Sustainability Model for the Internet of Health Things (IoHT) Using Reinforcement Learning with Mobile Edge Secured Services
Abstract
1. Introduction
- It employs a reinforcement learning technique to explore QoS and assist green computing technologies;
- It achieves an intelligent methodology based on global optimal solutions for IoHT-based systems and offers effective resource usage with edge computing;
- In addition, it secures the cloud environment by providing encryption and integrity verifications to enhance the consistency of massive amounts of data. The proposed model is compared to existing work in terms of energy- and security-related indicators.
2. Related Work
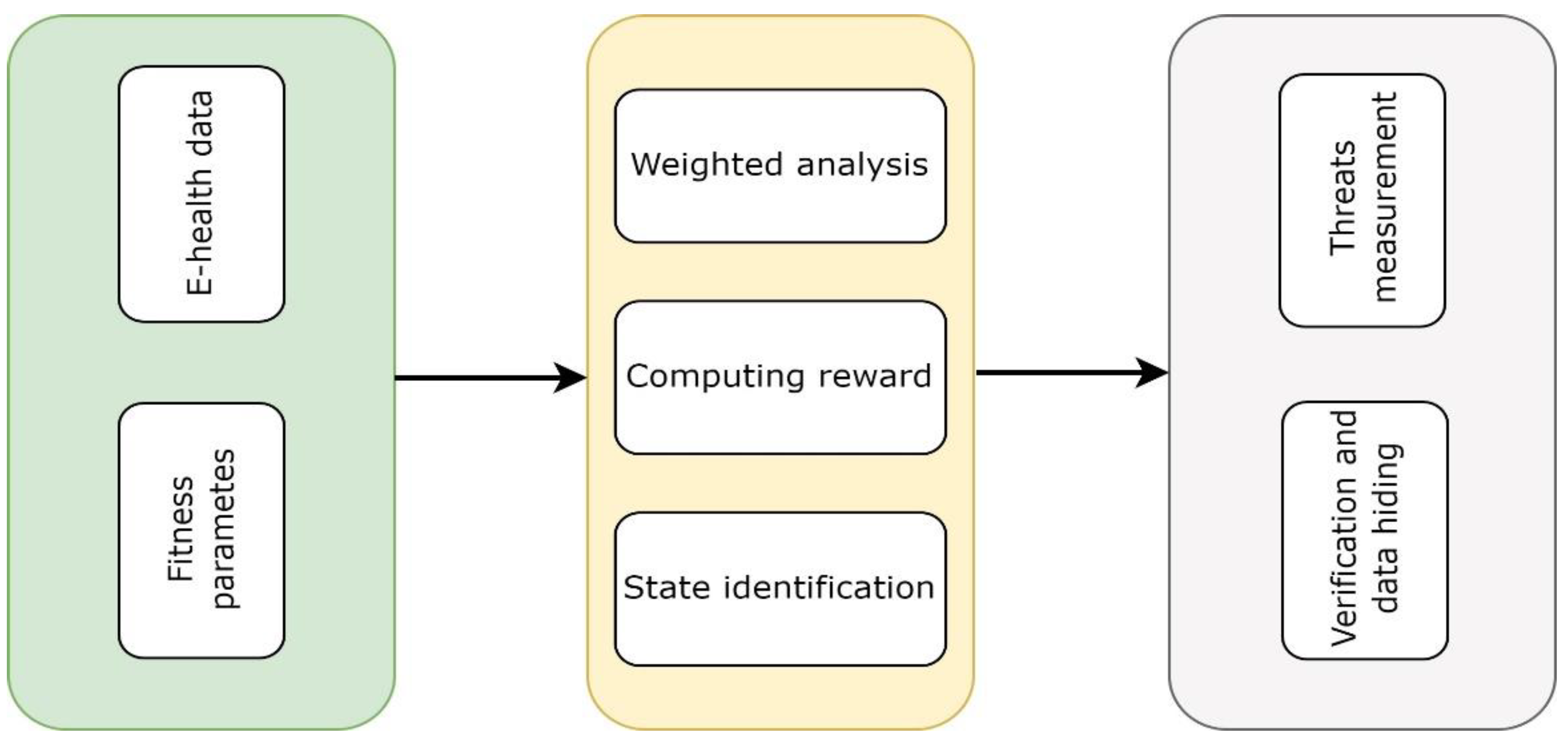
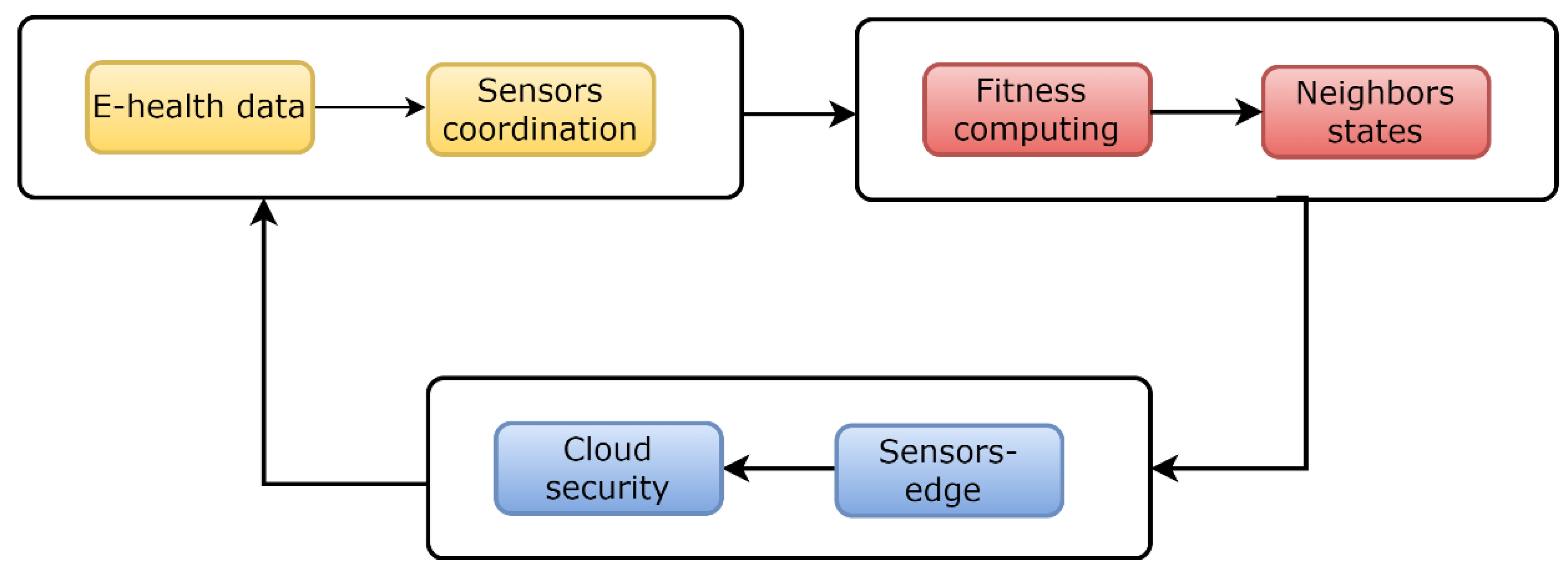
3. Exploring Machine Learning-Enabled Mobile Edge Computing Model with Secured Sustainable IoHT
3.1. Network Model and Assumptions
- The visual sensors have limited resources and are immobile;
- The sink node has no limited resources and is rotated around the edge boundary;
- IoT data can only be received to sink nodes using the edge boundary;
- Malicious nodes can generate false information and compromise the communication system;
- Each node has enough memory to store its neighbor’s information.
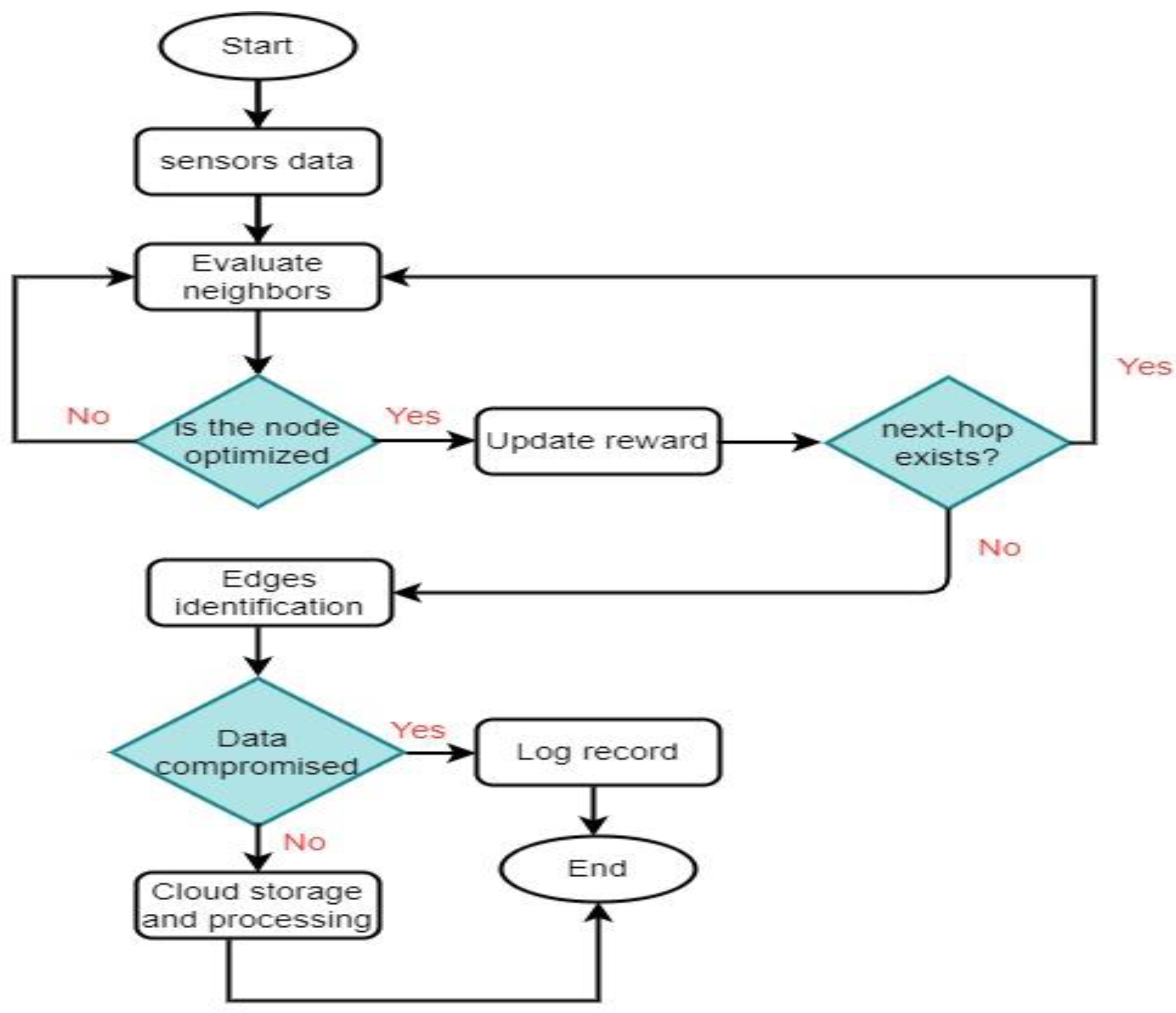
3.2. Proposal
3.3. Discussion
| Algorithm 1: Sustainable model using machine learning with secured data connections |
| 1. procedure network registration (R) //nodes and devices declaration |
| 2. devices initialization and sensing |
| 3. fitness parameters |
| 4. foreach (neighbors) do //weighted function with network metrics |
| 5. determine the weighted fitness |
| 6. α++ γ ∗ 1/ |
| 7. end for |
| 8. if of node i is maximum then //assigned rewards |
| 9. execute reward function R |
| 10. end if |
| 11. foreach (selected forwarder j) do //nodes-edges connection |
| 12. collaborate with edges in multi-hop paradigm |
| 13. end for |
| 14. end procedure |
| 15. procedure connections_secured //end-to-end secured connections |
| 16. share the identities and secret keys |
| 17. each forwarder validates its identity on the edges |
| 18. if identity is acceptable then |
| 19. call CBC for data chaining |
| 20. end if |
| 21. foreach (blocks) do |
| 22. verified its integrity |
| 23. end for |
| 24. end procedure |
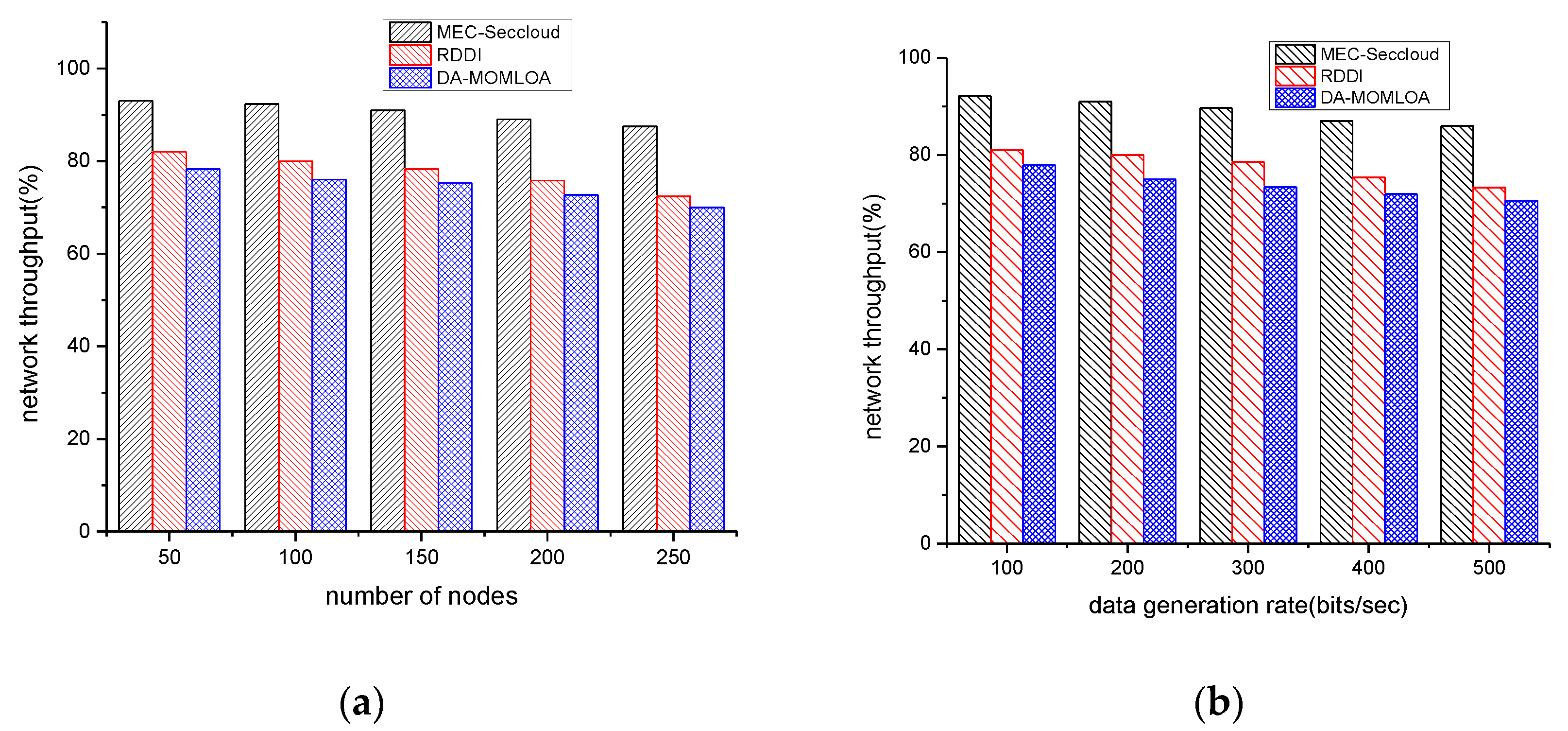
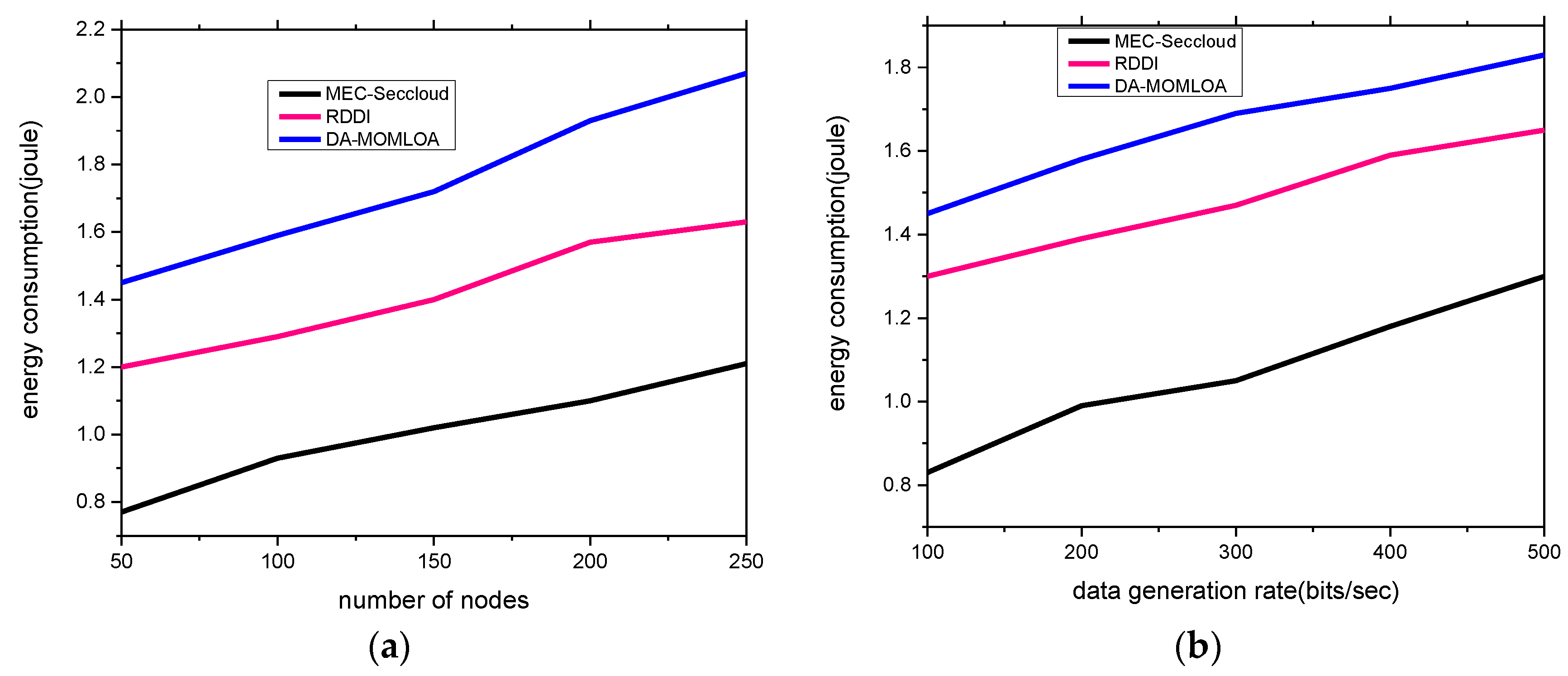
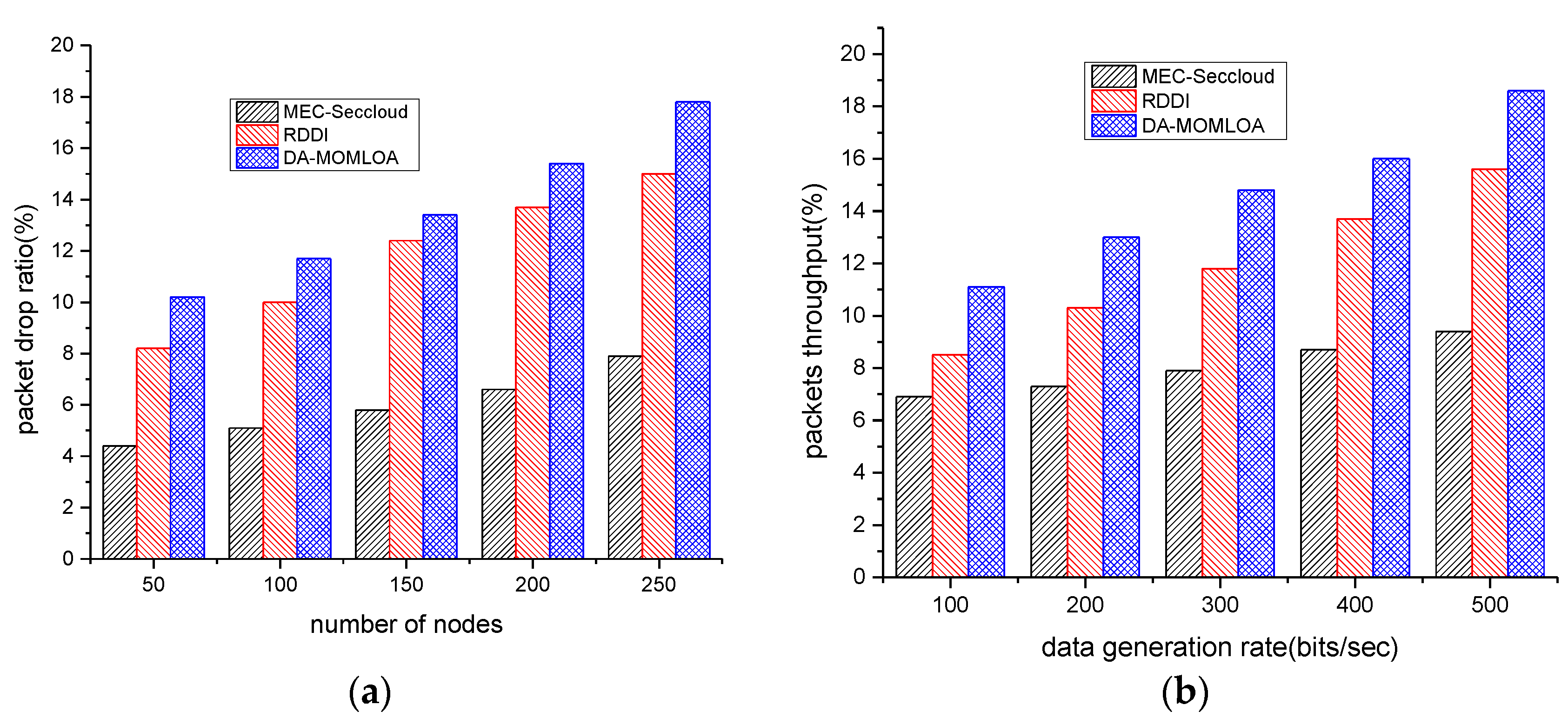
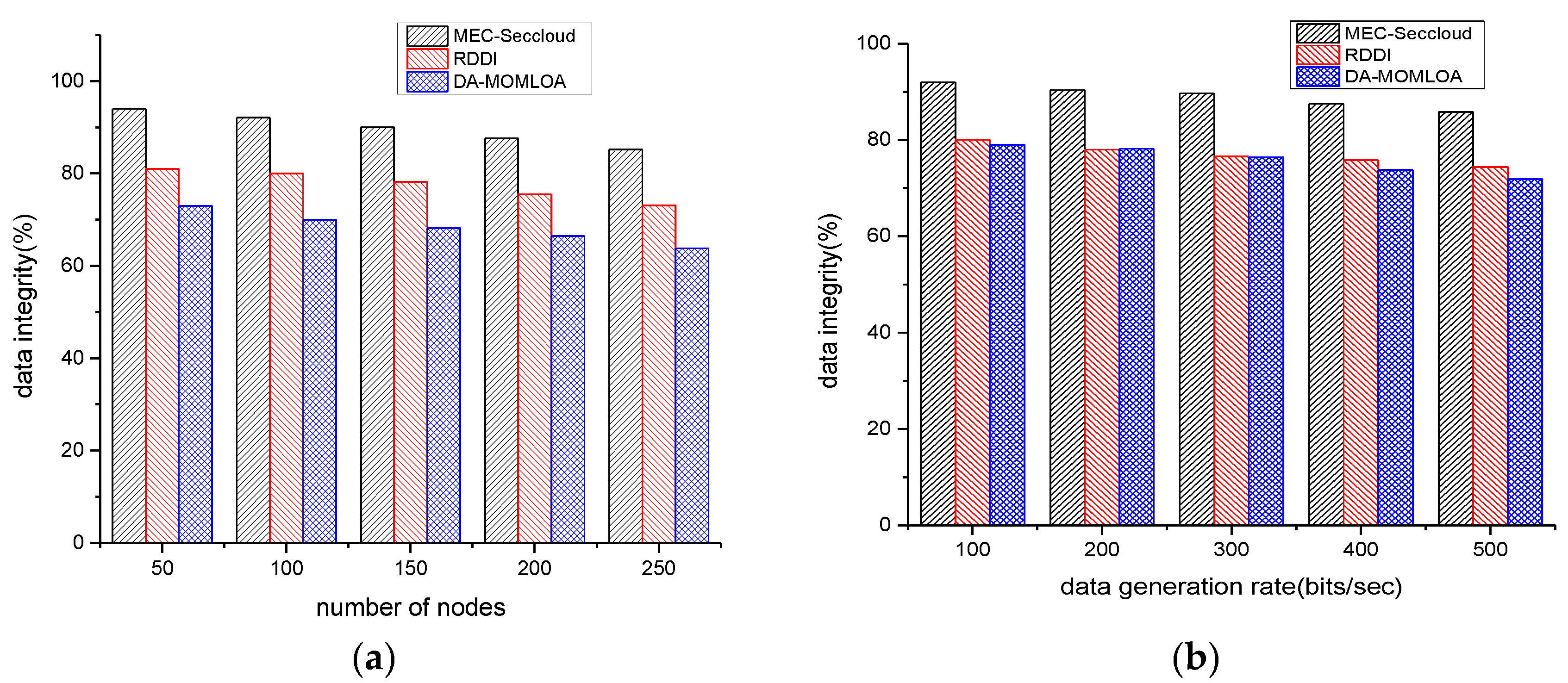
4. Simulations
Comparison with Existing Schemes
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Sara, G.S.; Sridharan, D. Routing in mobile wireless sensor network: A survey. Telecommun. Syst. 2014, 57, 51–79. [Google Scholar] [CrossRef]
- Keswani, B.; Mohapatra, A.G.; Mohanty, A.; Khanna, A.; Rodrigues, J.J.; Gupta, D.; de Albuquerque, V.H.C. Adapting weather conditions based IoT enabled smart irrigation technique in precision agriculture mechanisms. Neural Comput. Appl. 2019, 31, 277–292. [Google Scholar] [CrossRef]
- Lloret, J.; Parra, L.; Taha, M.; Tomás, J. An architecture and protocol for smart continuous eHealth monitoring using 5G. Comput. Netw. 2017, 129, 340–351. [Google Scholar] [CrossRef]
- Yuan, J.; Zhang, J.; Ding, S.; Dong, X. Cooperative localization for disconnected sensor networks and a mobile robot in friendly environments. Inf. Fusion 2017, 37, 22–36. [Google Scholar] [CrossRef]
- Nazir, S.; Ali, Y.; Ullah, N.; García-Magariño, I. Internet of things for healthcare using effects of mobile computing: A systematic literature review. Wirel. Commun. Mob. Comput. 2019, 2019, 5931315. [Google Scholar] [CrossRef]
- Acar, M.; Kaya, O. A healthcare network design model with mobile hospitals for disaster preparedness: A case study for Istanbul earthquake. Transp. Res. Part E Logist. Transp. Rev. 2019, 130, 273–292. [Google Scholar] [CrossRef]
- Mishra, S.; Mishra, B.K.; Tripathy, H.K.; Dutta, A. Analysis of the role and scope of big data analytics with IoT in health care domain. In Handbook of Data Science Approaches for Biomedical Engineering; Academic Press: Cambridge, MA, USA, 2020; pp. 1–23. [Google Scholar]
- Alshehri, F.; Muhammad, G. A comprehensive survey of the Internet of Things (IoT) and AI-based smart healthcare. IEEE Access 2020, 9, 3660–3678. [Google Scholar] [CrossRef]
- Rehman, A.; Haseeb, K.; Fati, S.M.; Lloret, J.; Peñalver, L. Reliable Bidirectional Data Transfer Approach for the Internet of Secured Medical Things Using ZigBee Wireless Network. Appl. Sci. 2021, 11, 9947. [Google Scholar] [CrossRef]
- Bhushan, B.; Sahoo, G. Requirements, protocols, and security challenges in wireless sensor networks: An industrial perspective. In Handbook of Computer Networks and Cyber Security; Springer: Cham, Switzerland, 2020; pp. 683–713. [Google Scholar] [CrossRef]
- El-Fouly, F.H.; Ramadan, R.A. E3AF: Energy efficient environment-aware fusion based reliable routing in wireless sensor networks. IEEE Access 2020, 8, 112145–112159. [Google Scholar] [CrossRef]
- Rehman, A.; Saba, T.; Haseeb, K.; Larabi Marie-Sainte, S.; Lloret, J. Energy-Efficient IoT e-Health Using Artificial Intelligence Model with Homomorphic Secret Sharing. Energies 2021, 14, 6414. [Google Scholar] [CrossRef]
- Mahajan, H.B.; Rashid, A.S.; Junnarkar, A.A.; Uke, N.; Deshpande, S.D.; Futane, P.R.; Alkhayyat, A.; Alhayani, B. Integration of Healthcare 4.0 and blockchain into secure cloud-based electronic health records systems. Appl. Nanosci. 2022, 1–14. [Google Scholar] [CrossRef]
- Zhou, M.; Hassan, M.M.; Goscinski, A. Emerging Edge-of-Things Computing for Smart Cities: Recent Advances and Future Trends; Elsevier: Amsterdam, The Netherlands, 2022; Volume 600, pp. 442–445. [Google Scholar]
- Rehman, A.; Haseeb, K.; Saba, T.; Kolivand, H. M-SMDM: A model of security measures using Green Internet of Things with Cloud Integrated Data Management for Smart Cities. Environ. Technol. Innov. 2021, 24, 101802. [Google Scholar] [CrossRef]
- Rosenkrantz, A.B.; Hanna, T.N.; Steenburg, S.D.; Tarrant, M.J.; Pyatt, R.S.; Friedberg, E.B. The current state of teleradiology across the United States: A national survey of radiologists’ habits, attitudes, and perceptions on teleradiology practice. J. Am. Coll. Radiol. 2019, 16, 1677–1687. [Google Scholar] [CrossRef]
- Kumar, S.; Fred, A.L.; Miriam, L.J.; Padmanabhan, P.; Gulyás, B.; Ajay, K.H. Applications of Image Processing in Teleradiology for the Medical Data Analysis and Transfer Based on IOT. In Machine Learning Approaches for Convergence of IoT and Blockchain; John Wiley & Sons: Hoboken, NY, USA, 2021; pp. 175–204. [Google Scholar] [CrossRef]
- Islam, N.; Haseeb, K.; Rehman, A.; Alam, T.; Jeon, G. An adaptive and secure routes migration model for the sustainable cloud of things. Clust. Comput. 2022, 1–12. [Google Scholar] [CrossRef]
- Ramson, S.J.; Raju, K.L.; Vishnu, S.; Anagnostopoulos, T. Nature inspired optimization techniques for image processing—A short review. In Nature Inspired Optimization Techniques for Image Processing Applications; Springer: Cham, Switzerland, 2019; pp. 113–145. [Google Scholar] [CrossRef]
- Karimi-Mamaghan, M.; Mohammadi, M.; Meyer, P.; Karimi-Mamaghan, A.M.; Talbi, E.-G. Machine Learning at the service of Meta-heuristics for solving Combinatorial Optimization Problems: A state-of-the-art. Eur. J. Oper. Res. 2022, 296, 393–422. [Google Scholar] [CrossRef]
- Sundhari, R.M.; Jaikumar, K. IoT assisted Hierarchical Computation Strategic Making (HCSM) and Dynamic Stochastic Optimization Technique (DSOT) for energy optimization in wireless sensor networks for smart city monitoring. Comput. Commun. 2020, 150, 226–234. [Google Scholar] [CrossRef]
- Nayak, P.; Swetha, G.; Gupta, S.; Madhavi, K. Routing in wireless sensor networks using machine learning techniques: Challenges and opportunities. Measurement 2021, 178, 108974. [Google Scholar] [CrossRef]
- Rehman, A.; Haseeb, K.; Saba, T.; Lloret, J.; Ahmed, Z. Mobility Support 5G Architecture with Real-Time Routing for Sustainable Smart Cities. Sustainability 2021, 13, 9092. [Google Scholar] [CrossRef]
- Ahmed, I.; Din, S.; Jeon, G.; Piccialli, F.; Fortino, G. Towards collaborative robotics in top view surveillance: A framework for multiple object tracking by detection using deep learning. IEEE/CAA J. Autom. Sin. 2020, 8, 1253–1270. [Google Scholar] [CrossRef]
- Frustaci, M.; Pace, P.; Aloi, G.; Fortino, G. Evaluating critical security issues of the IoT world: Present and future challenges. IEEE Internet Things J. 2017, 5, 2483–2495. [Google Scholar] [CrossRef]
- Kotenko, I.; Saenko, I.; Branitskiy, A. Framework for mobile Internet of Things security monitoring based on big data processing and machine learning. IEEE Access 2018, 6, 72714–72723. [Google Scholar] [CrossRef]
- Haseeb, K.; Islam, N.; Saba, T.; Rehman, A.; Mehmood, Z. LSDAR: A light-weight structure based data aggregation routing protocol with secure internet of things integrated next-generation sensor networks. Sustain. Cities Soc. 2020, 54, 101995. [Google Scholar] [CrossRef]
- Zhang, Z.; Xiao, Y.; Ma, Z.; Xiao, M.; Ding, Z.; Lei, X.; Karagiannidis, G.K.; Fan, P. 6G wireless networks: Vision, requirements, architecture, and key technologies. IEEE Veh. Technol. Mag. 2019, 14, 28–41. [Google Scholar] [CrossRef]
- Song, H.; Bai, J.; Yi, Y.; Wu, J.; Liu, L. Artificial intelligence enabled Internet of Things: Network architecture and spectrum access. IEEE Comput. Intell. Mag. 2020, 15, 44–51. [Google Scholar] [CrossRef]
- Haseeb, K.; Saba, T.; Rehman, A.; Ahmed, Z.; Song, H.H.; Wang, H.H. Trust management with fault-tolerant supervised routing for smart cities using internet of things. IEEE Internet Things J. 2022. [Google Scholar] [CrossRef]
- Philip, N.Y.; Rodrigues, J.J.; Wang, H.; Fong, S.J.; Chen, J. Internet of Things for in-home health monitoring systems: Current advances, challenges and future directions. IEEE J. Sel. Areas Commun. 2021, 39, 300–310. [Google Scholar] [CrossRef]
- Oughton, E.J.; Lehr, W.; Katsaros, K.; Selinis, I.; Bubley, D.; Kusuma, J. Revisiting wireless internet connectivity: 5G vs Wi-Fi 6. Telecommun. Policy 2021, 45, 102127. [Google Scholar] [CrossRef]
- Awoyemi, B.S.; Alfa, A.S.; Maharaj, B.T. Resource optimisation in 5G and internet-of-things networking. Wirel. Pers. Commun. 2020, 111, 2671–2702. [Google Scholar] [CrossRef]
- Ansere, J.A.; Han, G.; Wang, H.; Choi, C.; Wu, C. A reliable energy efficient dynamic spectrum sensing for cognitive radio IoT networks. IEEE Internet Things J. 2019, 6, 6748–6759. [Google Scholar] [CrossRef]
- Seyfollahi, A.; Ghaffari, A. Reliable data dissemination for the Internet of Things using Harris hawks optimization. Peer-to-Peer Netw. Appl. 2020, 13, 1886–1902. [Google Scholar] [CrossRef]
- Liu, X.; Qiu, T.; Wang, T. Load-balanced data dissemination for wireless sensor networks: A nature-inspired approach. IEEE Internet Things J. 2019, 6, 9256–9265. [Google Scholar] [CrossRef]
- Saranraj, G.; Selvamani, K.; Malathi, P. A novel data aggregation using multi objective based male lion optimization algorithm (DA-MOMLOA) in wireless sensor network. J. Ambient Intell. Humaniz. Comput. 2021, 1–9. [Google Scholar] [CrossRef]
- Younus, M.U.; Khan, M.K.; Anjum, M.R.; Afridi, S.; Arain, Z.A.; Jamali, A.A. Optimizing the lifetime of software defined wireless sensor network via reinforcement learning. IEEE Access 2020, 9, 259–272. [Google Scholar] [CrossRef]
- Guo, W.; Yan, C.; Lu, T. Optimizing the lifetime of wireless sensor networks via reinforcement-learning-based routing. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719833541. [Google Scholar] [CrossRef]
- Wang, J.X.; Kurth-Nelson, Z.; Tirumala, D.; Soyer, H.; Leibo, J.Z.; Munos, R.; Blundell, C.; Kumaran, D.; Botvinick, M. Learning to reinforcement learn. arXiv 2016, arXiv:1611.05763. [Google Scholar]
- Bellare, M.; Kilian, J.; Rogaway, P. The security of cipher block chaining. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 1994. [Google Scholar] [CrossRef]

| Comparative Approaches | Contributions and Limitations |
|---|---|
| Existing solutions |
|
| Proposed model | To support the secured cloud, a machine learning-based solution is provided that uses edge computing and provides an intelligent decision-making approach for massive data management. It also ensures cloud data security by guaranteeing authentication, data concealing with integrity, and protection against malicious access. |
| Parameters | Values |
|---|---|
| Simulation area | two-dimensional |
| Sensor nodes | 50–250 |
| Malicious nodes | 20 |
| Transmission power | 5 m |
| Initial energy | 5 J |
| Simulation time | 5000 s |
| Data flow | CBR |
| Sink node | 1 |
| Edge nodes | 10 |
| Cloud devices | 4 |
| Size of public key | 512 bits |
| Proposed Model and Existing Work | Network Throughput (%) | Energy Consumption (j) | Data Drop Ratio (%) | Data Integrity (%) |
|---|---|---|---|---|
| Number of Nodes: 50 to 250 | ||||
| MEC-Seccloud | 87.5 | 1.21 | 7.9 | 85.2 |
| RDDI | 72.4 | 1.63 | 15 | 73.1 |
| DA-MOMLOA | 70 | 2.07 | 17.8 | 63.8 |
| Data Generation Rates: 100 to 500 bits/sec | ||||
| MEC-Seccloud | 88 | 1.3 | 9.4 | 85.8 |
| RDDI | 77.4 | 1.65 | 15.6 | 74.4 |
| DA-MOMLOA | 73 | 1.83 | 18.6 | 71.9 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rehman, A.; Saba, T.; Haseeb, K.; Alam, T.; Lloret, J. Sustainability Model for the Internet of Health Things (IoHT) Using Reinforcement Learning with Mobile Edge Secured Services. Sustainability 2022, 14, 12185. https://doi.org/10.3390/su141912185
Rehman A, Saba T, Haseeb K, Alam T, Lloret J. Sustainability Model for the Internet of Health Things (IoHT) Using Reinforcement Learning with Mobile Edge Secured Services. Sustainability. 2022; 14(19):12185. https://doi.org/10.3390/su141912185
Chicago/Turabian StyleRehman, Amjad, Tanzila Saba, Khalid Haseeb, Teg Alam, and Jaime Lloret. 2022. "Sustainability Model for the Internet of Health Things (IoHT) Using Reinforcement Learning with Mobile Edge Secured Services" Sustainability 14, no. 19: 12185. https://doi.org/10.3390/su141912185
APA StyleRehman, A., Saba, T., Haseeb, K., Alam, T., & Lloret, J. (2022). Sustainability Model for the Internet of Health Things (IoHT) Using Reinforcement Learning with Mobile Edge Secured Services. Sustainability, 14(19), 12185. https://doi.org/10.3390/su141912185









