Reliable Requirements Engineering Practices for COVID-19 Using Blockchain
Abstract
1. Introduction
2. Literature Review
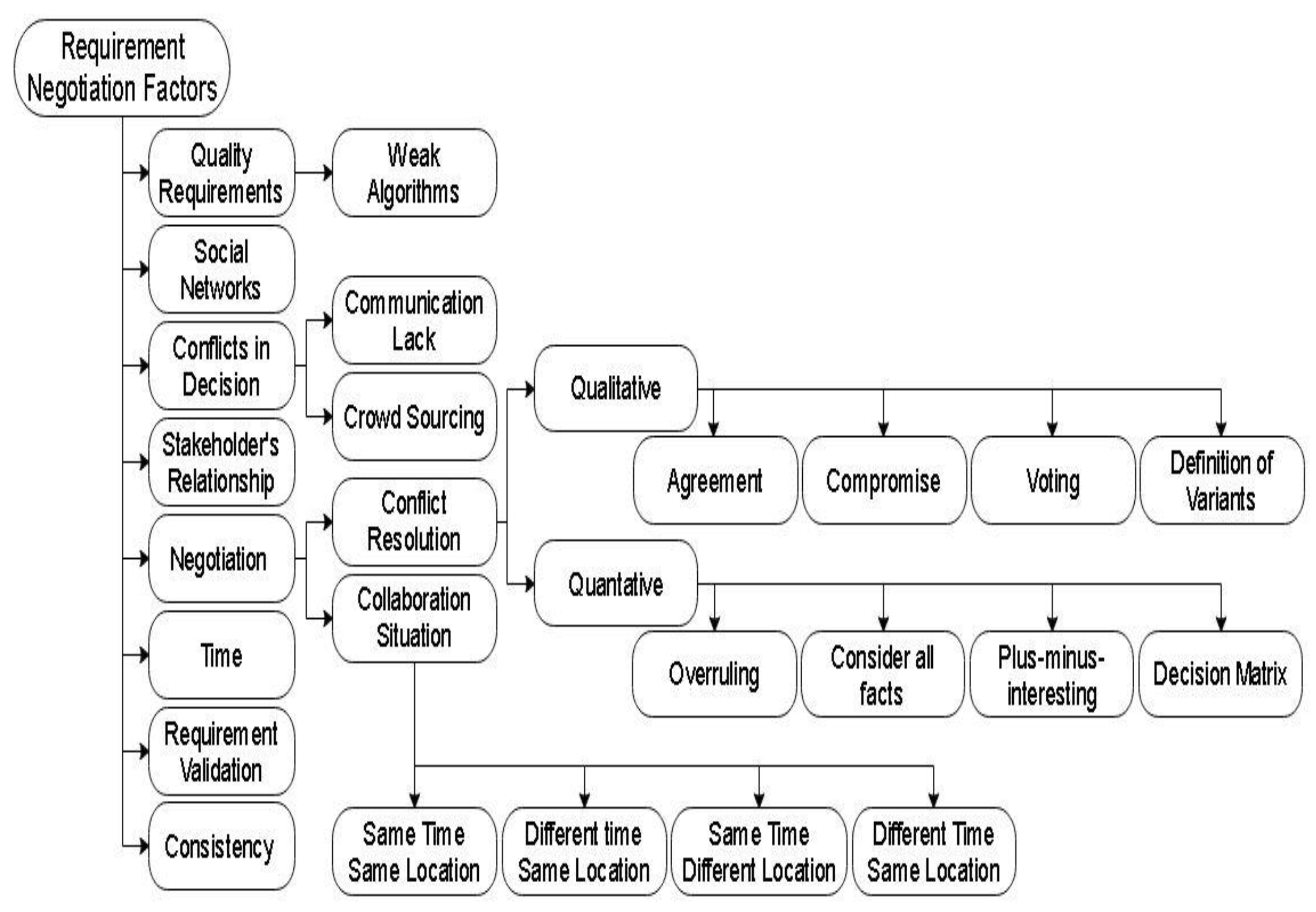
2.1. Quality
Weak Algorithms
2.2. Time
2.3. Social Network
2.4. Conflicts in Decision Making
2.4.1. Lack of Communication
2.4.2. Crowdsourcing
2.5. Power Relationship between Stakeholders
2.6. Consistency of Requirements
2.7. Requirement Validation
2.8. Requirement Negotiation
- Conflict resolution strategy
- Agreement: To negotiate a solution to the conflict, the stakeholders work together, which includes the discussions about views of each stakeholder to agree.
- Compromise: In this technique, all the stakeholders compromise on an acceptable solution that is generated after an analysis of various solutions.
- Voting: In this technique, the stakeholders simply vote in favor of the solution or against that solution, and the solution with high votes will be selected as the best solution.
- Definition of variants: In this technique, the preferred solution of stakeholders is implemented by applying their variants to the solution parameters. This is a qualitative technique [50].
- Overruling: In this technique, the solution of the most senior stakeholders is taken as the resolution. This technique works as the hierarchy of organizations.
- Consider all facts: In this technique, all the facts about specific conflicted requirements are considered and then prioritized in a readiness to be used as an input to the “Plus–Minus–Interesting” technique.
- Plus–Minus–Interesting: All the positive and negative facts of solutions alternative are analyzed in this technique. Two categories, one for Plus and one for Minus, are developed to list the positives and negatives. When a repercussion is neither a positive nor a negative item, it is placed in the Interesting column.
- Decision Matrix: The decision matrix consists of a comparison matrix of all key criteria to resolve a requirement conflict. These key criteria need to be considered against each solution alternative. The comparison of information in the matrix highlights the best solution to conflicts.
- 2.
- Collaboration situation
- Same time same location: The stakeholders collaborate at the same time and location. The face-to-face communication helps them communicate with each other easily.
- Different time same location: The stakeholders collaborate face to face, but their timings are different from each other. Thus, all the stakeholders cannot collaborate at the same time.
- Same time different location: The stakeholders collaborate at the same time but from different locations. Due to the communication gap, they face many problems and the rate of conflict between them is high.
- Different time different location: The stakeholders collaborate in different times and different location; due to the communication gap and different timing, conflicts arises.
2.9. Solution
- It facilitates people’s records with encryption and makes them secure and synchronized [55].
- Blockchain is allowing people to secure digital relationships that were impossible before because data is being disclosed, recorded, and secured differently [56].
- The main advantage of the Bitcoin-style blockchain systems is the immutability of data and decentralized authority [57].
- The decentralized feature of blockchain will help to create a decentralized ledger of requirements that will easily be accessible by stakeholders [58].
- The uniqueness of blockchain is that it is secure, immutable, and less costly [59].
- By using the blockchain platform in requirement negotiation, we can create requirement engineering practices that are more secure and accessible.
- It can help to gather and validate requirements easily for COVID-19 software projects [60].
- Blockchain technology integrates a series of technical systems with the following characteristics of decentralization, openness, autonomy, anonymity, security, and information that cannot be tempered [61].
3. Problem Statement
4. Objective
- To study the process of requirement elicitation, validation, and negotiation.
- To study blockchain-based frameworks.
- To study the strength and weaknesses of blockchain.
5. Research Questions
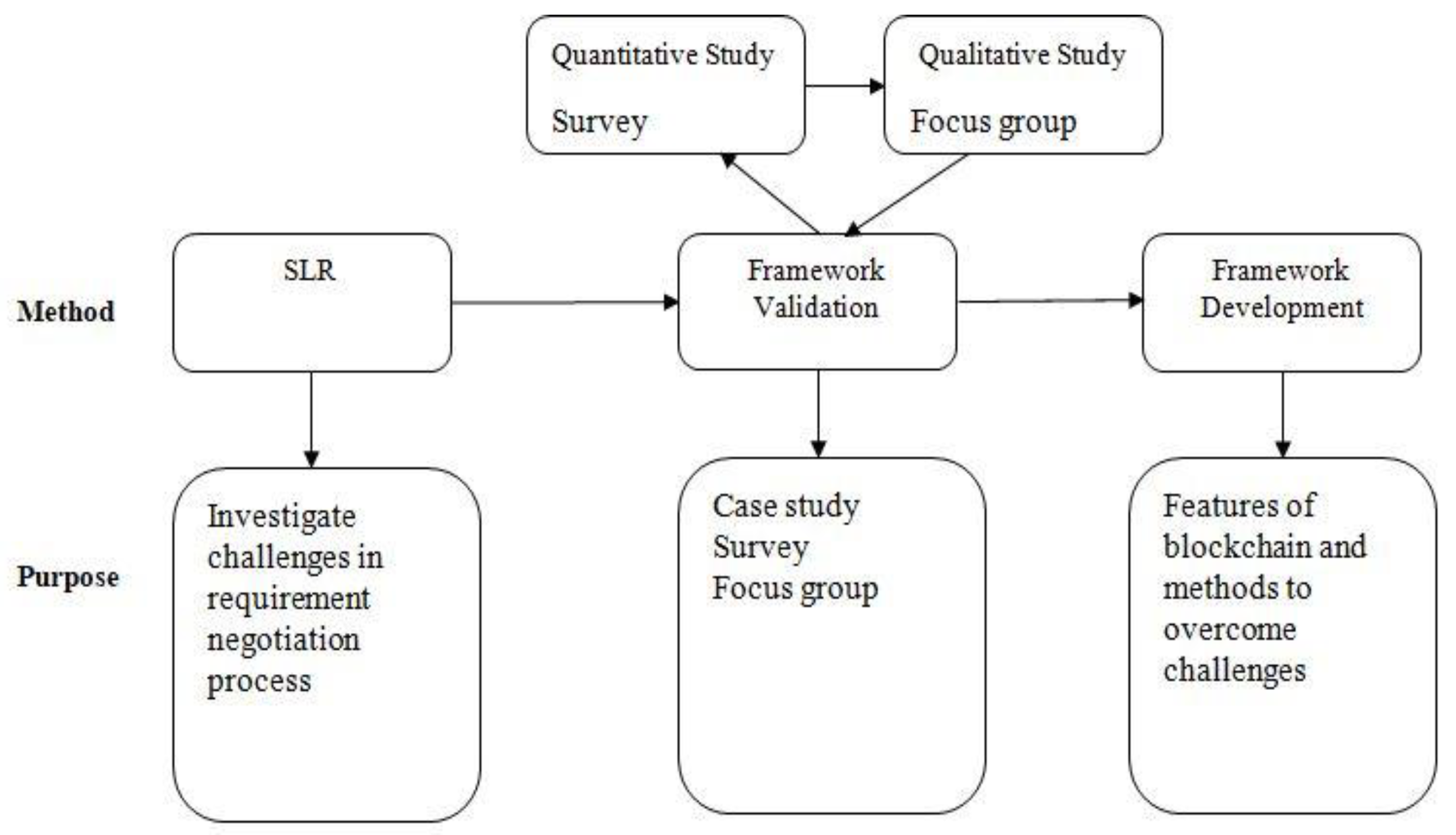
6. Methodology
7. Discussion
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Grünbacher, P.; Seyff, N. Requirements Negotiation. In Engineering and Managing Software Requirements; Springer Science and Business Media LLC: Berlin/Heidelberg, Germany, 2006; pp. 143–162. [Google Scholar]
- Ahmad, S. Negotiation in the Requirements Elicitation and Analysis Process. In Proceedings of the 19th Australian Conference on Software Engineering (aswec 2008), Perth, WA, Australia, 26–28 March 2008; pp. 683–689. [Google Scholar]
- Shahzad, B.; Said, A.M. Identification and Quantitative Analysis of Project Success Factors for Large Scale Projects. Int. J. Knowl. Soc. Res. 2014, 5, 83–95. [Google Scholar] [CrossRef][Green Version]
- Siddiqui, S.; Beg, M.; Fatima, S. Effectiveness of requirement prioritization using analytical hierarchy process (AHP) and planning game (PG): A comparative study. Int. J. Comput. Sci. Inf. Technol. 2013, 4, 46–49. [Google Scholar]
- Aurum, A.; Wohlin, C. Engineering and Managing Software Requirements; Springer: Berlin/Heidelberg, Germany, 2005. [Google Scholar]
- Kim, J.B.; Segev, A. A framework for dynamic eBusiness negotiation processes. In Proceedings of the IEEE International Conference on E-Commerce, Newport Beach, CA, USA, 24–27 June 2003; pp. 84–91. [Google Scholar]
- Su, S.Y.W.; Huang, C.; Hammer, J. A replicable Web-based negotiation server for e-commerce. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui, HI, USA, 7 January 2000. [Google Scholar]
- Saeed, M.S.; Sarwar, N.; Bilal, M. Efficient requirement engineering for small scale project by using UML. In Proceedings of the 2016 Sixth International Conference on Innovative Computing Technology (INTECH), Dublin, Ireland, 24–26 August 2016. [Google Scholar]
- Riaz, M.Q.; Rehman, F.U.; Maqbool, B.; Butt, W.H. Customization of requirement engineering best practices for Pakistan software industry. In Proceedings of the 2018 International Conference on Computing, Mathematics and Engineering Technologies (iCoMET), Sukkur, Pakistan, 3–4 March 2018. [Google Scholar]
- Lei, J.-Y.; Zhang, B.-C.; Fang, X.-H. Trust vector-based sensitive information protecting scheme in automatic trust negotiation. In Proceedings of the 2011 International Conference on Computer Science and Network Technology, Harbin, China, 24–26 December 2011; Volume 2, pp. 735–738. [Google Scholar]
- Anwer, S.; Ikram, N. Goal Oriented Requirement Engineering: A Critical Study of Techniques. In Proceedings of the 2006 13th Asia Pacific Software Engineering Conference (APSEC’06), Bangalore, India, 6–8 December 2006; pp. 121–130. [Google Scholar]
- Shahzad, B.; Abdullatif, A.M.; Ikram, N.; Mashkoor, A. Build Software or Buy: A Study on Developing Large Scale Software. IEEE Access 2017, 5, 24262–24274. [Google Scholar] [CrossRef]
- Shehzad, B.; Awan, K.M.; Lali, M.; Aslam, W. Identification of patterns in failure of software projects. J. Inf. Sci. Eng. 2017, 33, 1465–1479. [Google Scholar]
- Yu, S.; Lv, K.; Shao, Z.; Guo, Y.; Zou, J.; Zhang, B. A High Performance Blockchain Platform for Intelligent Devices. In Proceedings of the 2018 1st IEEE International Conference on Hot Information-Centric Networking (HotICN), Shenzhen, China, 15–17 August 2018; pp. 260–261. [Google Scholar] [CrossRef]
- Latifi, S.; Zhang, Y.; Cheng, L.-C. Blockchain-Based Real Estate Market: One Method for Applying Blockchain Technology in Commercial Real Estate Market. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 528–535. [Google Scholar]
- Chen, L.; Li, Y.; Wen, H.; Lei, W.; Hou, W.; Chen, J. Block Chain Based Secure Scheme For Mobile Communication. In Proceedings of the 2018 IEEE Conference on Communications and Network Security (CNS), Beijing, China, 30 May–1 June 2018; pp. 1–2. [Google Scholar]
- Makridakis, S.; Polemitis, A.; Giaglis, G.; Loucal, S. Blockchain current achievements and future prospects challenges combining AIBC. Future Internet 2019, 11, 258. [Google Scholar] [CrossRef]
- Mitani, T.; Otsuka, A. Traceability in permissioned blockchain. In Proceedings of the 2019 IEEE International Conference on Blockchain (Block-chain), Atlanta, GA, USA, 14–17 July 2019; pp. 286–293. [Google Scholar] [CrossRef]
- Malik, S.; Dedeoglu, V.; Kanhere, S.S.; Jurdak, R. TrustChain: Trust Management in Blockchain and IoT Supported Supply Chains. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 184–193. [Google Scholar]
- Peiyu, X.; Qian, Z.; Haining, W.; Haoyue, Z.; Chunyan, W. Exploration of Block chain Technology in Electric Power transaction. In Proceedings of the 2018 International Conference on Power System Technology (POWERCON), Guangzhou, China, 6–8 November 2018; Volume 2, pp. 729–733. [Google Scholar]
- Abdelatey, A.; Elkawkagy, M.; El-Sisi, A.B.; Keshk, A. RGSS-negotiation: A genetic-based approach for web service security negotiation. In Proceedings of the 2016 11th International Conference on Computer Engineering & Systems (ICCES), Cairo, Egypt, 20–21 December 2016; pp. 53–58. [Google Scholar] [CrossRef]
- Shahzad, B.; Afzal, T.; Irfan, R. Enhanced Risk Analysis-Relative Impact Factorization. In Proceedings of the 2005 International Conference on Information and Communication Technologies, Karachi, Pakistan, 27–28 August 2005. [Google Scholar]
- Elrakaiby, Y.; Ferrari, A.; Mylopoulos, J. CaRE: A refinement calculus for requirements engineering based on argumentation semantics. In Proceedings of the 2018 IEEE 26th International Requirements Engineering Conference (RE), Banff, AB, USA, 20–24 August 2018; pp. 364–369. [Google Scholar] [CrossRef]
- Gruenbacher, P. Collaborative requirements negotiation with EasyWinWin. In Proceedings of the 11th International Workshop on Database and Expert Systems Applications, London, UK, 4–8 September 2000; pp. 954–958. [Google Scholar]
- Mazón, J.-N.; Pardillo, J.; Trujillo, J. A model-driven goal-oriented requirement engineering approach for data ware-houses. Adv. Concept. Model. 2007, 4802, 255–264. [Google Scholar] [CrossRef]
- Shahzad, B.; Ullah, I.; Khan, N. Software Risk Identification and Mitigation in Incremental Model. In Proceedings of the 2009 International Conference on Information and Multimedia Technology, Jeju, Korea, 16-18 December 2009; pp. 366–370. [Google Scholar]
- Fricker, S.; Glinz, M. Comparison of Requirements Hand-off, Analysis, and Negotiation: Case Study. In Proceedings of the 2010 18th IEEE International Requirements Engineering Conference, Sydney, NSW, Australia, 27 September–1 October 2010; pp. 167–176. [Google Scholar]
- Shahzad, B.; Al-Wakeel, S. Software risk management and avoidance strategy. In Proceedings of the 2009 International Conference on Machine Learning and Computing, Perth, Australia, 10–12 July 2009; Volume 3. [Google Scholar]
- Nuseibeh, B.; Easterbrook, S.M. Requirements engineering: A roadmap. Proc. Conf. Future Softw. Eng. 2000, 1, 35–46. [Google Scholar]
- Arnuphaptrairong, T. Top ten lists of software project risks: Evidence from the literature survey. Int. Multi-Conference Eng. Comput. Sci. 2011, 1, 732–737. [Google Scholar]
- Baig, R.; Khan, W.A.; Haq, I.U.; Khan, I.M. Agent-Based SLA Negotiation Protocol for Cloud Computing. In Proceedings of the 2017 International Conference on Cloud Computing Research and Innovation (ICCCRI), Singapore, 11–12 April 2017; pp. 33–37. [Google Scholar]
- Seyff, N.; Hoyer, C.; Kroiher, E.; Grünbacher, P. Enhancing GSS-based Requirements Negotiation with Distributed and Mobile Tools. In Proceedings of the 14th IEEE International Workshops on Enabling Technologies: Infrastructure for Collaborative Enterprise (WETICE’05), Linköping, Sweden, 13–15 June 2005; pp. 87–92. [Google Scholar]
- van Lamsweerde, A. Goal-oriented requirements engineering: A roundtrip from research to practice. In Proceedings of the 12th IEEE Interna-tional Requirements Engineering Conference, Kyoto, Japan, 10 September 2004; pp. 3–6. [Google Scholar] [CrossRef]
- Tao, X.; Miao, Y. Interest Based Learning Activity Negotiation. In Proceedings of the 2008 International Conference on Cyberworlds, Hangzhou, China, 22–24 September 2008; pp. 58–64. [Google Scholar]
- Calefato, F.; Lanubile, F.; Romita, D.; Prikladnicki, R.; Pinto, J.H.S. Mobile speech translation for multilingual requirements meetings: A preliminary study. In Proceedings of the 2014 IEEE 9th International Conference on Global Software Engineering, Shanghai, China, 18–21 August 2014; pp. 145–152. [Google Scholar] [CrossRef]
- Valenca, G. Requirements negotiation model: A social oriented approach for software ecosystems evolution. In Proceedings of the 2013 21st IEEE International Requirements Engineering Conference (RE), Rio de Janeiro-RJ, Brazil, 15–19 July 2013; pp. 393–396. [Google Scholar]
- Agarwal, M.; Goel, S. Expert system and it’s requirement engineering process. In Proceedings of the International Conference on Recent Advances and Innovations in Engineering (ICRAIE-2014), Jaipur, India, 9–11 May 2014; pp. 1–4. [Google Scholar] [CrossRef]
- Pandey, D.; Suman, U.; Ramani, A. An Effective Requirement Engineering Process Model for Software Development and Requirements Management. In Proceedings of the 2010 International Conference on Advances in Recent Technologies in Communication and Computing, Kottayam, India, 16–17 October 2010; pp. 287–291. [Google Scholar]
- Mughal, S.; Abbas, A.; Ahmad, N.; Khan, S.U. A Social Network Based Process to Minimize In-Group Biasedness During Requirement Engineering. IEEE Access 2018, 6, 66870–66885. [Google Scholar] [CrossRef]
- Kukreja, N.; Boehm, B. Process implications of social networking-based requirements negotiation tools. In Proceedings of the 2012 International Conference on Software and System Process (ICSSP), Zurich, Switzerland, 2–3 June 2012; pp. 68–72. [Google Scholar]
- Boehm, B.; Egyed, A. Software requirements negotiation: Some lessons learned. In Proceedings of the 20th International Conference on Software Engineering, Kyoto, Japan, 6 August 2002; pp. 503–506. [Google Scholar]
- Kukreja, N. Winbook: A social networking based framework for collaborative requirements elicitation and WinWin ne-gotiations. In Proceedings of the 2012 34th International Conference on Software Engineering (ICSE), Zurich; 2012; pp. 1610–1612. [Google Scholar] [CrossRef]
- Schneider, K.; Karras, O.; Finger, A.; Zibell, B. Reframing societal discourse as requirements negotiation: Vision statement. In Proceedings of the 2017 IEEE 25th International Requirements Engineering Conference Workshops (REW), Lisbon, Portugal, 4–8 September 2017; pp. 188–193. [Google Scholar] [CrossRef][Green Version]
- Lenz, A.; Schoop, M. Decision Problems in Requirements Negotiations—Identifying the Underlying Structures. Bus. Inf. Syst. 2017, 293, 120–131. [Google Scholar]
- Zhu, S.; Hu, H.; Li, Y.; Li, W. Hybrid Blockchain Design for Privacy Preserving Crowdsourcing Platform. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 26–33. [Google Scholar]
- Yang, H.; Liang, P. Reasoning about Stakeholder Groups for Requirements Negotiation Based on Power Relationships. In Proceedings of the 2013 20th Asia-Pacific Software Engineering Conference (APSEC), Bangkok, Thailand, 2-5 December 2013; Volume 1, pp. 247–254. [Google Scholar]
- Seyff, N.; Betz, S.; Duboc, L.; Venters, C.; Becker, C.; Chitchyan, R.; Penzenstadler, B.; Nobauer, M. Tailoring Requirements Negotiation to Sustainability. In Proceedings of the 2018 IEEE 26th International Requirements Engineering Conference (RE), Banff, AB, Canada, 20–24 August 2018; pp. 304–314. [Google Scholar]
- Carvallo, J.P.; Franch, X. Requirements negotiation for multilayer system components. In Proceedings of the 2011 IEEE 19th International Requirements Engineering Conference, Washington, DC, USA, 29 August–2 September 2011; pp. 285–290. [Google Scholar]
- Bakhsh, S.T.; Shahzad, B.; Tahir, S. Risk management approaches for large scale software development. Inf. Sci. Eng. 2017, 33, 1547–1560. [Google Scholar] [CrossRef]
- Fernandes, J.M.; Machado, R.J. Requirements negotiation. Requir. Eng. Proj. 2016. [CrossRef]
- Liang, P.; Avgeriou, P.; Clerc, V. Requirements Reasoning for Distributed Requirements Analysis Using Semantic Wiki. In Proceedings of the 2009 Fourth IEEE International Conference on Global Software Engineering, Limerick, Ireland, 13–16 July 2009; pp. 388–393. [Google Scholar]
- Desai, H.; Kantarcioglu, M.; Kagal, L. A Hybrid Blockchain Architecture for Privacy-Enabled and Accountable Auctions. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 34–43. [Google Scholar]
- Park, A.; Li, H. The Effect of Blockchain Technology on Supply Chain Sustainability Performances. Sustainability 2021, 13, 1726. [Google Scholar] [CrossRef]
- Zhang, W.; Yuan, Y.; Hu, Y.; Huang, S.; Cao, S.; Chopra, A.; Huang, S. A Privacy-Preserving Voting Protocol on Blockchain. In Proceedings of the 2018 IEEE 11th International Conference on Cloud Computing (CLOUD), San Francisco, CA, USA, 2–7July 2018; pp. 401–408. [Google Scholar]
- Chen, Z.; Chen, S.; Xu, H.; Hu, B. A Security Authentication Scheme of 5G Ultra-Dense Network Based on Block Chain. IEEE Access 2018, 6, 55372–55379. [Google Scholar] [CrossRef]
- Wang, K.; Kim, H.S. FastChain: Scaling Blockchain System with Informed Neighbor Selection. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 376–383. [Google Scholar]
- Wang, G.; Shi, Z.; Nixon, M.; Han, S. ChainSplitter: Towards Blockchain-Based Industrial IoT Architecture for Supporting Hierarchical Storage. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 166–175. [Google Scholar]
- Linoy, S.; Mahdikhani, H.; Ray, S.; Lu, R.; Stakhanova, N.; Ghorbani, A. Scalable Privacy-Preserving Query Processing over Ethereum Blockchain. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 398–404. [Google Scholar]
- Catalini, C.; Gans, J.S. Some simple economics of the blockchain. Commun. ACM 2020, 63, 80–90. [Google Scholar] [CrossRef]
- Wan, L.; Eyers, D.; Zhang, H. Evaluating the Impact of Network Latency on the Safety of Blockchain Transactions. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 194–201. [Google Scholar]
- Wang, R.; He, J.; Liu, C.; Li, Q.; Tsai, W.-T.; Deng, E. A Privacy-Aware PKI System Based on Permissioned Blockchains. In Proceedings of the 2018 IEEE 9th International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 23–25 November 2018; pp. 928–931. [Google Scholar]
- Xu, T.; Li, T.; Liu, L.; Bryant, B.R. Negotiating Service Requirements among Strategic Actors. In Proceedings of the 2010 IEEE 34th Annual Computer Software and Applications Conference Workshops, Seoul, Korea, 19–23 July 2010; pp. 31–36. [Google Scholar]
- Salman, T.; Jain, R.; Gupta, L. A reputation management framework for knowledge-based and probabilistic block-chains. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 520–527. [Google Scholar] [CrossRef]
- Sharma, S.G.; Ahuja, L.; Goyal, D.P. Building Secure Infrastructure for Cloud Computing Using Blockchain. In Proceedings of the 2018 Second International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 14–15 June 2018; pp. 1985–1988. [Google Scholar] [CrossRef]
- Brito, J.; Castillo, A. Summary for policymakers. Clim. Change 2013, 29, 1–30. [Google Scholar] [CrossRef]
- Cui, G.; Shi, K.; Qin, Y.; Liu, L.; Qi, B.; Li, B. Application of block chain in multi-level demand response reliable mechanism. In Proceedings of the 2017 3rd ICIM, Chengdu, China, 21–23 April 2017; pp. 337–341. [Google Scholar] [CrossRef]
- Guo, H.; Li, W.; Nejad, M.; Shen, C.-C. Access control for electronic health records with hybrid blockchainedge architecture. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 44–51. [Google Scholar] [CrossRef]
- Nakasumi, M. Information sharing for supply chain management based on blockchain technology. In Proceedings of the IEEE 19th Conference on Business Informatics, Thessaloniki, Greece, 24–27 July 2017. [Google Scholar] [CrossRef]
- Yang, X.; Chen, Y.; Chen, X. Effective Scheme against 51% Attack on Proof-of-Work Blockchain with History Weighted Information. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 261–265. [Google Scholar]
- Li, S.; Xiao, H.; Wang, H.; Wang, T.; Qiao, J.; Liu, S. Blockchain Dividing based on node community clustering in intelligent manufacturing CPS. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 124–131. [Google Scholar] [CrossRef]
- Yang, S.; Chen, Z.; Cui, L.; Xu, M.; Ming, Z.; Xu, K. CoDAG: An Efficient and Compacted DAG-Based Blockchain Protocol. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 314–318. [Google Scholar]
- Stuart, H.; Scott, S.W. How to time-stamp a digital document. J. Cryptol. 1991, 3, 12. [Google Scholar]
- Davenport, A.; Shetty, S. Air Gapped Wallet Schemes and Private Key Leakage in Permissioned Blockchain Platforms. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 541–545. [Google Scholar]
- Peng, R.; Ye, Q.; Ye, M. A requirements maturity measurement approach based on SKLSE Wiki. In Proceedings of the 2010 IEEE 34th Annual Computer Software and Applications Conference Workshops, Seoul, Korea, 19–23 July 2010; pp. 251–254. [Google Scholar] [CrossRef]
- In, H.; Olson, D.; Rodgers, T. A requirements negotiation model based on multi-criteria analysis. In Proceedings of the Fifth IEEE International Symposium on Requirements Engineering, Toronto, ON, Canada, 7 August 2000; pp. 312–313. [Google Scholar] [CrossRef]
- Dubois, E.; Kritikos, K.; Kubicki, S. An Automatic Requirements Negotiation Approach for Business Services. In Proceedings of the 2011 IEEE Ninth European Conference on Web Services, Lugano, Switzerland, 14–16 September 2011; pp. 133–140. [Google Scholar]
- Miller, T.W. Do family risk factors influence attention deficit hyperactivity disorder via disruption of neurocognitive functioning? Diss. Abstr. Int. Sect. B Sci. Eng. 2010, 70, 6560. [Google Scholar] [CrossRef]
- He, Y.; Zhu, M.; Zheng, C. An efficient and minimum sensitivity cost negotiation strategy in automated trust negotiation. In Proceedings of the 2008 International Conference on Computer Science and Software Engineering, Wuhan, China, 12–14 December 2008; pp. 182–185. [Google Scholar] [CrossRef]
- Makridakis, S.; Polemitis, A.; Giaglis, G.; Louca, S. Blockchain: Current Achievements, Future Prospects/Challenges and Its Combination with AI; Faculty University of Nicosia, Members of the Blockchain/AI Team: Cyprus, Nicosia, 2017; pp. 1–21. [Google Scholar]
- Iqbal, N.; Sang, J. Fuzzy Logic Testing Approach for Measuring Software Completeness. Symmetry 2021, 13, 604. [Google Scholar] [CrossRef]
- da Silva, A.; Savić, D. Linguistic Patterns and Linguistic Styles for Requirements Specification: Focus on Data Entities. Appl. Sci. 2021, 11, 4119. [Google Scholar] [CrossRef]
- Yang, C.; Wu, L.; Yu, C.; Zhou, Y. A Phrase-Level User Requests Mining Approach in Mobile Application Reviews: Concept, Framework, and Operation. Information 2021, 12, 177. [Google Scholar] [CrossRef]
| Ref. | Key Factors | Merits | Demerits |
|---|---|---|---|
| [1] | Need to improve requirement engineering, the negotiation process | Help in pinpointing requirement negotiation process | A human being is performing the role of moderator, high chance of human error, not secure |
| [8] | A module-based integrated model is proposed and demonstrated with UML modeling | Produce a quality product | Not synchronized, techniques are not applicable on all types of expert systems, a requirement not defined properly |
| [9] | “Customized requirement engineering practices followed by the software development organization of Pakistan” | “Help us to understand the gaps in the requirement engineering process of Pakistan’s organizations and other developing countries” | Not prioritize efficiently, time consuming |
| [11] | “Synthesizes the underlying concepts of GORE concerning coverage of requirement engineering activities” | Make requirements clear | Not for large projects, not synchronized, time consuming |
| [25] | How to model goals and information requirements for data warehouses, and how to derive a conceptual multidimensional model | “Helps to provides the required information to support the decision-making process” | Not synchronized, techniques are not able to give the accurate results from different expert systems, requirements not defined properly |
| [29] | Better modeling and analysis of problem domains, development of richer models for capturing and analyzing non-functional requirements | Helps to find out an overview of software system requirement engineering. Helps to find challenges in software engineering | Not prioritized efficiently, time consuming |
| [38] | Model implementation for successful software development and requirement management | Helps to produce quality software products by its model | Other elicitation techniques can also be used, requirement validation is not used |
| [23] | Propose a refinement calculus for requirements engineering (Care) for gathering accurate requirements | Helps to refine to create accurate unambiguous and complete requirements | Lacks proper semantics, not a cost-effective evaluation |
| [33] | Adding goals in the requirement negotiation process | To improve the quality of requirement negotiation | “Progress in RE activities are felt to be harder to measure, the benefits of using RE technologies are felt to be hard to measure, requirements documents are generally perceived as big, complex, outdated, and too far away from the executable products customers are paying for” |
| Ref. | Key Factors | Merits | Demerits |
|---|---|---|---|
| [4] | “The results reveal that the intuitive and quick PG technique is superior to [the] AHP technique” | Two techniques of requirement prioritization are described, which help in making requirement negotiation. | Other models are neglected, time consuming, changeable, centralized |
| [1] | “To motivate the need for negotiation in requirements engineering to introduce fundamental concepts and terminology, and to provide an overview about negotiation research” | “Presenting a general negotiation process, typical negotiation stages. Framework covering important dimensions of requirements negotiation comprising the conflict resolution strategy, the collaboration situation of the stakeholders, and the degree of negotiation tool support discussing and classifying existing negotiation tools using the general process and framework” | Not for large projects, not synchronized, time-consuming |
| [44] | “Identifies decision problem structures in software requirements negotiations using a literature-based research approach” | “Helps to select appropriate scenarios of decision problem structures in software requirements negotiations” | Not for large projects, not synchronized, time consuming |
| [50] | Explains requirement negotiation process and its dimensions | Helps to identify the purpose of doing requirement negotiation | Not synchronized, techniques cannot be used for every kind of system, a requirement not defined properly |
| [6] | To create requirement negotiation process systematic | Systematic requirements Prioritize requirements | Time-consuming |
| [7] | Introduces a replicable web-based framework | To create a bargaining-type negotiating process that is easier with the framework | Complex and time and efforts consuming |
| [74] | Concept requirement maturity is proposed to give a degree to requirements | Prioritize requirements by their given maturity level | We should use approach improvement. Stability analysis, large-scale trial usage extension |
| [75] | “Offer useful tools to aid stakeholders [in the] negotiation process” | Helps rank the requirements | “Option generation and negotiation planning, criteria exploration and objective assessment for option score and criteria weight, systematic post-analysis for agreement and graphical support” |
| [31] | “Propose a formal model of Service Level Agreement (SLA)-based negotiations” | “Allows agent-based multi-round SLA negotiation for making dynamic offers influenced by varying client requirements, different pricing models, and decision strategies” | Multiple rules, multiple providers, multiple rounds, complex, not dynamic, and customized |
| [76] | “Proposes a broker-based BS negotiation framework that can automatically determine the non-functional requirements” | Helps to determine non-functional requirements and create a difference between functional and non-functional requirements | “Integration of this work with a BS composition approach” |
| [78] | “The policies participating trust negotiation is modeled as a Negotiation Petri Net, and a trust negotiation MSC strategy is proposed” | To use for security requirements in which user can trust that they are the best | “Complete trust negotiation model, which includes credential and policy rules, the trust negotiation strategies, consistency detectors, etc., will be built for the project |
| [24] | “Easy WinWin has been successfully applied to real-client custom development projects” | Improved involvement and interaction Defined process, support for different collaboration scenarios, improved prioritization, and elaboration of issues | Not efficient with the latest technology |
| [27] | “Evaluated the relative effect of requirements hand-off, analysis, and negotiation on requirements and design volatility and requirements understanding” | Ease challenges in the collaboration between marketing and development | “Address the understanding of requirements communication by evaluating the product manager’s evolving requirements understanding” |
| [32] | “Research in distributed and mobile requirement negotiation, describe the Easy WinWin, identify issues in face-to-face negotiations” | “Overcome issues with distributed and mobile tools. Broadband face-to-face interactions [and the] distributed ARENA II tool provides sufficient support for distributed teams” | “Complete, correct, and consistent requirements, quality of the gathered requirements need to be evaluated” |
| [34] | “Proposed an interest-based learning activity negotiation system” | “Negotiation learning content/activity plays an important role in effective learning; learners will have more opportunities to learn in a personalized style and with adaptive content” | Needs adoption of other knowledge models such as cognitive maps, or Bayesian networks |
| [35] | To overcome language problems among stakeholders who are remotely negotiating, software requirements including machine translation and speech recognition are merged to generate a mobile speech translator | Overcome language gap | Results are not confirmed |
| [62] | An automated service negotiation framework is introduced in these parties as negotiators are involved, who negotiate to reach an agreement | Negotiators can choose different negotiation strategies according to their preference and their requirements and preference | Develop negotiation mechanism experimental service platform, which is called Safary, |
| [2] | Introduced negotiation spiral model | “Well-aligned requirements by all the stakeholders, improved system quality, a sound basis for resource estimation, and less resource wastage | “Negotiation process because of tacit individual and undeclared perspectives perceptions will lead a sub-optimal set of requirements” |
| [40] | Introduced Winbook with a social networking-based way of capturing and negotiating | Improve the requirement negotiation process | Time-consuming |
| [46] | “Make use of the basic principles of requirements negotiation and define reasoning rules to reason about stakeholder groups for requirements negotiation, based on an extended i* modeling framework” | Improve power relationships between stakeholders | Still, there are challenges that affect the power relationship between stakeholders |
| [43] | “Discourse is reframed as a requirements process, suggest using techniques of requirements engineering (RE) and Crowd RE, propose video as a medium for communicating problems” | “With the explicit goal to state software, hardware, and organizational requirements, getting stakeholders involved“ | “Can be used directly for developing innovative software, which will speed up the implementation of a decision” |
| [48] | “Presenting software quality models as a framework to support the negotiation of both initial and rising requirements and the settlement of stakeholders’ concerns” | Approach supporting requirement negotiation between stakeholders and solving their conflicts | The approach did not present significant drawbacks |
| [36] | “How requirements negotiation collaborates to ecosystem’s health and success, defining negotiation strategies along Software Ecosystem evolution considering the Software Platform Management” | To develop improved quality software ecosystems | Not discussing the results after implementation |
| [21] | “An automated genetic-based approach for security negotiation among services is conducted” | Improving security, to get an acceptable security level for both sides | Securing only the web service and not covering all the conditions of web service |
| [41] | “Using an instrumented version of the USC WinWin groupware system” | To increase the quality of requirements | Not suitable for the latest technology-based negotiation |
| [47] | “Extended the WinWin Negotiation Model by incorporating sustainability concepts” | “Includes the ability to consider the impact of requirements on sustainability, [which] also allows practitioners to reflect on requirements and their effects on sustainability” | Further validate the initial findings and answer open questions |
| [10] | “A trust vector-based sensitive information protecting scheme is presented based on the existing schemes” | Recovers bugs, improved reliability | Not very efficient according to the advancement in technology |
| [42] | Collaborative requirements elicitation and management | WinWin negotiation framework is used to give better management in the requirement negotiation process on social media | “Could use with a relatively low learning curve and continually monitor the commitment status of the teams” |
| [30] | Investigate common risk factors and proposed the top ten lists of software risks | Helps in project planning and control purposes during the project execution | Repetitions in the model, not secure, complex |
| [37] | “Basic introduction of expert systems consisting of their composition, and basic characteristics and advantages” | “Helps to find suitable and best techniques during requirement engineering process, [which] is vital” | Techniques discussed are time-consuming, not secure |
| [39] | “Address the bias problem while identifying and prioritizing stakeholders” | “Identified the stakeholders and their requirements more efficaciously; prioritized the stakeholders significantly” | Not covering all the application areas |
| [77] | “Blockchain architecture as a new system solution to supply a reliable mechanism for secure and efficient medical record exchanges” | “Revolutionize the e-Health industry with greater efficiency by eliminating many of the intermediates” | Does not prioritize efficiently, time consuming |
| [51] | “Focus on the reasoning support, which is not fairly addressed by existing Semantic Wikis” | To help find requirements that are complex and different from all requirements | Cost and time effectiveness |
| [24] | Providing knowledge about handling risk factors occurring in software development | Strategies are provided to reduce risk factors | Strategies are provided for a comprehensive list of risk factors |
| [3] | Software project factors are identified, prioritized, and discussed in this research | The most important factors for software success are cost, time, and effort | Data are not gathered from latest projects success rate |
| [13] | Categories of risks according to their dimensions are identified, listed, and discussed | Helps to identify that budget, time, and complexity of process are the most important factors to improve | These identified risks can further be handled with the latest technologies |
| [12] | Factors are identified for both build versus buy software | Factors defined that need improvement in both build and buy software cases | Applicable on limited types of software |
| [22] | “Determines relative impact of risk factors on the software development activities” | “Relative impact ratio ensures determining the direct and indirect impacts of risk on all activities of software development” | “Risks factors can be better identified, and by using the avoidance strategies, they can be better avoided” |
| [26] | “A thorough handling and avoidance strategy is proposed for the identification of risk factors when the incremental model is used for software development” | “Advised strategies are expected to provide a helping hand for the avoidance or mitigation of a risk factor” | “Identified risk factors may grow in future and so can be the mitigation and avoidance strategies” |
| [49] | Proposes a Risk Reduction Model that minimizes risk and reduces the cost of development for large-scale projects without spending too many resources | Minimize risks, budget, resources, and time | Not applicable for small scale projects |
| Ref. | Key Factors | Merits | Demerits |
|---|---|---|---|
| [14] | Design a high-performance blockchain platform, using technologies | Efficient connection provides higher consensus efficiency while guaranteeing the decentralization, provides higher efficiency | Repetitions in the model, not secure, complex |
| [53] | Discussed whether Blockchain platform can improve the performance of supply chain sustainability | Positive impacts of blockchain on three pillars of sustainability, governance, social equity and protection. | This article neither do not estimates correlations and do not finds casual inference between performance of performance of sustainability and blockchain based supply chain. |
| [73] | Using air-gapped wallet techniques | Most secure implementation possible, provides an upper bound on wallet security, can help the user identify the weakest parts of their air-gapped wallet scheme | Wallet analysis and quantification |
| [71] | Propose a compacted DAG-based blockchain protocol CoDAG that greatly improves the throughput and performance of blockchain | Improve the linear structure of traditional blockchain protocol | Tune the parameters for better performance; combine with hybrid consensus to improve the throughput further |
| [45] | Propose a novel hybrid blockchain crowdsourcing platform to achieve decentralization and privacy preservation | Ensure secure communication between their users and the workers, decentralization, and privacy preservation | Test the performance of the public chain as well as the interaction between the public chain and the subchains |
| [58] | Proposed system uses big data processing techniques | Provides a secure, robust, and scalable way to process SQL queries over any blockchain | Time delays |
| [16] | Proposed a blockchain for mobile communication | Secure communication | Techniques discussed are time-consuming, not secure |
| [79] | Discussing blockchain achievements and future work | Helps to find future work in blockchain | Other elicitation techniques can also be used, requirement validation is not used |
| [20] | Combining the transaction link of energy “Internet with blockchain technology” | “Can effectively solve the transaction friction, maintain the order of the market, and guarantee the legitimacy of the transaction” | Not covering all the application areas |
| [44] | “The principle of fast authentication with an APG-PBFT algorithm is present in this paper | Can reduce the authentication frequency | Not prioritized efficiently, time consuming |
| [59] | Identify the cost of verification and networking | Gives an overview of cost factors of blockchain | Repetitions in the model, not secure, complex |
| [64] | Presents blockchain and compares the various platforms on which blockchain can be implemented | Illustrates the use of blockchain applications for building the secure infrastructure of cloud computing | Techniques discussed are time consuming, not secure |
| [65] | Introduction and explanation of bitcoin, Brito and Castillo both support innovation, clarity | Helps to understand the process of Bitcoin and digital trading using Bitcoin | Other elicitation techniques can also be used, requirement validation is not used |
| [66] | “Private blockchain is chosen to solve the problem of mutual trust between users, load aggregators, and power grids in multi-level demand–response reliable communication” | Demand response automation problem will be solved easily | Not covering all the application areas |
| [68] | “New life cycle model of power internet financial products was proposed under the blockchain effects” | Helps to improve the quality of software projects | Not for large projects, not synchronized, time-consuming |
| [72] | “Propose computationally practical procedures for digital time-stamping” | “Infeasible for a user either to back-date or to forward date his document, even with the collusion of a time-stamping service” | Not synchronized, techniques are not working for every expert system, requirements not defined properly |
| [10] | Identification of future prospects challenges in blockchain technology | Helps to improve the quality of blockchain-based frameworks | Not identifying all the future prospects |
| [52] | “Propose a novel hybrid blockchain architecture that combines private and public blockchain to allow sensitive bids to be opened on a private blockchain” | “Only the auctioneer can learn the bids, and no one else, efficient in terms of run time and monetary cost” | “Create a framework for multiple blockchains hosting different applications and show how we can better preserve privacy when private, public, and consortium blockchains are combined” |
| [61] | “Proposes a privacy-aware PKI system based on permission BCs” | “The separation of user registration and authorization, and has the characteristics of anonymity and conditional traceability, to protect users’ identity privacy” | “Security can be further improved” |
| [54] | “Propose a native blockchain voting protocol for peers to vote over their existing blockchain network without the need of any trusted or third party” | “Facilitates decision making in a decentralized and secure manner, end-to-end privacy, and possesses desirable properties such as detect ability and correct ability against cheating” | “Need to perform formal security analysis, potential security attacks, such as cartel attack, should be tested against the design” |
| [63] | The framework is applied to malicious node detection where malicious agents are excluded from blockchain consensus | Detecting and excluding malicious nodes | Can use for consensus calculation, where agent contribution depends on their prior performances |
| [67] | “Propose a hybrid architecture of using both blockchain and edge nodes to impose attribute-based access control of EHR data” | “To execute smart contracts to impose ACL policy and to record legitimate access events into blockchain” | “Investigate novel consensus protocol designs for the proposed mechanism to achieve better performance” |
| [70] | “Construct a trust relationship model according to the equipment communication characteristics of intelligent manufacturing CPS system” | “Can make statistical analysis of communication data in the system, improve the concurrency of the system” | Can be further improved |
| [15] | “Using employment of blockchain in RE market and represent the facilities it can give to the RE market” | “Offer meaningful tools for a game-theoretic stable-priced market, process integrity, network reliability and longevity, faster transactions, and lower transaction costs” | The architecture proposed can be more flexible and simpler |
| [57] | “Proposed a hierarchical storage structure to store the majority of the blockchain in clouds, and maintain the most recently generated blocks in a blockchain overlay network” | “Maintain both blocks and transactions generated by the IoT networks” | “Work on the implementation of the proposed blockchain-based IoT architecture in more real IoT applications” |
| [69] | “Proposed an approach to increase the cost of a successful 51% double-spending attack on Proof-of-Work types of blockchain protocols” | “Utilizes the frequency rate of miners in history blocks and calculates the total Historical Weighted Difficulty to determine if a branch switch is needed, can improve smaller blockchain security drastically with easy integration” | Only applicable on Ethereum |
| [60] | Investigate the impact of a wide range of network latency configuration on blockchain security | Quantify blockchain security | Time spent |
| [56] | “Propose fast chain to scale the effective block rate of blockchain systems” | “Reduces the block propagation time through its informed neighbor selection policy, effective when nodes have different mining powers” | “Time can be reduced by more effective techniques” |
| [18] | “Proposed the scheme that the transactions and their history in the permissioned blockchain can be verified and concealed from the permission-less blockchain” | “Transactions and their history in a permissioned blockchain can be verified and concealed from a permission-less blockchain” | “Time consuming” |
| [19] | “Proposed a trust management framework for blockchain-based supply chain applications” | “Address the issue of trust associated with the quality of commodities and the entities logging data on the blockchain” | “Different network models will affect the average throughput and latency of the system” |
| No. | Blockchain Methodological Contribution |
|---|---|
| 1. | Help to gather correct complete requirements |
| 2. | Requirement engineering processes will be secure |
| 3. | Requirement engineering processes will be easily accessible |
| 4. | Will reduce their time and efforts of developers with improved quality of requirements |
| 5. | Will ensure consistency and synchronization of requirements |
| 6. | The failure rate of projects will be reduced |
| 7. | The rate of successful projects will be increased |
| No. | Blockchain Research Contribution |
|---|---|
| 1. | Researchers will easily negotiate for data elicitation and validation |
| 2. | Students will further use blockchain for better performance of methods and algorithms used in software engineering |
| 3. | The quality of the requirement negotiation process will be improved |
| 4. | Help researchers to gather quality data. |
| 5. | Requirements will be prioritized according to their importance and need |
| 6. | Requirements will be validated |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shahzad, B.; Javed, I.; Shaikh, A.; Sulaiman, A.; Abro, A.; Ali Memon, M. Reliable Requirements Engineering Practices for COVID-19 Using Blockchain. Sustainability 2021, 13, 6748. https://doi.org/10.3390/su13126748
Shahzad B, Javed I, Shaikh A, Sulaiman A, Abro A, Ali Memon M. Reliable Requirements Engineering Practices for COVID-19 Using Blockchain. Sustainability. 2021; 13(12):6748. https://doi.org/10.3390/su13126748
Chicago/Turabian StyleShahzad, Basit, Iqra Javed, Asadullah Shaikh, Adel Sulaiman, Ahsanullah Abro, and Muhammad Ali Memon. 2021. "Reliable Requirements Engineering Practices for COVID-19 Using Blockchain" Sustainability 13, no. 12: 6748. https://doi.org/10.3390/su13126748
APA StyleShahzad, B., Javed, I., Shaikh, A., Sulaiman, A., Abro, A., & Ali Memon, M. (2021). Reliable Requirements Engineering Practices for COVID-19 Using Blockchain. Sustainability, 13(12), 6748. https://doi.org/10.3390/su13126748









