Flexible-Clustering Based on Application Priority to Improve IoMT Efficiency and Dependability
Abstract
:1. Introduction
- Faint role of application and service priority to define and propose security methods for IoMT-based applications
- Lack of considering application priority to provide privacy methods for the IoMT.
- Customizing the security and privacy methods to the specific applications and sensors
- Lack of targeting and generalizing methods to support the applications in facing risky situations and unpredictable conditions
- Neglecting the imposing communication delay and energy consumption overheads to the performance of the IoMT applications
- Considering application priority to decision-making about dedicating a proper healthcare service to the requester
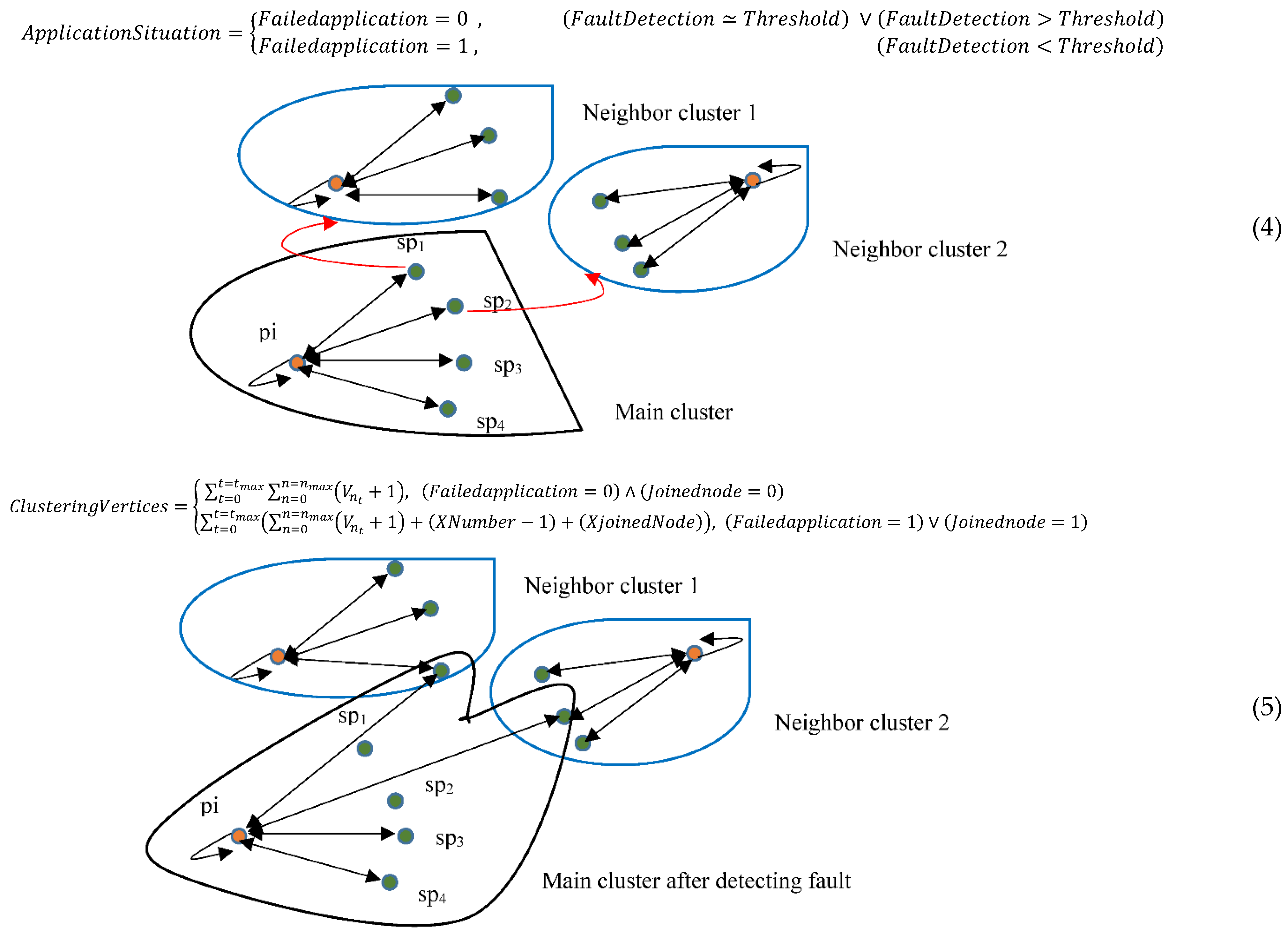
- Considering service priority to identify the appropriate neighbor nodes after detecting faults
- Analyzing the IoMT applications’ efficiency and dependability based on the applications and services’ priority
- Providing a method for flexible clustering a graph vertices and edges for improving security, availability, confidence, and privacy
- Providing the Equations and models to describe flexible clustering, node mapping, and estimating availability, security, privacy, and dependability
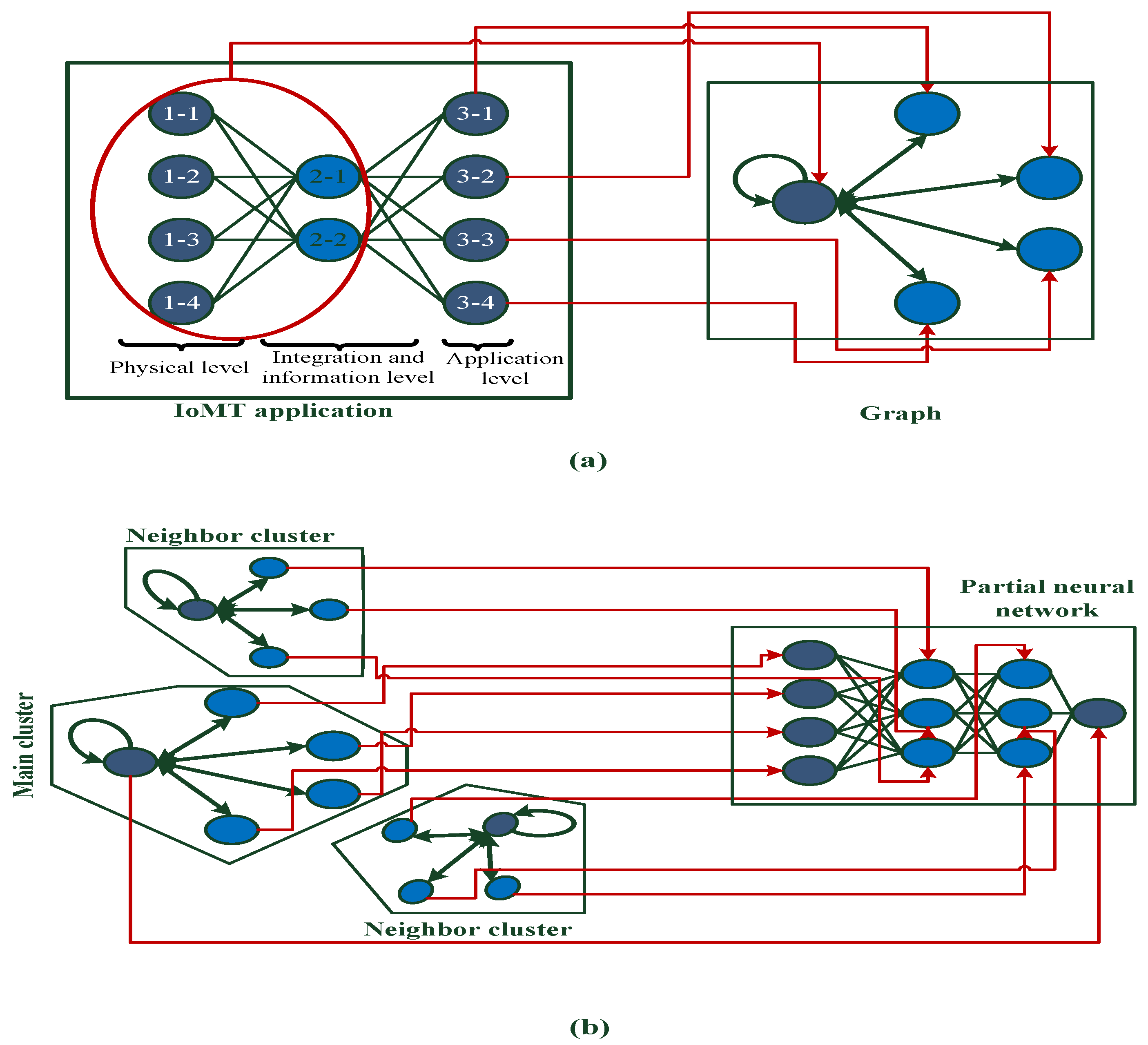
- Presenting node mapping method to transfer the application’s service providers role onto a graph vertices
- Employing a quasi-mapping approach to transfer the role of graph’s nodes onto a partial neural network’s neurons to identify the appropriate service providers nodes for joining the cluster
- Pruning the unfit and defective nodes to improve dependability and performance (total delay and energy)
2. Related Work
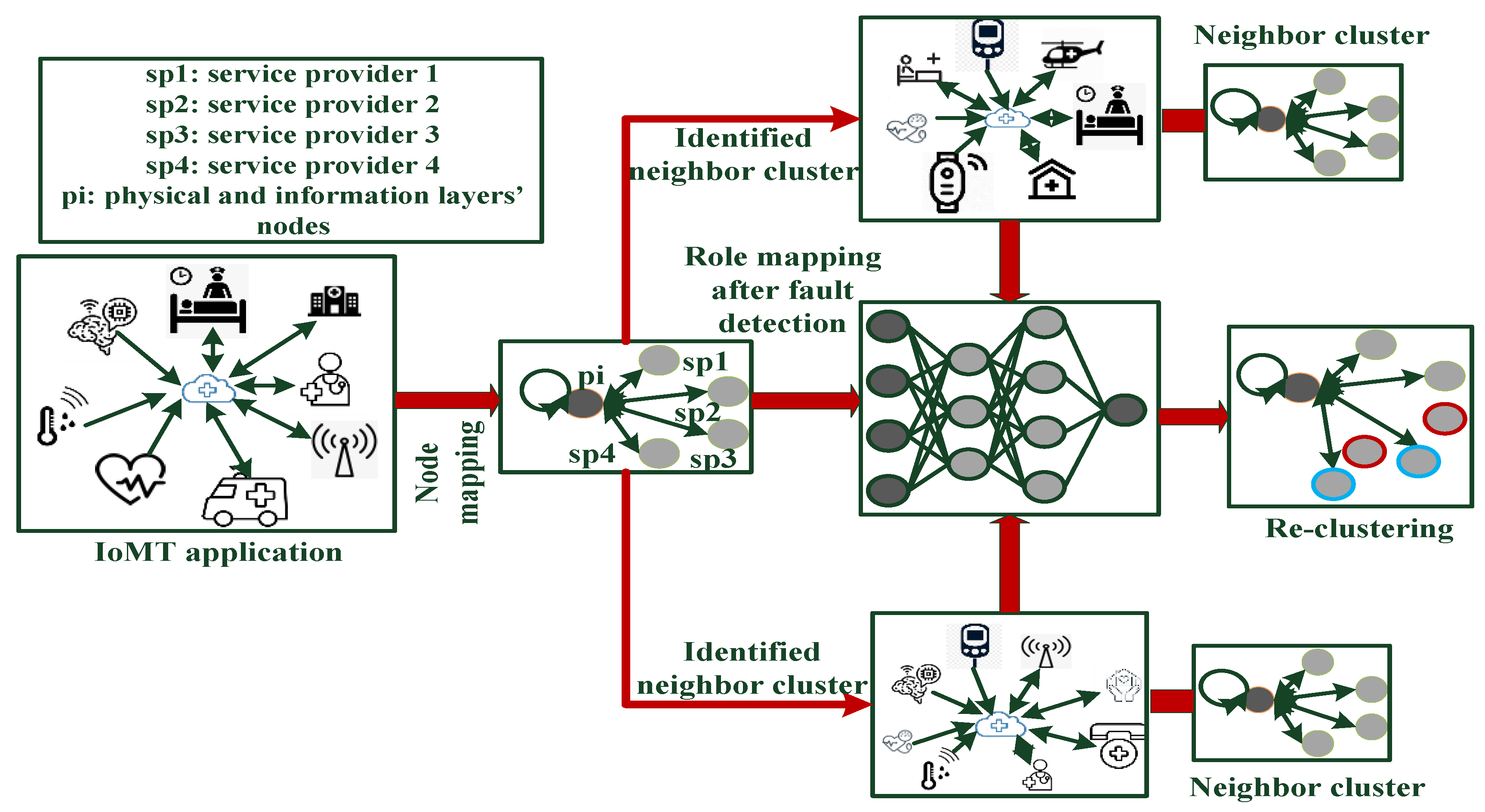
3. Flexible Cluster Modeling and NFC Algorithm
3.1. Defining Applications and Collecting a Dataset
3.2. Presenting Equations and Models
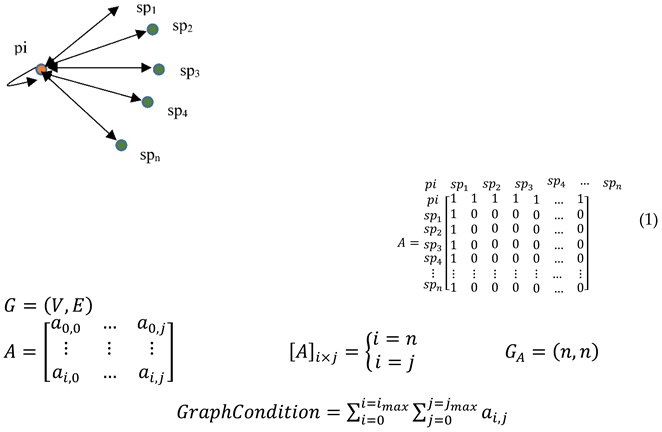
- [A]i×j demonstrates the matrix of the relationship between vertices of GA = (V, E), where i and j are indexes of rows and columns number of the matrix.
- GA = (V, E) consists of V vertices and E edges based on the number of the application’s nodes (Defining vertices) and the relationship between them (Defining edges) where (V = i) and (E = j), and (i = j = n) by describing n as the number service providers and pi node (as the accumulated node of the physical and information layers’ components).
- GraphCondition estimates the sum of [A]i×j matrix’s elements to investigate the relationship between service providers’ vertices (sp) and pi for utilizing its value to detect fault where ai,j describes the located element of the matrix in I row and j column.
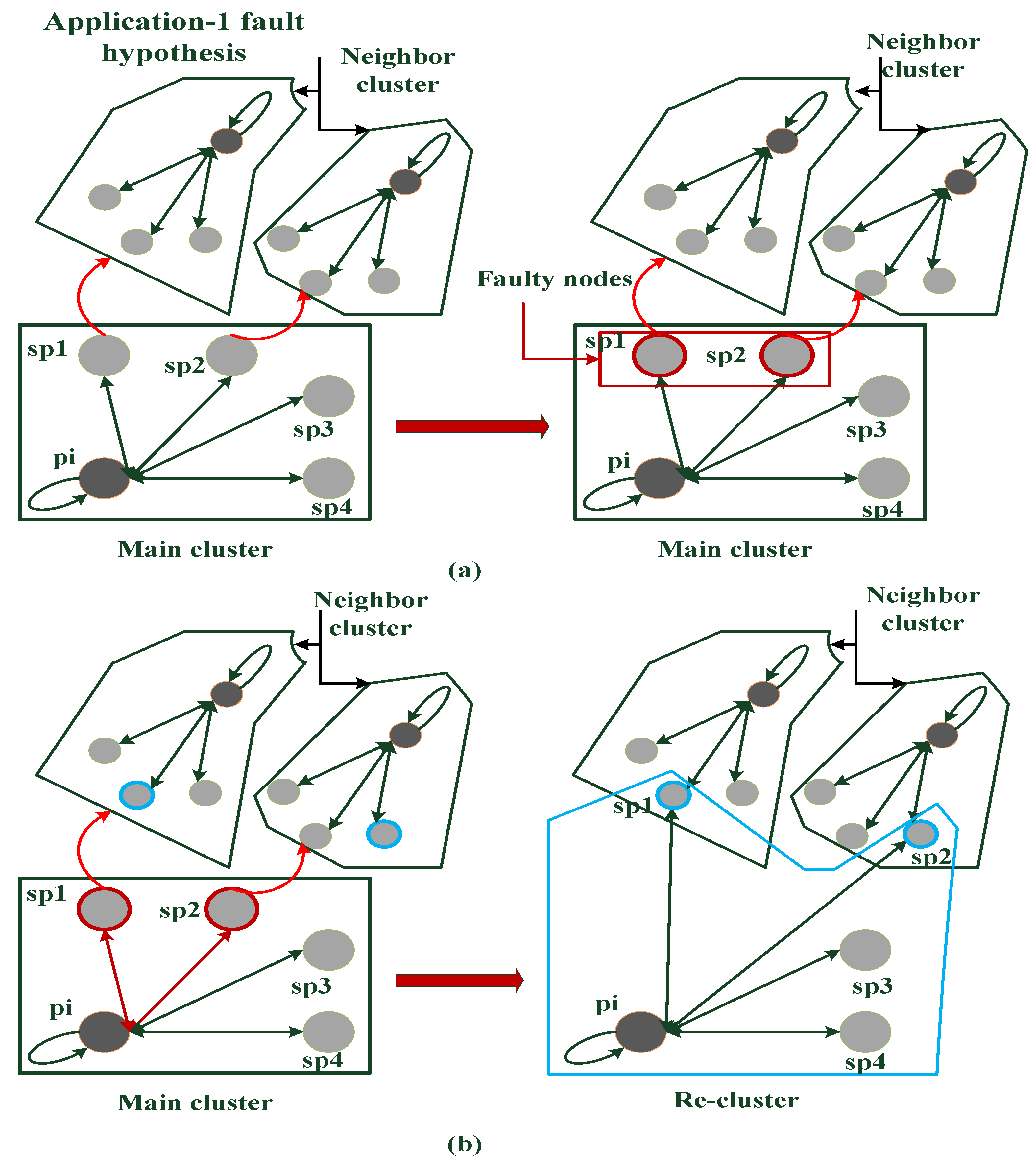
- Threshold defines a value for each application based on service and their priority for deciding to employ the neighbor servers after detecting faults. Xnumber and spn demonstrate the threshold number of defective service providers and the total number of the initial servers of the application.
- FaultDetection estimates a value to detect fault based on the sum of [A]i×j matrix’s elements (GraphCondition) and the expected value of the GraphCondition parameter, which is evaluated byas the maximum number of rows and columns.
- ApplicationSituation determines the situation of the application after detecting fault based on the estimated threshold’s value by defining the FailedApplication parameter and quantifying it.
- ClusteringVertices categorizes the vertices of GA (A graph) to cluster them based on two conditions of normal and faulty situations when identifying the application is as correct (Initial clustering) and facing failed application or joining a new service provider (Re-clustering) to application, which the joined node describes the number of new joined servers to application.
- [U]p×q describes a matrix to define the neurons of a neural network input layer where p and q determine the number of rows and columns of the [U]p×q matrix.
- [H]y×z is a matrix to describe the neurons of a NN’s hidden layer with y rows and z columns.
- NeuronMapping describes mapping the initial service provider, neighbor servers, and pi (Accumulated physical and information levels’ nodes) nodes onto the input, hidden, and output layers’ neurons, where up,q and hy,z are the elements of [U]p×q and [H]y×z matrices.
- PenaltyFault estimates the penalty value based on the threshold and output values and the total number of services at t time, where OutputNt and ThresholdNN indicate the output neuron’s value at t time and the estimated threshold value of the neural network.
- computes the value of the hidden layer’s weight after imposing the estimated penalty value onto them by(the initial value of the hidden layer’s weight) andvalues where d and Fault are the indexes for the weight and the related penalty to the detected fault.
- demonstrates estimating the value of the output layer’s weights at the time after imposing the computed penalty onto them whereandillustrate the values of the initial output weight and penalty with d and Fault indexes, respectively.
- ServiceAvailability estimates the application availability at t time based on analyzing the output neuron’s value after pruning weak weights and neurons where OutputAvailable demonstrates the availability of the output neuron.
- ServiceSecurity assesses the application security based on the number of correct services received (CorrectServicet) and the total number of services (TotalServicet) at t time.
- ServicePrivacy analyzes the application’s privacy by defining the edges between GA vertices and removing the related connections to the faulty nodes where ServiceSecuritypi describes the security of the pi vertex.
- Dependability estimates the application dependability where α, β, and µ are the impact factors of availability, security, and confidence.
3.3. Node Mapping and Flexible Clustering Algorithm
| Algorithm 1 Node mapping and flexible clustering (NFC) | |
| Inputs: | 1-PIS: The node’s values of the Physical and information and integration layers (HeartRateSensor, SugarLevelSensor, BloodPressureSensor, GPSSensor, DoctorService, NurseService) whereas PIS⸦ Natural number |
| 2-HSP: The nodes’ value of healthcare service providers (ClimbingStationService, MauntaieeringReliefService, EmergencyService, PoliceStationService) | |
| Output: | ApplicationDependability: The output’s value for analyzing the application dependability whereas 0 ≤ ApplicationDependability ≤ 1 |
| Parameter declaration: PI: Physical sensor and integration service = {HeartRate, SugarLevel, BloodPressure, GPS, Doctor, Nurse} SP: ={ClimbingStation, MountaineeringRelief, Emergency, PoliceStation} pi: ={0, 1,…, 4, 5} s: ={1, 2, 3, 4} i: Row index = {0, 1, 2, 3} j: Column index = {0, 1, 2, 3} nc: Neighbor cluste = {0, 1, 2} p: ={0, 1,…, 4, 5} q: ={0, 1,…, 4, 5} x: Neighbor node whereas x ⊂ Natural number and x ≥ 0 y: Joined node whereas y ⊂ Natural number and y ≥ 0 t: Available time whereas t ⊂ Natural number and t ≥ 0 α: The impact factor of IoMT application availability whereas α ⊂ Binary number β: The impact factor of IoMT application security whereas β ⊂ Binary number µ: The impact factor of IoMT application confidence whereas µ ⊂ Binary number | |
| Algorithm 2 NFC’s phase 1 | |
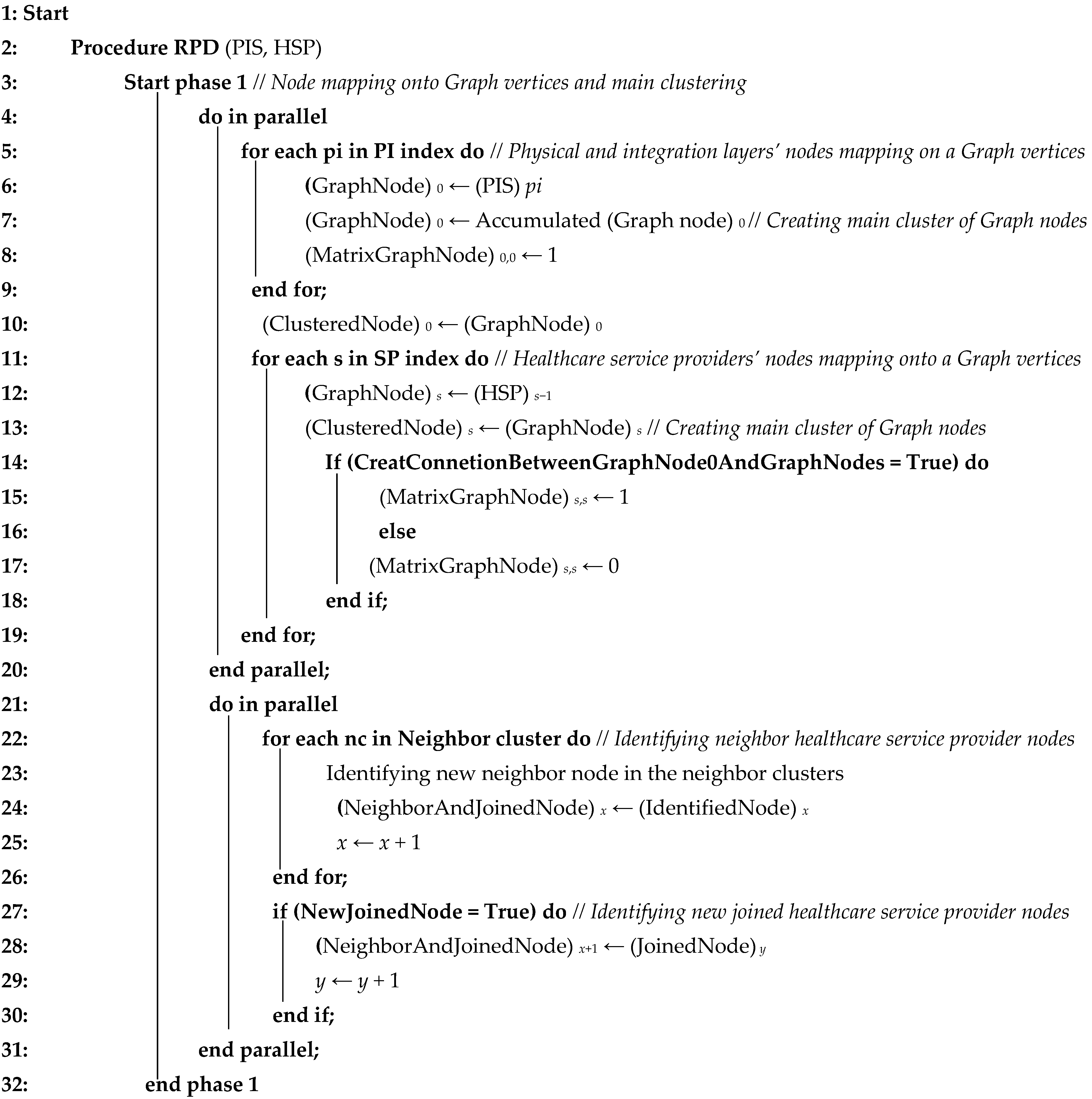 |
| Algorithm 3 NFC’s phase 2 | |
 |
| Algorithm 4 NFC’s phase 3 | |
 |
| Algorithm 5 NFC’s phase 4 | |
 |
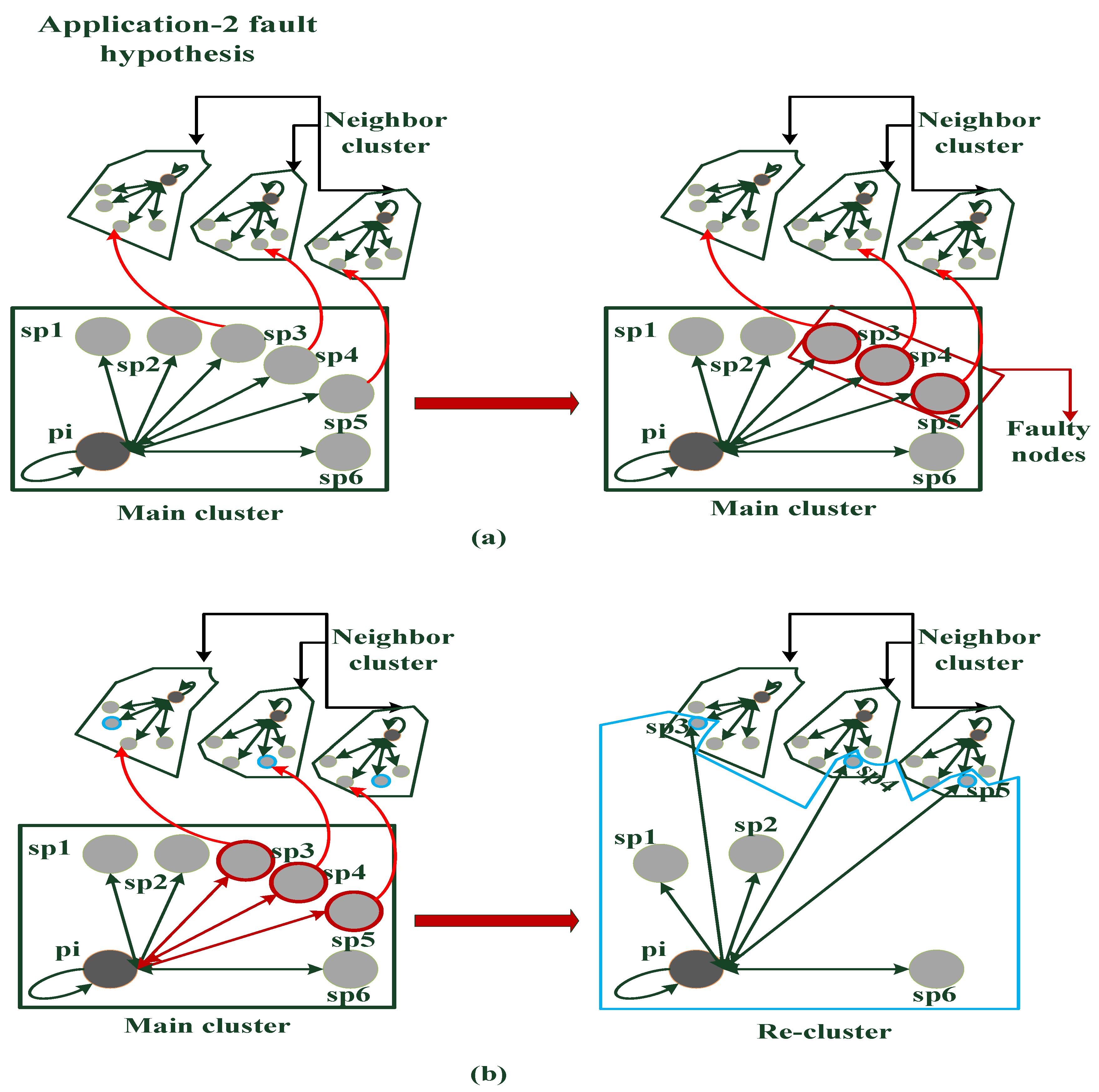
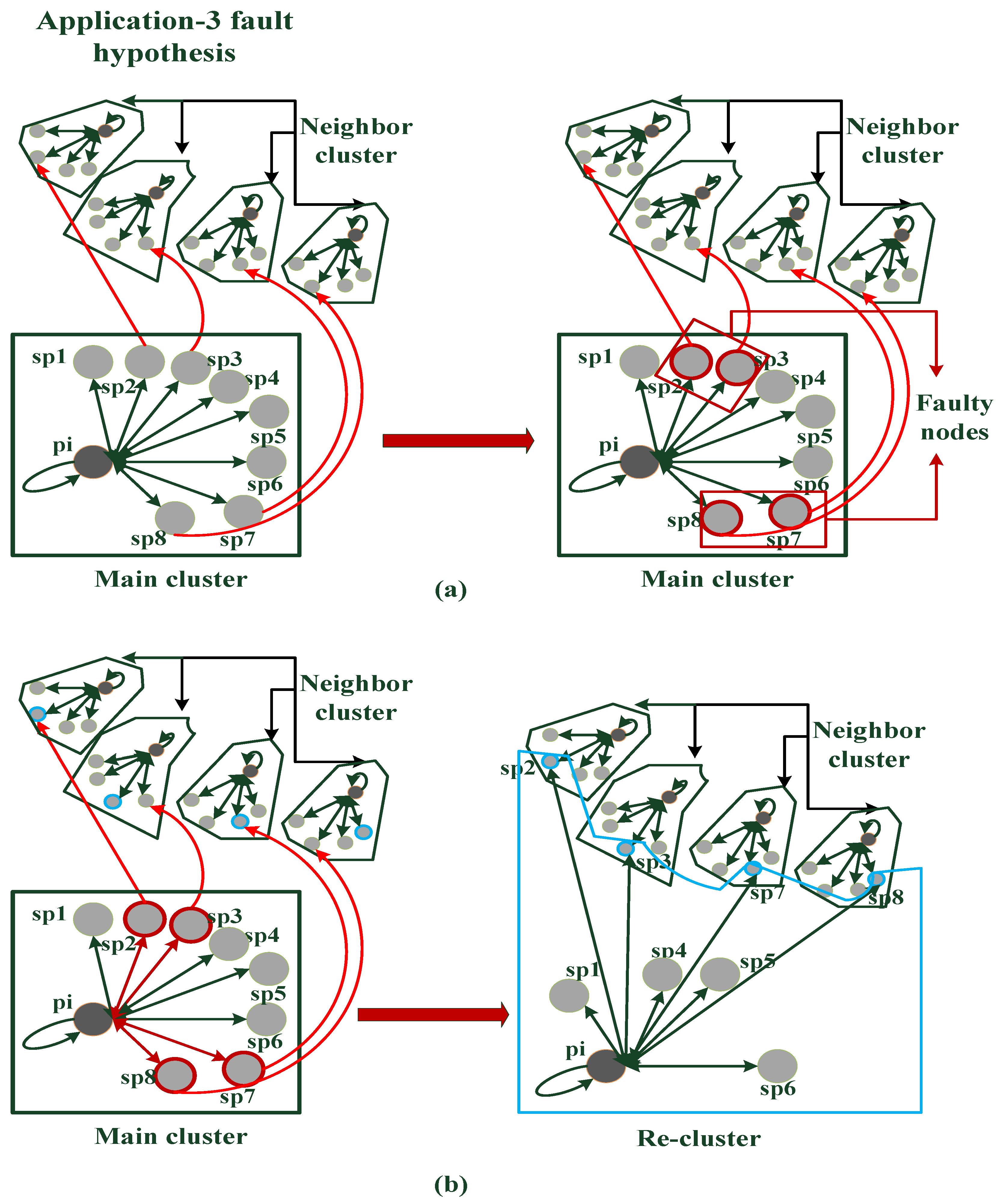
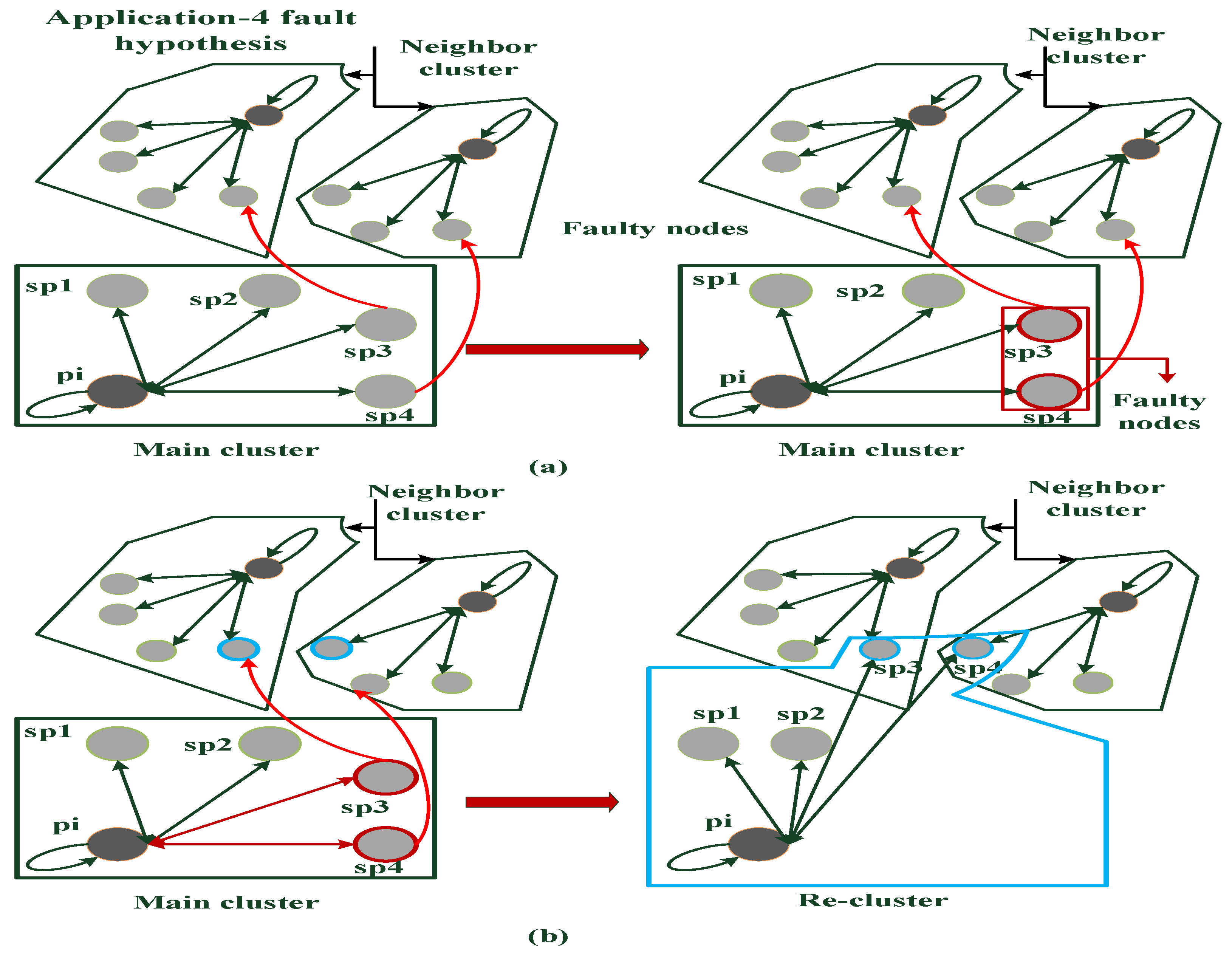
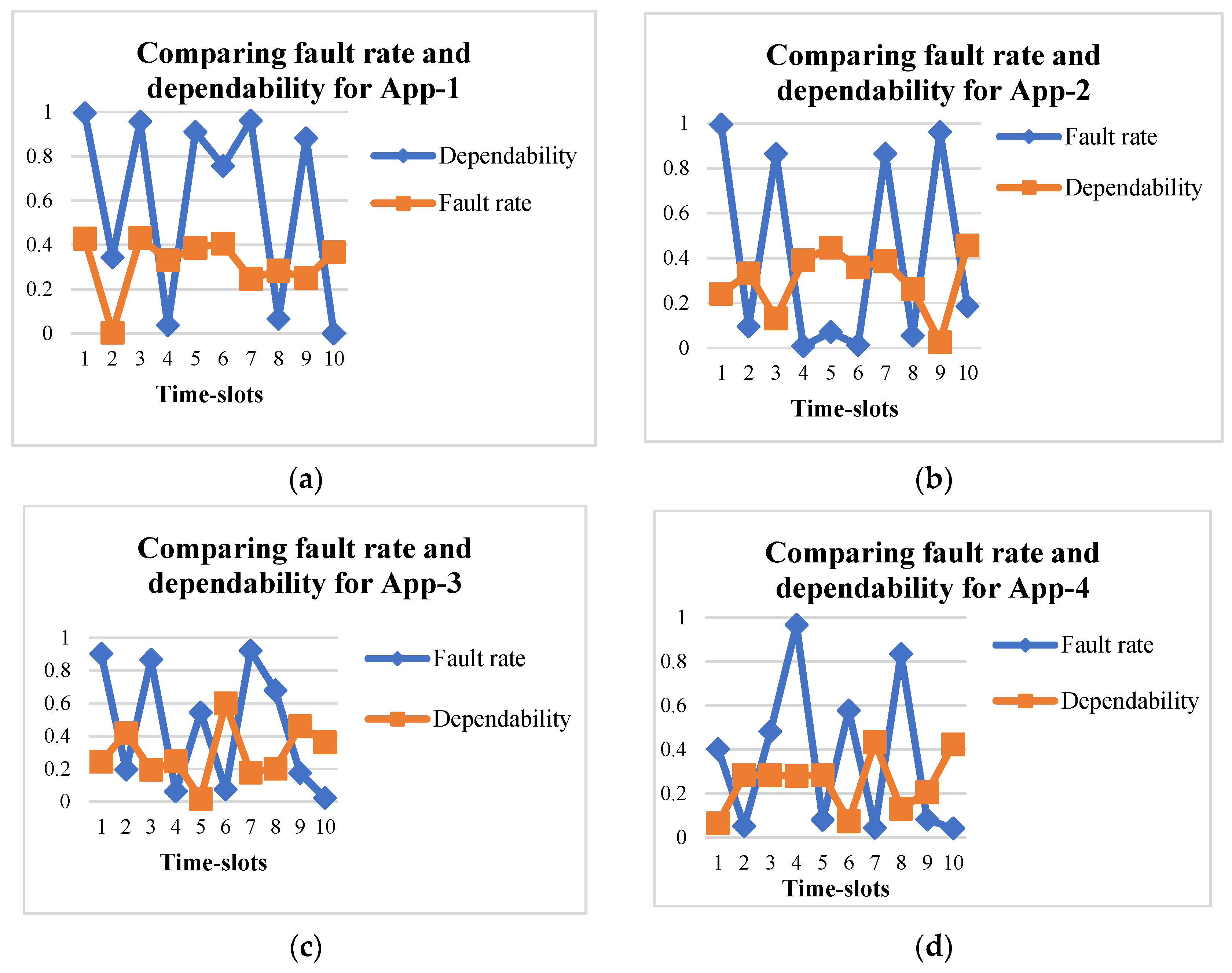
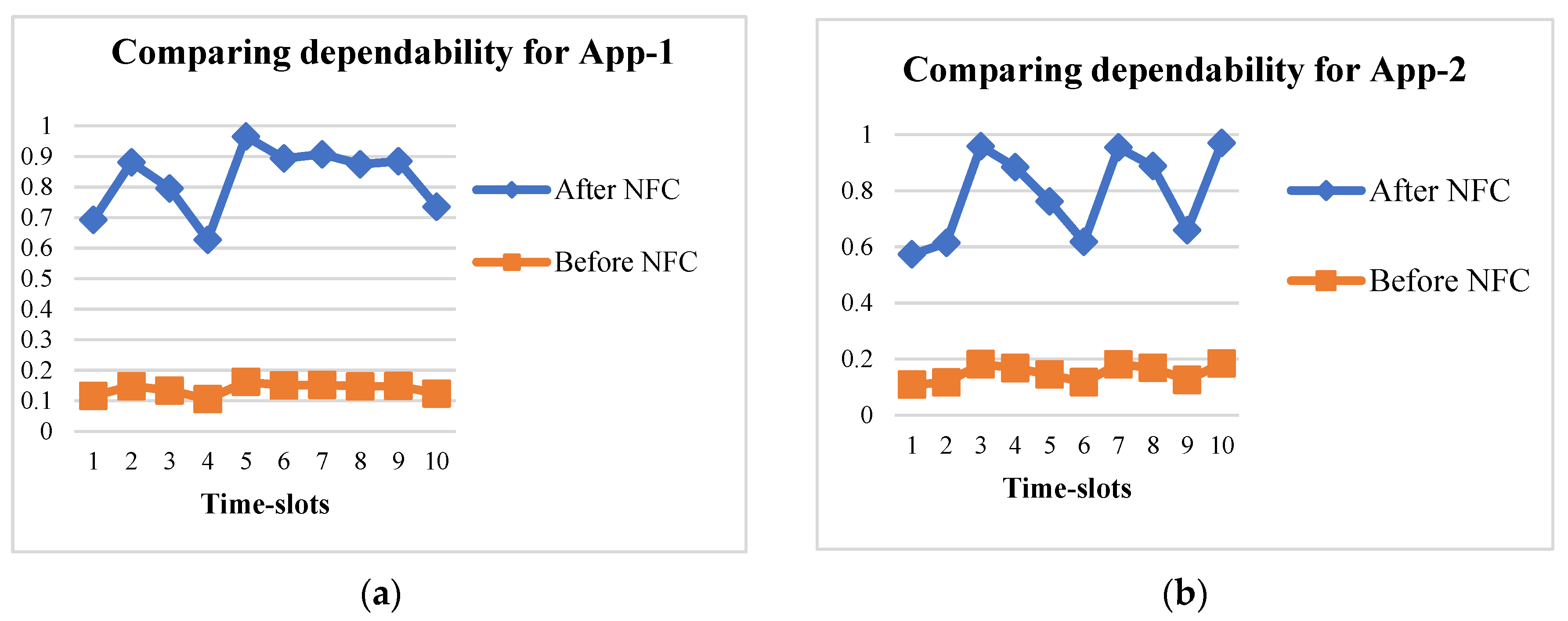
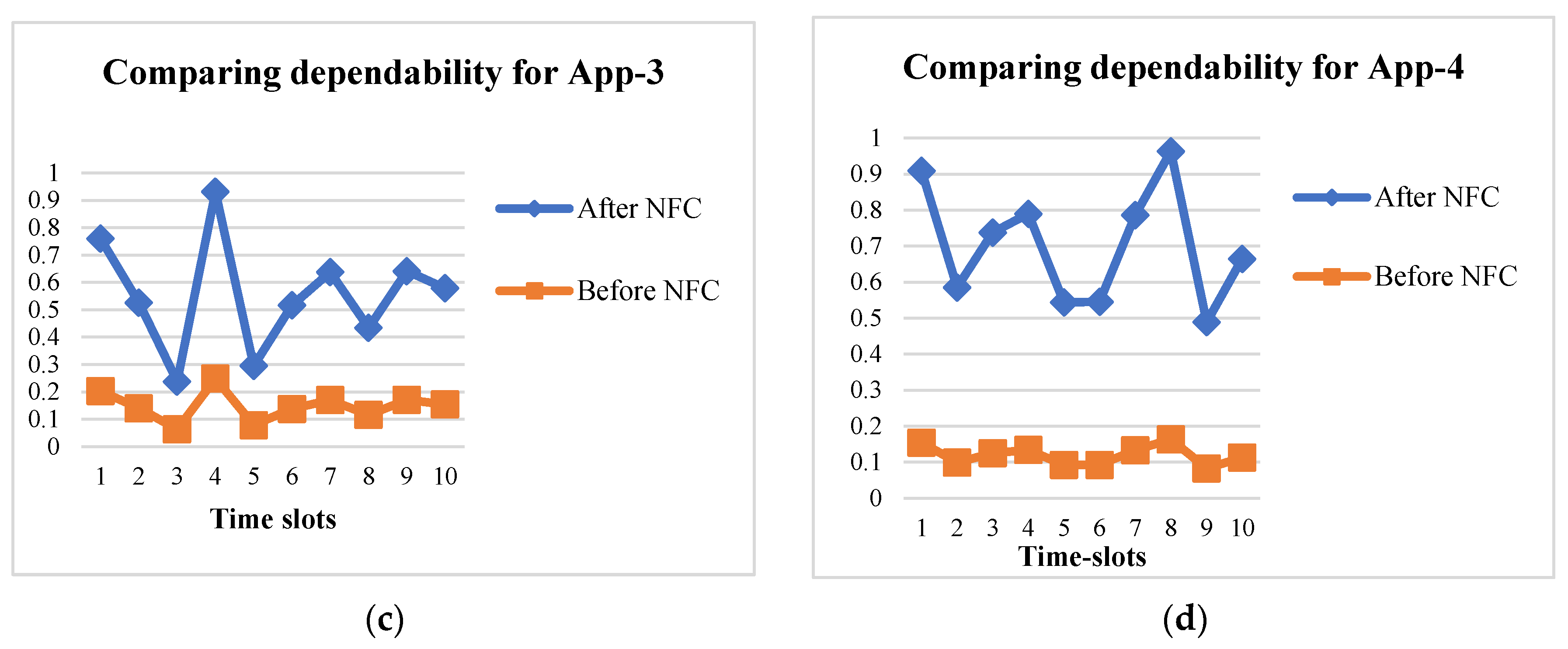
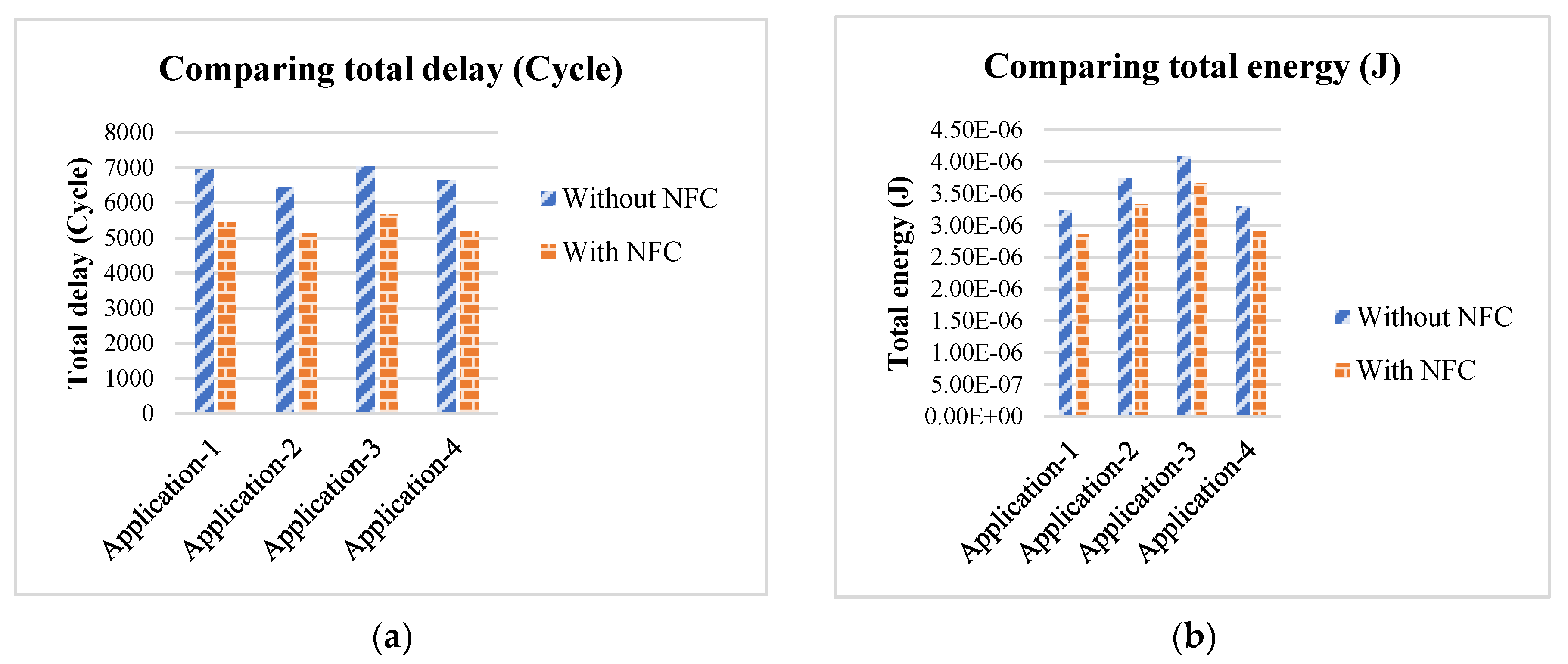
4. Simulation Results and Observations
5. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Jha, A.; Athanerey, A.; Kumar, A. Role and challenges of internet of things and informatics in Healthcare research. Health Technol. 2022, 12, 701–712. [Google Scholar] [CrossRef]
- Gupta, S.; Yadav, B.; Gupta, B. Security oIoT-based e-healthcare applications using blockchain. In Advances in Blockchain Technology for Cyber Physical Systems; Springer: Cham, Switzerland, 2022; pp. 79–107. [Google Scholar]
- Almalki, F.A.; Othman, S.B.; Sakli, H.; Angelides, M. Revolutionizing healthcare by coupling Unmanned Aerial Vehicles (UAVs) to Internet of Medical Things (IoMT). In Digital Health Transformation with Blockchain and Artificial Intelligence; CRC Press: Boca Raton, FL, USA, 2022; pp. 47–59. [Google Scholar]
- Mohapatra, S.; Sahoo, P.K. Internet of medical things: Applications and research issues in healthcare monitoring. In InIoT Applications for Healthcare Systems; Springer: Cham, Switzerland, 2022; pp. 1–31. [Google Scholar]
- Verma, G.; Shahi, A.P.; Prakash, S. A study towards recent trends, issues and research challenges of intelligent IoT healthcare techniques: IoMT and CIoMT. In Proceedings of the Trends in Electronics and Health Informatics; Springer: Singapore, 2022; pp. 177–190. [Google Scholar]
- Yasmeen, G.; Javed, N.; Ahmed, T. Interoperability: A Challenge for IoMT. ECS Trans. 2022, 107, 4459–4467. [Google Scholar] [CrossRef]
- Adil, M.; Khan, M.K.; Jadoon, M.M.; Attique, M.; Song, H.; Farouk, A. An AI-enabled Hybrid lightweight Authentication Scheme for Intelligent IoMT based Cyber-Physical Systems. IEEE Trans. Netw. Sci. Eng. 2022. [Google Scholar] [CrossRef]
- Amintoosi, H.; Nikooghadam, M.; Shojafar, M.; Kumari, S.; Alazab, M. Slight: A lightweight authentication scheme for smart healthcare services. Comput. Electr. Eng. 2022, 99, 107803. [Google Scholar] [CrossRef]
- Haque, R.U.; Hasan, A.S. Overview of blockchain-based privacy preserving machine learning for IoMT. In Big Data Intelligence for Smart Applications; Springer: Cham, Switzerland, 2022; pp. 265–278. [Google Scholar]
- Haque, R.U.; Hasan, A.S.; Nishat, T.; Adnan, M.A. Privacy-preserving-means clustering over blockchain-based encrypted IoMT Data. In Advances in Blockchain Technology for Cyber Physical Systems; Springer: Cham, Switzerland, 2022; pp. 109–123. [Google Scholar]
- Lakhan, A.; Mohammed, M.A.; Nedoma, J.; Martinek, R.; Tiwari, P.; Vidyarthi, A.; Alkhayyat, A.; Wang, W. Federated-learning based privacy preservation and fraud-enabled blockchain IoMT system for healthcare. IEEE J. Biomed. Health Inform. 2022, 1–11. [Google Scholar] [CrossRef]
- Gaba, G.S.; Hedabou, M.; Kumar, P.; Braeken, A.; Liyanage, M.; Alazab, M. Zero knowledge proofs based authenticated key agreement protocol for sustainable healthcare. Sustain. Cities Soc. 2022, 80, 103766. [Google Scholar] [CrossRef]
- Rana, A.; Chakraborty, C.; Sharma, S.; Dhawan, S.; Pani, S.K.; Ashraf, I. Internet of medical things-based secure and energy-efficient framework for health care. Big Data 2022, 10, 18–33. [Google Scholar] [CrossRef]
- Ghazal, T.M.; Hasan, M.K.; Abdallah, S.N.; Abubakkar, K.A. Secure IoMT pattern recognition and exploitation for multimedia information processing using private blockchain and fuzzy logic. Trans. Asian Low-Resour. Lang. Inf. Process. 2022. [Google Scholar] [CrossRef]
- Fuke, R.P.; Mahajan, R.P. Pragmatic Analysis of IoMT Network Modelling Techniques from a Statistical Perspective. In Proceedings of the 2022 International Conference on Electronics and Renewable Systems (ICEARS), Tuticorin, India, 16–18 March 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 531–542. [Google Scholar]
- Pelekoudas-Oikonomou, F.; Zachos, G.; Papaioannou, M.; de Ree, M.; Ribeiro, J.C.; Mantas, G.; Rodriguez, J. Blockchain-based security mechanisms for IoMT Edge networks in IoMT-based healthcare monitoring systems. Sensors 2022, 22, 2449. [Google Scholar] [CrossRef]
- Wazid, M.; Gope, P. BACKM-EHA: A novel blockchain-enabled security solution for IoMT-based e-healthcare applications. ACM Trans. Internet Technol. (TOIT) 2022. [Google Scholar] [CrossRef]
- Sampathkumar, A.; Tesfayohani, M.; Shandilya, S.K.; Goyal, S.B.; Shaukat Jamal, S.; Shukla, P.K.; Bedi, P.; Albeedan, M. Internet of Medical Things (IoMT) and reflective belief design-based big data analytics with Convolution Neural Network-Metaheuristic Optimization Procedure (CNN-MOP). Comput. Intell. Neurosci. 2022, 2022, 2898061. [Google Scholar] [CrossRef] [PubMed]
- Garg, N.; Petwal, R.; Wazid, M.; Singh, D.P.; Das, A.K.; Rodrigues, J.J. On the design of an AI-driven secure communication scheme for Internet of medical things environment. Digit. Commun. Netw. 2022. [Google Scholar] [CrossRef]
- Ibaida, A.; Abuadbba, A.; Chilamkurti, N. Privacy-preserving compression model for efficient IoMT ECG sharing. Comput. Commun. 2021, 166, 1–8. [Google Scholar] [CrossRef]
- Wei, T.; Liu, S.; Du, X. Learning-based efficient sparse sensing and recovery for privacy-aware IoMT. IEEE Internet Things J. 2022, 9, 9948–9959. [Google Scholar] [CrossRef]
- Si-Ahmed, A.; Al-Garadi, M.A.; Boustia, N. Survey of machine learning based intrusion detection methods for internet of medical things. arXiv preprint 2022, arXiv:2202.09657. [Google Scholar]
- Nayak, J.; Meher, S.K.; Souri, A.; Naik, B.; Vimal, S. Extreme learning machine and bayesian optimization-driven intelligent framework for IoMT cyber-attack detection. J. Supercomput. 2022, 78, 14866–14891. [Google Scholar] [CrossRef]
- Rahmani, A.M.; Ali Naqvi, R.; Ali, S.; Hosseini Mirmahaleh, S.Y.; Hosseinzadeh, M. Quasi-Mapping and Satisfying IoT Availability with a Penalty-Based Algorithm. Mathematics 2021, 9, 3286. [Google Scholar] [CrossRef]
- Pustokhina, I.V.; Pustokhin, D.A.; Gupta, D.; Khanna, A.; Shankar, K.; Nguyen, G.N. An effective training scheme for deep neural network in edge computing enabled Internet of medical things (IoMT) systems. IEEE Access 2020, 8, 107112–107123. [Google Scholar] [CrossRef]
- CupCarbon Simulator. Available online: http://cupcarbon.com/ (accessed on 1 June 2022).
- Khan, I.A.; Moustafa, N.; Razzak, I.; Tanveer, M.; Pi, D.; Pan, Y.; Ali, B.S. XSRU-IoMT: Explainable simple recurrent units for threat detection in Internet of Medical Things networks. Future Gener. Comput. Syst. 2022, 127, 181–193. [Google Scholar] [CrossRef]
- Rasool, R.U.; Ahmad, H.F.; Rafique, W.; Qayyum, A.; Qadir, J. Security and privacy of Internet of medical things: A contemporary review in the age of surveillance, botnets, and adversarial ML. J. Netw. Comput. Appl. 2022, 201, 103332. [Google Scholar] [CrossRef]
- Hossen, M.N.; Panneerselvam, V.; Koundal, D.; Ahmed, K.; Bui, F.M.; Ibrahim, S.M. Federated Machine Learning for Detection of Skin Diseases and Enhancement of Internet of Medical Things (IoMT) Security. IEEE J. Biomed. Health Inform. 2022. [Google Scholar] [CrossRef] [PubMed]
- Enamamu, T.S. Intelligent authentication framework for Internet of Medical Things (IoMT). In Illumination of Artificial Intelligence in Cybersecurity and Forensics; Springer: Cham, Switzerland, 2022; pp. 97–121. [Google Scholar]
- Lee, T.F.; Ye, X.; Lin, S.H. Anonymous Dynamic Group Authenticated Key Agreements Using Physical Unclonable Functions for Internet of Medical Things. IEEE Internet Things J. 2022, 6, 15336–15348. [Google Scholar] [CrossRef]
- Bevish Jinila, Y.; Prayla Shyry, S.; Christy, A. A Multi-component-based zero trust model to mitigate the threats in internet of medical things. In Data Engineering for Smart Systems; Springer: Singapore, 2022; pp. 605–613. [Google Scholar]
- Samuel, O.; Omojo, A.B.; Onuja, A.M.; Sunday, Y.; Tiwari, P.; Gupta, D.; Hafeez, G.; Yahaya, A.S.; Fatoba, O.J.; Shamshirband, S. IoMT: A COVID-19 Healthcare System driven by Federated Learning and Blockchain. IEEE J. Biomed. Health Inform. 2022. [Google Scholar] [CrossRef]
- Ali, A.; Almaiah, M.A.; Hajjej, F.; Pasha, M.F.; Fang, O.H.; Khan, R.; Teo, J.; Zakarya, M. An industrial IoT-based blockchain-enabled secure searchable encryption approach for healthcare systems using neural network. Sensors 2022, 22, 572. [Google Scholar] [CrossRef] [PubMed]
- Mubashar, A.; Asghar, K.; Javed, A.R.; Rizwan, M.; Srivastava, G.; Gadekallu, T.R.; Wang, D.; Shabbir, M. Storage and proximity management for centralized personal health records using an ipfs-based optimization algorithm. J. Circuits Syst. Comput. 2022, 31, 2250010. [Google Scholar] [CrossRef]
- Nie, X.; Zhang, A.; Chen, J.; Qu, Y.; Yu, S. Blockchain-empowered secure and privacy-preserving health data sharing in edge-based IoMT. Secur. Commun. Netw. 2022, 2022, 8293716. [Google Scholar] [CrossRef]
- Kaur, D.; Singh, S.; Mansoor, W.; Kumar, Y.; Verma, S.; Dash, S.; Koul, A. Computational intelligence and metaheuristic techniques for brain tumor detection through IoMT-Enabled MRI Devices. Wirel. Commun. Mob. Comput. 2022, 2022, 1519198. [Google Scholar] [CrossRef]
- Reddy, D.K.; Behera, H.S.; Nayak, J.; Routray, A.R.; Kumar, P.S.; Ghosh, U. A Fog-Based Intelligent Secured IoMT Framework for Early Diabetes Prediction. In Intelligent Internet of Things for Healthcare and Industry; Springer: Cham, Switzerland, 2022; pp. 199–218. [Google Scholar]
- Sharifshazileh, M.; Burelo, K.; Sarnthein, J.; Indiveri, G. An electronic neuromorphic system for real-time detection of high frequency oscillations (HFO) in intracranial EEG. Nat. Commun. 2021, 12, 3095. [Google Scholar] [CrossRef]
- Alon, H.D.; Ligayo, M.A.D.; Melegrito, M.P.; Cunanan, C.F.; Uy, I.I.E. Deep-Hand: A deep inference vision approach of recognizing a hand sign language using american alphabet. In Proceedings of the 2021 International Conference on Computational Intelligence and Knowledge Economy (ICCIKE), Dubai, United Arab Emirates, 17–18 March 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 373–377. [Google Scholar]
- Sellaturay, P.; Nasser, S.; Ewan, P. Polyethylene glycol–induced systemic allergic reactions (anaphylaxis). J. Allergy Clin. Immunol. Pract. 2021, 9, 670–675. [Google Scholar] [CrossRef]
- Dick, K.; Pattang, A.; Hooker, J.; Nissan, N.; Sadowski, M.; Barnes, B.; Tan, L.H.; Burnside, D.; Phanse, S.; Aoki, H.; et al. Human–Soybean allergies: Elucidation of the seed proteome and comprehensive protein–protein interaction prediction. J. Proteome Res. 2021, 20, 4925–4947. [Google Scholar] [CrossRef]
- Muramatsu, K.; Imamura, H.; Tokutsu, K.; Fujimoto, K.; Fushimi, K.; Matsuda, S. Epidemiological study of hospital admissions for food-induced anaphylaxis using the Japanese Diagnosis Procedure Combination Database. J. Epidemiol. 2022, 32, 163–167. [Google Scholar] [CrossRef] [PubMed]
- Rauch, S.; Wallner, B.; Ströhle, M.; Dal Cappello, T.; Brodmann Maeder, M. Climbing accidents—Prospective data analysis from the international alpine trauma registry and systematic review of the literature. Int. J. Environ. Res. Public Health 2020, 17, 203. [Google Scholar] [CrossRef] [PubMed]
- Satava, R.; Angood, P.B.; Harnett, B.; Macedonia, C.; Merrell, R. The physiologic cipher at altitude: Telemedicine and real-time monitoring of climbers on Mount Everest. Telemed. J. E-Health 2000, 6, 303–313. [Google Scholar] [CrossRef] [PubMed]
- Dataset. Available online: https://books.google.com/books/about/The_Himalaya_by_the_Numbers.html?id=9kiiuAAACAAJ&source=kp_book_description (accessed on 10 May 2022).
- Dataset. Available online: https://medium.com/ai-techsystems/analyzing-eeg-brainwave-data-to-detect-emotions-on-cainvas-48833f3f0811 (accessed on 10 May 2022).
- Dataset. Available online: https://www.kaggle.com/datasets/piotrgrabo/breastcancerproteomes (accessed on 10 May 2022).
- Dataset. Available online: https://www.kaggle.com/datasets/andrewgao/alzheimers-gene-expression-profiles (accessed on 10 May 2022).
- Dataset. Available online: https://ncdrisc.org/data-downloads-blood-pressure.html (accessed on 10 May 2022).
- Dataset. Available online: https://www.kaggle.com/datasets/johnsmith88/heart-diseasedataset?resource=download&select=heart.csv (accessed on 10 May 2022).
- Dataset. Available online: https://www.ons.gov.uk/peoplepopulationandcommunity/birthsdeathsandmarriages/deaths/datasets/climaterelatedmortalityandhospitaladmissionsenglandandwales (accessed on 10 May 2022).
- Dataset. Available online: https://www.ons.gov.uk/peoplepopulationandcommunity/healthandsocialcare/healthcaresystem/datasets/nationalsurveyofbereavedpeoplevoices (accessed on 10 May 2022).
- Dataset. Available online: https://www.ons.gov.uk/peoplepopulationandcommunity/healthandsocialcare/conditionsanddiseases (accessed on 10 May 2022).
- Dataset. Available online: https://ourworldindata.org/covid-vaccinations (accessed on 10 May 2022).
- Collected Dataset. Available online: https://github.com/yasamanhosseini/Flexible-clustering-IoMT-nodes (accessed on 20 July 2022).
- Dataset. Available online: https://www.javatpoint.com/design-patterns-in-java (accessed on 10 May 2022).
- Dataset. Available online: https://www.geeksforgeeks.org/python-design-patterns/ (accessed on 10 May 2022).
- Dataset. Available online: https://releases.ubuntu.com/16.04/ (accessed on 10 May 2022).
- Dataset. Available online: https://support.apple.com/downloads/macos (accessed on 10 May 2022).
- Dataset. Available online: https://jupyter.org/ (accessed on 10 May 2022).
- Dataset. Available online: https://www.tensorflow.org/ (accessed on 10 May 2022).
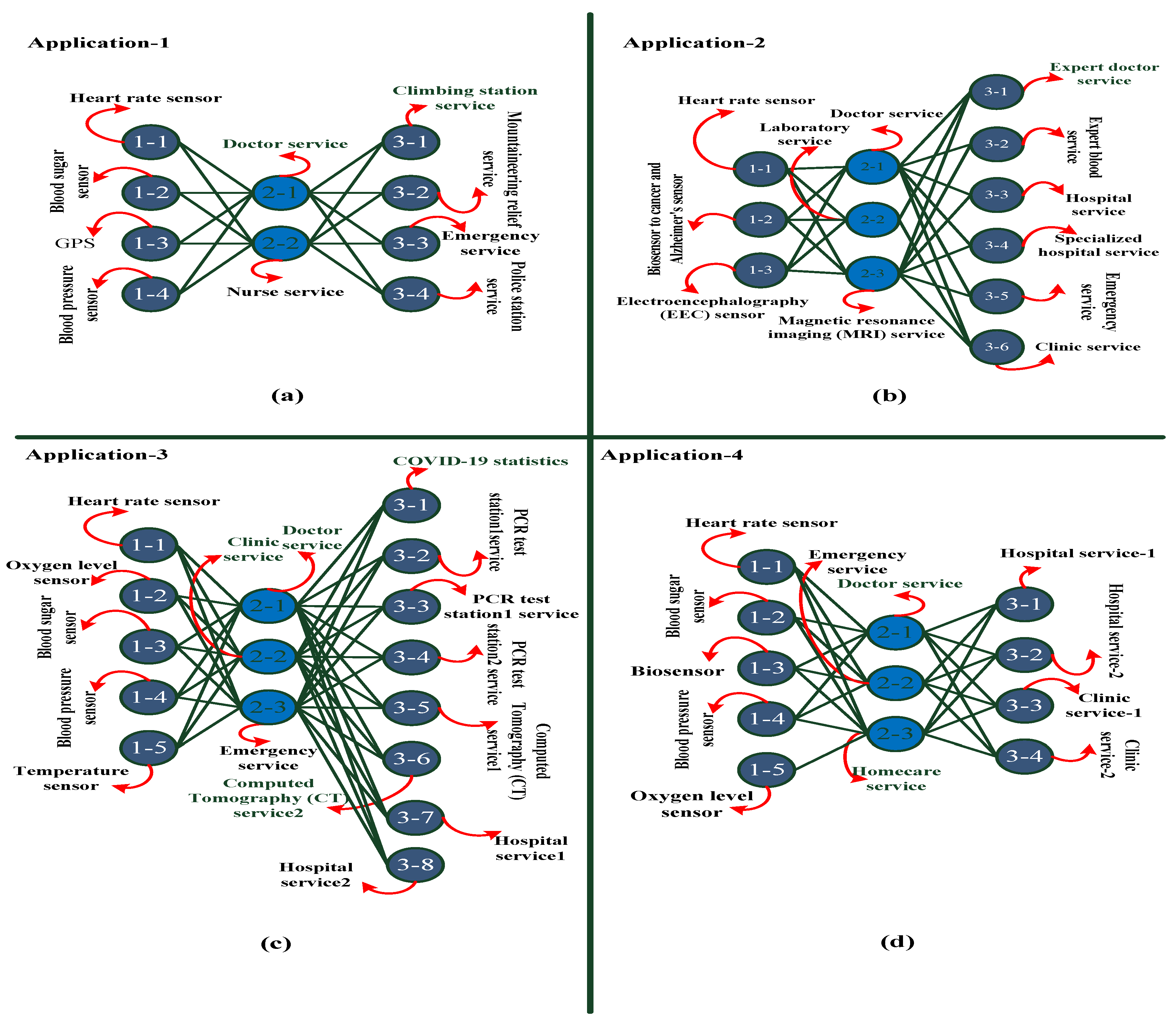
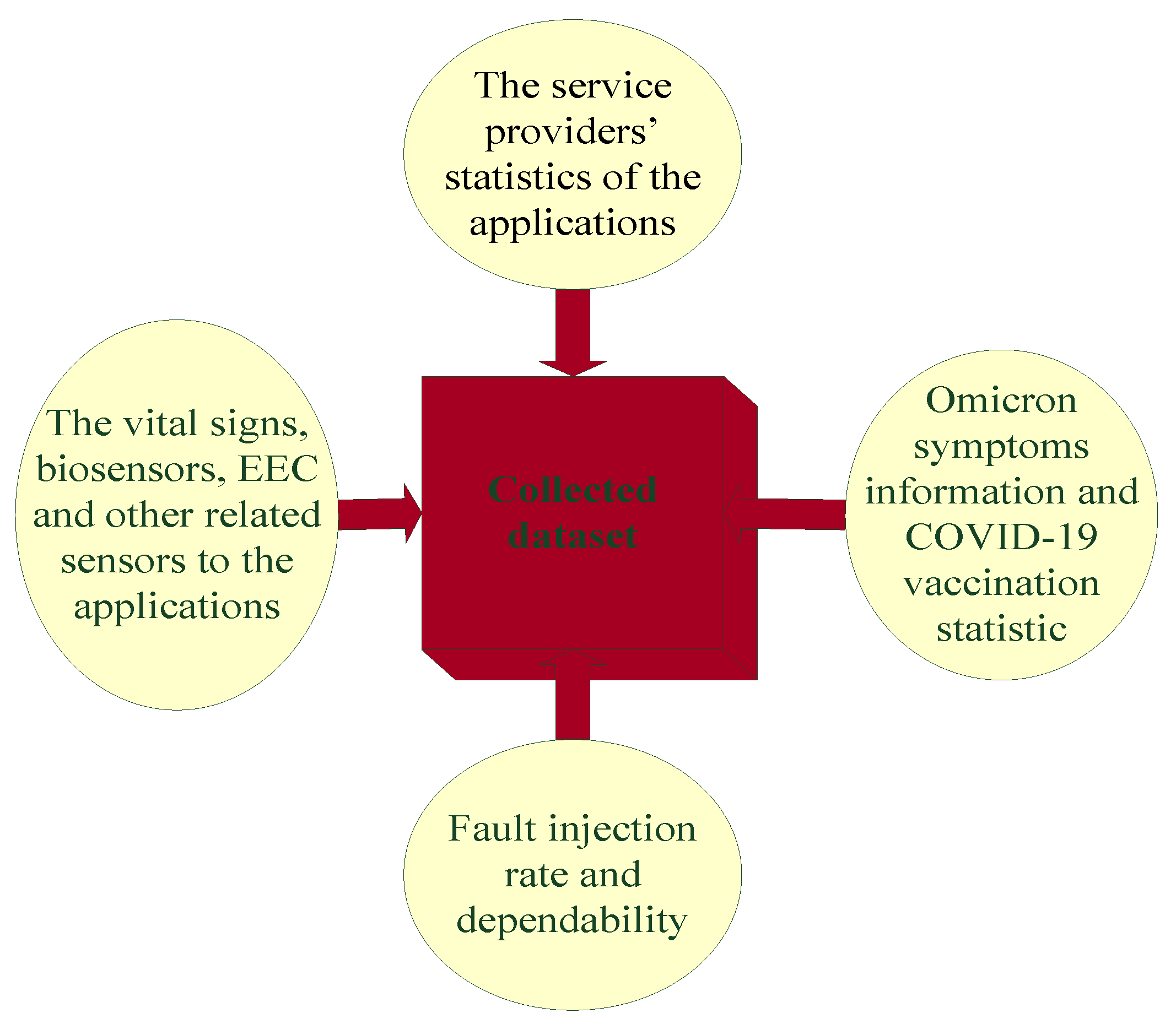

| Case Study | Method | Advantage | Weakness |
|---|---|---|---|
| Khan et al. [27] |
|
|
|
| Rasool et al. [28] |
|
|
|
| Hossen et al. [29] |
|
|
|
| Enamamu et al. [30] |
|
|
|
| Lee et al. [31] |
|
|
|
| Bevish et al. [32] |
|
|
|
| Samuel et al. [33] |
|
|
|
| Ali et al. [34] |
|
|
|
| Mubashar et al. [35] |
|
|
|
| Nie et al. [36] |
|
|
|
| Kaur et al. [37] |
|
|
|
| Reddy et al. [38] |
|
|
|
| Sharifshazileh et al. [39] |
|
|
|
| Alon et al. [40] |
|
|
|
| This idea |
|
|
|
| Parameter | Description | Condition |
|---|---|---|
| A | Matrix of Graph A | — |
| U | Matrix of neural network’s input layer | — |
| H | Matrix of neural network’s hidden layer | — |
| GA | Graph A based on the relationship between physical, information, and integration layers’ nodes and healthcare service providers of an application | — |
| V | The vertices of Graph A | 0 ≥ V |
| E | The edges of Graph A | 0 ≥ E |
| i | The row number of matrix A | 0 ≤ i ≤ imax |
| j | Column number of matrix A | 0 ≤ j ≤ jmax |
| p | The row number of matrix U | 0 ≤ p ≤ pmax |
| q | Column number of matrix U | 0 ≤ q ≤ qmax |
| y | The row number of matrix H | 0 ≤ y ≤ ymax |
| z | Column number of matrix H | 0 ≤ z ≤ zmax |
| pi | Physical, integration, and information layers’ nodes of Graph A | — |
| sp | Healthcare service provider node of Graph A | — |
| n | The number of ahealthcare service providers | 0 ≤ n ≤ nmax |
| s | The number of services of the neural network output | 0 ≤ s ≤ smax |
| ai,j | Matrix A’s element | (ai,j = 0) OR (ai,j = 1) |
| up,q | Matrix U’s element | (up,q = 0) OR (up,q = 1) |
| hy,z | Matrix H’s element | (hy,z = 0) OR (hy,z = 1) |
| imax | The maximum number of matrix A’s rows | 0 ≥ imax |
| jmax | The maximum number of matrix A’s columns | 0 ≥ jmax |
| pmax | The maximum number of matrix U’s rows | 0 ≥ pmax |
| qmax | The maximum number of matrix U’s columns | 0 ≥ qmax |
| ymax | The maximum number of matrix H’s rows | 0 ≥ ymax |
| zmax | The maximum number of matrix H’s columns | 0 ≥ zmax |
| nmax | The maximum number of a healthcare service provider | 0 ≥ nmax |
| smax | The maximum number of services of the neural network output | 0 ≥ smax |
| d | The total number of hidden layer’s weights | 0 ≥ d |
| l | The total number of output layer’s weights | 0 ≥ l |
| GraphCondition | The relationship between service providers, physical and integration, and information layers nodes | 0 ≥ GraphCondition |
| XNumber | The threshold number of defective nodes | 0 ≥ XNumber |
| XjoinedNode | The number of newly joined nodes | 0 ≥ XjoinedNode |
| Threshold | The threshold value of application validation based on priority | 0 ≥ Threshold |
| FaultDetection | Detecting faults in the service providers | 0 ≥ FaultDetection |
| ApplicationSituation | Investigating the IoMT application’s situation in fault detection | (ApplicationSituation = 0) OR (ApplicationSituation = 1) |
| NeuronMapping | Mapping Graph’s nodes onto a neural network neurons | — |
| OutputN | Output neuron | 0 ≤ OutputN ≤ 1 |
| Failedapplication | The situation of faulty service providers | (Failedapplication = 0) OR (Failedapplication = 1) |
| joinednode | The situation of new joined nodes | (joinednode = 0) OR (joinednode = 1) |
| Fault | The fault number | 0 ≤ Fault ≤ Faultmax |
| Faultmax | The maximum number of fault | 0 ≥ Faultmax |
| PenaltyFault | The penalty for a fault | 0 ≥ PenaltyFault |
| ThresholdNN | The threshold value of the neural network’s output | 0 ≥ ThresholdNN |
| The service with s number at t time | 0 ≥ | |
| Hidden layer’s weights’ values with d index | — | |
| The initial value of the hidden layer’s weights | — | |
| Output layer’s weights’ values with l index | — | |
| The initial value of the output layer’s weights | — | |
| ServiceAvailability | Service availability of the IoMT application | 0 ≤ ServiceAvailability ≤ 1 |
| OutputAvailabilityt | The availability of output neuron at t time | 0 ≤ OutputAvailability ≤ 1 |
| ServiceSecuritypi | IoMT application security based on pi | 0 ≤ ServiceSecuritypi ≤ 1 |
| CorrectServicet | The number of received correct services at t time | — |
| TotalServicet | The total number of received services at t time | — |
| ServicePrivacy | A definition of application privacy is based on the relationship between its nodes and security | — |
| En | The related edge of Graph A to service provider n | — |
| α | Impact factor of availability on dependability | 0 ≤ α ≤ 1 |
| β | Impact factor of security on dependability | 0 ≤ β ≤ 1 |
| µ | Impact factor of confidence on dependability | 0 ≤ µ ≤ 1 |
| Dependability | IoMT application dependability | 0 ≥ Dependability |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rahmani, A.M.; Hosseini Mirmahaleh, S.Y. Flexible-Clustering Based on Application Priority to Improve IoMT Efficiency and Dependability. Sustainability 2022, 14, 10666. https://doi.org/10.3390/su141710666
Rahmani AM, Hosseini Mirmahaleh SY. Flexible-Clustering Based on Application Priority to Improve IoMT Efficiency and Dependability. Sustainability. 2022; 14(17):10666. https://doi.org/10.3390/su141710666
Chicago/Turabian StyleRahmani, Amir Masoud, and Seyedeh Yasaman Hosseini Mirmahaleh. 2022. "Flexible-Clustering Based on Application Priority to Improve IoMT Efficiency and Dependability" Sustainability 14, no. 17: 10666. https://doi.org/10.3390/su141710666
APA StyleRahmani, A. M., & Hosseini Mirmahaleh, S. Y. (2022). Flexible-Clustering Based on Application Priority to Improve IoMT Efficiency and Dependability. Sustainability, 14(17), 10666. https://doi.org/10.3390/su141710666







