Cybersecurity Policy and the Legislative Context of the Water and Wastewater Sector in South Africa
Abstract
1. Introduction
2. Cybersecurity Policy and Legislative Environment
2.1. International System
2.1.1. International Cybersecurity Stakeholders
- African Union
- African Network Information Centre
- Council of Europe
- Forum of Incident Response and Security Teams (FIRST)
- International Criminal Police Organisation (Interpol)
- International Telecommunication Union
- Southern African Development Community
- United Nations
2.1.2. International Cybersecurity Laws
- The Budapest Convention
- The ITU Global Cybersecurity Agenda
- UN General Assembly resolution 70/237
- UN General Assembly resolution 73/27
- UN General Assembly resolution 73/266
- WSIS Geneva Plan of Action
2.1.3. International Water-Specific Cybersecurity Challenges
2.2. National System
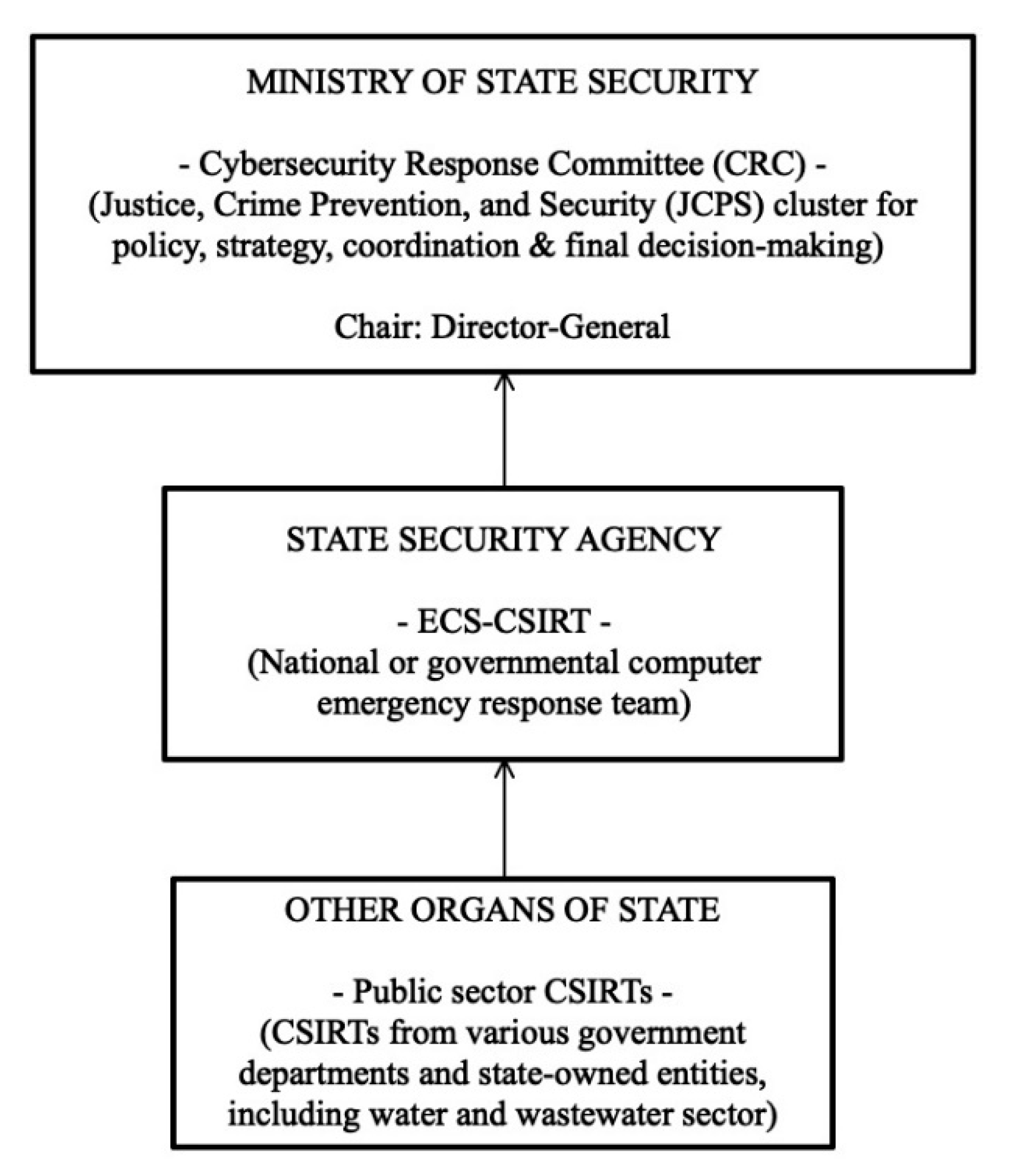
2.2.1. National Cybersecurity Stakeholders
- State Security Agency (SSA)
- -
- Electronic Communications Security—Cyber Security Incidents Response Team (ECS-CSIRT)
- -
- Cybersecurity Centre
- Department of Communications and Digital Technologies (DCDT)
- -
- National Cybersecurity Hub
- -
- Cyber Inspectorate
- -
- National Cybersecurity Advisory Council
- Department of Defence (DoD)
- -
- Cyber Command
- -
- Centre Headquarters
- South African Police Service (SAPS)
- -
- Cyber Crime Centre
- Department of Justice and Constitutional Development
- -
- National Prosecuting Authority
- Department of Trade, Industry and Competition
- Department of Public Service and Administration
- Department of International Relations and Cooperation
- Department of Science and Innovation
- Public sector Cyber Security Incidents Response Teams (CSIRTs)
- Industry CSIRTs
- State Information Technology Agency
- South African Revenue Service
2.2.2. National Cybersecurity Legislation and Policies
- Constitution of the Republic of South Africa of 1996
- Broadband Infraco Act 33 of 2007
- Companies Act 71 of 2008
- Consumer Protection Act 68 of 2008
- Competition Act 89 of 1998
- Copyright Act 98 of 1978
- Corporate Governance of Information and Communications Technology Framework
- Critical Infrastructure Protection Act (CIPA) 8 of 2019
- Cryptography regulations
- Cybercrimes Bill of 2019 (waiting for assent by the President)
- Cyber Warfare Strategy
- Defence Review
- Designs Act 195 of 1993
- E-government strategy and roadmap (national)
- E-government strategy for each province
- Electronic Communications and Transactions Act 25 of 2002 (ECT Act)
- Electronic Communications Act 36 of 2005
- Films and Publications Act 65 of 1996
- Financial Intelligence Centre Act 38 of 2001
- Independent Communications Authority of South Africa Act 13 of 2000
- Inter-Governmental Relations Framework of 2005
- King IV Report on Corporate Governance
- National Archives and Record Service of South Africa Act 43 of 1996
- National Development Plan
- National Cybersecurity Policy Framework
- National Prosecutions Act 32 of 1998
- Prevention of Organized Crime Act 38 of 1999
- Promotion of Access to Information Act (PAIA) 25 of 2002
- Protection of Constitutional Democracy against Terrorism and Related Activities Act 33 of 2004
- Protection of Personal Information (POPI) Act 4 of 2013
- Protection of State Information Bill
- Protection from Harassment Act 17 of 2011
- Promotion of Equality and Prevention of Unfair Discrimination Act 4 of 2000
- Public Service Act: Regulation
- Regulation of Interception of Communications and Provision of Communication-related Information Act 70 of 2002 (or RICA)
- State Information Technology Agency Act 88 of 1998
- Trade Marks Act 194 of 1993
2.2.3. National Cybersecurity Challenges
2.3. Sector System
2.3.1. Water Stakeholders
- Parliament Portfolio Committee
- National Department of Water and Wastewater
- Regional Department of Water and Wastewater
- Provincial governments
- Local governments (municipalities as water service authorities, or water service providers through subcontractors)
- Water boards/regional water utilities
- Catchment management agencies
- Water-user associations
- Water Research Commission
- Trans-Caledon Tunnel Authority
- Water Tribunal
- Water trading entity
2.3.2. Water Legislation and Policies
- Constitution of the Republic of South Africa of 1996—Chapter 2, sections 10, 24(a), 27(1)(b), 27(2), and 152(1)(d); Chapter 6, section 139(1); Chapter 7, section 154(1); Schedule 4, Part B
- Housing Act 107 of 1997
- National Water Act 36 of 1998
- Water Services Act 108 of 1997
- Water Research Act 34 of 1971
- National Environmental Management Act 107 of 1998
- Local Government: Municipal Structures Act 117 of 1998
- Local Government: Municipal Systems Act 32 of 2000
- Strategic Framework on Water Services of 2003
- Chapter 4 of the National Development Plan
- National Water Policy Review of 2013
- National Wastewater Policy of 2016
- Water and Wastewater Climate Change Policy of 2017
- National Water Resources Strategy, Second Edition, of 2013
- White Paper on Basic Household Wastewater of 2001
- White Paper on National Water Policy for South Africa of 1997
- White Paper on Water Supply and Wastewater of 1994
- National Water and Wastewater Master Plan of 2019
2.3.3. Water Cyber Critical Infrastructure Protection Challenges
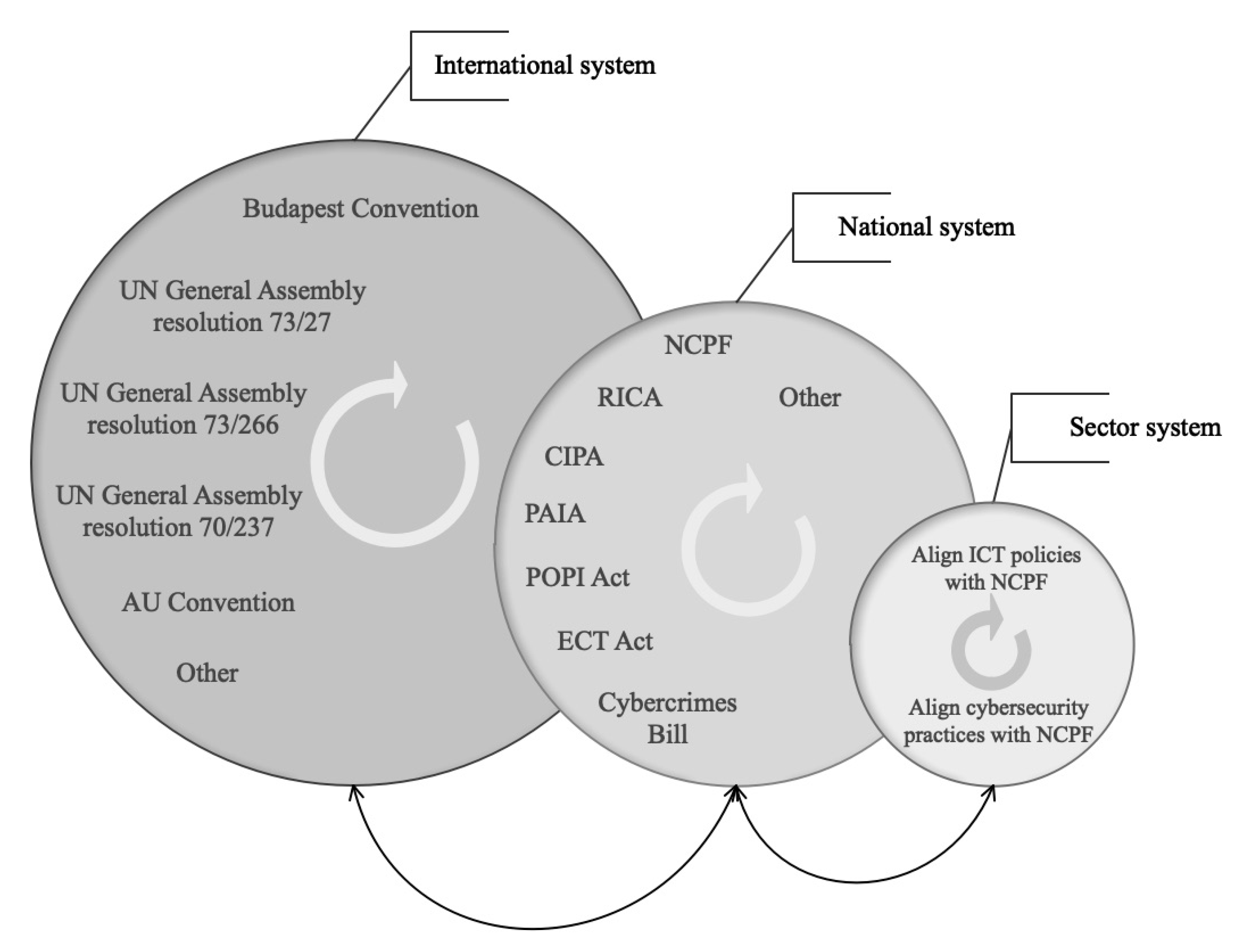
2.4. Systems Interrelationships
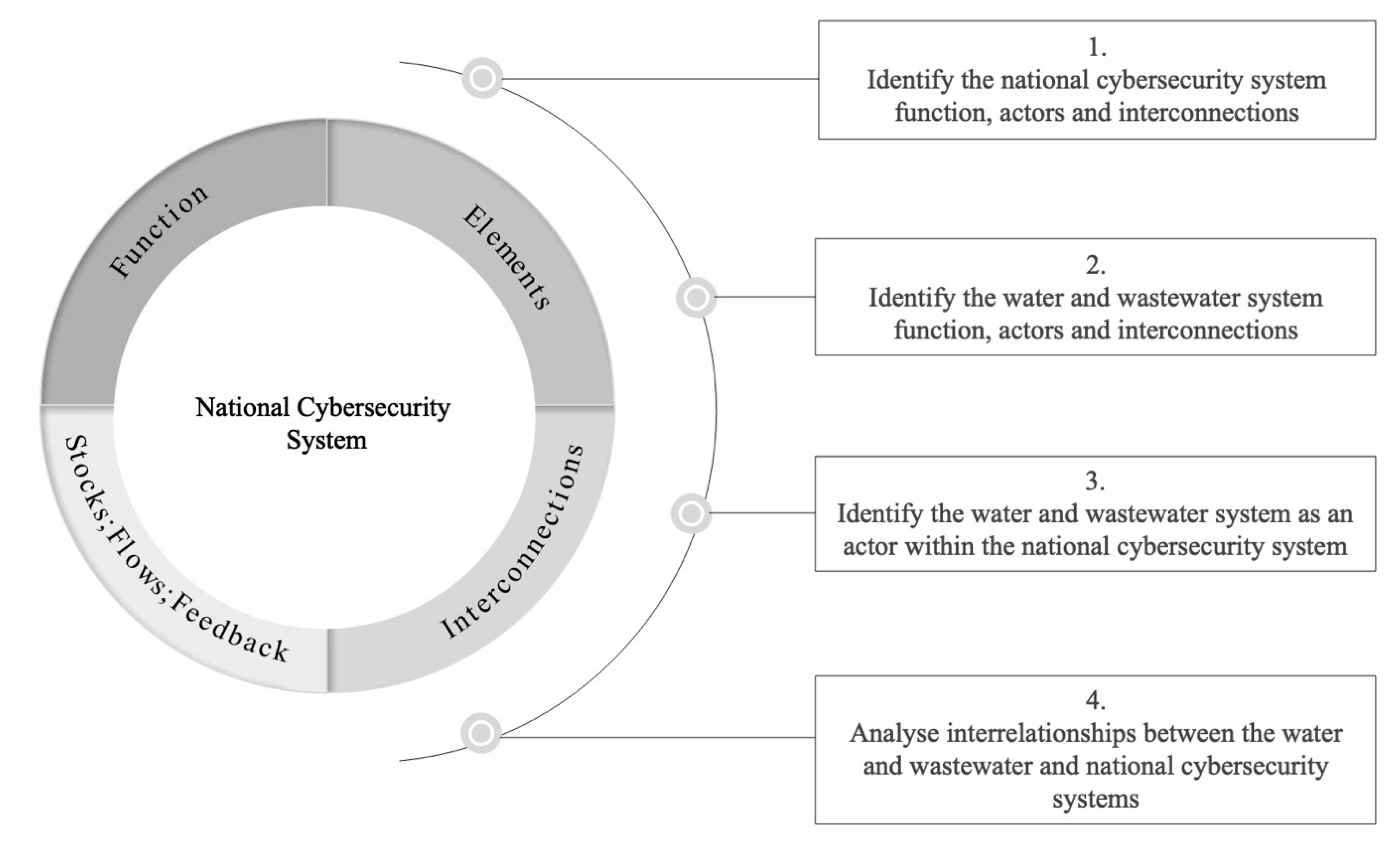
3. Materials and Methods
4. Results
4.1. Identify the National Cybersecurity System Function, Actors and Interconnections
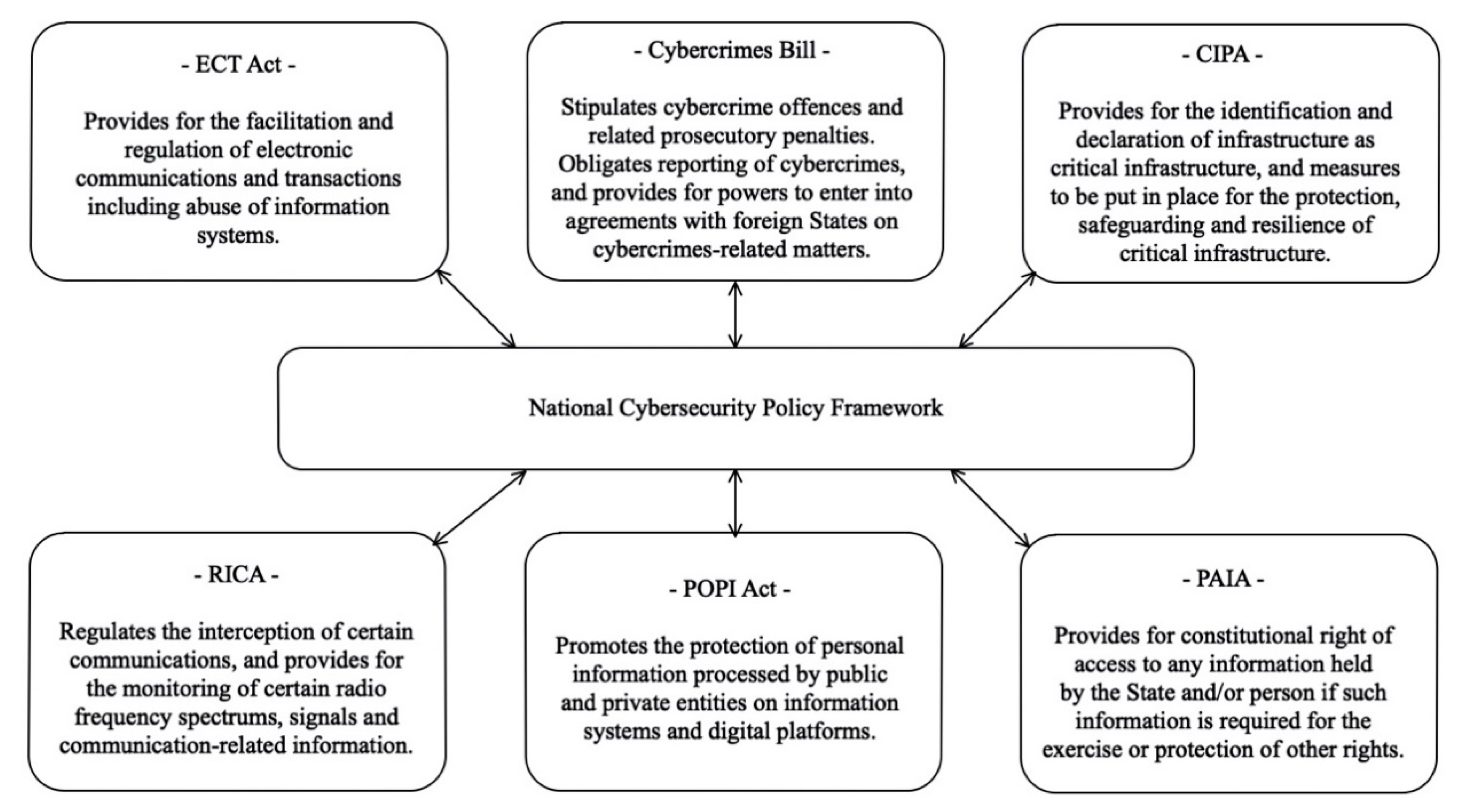
- Subsections 16.4(b) and 16.4(c) of the NCPF mandate the DCDT to establish the National Cybersecurity Advisory Council and Cybersecurity Hub, which in turn is tasked to encourage and facilitate the establishment of industry CSIRTs, whereas Chapter 12 of the ECT Act mandates the same government department to establish a Cyber Inspectorate unit and appoint cyber inspectors. Firstly, no Cyber Inspectorate unit has ever been established and no cyber inspectors were ever appointed to date. Secondly, except for the banking industry, which has SABRIC, there are few other industry CSIRTs, even those are not actively coordinated for information sharing and incidents recording in a national database. Lastly, the National Cybersecurity Advisory Council is non-existent or at least its activities, if any, are not visible.
- The NCPF recognises and encourages cybersecurity education for technical skills development, user awareness campaigns, and research and development in Section 2.7 of the policy. However, there are no visible and coordinated nation-wide activities to address insufficient technical cybersecurity skills and user awareness campaigns in the country.
- The CIPA provides for infrastructure resilience, albeit without explicitly stating whether this includes cyber resiliency. Moreover, the SAPS is yet to develop regulations to implement the Act.
- Despite the existence of the different pieces of cybersecurity-related legislation and policies, there seems to be a lack of capacity and capability by law enforcement agencies in fighting cybercrimes in South Africa.
4.2. Identify the Water and Wastewater System Function, Actors and Interconnections
4.3. Identify the Water and Wastewater System as an Actor in the National Cybersecurity System
4.4. Analyse Interrelations between the Water and Wastewater and National Cybersecurity Systems
5. Discussion
6. Recommendations
- The National Cybersecurity Advisory Council, and/or Cybersecurity Hub, and/or Cyber Inspectorate unit should either be moved from the DCDT, or their operating models and mandates be reviewed, or a combination of both.
- The Critical Infrastructure Protection Act should be amended to explicitly include “cyber” and/or “digital or information” infrastructure in its definitions of “infrastructure” and “critical infrastructure” terms.
- To boost capacity and capability in fighting cybercrimes in the sort-term, South African law enforcement agencies may need to partner with international stakeholders such as Interpol and similar others to develop cybercrimes and digital forensics skills. For medium to long term solutions, the law enforcement agencies should recruit the best and brightest students with passion and a keen interest in cybercrimes and digital forensics from local universities.
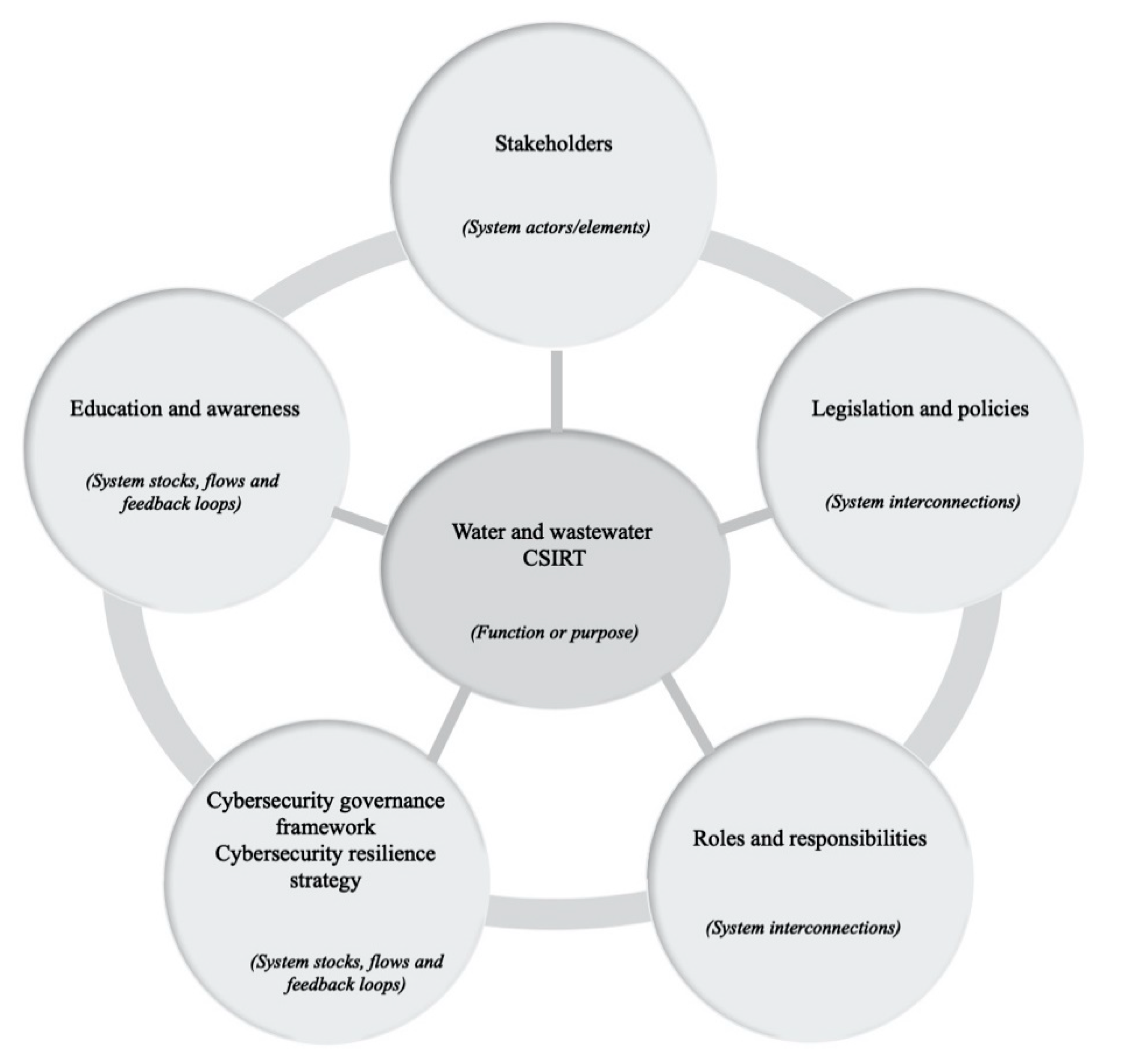
- Establish a sector computer security incidents response team. Establish the national water CSIRT that will have specialist teams serving both the IT and ICS cybersecurity requirements to help formulate and implement the cybersecurity governance framework, resilience strategy, and education and awareness campaigns. Although the establishment of the CSIRT to be hosted at the DWS requires no development of new legislation and/or policies or amendments of existing ones, the authors recommend that a sector-specific agency be established. This would indeed require either the development of a new piece of legislation or amendment of the CIPA and probably the National Water Act. The rationale behind this recommendation is based on international best practices where it would appear that sector-specific agencies for each classified critical infrastructure sector are the best way to look after the cybersecurity requirements of a sector.
- Develop a sector cybersecurity governance framework. Probably most of the sector stakeholders have a cybersecurity governance framework at organisational level based largely, if not solely, on corporate IT security requirements. Such stakeholders merely need to align these with the NCPF as stipulated in Section 16.7 of the policy and incorporate ICS cybersecurity requirements where applicable. At sector level, a governance framework would help with facilitating the exchange of cybersecurity information, sharing of knowledge and collaboration, skills development, and rapid responses to incidents.
- Develop a sector cybersecurity resilience strategy. Cybersecurity resilience refers to a critical infrastructure’s capability to anticipate, withstand, adapt and/or rapidly recover from any cyber terrorism, cybercriminal activities, cyber vandalism, cyber sabotage, accidents, or naturally occurring threats or human error induced infrastructure failure. This refers more to the water and wastewater ICS as critical infrastructure. Likewise, at sector level, a cybersecurity resilience strategy would help with ICS cybersecurity information exchange, knowledge sharing and collaboration, skills development, and rapid recovery from any deliberate cyberattacks, accidents, or naturally occurring threats or incidents.
- Encourage sector members to have documented ICS cybersecurity policies and procedures. The water and wastewater sector members who either own and/or operate a critical infrastructure (or water ICS) should be encouraged to have documented ICS cybersecurity policies and procedures separate from the corporate IT security policies and procedures in their security operations centres.
- Develop a sector cybersecurity education and skills development strategy. A coordinated skills development programme in collaboration with the Cybersecurity Hub in the DCDT, Cybersecurity Centre in the SSA, and other external stakeholders as stipulated in the NCPF should be initiated through the water CSIRT. The sector can partner with academic institutions such as the University of Johannesburg and ICS vendors to develop a formal but customised ICS cybersecurity training and certification programme. This could bolster the specialist domain of ICS cybersecurity in the country tremendously as IT security already has an established body of knowledge and certification programmes. Ultimately, though, the desired picture is to have a cross-functional team of cybersecurity experts in the CSIRT sector to share their varied domain knowledge and experiences to evaluate and mitigate risk in the sector. Thus, cybersecurity operation centres in member organisations should comprise both IT security and specialist ICS cybersecurity experts where applicable.
- Develop a sector cybersecurity awareness campaign strategy. Coordinated sector-wide cybersecurity education and awareness campaigns should become regular occurrences.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
Appendix A. Analysis of the National Cybersecurity Policy Framework System
| Researcher | Stakeholders (Elements/Actors) | Legislation and Policies (Interconnections) | Gaps or Identified Challenges |
|---|---|---|---|
| [100] | Domestic
| ||
| [101] | Foreign
|
| |
| [102] | Foreign
|
| |
| [36] | Domestic
|
|
|
| [66] | Domestic
|
| |
| [38] | Domestic
|
|
|
| [103] | Domestic
|
| |
| [57] |
| ||
| [63] | Domestic
|
|
|
| [37] | Domestic
|
|
|
| [104] |
|
|
References
- UN. Make the SDGs a Reality. Available online: https://web.archive.org/web/20201110154701/https://sdgs.un.org/#goal_section (accessed on 10 November 2020).
- White, R. Risk analysis for critical infrastructure protection. In Critical Infrastructure Security and Resilience. Advanced Sciences and Technologies for Security Applications; Gritzalis, D., Theocharidou, M., Stergiopoulos, G., Eds.; Springer: Cham, Switzerland, 2019; pp. 35–54. [Google Scholar]
- Birkett, D.; Mala-Jetmarova, H. Plan, prepare and safeguard: Water critical infrastructure protection in Australia. In Securing Water and Wastewater Systems: Protecting Critical Infrastructure; Clark, R.M., Hakim, S., Eds.; Springer International Publishing: Cham, Switzerland, 2014; pp. 287–313. [Google Scholar]
- Zabašta, A.; Juhna, T.; Tihomirova, K.; Rubulis, J.; Ribickis, L. Latvian practices for protecting water and wastewater infrastructure. In Securing Water and Wastewater Systems: Protecting Critical Infrastructure; Clark, R.M., Hakim, S., Eds.; Springer International Publishing: Cham, Switzerland, 2014; pp. 315–342. [Google Scholar]
- Möderl, M.; Rauch, W.; Achleitner, S.; Lukas, A.; Mayr, E.; Neunteufel, R.; Perfler, R.; Neuhold, C.; Godina, R.; Wiesenegger, H.; et al. Austrian activities in protecting critical water infrastructure. In Securing Water and Wastewater Systems: Protecting Critical Infrastructure; Clark, R.M., Hakim, S., Eds.; Springer International Publishing: Cham, Switzerland, 2014; pp. 343–373. [Google Scholar]
- Tiirmaa-Klaar, H. Building national cyber resilience and protecting critical information infrastructure. J. Cyber Policy 2016, 1, 94–106. [Google Scholar] [CrossRef]
- Alexander, A.; Graham, P.; Jackson, E.; Johnson, B.; Williams, T.; Park, J. An analysis of cybersecurity legislation and policy creation on the state level. In National Cyber Summit (NCS) Research Track. NCS 2019. Advances in Intelligent Systems and Computing; Choo, K.K., Morris, T., Peterson, G., Eds.; Springer: Cham, Switzerland, 2020; Volume 1055, pp. 30–43. [Google Scholar]
- Burmeister, O.; Phahlamohlaka, J.; Al-Saggaf, Y. Good governance and virtue in South Africa’s cyber security policy implementation. Int. J. Cyber Warf. Terror. 2015, 5, 19–29. [Google Scholar] [CrossRef][Green Version]
- Jansen van Vuuren, J.; Leenen, J.; Zaaiman, J.J. Using an ontology as a model for the implementation of the national cybersecurity policy framework for South Africa. In Proceedings of the 9th International Conference on Cyber Warfare and Security 2014 (ICCWS 2014), West Lafayette, IN, USA, 24–25 March 2014; pp. 107–115. [Google Scholar]
- Ismail, S.; Sitnikova, E.; Slay, J. Using integrated system theory approach to assess security for SCADA systems cyber security for critical infrastructures: A pilot study. In Proceedings of the 11th International Conference on Fuzzy Systems and Knowledge Discovery (FSKD 2014), Xiamen, China, 19–21 August 2014; pp. 1000–1006. [Google Scholar]
- NIST. Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1. Available online: https://web.archive.org/web/20201109030328/https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf (accessed on 10 November 2020).
- Rasekh, A.; Hassanzadeh, A.; Mulchandani, S.; Modi, S.; Banks, M.K. Smart water networks and cyber security. J. Water Resour. Plan. Manag. 2016, 142, 1–3. [Google Scholar] [CrossRef]
- Hassanzadeh, A.; Rasekh, A.; Galelli, S.; Aghashahi, M.; Taormina, R.; Ostfeld, A.; Banks, M.K. A review of cybersecurity incidents in the water sector. J. Environ. Eng. 2020, 146, 03120003. [Google Scholar] [CrossRef]
- Hahn, A. Operational technology and information technology in industrial control systems. In Cyber-Security of SCADA and Other Industrial Control Systems: Advances in Information Security; Colbert, E.J.M., Kott, A., Eds.; Springer International Publishing: Cham, Switzerland, 2016; Volume 66, pp. 51–68. [Google Scholar]
- Sullivan, D.; Luiijf, E.; Colbert, E.J.M. Components of industrial control systems. In Cyber-Security of SCADA and Other Industrial Control Systems: Advances in Information Security; Colbert, E.J.M., Kott, A., Eds.; Springer International Publishing: Cham, Switzerland, 2016; Volume 66, pp. 15–28. [Google Scholar]
- Weiss, J. Industrial Control System (ICS) cyber security for water and wastewater systems. In Securing Water and Wastewater Systems: Protecting Critical Infrastructure; Clark, R.M., Hakim, S., Eds.; Springer International Publishing: Cham, Switzerland, 2014; pp. 87–105. [Google Scholar]
- White, R.; George, R.; Boult, T.; Chow, C.E. Apples to apples: RAMCAP and emerging threats to lifeline infrastructure. Homel. Secur. Aff. 2016, 12, 1–20. [Google Scholar]
- Ramotsoela, D.; Abu-Mahfouz, A.; Hancke, G. A survey of anomaly detection in industrial wireless sensor networks with critical water system infrastructure as a case study. Sensors 2018, 18, 2491. [Google Scholar] [CrossRef] [PubMed]
- Purvis, B.; Mao, Y.; Robinson, D. Three pillars of sustainability: In search of conceptual origins. Sustain. Sci. 2019, 14, 681–695. [Google Scholar] [CrossRef]
- Clark, R.M.; Panguluri, S.; Nelson, T.D.; Wyman, R.P. Protecting drinking water utilities from cyberthreats. J. Am. Water Works Assoc. 2017, 109, 50–58. [Google Scholar] [CrossRef]
- Barbier, E.B.; Burgess, J.C. The sustainable development goals and the systems approach to sustainability. Econ. E-J. 2017, 11, 1–22. [Google Scholar] [CrossRef]
- Chowdhury, R. Systems Thinking for Management Consultants: Flexible Systems Management; Springer International Publishing: Singapore, 2019. [Google Scholar]
- Fiksel, J. Systems Thinking. In Resilient by Design: Creating Businesses that Adapt and Flourish in a Changing World; Fiksel, J., Ed.; Island Press: Washington, DC, USA, 2015; pp. 35–50. [Google Scholar]
- Chung, A.; Dawda, S.; Hussain, A.; Shaikh, S.A.; Carr, M. Cybersecurity: Policy. In Encyclopedia of Security and Emergency Management; Shapiro, L., Maras, M.H., Eds.; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Srinivas, J.; Das, A.K.; Kumar, N. Government regulations in cyber security: Framework, standards and recommendations. Future Gener. Comput. Syst. 2019, 92, 178–188. [Google Scholar] [CrossRef]
- Brechbühl, H.; Bruce, R.; Dynes, S.; Johnson, M.E.E. Protecting critical information infrastructure: Developing cybersecurity policy. Inf. Technol. Dev. 2010, 16, 83–91. [Google Scholar] [CrossRef]
- OECD. Cybersecurity Policy Making at a Turning Point: Analysing a New Generation of National Cybersecurity Strategies for the Internet Economy. Available online: https://web.archive.org/web/20201017142718/http://www.oecd.org/sti/ieconomy/cybersecurity%20policy%20making.pdf (accessed on 10 November 2020).
- UNECE. Working Party on Regulatory Cooperation and Standardization Policies (WP.6)—Report on the Sectoral Initiative on Cyber Security. 2019. Available online: https://web.archive.org/web/20201217093616/https://undocs.org/pdf?symbol=en%2FECE%2FCTCS%2FWP.6%2F2019%2F9 (accessed on 17 December 2020).
- Sabillon, R.; Cavaller, V.; Cano, J. National Cyber Security Strategies: Global Trends in Cyberspace. Int. J. Comput. Sci. Softw. Eng. 2016, 5, 67–81. [Google Scholar]
- WMO. Water and Cyber Security—Protection of Critical Water-Related Infrastructure. Available online: https://web.archive.org/web/20201118080434/https://public.wmo.int/en/events/meetings/water-and-cyber-security-protection-of-critical-water-related-infrastructure-online (accessed on 17 December 2020).
- Dlamini, I.Z.; Taute, B.; Radebe, J. Framework for an African policy towards creating cyber security awareness. In Proceedings of the Southern African Cyber Security Awareness Workshop (SACSAW 2011), Gaborone, Botswana, 12 May 2011; pp. 15–31. [Google Scholar]
- Budapest Convention. Convention on Cybercrime, European Treaty Series—No. 185. Available online: https://web.archive.org/web/20200724075610/https://www.europarl.europa.eu/meetdocs/2014_2019/documents/libe/dv/7_conv_budapest_/7_conv_budapest_en.pdf (accessed on 10 November 2020).
- Clough, J. A world of difference: The Budapest convention on cybercrime and the challenges of harmonisation. Monash Univ. Law Rev. 2014, 40, 698–736. [Google Scholar]
- Wicki-Birchler, D. The Budapest Convention and the General Data Protection Regulation: Acting in concert to curb cybercrime? Int. Cybersecur. Law Rev. 2020, 1, 63–72. [Google Scholar] [CrossRef]
- Budapest Convention. Chart of Signatures and Ratifications of Treaty 185: Convention on Cybercrime, Status as of 05/11/2020. Available online: https://web.archive.org/web/20201110182746/https://www.coe.int/en/web/conventions/full-list/-/conventions/treaty/185/signatures?p_auth=9UQ3WQaH (accessed on 10 November 2020).
- Ntsaluba, N. Cybersecurity Policy and Legislation in South Africa. Master’s Thesis, University of Pretoria, Pretoria, South Africa, 2017. [Google Scholar]
- Detecon. E-Commerce, Cybercrime and Cybersecurity—Status, Gaps and the Road Ahead. Available online: https://web.archive.org/web/20201110182612/https://www.dtps.gov.za/index.php?option=com_phocadownload&view=category&download=121%3A20131126_policy-review_e-commerce-cybercrime-and-cybersecurity_final&id=39%3Ae-commerce-cyber-security&Itemid=143 (accessed on 10 November 2020).
- Sutherland, E. Governance of cybersecurity-the case of South Africa. Afr. J. Inf. Commun. 2017, 20, 83–112. [Google Scholar] [CrossRef]
- Coleman, D. Digital colonialism: The 21st century scramble for Africa through the extraction and control of user data and the limitations of data protection laws. Mich. J. Race Law 2019, 24, 417–439. [Google Scholar]
- AU Convention. List of Countries Which Have Signed, Ratified/Acceded to the African Union Convention on Cyber Security and Personal Data Protection. Available online: https://au.int/sites/default/files/treaties/29560-sl-AFRICAN%20UNION%20CONVENTION%20ON%20CYBER%20SECURITY%20AND%20PERSONAL%20DATA%20PROTECTION.pdf (accessed on 5 November 2020).
- UN. Resolution Adopted by the General Assembly on 23 December 2015. Available online: https://web.archive.org/web/20200913145346/https://undocs.org/en/A/RES/70/237 (accessed on 10 November 2020).
- WSIS. Basic Information: About WSIS. Available online: https://web.archive.org/web/20201110172646/https://www.itu.int/net/wsis/basic/about.html (accessed on 10 November 2020).
- UN. Open-Ended Working Group. Available online: https://web.archive.org/web/20201110172949/https://www.un.org/disarmament/open-ended-working-group/ (accessed on 10 November 2020).
- UN. Group of Governmental Experts. Available online: https://web.archive.org/web/20201110173326/https://www.un.org/disarmament/group-of-governmental-experts/ (accessed on 10 November 2020).
- Janke, R.; Tryby, M.; Clark, R.M. Protecting water supply critical infrastructure: An overview. In Securing Water and Wastewater Systems: Protecting Critical Infrastructure; Clark, R.M., Hakim, S.S., Eds.; Springer International Publishing: Cham, Switzerland, 2014; pp. 29–85. [Google Scholar]
- Clark, R.M.; Hakim, S. Securing Water and Wastewater Systems: Global Experiences; Springer International Publishing: Cham, Switzerland, 2014. [Google Scholar]
- Spathoulas, G.; Katsikas, S. Towards a secure Industrial Internet of Things. In Security and Privacy Trends in the Industrial Internet of Things: Advanced Sciences and Technologies for Security Applications; Alcaraz, C., Ed.; Springer International Publishing: Cham, Switzerland, 2019; pp. 29–45. [Google Scholar]
- CISA. Alert (AA20-352A): Advanced Persistent Threat Compromise of Government Agencies, Critical Infrastructure, and Private Sector Organizations. Available online: https://web.archive.org/web/20201218004033/https://us-cert.cisa.gov/ncas/alerts/aa20-352a (accessed on 18 December 2020).
- Galinec, D.; Možnik, D.; Guberina, B. Cybersecurity and cyber defence: National level strategic approach. Automatika 2017, 58, 273–286. [Google Scholar] [CrossRef]
- Birkett, D.M. Water critical infrastructure security and its dependencies. J. Terror. Res. 2017, 8, 1–21. [Google Scholar] [CrossRef]
- Chung, J.J. Critical infrastructure, cybersecurity, and market failure. Or. Law Rev. 2018, 96, 441–476. [Google Scholar]
- Bernieri, G.; Pascucci, F. Improving Security in Industrial Internet of Things: A Distributed Intrusion Detection Methodology. In Security and Privacy Trends in the Industrial Internet of Things: Advanced Sciences and Technologies for Security Applications; Alcaraz, C., Ed.; Springer International Publishing: Cham, Switzerland, 2019; pp. 161–179. [Google Scholar]
- Krotofil, M.; Kursawe, K.; Gollmann, D. Securing industrial control systems. In Security and Privacy Trends in the Industrial Internet of Things: Advanced Sciences and Technologies for Security Applications; Alcaraz, C., Ed.; Springer International Publishing: Cham, Switzerland, 2019; pp. 3–26. [Google Scholar]
- Clark, R.M.; Hakim, S.; Panguluri, S. Protecting water and wastewater utilities from cyber-physical threats. Water Environ. J. 2018, 32, 384–391. [Google Scholar] [CrossRef]
- Ranathunga, D.; Roughan, M.; Nguyen, H.; Kernick, P.; Falkner, N. Case Studies of SCADA firewall configurations and the implications for best practices. IEEE Trans. Netw. Serv. Manag. 2016, 13, 871–884. [Google Scholar] [CrossRef]
- Panguluri, S.; Phillips, W.; Cusimano, J. Protecting water and wastewater infrastructure from cyber attacks. Front. Earth Sci. 2011, 5, 406–413. [Google Scholar] [CrossRef]
- Pretorius, B.; Van Niekerk, B. Cyber-Security for ICS/SCADA: A South African perspective. Int. J. Cyber Warf. Terror. 2016, 6, 1–16. [Google Scholar] [CrossRef][Green Version]
- Stellios, I.; Kotzanikolaou, P.; Psarakis, M. Advanced persistent threats and zero-day exploits in industrial Internet of Things. In Security and Privacy Trends in the Industrial Internet of Things: Advanced Sciences and Technologies for Security Applications; Alcaraz, C., Ed.; Springer International Publishing: Cham, Switzerland, 2019; pp. 47–68. [Google Scholar]
- Noble, T.; Manalo, C.; Miller, K.; Ferro, C. Cybersecurity assessments of 30 drinking water utilities. J. N. Engl. Water Works Assoc. 2017, 131, 219–227. [Google Scholar]
- McNabb, J.K. Securing public drinking water utilities. J. N. Engl. Water Works Assoc. 2012, 27, 37–59. [Google Scholar]
- Gourisetti, S.N.G.; Mylrea, M.; Patangia, H. Cybersecurity vulnerability mitigation framework through empirical paradigm: Enhanced prioritized gap analysis. Future Gener. Comput. Syst. 2020, 105, 410–431. [Google Scholar] [CrossRef]
- Jansen van Vuuren, J.C.; Leenen, L.; Phahlamohlaka, J.; Zaaiman, J. An approach to governance of cybersecurity in South Africa. Int. J. Cyber Warf. Terror. 2014, 2, 13–27. [Google Scholar] [CrossRef]
- Kshetri, N. Cybercrime and cybersecurity issues in the BRICS economies. J. Glob. Inf. Technol. Manag. 2015, 18, 245–249. [Google Scholar] [CrossRef]
- Wolfpack. The South African Cyber Threat Barometer: A Strategic Public-Private Partnership (PPP) Initiative to Combat Cybercrime in SA. Available online: https://web.archive.org/web/20201110174518/http://docplayer.net/17043391-2012-3-the-south-african-cyber-threat-barometer-a-strategic-public-private-partnership-ppp-initiative-to-combat-cybercrime-in-sa.html (accessed on 10 November 2020).
- South Africa. National Cybersecurity Policy Framework (NCPF). Available online: https://web.archive.org/web/20200701182327/https://www.gov.za/sites/default/files/gcis_document/201512/39475gon609.pdf (accessed on 10 November 2020).
- Mutemwa, M.; Mtsweni, J.; Mkhonto, N. Developing a cyber threat intelligence sharing platform for South African organisations. In Proceedings of the Conference on Information Communication Technology and Society (ICTAS 2017), Durban, South Africa, 9–10 March 2017. [Google Scholar]
- Government of South Africa. What Are the Government Clusters and Which Are They? Available online: https://web.archive.org/web/20201110180329/https://www.gov.za/faq/guide-government/what-are-government-clusters-and-which-are-they (accessed on 10 November 2020).
- South Africa. South African Constitution (as amended). Available online: https://web.archive.org/web/20201101003156/https://justice.gov.za/legislation/constitution/SAConstitution-web-eng.pdf (accessed on 10 November 2020).
- South Africa. Cybercrimes Bill (B6-2017). Available online: https://web.archive.org/web/20200805080827/https://pmg.org.za/bill/684/?via=homepage-card (accessed on 10 November 2020).
- South Africa. Critical Infrastructure Protection Act 8 of 2019. Available online: https://web.archive.org/web/20201110181412/https://www.gov.za/sites/default/files/gcis_document/201911/4286628-11act8of2019criticalinfraprotectact.pdf (accessed on 10 November 2020).
- South Africa. Protection of Personal Information Act. 2013. Available online: https://web.archive.org/web/20201014062057/https://www.justice.gov.za/inforeg/docs/InfoRegSA-POPIA-act2013-004.pdf (accessed on 10 November 2020).
- South Africa. The Regulation of Interception of Communications and Provision of Communication-Related Information Act. Available online: https://web.archive.org/web/20200918041001/https://www.gov.za/documents/regulation-interception-communications-and-provision-communication-related-information--13 (accessed on 10 November 2020).
- South Africa. Electronic Communications and Transactions Act. Available online: https://web.archive.org/web/20201106144645/https://www.gov.za/sites/default/files/gcis_document/201409/a25-02.pdf (accessed on 10 November 2020).
- South Africa. Promotion of Access to Information Act No. 2 of 2000. Available online: https://web.archive.org/web/20200517051020/https://www.justice.gov.za/legislation/acts/2000-002.pdf (accessed on 10 November 2020).
- Karabacak, B.; Yildirim, S.O.; Baykal, N. Regulatory approaches for cyber security of critical infrastructures: The case of Turkey. Comput. Law Secur. Rev. 2016, 32, 526–539. [Google Scholar] [CrossRef]
- De Bruijn, H.; Janssen, M. Building cybersecurity awareness: The need for evidence-based framing strategies. Gov. Inf. Q. 2017, 34, 1–7. [Google Scholar] [CrossRef]
- DWS. Department of Water and Sanitation 2018/19 Annual Report, Vote 36: Water Is Life—Sanitation Is Dignity. Available online: https://web.archive.org/web/20201110183936/http://www.dwa.gov.za/documents/AnnualReports/19213_Annual%20Report%20201819inhouse.pdf (accessed on 10 November 2020).
- Government SA. National Water and Sanitation Master Plan, Volume 1: Call to Action, Version 10.1: Ready for the Future and Ahead of the Curve. Available online: https://web.archive.org/web/20200408080543/https://www.gov.za/sites/default/files/gcis_document/201911/national-water-and-sanitation-master-plandf.pdf (accessed on 10 November 2020).
- Makaya, E.; Rohse, M.; Day, R.; Vogel, C.; Mehta, L.; McEwen, L.; Rangecroft, S.; Van Loon, A.F.E. Water governance challenges in rural South Africa: Exploring institutional coordination in drought management. Water policy 2020, 22, 519–540. [Google Scholar] [CrossRef]
- Government SA. Water and Sanitation. Available online: https://www.gov.za/about-sa/water-affairs (accessed on 10 November 2020).
- SERI. Water and Sanitation Legislation and Regulations. Available online: https://web.archive.org/web/20170301051254/https://www.seri-sa.org/index.php/links/policy-and-legislation/15-links/policy-and-legislation/87-water-and-sanitation (accessed on 10 November 2020).
- Stuart-Hill, S.I.; Schulze, R.E. Does South Africa’s water law and policy allow for climate change adaptation? Clim. Dev. 2010, 2, 128–144. [Google Scholar] [CrossRef]
- Pedrosa, V.A. The necessity of IWRM: The case of San Francisco river water conflicts. In Integrated Water Resource Management; Vieira, E.O., Sandoval-Solis, S., Pedrosa, V.A., Ortiz-Partida, J.P., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 27–34. [Google Scholar]
- Meadows, D. Thinking in Systems: A Primer; Earthscan: London, UK, 2008. [Google Scholar]
- Senge, P.M. The Fifth Discipline: The Art and Practice of the Learning Organization; Doubleday, Random House: New York, NY, USA, 2006. [Google Scholar]
- Ramos, H. Creativity and Systems Thinking. In Encyclopedia of Creativity, Invention, Innovation and Entrepreneurship; Carayannis, E.G., Ed.; Springer International Publishing: New York, NY, USA, 2013; pp. 12–58. [Google Scholar]
- Schuster, S. The art of Thinking in Systems: Improve Your Logic, Think More Critically, and Use Proven Systems to Solve Your Problems; CreateSpace Independent Publishing Platform: Scotts Valley, CA, USA, 2018; ISBN 9781983847547. [Google Scholar]
- SEBoK Editorial Board. The Guide to the Systems Engineering Body of Knowledge (SEBoK); v. 2.3; BKCASE: Hoboken, NJ, USA, 2020. [Google Scholar]
- Stroh, D.P. Systems Thinking for Social Change: A practical Guide for Solving Complex Problems, Avoiding Unintended Consequences, and Achieving Lasting Results; Chelsea Green Publishing: White River Junction, VT, USA, 2015. [Google Scholar]
- Sterman, J.D. Business Dynamics: Systems Thinking and Modeling for a Complex World; Irwin/McGraw-Hill: New York, NY, USA, 2000; ISBN 13 9780072311358. [Google Scholar]
- Sutherland, E. The Fourth Industrial Revolution–The Case of South Africa. Politikon 2020, 47, 233–252. [Google Scholar] [CrossRef]
- Gcaza, N. Cybersecurity awareness and education: A necessary parameter for smart communities. In Proceedings of the Twelfth International Symposium on Human Aspects of Information Security and Assurance (HAISA 2018), Dundee, Scotland, 29–31 August 2018; pp. 80–90. [Google Scholar]
- Mahlaka, R. Experian Offers Mea Culpa after Massive Data Breach Blunder. Available online: https://web.archive.org/web/20201110190306/https://www.dailymaverick.co.za/article/2020-08-23-experian-offers-mea-culpa-after-massive-data-breach-blunder/ (accessed on 10 November 2020).
- Merten, M. SAPS Regulations: It’s Crucial to Watch Critical Infrastructure Rules to Prevent a Power Grab. Available online: https://web.archive.org/web/20200808183846/https://www.dailymaverick.co.za/article/2020-04-03-saps-regulations-its-crucial-to-watch-critical-infrastructure-rules-to-prevent-a-power-grab/ (accessed on 10 November 2020).
- Timmers, P. The European Union’s cybersecurity industrial policy. J. Cyber Policy 2018, 3, 363–384. [Google Scholar] [CrossRef]
- Flowers, A.; Zeadally, S. US policy on active cyber defense. J. Homel. Secur. Emerg. Manag. 2014, 11, 289–308. [Google Scholar] [CrossRef]
- Van Woensel, L. Systems thinking and assessing cross-policy impacts. In A Bias Radar for responsible POLICY-MAKING: Foresight-Based Scientific Advice; Van Woensel, L., Ed.; Palgrave Macmillan: Cham, Switzerland, 2020; pp. 69–84. [Google Scholar]
- De Jong, M.D.T.; Neulen, S.; Jansma, S.R. Citizens’ intentions to participate in governmental co-creation initiatives: Comparing three co-creation configurations. Gov. Inf. Q. 2019, 36, 490–500. [Google Scholar] [CrossRef]
- Karlsson, F.; Holgersson, J.; Söderström, E.; Hedström, K. Exploring user participation approaches in public e-service development. Gov. Inf. Q. 2012, 29, 158–168. [Google Scholar] [CrossRef]
- Phahlamohlaka, J.; Hefer, J. The Impact of cybercrimes and cybersecurity Bill on South African national cybersecurity: An institutional theory analytic perspective. In Proceedings of the THREAT 2019 Cybersecurity Summit, Johannesburg, South Africa, June 2019; pp. 1–7. [Google Scholar]
- De Barros, M.J.Z.; Lazarek, H.; Jennifer, M. Comparative study of cybersecurity policy among South Africa and Mozambique. In Proceedings of the 13th International Conference on Cyber Warfare and Security (ICCWS 2018), Reading, UK, 8–9 March 2018; pp. 521–529. [Google Scholar]
- Dalton, W.; Jansen Van Vuuren, J.; Westcott, J. Building cybersecurity resilience in Africa. In Proceedings of the 12th International Conference on Cyber Warfare and Security (ICCWS 2017), Dayton, OH, USA, 2–3 March 2017; pp. 112–120. [Google Scholar]
- Van Niekerk, B. An analysis of cyber-incidents in South Africa. Afr. J. Inf. Commun. 2017, 20, 113–132. [Google Scholar] [CrossRef]
- Dlamini, I.Z.; Modise, M. Cyber security awareness initiatives in South Africa: A synergy approach. In Case Studies in Information Warfare and Security for Researchers, Teachers and Students; Warren, M., Ed.; ACPIL: London, UK, 2013; pp. 1–22. [Google Scholar]

| Challenge | Description | Source |
|---|---|---|
| Supply chain compromises | Third-party contractors and vendors are used as access vectors to the intended victim’s computer networks. | [12,48,52] |
| Increased cyber connectivity | Introduction of internet communication protocols to industrial control systems (ICSs) exposes them to security risks through the IT domain. | [12,13,53] |
| False sense of security by obscurity | Older supervisory control and data acquisition (SCADA) systems were isolated from corporate IT networks. With increasing cyber connectivity, they become difficult to secure due to design for safety and performance. | [53,54] |
| Network misconfigurations | Vulnerable computer network as a result of the misconfiguration of the firewall and related tools. | [45,55,56] |
| No media protection enforcement | Data theft due to a lack of removable media policy enforcement. | [57] |
| Unsecured remote access | Remote access to ICSs through untrusted devices, usually by third-party contractors and vendors increases cyber risk. | [53,58] |
| Undocumented policies and procedures | Undocumented cybersecurity policies and procedures make enforcement and compliance difficult. This inevitably increases organisational cyber risk. | [20,56] |
| Untrained personnel | Training and awareness of staff achieves significant cybersecurity improvements. The opposite also applies. | [20,59,60] |
| Legislation | Current Status |
|---|---|
| Computer Evidence Act 57 of 1983 | Repealed by the ECT Act 25 of 2002. |
| Copyright Act 98 of 1978 | Amended after 1994. |
| Critical Infrastructure Bill of 2017 | Signed into law on 28 November 2019, and it is now the Critical Infrastructure Protection Act 8 of 2019 (Critical Infrastructure Act). |
| Cybercrimes and Cybersecurity Bill of 2017 | Revised and approved as the Cybercrimes Bill by the National Council of Provinces on 1 July 2020. |
| Monitoring and Prohibition Act 127 of 1992 | Repealed by RICA. |
| National Key Points Act 102 of 1980 | Repealed by CIPA. |
| Sections 85 to 88 of the ECT Act | Repealed and substituted by sections 2 to 12 of the newly approved Cybercrimes Bill. |
| Section 89 of the ECT Act | Amended as outlined in section 58 of the Cybercrimes Bill. |
| Challenge | Description |
|---|---|
| Poor public-private partnerships track record | There is generally a poor track record of inter-ministerial coordination of government projects. It becomes even complex when stakeholders from industry, civil society, and special interest groups are involved. |
| Insufficient technical cybersecurity skills and user awareness education in South Africa | Development of technical cybersecurity skills must be prioritised by government. Public user education and awareness are pertinent aspects to preventing spoofing and phishing related cybercrimes in the country. |
| Independent and uncoordinated cybersecurity awareness initiatives | Currently, disparate and uncoordinated cybersecurity awareness training initiatives do exist. An integrated and coordinated approach to educating the public digital user about the dangers of cyberspace would be more effective. |
| Missing sector CSIRTs | With the exception of the banking sector which has the South African Banking Risk Information Centre (SABRIC), missing sector CSIRTs refers to the absence of CSIRTs in major sectors of the country, for example, in the mining, aviation, and agricultural sectors. These would be effective in sector information sharing and national coordination of cybersecurity incident responses. |
| Requirement for the establishment of new and dedicated cybersecurity institutions | The most critical cyber threats in South Africa are to the national critical infrastructure, intelligence agencies, and military. While the military and intelligence agencies are to some degree equipped to tackle cybersecurity, the provincial and local governments as well as the private sector operate and manage the vast majority of the national critical infrastructure. These entities must also be equipped to effectively protect the national critical infrastructure in a coordinated manner. This warrants the establishment of new and dedicated cybersecurity institutions. |
| Implementation of critical infrastructure protection still in abeyance | Protection of critical infrastructure is key in advanced cybersecurity strategies and must include strategies for cyber resilience and crisis management. Regulations are yet to be promulgated to implement the Critical Infrastructure Act. |
| Outstanding commitment to existing security conventions | There are no visible commitments to existing conventions such as the Budapest and African Union Convention on Cyber Security and Personal Data Protection. This would help in international collaboration on fighting cybercrimes, capacity building, and information sharing. |
| Lack of capacity and capability by law enforcement agencies | There is a huge gap between enacted laws and practical enforcement capability on the ground in most emerging and developing countries such as South Africa. This speaks to the point regarding the development of technical cybersecurity skills and user education and awareness. |
| Missing Cyber Inspectorate unit | A Cyber Inspectorate unit with powers to inspect, search, and seize cyber content in pursuit of unlawful digital acts was never established as clearly delineated in the ECT Act enacted in 2002. This is exacerbated by a poor track record of inter-ministerial coordination of complex government programmes. |
| International cooperation | South Africa is a non-member state signatory to the Council of Europe’s international Convention on cybercrime—the Budapest Convention. However, a clear commitment to the Convention is lacking as it is yet to be ratified since its signing on 23 November 2001. |
| Challenge | Description |
|---|---|
| National Water Act provides for protection of raw water | This does not refer to the protection of raw water cyber critical infrastructure. Instead, it refers to the planning, monitoring and managing of water resources in a coordinated manner. |
| The Strategic Framework on Water Services of 2003 provides for protection of water assets | This does not refer to the cyber protection of water assets. Instead, it refers to the repair, maintenance, and rehabilitation of water systems. |
| Cybersecurity Purpose (System Function) | Cybersecurity Stakeholders (System Elements/Actors) | Cybersecurity Legislation and Policies (System Interconnections) | |
|---|---|---|---|
| International cybersecurity system | Defined | Partially defined | Partially defined |
| National cybersecurity system | Defined | Defined | Defined |
| Water and wastewater sector as a system | Not defined | Not defined | Not defined |
| Water and wastewater sector as a stakeholder | Defined | Defined | Defined |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Malatji, M.; Marnewick, A.L.; von Solms, S. Cybersecurity Policy and the Legislative Context of the Water and Wastewater Sector in South Africa. Sustainability 2021, 13, 291. https://doi.org/10.3390/su13010291
Malatji M, Marnewick AL, von Solms S. Cybersecurity Policy and the Legislative Context of the Water and Wastewater Sector in South Africa. Sustainability. 2021; 13(1):291. https://doi.org/10.3390/su13010291
Chicago/Turabian StyleMalatji, Masike, Annlizé L. Marnewick, and Suné von Solms. 2021. "Cybersecurity Policy and the Legislative Context of the Water and Wastewater Sector in South Africa" Sustainability 13, no. 1: 291. https://doi.org/10.3390/su13010291
APA StyleMalatji, M., Marnewick, A. L., & von Solms, S. (2021). Cybersecurity Policy and the Legislative Context of the Water and Wastewater Sector in South Africa. Sustainability, 13(1), 291. https://doi.org/10.3390/su13010291





