A Method of Optimizing a Set of Programs for Mitigating Threats Related to the Undertaking of a Contract for the Execution of Construction Works
Abstract
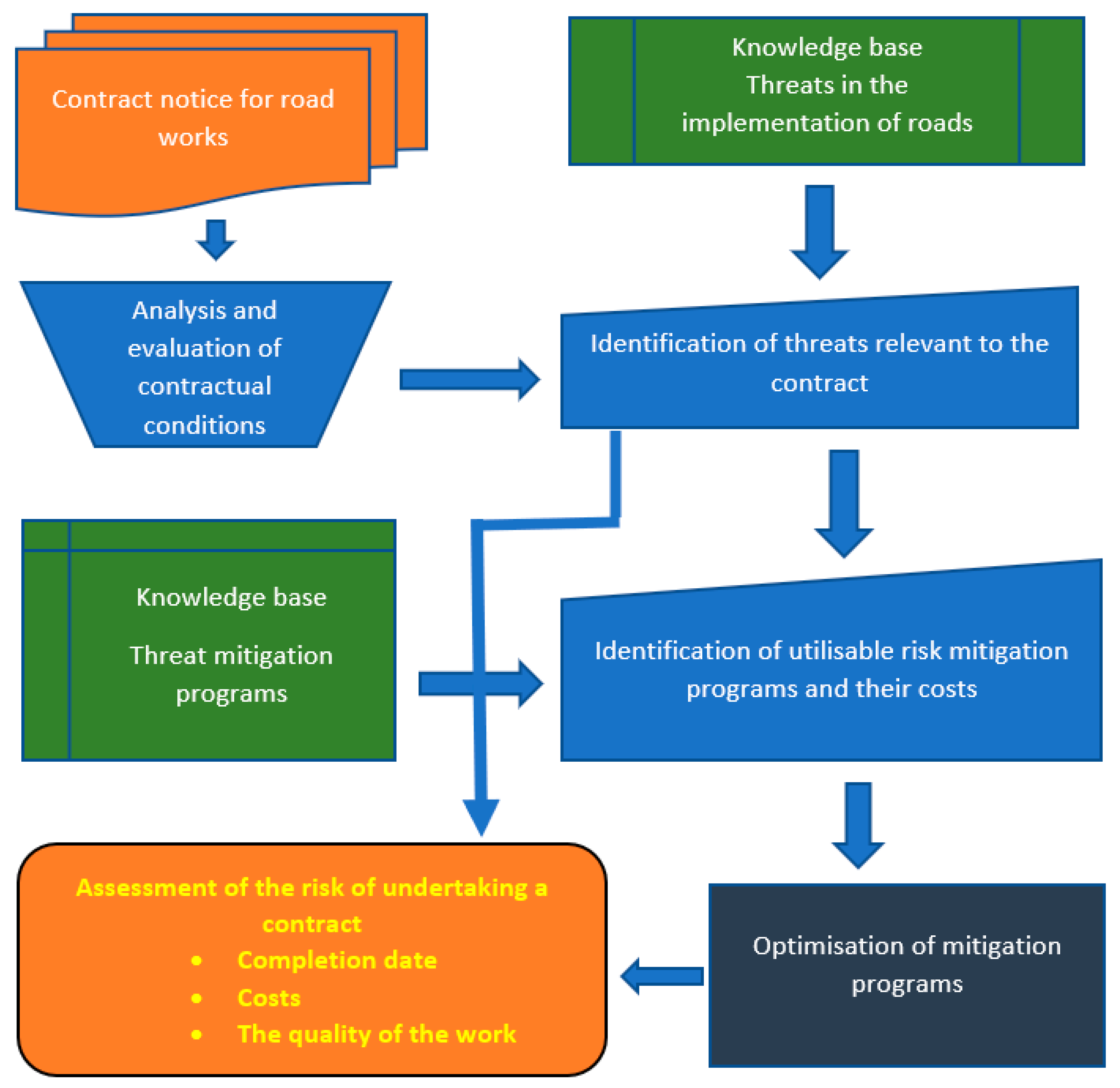
:1. Introduction
2. The Problem of Risk Management
3. Risk and Threats
4. Optimizing a Set of Programs for Mitigating Threats
- Assign Boolean variable wj to each subset x(rj);
- Create an alternative conjunctive expression:
- Convert this expression to the form of an irreducible Boolean sum (mfa):
5. Example
5.1. Data for Analysis
5.2. Application of the Algorithm
5.3. Conclusions
6. Summary
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Brancia, A. SMES Risk Management: An analysis of the Existing Literature Considering the Different Risk Streams. In Proceedings of the 8th AGSE International Entrepreneurship Research Exchange, Melbourne, Australia, 1–4 February 2011. [Google Scholar]
- Dallas, M.F. Value & Risk Management: A Guide to Best Practice; Blackwell Publishing: Oxford, UK, 2006; pp. 14–18. [Google Scholar]
- Godfrey, P.S.; Halcrow, W. Control of Risk. A Guide to the Systematic Management of Risk from Construction; CIRIA: London, UK, 1996; pp. 13–17. [Google Scholar]
- Iqbala, S.; Choudhryb, R.M.; Holschemacherc, K.; Alia, A.; Tamošaitienė, J. Risk management in construction projects. Technol. Econ. Dev. Econ. 2015, 21, 65–78. [Google Scholar] [CrossRef]
- Marcinek, K.; Foltyn-Zarychta, M.; Tworek, P. Decision making in processes entrepreneurship: Method of risk assessment in the practice of the largest Polish companies in the light of the empirical research. In Finance and Risk, Proceedings of the 13th International Scientific Conference; Springer: Berlin/Heidelberg, Germany, 2011; pp. 383–395. [Google Scholar]
- Hillson, D. Developing effective risk responses. In Proceedings of the 30th Annual Project Management Institute Seminars & Symposium, Philadelphia, PA, USA, 10–16 October 1999. [Google Scholar]
- Lam, J. Enterprise Risk Management; Wiley & Sons: Hoboken, NJ, USA, 2003. [Google Scholar]
- Tworek, P. Ryzyko Wykonawców Przedsięwzięć Inwestycyjnych; Akademia Ekonomiczna im. K. Adamieckiego, Uniwersytet Ekonomiczny w Katowicach: Katowice, Poland, 2010. [Google Scholar]
- Li, R.Y.M. Econometric modelling of risk adverse behaviours of entrepreneurs in the provision of house fittings in China. Constr. Econ. Build. 2012, 12, 72–82. [Google Scholar] [CrossRef] [Green Version]
- Dey, P.K. Project Risk Management: A Combined Analytic Hierarchy Process and Decision Tree Approach. Cost Eng. 2002, 44, 13–26. [Google Scholar]
- Smith, N.J.; Merna, T.; Jobling, P. Managing Risk in Construction Projects; Blackwell Publishing: Oxford, UK, 2008. [Google Scholar]
- Tang, W.; Qiang, M.; Duffield, C.F.; Young, D.M.; Lu, Y. Risk Management in the Chinese Construction Industry. J. Constr. Eng. Manag. 2007, 133, 944–956. [Google Scholar] [CrossRef]
- Zwikael, O.; Sadeh, A. Planning effort as an effective risk management tool. J. Oper. Manag. 2007, 25, 755–767. [Google Scholar] [CrossRef]
- Marcinek, K. Ryzyko Projektów Inwestycyjnych. Prace Naukowe; Wydawnictwo Akademii Ekonomicznej: Katowice, Poland, 2001; p. 219. [Google Scholar]
- Royer, P.S. Project Risk Management; Copyring by Management Concepts, Inc.: Vienna, VA, USA, 2002. [Google Scholar]
- Edwards, L. Practical Risk Management in the Construction Industry; Thomas Telford Publications: London, UK, 1995. [Google Scholar]
- Pheng, L.S.; Chuan, Q.T. Environmental factors and work performance of project managers in the construction industry. Int. J. Proj. Manag. 2006, 24, 24–37. [Google Scholar] [CrossRef]
- Winegard, A.; Warhoe, S.P. Understanding Risk to Mitigate Changes and Avoid Disputes. In AACE International Transaction; The Association for the Advancement of Cost Engineering: Orlando, FL, USA, 2003; Volume 1, pp. 1–8. [Google Scholar]
- Teixeira, J.C.; Kulejewski, J.; Krzemiński, M.; Zawistowski, J. Zarządzanie Ryzykiem w Budownictwie; Guimaraes: Warszawa, Poland, 2011. [Google Scholar]
- Śladowski, G. Use of Meta-Networks to Evaluate Key Agents, Knowledge and Resources in the Planning of Construction Projects. Arch. Civ. Eng. 2018, 64, 111–129. [Google Scholar] [CrossRef] [Green Version]
- Zhu, J.; Mostafavi, A. Characterization of the underlying mechanisms of vulnerability in complex projects using dynamic network simulation. In Proceedings of the 2017 Winter Simulation Conference (WSC), Las Vegas, NV, USA, 3–6 December 2017; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2017; pp. 2436–2447. [Google Scholar]
- Zhu, J.; Mostafavi, A. An Integrated Framework for the Assessment of the Impacts of Uncertainty in Construction Projects Using Dynamic Network Simulation. In Proceedings of the 2015 ASCE International Workshop on Computing in Civil Engineering, Austin, TX, USA, 21–23 June 2015; pp. 355–362. [Google Scholar]
- Zhu, J.; Mostafavi, A. Dynamic Meta-Network Modeling for an Integrated Project Performance Assessment under Uncertainty. In Proceedings of the Construction Research Congress, San Juan, PR, USA, 31 May–2 June 2016; pp. 2340–2350. [Google Scholar]
- Śladowski, G. Meta-Sieci w Proaktywnym Podejściu do Planowania Rewaloryzacji Zabytkowych Obiektów Budowlanych; Wydawnictwo Politechniki Krakowskiej: Kraków, Poland, 2021. [Google Scholar]
- Jaśkowski, P.; Biruk, S. Analiza czynników ryzyka czasu realizacji przedsięwzięć budowlanych. Czas. Tech. 2010, 107, 157–166. [Google Scholar]
- Skorupka, D. Identification and Initial Risk Assessment of Construction Projects in Poland. J. Manag. Eng. 2008, 24, 120–127. [Google Scholar] [CrossRef]
- Cristóbal, J.R.S. Time, Cost, and Quality in a Road Building Project. J. Constr. Eng. Manag. 2009, 135, 1273. [Google Scholar] [CrossRef]
- Dytczak, M.; Ginda, G. Production engineering tools for civil engineering practice—The case of FMEA. Czas. Tech. 2017, 10, 85–92. [Google Scholar] [CrossRef]
- Liaudanskiene, R.; Ustinovichius, L. Review of risk assessment methods and the peculiarities of their application at construc-tion sites. In Proceedings of the 10th International Conference Modern Building Materials, Structures and Techniques, Vilnus, Lithuania, 19–21 May 2010; pp. 446–450. [Google Scholar]

| Threat Symbol | Description of Threats |
|---|---|
| t1 | Threat of failure to meet quality standards: due to the fact that the deadline is short with regard to the scope of work to be done, the implementation will be rushed. |
| t2 | Threat of extending the scope of the work: the geological documentation shows that due to the fact that there may be organic soils in the substrate, it may be necessary to replace the soil. |
| t3 | Threat of reducing the scope of the work: a “quantity survey contract” where, on the basis of the design documentation, it turns out that the bill of quantities is overestimated. |
| t4 | Threat of a lack of availability of subcontractors: a large range of industry and specialist works, a short deadline of work and the tender announced in the middle of the year when some companies already have a full portfolio of orders. |
| t5 | Threat of failure to meet the contractual deadline: a large scope of work. |
| t6 | Threat of difficulties in acquiring specialized workers: a large scope of industry and specialist works, a short deadline of works and the tender announced in the middle of the year when some companies already have a full portfolio of orders. |
| t7 | Threat of inexperienced and unreliable subcontractors. |
| t8 | Threat of exceeding the planned costs due to deadlines: due to the short implementation time, it will be necessary to hire additional contractors. |
| t9 | Threat of exceeding the planned costs due to weather conditions: the task is carried out in unsuitable weather conditions, and there are additional costs in order to maintain quality. |
| t10 | Threat of availability of materials at a given time: short completion time (e.g., a bridge is meant to be built, and the waiting time for the designed load-bearing structure is longer than the time for the completion of the contract). |
| t11 | Threat of investor’s preferences being unfavorable for the project: (e.g., when calculating an order, an alternative solution is assumed) replacement of the bridge structure with one that is available faster. |
| t12 | Threat related to the investor’s decision making: (e.g., the structure of the bridge is planned to be changed) there is a risk of delays in making decisions by the investor. |
| t13 | Threat of incurring costs too high for the purchase of materials and structures (e.g., the bridge structure is planned to be exchanged from plate girder beams to rolled beams, which are 40% cheaper and available faster). |
| t14 | Threat to the timely delivery of building materials: we need a bridge structure, and the schedule does not have enough time for possible delays. |
| Risk Mitigation Programs | ||
|---|---|---|
| Symbol | Description | Cost |
| r1 | Increasing the employment of “own employees” and conducting appropriate training. | c1 = 200,000 |
| r2 | Conducting on-site supervision. | c2 = 2500 |
| r3 | Carrying out geological surveys. | c3 = 5000 |
| r4 | Finding subcontractors and suppliers at the tender stage. | c4 = 10,000 |
| r5 | Detailed analysis of the project and the verification of the bill of quantities. | c5 = 4000 |
| r6 | Applying (at the tender stage) for making an appropriate provision in the contract in order to regulate the possibility of extending the time needed to perform the task without charging the contractor financial penalties. | c6 = 0 |
| r7 | Adding contractual penalties to the offer price for failure to meet the completion deadline. | c7 = 170,000 |
| r8 | Obtaining a structure supplier and guaranteeing delivery on time at the tender stage. | c8 = 25,000 |
| r9 | Acceptance of calculation provisions for performance difficulties (e.g., in the event of disagreement with the change in construction). | c9 = 110,000 |
| r10 | Replacement designs (e.g., a question to the investor regarding whether he will allow a change in the structure). | c10 = 20,000 |
| r11 | Acceptance of calculation provisions for the increase in material purchase costs. | c11 = 30,000 |
| Threat Mitigation Programs and Their Costs | Threats and the Binary Matrix B of the Impact of the Programs on These Threats | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| R | C | t1 | t2 | t3 | t4 | t5 | t6 | t7 | t8 | t9 | t10 | t11 | t12 | t13 | t14 |
| r1 | c1 | 1 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| r2 | c2 | 0 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| r3 | c3 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| r4 | c4 | 1 | 0 | 0 | 1 | 0 | 1 | 1 | 1 | 0 | 1 | 0 | 0 | 0 | 1 |
| r5 | c5 | 0 | 1 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| r6 | c6 | 1 | 0 | 0 | 0 | 1 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 |
| r7 | c7 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 1 |
| r8 | c8 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 1 |
| r9 | c9 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 |
| r10 | c10 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 1 | 1 | 1 | 0 |
| r11 | c11 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 |
| Rw | Threat Mitigation Programs | Cost cw | Total Cost |
|---|---|---|---|
| r1 | Increasing the employment of “own employees” and conducting appropriate training. | c1 = 200,000 | c1 + c2 + c4 + c10 + c11 = 262,500 |
| r2 | Conducting on-site supervision. | c2 = 2500 | |
| r4 | Finding subcontractors and suppliers at the tender stage. | c4 = 10,000 | |
| r10 | Replacement designs (e.g., a question to the investor regarding whether he or she will allow a change in the structure). | c10 = 20,000 | |
| r11 | Acceptance of calculation provisions for the increase in material purchase costs. | c11 = 30,000 | |
| r2 | Conducting on-site supervision. | c2 = 2500 | c2 + c4 + c6 + c10 + c11 = 62,500 |
| r4 | Finding subcontractors and suppliers at the tender stage. | c4 = 10,000 | |
| r6 | Applying (at the tender stage) for making an appropriate provision in the contract in order to regulate the possibility of extending the time needed to perform the task without charging the contractor financial penalties. | c6 = 0 | |
| r10 | Replacement designs (e.g., a question to the investor regarding whether he will allow a change in the structure). | c10 = 20,000 | |
| r11 | Acceptance of calculation provisions for the increase in material purchase costs. | c11 = 30,000 | |
| r4 | Finding subcontractors and suppliers at the tender stage. | c4 = 10,000 | c4 + c5 + c7 + c10 + c11 = 214,000 |
| r5 | Detailed analysis of the project and the verification of the bill of quantities. | c5 = 4000 | |
| r7 | Adding contractual penalties to the offer price for failure to meet the completion deadline. | c7 = 170,000 | |
| r10 | Replacement designs (e.g., a question to the investor regarding whether he or she will allow a change in the structure). | c10 = 20,000 | |
| r11 | Acceptance of calculation provisions for the increase in material purchase costs. | c11 = 30,000 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Budek-Wiśniewska, K.; Marcinkowski, R. A Method of Optimizing a Set of Programs for Mitigating Threats Related to the Undertaking of a Contract for the Execution of Construction Works. Sustainability 2021, 13, 12309. https://doi.org/10.3390/su132112309
Budek-Wiśniewska K, Marcinkowski R. A Method of Optimizing a Set of Programs for Mitigating Threats Related to the Undertaking of a Contract for the Execution of Construction Works. Sustainability. 2021; 13(21):12309. https://doi.org/10.3390/su132112309
Chicago/Turabian StyleBudek-Wiśniewska, Katarzyna, and Roman Marcinkowski. 2021. "A Method of Optimizing a Set of Programs for Mitigating Threats Related to the Undertaking of a Contract for the Execution of Construction Works" Sustainability 13, no. 21: 12309. https://doi.org/10.3390/su132112309
APA StyleBudek-Wiśniewska, K., & Marcinkowski, R. (2021). A Method of Optimizing a Set of Programs for Mitigating Threats Related to the Undertaking of a Contract for the Execution of Construction Works. Sustainability, 13(21), 12309. https://doi.org/10.3390/su132112309






