Compared with TSC, blockchain technology uses encryption algorithms to ensure the security of data transmission, and the characteristics of smart contracts expand the transaction scale. This part will first use the three-party evolutionary game model to prove that financial institutions, core enterprises, and SMEs prefer to use the BSC. The use of blockchain technology has enabled enterprises and financial institutions to expand their scale and achieve sustainable development. In the context of BSC, we then explore the factors that influence data sharing between the three parties. In the supply chain, core enterprises often occupy the leading position because of their large scale and sufficient funds. Financial institutions, such as banks, tend to cooperate with core enterprises. On the other hand, SMEs are difficult to obtain bank loans for and therefore rely on core enterprises for transactions. On the basis of this observation, we construct a dynamic evolutionary game model between core enterprises and SMEs. On this basis, we study the game theory between core enterprises and financial institutions. Under specific conditions, core enterprises and financial institutions benefit from cooperation and achieve sustainable development.
3.1. BSC vs. TSC in a Three-Party Dynamic Evolutionary Game Model
(1) Model Hypotheses
Hypothesis 1: The players in this model are core enterprises , the SMEs , and financial institution The three parties are participants in bounded rationality, and strategy selection gradually evolves and stabilizes to the optimal strategy over time.
Hypothesis 2: The strategy space for the core enterprises and SMEs is = {upload real data, upload false data}. The probability that the core enterprise chooses action is , and the probability of choosing action is . Similarly, and are probabilities that SMEs choose action and respectively. The strategy space for the financial institution is = {BSC, TSC}. The probability that the financial institution chooses action is , and the probability of choosing action is .
Hypothesis 3: In the TSC, the payoffs of core enterprises, SMEs, and financial institutions are respectively. In the BSC, the payoffs of core enterprises, SMEs, and financial institutions are respectively. Compared to TSC, BSC has expanded the transaction scale and improved the payoff of all three parties, so .
Hypothesis 4: The number of data shared by core enterprises and SMEs is respectively. Data may be lost during transmission, resulting in poor quality shared data. In the TSC, after transmission is complete, the data shared by the core enterprises and SMEs are Where, represents the accuracy of data in the TSC. Blockchain technology improves the accuracy and security of data transmission. Therefore, we assume that after data transmission in the BSC, the data shared by core enterprises and SMEs are still .
Hypothesis 5: If both core enterprises and SMEs upload real data, an additional synergy payoff will be generated. The value of the synergy payoff is and in BSC and TSC, respectively. The synergy payoff is proportional to the sum of the uploaded data. Therefore, it is reasonable to suppose , and is the coefficient of the synergy payoff. Core enterprises and SMEs share the synergy payoff. The proportion of core enterprises is , the proportion of SMEs is , where . Because core enterprises and SMEs share real data, the transaction scale expands, and financial institutions obtain additional payoff in the BSC and TSC, respectively. In BSC, the supply chain expands the transaction scale and financial institutions gain more profits. Therefore, we assume that .
Hypothesis 6: Uploading real data will bring risks, and the transaction’s counterparty will take the opportunity to lower the price after obtaining the real data. Thus, in the BSC, the risk cost for core enterprises and SMEs uploading real data is supposed as , respectively. The cost of core enterprises is higher than that of SMEs, so . Similarly, in the TSC, the risk cost for core enterprises and SMEs uploading real data is supposed as respectively, where . Blockchain technology improves the security of data transmission and sharing. Therefore, we assume .
Based on the above assumptions, the related symbols are further described in
Table 1.
(2) Model Construction
From the above analysis, we can obtain the payoff matrix of the dynamic game between the core enterprises, the SMEs, and the financial institution, as shown in
Table 2.
(3) Model analysis.
In this section, we analyze whether financial institutions choose BSC or TSC, so we calculate and compare the payoff of core enterprises, SMEs, and financial institutions in BSC or TSC, respectively.
We assume that the average payoffs of core enterprises in BSC and TSC are
and
, respectively. After the calculation, we obtain the following formula:
The average payoffs of SMEs in BSC and TSC are
and
, respectively. After the calculation, we obtain the following formula.
The average payoffs of financial institutions in BSC and TSC are
and
, respectively. After the calculation, we obtain the following formula.
From (1) to (6), we obtain . Therefore, financial institutions, core enterprises, and SMEs tend to choose BSC. In the subsequent analysis, we calculate and analyze in the context of blockchain by default.
3.2. Dynamic Game between Core Enterprises and SMEs in BSC
(1) Model Hypotheses
Hypothesis 1: The players in this model are core enterprises and the SMEs , both of which are limited rational agents. The strategy space for the core enterprises and SMEs is = {upload real data, upload false data}. The probability that the core enterprise chooses action is , and the probability of choosing action is . Similarly, and are probabilities that SMEs choose action and , respectively.
Hypothesis 2: In BSC, the core enterprises and SMEs obtain payoff respectively. The number of data shared by core enterprises and SMEs is respectively. If the two agents upload real data, an additional synergy payoff is obtained. The synergy payoff is proportional to the sum of the uploaded data. Therefore, it is reasonable to suppose , and is the coefficient of the synergy payoff. The core enterprises and the SMEs share the synergy payoff. The proportion of core enterprises is , the proportion of SMEs is , where . Therefore, the synergy payoff obtained by core enterprises and SMEs are and respectively.
Hypothesis 3: Uploading real data will bring risks, and the transaction’s counterparty will take the opportunity to lower the price after obtaining the real data. Thus, the risk cost for the core enterprises and SMEs uploading real data is supposed as respectively. The cost of core enterprises is higher than that of SMEs, so . The total risk cost is proportional to the data on the chain, so , , where is the risk coefficient for uploading data.
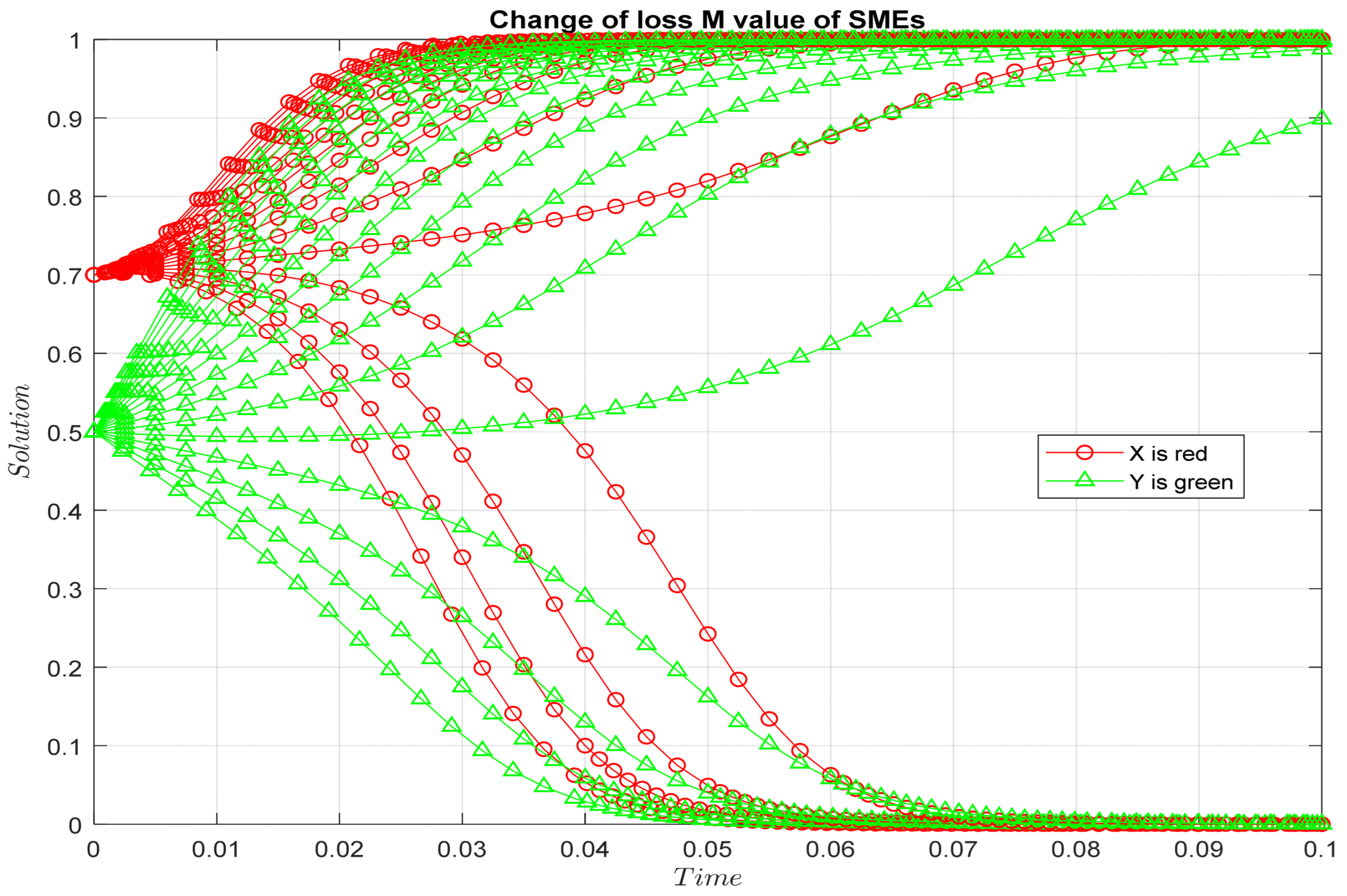
Hypothesis 4: Core enterprises have a strong influence on SMEs. If an SME uploads false data, the core company will penalize the SME when it is discovered. For example, core enterprises may reduce or even cancel the contracts. The impact of SMEs uploading false data to core enterprises is negligible, but the penalties imposed on SMEs by core enterprises result in SMEs suffering huge losses. Assuming that the core enterprises penalize the SMEs after the SMEs upload false data, the SME’s loss is
, where
. Meanwhile, we assume that
, since SMEs will lose core business (
Table 3).
(2) Model Construction
From the above analysis, we can obtain the payoff matrix of the dynamic game between the core enterprises and the SMEs, as shown in
Table 4.
(3) The replication dynamic equation
In the evolutionary game process, the core enterprises and SMEs continue to transfer stability strategies to the subsequent game process through learning and imitation. When and are equal to a certain value, both sides have a stable state. When the values of and change, the game strategy of both sides also changes.
According to
Table 4, the expected payoff of the core enterprises
when adopting the strategies of “uploading real data” and “uploading false data” is
respectively. The average payoff is
. The following information can be obtained as follows:
The replication dynamic equation is a dynamic differential equation formed by simulating the replication dynamic mechanism process of the biological evolutionary game, which is used to describe the frequency of dominant strategies taken by game players. If
, core enterprises choose the action strategy of uploading real data, which can bring a higher payoff than the average payoff. At this time, the proportion
of core enterprises choosing to upload real data strategy will increase with time. If
, core enterprises choose the action strategy of uploading false data, which can bring a higher than average payoff. At this time, the proportion
of core enterprises choosing to upload false data strategy will increase with time. The replication dynamic equation of probability
for core enterprises to adopt the strategy of “uploading real data” is as follows.
The steady-state value describes the extent to which core enterprises will choose to upload real data through a dynamic evolutionary game. The steady-state values and can be solved from .
Assume that the expected payoff of SMEs
when adopting the strategy of “uploading real data” and “uploading false data” is respectively
. The average payoff is
. After the calculation, we obtain the following formula:
The replication dynamic equation of probability
for SMEs to adopt the strategy of “uploading real data” is as follows:
The steady-state value describes the extent to which SMEs will choose to upload real data through a dynamic evolutionary game. The steady-state values and can be solved from .
(4) The trend and stability of the core enterprise action strategy
According to the replication dynamic Equation (10), its derivative can be calculated as follows:
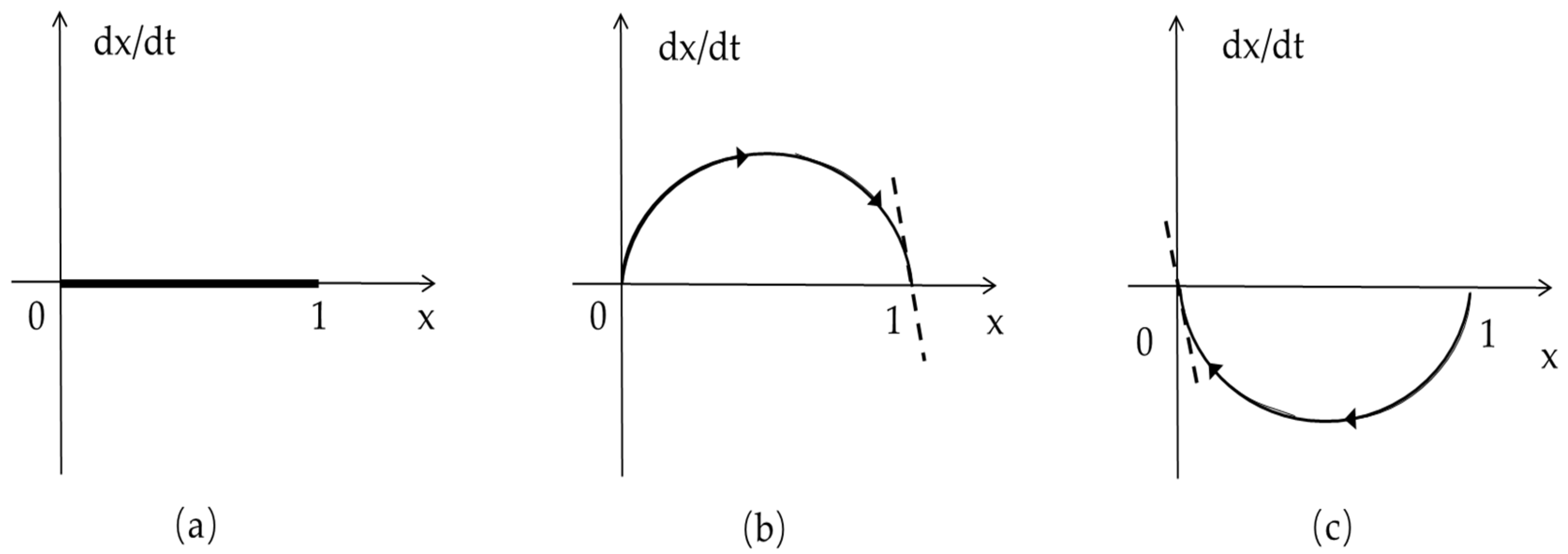
When
, that is,
is always stable. At this time, the replication dynamic equation of the core enterprise is shown in
Figure 1a. When SMEs choose the action strategy of uploading real data with the probability of
, there is no difference between the payoff of core enterprises choosing to upload real data or false data. That is,
is the stable state of core enterprises.
When
,
and
are two possible stable points of
. Because
,
is an evolutionary stability strategy. The replication dynamics of the core enterprises are shown in
Figure 1b. When the SMEs choose the action strategy of uploading real data with a probability higher than
, core enterprises will gradually change from uploading false data to uploading real data. At this time, uploading real data is the core enterprise’s evolutionary stability strategy.
When
,
and
are two possible stable points of
. Because
,
is an evolutionary stability strategy. The replication dynamics of the core enterprises are shown in
Figure 1c. When the SMEs choose the action strategy of uploading real data with a probability lower than
, core enterprises will gradually change from uploading real data to uploading false data. At this time, uploading false data is the core enterprise’s evolutionary stability strategy.
(5) The trend and the stability of the SMEs action strategies
According to the replication dynamic Equation (14), its derivative can be calculated as follows:
When , that is, is always stable. When core enterprises choose the action strategy of uploading real data with the probability of , there is no difference between the payoff of SMEs choosing to upload real data or false data. That is, is the stable state of SMEs.
When , and are two possible stable points of . Because , is an evolutionary stability strategy. When core enterprises choose the action strategy of uploading real data with a probability higher than , SMEs will gradually change from uploading false data to uploading real data. At this time, uploading real data is the evolutionary stability strategy of SMEs.
When , and are two possible stable points of . Because , is an evolutionary stability strategy. When core enterprises choose the action strategy of uploading real data with a probability lower than , SMEs will gradually change from uploading real data to uploading false data. At this time, uploading false data is the evolutionary stability strategy of SMEs.
(6) Equilibrium analysis of dynamic evolution
Core enterprises and SMEs have reached a stable state through continuous evolution. According to Equations (10) and (14), let and to obtain the five equilibrium points of the replicated dynamic equation, , where .
According to the replication dynamic equation of core enterprises and SMEs, the corresponding Jacobian matrix can be obtained as follows:
The dynamic game solution space between core enterprises and SMEs is
, thus
,
. According to the stability theorem of the differential equation, when the determinant (
) of the Jacobian matrix of a local equilibrium point is greater than zero and the trace of the Jacobian matrix (
) is less than zero, the local equilibrium point is a stable strategy in an evolutionary game. The steady-state analysis of five local equilibrium points is shown in
Table 5.
It can be seen in
Table 5 that the two stable equilibrium points of the evolutionary game between core enterprises and SMEs are
and
. SMEs and core enterprises stay consistent in their action strategies and choose to upload real data or false data at the same time.
and
indicate that the action strategies of the core enterprises and the SMEs are inconsistent and are unstable points.
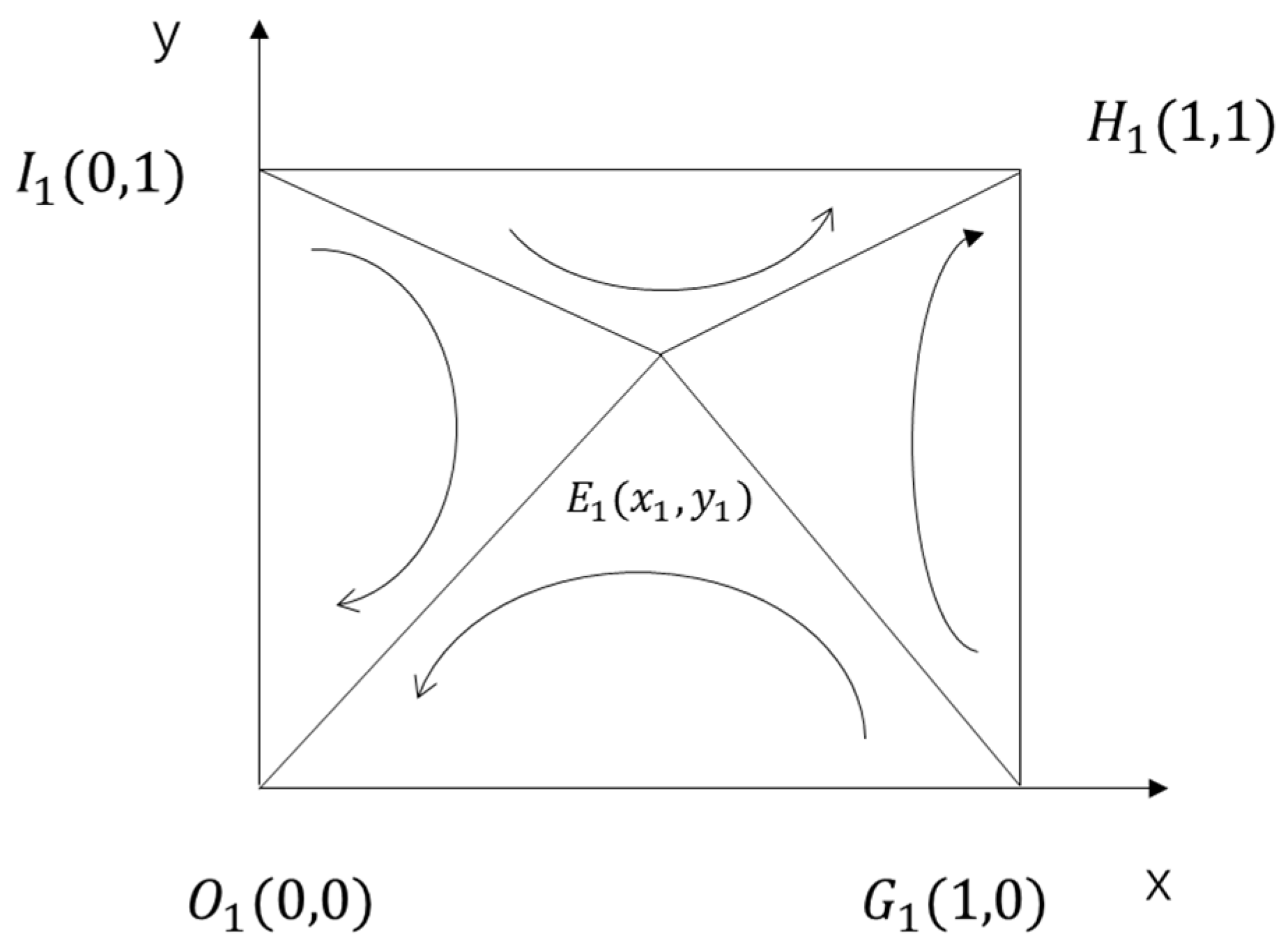
is a saddle point. The phase diagram of the dynamic evolution of core enterprises and SMEs is shown in
Figure 2.
is the key point where the replication dynamic curve tends to
and
. If the initial point of the game between core enterprises and SMEs is near
, a slight disturbance will affect the trend of the replication dynamic curve. The point at which the curve ultimately tends to ultimately depends on the area
of polygon
and the area
of polygon
. If
, the copied dynamic curve will tend to
. Both core enterprises and SMEs tend to upload the evolution results of false data. If
, the replication dynamic curve will tend to
. Both core enterprises and SMEs tend to upload the evolution results of real data. Analyze the factors that influence the tendency of both parties to upload real data. The key is to analyze the factors that affect
changes. After calculation, the
formula is as follows.
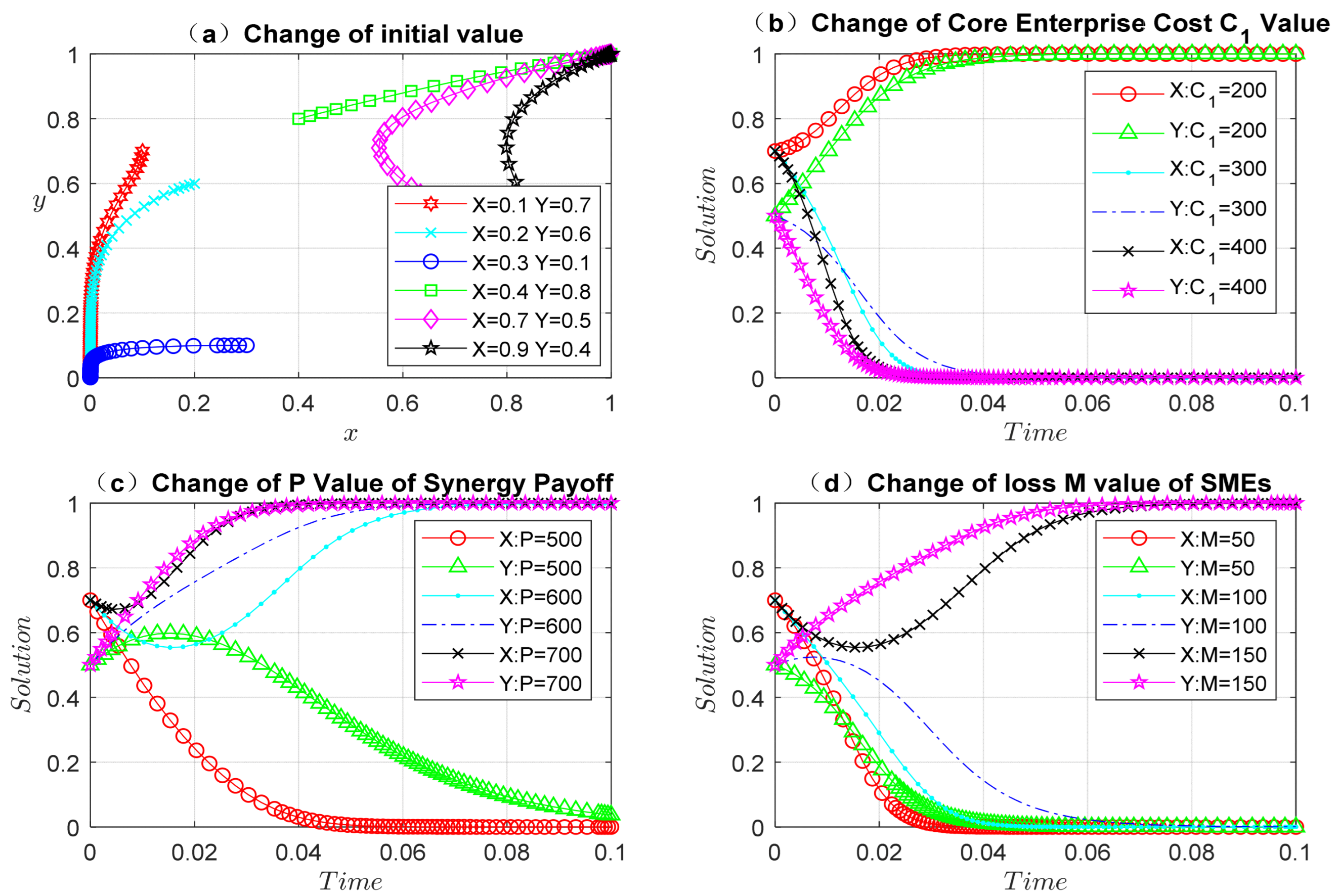
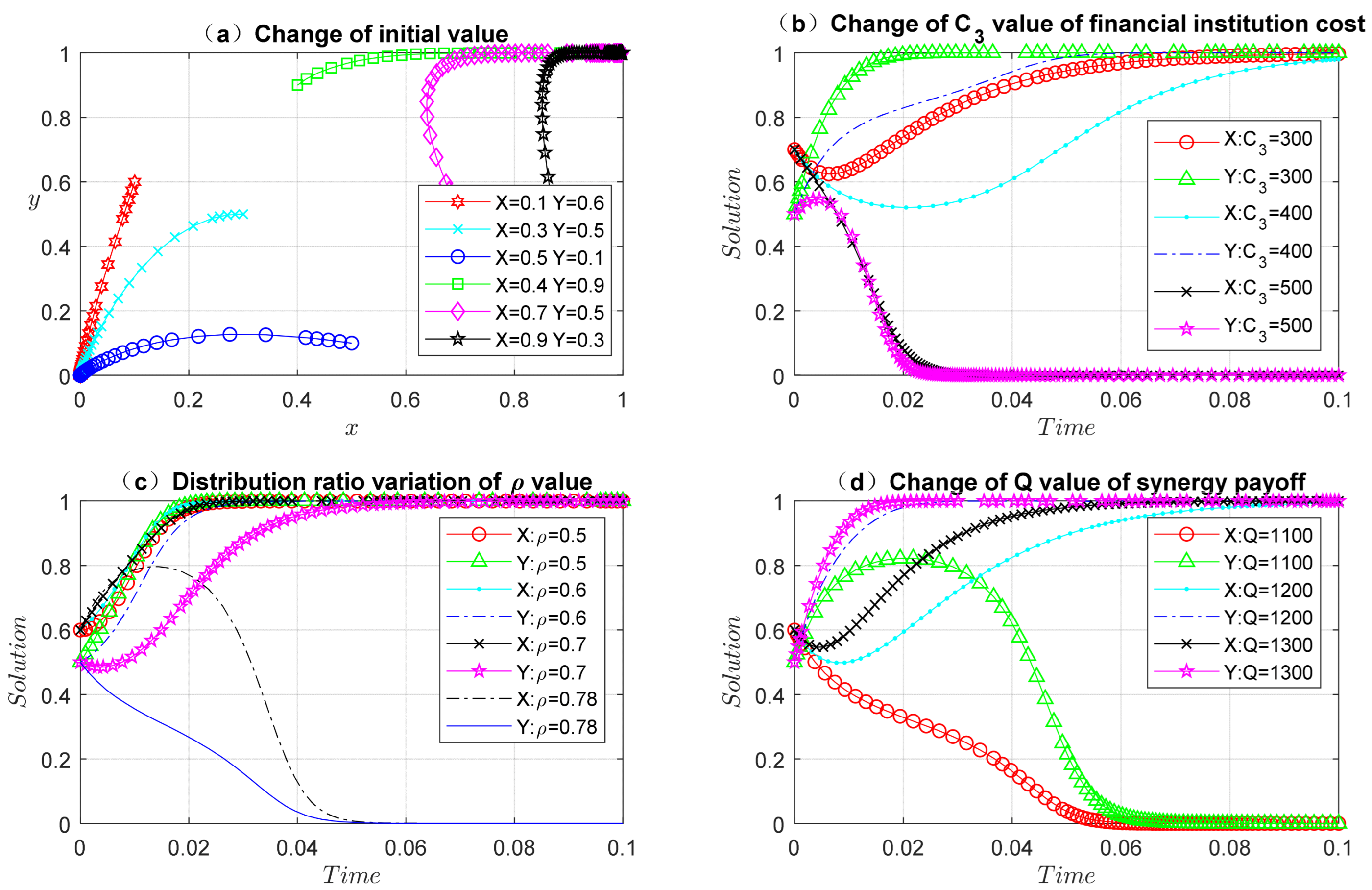
Proposition 1. (i) The higher the synergy payoff between core enterprises and SMEs, the more likely both parties will upload real data. The greater the influence of the core enterprises on the SMEs, the more the parties tend to upload real data. (ii) The higher the risk cost of uploading data by core enterprises and SMEs, the more likely they are to upload false data. (iii) The proportion of real data uploaded by both parties and the distribution of collaboration payoff present an inverted U-shaped result. With the increase in the proportion of collaboration payoff allocated to core enterprises, both parties tend to upload real data. When the proportion of the distribution exceeds a certain threshold, with an increasing proportion of the distribution, both parties tend to upload false data.
(The proof of Proposition 1 is shown in
Appendix A.)
It can be found from Proposition 1 that when the synergy payoff increases, the willingness of core enterprises and SMEs to share real data also increases. At the same time, the core enterprises have a strong influence on the SMEs, leading SMEs to adopt the action strategy of following the core enterprises. The risk costs of uploading data affect the authenticity of shared data. Only by taking various measures to reduce risk cost can the authenticity of shared data be effectively improved. The principle of “giving priority to efficiency and giving consideration to fairness” should be followed in the distribution of synergy payoff. Core enterprises play a greater role and should be appropriately inclined toward core enterprises when allocating synergy payoff. The reason is that the core enterprises have larger scale, more data, and greater influence in transactions. However, the principle of fairness should also be followed. When the interests of SMEs are seriously damaged, SMEs will take a non-cooperative attitude. Therefore, the principles of efficiency first and fairness at the same time should be taken into account in the distribution of synergy payoff.
3.3. Dynamic Game between Core Enterprises and Financial Institution under the Reward and Punishment Mechanisms in BSC
According to Proposition 1, SMEs adopt the action strategy of following the core enterprises. Therefore, the game between core enterprises and financial institutions becomes more important. If financial institutions can build a reasonable reward and punishment mechanism to encourage core enterprises to upload real data, SMEs will also upload real data, and the quality of shared data will improve.
(1) Model Hypotheses
Hypothesis 1: The main players in this part are the core enterprises and the financial institution , both of which are limited in their rationality. The strategy space of the core enterprises is = {upload real data, upload false data}. The probability that the core enterprise chooses action is , and the probability of choosing action is . The strategy space of the financial institutions is = {strict supervision, loose supervision}. The probability that the core enterprise chooses action is , and the probability of choosing action is .
Hypothesis 2: In BSC, core enterprises and financial institutions can obtain and in the initial state. Under the financial blockchain platform, the number of online data for core enterprises is . When financial institutions choose strict supervision, they can find out whether the data shared by the core enterprises are true. If the data for the core company are true, the financial institutions will reward the core company with the amount of . Suppose the online data for the core enterprises is false. In that case, the core enterprises will receive punishment . and are the reward and punishment coefficients of the core enterprises. Financial institutions will not be able to identify the authenticity of data when they choose loose regulation, so they will not reward and punish enterprises.
Hypothesis 3: Enterprises upload real data, which is risky. Assume that the risk cost of uploading real data from core enterprises is , which is proportional to the total amount of data on-line. Therefore, assume that , , and is the risk coefficient of core enterprises. When financial institutions adopt strict supervision, it will be more costly. Assuming that the cost of strict supervision is , and the cost of loose supervision is small, it is set to 0 for convenience. In reality, if data leaks, the core enterprises will suffer a heavy loss, which is much greater than the supervision cost of a financial institution, so it is assumed that .
Hypothesis 4: If financial institutions choose strict supervision and ultimately ensure that core enterprises upload real data, their achievements on the blockchain financial platform will be rewarded by the superior institutions with the amount of
, where γ is the reward coefficient given to the financial institution (
Table 6).
(2) Model Construction
From the above analysis, we can obtain the dynamic game payoff matrix between the core enterprises and financial institutions, as shown in
Table 7:
(3) Model analysis
Similar to the research method in
Section 3.2, the following conclusions can be drawn (see
Appendix A for a detailed derivation).
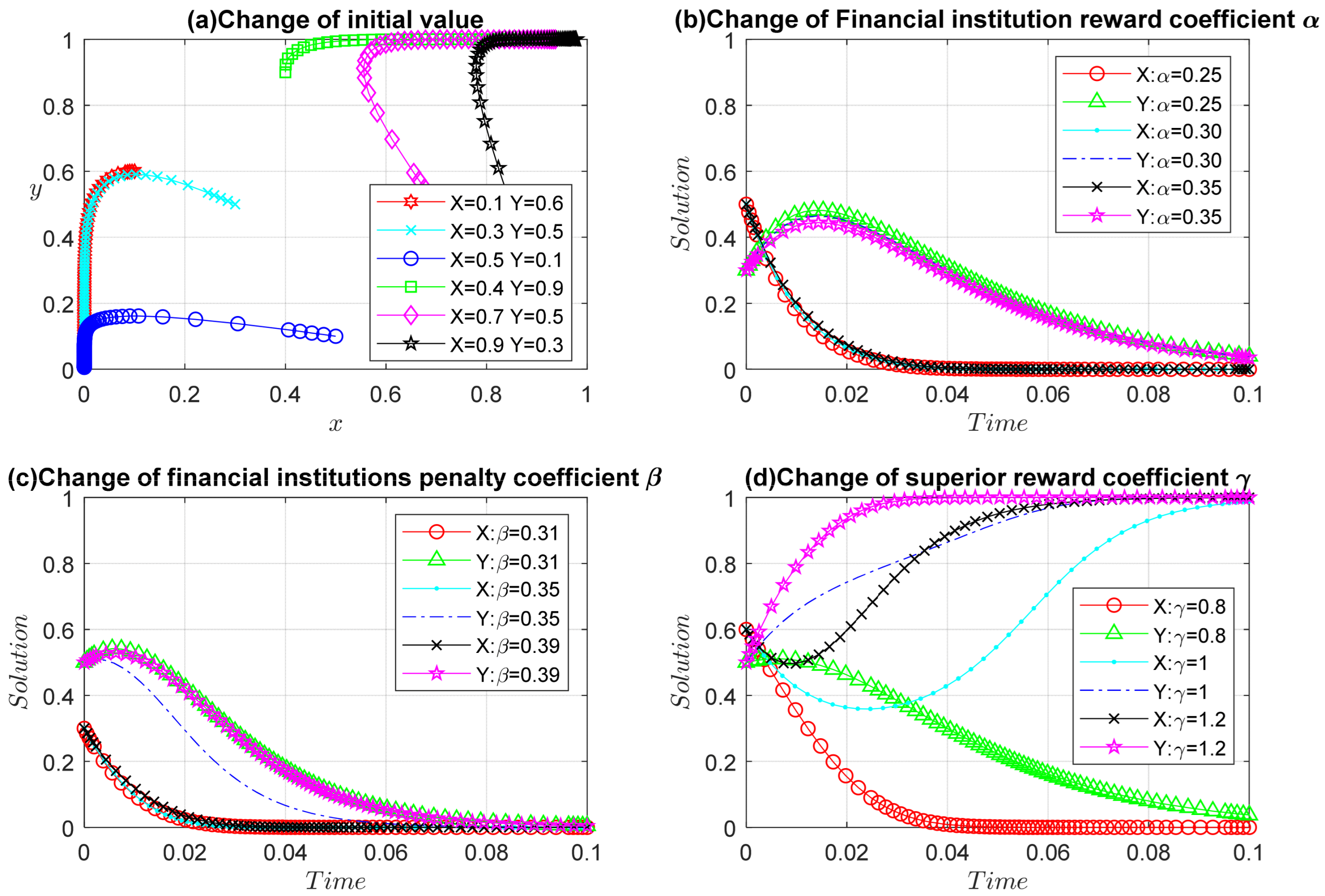
Proposition 2. (i) The more rewards the superior institution gives to financial institutions, the more financial institutions tend to be strictly supervised, and the core enterprises will choose to upload real data. (ii) The higher the risk cost of uploading data by the core enterprises, the more likely the core enterprises are to upload false data, and the financial institution chooses loose supervision. The higher the supervision cost of the financial institution, the more the financial institution tends to choose loose supervision, and the core enterprises will choose to upload false data.
(The proof of Proposition 2 is shown in
Appendix A.)
It can be seen from Proposition 2 that the more financial institutions attach importance to the development of the blockchain financial platform, the more support they give to financial institutions, and the more they can promote financial institutions to choose strict supervision so as to improve the quality of the online data of core enterprises. As SMEs follow the action strategy of core enterprises, they also choose to upload real data in the background of the attention of higher authorities, thus improving the data quality of the blockchain financial platform as a whole. The reasonable and effective use of blockchain and other technologies can effectively promote enterprises to upload real data by improving regulatory efficiency, ensuring the security of blockchain financial platform data, and reducing regulatory and risk costs. The formula of the partial derivative () is too complex to determine the symbol. We analyze it in the simulation part.
3.4. Dynamic Game between Core Enterprises and Financial Institutions under the Synergy Payoff Mechanism in BSC
This part focuses on building new paths and methods to improve the authenticity of enterprise online data. That is, core enterprises upload real data, and financial institutions choose strict supervision to bring synergy payoffs to core enterprises and financial institutions. Strict supervision of financial institutions improves online data quality and reduces financial risks caused by false data. At the same time, the higher the online data quality of the core enterprises, the more widely the blockchain will be promoted, and more enterprises will tend to use the blockchain financial platform. As enterprises upload more real data, it will promote transaction scale and generate higher profits. At the same time, the use of blockchain technology can improve transaction efficiency and reduce transaction costs. The application of blockchain technology benefits both financial institutions and enterprises. That is, the improvement of the quality of shared data will increase the synergy payoff, which will benefit both players.
This part of the model explains how the size and division of the synergy payoff affect the quality of the data on the blockchain financial platform. The hypotheses in this part are basically consistent with those in
Section 3.3. This part does not consider the reward or punishment of financial institutions for the core enterprises’ uplink data, nor the reward of superior institutions for financial institutions. Assuming that financial institutions are strictly supervised and core enterprises share real data, a synergy payoff
will be generated. The core enterprises and financial institutions obtain
, where
refers to the distribution proportion obtained by the core enterprises from the synergy payoff (
Table 8).
From the above analysis, we can obtain the dynamic game payoff matrix between the main enterprises and financial institutions, as shown in
Table 9. Similar to the research method in
Section 3.1, the following conclusions can be drawn (see
Appendix A for a detailed derivation).
Proposition 3. (i) The greater the synergy payoff created by financial institutions and core enterprises, the more financial institutions tend to be strictly supervised, and core enterprises will choose to upload real data. (ii) With the increase in the proportion of synergy payoff allocated to core enterprises, financial institutions tend to be strictly supervised, and core enterprises tend to upload real data. However, when the distribution ratio exceeds a certain threshold, with an increasing distribution ratio, financial institutions tend to loosen supervision, and core enterprises tend to upload false data.
(The proof of Proposition 3 is shown in
Appendix A.)
As seen in Proposition 3, the greater the synergy payoff created by financial institutions and core enterprises, the more it can promote financial institutions to choose strict supervision and core enterprises to choose to upload real data. As SMEs adopt the action strategy of following the core enterprises, improving the synergy payoff will improve the overall quality of shared data. Collaborating and sharing data between enterprises and financial institutions can effectively improve efficiency and promote sustainable development. Financial institutions should use blockchain technology to build a more powerful and complete financial platform that can not only ensure data security and reduce financial risks but also improve transaction scale and reduce transaction costs. The proportion of synergy payoff should be reasonably distributed to improve the enthusiasm of the core enterprises to upload real data. Financial institutions are service institutions, and core enterprises belong to the real economy. The proportion of synergy payoff should be appropriately inclined to core enterprises. In this way, core enterprises can be encouraged to upload real data and increase the scale of transactions. SMEs will follow the core enterprises’ strategy. At the same time, we should pay attention to the interests of financial institutions, rationally distribute the synergy payoff, and encourage financial institutions to serve the real economy better.
We use the three-party dynamic evolutionary game to analyze the reward and punishment mechanisms and the synergy payoff mechanism. We finally find that the conclusion is the same as Propositions 2 and 3. See
Appendix A for a detailed calculation and demonstration steps.