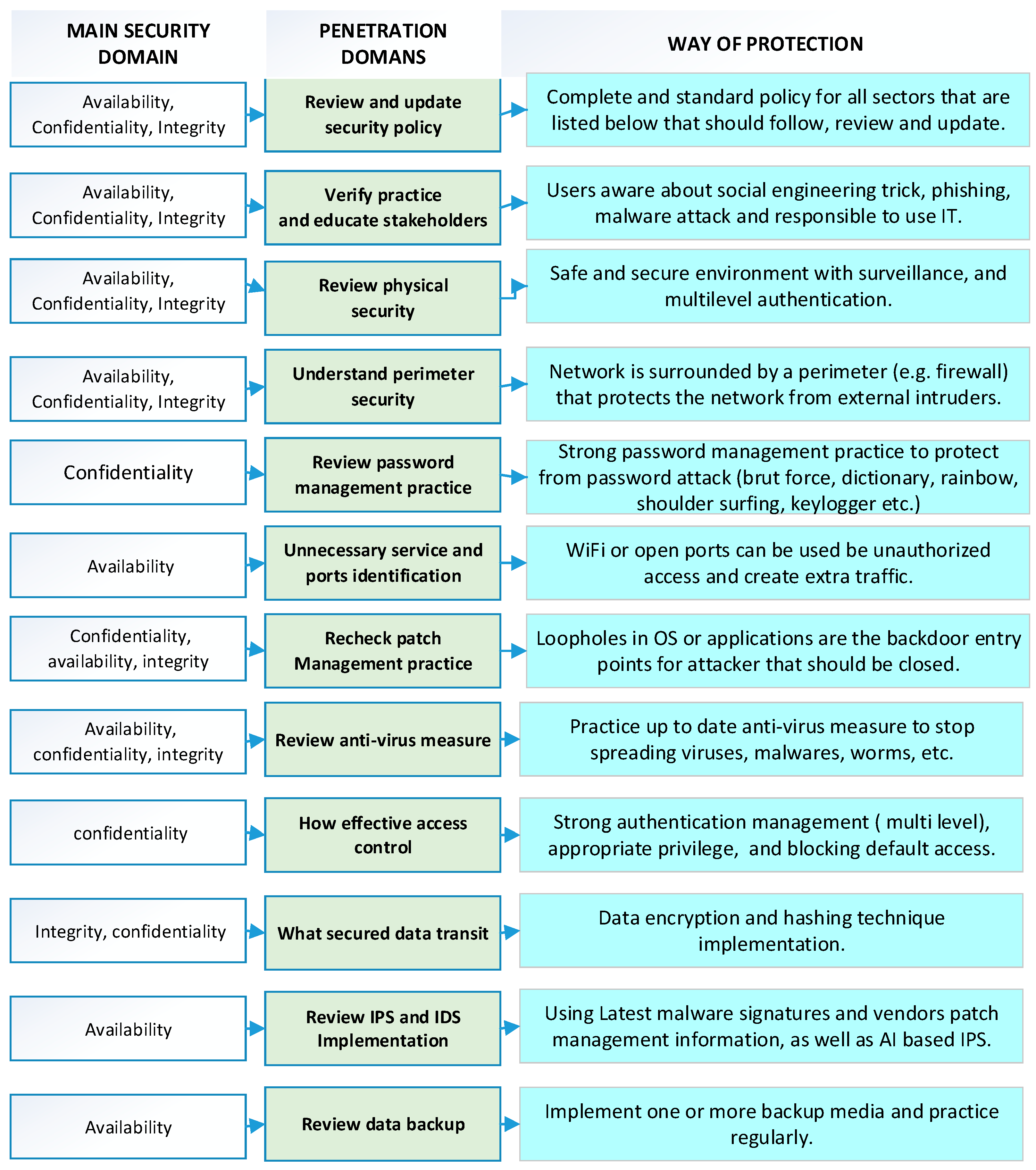
9.1. Recent Trend
9.2. Observation
- Integrated penetration policy procedures should be guided by standards and frameworks.
- Organizations should show importance of all vulnerabilities and consider that security is an integrated task (any weakness could be a cause of a massive disaster).
- Organizations should implement the penetration test regularly or on demand (new/updated deployment), which could be both manual and automatic to improve the validation of the test result. The penetration process should be reviewed and updated regularly to protect the system from newly arrived threats.
- Penetration practice minimizes unexpected damages and disruptions; as a result, an organization can ensure quality of service and improve sustainable practices.
9.3. Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Senol, M.; Karacuha, E. Creating and Implementing an Effective and Deterrent National Cyber Security Strategy. J. Eng. 2020, 2020, 5267564. [Google Scholar] [CrossRef]
- Alzoubi, Y.I.; Osmanaj, V.H.; Jaradat, A.; Al-Ahmad, A. Fog computing security and privacy for the Internet of Thing applications: State-of-the-art. Secur. Priv. 2021, 4, e145. [Google Scholar] [CrossRef]
- Villa, E.; Ruiz, L.; Valencia, A.; Picón, E. Electronic commerce: Factors involved in its adoption from a bibliometric analysis. J. Theor. Appl. Electron. Commer. Res. 2018, 13, 39–70. [Google Scholar] [CrossRef]
- Chukwu, M.A.; Idoko, E.C. Inhibitors of Electronic Banking Platforms’ Usage Intention in Deposit Money Banks: Perspectives of Elderly Customers in Developing Economy. Schizophr. Bull. 2021, 7, 134–145. [Google Scholar] [CrossRef]
- Buja, A.G. Cyber Security Featuresfor National E-Learning Policy. Turk. J. Comput. Math. Educ. 2021, 12, 1729–1735. [Google Scholar] [CrossRef]
- Barr, J.R.; D’Auria, D.; Persia, F. Telemedicine, Homecare in the Era of COVID-19 & Beyond. In Proceedings of the Third International Conference on Artificial Intelligence for Industries (AI4I), Irvine, CA, USA, 21–23 September 2020; pp. 48–51. [Google Scholar]
- Herrera, A.V.; Ron, M.; Rabadão, C. National cyber-security policies oriented to BYOD (bring your own device): Systematic review. In Proceedings of the 2017 12th Iberian Conference on Information Systems and Technologies (CISTI), Lisbon, Portugal, 21–24 June 2017; pp. 644–648. [Google Scholar]
- Robichau, B.P. Healthcare Information Privacy and Security: Regulatory Compliance and Data Security in the Age of Electronic Health Records, 1st ed.; 233 Spring St Fl 7; Apress: New York, NY, USA, 2014; ISBN 10-1430266767. [Google Scholar]
- Yang, P.; Xiong, N.; Ren, J. Data security and privacy protection for cloud storage: A survey. IEEE Access 2020, 8, 131723–131740. [Google Scholar] [CrossRef]
- Al Jaafreh, A.; Al-Adaileh, R.; Gill, A.; Al-Ani, A.; Alzoubi, Y. A review of literature of initial trust in e-services: The case of internet banking services in Jordanian context. J. Electron. Bank. Syst. 2014, 2014, 690673. [Google Scholar] [CrossRef]
- Alzoubi, Y.I.; Al-Ahmad, A.; Jaradat, A. Fog computing security and privacy issues, open challenges, and blockchain solution: An overview. Int. J. Electr. Comput. Eng. 2021, 11, 5081–5088. [Google Scholar] [CrossRef]
- UVM. Enterprise Risk Management Program: Guide to Risk Assessment & Response. Available online: https://www.uvm.edu/sites/default/files/Enterprise-Risk-Management/POSTED_Prog_Primer_Trustee_Orientation.pdf (accessed on 10 September 2022).
- InfoSec Institute. Ashley Madison Revisited: Legal, Business and Security Repercussions. Available online: http://resources.infosecinstitute.com/ashley-madison-revisited-legal-business-and-security-repercussions (accessed on 10 September 2022).
- PwC. Limiting the Impact of Data Breaches the Case of the Sony Play Station Network. Available online: http://www.strategyand.pwc.com/reports/limiting-impact-data-breaches-case (accessed on 10 September 2022).
- Dark Reading. Sony Data Breach Cleanup to Cost $171 Million. Available online: http://www.darkreading.com/attacks-and-breaches/sony-data-breach-cleanupto-cost-\$171-million/d/d-id/1097898 (accessed on 10 September 2022).
- Lee, T. Forget the Ashley Madison or Sony Hacks—A Crippling Cyberattack Is Imminent in the US. The Guardian. Available online: http://www.theguardian.com/technology/2015/jul/26/cybercrime-hacking-internet-of-things-target (accessed on 10 September 2022).
- The Huffington Post. A Look Back at the Target Breach. Available online: http://www.huffingtonpost.com/eric-dezenhall/a-look-back-at-the-target_b_7000816.html (accessed on 10 September 2022).
- Talktalk Hackers Go on £600 Spending Spree with Stolen Card Details as Boss Says Its too Early to Consider Compensation. The Mirror. Available online: http://www.mirror.co.uk/news/uk-news/talktalk-hackers-go-600-spending6694321 (accessed on 10 September 2022).
- Ashley, M. Aftermath: Confessions, Suicide Reports and Hot on the Hacker’s Trail. National Post. Available online: http://news.nationalpost.com/news/canada/ashley-madison-aftermath-confessions-suicide-reports-and-hot-on-the-hackers-trail (accessed on 10 September 2022).
- McDaid, L. Talktalk Cyber-Attack: County Londonderry Man Targeted. BBC News. Available online: http://www.bbc.co.uk/news/uk-34613921 (accessed on 10 September 2022).
- Pranggono, B.; Arabo, A. COVID-19 pandemic cybersecurity issues. Internet Technol. Lett. 2020, 4, e247. [Google Scholar] [CrossRef]
- Rijnetu, I. 100+ Essential Penetration Testing Statistics [2023 Edition], Pentest. Publisher Pentest-Tools.com. February 2023. Available online: https://pentest-tools.com/blog/penetration-testing-statistics (accessed on 16 April 2023).
- Shank, S. Penetration Testing in 2022: Key Trends and Challenges. The State of Security. Available online: https://www.tripwire.com/state-of-security/security-data-protection/penetration-testing-in-2022-key-trends-and-challenges/ (accessed on 20 September 2022).
- Recent Cyber Attacks & Data Breaches in 2022. Available online: https://purplesec.us/security-insights/data-breaches/ (accessed on 19 September 2022).
- Perwej, Y.; Abbas, Q.; Dixit, J.P.; Akhtar, N.; Jaiswal, A.K. A Systematic Literature Review on the Cyber Security. Int. J. Sci. Res. Manag. 2021, 9, 669–710. [Google Scholar] [CrossRef]
- Goel, J.N.; Mehtre, B.M. Vulnerability assessment & penetration testing as a cyber-defense technology. Procedia Comput. Sci. 2015, 57, 710–715. [Google Scholar] [CrossRef]
- Ghanem, C.; Chen, T.M. Reinforcement learning for efficient network penetration testing. Inf. Int. Interdiscip. J. 2020, 11, 6. [Google Scholar] [CrossRef]
- Vaca, A.J.V.; Gasca, R.M.; Fombella, J.A.C.; Lopez, M.T.G. AMADEUS: Towards the Automated security testing. In Proceedings of the 24th ACM Conference on Systems and Software Product Line: Volume A, New York, NY, USA, 19–23 October 2020; pp. 1–12. [Google Scholar]
- Yaacoub, J.P.; Hassan, N.; Noura, O.S.; Chehab, A. Robotics cyber security: Vulnerabilities, attacks, countermeasures, and recommendations. Int. J. Inf. Secur. 2021, 15, 115–158. [Google Scholar] [CrossRef] [PubMed]
- Nguyen, G.; Dlugolinsky, S.; Tran, V.; Garcia, A.L. Deep learning for proactive network monitoring and security protection. IEEE Access 2020, 8, 19696–19716. [Google Scholar] [CrossRef]
- Trifonov, R.; Manolov, G.; Yoshinov, R.; Pavlova, G. A Survey of Artificial Intelligence for Enhancing the Information Security. Int. J. Dev. Res. 2017, 7, 16866–16872. Available online: https://www.journalijdr.com/sites/default/files/issue-pdf/10933.pdf (accessed on 12 October 2022).
- Collier, Z.; DiMase, D.; Walters, S.; Tehranipoor, M.; Lambert, J. Cybersecurity Standards: Managing Risk and Creating Resilience. Computer 2014, 47, 70–76. [Google Scholar] [CrossRef]
- Knapp, K.J.; Maurer, C.; Plachkinova, M. Maintaining a cybersecurity curriculum: Professional certifications as valuable guidance. J. Inf. Syst. Educ. 2017, 28, 101–114. [Google Scholar]
- CVE Details, The Ultimate Security Vulnerability Datasource. Available online: https://www.cvedetails.com/vulnerability-list/year-2023/vulnerabilities.html (accessed on 4 June 2023).
- Sarker, K.U.; Deraman, A.; Hasan, R.; Abbas, A. A 4-Layered Plan-driven Model (4LPdM) to Improve Software Development. Int. J. Adv. Comput. Sci. Appl. (IJACSA) 2022, 13, 589–600. [Google Scholar] [CrossRef]
- Sarker, K.U.; Deraman, A.; Hasan, R.; Abbas, A. SQ-Framework for Improving Sustainability and Quality into Software Product and Process. Int. J. Adv. Comput. Sci. Appl. (IJACSA) 2020, 11, 69–78. [Google Scholar] [CrossRef]
- Herzog, P. The Open Source Security Testing Methodology Manual (OSSTMM) 3. Contemporary Security Testing and Analysis; ISECOM: Cardedeu, Spain, 2010. [Google Scholar]
- Saad, E.; Mitchel, R. OWASP Web Security Testing Guide, Version 4.2. OSASP. Available online: https://owasp.org/www-project-web-security-testing-guide/ (accessed on 17 March 2023).
- Willemsen, J.; Holguera, C.; Mueller, B.; Schleier, S. MASTG. Mobile Application Security Testing Guide. Version v1.5.0. Available online: https://mas.owasp.org/#our-mission (accessed on 17 March 2023).
- OWASP Firmware Security Testing Methodology. Available online: https://github.com/scriptingxss/owasp-fstm (accessed on 22 September 2022).
- Framework for Improving Critical Infrastructure Cybersecurity. Version 1.1. National Institute of Standards and Technology. Available online: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf (accessed on 17 March 2023).
- PTEST. High Level Organization of the Standard. Available online: http://www.pentest-standard.org/index.php/Main_Page (accessed on 23 March 2023).
- PTES Technical Guidelines. Available online: http://www.pentest-standard.org/index.php/PTES_Technical_Guidelines (accessed on 23 September 2022).
- FAQ. Penetration Testing Execution Standard. Available online: http://www.pentest-standard.org/index.php/FAQ (accessed on 23 March 2023).
- Information System Security Assessment Framework (ISSAF). Future Learn. Available online: https://www.futurelearn.com/info/courses/ethical-hacking-an-introduction/0/steps/71521 (accessed on 23 March 2023).
- Cordero, J.A.V. ISO/IEC standards as mechanisms of proactive responsibility in the General Data Protection Regulation. Internet Derecho Política Rev. D’internet Dret Política 2021, 33, 7. [Google Scholar]
- Arora, V. Comparing Different Information Security Standards: COBIT vs. ISO 27001; Carnegie Mellon University: Doha, Qatar, 2010; Available online: https://varunarora.com/assets/iso27001-vs-cobit/paper.pdf (accessed on 3 April 2023).
- Boboň, S. Analysis of NIST FIPS 140-2 Security Certificates; Masaryk University: Brno, Czech Republic, 2021; Available online: https://is.muni.cz/th/wftuc/?lang=en (accessed on 12 April 2023).
- Azmi, R.; Tibben, W.; Win, K. Review of cybersecurity frameworks: Context and shared concepts. J. Cyber Policy 2018, 3, 258–283. [Google Scholar] [CrossRef]
- Huamani, R.; Eduardo, R. Implementación de un Plan de Seguridad Informática Basado en la Norma ISO IEC/27002, Para Optimizar la Gestión en la Corte Superior de Justicia de Lima; Universidad Privada del Norte: Trujillo, Peru, 2022; Available online: https://hdl.handle.net/11537/29848 (accessed on 13 April 2023).
- Putri, M.K.; Hakim, A.R. Perancangan Manajemen Risiko Keamanan Informasi Layanan Jaringan MKP Berdasarkan Kerangka Kerja ISO/IEC 27005: 2018 dan NIST SP 800-30 Revisi 1. J. Info Kripto 2021, 15, 134–141. [Google Scholar] [CrossRef]
- Taherdoost, H. Understanding Cybersecurity Frameworks and Information Security Standards—A Review and Comprehensive Overview. Electronics 2022, 11, 2181. [Google Scholar] [CrossRef]
- Choo, K.-K.R.; Gai, K.; Chiaraviglio, L.; Yang, Q. A multidisciplinary approach to Internet of Things (IoT) cybersecurity and risk management. Comput. Secur. 2021, 102, 102136. [Google Scholar] [CrossRef]
- Macher, G.; Schmittner, C.; Veledar, O.; Brenner, E. ISO/SAE DIS 21434 Automotive Cybersecurity Standard—In a Nutshell. In Computer Safety, Reliability, and Security; Springer: Cham, Switzerland, 2020; Volume 12235, pp. 123–135. [Google Scholar] [CrossRef]
- Leander, B.; Čaušević, A.; Hansson, H. Applicability of the IEC 62443 Standard in Industry 4.0/IIoT. In Proceedings of the 14th International Conference on Availability, Reliability and Security, Canterbury, UK, 26 August 2019; Association for Computing Machinery: New York, NY, USA; Canterbury, UK, 2019; pp. 1–8. [Google Scholar]
- Tofan, D. Information Security Standards. J. Mob. Embed. Distrib. Syst. 2011, 3, 128–135. [Google Scholar]
- Schmitz, C.; Schmid, M.; Harborth, D.; Pape, S. Maturity level assessments of information security controls: An empirical analysis of practitioners’ assessment capabilities. Comput. Secur. 2021, 108, 102306. [Google Scholar] [CrossRef]
- Basu, S. 17 Best Penetration Testing Tools/Software of 2022 [Reviewed], Astra Security Blog. 2022. Available online: https://www.getastra.com/blog/security-audit/best-penetration-testing-tools/?utm_term=&utm_campaign (accessed on 15 April 2023).
- Fruhlinger, J.; Porup, J.M. 11 Penetration Testing Tools the Pros Use, CSO Online. CSO. Available online: https://www.csoonline.com/article/2943524/11-penetration-testing-tools-the-pros-use.html (accessed on 15 April 2023).
- Siyal, G. The Top 10 Penetration Testing Tools for Security Professionals, MUO. Available online: https://www.makeuseof.com/penetration-testing-for-security-professionals/ (accessed on 15 April 2023).
- Jevtic, G. 13 Powerful Penetration Testing Tools the Pros Use, phoenixNAP Blog. Available online: https://phoenixnap.com/blog/best-penetration-testing-tools (accessed on 15 April 2023).
- Williams, L. 27 Best Penetration Testing (Pentest) Tools in 2022, Guru99. Available online: https://www.guru99.com/top-5-penetration-testing-tools.html (accessed on 15 April 2023).
- Editorial, G. Astra Pentest Reviewed—Easy, Continuous Vulnerability Scanning & Compliance, Geekflare. Available online: https://geekflare.com/astra-pentest-review/ (accessed on 15 April 2023).
- Risk Scoring System. Characterizing Identified Vulnerabilities and Numerically Scoring the Potential Severity Using a Mission Impact Focus. Available online: https://www.riskscoringsystem.com/ (accessed on 13 April 2023).
- INCIBE. Industrial CVSS: Alternative Calculations for Different Needs. 2019. Available online: https://www.incibe-cert.es/en/blog/industrial-cvss-alternative-calculations-different-needs (accessed on 13 April 2023).
- Bodungen, C. Industrial Vulnerability Scoring System (IVSS). 2019. Available online: https://securingics.com/IVSS/IVSS.html (accessed on 15 April 2023).
- Figueroa-Lorenzo, S.; Añorga, J.; Arrizabalaga, S. A Survey of IIoT Protocols. ACM Comput. Surv. 2020, 53, 1–53. [Google Scholar] [CrossRef]
- Strategies to Mitigate Cyber Security Incidents—Mitigation Details. Australian Signals Directorate, Australian Cyber Security Centre. February 2017. Available online: www.cyber.gov.au/sites/default/files/2019-03/Mitigation_Strategies_2017_Details_0.pdf (accessed on 15 April 2023).
- CVSS Version 3.1 Release. Common Vulnerability Scoring System Version 3.1: Specification Document. Available online: https://www.first.org/cvss/specification-document (accessed on 15 April 2023).
- Al-Ahmad, A.S.; Kahtan, H.; Hujainah, F.; Jalab, H.A. Systematic literature review on penetration testing for mobile cloud computing applications. IEEE Access 2019, 7, 173524–173540. [Google Scholar] [CrossRef]
- Alghamdi, A.A. Effective Penetration Testing Report Writing. In Proceedings of the 2021 International Conference on Electrical, Computer, Communications and Mechatronics Engineering (ICECCME), Mauritius, 7–8 October 2021; pp. 1–5. [Google Scholar]
- Singh, A. Metasploit Penetration Testing Cookbook, 2nd ed.; Packt Publishing: Birmingham, UK, 2012; ISBN 978-1849517423. [Google Scholar]
- Moradov, O. Penetration Testing Report: 6 Key Sections and 4 Best Practices. 2021. Available online: https://brightsec.com/blog/penetration-testing-report/ (accessed on 18 September 2022).
- Caudill, B. Four Things Every Penetration Test Report Should Have. Available online: https://rhinosecuritylabs.com/penetration-testing/four-things-every-penetration-test-report/ (accessed on 18 September 2022).
- Firewall Penetration Testing: Steps, Methods & Tools. Available online: https://purplesec.us/firewall-penetration-testing/ (accessed on 19 September 2022).
- 2022 Penetration Testing Report. Coresecurity by HelpSystem. Available online: https://static.helpsystems.com/core-security/pdfs/guides/cs-2022-pen-testing-report.pdf (accessed on 15 September 2022).
- Paul, G.; Irvine, J. Privacy implications of wearable health devices. In Proceedings of the 7th International Conference on Security of Information and Networks, Glasgow, UK, 9–11 September 2014; pp. 117–121. [Google Scholar]
- Herzig, T.; Walsh, T. Implementing Information Security in Healthcare: Building a Security Program, 1st ed.; CRC Press: Boca Raton, FL, USA, 2020; ISBN 978-1938904349. [Google Scholar]
- Li, R.; Zhao, Z.; Sun, Q.; Chih-Lin, I.; Yang, C.; Chen, X.; Zhao, M.; Zhang, H. Deep reinforcement learning for resource management in network slicing. IEEE Access 2018, 6, 74429–74441. [Google Scholar] [CrossRef]
- Houser, A.M. Mental Models for Cybersecurity: A Formal Methods Approach. University at Buffalo, State University of New York. 2018. Available online: http://fhsl.eng.buffalo.edu/publications/Houser_dissertation.pdf (accessed on 13 April 2023).
- Kostyuk, N.; Wayne, C. Communicating Cybersecurity: Citizen Risk Perception of Cyber Threats. Available online: http://www-personal.umich.edu/~nadiya/communicatingcybersecurity.pdf (accessed on 13 April 2023).
- Jump, M. Fighting Cyberthreats with Technology Solutions. Biomed. Instrum. Technol. 2019, 53, 38–43. [Google Scholar] [CrossRef]
- Jain, A.K.; Goel, D.; Agarwal, S.; Singh, Y.; Bajaj, G. Predicting Spam Messages Using Back Propagation Neural Network. Wirel. Pers. Commun. 2020, 110, 403–422. [Google Scholar] [CrossRef]
- Farahmand, F.; Navathe, S.B.; Enslow, P.H.; Sharp, G.P. Managing vulnerabilities of information systems to security incidents. In Proceedings of the 5th International Conference on Electronic Commerce, Pittsburgh, PA, USA, 30 September–3 October 2003; Association for Computing Machinery: New York, NY, USA; pp. 348–354. [Google Scholar]
- Perwej, Y.; Omer, M.K.; Sheta, O.E.; Harb, H.A.M.; Adrees, M.S. The Future of Internet of Things (IoT) and Its Empowering Technology. Int. J. Eng. Sci. Comput. (IJESC) 2019, 9, 20192–20202. [Google Scholar]
- Xiao, B.; Chen, W.; He, Y.; Hsing, E.; Sha, M. An Active Detecting Method against SYN Flooding attack. In Proceedings of the 11th International Conference on Parallel and Distributed Systems (ICPADS2005), Fukuoka, Japan, 20–22 July 2005; pp. 709–715. [Google Scholar]
- Keshri, A. Top 5 Penetration Testing Methodologies and Standards. 2022. Available online: https://www.getastra.com/blog/security-audit/penetration-testing-methodology/#owasp (accessed on 23 March 2023).
- Bertoglio, D.D.; Zorzo, A.F. Overview and open issues on penetration test. J. Braz. Comput. Soc. 2017, 23, 2. [Google Scholar] [CrossRef]
- Insight Report. Global Cybersecurity Outlook. WorForum. January 2022. Available online: https://www3.weforum.org/docs/WEF_Global_Cybersecurity_Outlook_2022.pdf (accessed on 25 March 2023).
- Purser, S. Standards for Cyber Security. In Best Practices in Computer Network Defense: Incident Detection and Response; Hathaway, M.E., Ed.; IOS Press: Washington, DC, USA, 2014; pp. 97–106. ISBN 978-1614993711. [Google Scholar]
- Karie, N.M.; Sahri, N.M.; Yang, W.; Valli, C.; Kebande, V.R. A Review of Security Standards and Frameworks for IoT-Based Smart Environments. IEEE Access 2021, 9, 121975–121995. [Google Scholar] [CrossRef]
- Taherdoost, H. Understanding of E-service Security Dimensions and its effect on Quality and Intention to Use. Inf. Comput. Secur. 2017, 25, 535–559. [Google Scholar] [CrossRef]
- Maleh, Y.; Sahid, A.; Alazab, M.; Belaissaoui, M. IT Governance and Information Security: Guides, Standards, and Frameworks, 1st ed.; CRC Press: Boca Raton, FL, USA, 2021; ISBN 9780367753245. [Google Scholar]
- Fonseca-Herrera, O.A.; Rojas, A.E.; Florez, H. A model of an information security management system based on NTC-ISO/IEC 27001 standard. IAENG Int. J. Comput. Sci. 2021, 48, 213–222. Available online: https://www.iaeng.org/IJCS/issues_v48/issue_2/IJCS_48_2_01.pdf (accessed on 12 April 2023).
- Arora, D. Five Penetration Testing Challenges that Should Concern Organizations. ERMProtect IT Security Consultant. Available online: https://ermprotect.com/blog/five-penetration-testing-challenges-that-should-concern-organizations/ (accessed on 13 April 2023).
- Dong, S.; Cao, J.; Fan, Z. A Review on Cybersecurity in Smart Local Energy Systems: Requirements, Challenges, and Standards. Available online: https://arxiv.org/ftp/arxiv/papers/2108/2108.08089.pdf (accessed on 1 April 2023).
- Mell, P.; Scarfone, K.; Romanosky, S. CVSS v2 Complete Documentation. FIRST. Available online: www.first.org/cvss/v2/guide (accessed on 13 April 2023).
- Paz, J. The State of Pen Testing 2022 Report, Cobalt. Available online: https://www.cobalt.io/blog/the-state-of-pentesting-2022-how-labor-shortages-are-impacting-cybersecurity-and-developer-professionals (accessed on 15 April 2023).
- Chopra, S. The Ultimate Checklist for Your Penetration Testing Report. 26 May 2023. Available online: https://redfoxsec.com/blog/penetration-testing-report/ (accessed on 12 June 2023).
- Penetration Testing: Trends & Challenges in 2022: Valuementor. Cyber Security Services & Payment Security Services Company. Available online: https://valuementor.com/penetration-testing/penetration-testing-trends-challenges-in-2022/ (accessed on 16 April 2023).
- Vyas, S.; Hannay, J.; Bolton, A.; Burnap, P. Automated Cyber Defence: A Review. Proc. ACM Meas. Anal. Comput. Syst. 2023, 37, 111. [Google Scholar]
- Faeroy, F.L.; Yamin, M.M.; Shukla, A.; Katt, B. Automatic Verification and Execution of Cyber Attack on IoT Devices. Sensors 2023, 23, 733. [Google Scholar] [CrossRef]
- Li, G.; Ren, L.; Fu, Y.; Yang, Z.; Adetola, V.; Wen, J.; Zhu, Q.; Wu, T.; Candan, K.S.; O’Neill, Z. A critical review of cyber-physical security for building automation systems. Annu. Rev. Control 2023, 55, 237–254. [Google Scholar] [CrossRef]
- Heiding, F.; Süren, E.; Olegård, J.; Lagerström, R. Penetration testing of connected households. Comput. Secur. 2023, 126, 103067. [Google Scholar] [CrossRef]
- Garrad, P.; Unnikrishnan, S. Reinforcement learning in VANET penetration testing. Results Eng. 2023, 17, 100970. [Google Scholar] [CrossRef]
- Rak, M.; Salzillo, G.; Granata, D. ESSecA: An automated expert system for threat modelling and penetration testing for IoT ecosystems. Comput. Electr. Eng. 2022, 99, 107721. [Google Scholar] [CrossRef]
- Comert, C.; Kulhandjian, M.; Gul, O.M.; Touazi, A.; Ellement, C.; Kantarci, B.; D’Amours, C. Analysis of Augmentation Methods for RF Fingerprinting under Impaired Channels. In Proceedings of the 2022, ACM Workshop on Wireless Security and Machine Learning (WiseML’22), San Antonio, TX, USA, 19 May 2022; Association for Computing Machinery: New York, NY, USA; pp. 3–8. [Google Scholar] [CrossRef]
- Gul, O.M.; Kulhandjian, M.; Kantarci, B.; Touazi, A.; Ellement, C.; D’amours, C. Secure Industrial IoT Systems via RF Fingerprinting Under Impaired Channels with Interference and Noise. IEEE Access 2023, 11, 26289–26307. [Google Scholar] [CrossRef]
- Zhiyan, C.; Omer, M.G.; Burak, K. Practical Byzantine Fault Tolerance-based Robustness for Mobile Crowdsensing. Distrib. Ledger Technol. 2023, 2, 2769–6472. [Google Scholar] [CrossRef]

| Domain | Subdomain | Reference | Specification |
|---|---|---|---|
| Methodology/framework for pen test | Open Source Security Testing Methodology (OSSTMM) | [37] | This is basically an audit methodology that is easily adaptable in cyberspace for penetration purposes. |
| Open Web Application Security Project (OWASP) | [38,39,40] | A testing guide concentrated on security for firmware, web applications, and mobile applications. | |
| National Institute of Security and Testing (NIST) | [41] | A flexible cyber security framework concentrated on risk assessment and mitigation plans that can adapt easily. | |
| Penetration Testing Execution Standard (PTES) | [42,43,44] | Security experts developed this to specify tools and techniques based on the penetration domain. | |
| Information System Security Assessment Framework (ISSAF) | [45] | A framework for developing one’s own penetration methodology that can establish a relationship between tasks and tools. | |
| Pen testing standards | Commonly used ISO 27000 family | [46,47,48,49,50,51] | Concentrate on security in Information Systems, security risk management, and improvement security practices. |
| Industry-Related Standard Family | [48,52,53,54,55] | Industry standards: ETSI EN 303 645, ISO/SAE 21434, FIPS 140-2, and IEC 62443; concentrate on security in the cyber world and IoT devices. | |
| BIS standard | [52,56,57] | Developed by the German government, focusing on the security product; three distinguished wings: BIS 100-1, 2, and 3. | |
| Penetration tools | Network scanning | [58,59,60] | KaliLinux, WireShark, nmap, Metasploit |
| Web application scanning | [58,59,61] | Invicti/Netsparker, BeEF, Zed Attack Proxy, Brup Suit, Nikto, W3AF, | |
| Malware scanning | [58,61] | Nessues, KaliLinux, Acunetix, | |
| General vulnerability check | [58,61,62] | KaliLinux, Intruder, Metasploit, SQLmap, Acunetix | |
| Traffic scanning | [58,59,63] | WireShark, Astra, Brup Suit | |
| Penetration scoring methods | Risk Scoring System (RSS) | [64] | Numerical scoring system, poor performance in complex to complex systems. |
| Threat, Exposure, Mission, Safety, and Loss (TEMSL) | [65] | Vulnerability remarks: none, some, significant, and it is still in progress. | |
| Industrial Vulnerability Scoring System | [65,66] | Still in progress, and focusing on industry management. | |
| Common Vulnerability Scoring System (CVSS) | [67,68,69] | Numerical scoring, industry standards for IT. |
| Virus | Way of Affecting | Way of Spreading | Way of Protection |
|---|---|---|---|
| Boot sector virus | Overwrites/installs code with the boot file. | Through physical media, mostly. | Stop the initial payload from installing and use a good anti-virus. |
| Parasitic virus | Attaches itself to the exe. file and delivers a payload when the program is executing. | Mostly online links and documents. | Avoid unsecure Wi-Fi and clicking links without being sure; use anti-virus. |
| Stealth virus | It averts anti-virus scanning and hides itself. It attacks the OS processes. | Downloaded through email attachments or unverified software. | Use up-to-date strong anti-virus signatures. |
| Polymorphic virus | Makes a copy of itself when coming in touch and updates the copies. | Creates and modifes its version as well as encrypts their codes that are different from each other. | Preferable cloud native environment; use up-to-date next-generation anti-virus software as well as pop-up blockers. |
| Marco virus | Infects Microsoft Office files and OS that can transport between different OSs. | When an infected document is shared and forwarded. | Strong anti-virus software and awareness about email phishing are preferable. |
| Multipartite virus | It can infect more than one way, both programs and boot sectors. | Typically spread by attaching it to a self-executable file. | Avoiding clicking on suspicious links, use reliable anti-virus software, and keep a backup. |
| Spawn/companion virus | It does not physically touch the files. | Self-copy is saved by the name of another file with a different extension. | Prevention measures of the virus. |
| Web scripting virus | Stand-alone file that could be executed by the interpreter. | Spread through infected websites and steals data or damages file. | Secure web browser, antivirus software, and cyber security measures. |
| Penetration Methodology | Description |
|---|---|
| Open-Source Security Testing Methodology Manual (OSSTMM) [37] | Features: IOSSTMM is an audit methodology for security testing that is adaptable to vulnerability assessment, penetration testing, or ethical hacking. Version 3 (the latest one) of OSSTMM is developed to execute penetration testing for physical and virtual infrastructure, middleware, clouds, networks (mobile, telecommunication, wireless), humans, and data handling issues. It performs security tests at the operation level and does not concentrate on anecdotal evidence or assumptions. There is a set of attack surface and visualization tools for comparative analysis. It also includes a quantitative risk assessment facility. Advantages: It welcomes anyone to an open-source system testing process that shows repetitive and consistent results. It could be integrated with existing laws, policies, and industry regulations. There is guidance to protect the intellectual property of the organization. Disadvantages: The repetitive work increases the complexity, time, and cost as well as the additional effort required to adopt the methodology in the penetration process. Before starting the penetration test, a tester needs to read and understand all processes clearly for adaptation to the system. It focuses on the certification of a security tester and organization. |
| Open Web Application Security Project (OWASP) [38,39,40] | Features: It has three different testing guides based on the type of application, and these are: OWASP Web Security Testing Guide [38]: It concentrates on the software development process and on reducing bugs in the applications. A developer can utilize this to produce secure code and for quality assurance. A software tester can check the software before the release, a project manager can incorporate it to maintain the overall security of the enterprise, and a security expert can verify the security holes. OWASP Mobile Application Security [39]: It provides a service for testing, checklists, test cases, and reverse engineering to review a system, and its working principles are updated regularly. It is guided by a Mobile Application Security Verification Standard (MASVS) that could be used by a mobile app developer, tester, architecture designer, and mobile security professional. It suggests adding test cases for all requirements and tracking compliance for practical assessment. This guide consists of specific guidelines for the Android platform and the iOS platform besides the general guidelines for the vulnerability testing. Reverse engineering, tempering techniques, and prevention methods are incorporated in every case. OWASP Firmware Security Testing Methodology [40]: It is constructed to explore victims’ firmware and examine the features of that firmware. It extracts the characteristics, carves, emulates, and analyzes the content of the file system of a targeted firmware. It is used to execute dynamic security tests of firmware from the interface and analyze runtime binaries or binary exploitation to attain at the root. Moreover, it is now extended to mobile apps that deal with Internet of Things (IoT) and cloud-based information. Advantages: It is highly application-oriented, and it concentrates on the development process, coding, and testing of web-based software, mobile applications, and embedded systems. Integrating security features into a product is the main purpose of this framework. It is also commonly used as a penetration testing framework. Disadvantages: It is mostly concentrated on applications’ security rather than organizations’ security. |
| National Institute of Security and Testing (NIST) [41] | Features: The NIST cyber security framework consists of three main components: the framework core, framework implementation tiers, and framework profile for risk management. Identification, protection, detection, responding, and recovery are the five continuous functions of the core of the framework. It remarks discrete outcomes of subcategories for each function and attempts to match with existing industry standards, practice, and guidelines. It tries to communicate from the strategic level to the operation level on account of the security purposes of the organization. Framework implementation tiers describe the degree of an organization’s cybersecurity practices (i.e., risk management and threat awareness practices, repeatable and adaptive processes). An organization is categorized from tier one to tier four based on the current security practice, threat management, legal and/or regulatory limitations, the business objective, and the constraints of the organization. These outcomes guide a team in developing recommendations for further improvement. An organization can select categories and subcategories from the framework, where a framework profile shows the assumed outcome according to selected categories and subcategories. The profile is aligned with standard guidelines and practices that help to improve the security posture of the current system. A current profile could be used to prioritize and measure the progress towards the target profile. Advantages: This is concentrated on the risk assessments and could be adapted to any organization by selecting categories and subcategories from the framework. Business missions are reinforced in each component of the framework that supports enhancing business security and achieving business goals. Disadvantages: A pen tester needs a very good idea of the framework and the security requirements of the organization before adapting the framework. |
| Penetration Testing Execution Standard (PTES) [42] | Features: It is developed by security experts for seven consecutive steps: pre-engagement interactions or initial communication to know the reasons for pen testing; the intelligence gathering phase collects information of the system; the threats modeling step identifies the existing threats; vulnerability analysis is performed to select the required tools and techniques of exploitation; evidence exploitation and keeping the evidence; analysis of the impact of exploitation on the organization; and developing a detailed report with recommendations. Advantages: It supports a technical guide [43] that specifies tools, domains, and techniques for the penetration test. It tries to develop a minimum baseline for the pen test that cannot cover all scenarios [44]. It generates executive and technical reports for the enterprise [44]. Disadvantages: This is comparatively new, and, until now it has been in the improvement stage. It can be implemented by businesses and security service providers [42]. |
| Information System Security Assessment Framework (ISSAF) [45] | Features: ISSAF is aimed at delivering a comprehensive guide to developing our own pen test methodology that links each step of the penetration test with a specific tool [45]. There are three steps in ISSAF: Step 1 performs the identification of a communication channel between an organization and a pen tester company; it detects the scope, approach, and methodology for execution, and it performs agreement for penetration based on the test case and escalation path. Tools and techniques are explained in Step 2 to specify the targeted area such as the application, database, network, and hosts. It illustrates the detailed scope of the penetration test that is well defined and structured with the process of execution phases. Finally, a complete test is performed in this step. Step 3 is quite brief and focuses on removing the artifacts that are created during the penetration test as well as developing technical and executive reports. Advantages: It establishes relationships between tasks and respective tools. Disadvantages: It is not maintained properly and is a little bit out of date [45]. |
| Standard | Features |
|---|---|
| Commonly used ISO 27000 family [46] | The International Electro Technical Commission (IEC) and International Organization for Standardization (ISO) published the ISO/IEC 27000 series that concentrates on the security of information systems management (ISM) [47]. 27001:2013 has seven steps (installation, operation, monitoring, controlling, maintenance, review, performance, and improvement) that can lead to improved information security practices in business organizations [56]. It supports managing business information and personal information secretly, which can improve the branding of an enterprise [94]. The organization’s assets are securely managed and protected by 27002:2013. Moreover, the personnel, operations, business continuity, compliance, and information of an organization are protected by the guidelines of 27002:2013 [49]. A responsible individual can implement the best practice recommendations of 27002:2013 to improve the security posture of an enterprise [50]. Organizations implement 27005:2018 for cybersecurity risk management with the standard ISO/IEC 27001. ISO/IEC 27005 has employed seven elements in the risk management process [49] that ensure risk mitigation at a satisfactory level, though it depends on the skill, practice, size, sector, and budget of the company [51]. 27006:2015 was initiated for information security certification management by a third party to enhance the trustworthiness of the organization [56]. Information security standards are specified as ISO/IEC 27003:2017 (guidance), ISO/IEC27000:2018 (vocabulary), ISO/IEC 27007:2017 (auditing), ISO/IEC 27004:2016 (monitoring, analysis, evaluation), ISO/IEC 27014:2013 (governance of information security), ISO/IEC 27017:2015 (code of practice) [49], etc. |
| Industry-Related Standard Family [52] | ETSI EN 303 645, ISO/SAE 21434, FIPS 140-2, and IEC 62443 are commonly used by industry standards for special purposes in industry risk mitigation [52]. ETS EN 303 745 mainly concentrates on the policy procedure development for Internet of Things (IoT) management devices [53]. It includes all stakeholders who are related to IoT-based product manufacturing and application development [53]. The ISO/SAE 21434 standard is applied to manage risk and protect road vehicles from cyberattacks. It is extended to minimize risk in the process of vehicle production, development, and maintenance [54]. FIPS 140-2 defines four security levels known as secure cryptography modules that are accepted by federal agencies of the United States and Canada [48]. IEC 62443 consists of a series of international standards for cybersecurity in industry automation [55]. It has different categories to meet the threat protection in the area of cybersecurity. |
| BSI Standard [56] | Bundesamt für Sicherheit in der Informationstechnik (BSI IT) is developed by a German government agency [52] that is responsible for the security of digital communication and computers. It also focuses on the security products, security labs, and security processes [56]. BSI 100-1 describes a few mandatory requirements that are integrated with ISO 27001 to ensure the security of IT infrastructure [56]. The BSI 100-2 standard concentrates on IT security management, step-by-step task implementation for security, and integrating the best practices, while BSI 100-3 is developed for risk analysis based on IT-Grundschutz principles [57]. |
| Method | Scoring System | Application Domain | Limitations |
|---|---|---|---|
| Risk Scoring System (RSS) [64] | Provides a numerical mean score of vulnerabilities | Medical, Commercial Aviation, Weapon System | Fails for complex-to-complex systems |
| Threat, Exposure, Mission, Safety, and Loss (TEMSL) [65] | Vulnerabilities are ranked with quality terms: none, some, and significant. It uses a decision tree to show the priority. | It is applicable where qualified priority (never, next, now) is suitable. | Not standardization: still in progress [65] |
| Industrial Vulnerability Scoring System [66] | It calculates the final score based on four different scores. | Focusing on applying it in the industry security scoring management. | Not standardization: still in progress [65] |
| Common Vulnerability Scoring System (CVSS) [68] | The latest version (CVSSv3.1) calculates scores for three different areas: Base, Temporal, and Environment metrics. | Industry Standard and focuses on IT fields. Could be adjusted in any industry for risk assessment. | Some experts believe that it is difficult to draw the conclusion from temporal and environment scores [68]. |
| CVSSv2 | CVSSv3.0 | CVSSv3.1 |
|---|---|---|
| The score reflects the impact of the vulnerabilities on the entire system. | The score reflects the impact of the vulnerabilities on the impacted components of the system. | The score reflects the impact of the vulnerabilities on the impacted components of the system. |
| This version does not consider environment metrics. | The vulnerabilities that are related to the environment of the application are considered. | The impact of the CVSSv3 environment metrics is modified for subgroups. |
| There is no indication when a vulnerability affects more than one application in a system. | Scope metrics indicate when a vulnerability impacts other applications in the same system. | The vulnerable and impact components are reformulated and clearly indicated by the scope metrics. |
| The impact of a vulnerable application is reflected by impact metrics. | Impact metrics are reflected by the impact degree (none, low, high). | The impact metrics score the result of an exploitation. |
| Authentication metrics may ignore many aspects of vulnerability. | The importance of privileges is reflected by a privilege attack. | A privilege score is generated by an attacker after exploitation and compared with the previous score. |
| Access complexity includes the user’s interaction and configuration of the system. | The complexity of the user interaction and attacks is separated in access complexity. | It demolishes the description ambiguity of the access complexity. |
| An attack vector can consist of physical hardware and a local access system. | Attack vector metrics separate the local complexity from the hardware complexity of the system. | Attack vector metrics are reformulated for the description values of the local, network, and physical components of the system. |
| Reference | Year | Proposal | Way of Execution Penetration | Limitation |
|---|---|---|---|---|
| Sanyam et al. [101] | 2023 | Automated cyber defense | Automated real-time network protection agent generation that would be adaptable for regular penetration testing. | Only for malware penetration. |
| Faeroy et al. [102] | 2023 | Autonomous penetration | Proposed a model for autonomous penetration test and focuses on the vulnerabilities identification of IoT devices. | Limited by Wi-Fi vulnerabilities for IoT. |
| Guewen et al. [103] | 2023 | Automated building safety | Proposed autonomous three-level security for building an automation system that is applicable for regular penetration. | Limited physical penetration. |
| Fredrik et al. [104] | 2023 | Manual pen testing | Applied to a house for physical security and surveillance. | Applied for physical penetration. |
| Phillip and Saritha [105] | 2023 | Pen testing Simulation | Applied the reinforcement learning method for simulation-based penetration testing. | For autonomous vehicles. |
| Massimiliano et al. [106] | 2022 | Systematic IoT testing | Proposed intelligent thread modeling system for performing penetration on IoT infrastructure. | For home IoT security devices. |
| Ceren Comenrt et al. [107] | 2022 | Secure fingureprinting transmission method | Various augmentive methods are applied to securely transmit radio frequency fingerprinting in critical infrastructure such as autonomous vehicle networks. | Only for radio frequency fingureprinting receivers. |
| O.M Gul et al. [108] | 2023 | Secure fingureprinting transmission approach | Various augmentive methods are applied to securely transmit radio frequency fingerprinting in critical infrastructure such as industrial IoT. | Only industry IoT environments are considered. |
| Z. chen et al. [109] | 2023 | Tempering protection system | A blockchain-based decentralized mobile crowdsensing is proposed, which is against tempering in IoT sensing environments. | Works against tempering and fake requests. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sarker, K.U.; Yunus, F.; Deraman, A. Penetration Taxonomy: A Systematic Review on the Penetration Process, Framework, Standards, Tools, and Scoring Methods. Sustainability 2023, 15, 10471. https://doi.org/10.3390/su151310471
Sarker KU, Yunus F, Deraman A. Penetration Taxonomy: A Systematic Review on the Penetration Process, Framework, Standards, Tools, and Scoring Methods. Sustainability. 2023; 15(13):10471. https://doi.org/10.3390/su151310471
Chicago/Turabian StyleSarker, Kamal Uddin, Farizah Yunus, and Aziz Deraman. 2023. "Penetration Taxonomy: A Systematic Review on the Penetration Process, Framework, Standards, Tools, and Scoring Methods" Sustainability 15, no. 13: 10471. https://doi.org/10.3390/su151310471
APA StyleSarker, K. U., Yunus, F., & Deraman, A. (2023). Penetration Taxonomy: A Systematic Review on the Penetration Process, Framework, Standards, Tools, and Scoring Methods. Sustainability, 15(13), 10471. https://doi.org/10.3390/su151310471






