A Sustainable Approach: Increasing Students’ Information-Technology Competences and Job-Seeking Capabilities through Course Redesign Using FIT Framework and Active Learning Pedagogy
Abstract
1. Introduction
1.1. Background
1.2. Fu Jen Catholic University’s Information Technology Literacy Program
1.3. Motivations and the Purposes of This Article
2. Literature Review
2.1. Information Technology Literacy and Fluency
2.2. Active Learning as a Teaching Strategy
2.2.1. Background
2.2.2. Technology-Enabled Active Learning Tools
3. Course Redesign and Incorporating Active Learning Strategies
3.1. Restructuring Course Content by Applying FIT Intellectual Framework
3.2. Defining Learning Outcomes
3.3. Teaching Strategies
- Learning by visual presentations via PowerPoint slides and selected YouTube videos:
- (a)
- Assignment 2: Evolution of the Internet and its impacts;
- (b)
- Network safety, security risks, cyber-attacks, and case studies;
- (c)
- Cloud computing basics and its applications and impacts;
- (d)
- Demonstrating prevention methods using secure password rules, and ISMS, etc.;
- Learning by doing:
- (a)
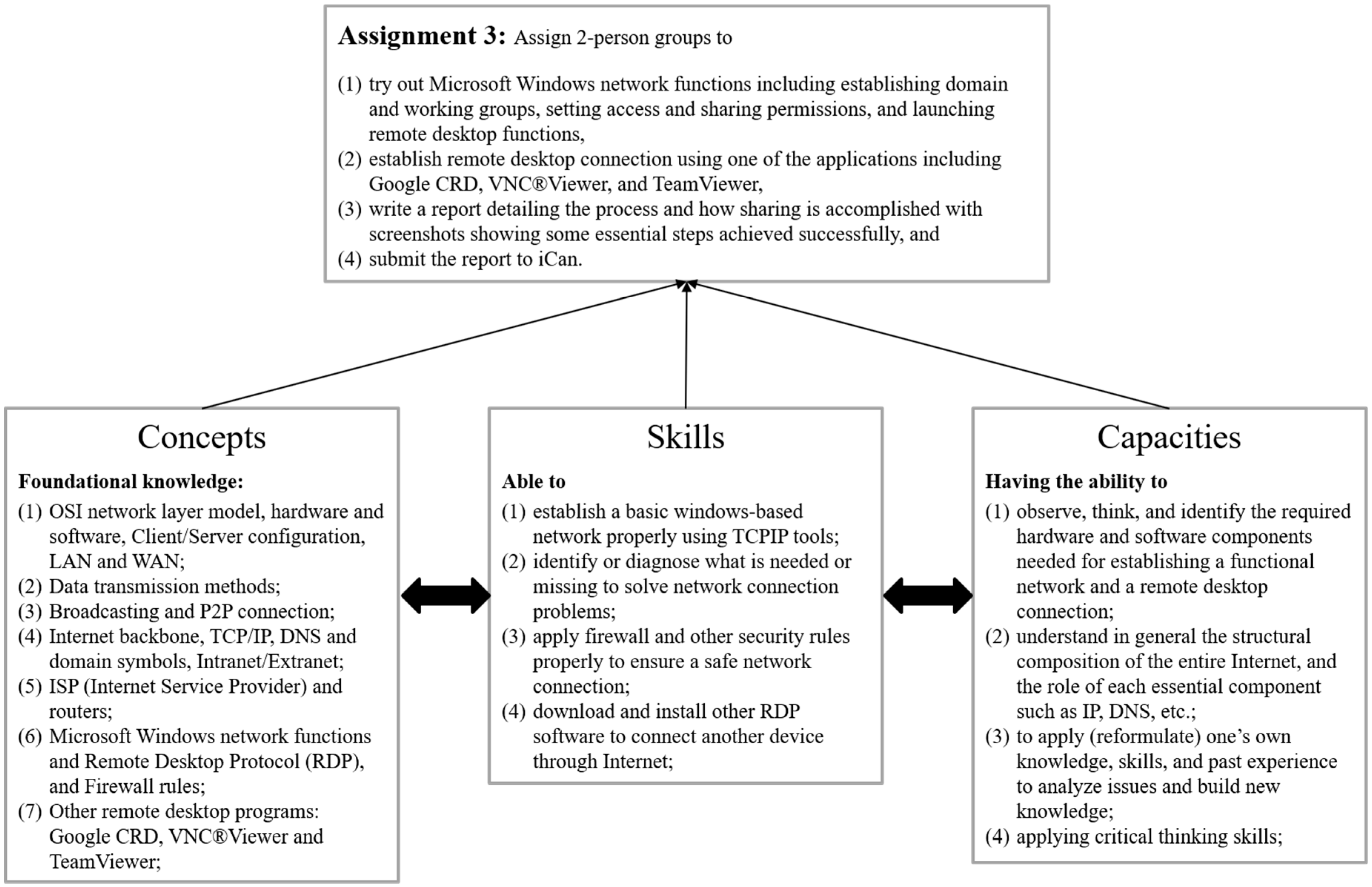
- Assignment 3: Working as a team to establish a secure network using Microsoft Windows network functions and remote desktop connection with other applications;
- (b)
- Practicing email system basics and advanced features;
- (c)
- Learning Google Docs productivity, sharing, and social tools;
- (d)
- Creating a simple web page with http:// and https:// access, respectively, and exploring the security risks between the two;
- (e)
- Browsing browser-related security and privacy controls;
- (f)
- Assignment 5: Using smartphone, Panoramio, and YouTube editing tools to create a short video;
- Learning by reading and writing:
- (a)
- Read selected articles on Intellectual Property Rights (IPR) and Creative Commons (CC) Licenses, and submit a written report;
- (b)
- Write a report on each of the topics presented through visual presentation;
- Learning by observation and exploration:
- (a)
- Assignment 1: Finding the configuration of the Internet connection at home, dorm, or apartment, and submitting a written summary report;
- (b)
- Assignment 4: Taking students to visit a network technology exhibit and submit a written report.
4. Methodology
4.1. Research Design (Objectives, Pre-Tests, Post-Tests, Questionaire)
4.2. Analyses and Results
4.3. Limitations and Implications
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Vadantham, A.; Breeden, L. Networking for K-12 education: The Federal perspective. Internet Res. Electron. Netw. Appl. Policy 1995, 5, 29–39. [Google Scholar] [CrossRef]
- Zhang, K.; Hung, J. E-Learning in Taiwan’s higher education: Policies, practices, and problems. Int. J. Inf. Commun. Technol. 2006, 2, 37–52. [Google Scholar] [CrossRef]
- Lu, M. Higher Education Reform in the Republic of China; Minister of Education: Taiwan, China, 2001. Available online: https://english.moe.gov.tw/cp-13-14087-CF128-2.html (accessed on 18 March 2020).
- Gong, G. Taiwan Internet Evolution: Status Report. Information Technology Promotion Division, Institute for Information Industry (III). Available online: http://web.simmons.edu/~chen/nit/NIT’98/98-051-Gong.html (accessed on 18 March 2020).
- Tu, C.; Twu, H. Educational technology in Taiwan. Educ. Media Int. 2002, 39, 153–164. [Google Scholar]
- TMOE (Taiwan’s Ministry of Education). Information and Internet Education. 2005. Available online: https://english.moe.gov.tw/cp-13-13941-1E58B-1.html (accessed on 18 March 2020).
- World Economic Forum. The Global Information Technology Report 2019. Available online: http://www3.weforum.org/docs/WEF_TheGlobalCompetitivenessReport2019.pdf (accessed on 18 March 2020).
- Fu Jen Catholic University. About Fu Jen: Facts at a Glance. 2020. Available online: http://www.fju.edu.tw/aboutFju.jsp?labelID=22 (accessed on 13 May 2020).
- Holistic Education Center, Fu Jen Catholic University. 2020. Available online: http://www.fju.edu.tw/academics.jsp?labelID=13 (accessed on 13 May 2020).
- Zhen, R.W. A Study on the Effectiveness Evaluation and Employment of the Young People’s Employment; Executive Yuan Youth Counseling Committee: Taiwan, China, 2011. [Google Scholar]
- Sullivan, M.A.; Dilek, Y. Enhancing scientific literacy through the use of information technology in introductory geoscience classes. J. Geosci. Educ. 1997, 45, 308–313. [Google Scholar] [CrossRef]
- van Eijck, M.; Roth, W. Rethinking the role of information technology-based research tools in students’ development of scientific literacy. J. Sci. Educ. Technol. 2007, 16, 225–238. [Google Scholar] [CrossRef]
- Bauer, A.M.; Thielk, S.M.; Katon, W.; Unutzer, J.; Arean, P. Aligning health information technologies with effective service delivery models to improve chronic disease care. Prev. Med. 2014, 66, 167–172. [Google Scholar] [CrossRef]
- Epperson, A. Computer literacy revisited: A comprehensive investigation of computer literacy. ACM Inroads 2010, 1, 30–33. [Google Scholar] [CrossRef]
- Hoffman, M.; Blake, J. Computer literacy: Today and tomorrow. J. Comput. Sci. Coll. 2003, 18, 221–233. [Google Scholar]
- Isokpehi, R.D.; Thomas, B.N.; Ojo, A.K.; Sofoluwe, A.B.; Coker, A.O. Information technology literacy among Nigerian microbiology students and professionals. World J. Microbiol. Biotechnol. 2000, 16, 423–4214. [Google Scholar] [CrossRef]
- King, K.M. Evolution of the computer literacy. EDUCOM Bull. 1985, 20, 18–21. [Google Scholar]
- Perez, J.; Murray, M. Computer for the masses: Extending the computer science curriculum with information technology literacy. Consort. Comput. Sci. Coll. 2008, 22, 220–226. [Google Scholar]
- Osborne, C. Planning for IT literacy in an institution of higher education: A Case Study. Comput. J. 1993, 36, 343–350. [Google Scholar] [CrossRef][Green Version]
- Halaris, A. Towards a definition of computing literacy for the liberal arts environment. ACM SIGCSE Bull. 1995, 17, 320–326. [Google Scholar]
- NRC (National Research Council). Being Fluent with Information Technology; National Academic Press: Washington, DC, USA, 1999. [Google Scholar]
- Bonwell, C.C.; Eison, J.A. Active learning: Creating excitement in the classroom. In ASHE-ERIC on Higher Education Reports; George Washington Univ., School of Education and Human Development: Washington, DC, USA, 1991. [Google Scholar]
- Cattaneo, K.H. Telling active learning pedagogies apart: From theory to practice. J. New Approaches Educ. Res. 2017, 6, 144–152. [Google Scholar] [CrossRef]
- Mitchell, A.; Petter, S.; Harris, A.I. Learning by doing: Twenty successful active learning exercises for information systems courses. J. Inf. Technol. Educ. Innov. Pract. 2017, 16, 21–46. [Google Scholar] [CrossRef]
- Freeman, S.; Eddy, S.L.; McDonough, M.; Smith, M.K.; Okoroafor, N.; Jordt, H.; Wenderoth, M.P. Active learning increases student performance in science, engineering, and mathematics. Proc. Natl. Acad. Sci. USA 2014, 111, 8410–8415. [Google Scholar] [CrossRef]
- Patton, C.M. Employing active learning strategies to become the facilitator, not the authoritarian: A literature review. J. Instr. Res. 2015, 4, 134–141. [Google Scholar] [CrossRef]
- Prince, M. Does active learning work? A review of the research. J. Eng. Educ. 2004, 93, 223–231. [Google Scholar] [CrossRef]
- Alavi, M. Computer-mediated collaborative learning: An Empirical Evaluation. MIS Q. 1994, 18, 159–174. [Google Scholar] [CrossRef]
- Reid, L.A.; Weber, C.M. Using technology-Enabled active learning tools to introduce business ethics topics in business law courses: A few practical examples. J. Leg. Stud. Educ. 2008, 25, 283–305. [Google Scholar] [CrossRef]
- Snowball, J.; Mostert, M. Introducing a learning management system in a large first year class: Impact on lectures and students. S. Afr. J. High. Educ. 2010, 24, 818–831. [Google Scholar] [CrossRef][Green Version]
- Schroeder-Moreno, M.S. Enhancing active and interactive learning online—Lessons learned from an online introductory agroecology course. N. Am. Coll. Teach. Agric. J. 2010, 54, 21–30. [Google Scholar]
- Huang, Y.; Asghar, A. Science education reform in Confucian learning cultures: Teachers’ perspectives on policy and practice in Taiwan. Cult. Stud. Sci. Educ. 2018, 13, 101–131. [Google Scholar] [CrossRef]
- Teng, L.Y. Infusing a collaborative learning curriculum to enhance active college learning. Coll. Q. 2006, 9, 1–18. [Google Scholar]
- Van den Branden, K. Sustainable education: Exploiting students’ energy for learning as a renewable resource. Sustainability 2015, 7, 5471–5487. [Google Scholar] [CrossRef]

| Unit # | Topics |
|---|---|
| 1. | General Introduction: A brief history of network evolution, the Internet, World Wide Web (WWW), Impacts on personal life, society, and the globe. |
| 2. | Network basics: a. Terminology; b. Network topology-OSI (Open Systems Interconnection Reference Model) model, required hardware and software components, data transmission methods, client/server configuration, LAN (Local Area Network) and WAN (Wide Area Network); c. Broadcasting, multicasting, and point-to-point (P2P) connection; d. Internet backbone, TCP/IP (Transmission Control Protocol/Internet Protocol), DNS (Domain Name Service), web address composition and domain symbols, Intranet, Extranet, http:// vs https:// *, ISP (Internet Service Provider); e. Microsoft Windows network functions, Remote Desktop Protocol (RDP), and firewall rules *; f. Other Remote Desktop connection applications: Google Chrome Remote Desktop (CRD), VNC®Viewer, and TeamViewer *; g. Wireless network, connection methods (WAP (Wireless Application Protocol), GPRS (General Packet Radio Service)), and hot spots; h. Broadband network and required hardware and software components *. |
| 3. | Network Resources and applications: a. Email messaging principles, POP3 (Post Office Protocol-Version 3), filter, spam mails, phishing *, malware, viruses, and other security risks *; b. Web browser operating principles, useful web browser features (e.g., bookmarks and favorite folders), privacy and security controls *, popular search engines, FTP (File Transfer Protocol) and P2P file transfer; c. Web 2.0 characteristics and its impacts, social media and Facebook; Open Source software *, freeware *, shareware, etc.; d. Proxy server and VPN (Virtual Private Network) principles and purposes *; e. Navigating the University, library networked resources, and Taiwan research resources network. |
| 4. | Emerging Network Resources and Applications, Awareness of Cyber Risks and Safety: a. Cloud computing basics: virtualization and virtual machine technology; * b. Google Docs productivity and sharing tools for collaboration and social; c. Other document sharing and collaboration websites: Evernote, Dropbox, Panoramio, etc.; * d. Intellectual Property Rights (IPR), Creative Commons (CC) Licenses *, regulations and prevention; e. Cyber-attacks: hackers, crackers, malware, Trojan Hose virus,DDoS (Distributed Denial-of-Service), ransomware, etc.; * f. Brief introduction to future networks: 4G, 5G high-speed networks and their physical components. * |
| Unit # | Topics | FIT Knowledge Components and Expectations |
|---|---|---|
| 1 | General Introductions: Have students find and share information about both positive and negative impacts of the Internet they have heard and experienced so far, either in class or through the discussion forum facility on the iCan5 Learning System. | Skills and capabilities: To find relevant information and use productivity tools to organize, present, and share the findings in class and via the discussion forum. |
| 2 | Network Basics: a. Learning by exploration: Assignment 1: Have students (1) find the configuration of their Internet connection at home, dorm, or apartment, (2) identify the connection method used and the required devices, (3) issue router commands on a PC to find connection data (i.e., IP, DNS, etc.), (4) evaluate the advantages and disadvantages of each method, (5) write a summary report with a configuration drawing attached and share the reports in class and discussion forum, and (6) submit the report for grading through iCan5; b. Learning via slide and video presentations using flipping-classroom approach: Assignment 2: Students should watch six selected YouTube videos on Internet evolution and write a 300-word report on the most interesting presentation and submit the report on iCan5; c. Learning by doing: Assignment 3: Assigning groups to (1) try out Microsoft Windows network functions, including establishing domain and working groups, setting access and sharing permissions, and launching remote desktop functions, (2) establish remote desktop using one of: Google CRD, VNC®Viewer, and TeamViewer, (3) write a report detailing the process and how sharing is accomplished with screenshots showing the essential steps achieved successfully, and (4) submit the report on iCan5; d. Two in-class online multiple-choice quizzes on conceptual topics and terminology; | Skills: Students are able to (1) establish a basic windows-based network properly using Microsoft Windows network function tools, (2) identify or diagnose what is needed to solve network connection problems, and (3) apply firewall and other security rules properly to ensure a safe network connection. Capabilities: (1) to observe, think, and identify the required hardware and software components needed for establishing a functional network and a remote desktop connection, (2) to understand in general the structural composition of the entire Internet and the role of each essential component, such as IP, DNS, data packet transmission methods, etc., (3) to understand the usefulness and the negative impacts of the Internet (4) to find out how to troubleshoot and recover a personal network connection when encountering problems through critical thinking. |
| 3 | Network Resources and applications: a. Learning by doing: Practicing group mailing, filtering, moving incoming emails to designated folders automatically, managing discussion threads, password change and update, creating a group and starting communication within the group, etc.; b. Learning via visual presentations using flipping-classroom approach: Having students watch slides on network safety, security risks, and cyber-attacks by presenting case studies, explaining why, how, and what they are. This includes hackers, cracker, malware, computer viruses, DDoS (Distributed Denial of Service), phishing, Trojan Horse virus, Spoofing, Smurf attacks, ransomware, etc.), demonstrating prevention methods and applying secure password rules, and ISMS (Information Security Management System) principles and policies, etc. c. Learning by doing: Having students create simple web pages using http:// and https:// access to demonstrate possible network risks and how browser personal data safety controls work; d. Quiz on TCP/IP, DHCP, DNS, etc.; e. Midterm exam on Email topics; | Skills: Students are able to (1) manage personal email and other online accounts including Facebook effectively, (2) navigate the University, library resources, government, and scientific organization websites to find information for academic, research, and personal needs, and (3) use web browser settings to change sound, display, and other features to personal liking, and (4) use security settings to protect personal computer and personal privacy from any possible cyber risks. Capabilities: Students can (1) grasp the basic structural and functional components of a website quickly, (2) protect personal computer from malicious cyber-attacks, (3) take appropriate measures to minimize cyber security risks, (4) stay safe and secure when accessing and using networked resources and applications. |
| 4 | Emerging Network Resources and Applications, Awareness of Network Risks and Safety: a. Learning via visual presentation using flipping-classroom approach: Have students (1) watch selected YouTube videos on Cloud Computing technology basics, applications, and implications; (2) have students write a summary report, and (3) submit the report on iCan5 for grading; b. Learning by reading and writing: Have students read selected articles on IPR and CC regulations. Have students write a report summarizing IPR and CC, as well as associated regulations, violations, and violation prevention strategies c. Learning by observation and exploration: Taking students to visit Taipei World Commerce Technology Exhibits, sponsored by the government information technology agencies and technology companies; Assignment 4: Having students submit a 5-page report through iCan5 on the exhibit that interested them the most, summarizing why this specific exhibit attracted them, what they learned, and what their thoughts on future development and overall perspectives about the Exhibits; d. Learning by doing: Assignment 5: Using the picture and video editing tools available on Panoramio, YouTube, and Google Drive to create a short video at least one minute in length. The completed video should include background music, a title screen showing the creator’s name, creation date, etc. and pictures taken on the campus using personal smartphone, and ending with credits and notes illustrating the steps taken to complete this project. Share the finished project with the entire class on discussion forum; e. Final Exam on VPN access and setup topics; | Skills: Students are able to (1) use Google Docs tools and other web sharing services to create images, documents, and videos for personal use, sharing, or collaboration, (2) download and install other web browsers, web software, and apps for personal needs, (3) use cloud storage websites including Google, Dropbox, Evernote, etc. to upload, download, backup, share, and collaborate on documents with classmates and friends. Capabilities: Students can (1) comprehend the necessity for backing up the data created by or important to oneself and choose the best option to do so dutifully, (2) use other authors’ works while avoiding IPR and CC violations, (3) apply (reformulate) one’s own knowledge, skills, and past experience to analyze issues critically for solving network or web technology related problems, (4) utilize the available network resources and applications further to learn and to build new knowledge, (5) stay aware of the possibility of cyber risks whenever being online, (6) adapt easily to technology changes, (7) further enrich oneself independently for pursuing future academic and career success. |
| Course Content | Learning Outcome |
|---|---|
| Network Basics | 1. Students will understand the basic structure of a network and its applications; 2. Students will understand what IP Address, DNS, WWW, and Cloud Computing are about; 3. Students will understand the purposes of MAC (Media Access Control) Address, DHCP (Dynamic Host Configuration Protocol), OSI 7-layer structure; 4. Students will understand the components required to establish a network access from home and know how to resolve a network connection problem; |
| Network Resources and Applications | 5. Students will know network resources and applications including Facebook and PTT (a Taiwan-based electronic bulletin board); 6. Students will know the purposes and functions of Evernote, Dropbox, and Panoramio Applications; 7. Students will be able to use essential email system features, including importing and exporting mail and contacts; 8. Students will know how to download college licensed software and library resources for academic and personal use; 9. Students will know how to use several popular web browsers and their bookmark features; 10. Students will understand the importance of backing up personal computer data and know how to perform backup using external storage media including CD disc, thumb drive, and cloud storage; 11. Students will understand the differences between http:// and https://; |
| Emerging Network Resources and Applications, Awareness of Network Risks, and Safety | 12. Students will understand what IPR and CC are about, as well as the legal risks of downloading unauthorized online software, music, and movies for personal possession and use; 13. Students will understand the importance of protecting their personal computers from unwanted intrusions by using an account password created via secure password creation rules; 14. Students will understand the necessity of changing their university Single-Sign-On (LDAP) login password periodically to secure their personal account access and data privacy; 15. Students will understand the importance of changing their passwords periodically in order to secure their personal computer and online account access; 16. Students will understand the importance of adopting a personal password management strategy to secure their online account access; 17. Students will know how to set up Facebook’s device-specific logins (personal computer, cellphone, iPad, etc.) and privacy protection; 18. Students will understand what phishing is and how it works; 19. Students will understand what Trojan and Zombie viruses are and how they work; 20. Students will know how to lock their computer properly when they need to be away for a short period of time; |
| Learning Outcome Question | Median | Students Who Chose the Response Better Than the Median | |||
|---|---|---|---|---|---|
| Pre-Test | Post-Test | ||||
| # | % (n = 177) | # | % (n = 177) | ||
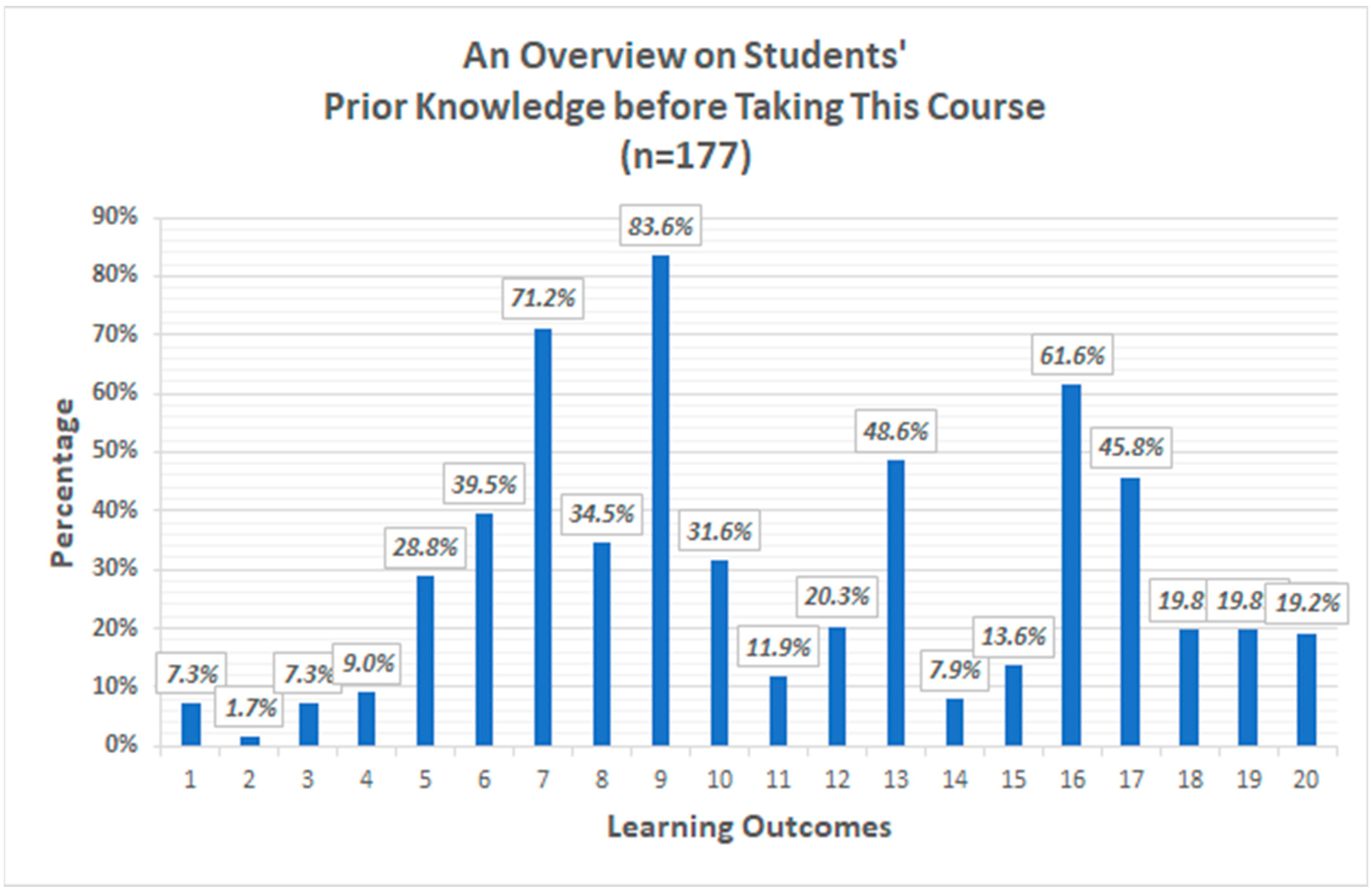
| 1 | 3 | 13 | 7.3% | 106 | 59.4% |
| 2 | 3 | 3 | 1.7% | 144 | 81.4% |
| 3 | 3 | 13 | 7.3% | 123 | 69.5% |
| 4 | 3 | 16 | 9.0% | 117 | 66.1% |
| 5 | 3 | 51 | 28.8% | 168 | 94.9% |
| 6 | 2.5 | 70 | 39.5% | 172 | 97.2% |
| 7 | 2.5 | 126 | 71.1% | 151 | 85.3% |
| 8 | 2 | 61 | 34.4% | 136 | 76.8% |
| 9 | 2.5 | 148 | 83.6% | 167 | 94.4% |
| 10 | 3.5 | 56 | 31.6% | 119 | 67.2% |
| 11 | 2 | 21 | 11.9% | 110 | 62.1% |
| 12 | 3 | 36 | 20.3% | 104 | 58.8% |
| 13 | 2.5 | 86 | 48.6% | 141 | 79.7% |
| 14 | 3 | 14 | 7.9% | 42 | 23.7% |
| 15 | 2.5 | 24 | 13.6% | 53 | 29.9% |
| 16 | 2 | 109 | 61.6% | 140 | 79.1% |
| 17 | 2.5 | 81 | 45.8% | 120 | 67.8% |
| 18 | 2 | 35 | 19.8% | 149 | 84.2% |
| 19 | 2 | 35 | 19.8% | 150 | 84.7% |
| 20 | 2 | 34 | 19.2% | 82 | 46.3% |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pan, T.-M.; Fan, K.-C. A Sustainable Approach: Increasing Students’ Information-Technology Competences and Job-Seeking Capabilities through Course Redesign Using FIT Framework and Active Learning Pedagogy. Sustainability 2020, 12, 4094. https://doi.org/10.3390/su12104094
Pan T-M, Fan K-C. A Sustainable Approach: Increasing Students’ Information-Technology Competences and Job-Seeking Capabilities through Course Redesign Using FIT Framework and Active Learning Pedagogy. Sustainability. 2020; 12(10):4094. https://doi.org/10.3390/su12104094
Chicago/Turabian StylePan, Tung-Ming, and Kuo-Chin Fan. 2020. "A Sustainable Approach: Increasing Students’ Information-Technology Competences and Job-Seeking Capabilities through Course Redesign Using FIT Framework and Active Learning Pedagogy" Sustainability 12, no. 10: 4094. https://doi.org/10.3390/su12104094
APA StylePan, T.-M., & Fan, K.-C. (2020). A Sustainable Approach: Increasing Students’ Information-Technology Competences and Job-Seeking Capabilities through Course Redesign Using FIT Framework and Active Learning Pedagogy. Sustainability, 12(10), 4094. https://doi.org/10.3390/su12104094






