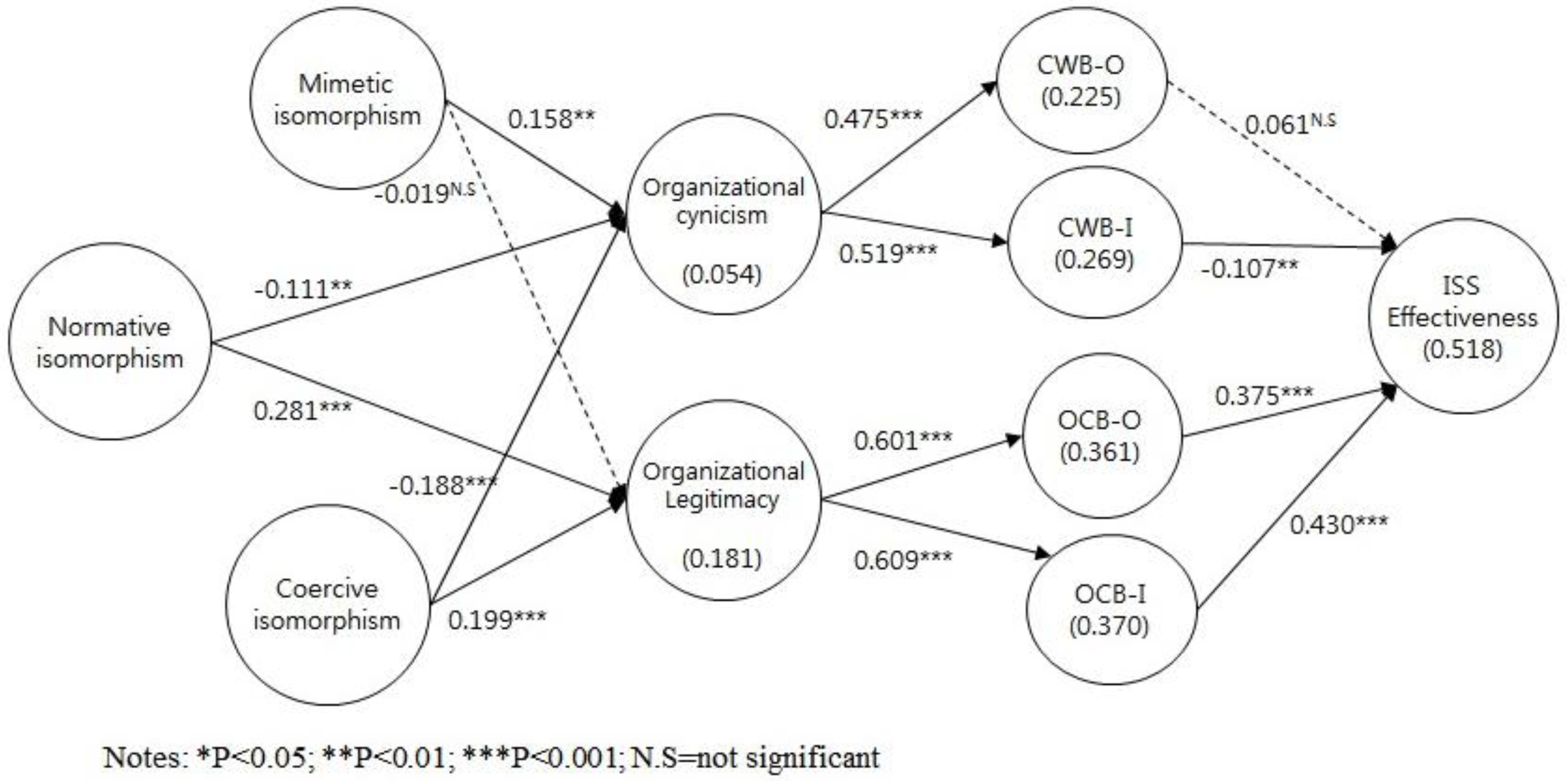
2.4.1. Legitimacy Path: Isomorphism, Legitimacy, and OCB for ISS Effectiveness
It is a well-known proposition that isomorphism leads to legitimacy [
20]. Furthermore, isomorphism highlights its importance [
54]. Institution theory stresses that organizational changes do not occur for better organizational substantive performance, but for greater legitimacy [
32]. Institutional isomorphism requires changes to organizational norms, beliefs, structures, practices, and processes, and legitimacy justifies these changes. Organizational members accept the increased legitimacy gained through isomorphism as an adaptive action for their survival [
55].
The strategic approach notes that organizations use legitimacy as an operational resource to help achieve their objectives and goals [
56], while institutional theory emphasizes legitimacy as “a condition reflecting perceived consonance with relevant rules, norms, and beliefs” ([
57], p. 59). Suchman ([
58], pp. 573–574) integrated the two views to define legitimacy as “the generalized perception or assumption that the actions of an entity are desirable, proper, or appropriate within some socially constructed system of norms, beliefs, and definitions”. Suchman ([
58], p. 571) also elucidated the role of legitimacy as “an anchor-point of a vastly expanded theoretical apparatus addressing the normative and cognitive forces that constrain, construct, and empower organizational actors”.
Westphal et al. [
59] argued that different types of legitimacy are shaped by different attributes or levels of isomorphism; for example, individual legitimacy is based on authority and accepted social structure, and organizational legitimacy originates from the organization’s prevalent cultural values. This study investigates organizational legitimacy as a central construct of the ISS research model, as organizational legitimacy internalizes the organizational changes stemming from isomorphic influences, and isomorphism functions as an external force. Perceived value congruence and legitimacy are identified as intrinsic incentives for ISS compliance that positively influence it [
60]. When institutional isomorphism forces national governments to engage in ISS, legitimacy leads organizational actors to identify the new ISS practices as a “socially constructed system of norms, beliefs, and definitions” [
57].
Coercive isomorphism, such as enforcing the Sarbanes–Oxley Act as a universal mandate, has established a new legitimacy for information security practices and protocols [
37]. By adopting total quality management practices, consultants as change agents have normative and mimetic influences, and their input is valued not only as knowledge and as technological advice, but also as a source of legitimacy [
61]. Hence, the following hypotheses are proposed:
Hypothesis 1 (H1). Normative isomorphism is positively associated with ISS legitimacy.
Hypothesis 2 (H2). Coercive isomorphism is positively associated with ISS legitimacy.
Hypothesis 3 (H3). Mimetic isomorphism is positively associated with ISS legitimacy.
Organ ([
62], p. 4) defined OCBs as “individual behavior[s] that [are] discretionary, not directly or explicitly recognized by the formal reward system, and that in the aggregate promote the effective functioning of the organization”. These are organizational members’ discretionary behaviors, which exceed basic requirements and result in improved organizational effectiveness [
25,
63]. Furthermore, OCBs include OCB-organization (OCB-O) and OCB-individual (OCB-I), which benefit the organization and the individual, respectively. These types distinguish OCBs based on the target or beneficiary of a specific OCB behavior [
64]. While OCB-O encompasses civic virtue, conscientiousness, and sportsmanship, OCB-I encapsulates altruism and courtesy [
65].
Legitimacy leads to organizational members’ OCBs as well as organizational commitment and job satisfaction [
66]. As perceived legitimacy (i.e., organizational members perceive the ISS as appropriate and desirable) justifies ISS compliance [
60], perceived legitimacy may lead to OCB when ISS compliance is perceived as meaningful. Organizational actors’ perceptions of their own work as meaningful positively affect OCB [
67]. Thus, this study proposes the following hypotheses:
Hypothesis 4 (H4). The legitimacy of ISS is positively associated with OCB-I.
Hypothesis 5 (H5). The legitimacy of ISS is positively associated with OCB-O.
Furthermore, OCB can improve individual compliance with information security policies and lead to success in information systems [
68]. While it has been suggested that OCB positively relates to organizational effectiveness, efficiency, and success [
18,
64], empirical studies have seldom explored the relationship between OCBs and organizational effectiveness [
22].
Defined as “individual behavior that is discretionary, not dependent on the use of rewards or punishments to encourage performance, and that in the aggregate promotes the effective functioning of the organization” [
62], OCB encourages employees to accept change and find constructive resolutions to problems. This also helps employees cooperate with each other, and share power in the organization’s politics. Moreover, OCB can increase individuals’ willingness to resolve conflicts and dedicate themselves to their organization, rather than seeking benefits for themselves individually or for the groups in which they participate [
69].
Furthermore, such OCBs as helping and advising can improve the effectiveness of information security policies, or ISPs [
70,
71]. Helping involves a small, considerate behavior toward others, and can involve assisting employees who are unfamiliar with ISPs. This can also include with how to implement them may act appropriately by providing guidance to ISPs, identifying inappropriate conduct, or helping others learn the ISPs. Individuals in the working environment can voluntarily provide assistance to keep ISPs. Advising, or providing advice, is another cooperative organizational behavior, and provides feedback intended to improve the current situation [
72]. Advising is crucial in a contemporary information security environment, in which new threats emerge and frequent changes occur in technologies. Providing adequate advice from employees can encourage individuals to comply with ISPs, and can enhance the ISPs’ content.
OCB can be categorized into OCB-I and OCB-O depending on whether a behavior or its target is directed at individuals or an organization [
64]. First, OCB-I benefits individuals, as this involves an organizational member actively providing advice to other members regarding how to use ISS systems; this category consists of both altruism and courtesy [
64,
73]. Furthermore, OCB-O targets organizations, such as an organizational member voluntarily reporting a hacking e-mail to the organization, and involves conscientiousness, civic virtue, and sportsmanship [
64,
73].
Although OCB has been studied in various fields for several decades, few researchers have investigated whether OCBs can successfully prompt socio-emotional support, which directly influences the success of both ISS implementation [
14,
68] and ISS effectiveness [
71]. Based on previous studies, this study anticipates that OCB positively improves ISS effectiveness. Thus, this study proposes that:
Hypothesis 6 (H6). OCB-I is positively associated with ISS effectiveness.
Hypothesis 7 (H7). OCB-O is positively associated with ISS effectiveness.
2.4.2. Organizational Cynicism Path: Isomorphism, Organizational Cynicism, CWB, and ISS Effectiveness
People rarely welcome change, and especially in a work context in which they must strive to change their established routines and increase their cognitive load [
74]. People tend to resist change and become cynical about anything that interrupts the status quo in their working lives [
65]. When faced with social forces to change the organization, or in this case, ISS policy implementation, an employee’s stance is cynical, at best. Organizational cynicism has been identified as a prevalent phenomenon in organizations [
75,
76], and has recently received increasing attention in research on organizational changes [
77,
78]. According to Reichers, Wanous, and Austin [
60], organizational cynicism is conceptually and closely linked to organizational change. Bergström, Styhre, and Thilander ([
77], p. 384) argued that “organizational cynicism has been viewed as a form of resistance driven by the unsuccessful implementation of organizational change or, in contrast, as a direct negative attitude towards management”. Stanley, Meyer, and Topolnytsky [
79] found that change-specific cynicism predicts the intention to resist change, and [
80] described cynicism as a discursive tactic of resistance. Organizational cynicism results in increased beliefs of unfairness as a cognitive aspect; feelings of distrust as an affective aspect; and related actions about and against the organization as a behavioral aspect [
81]. Organizational cynicism causes various negative workplace behaviors, such as frequent absences, poor performance, and grievances [
82], and passive participation or inaction in organizational change efforts [
60].
Dean et al. ([
76], p. 345) defined organizational cynicism as “a negative attitude toward one’s employing organization, comprising three dimensions: (1) a belief that the organization lacks integrity; (2) negative affect toward the organization; and (3) tendencies to disparaging and critical behaviors toward the organization that are consistent with these beliefs and affect”. Dean et al.’s [
76] definition is based on the conceptualization of organizational cynicism as an attitude detrimental to the organization. Stanley et al. ([
79], p. 452) defined the characteristic of cynicism as the “disbelief in the motives of others”. The authors further identified three types of cynicism: change-specific cynicism, as “a disbelief of management’s stated or implied motives for a specific organizational change”; management cynicism, as “a disbelief in management’s stated or implied motives for decisions or actions in general”; and dispositional cynicism, as “a disbelief in the stated or implied motives of people in general for their decisions or actions” ([
79], p. 436). This study focused on change-specific cynicism, because this addresses organizational change for ISS innovation; and management cynicism, because it is incredibly difficult to ignore the interaction effects between employees’ disbelief in a specific organizational change and their general disbelief.
Executives and managers typically value employees who are willing to respond positively to the initiation of change. However, organizations attempting to change established routines or introduce new ones frequently falter when insiders resist these changes [
83]. This often occurs for simple reasons; specifically, the benefits of these changes may not be in concert with the interests of the individuals being asked to make the changes [
38]. This phenomenon of resistance and organizational cynicism can be explained relative to institution theory, as the social forces shaping organizations can be coercive, normal, or mimetic [
20,
84]. Furthermore, these different forces might have different effects on the levels of organizational cynicism.
Studies of organizational cynicism have been extremely scarce in information systems research, but resistance has been documented. As organizational cynicism can be viewed as a form of resistance, this study extends the literature review on organizational cynicism to that of resistance in information systems literature. Resistance has been recognized as a critical variable in information systems research [
85] as well as in organizational transformation literature [
38]. Lapointe and Rivard [
85] identified four different theoretical models to explain user resistance: (1) the power theory [
85], (2) equity theory [
86], (3) passive-aggressive theory [
87], and (4) attribution theory [
79]. These theories of resistance can be used to relate institution theory to user resistance, as follows.
The pressures coming from professional organizations and colleagues are normative isomorphic forces. Normative isomorphism results in the organizational members’ professionalization and creates similar orientations and dispositions among these members through their similar education and training experiences and participation in professional networks [
9]. These normative pressures are more readily accepted than other institutional forces, as they come from similar shared experiences and orientations. Thus, it is posited that normative isomorphism may mitigate organizational cynicism.
Hypothesis 8 (H8). Normative isomorphism is negatively associated with organizational cynicism toward ISS.
The power theory in information systems resistance research portrays resistance as a result of the redistribution or loss of power [
88]. Regarding user resistance, users are more likely to resist when they perceive that the system instigates a loss of power on their part, whether implicitly or explicitly [
89]. Moreover, it can be inferred that the level of resistance relates to the feeling of losing importance. Coercive isomorphic forces result from both formal and informal pressures placed on organizations by the authorities upon which they depend [
20]. Thus, such pressures may be felt as forcefully unbalancing the present state of power, which may cause people to resist the changes to be implemented [
90]. Generally, ISS mandates by external authorities are expected to increase the message receiver’s resistance. Thus, it is posited here that coercive isomorphism may increase the level of organizational cynicism as a form of resistance on the user’s side.
Hypothesis 9 (H9). Coercive isomorphism is positively associated with organizational cynicism toward ISS.
Mimetic isomorphic forces occur due to high uncertainty, which is a powerful driver in persuading organizations to imitate and follow the models in other leading organizations [
83]. When technologies are not clearly understandable, the goals of changes are ambiguous, or the consequences of technologies are unclear, organizations may attempt to follow other organizations, especially leading ones [
20]. Mimetic isomorphic forces may increase or decrease the level of organizational cynicism depending upon the reason for mimicry. When this reason justifiably relates to an individual benefit [
26], employees will not strongly resist. However, when the reason for mimetic adoption is not clearly explained or justifiable for employees’ benefit [
26], they may resist or nonetheless act passive-aggressively [
86]. Regarding ISS, the goals and processes of ISS policy and practice do not directly relate to employees’ business activities in most organizations; therefore, ISS’ benefit is unclear to most employees. Thus, it is posited that mimetic social forces may increase organizational cynicism.
Hypothesis 10 (H10). Mimetic isomorphism is positively associated with organizational cynicism toward ISS.
Organizational cynics criticize their organization for a lack of integrity [
76] and sincerity, unfair operations [
66], and prevalent unscrupulous behavior [
76]. Although organizational cynicism cannot be identified as a simple representation of a lack of organizational commitment, it negatively relates to organizational commitment [
76]. Organizational cynicism, as a barrier to the enforcement of organizational changes, was viewed from the management perspective as organizational members’ reactions to inappropriately implemented changes and managerial incapacity [
77]. Furthermore, Bergström et al. ([
77], p. 387) argued, “Perhaps the most important consequence of cynicism is that the legitimacy of leadership may be undermined and the organization’s capacity for future changes is decreased”.
Organizational cynicism may hinder organizational changes because it fuels suspicion of change agents’ motivations, and increases the inertia and indifference to these agents’ efforts [
91]. Moreover, organizational cynicism compels employees to ignore new programs and procedures [
75]. MacLean and Behnam (2010) [
92] studied the dynamic between decoupling, legitimacy, and institutionalized misconduct to suggest that members’ organizational cynicism regarding decoupled programs resulted in internal illegitimacy. Furthermore, Holderness et al. [
70] argued that members with negative legitimacy perceptions of their formal ethical program might adopt views that are more cynical; IT resistance also includes this organizational cynicism [
47].
Accordingly, it may be reasonable to propose that organizational cynicism might generally cause CWB and breed suspicion of an organization’s ulterior motives, as organizational cynicism results in employees’ widespread suspicions of the motivations underlying new programs [
91]. Additionally, organizational cynicism tends to deny organizational integrity, which is fortified by the legitimacy led by isomorphism.
According to Reichers, Wanous, and Austin [
60], organizational cynicism about change can cause a decline in employees’ motivation, job satisfaction, and loyalty. Accordingly, employees tend to engage in CWB, which can be defined as “[…] voluntary acts that violate significant organizational norms and are contrary to the organization’s legitimate interests” ([
93], p. 554). Like OCB, CWB has been distinguished by interpersonally (CWB-I: deviant behavior directed toward other employees, such as gossiping about coworkers) and organizationally directed (CWB-O: deviant behavior directed toward the organization, such as taking overly long breaks) aspects of workplace deviance [
53].
The assumption that human agents have malicious intentions leads ISS research regarding how to control employees’ antisocial or problematic ISS-related behavior, such as corrupting organizational information, disabling ISS, or destroying or deleting data [
94]. This kind of ISS-related misconduct can be regarded as CWB to ISS [
95]. Organizational cynicism-induced or resistance behavior can be passive, such as verbal reactions; or aggressive, such as sabotage and indifference. Generally, it manifests as counterproductive behavior [
96]. Similarly, counter-ISS behavior can be as passive, as with non-compliance; or active, as with leaking. As CWB is designed to mitigate negative effects [
95], organizational cynicism acts as a negative effect, and attitude becomes a proximal cause of CWB. Thus, it is posited here that the organizational cynicism toward ISS policies and practices will increase the level of counter-ISS workplace behavior, which will decrease the ISS’ effectiveness:
Hypothesis 11 (H11). Organizational cynicism toward ISS is positively associated with ISS-related CWB-O.
Hypothesis 12 (H12). Organizational cynicism toward ISS is positively associated with ISS-related CWB-I.
Hypothesis 13 (H13). Employees’ ISS-related CWB-O is negatively associated with ISS effectiveness.
Hypothesis 14 (H14). Employees’ ISS-related CWB-I is negatively associated with ISS effectiveness.