Critical Controlling for the Network Security and Privacy Based on Blockchain Technology: A Fuzzy DEMATEL Approach
Abstract
1. Introduction
- Privacy of Users (Anonymity): User privacy refers to transforming a blockchain user’s genuine identity into something that cannot be traced while ensuring that the original identity remains untraceable. It masks the user’s identity by replacing their genuine network address with a computer-generated one [26];
- Personal Data Privacy (Confidentiality): The privacy of blockchain data is maintained by hiding the contents of a transaction. Confidentiality is another term for data privacy. Data confidentiality ensures that the contents of transactions are protected from illegal access, manipulation, and alteration [27].
- Consensus processes in blockchain maintain Internet security;
- Blockchain is a solution to Internet’s insecurity.
- Blockchain can dramatically lower equipment costs while improving Internet infrastructure’s effectiveness;
- Blockchain has the potential to extend the life of products and services.
2. Literature Review
- Identifying effective security criteria using BT shows the need to apply this technique in NS;
- Provides a comprehensive framework for security standards based on the new Chinese BT;
- The proposed research solution is designed in a three-step approach using conventional multi-criteria decision-making tools.
3. Research Methodologies
3.1. Fuzzy Logic
- (1)
- Reflexive: .
- (2)
- Symmetric: namely, .
- (3)
- Transitive:
3.2. Fuzzy DEMATEL
3.2.1. Calculation of the Left and Right Bounds of Normal Values
3.2.2. Calculation of Crisp Normalized Values
3.2.3. Computation of Final Crisp Values
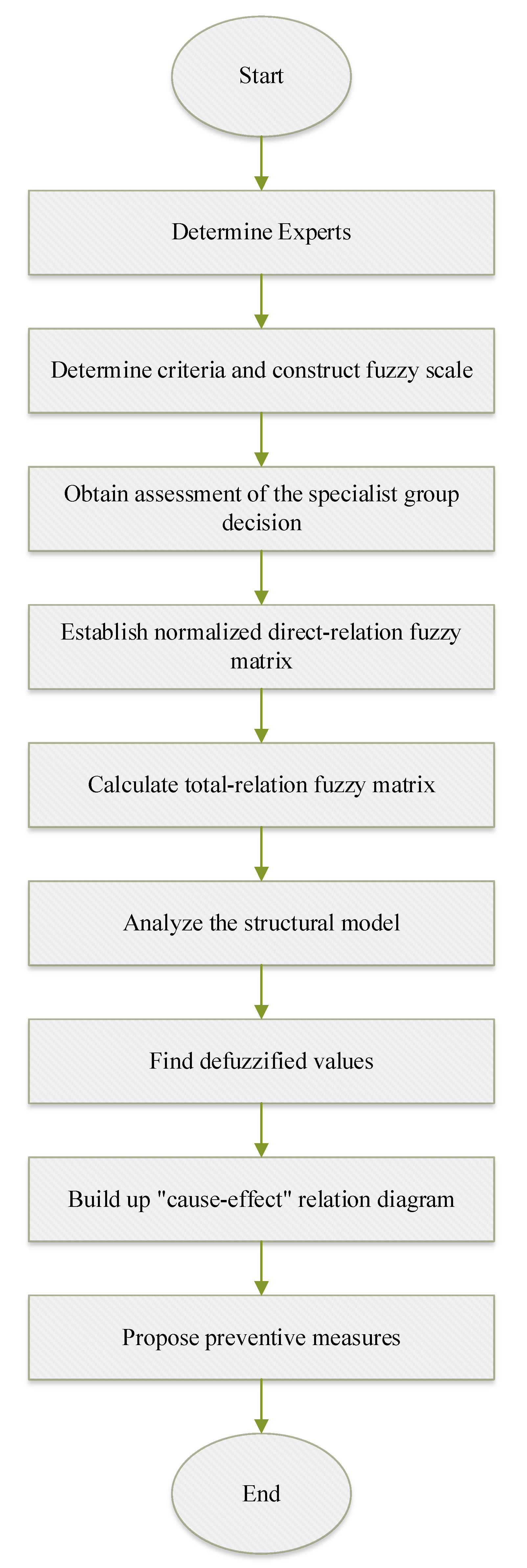
- The sum of rows and columns of matrix Z’s crisp values yields Rj and Ci vector representations. Summing rows and columns can determine a barrier’s influence and influenceability. Using the (Rj − Ci) index, it is possible to explain the causal–effect relationship between the barriers. In terms of influence power, this index represents the barrier’s total effects. The (Rj − Ci) index explains how barriers are related causally using the relation map as a cause-and-effect category. Positive index values indicate that the factor has influenced other factors, whereas negative values indicate that other factors have affected the factor. Figure 2 depicts the procedures implicated in the fuzzy DEMATEL method.
3.3. Important Factors
- Reliability (CR1): Reliability would fulfill IoT device safety, auditing, and inspection [67];
- Prevention (CR2): A technique to enhance IoT cyber security against attacks that consume bandwidth in modern IoT devices [68];
- Network access management (CR3): Related to IoT access management, which is occasionally developed by the Internet Engineering Task Force or the Open Mobile Alliance [69];
- Intrusion detection (CR4): Intrusion Detection Systems (IDS) are used in cloud systems to detect cyberattacks [70];
- Availability (CR5): The blockchain’s persistence property causes availability. Once an update is included in a valid block on the blockchain, it is impossible to remove it [71];
- Authentication( CR6): The authentication mechanism ensures that only authorized users can exchange data and access resources [72];
- Privacy (CR7): The blockchain concept encompasses the user’s and transactions’ privacy [73];
4. An Illustrative Case Study of Fuzzy DEMATEL
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Azizi, N.; Malekzadeh, H.; Akhavan, P.; Haass, O.; Saremi, S.; Mirjalili, S. IoT–Blockchain: Harnessing the Power of Internet of Thing and Blockchain for Smart Supply Chain. Sensors 2021, 21, 6048. [Google Scholar] [CrossRef] [PubMed]
- Kia, M.M.; Alzubi, J.A.; Gheisari, M.; Zhang, X.; Rahimi, M.; Qin, Y. A novel method for recognition of Persian alphabet by using fuzzy neural network. IEEE Access 2018, 6, 77265–77271. [Google Scholar] [CrossRef]
- Ashourian, M.; Gheisari, M.; Hashemi Talkhoncheh, A. An improved node scheduling scheme for resilient packet ring network. Majlesi J. Electr. Eng. 2015, 9, 43–50. [Google Scholar]
- Hassija, V.; Ratnakumar, R.; Chamola, V.; Agarwal, S.; Mehra, A.; Kanhere, S.S.; Binh, H.T.T. A Machine Learning and Blockchain Based Secure and Cost-Effective Framework for Minor Medical Consultations. Sustain. Comput. Informatics Syst. 2022, 35, 100651. [Google Scholar] [CrossRef]
- Stephan, T.; Sharma, K.; Shankar, A.; Punitha, S.; Varadarajan, V.; Liu, P. Fuzzy-Logic-Inspired Zone-Based Clustering Algorithm for Wireless Sensor Networks. Int. J. Fuzzy Syst. 2021, 23, 506–517. [Google Scholar] [CrossRef]
- Zanna, P.; Radcliffe, P.; Kumar, D. Preventing Attacks on Wireless Networks Using SDN Controlled OODA Loops and Cyber Kill Chains. Sensors 2022, 22, 9481. [Google Scholar] [CrossRef]
- Mohanta, B.K.; Jena, D.; Satapathy, U.; Patnaik, S. Survey on IoT Security: Challenges and Solution Using Machine Learning, Artificial Intelligence and Blockchain Technology. Internet Things 2020, 11, 100227. [Google Scholar] [CrossRef]
- Hendalianpour, A. Mathematical Modeling for Integrating Production-Routing-Inventory Perishable Goods: A Case Study of Blood Products in Iranian Hospitals. In Proceedings of the International Conference on Dynamics in Logistics, Breman, Germany, 20–22 February 2018; pp. 125–136. [Google Scholar]
- Du, Y.W.; Sun, X.L. Influence Paths of Marine Ranching Ecological Security in China Based on Probabilistic Linguistic Term Sets and Qualitative Comparative Analysis. Int. J. Fuzzy Syst. 2021, 23, 228–242. [Google Scholar] [CrossRef]
- Oktian, Y.E.; Le, T.-T.-H.; Jo, U.; Kim, H. RealPrice: Blockchain-Powered Real-Time Pricing for Software-Defined Enabled Edge Network. Sensors 2022, 22, 9639. [Google Scholar] [CrossRef]
- Kumar, C.; Bharati, T.S.; Prakash, S. Online Social Network Security: A Comparative Review Using Machine Learning and Deep Learning. Neural Process. Lett. 2021, 53, 843–861. [Google Scholar] [CrossRef]
- Wu, W.W. Mining Significant Factors Affecting the Adoption of SaaS Using the Rough Set Approach. J. Syst. Softw. 2011, 84, 435–441. [Google Scholar] [CrossRef]
- Miglani, A.; Kumar, N. Blockchain Management and Machine Learning Adaptation for IoT Environment in 5G and beyond Networks: A Systematic Review. Comput. Commun. 2021, 178, 37–63. [Google Scholar] [CrossRef]
- Liu, P.; Hendalianpour, A.; Hafshejani, M.F.; Yaghoobi, F.; Feylizadeh, M. System Dynamics Model: Developing Model for Supplier Selection with a Focus on CSR Criteria. Complex Intell. Syst. 2023, 9, 99–114. [Google Scholar] [CrossRef]
- Hendalianpour, A.; Razmi, J.; Gheitasi, M. Comparing Clustering Models in Bank Customers: Based on Fuzzy Relational Clustering Approach. Accounting 2017, 3, 81–94. [Google Scholar] [CrossRef]
- Yontar, E. Critical Success Factor Analysis of Blockchain Technology in Agri-Food Supply Chain Management: A Circular Economy Perspective. J. Environ. Manag 2023, 330, 117173. [Google Scholar] [CrossRef]
- Singh, R.; Khan, S.; Dsilva, J.; Centobelli, P. Blockchain Integrated IoT for Food Supply Chain: A Grey Based Delphi-DEMATEL Approach. Appl. Sci. 2023, 13, 1079. [Google Scholar] [CrossRef]
- Liu, P.; Hendalianpour, A.; Fakhrabadi, M.; Feylizadeh, M. Integrating IVFRN-BWM and Goal Programming to Allocate the Order Quantity Considering Discount for Green Supplier. Int. J. Fuzzy Syst. 2022, 24, 989–1011. [Google Scholar] [CrossRef]
- Ge, H.; Yue, D.; Xie, X.; Deng, S.; Hu, S. Security Control of Networked T–S Fuzzy System Under Intermittent DoS Jamming Attack with Event-Based Predictor. Int. J. Fuzzy Syst. 2019, 21, 700–714. [Google Scholar] [CrossRef]
- Alabool, H.; Kamil, A.; Arshad, N.; Alarabiat, D. Cloud Service Evaluation Method-Based Multi-Criteria Decision-Making: A Systematic Literature Review. J. Syst. Softw. 2018, 139, 161–188. [Google Scholar] [CrossRef]
- Zhang, Y.; Chen, Y.; Miao, K.; Ren, T.; Yang, C.; Han, M. A Novel Data-Driven Evaluation Framework for Fork after Withholding Attack in Blockchain Systems. Sensors 2022, 22, 9125. [Google Scholar] [CrossRef]
- Liu, P.; Hendalianpour, A.; Hamzehlou, M.; Feylizadeh, M.R.; Razmi, J. Identify and Rank the Challenges of Implementing Sustainable Supply Chain Blockchain Technology Using the Bayesian Best Worst Method. Technol. Econ. Dev. Econ. 2021, 27, 656–680. [Google Scholar] [CrossRef]
- Jan, M.A.; Cai, J.; Gao, X.C.; Khan, F.; Mastorakis, S.; Usman, M.; Alazab, M.; Watters, P. Security and Blockchain Convergence with Internet of Multimedia Things: Current Trends, Research Challenges and Future Directions. J. Netw. Comput. Appl. 2021, 175, 102918. [Google Scholar] [CrossRef] [PubMed]
- Siddiqui, Z.A.; Haroon, M. Application of Artificial Intelligence and Machine Learning in Blockchain Technology. In Artificial Intelligence and Machine Learning for EDGE Computing; Academic Press: Cambridge, MA, USA, 2022; pp. 169–185. ISBN 9780128240540. [Google Scholar]
- Bailur, R.P.; Rao, S.; Iyengar, D. Use of Blockchain Partnerships to Enable Transparency in Supply Chain Digitization. In The Oxford Handbook of Supply Chain Management; Choi, T.Y., Li, J.J., Rogers, D.S., Schoenherr, T., Wagner, S.M., Eds.; Oxford University Press: Oxford, UK, 2020. [Google Scholar]
- Amponsah, A.A.; Adekoya, A.F.; Weyori, B.A. A Novel Fraud Detection and Prevention Method for Healthcare Claim Processing Using Machine Learning and Blockchain Technology. Decis. Anal. J. 2022, 4, 100122. [Google Scholar] [CrossRef]
- Junejo, A.Z.; Hashmani, M.A.; Memon, M.M. Empirical Evaluation of Privacy Efficiency in Blockchain Networks: Review and Open Challenges. Appl. Sci. 2021, 11, 7013. [Google Scholar] [CrossRef]
- Errampalli, M.; Patil, K.S.; Prasad, C.S.R.K. Evaluation of Integration between Public Transportation Modes by Developing Sustainability Index for Indian Cities. Case Stud. Transp. Policy 2020, 8, 180–187. [Google Scholar] [CrossRef]
- Patil, P.; Sangeetha, M.; Bhaskar, V. Blockchain for IoT Access Control, Security and Privacy: A Review. Wirel. Pers. Commun. 2021, 117, 1815–1834. [Google Scholar] [CrossRef]
- Gaur, R.; Prakash, S.; Kumar, S.; Abhishek, K.; Msahli, M.; Wahid, A. A Machine-Learning–Blockchain-Based Authentication Using Smart Contracts for an IoHT System. Sensors 2022, 22, 9074. [Google Scholar] [CrossRef]
- Xu, L.D.; Lu, Y.; Li, L. Embedding Blockchain Technology into IoT for Security: A Survey. IEEE Internet Things J. 2021, 8, 10452–10473. [Google Scholar] [CrossRef]
- Shen, B.; Xu, X.; Yuan, Q. Selling Secondhand Products through an Online Platform with Blockchain. Transp. Res. Part E Logist. Transp. Rev. 2020, 142, 102066. [Google Scholar] [CrossRef]
- Jakeri, M.M.; Hassan, M.F. Criteria Prioritization in Adaptive Security Activities Selection, ASAS Model Using Analytic Network Process, ANP. In Proceedings of the 2019 IEEE Conference on Application, Information and Network Security (AINS), Pulau Pinang, Malaysia, 19–21 November 2019; IEEE: Manhattan, NY, USA; pp. 6–11. [Google Scholar]
- Zhou, J.; Wu, Y.; Liu, F.; Tao, Y.; Gao, J. Prospects and Obstacles Analysis of Applying Blockchain Technology to Power Trading Using a Deeply Improved Model Based on the DEMATEL Approach. Sustain. Cities Soc. 2021, 70, 102910. [Google Scholar] [CrossRef]
- Karuppiah, K.; Sankaranarayanan, B.; Ali, S.M. A Decision-Aid Model for Evaluating Challenges to Blockchain Adoption in Supply Chains. Int. J. Logist. Res. Appl. 2023, 26, 257–278. [Google Scholar] [CrossRef]
- Varshney, T.; Sharma, N.; Kaushik, I.; Bhushan, B. Authentication Encryption Based Security Services in Blockchain Technology. In Proceedings of the 2019 International Conference on Computing, Communication, and Intelligent Systems (ICCCIS), Greater Noida, India, 18–19 October 2019; IEEE: Manhattan, NY, USA; Volume 2019, pp. 63–68. [Google Scholar]
- Schlecht, L.; Schneider, S.; Buchwald, A. The Prospective Value Creation Potential of Blockchain in Business Models: A Delphi Study. Technol. Forecast. Soc. Chang. 2021, 166, 120601. [Google Scholar] [CrossRef]
- Schwerin, S. Blockchain and Privacy Protection in the Case of the European General Data Protection Regulation (GDPR): A Delphi Study. J. Br. Blockchain Assoc. 2018, 1, 1–77. [Google Scholar] [CrossRef]
- Kamalov, F.; Moussa, S.; El Khatib, Z.; Mnaouer, A.B. Orthogonal Variance-Based Feature Selection for Intrusion Detection Systems. In Proceedings of the 2021 International Symposium on Networks, Computers and Communications (ISNCC), Dubai, United Arab Emirates, 31 October–2 November 2021; pp. 1–5. [Google Scholar]
- Kamalov, F.; Moussa, S.; Zgheib, R.; Mashaal, O. Feature Selection for Intrusion Detection Systems. In Proceedings of the 2020 13th International Symposium on Computational Intelligence and Design (ISCID), Hangzhou, China, 12–13 December 2020; pp. 265–269. [Google Scholar]
- Thabtah, F.; Kamalov, F. Phishing Detection: A Case Analysis on Classifiers with Rules Using Machine Learning. J. Inf. Knowl. Manag. 2017, 16, 1750034. [Google Scholar] [CrossRef]
- Wang, H.; Wang, X.A.; Xiao, S.; Liu, J. Sen Decentralized Data Outsourcing Auditing Protocol Based on Blockchain. J. Ambient Intell. Humaniz. Comput. 2021, 12, 2703–2714. [Google Scholar] [CrossRef]
- Wang, X.A.; Liu, Y.; Sangaiah, A.K.; Zhang, J. Improved Publicly Verifiable Group Sum Evaluation over Outsourced Data Streams in IoT Setting. Computing 2019, 101, 773–790. [Google Scholar] [CrossRef]
- Panda, S.; Modak, N.M.; Pradhan, D. Corporate Social Responsibility, Channel Coordination and Profit Division in a Two-Echelon Supply Chain. Int. J. Manag. Sci. Eng. Manag. 2016, 11, 22–33. [Google Scholar] [CrossRef]
- Gheisari, M.; Wang, G.; Chen, S.; Seyfollahi, A. A method for privacy-preserving in IoT-SDN integration environment. In Proceedings of the 2018 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Ubiquitous Computing & Communications, Big Data & Cloud Computing, Social Computing & Networking, Sustainable Computing & Communications (ISPA/IUCC/BDCloud/SocialCom/SustainCom), Melbourne, VIC, Australia, 11–13 December 2018; pp. 895–902. [Google Scholar] [CrossRef]
- Iqbal, A.; Amir, M.; Kumar, V.; Alam, A.; Umair, M. Integration of next Generation IIoT with Blockchain for the Development of Smart Industries. Emerg. Sci. J. 2020, 4, 1–17. [Google Scholar] [CrossRef]
- Si, H.; Sun, C.; Li, Y.; Qiao, H.; Shi, L. IoT Information Sharing Security Mechanism Based on Blockchain Technology. Futur. Gener. Comput. Syst. 2019, 101, 1028–1040. [Google Scholar] [CrossRef]
- Kabak, Ö.; Ülengin, F.; Çekyay, B.; Önsel, Ş.; Özaydın, Ö. Critical Success Factors for the Iron and Steel Industry in Turkey: A Fuzzy DEMATEL Approach. Int. J. Fuzzy Syst. 2016, 18, 523–536. [Google Scholar] [CrossRef]
- Guo, X.; Liu, A.; Li, X.; Xiao, Y. Research on the Intelligent Fault Diagnosis of Medical Devices Based on a DEMATEL-Fuzzy Concept Lattice. Int. J. Fuzzy Syst. 2020, 22, 2369–2384. [Google Scholar] [CrossRef]
- Han, W.; Sun, Y.; Xie, H.; Che, Z. Hesitant Fuzzy Linguistic Group DEMATEL Method with Multi-Granular Evaluation Scales. Int. J. Fuzzy Syst. 2018, 20, 2187–2201. [Google Scholar] [CrossRef]
- Suzan, V.; Yavuzer, H. A Fuzzy Dematel Method To Evaluate The Most Common Diseases In Internal Medicine. Int. J. Fuzzy Syst. 2020, 22, 2385–2395. [Google Scholar] [CrossRef]
- Lin, A.J.; Chang, H.-Y.; Huang, S.-W.; Tzeng, G.-H. Improving Service Quality of Wealth Management Bank for High-Net-Worth Customers During COVID-19: A Fuzzy-DEMATEL Approach. Int. J. Fuzzy Syst. 2021, 23, 2449–2466. [Google Scholar] [CrossRef]
- Xie, H.; Ren, Q.; Duan, W.; Sun, Y.; Han, W. New Dynamic Group DEMATEL Decision-Making Method Based on Hesitant Fuzzy Linguistic Term Sets. Int. J. Fuzzy Syst. 2021, 23, 2118–2131. [Google Scholar] [CrossRef]
- Xu, X.; Su, P.; Wang, F.; Chen, L.; Xie, J.; Atindana, V.A. Coordinated Control of Dual-Motor Using the Interval Type-2 Fuzzy Logic in Autonomous Steering System of AGV. Int. J. Fuzzy Syst. 2021, 23, 1070–1086. [Google Scholar] [CrossRef]
- Li, H.; Wang, W.; Fan, L.; Li, Q.; Chen, X. A Novel Hybrid MCDM Model for Machine Tool Selection Using Fuzzy DEMATEL, Entropy Weighting and Later Defuzzification VIKOR. Appl. Soft Comput. 2020, 91, 106207. [Google Scholar] [CrossRef]
- Jana, S.H.; Jana, B. Application of Random Triangular and Gaussian Type-2 Fuzzy Variable to Solve Fixed Charge Multi-Item Four Dimensional Transportation Problem. Appl. Soft Comput. 2020, 96, 106589. [Google Scholar] [CrossRef]
- Liu, P.; Hendalianpour, A.; Hamzehlou, M.; Feylizadeh, M. Cost Reduction of Inventory-Production-System in Multi-Echelon Supply Chain Using Game Theory and Fuzzy Demand Forecasting. Int. J. Fuzzy Syst. 2022, 24, 1793–1813. [Google Scholar] [CrossRef]
- Parmar, P.S.; Desai, T.N. Evaluating Sustainable Lean Six Sigma Enablers Using Fuzzy DEMATEL: A Case of an Indian Manufacturing Organization. J. Clean. Prod. 2020, 265, 121802. [Google Scholar] [CrossRef]
- Dutta, P. Mathematics of Uncertainty: An Exploration on Semi-Elliptic Fuzzy Variable and Its Properties. SN Appl. Sci. 2020, 2, 111. [Google Scholar] [CrossRef]
- Hendalianpour, A.; Fakhrabadi, M.; Zhang, X.; Feylizadeh, M.R.; Gheisari, M.; Liu, P.; Ashktorab, N. Hybrid Model of IVFRN-BWM and Robust Goal Programming in Agile and Flexible Supply Chain, a Case Study: Automobile Industry. IEEE Access 2019, 7, 71481–71492. [Google Scholar] [CrossRef]
- Jiang, S.; Shi, H.; Lin, W.; Liu, H.-C. A Large Group Linguistic Z-DEMATEL Approach for Identifying Key Performance Indicators in Hospital Performance Management. Appl. Soft Comput. 2020, 86, 105900. [Google Scholar] [CrossRef]
- Opricovic, S.; Tzeng, G.H. Defuzzification within a Multi-criteria Decision Model. Int. J. Uncertain. Fuzziness Knowl. Based Syst. 2003, 11, 635–652. [Google Scholar] [CrossRef]
- Mohammadfam, I.; Mirzaei Aliabadi, M.; Soltanian, A.R.; Tabibzadeh, M.; Mahdinia, M. Investigating Interactions among Vital Variables Affecting Situation Awareness Based on Fuzzy DEMATEL Method. Int. J. Ind. Ergon. 2019, 74, 102842. [Google Scholar] [CrossRef]
- Amirghodsi, S.; Naeini, A.B.; Makui, A. An Integrated Delphi-DEMATEL-ELECTRE Method on Gray Numbers to Rank Technology Providers. IEEE Trans. Eng. Manag. 2020, 69, 1348–1364. [Google Scholar] [CrossRef]
- Chen, L.; Hendalianpour, A.; Feylizadeh, M.R.; Xu, H. Factors Affecting the Use of Blockchain Technology in Humanitarian Supply Chain: A Novel Fuzzy Large-Scale Group-DEMATEL. Gr. Decis. Negot. 2023, 32, 359–394. [Google Scholar] [CrossRef]
- Qian, Y.; Jiang, Y.; Chen, J.; Zhang, Y.; Song, J.; Zhou, M.; Pustišek, M. Towards Decentralized IoT Security Enhancement: A Blockchain Approach. Comput. Electr. Eng. 2018, 72, 266–273. [Google Scholar] [CrossRef]
- Choudhary, S.; Kesswani, N. Detection and Prevention of Routing Attacks in Internet of Things. In Proceedings of the 17th IEEE International Conference on Trust, Security and Privacy in Computing, New York, NY, USA, 1–3 August 2018; pp. 1537–1540. [Google Scholar]
- Novo, O. Scalable Access Management in IoT Using Blockchain: A Performance Evaluation. IEEE Internet Things J. 2019, 6, 4694–4701. [Google Scholar] [CrossRef]
- Alkadi, O.; Moustafa, N.; Turnbull, B. A Review of Intrusion Detection and Blockchain Applications in the Cloud: Approaches, Challenges and Solutions. IEEE Access 2020, 8, 104893–104917. [Google Scholar] [CrossRef]
- Boudguiga, A.; Bouzerna, N.; Granboulan, L.; Olivereau, A.; Quesnel, F.; Roger, A.; Sirdey, R. Towards Better Availability and Accountability for IoT Updates by Means of a Blockchain. In Proceedings of the 2nd IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Paris, France, 26–28 April 2017; IEEE: Manhattan, NY, USA; pp. 50–58. [Google Scholar]
- Khan, M.A.; Salah, K. IoT Security: Review, Blockchain Solutions, and Open Challenges. Futur. Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Security and Privacy on Blockchain. ACM Comput. Surv. 2019, 52, 51. [Google Scholar] [CrossRef]
- Gheisari, M.; Ebrahimzadeh, F.; Rahimi, M.; Moazzamigodarzi, M.; Liu, Y.; Dutta Pramanik, P.K.; Heravi, M.A.; Mehbodniya, A.; Ghaderzadeh, M.; Feylizadeh, M.R.; et al. Deep learning: Applications, architectures, models, tools, and frameworks: A comprehensive survey. CAAI Trans. Intell. Technol. 2023. [Google Scholar] [CrossRef]
- Thakore, R.; Vaghashiya, R.; Patel, C.; Doshi, N. Blockchain—Based IoT: A Survey. Procedia Comput. Sci. 2019, 155, 704–709. [Google Scholar] [CrossRef]
- Jivanyan, A. Lelantus: Towards Confidentiality and Anonymity of Blockchain Transactions from Standard Assumptions. Available online: https://lelantus.io/lelantus.pdf (accessed on 1 March 2023).
- Ghaderzadeh, M.; Aria, M. Management of COVID-19 Detection Using Artificial Intelligence in 2020 Pandemic. In Proceedings of the 5th International Conference on Medical and Health Informatics, Kyoto, Japan, 14–16 May 2021; pp. 32–38. [Google Scholar]
- Hosseini, A.; Eshraghi, M.A.; Taami, T.; Sadeghsalehi, H.; Hoseinzadeh, Z.; Ghaderzadeh, M.; Rafiee, M. A mobile application based on efficient lightweight CNN model for classification of B-ALL cancer from non-cancerous cells: A design and implementation study. Inform. Med. Unlocked 2023, 39, 101244. [Google Scholar] [CrossRef]

| Preference in Terms of Score | Description of the Linguistic Variable | Equivalent Trapezoidal Fuzzy Numbers (TrFN) |
|---|---|---|
| 0 | No Influence (No) | (0, 0, 0.1, 0.2) |
| 1 | Very Low Influence (VL) | (0.1, 0.2, 0.3, 0.4) |
| 2 | Low Influence (L) | (0.3, 0.4, 0.5, 0.6) |
| 3 | High Influence (H) | (0.5, 0.6, 0.7, 0.8) |
| 4 | Very High Influence (VH) | (0.7, 0.8, 0.9, 1) |
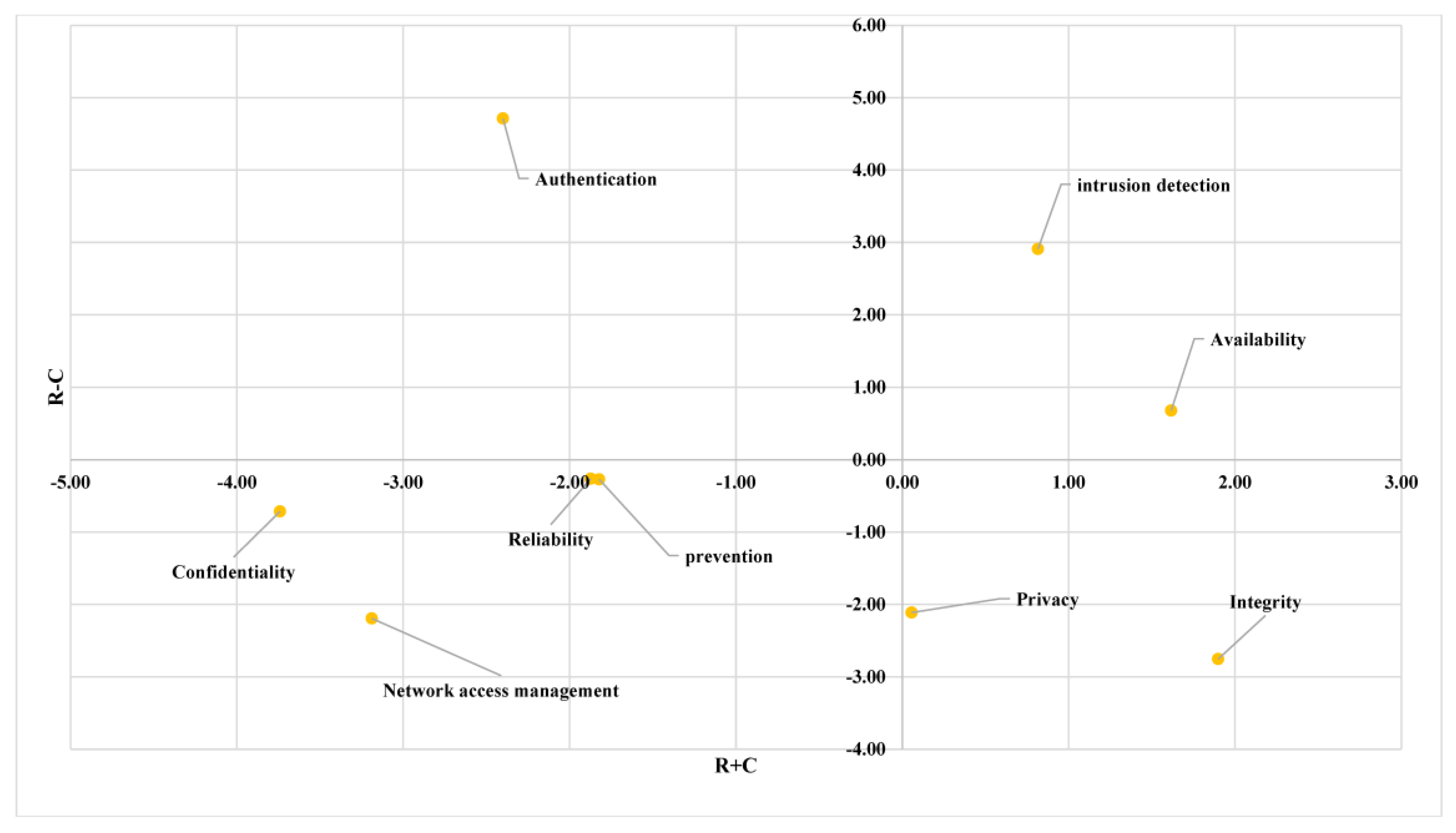
| Criteria | R | C | R + C | R − C | Cause/Effect |
|---|---|---|---|---|---|
| CR1 | −1.07 | −0.81 | −1.87 | −0.26 | Effect |
| CR2 | −1.05 | −0.78 | −1.82 | −0.27 | Effect |
| CR3 | −2.69 | −0.50 | −3.19 | −2.19 | Effect |
| CR4 | 1.86 | −1.05 | 0.82 | 2.91 | Cause |
| CR5 | 1.15 | 0.47 | 1.62 | 0.68 | Cause |
| CR6 | 1.16 | −3.56 | −2.40 | 4.71 | Cause |
| CR7 | −1.03 | 1.08 | 0.06 | −2.11 | Effect |
| CR8 | −0.43 | 2.33 | 1.90 | −2.75 | Effect |
| CR9 | −2.23 | −1.51 | −3.74 | −0.71 | Effect |
| Criteria | CR1 | CR1 | CR1 | CR1 | CR1 | CR1 | CR1 | CR1 | CR1 |
|---|---|---|---|---|---|---|---|---|---|
| CR1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 |
| CR2 | 0 | 1 | 1 | 0 | 0 | 1 | 1 | 0 | 0 |
| CR3 | 0 | 0 | 1 | 1 | 0 | 0 | 1 | 1 | 1 |
| CR4 | 1 | 0 | 1 | 1 | 1 | 1 | 1 | 1 | 0 |
| CR5 | 0 | 1 | 0 | 1 | 1 | 0 | 1 | 1 | 1 |
| CR6 | 0 | 1 | 1 | 0 | 1 | 1 | 1 | 1 | 0 |
| CR7 | 1 | 1 | 1 | 0 | 1 | 1 | 1 | 1 | 0 |
| CR8 | 0 | 0 | 0 | 1 | 0 | 0 | 1 | 1 | 1 |
| CR9 | 1 | 0 | 1 | 0 | 1 | 1 | 0 | 0 | 1 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kamalov, F.; Gheisari, M.; Liu, Y.; Feylizadeh, M.R.; Moussa, S. Critical Controlling for the Network Security and Privacy Based on Blockchain Technology: A Fuzzy DEMATEL Approach. Sustainability 2023, 15, 10068. https://doi.org/10.3390/su151310068
Kamalov F, Gheisari M, Liu Y, Feylizadeh MR, Moussa S. Critical Controlling for the Network Security and Privacy Based on Blockchain Technology: A Fuzzy DEMATEL Approach. Sustainability. 2023; 15(13):10068. https://doi.org/10.3390/su151310068
Chicago/Turabian StyleKamalov, Firuz, Mehdi Gheisari, Yang Liu, Mohammad Reza Feylizadeh, and Sherif Moussa. 2023. "Critical Controlling for the Network Security and Privacy Based on Blockchain Technology: A Fuzzy DEMATEL Approach" Sustainability 15, no. 13: 10068. https://doi.org/10.3390/su151310068
APA StyleKamalov, F., Gheisari, M., Liu, Y., Feylizadeh, M. R., & Moussa, S. (2023). Critical Controlling for the Network Security and Privacy Based on Blockchain Technology: A Fuzzy DEMATEL Approach. Sustainability, 15(13), 10068. https://doi.org/10.3390/su151310068










