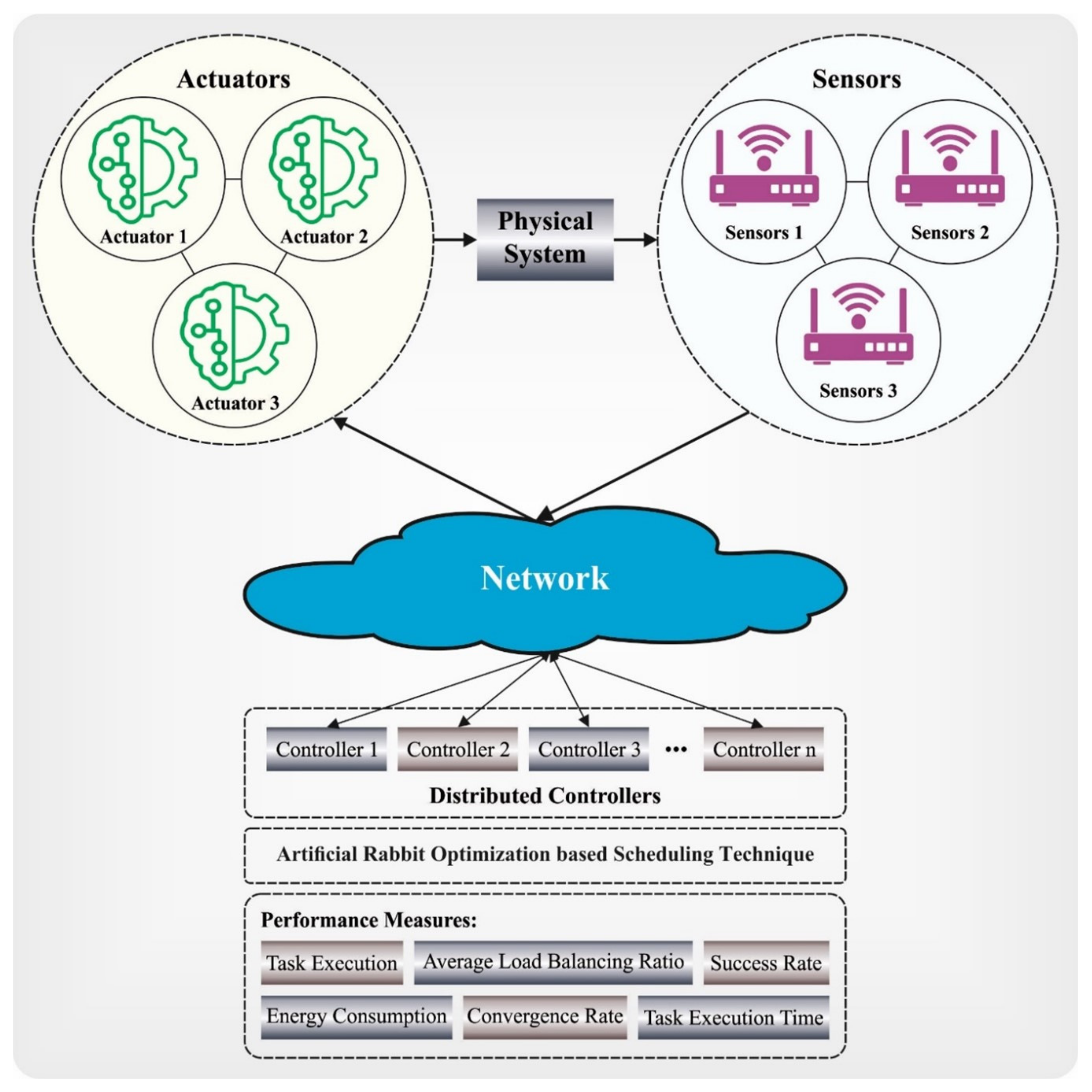
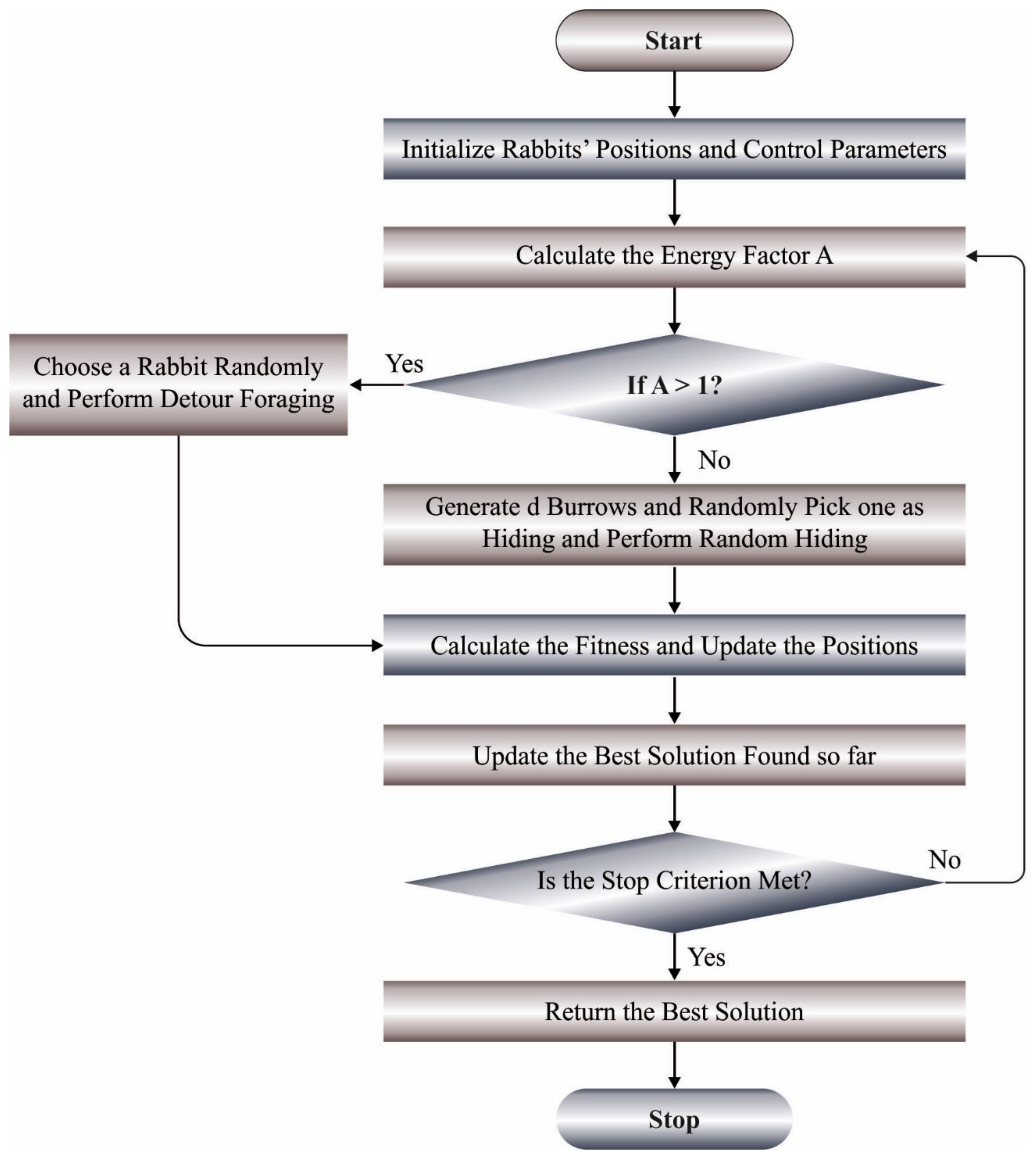
1. Introduction
Technological revolutions have intensely transformed customs within society, in which humans are irreversibly coupled with countless interlinked electronic gadgets and their cyber methods. This procedure is still ongoing, offering novel application scenarios and the continually arising novel scientific difficulties involved in the research fields of cyber-physical systems (CPS) and the Internet of Things (IoT) [
1]. The application scenarios involve the fields of manufacturing, assisted living, telerehabilitation, e-health, automotive and smart environments. Certainly, by utilizing these mechanisms, both industry and users obtain a wide range of advantages in relation to their requirements that involve performance enhancement, security, low cost, and comfort [
2]. The first and foremost objective is to enable users, machines, and applications to communicate and understand their surrounding atmosphere. By addressing the fundamental needs of users, such as communication, and mobility, water provisioning, and assistive monitoring, different communities (for instance embedded and intelligent) debate to support their views, technologies, and approaches [
3]. These solutions can typically be, inappropriately, technically based, while the actual requirements of the particular application domain and its users may be ignored.
CPS range from comparatively small mechanisms, such as automobiles and aircraft, to large mechanisms such as the national power grid [
4]. The physical features of these mechanisms will be regulated well by controllers by placing algorithms and computers into a loop; however, to attain the complete advantage of compiling CPS, power consumption, control, and computing can no longer be maximized distinctly [
5]. The dynamics of physical systems and the dynamics of computers communicate in ways that need basically novel design techniques. Principally, they involve mechanisms with distinct performances, hardware, and time limitations which have direct communication with the atmosphere, such as a transportation system, a control system, a robotic system, and many more [
6]. Each requirement arises from various kinds of applications; therefore, numerous types of scheduling systems are required.
A flexible scheduling policy that alters in accordance with different needs indicates a desideratum in many cases [
7]. Handling such complicated difficulties has led to the advancement of novel ideas and a novel class of models: the mixed criticality system [
8], which is “an embedded computing platform where application functions of various criticality share computation and or transmission resources” [
9]. In numerous cases, the safety and real-time needs should match the limited resources, minimum cost, and small power limitations, which raises the difficulty level in CPS cases. The method of utilizing mixed criticality scheduling in CPS was mostly application based, resulting in a variety of specific task methods having a multitude of system performance limitations [
10]. These techniques, while featuring higher real-world relevance, have inadequacies when it comes to interaction and scalability in an unpredictable atmosphere.
In this study, we propose a new artificial rabbit optimization enabled energy-efficient task-scheduling scheme (ARO-EETSS) for the CPS environment. The goal of the presented model is to allocate autonomous tasks to different resources, and thus the entire task completion period is minimized and resources totally exploited. To demonstrate the higher efficiency of the ARO-EETSS system, a sequence of simulations was performed. In summary, the paper’s contribution is given as follows.
Propose a new ARO-EETSS technique for scheduling tasks in the CPS environment. To the best of our knowledge, none of the existing task schedulers are based on the ARO algorithm and the ARO-EETSS technique does not exist in the literature.
Derive a task scheduler to assign autonomous tasks to different resources.
Validate the performance of the ARO-EETSS technique under different aspects.
2. Related Works
In [
11], the authors modelled an energy-aware CPS (E-CPS) for Big Data analysis and recessive construction anomaly detection. The proposed model included a data association and data reduction study, which was devised for examining manufactured data in E-CPS. An energy Big Data-driven recessive production anomaly study technique was devised on the basis of DBN by consideration of the dynamics and complexity of the manufacturing procedure. In [
12], the authors initially developed the mobile CPS (MCPS) security maximized issue as a mixed integer nonlinear programming (MINLP) issue and next converted it as an MILP issue without efficiency degradations. To resolve the converted MILP issue proficiently, the researchers suggested a decomposed technique for deriving the optimal task scheduling (TS) solution as an alternative utilizing MILP resolvers that might be time-consuming for MCPS of huge granularity.
Energy-aware and service-level agreements (SLAs) determining the job schedule structure based on MapReduce were proposed in [
13]. The main objective of this modelled structure was to sightsee task-to-slot or container map issues as a unique case of energy-aware scheduling from deadline-limited cases. Therefore, this complexity was extracted as a complicated multi-objective issue that has various limitations. For solving this issue proficiently, it was divided into three sub-problems (SPs), such as deadline segregation, mapping, and minimizing stage energy-aware scheduling. In [
14], the researchers studied the issue of TS in a heterogeneous multi-processor mechanism on chip (MPSoC) positioned in the IoT to optimize the security quality in energy, real-time, and task-precedence limitations. The authors initially offered an MILP design to schedule and allocate reliant on tasks having energy and real-time limitations on the heterogeneous MPSoC mechanism for maximizing security quality.
Tang et al. [
15] presented an effectual scheduling technique that gratified cost and functional reliability limitations in multi-functional mixed-criticality task replication executing cases. Utilizing the modelled fault-tolerant hardware cost-aware multi-functional safety assurance (FT_HCMSA) technique could minimize DMR of higher criticality purpose suggestively when meeting the automotive functional security. Hossain et al. [
16] presented an energy-aware CPS therapy mechanism (T-CPS) that inculcated smart gadgets and things in both the cyber and physical worlds for a therapy system. In [
17], the authors recommended an energy aware meta-heuristic technique related to a Harris Hawks optimized technique related to local search strategy (HHOLS) for TS in fog computing (FC) (TSFC) for enhancing the quality of service offered to users from Industrial-Internet-of-Things (IIoT) applications. Firstly, the authors explained the higher virtual layered FC method considering its varied structure. The scaling and normalization stage helped the HHO to solve the TSFC, which would be discrete.
Ghobaei-Arani et al. [
18] examined a TS technique dependent upon the moth-flame optimized (MFO) technique for assigning a better group of tasks to fog node for meeting the approval of the service quality requirements of CPS applications so that the entire execution time of tasks is minimized. The minimized task execution and transmission time in the presented technique were assumed the main functions. In [
19], the authors examined energy-efficient and contention-aware static TS with priority and deadline constraints on intelligent edge devices utilizing heterogeneous VFI-based NoC-MPSoCs (VFI-NoC-HMPSoC) with DVFS-enabled processors. Different from the existing population-based optimized systems, the authors presented a new population-based technique named ARSH-FATI which is dynamically switched betwixt exploitative and explorative searching modes at run-time. Xu et al. [
20] defined a new method for reducing thermally induced damage from CPS processors by targeting dynamic voltage and frequency scaling (DVFS) to high activity task stages. Specifically, by preferably slowing down high activity task stages, major extra savings in energy and thermal stress were obtained to provide a count of computational slowdowns; this method demonstrated that higher than typical approaches utilize DVFS without regard to activity level.
4. Results and Discussion
This section assesses the TS performance of the ARO-EETSS model in the CPS environment. The proposed model was simulated using MATLAB tool.
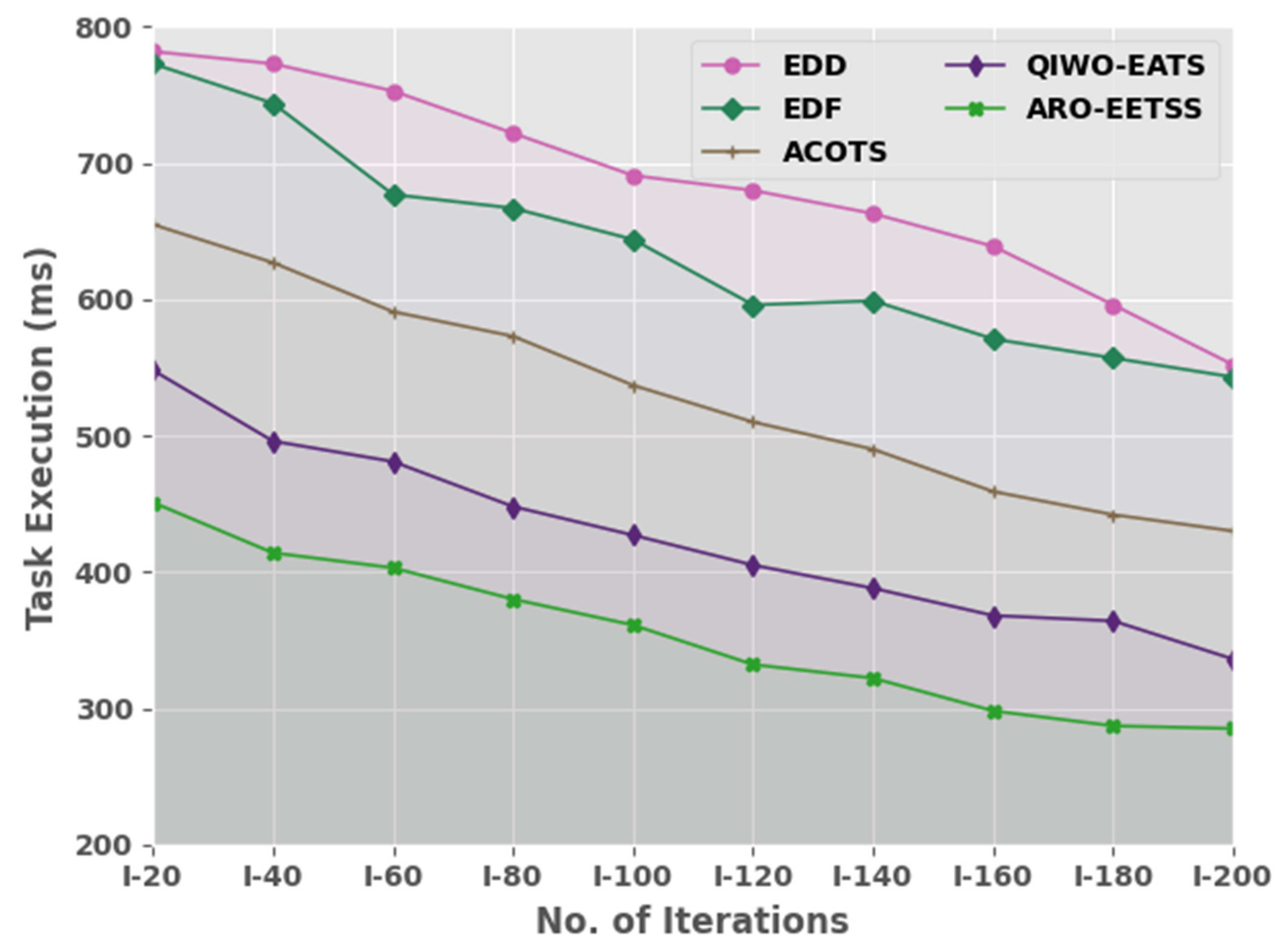
Table 1 and
Figure 3 compare the task execution time (TET) examination of the ARO-EETSS method with current approaches such as earliest due date (EDD), earliest deadline first (EDF), ant colony optimization-based task scheduler (ACOTS), and quantum invasive weed optimization-based energy-aware scheduling (QIWO-EATS) [
4]. The experimental values suggested the ARO-EETSS method reached least TET values under all iterations. For instance, on I-20 iterations, the ARO-EETSS model showed the lowest TET of 451 ms whereas the EDD, EDF, ACOTS, and QIWO-EATS models demonstrated higher TETs of 782, 773, 655, and 548 ms, respectively. Along with that, on I-100 iterations, the ARO-EETSS method displayed the lowest TET of 361 ms where the EDD, EDF, ACOTS, and QIWO-EATS methods showed increased TETs of 691, 644, 537, and 427 ms, correspondingly.
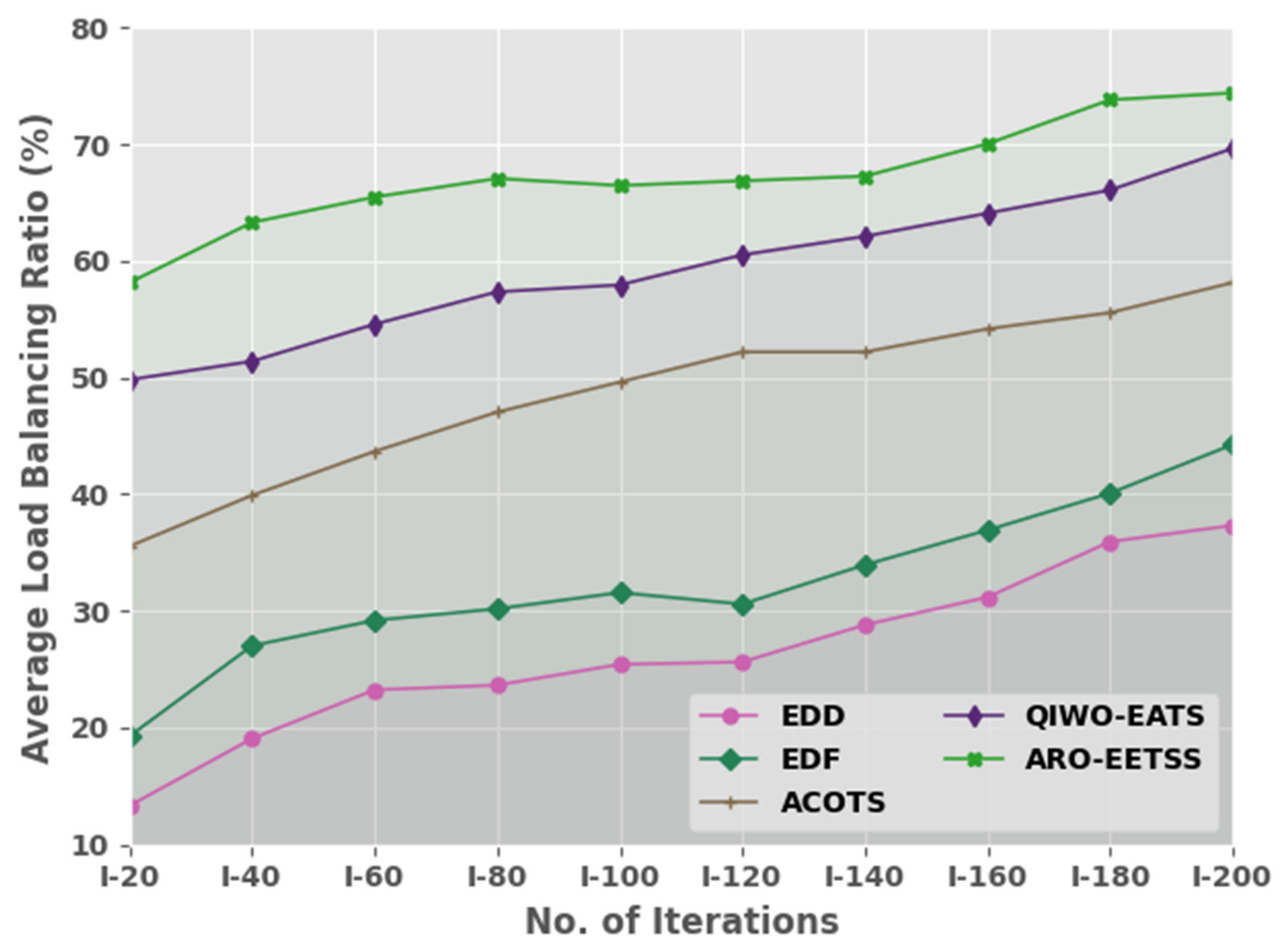
An average load balancing ratio (ALBR) of the ARO-EETSS method with current methodologies is investigated in
Table 2 and
Figure 4. The outcomes denoted the ARO-EETSS method gained improved outcomes in all iterations. For example, on I-20 iterations, the ARO-EETSS method offered a maximum ALBR of 58.16% whereas the EDD, EDF, ACOTS, and QIWO-EATS models depicted higher ALBRs of 13.32, 19.27, 35.54, and 49.83% respectively. In addition, on I-100 iterations, the ARO-EETSS method presented a maximum ALBR of 66.49% whereas the EDD, EDF, ACOTS, and QIWO-EATS methods portrayed higher ALBRs of 25.42, 31.57, 49.63, and 57.96%, correspondingly.
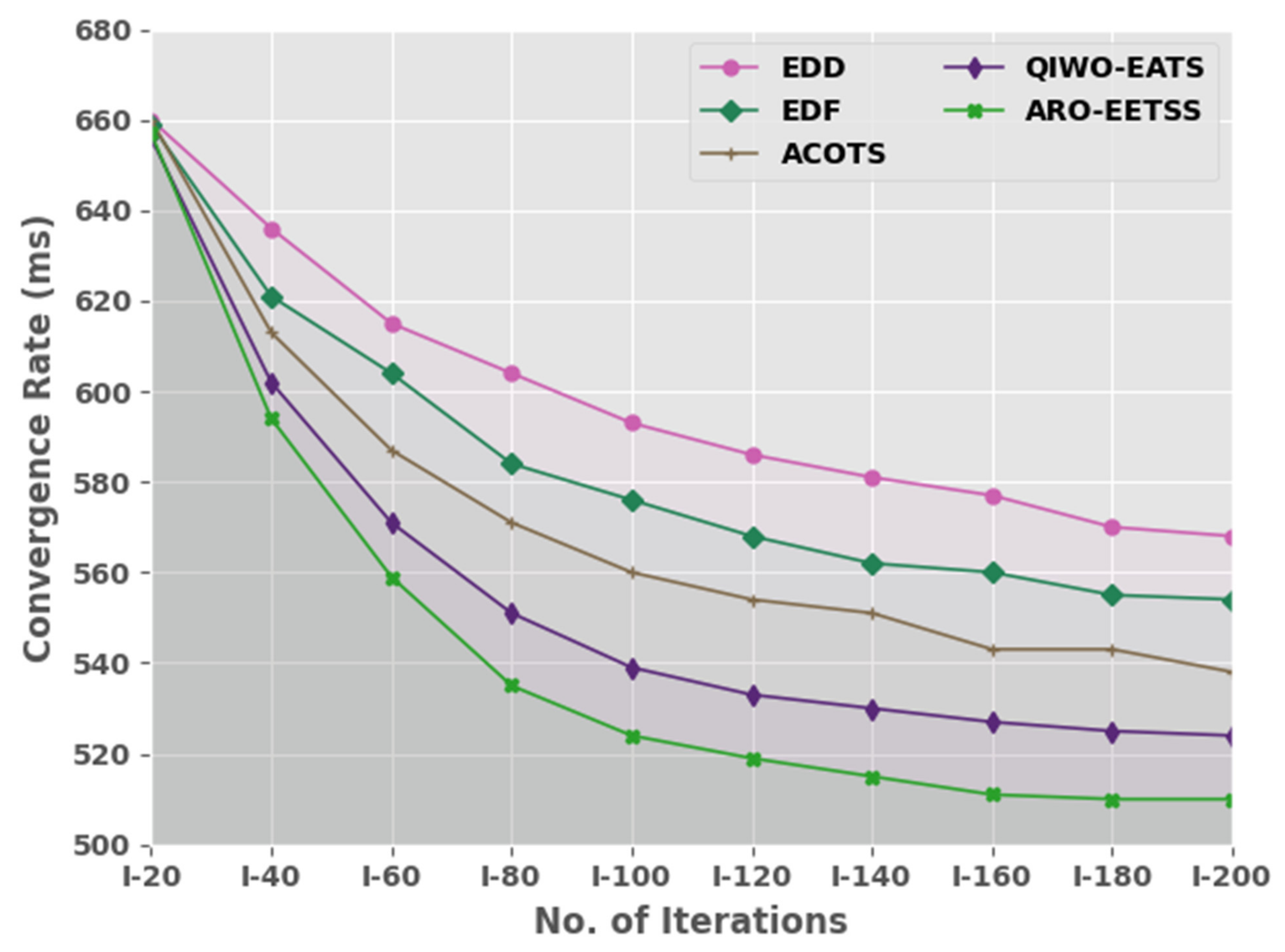
Table 3 and
Figure 5 compare the task convergence rate (CR) inspection of the ARO-EETSS method with recent methods. The experimental values denoted by the ARO-EETSS method reached lowest CR values under all iterations. For example, on I-20 iterations, the ARO-EETSS approach displayed a minimal CR of 657 ms whereas the EDD, EDF, ACOTS, and QIWO-EATS methods demonstrated increased CRs of 660, 659, 660, and 656 ms, correspondingly. Similarly, on I-100 iterations, the ARO-EETSS method exhibited the lowest CR of 524 ms whereas the EDD, EDF, ACOTS, and QIWO-EATS methods demonstrated increased CRs of 593, 576, 560, and 539 ms, correspondingly.
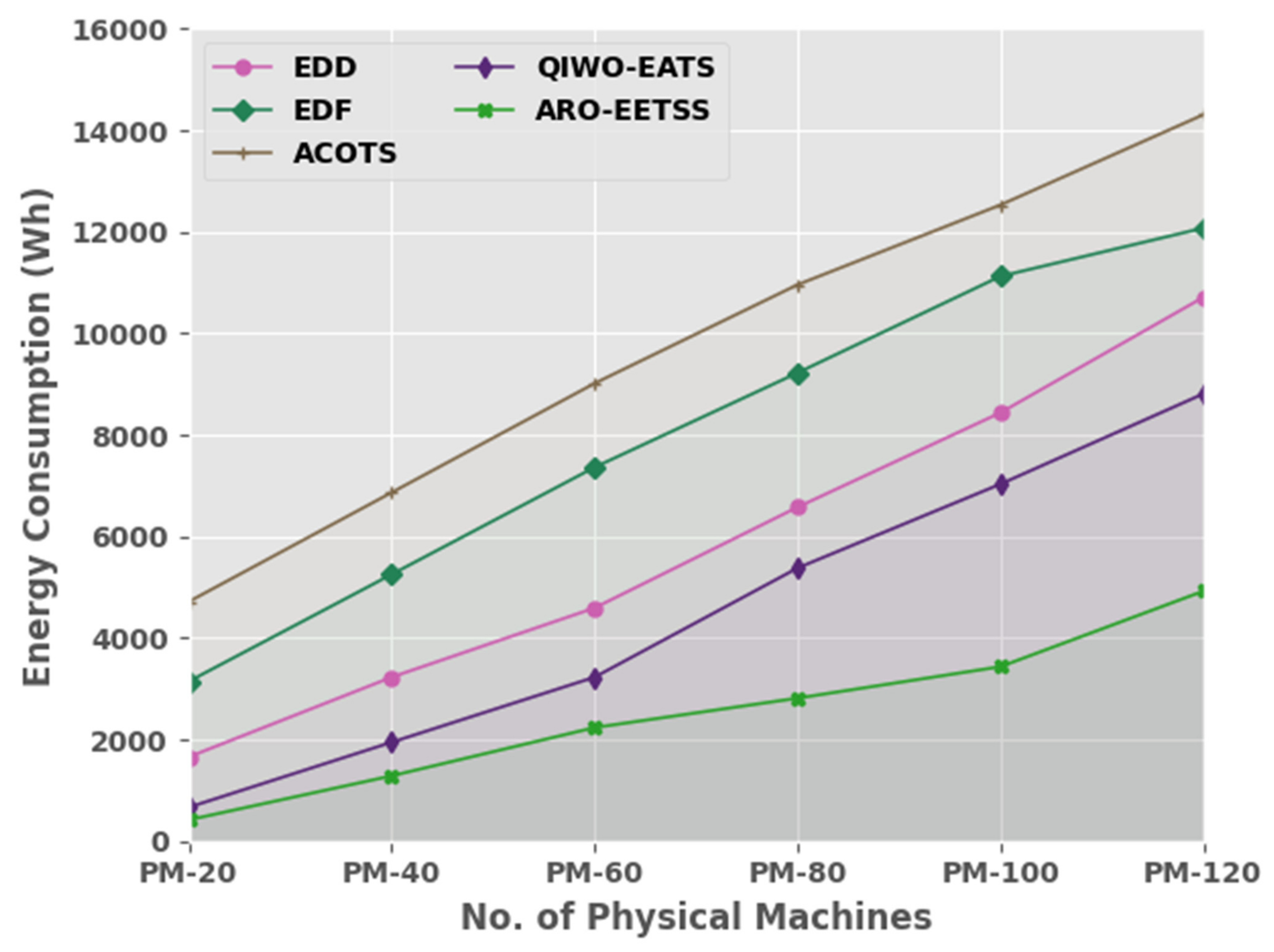
Table 4 and
Figure 6 compare the task energy consumption (ECON) inspection of ARO-EETSS method with recent methods. The experimental values denoted by the ARO-EETSS approach reached the least ECON values under all iterations. For example, on PM20, the ARO-EETSS technique showed a reduced ECON of 417 Wh whereas the EDD, EDF, ACOTS, and QIWO-EATS approaches illustrated higher ECONs of 1657, 3146, 4717, and 665 Wh, correspondingly. Moreover, on PM-100, the ARO-EETSS method exemplified a reduced ECON of 3435 Wh, for which the EDD, EDF, ACOTS, and QIWO-EATS methods demonstrated higher ECONs of 8439, 11,127, 12,533, and 7033 Wh, correspondingly.
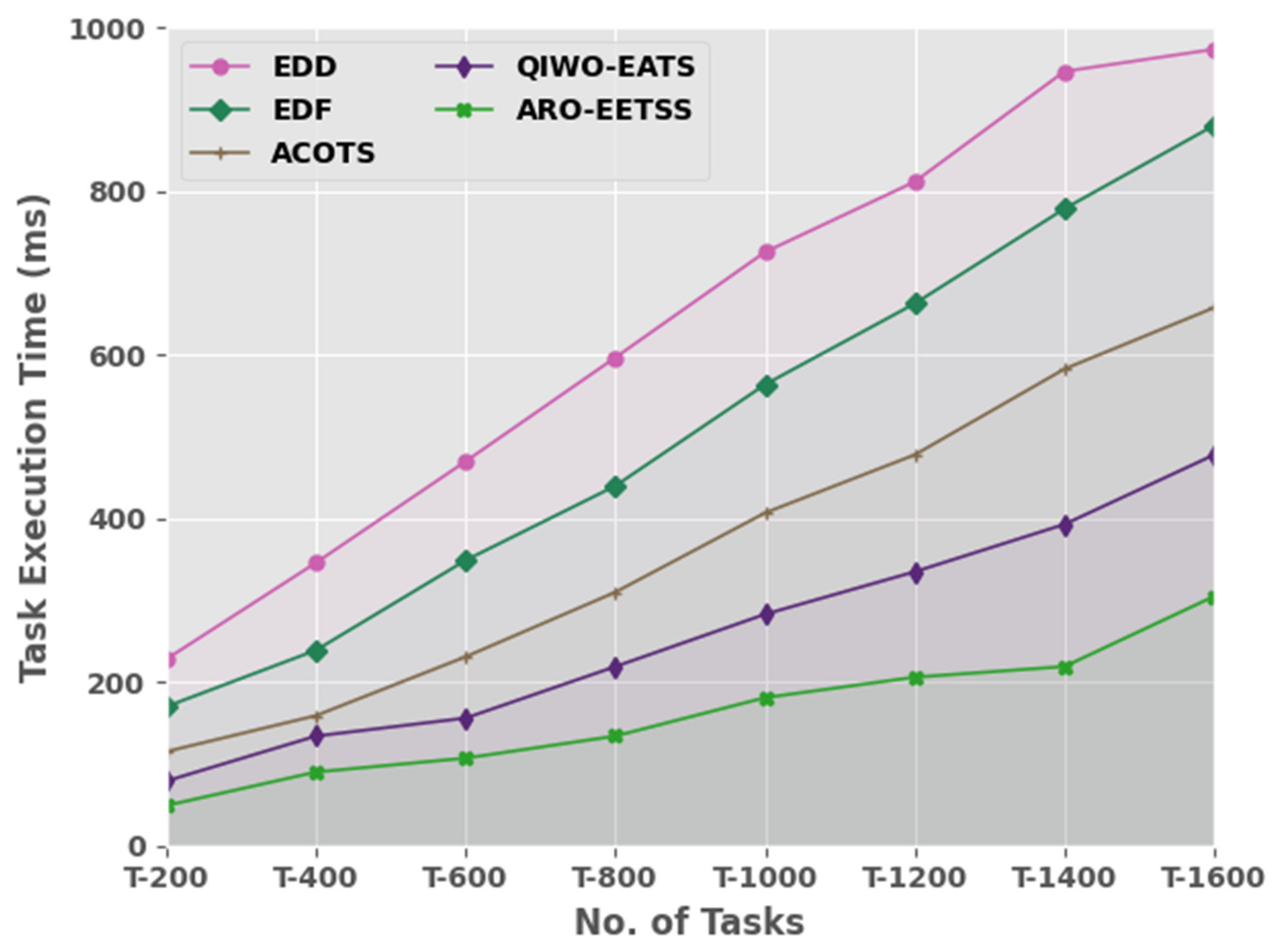
Table 5 and
Figure 7 compare the TET inspection of the ARO-EETSS method with recent methods. The experimental values denoted by the ARO-EETSS approach reached the lowest TET values under all iterations. For example, on T-200 tasks, the ARO-EETSS technique displayed a minimal TET of 49 ms, whereas the EDD, EDF, ACOTS, and QIWO-EATS models demonstrated higher TETs of 228, 170, 115, and 79 ms, correspondingly. Further, on T-1000 tasks, the ARO-EETSS method showed a reduced TET of 181 ms but the EDD, EDF, ACOTS, and QIWO-EATS methods established increased TETs of 726, 564, 407, and 283 ms, correspondingly.
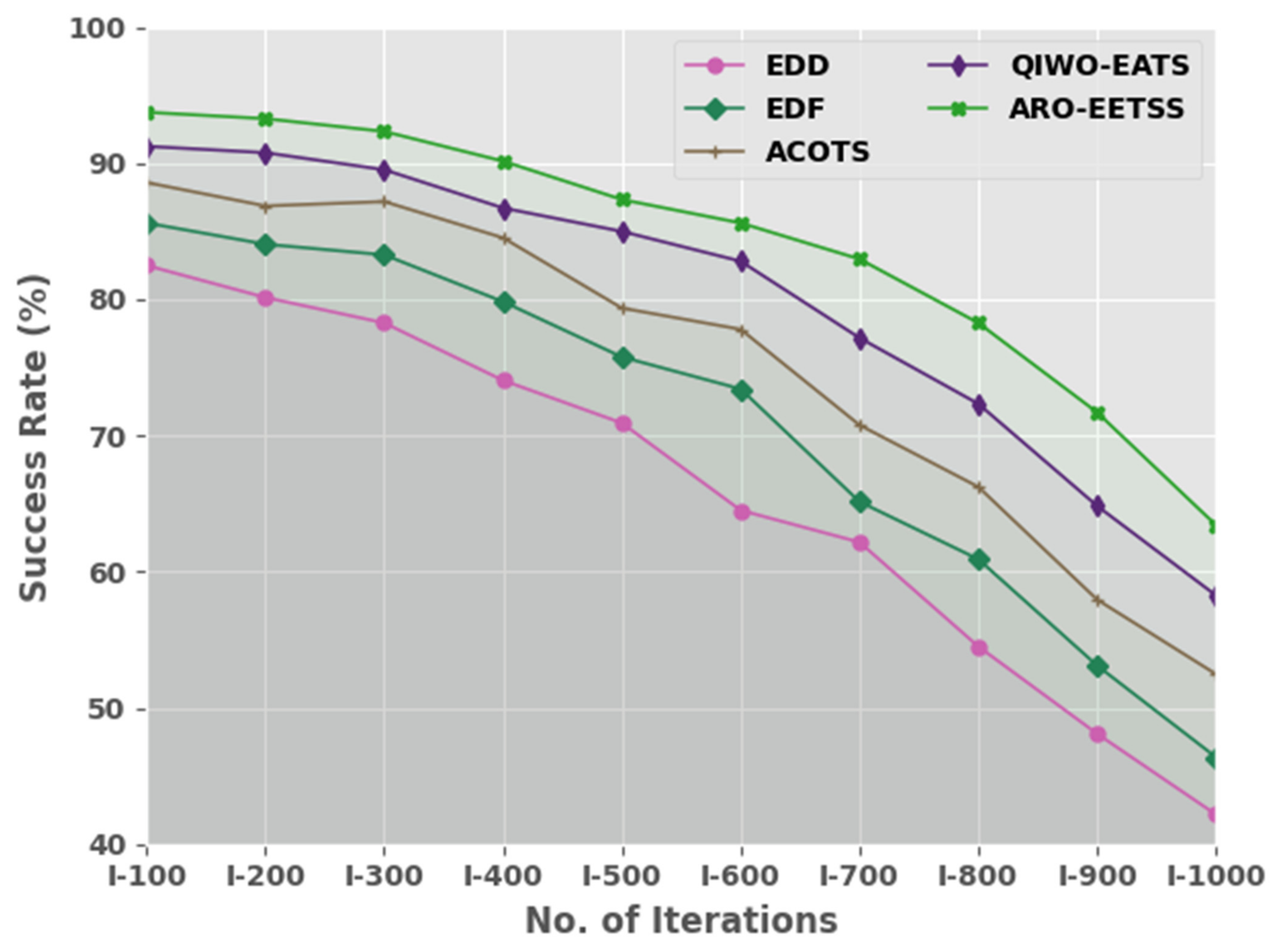
The success rate (SR) of the ARO-EETSS method against recent models is shown in
Table 6 and
Figure 8. The outcomes denoted that the ARO-EETSS approach obtained improved outcomes in every iteration. For example, on I-100 iterations, the ARO-EETSS method offered a maximum SR of 93.73%, where the EDD, EDF, ACOTS, and QIWO-EATS approaches showed maximum SRs of 82.48, 85.60, 88.57, and 91.23%, correspondingly.
Furthermore, on I-500 iterations, the ARO-EETSS method presented a maximum SR of 87.32%, whereas the EDD, EDF, ACOTS, and QIWO-EATS methods gave SRs of 70.91, 75.76, 79.35, and 84.98%, correspondingly. These results show that the presented method has enhanced performance over other existing methods.
5. Conclusions
In this article, a novel ARO-EETSS system was introduced for TS from the CPS environment. The presented ARO-EETSS system depends upon the existing natural practices of rabbits, encompassing detour foraging and random hiding. In the presented ARO-EETSS technique, the TS process was carried out via the allocation of autonomous tasks to dissimilar resources, and thus the entire task completion period was minimized and resources were totally exploited. To demonstrate the higher efficiency of the ARO-EETSS system, a sequence of experiments was performed. The comparison study underlined the higher performance of the ARO-EETSS technique with respect to several measures.
In future, the outcomes of ARO-EETSS system will be improved by the use of hybrid metaheuristic optimization algorithms. Furthermore, in future, data deduplication mechanisms can be designed to improve network efficiency. Though adequate discussions and assessments have already been made in this work, some future work is discussed here. Flexible and dynamic TS can improve the schedulability of the CPS environment by the use of statistical learning techniques for supervision and cloud computing facilities for adaptively managing resource reclamation. In addition, a scheduler that better matches the dual-period model also deserves to be explored. An accurate timing analysis will be utilized for the effective analysis of resource utilization. Moreover, a real-world case study would provide stronger support for the usability of the framework. To transform the proposed method into a real-world application, some details related to software development, kernel modification, and communication with the cloud need to be formalized in future.