Information Systems Security (ISS) of E-Government for Sustainability: A Dual Path Model of ISS Influenced by Institutional Isomorphism
Abstract
1. Introduction
2. Theoretical Model and Hypotheses
2.1. ISS and Institution Theory
2.2. Three Types of Isomorphism and Their Influences on Government Organizations
2.3. ISS Effectiveness
2.4. Dual Paths
2.4.1. Legitimacy Path: Isomorphism, Legitimacy, and OCB for ISS Effectiveness
2.4.2. Organizational Cynicism Path: Isomorphism, Organizational Cynicism, CWB, and ISS Effectiveness
3. Methodology
3.1. Measurement of Constructs
3.2. Data Collection
4. Data Analysis and Results
5. Discussion and Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
Appendix A. Item Correlation
| NOR1 | NOR2 | NOR3 | COR1 | COR2 | COR3 | MIM1 | MIM2 | MIM3 | LEG1 | LEG2 | LEG3 | LEG4 | CYN1 | CYN2 | CYN3 | CYN4 | CYN4 | CYN6 | OCI1 | OCI2 | OCI3 | OCI4 | OCI5 | OCI6 | OCO1 | OCO2 | OCO3 | OCO4 | OCO5 | OCO6 | CWI1 | CWI2 | CWI3 | CWO1 | CWO2 | CWO3 | ISS1 | ISS2 | ISS3 | ISS4 | ISS5 | ISS6 | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| NOR1 | 1.000 | ||||||||||||||||||||||||||||||||||||||||||
| NOR2 | 0.319** | 1.000 | |||||||||||||||||||||||||||||||||||||||||
| NOR3 | 0.452** | 0.563** | 1.000 | ||||||||||||||||||||||||||||||||||||||||
| COR1 | 0.323** | 0.429** | 0.468** | 1.000 | |||||||||||||||||||||||||||||||||||||||
| COR2 | 0.546** | 0.300** | 0.405** | 0.467** | 1.000 | ||||||||||||||||||||||||||||||||||||||
| COR3 | 0.464** | 0.388** | 0.440** | 0.308** | 0.552** | 1.000 | |||||||||||||||||||||||||||||||||||||
| MIM1 | 0.426** | 0.192** | 0.385** | 0.247** | 0.396** | 0.426** | 1.000 | ||||||||||||||||||||||||||||||||||||
| MIM2 | 0.362** | 0.212** | 0.229** | 0.190** | 0.313** | 0.304** | 0.498** | 1.000 | |||||||||||||||||||||||||||||||||||
| MIM3 | 0.359** | 0.362** | 0.309** | 0.272** | 0.411** | 0.407** | 0.456** | 0.489** | 1.000 | ||||||||||||||||||||||||||||||||||
| LEG1 | 0.181** | 0.328** | 0.319** | 0.303** | 0.190** | 0.261** | 0.041 | 0.049 | 0.274** | 1.000 | |||||||||||||||||||||||||||||||||
| LEG2 | 0.187** | 0.343** | 0.329** | 0.349** | 0.251** | 0.281** | 0.075 | 0.076 | 0.319** | 0.852** | 1.000 | ||||||||||||||||||||||||||||||||
| LEG3 | −0.013 | 0.110* | 0.105* | 0.182** | 0.061 | 0.076 | 0.030 | −0.085 | 0.152** | 0.271** | 0.307** | 1.000 | |||||||||||||||||||||||||||||||
| LEG4 | 0.147** | 0.357** | 0.281** | 0.214** | 0.197** | 0.240** | 0.029 | 0.069 | 0.247** | 0.661** | 0.672** | 0.175** | 1.000 | ||||||||||||||||||||||||||||||
| CYN1 | 0.039 | −0.124* | −0.098 | −0.026 | 0.009 | −0.002 | 0.058 | 0.095 | 0.007 | −0.175** | −0.185** | −0.414** | −0.0147** | 1.000 | |||||||||||||||||||||||||||||
| CYN2 | 0.006 | −0.076 | −0.091 | −0.098 | −0.058 | −0.033 | 0.079 | 0.150** | −0.045 | −0.210** | −0.229** | −0.477** | −0.148** | 0.632** | 1.000 | ||||||||||||||||||||||||||||
| CYN3 | −0.190** | −0.331** | −0.299** | −0.216** | −0.207** | −0.243** | −0.070 | −0.041 | −0.236** | −0.575** | −0.567** | −0.226** | −0.531** | 0.207** | 0.269** | 1.000 | |||||||||||||||||||||||||||
| CYN4 | −0.010 | −0.128* | −0.084 | −0.119* | −0.078 | −0.144** | 0.032 | 0.127* | −0.086 | −0.335** | −0.355** | −0.532** | −0.232** | 0.473** | 0.571** | 0.389** | 1.000 | ||||||||||||||||||||||||||
| CYN5 | 0.010 | −0.093 | −0.058 | −0.162** | −0.047 | −0.073 | 0.097 | 0.152** | −0.031 | −0.353** | −0.369** | −0.490** | −0.259** | 0.469** | 0.544** | 0.335** | 0.787** | 1.000 | |||||||||||||||||||||||||
| CYN6 | 0.017 | −0.073 | −0.050 | −0.167** | −0.113* | −0.121* | 0.030 | 0.085 | −0.101* | −0.337** | −0.367** | −0.474** | −0.232** | 0.406** | 0.520** | 0.354** | 0.766** | 0.782** | 1.000 | ||||||||||||||||||||||||
| OCI1 | 0.056 | 0.246** | 0.185** | 0.227** | 0.163** | 0.151** | 0.016 | 0.021 | 0.200** | 0.459** | 0.475** | 0.192** | 0.417** | −0.158** | −0.129* | −0.381** | −0.255** | −0.235** | −0.229** | 1.000 | |||||||||||||||||||||||
| OCI2 | 0.140** | 0.271** | 0.204** | 0.256** | 0.177** | 0.157** | −0.053 | −0.039 | 0.197** | 0.507** | 0.497** | 0.201** | 0.411** | −0.160** | −0.190** | −0.403** | −0.244** | −0.227** | −0.254** | 0.735** | 1.000 | ||||||||||||||||||||||
| OCI3 | 0.125* | 0.265** | 0.153** | 0.197** | 0.117* | 0.159** | −0.024 | −0.014 | 0.206** | 0.466** | 0.459** | 0.113* | 0.475** | −0.068 | −0.077 | −0.364** | −0.181** | −0.194** | −0.179** | 0.560** | 0.681** | 1.000 | |||||||||||||||||||||
| OCI4 | 0.081 | 0.265** | 0.161** | 0.177** | 0.109* | 0.137** | 0.038 | 0.033 | 0.224** | 0.445** | 0.469** | 0.045 | 0.459** | −0.064 | −0.023 | −0.340** | −0.133** | −0.171** | −0.121* | 0.565** | 0.625** | 0.761** | 1.000 | ||||||||||||||||||||
| OCI5 | 0.046 | 0.250** | 0.150** | 0.168** | 0.079 | 0.129* | −0.049 | 0.033 | 0.218** | 0.528** | 0.506** | 0.104* | 0.462** | −0.108* | −0.104* | −0.361** | −0.181** | −0.185** | −0.227** | 0.576** | 0.686** | 0.708** | 0.779** | 1.000 | |||||||||||||||||||
| OCI6 | 0.064 | 0.262** | 0.167** | 0.203** | 0.130* | 0.163** | −0.008 | 0.006 | 0.215** | 0.522** | 0.515** | 0.170** | 0.492** | −0.091 | −0.081 | −0.374** | −0.206** | −0.226** | −0.220** | 0.612** | 0.674** | 0.694** | 0.680** | 0.736** | 1.000 | ||||||||||||||||||
| OCO1 | 0.114* | 0.313** | 0.225** | 0.304** | 0.313** | 0.211** | 0.003 | 0.010 | 0.234** | 0.447** | 0.468** | 0.274** | 0.348** | −0.180** | −0.301** | −0.453** | −0.361** | −0.328** | −0.321** | 0.438** | 0.442** | 0.339** | 0.276** | 0.331** | 0.452** | 1.000 | |||||||||||||||||
| OCO2 | 0.131** | 0.251** | 0.187** | 0.257** | 0.277** | 0.205** | 0.031 | 0.061 | 0.258** | 0.504** | 0.517** | 0.289** | 0.390** | −0.191** | −0.247** | −0.446** | −0.294** | −0.263** | −0.305** | 0.455** | 0.504** | 0.415** | 0.342** | 0.390** | 0.505** | 0.677** | 1.000 | ||||||||||||||||
| OCO3 | −0.031 | 0.106* | 0.107* | 0.020 | 0.014 | 0.103* | 0.001 | −0.127* | 0.113* | 0.326** | 0.323** | 0.366** | 0.207** | −0.378** | −0.415** | −0.258** | −0.425** | −0.395** | −0.368** | 0.285** | 0.289** | 0.208** | 0.189** | 0.259** | 0.263** | 0.344** | 0.376** | 1.000 | |||||||||||||||
| OCO4 | 0.026 | 0.137** | 0.082 | 0.113* | 0.090 | 0.072 | −0.054 | −0.132** | 0.113* | 0.310** | 0.329** | 0.438** | 0.192** | −0.368** | −0.433** | −0.310** | −0.570** | −0.468** | −0.486** | 0.248** | 0.309** | 0.206** | 0.113* | 0.174** | 0.266** | 0.462** | 0.463** | 0.572** | 1.000 | ||||||||||||||
| OCO5 | −0.035 | 0.134** | 0.047 | 0.016 | 0.022 | 0.046 | −0.171** | −0.193** | −0.017 | 0.355** | 0.368** | 0.356** | 0.271** | −0.329** | −0.360** | −0.284** | −0.443** | −0.451** | −0.404** | 0.258** | 0.308** | 0.277** | 0.236** | 0.296** | 0.318** | 0.347** | 0.348** | 0.530** | 0.597** | 1.000 | |||||||||||||
| OCO6 | 0.062 | 0.249** | 0.136** | 0.152** | 0.144** | 0.089 | −0.064 | 0.011 | 0.123* | 0.398** | 0.384** | 0.167** | 0.318** | −0.139** | −0.0233** | −0.415** | −0.281** | −0.305** | −0.250** | 0.366** | 0.331** | 0.258** | 0.273** | 0.331** | 0.373** | 0.421** | 0.429** | 0.210** | 0.272** | 0.381** | 1.000 | ||||||||||||
| CWI1 | −0.073 | 0.008 | −0.083 | −0.094 | −0.024 | −0.049 | 0.085 | 0.146** | 0.043 | −0.207** | −0.228** | −0.309** | −0.149** | 0.316** | 0.394** | 0.191** | 0.396** | 0.382** | 0.415** | −0.082 | −0.178** | −0.084 | −0.009 | −0.058 | −0.060 | −0.200** | −0.215** | −0.331** | −0.426** | −0.345** | −0.124* | 1.000 | |||||||||||
| CWI2 | −0.045 | 0.013 | −0.021 | −0.083 | −0.019 | −0.070 | 0.057 | 0.127* | −0.040 | −0.291** | −0.279** | −0.261** | −0.161** | 0.215** | 0.324** | 0.215** | 0.361** | 0.371** | 0.396** | −0.225** | −0.245** | −0.214** | −0.198** | −0.244** | −0.206** | −0.259** | −0.281** | −0.455** | −0.424** | −0.413** | −0.154** | 0.641** | 1.000 | ||||||||||
| CWI3 | 0.022 | −0.043 | −0.006 | −0.090 | −0.035 | −0.062 | 0.094 | 0.126* | −0.050 | −0.248** | −0.292** | −0.330** | −0.143** | 0.307** | 0.403** | 0.162** | 0.445** | 0.421** | 0.487** | −0.152** | −0.214** | −0.147** | −0.041 | −0.131** | −0.174** | −0.309** | −0.336** | −0.369** | −0.495** | −0.422** | −0.154** | 0.682** | 0.649** | 1.000 | |||||||||
| CWO1 | −0.067 | −0.023 | −0.019 | −0.163** | −0.0113* | −0.081 | 0.038 | 0.075 | −0.070 | −0.283** | −0.333** | −0.301** | −0.193** | 0.197** | 0.280** | 0.212** | 0.332** | 0.358** | 0.402** | −0.239** | −0.305** | −0.274** | −0.202** | −0.269** | −0.249** | −0.345** | −0.388** | −0.407** | −0.471** | −0.442** | −0.185** | 0.592** | 0.697** | 0.729** | 1.000 | ||||||||
| CWO2 | −0.030 | −0.131** | −0.115* | −0.136** | −0.084 | −0.082 | −0.026 | −0.025 | −0.111* | −0.272** | −0.300** | −0.359** | −0.195** | 0.286** | 0.356** | 0.156** | 0.356** | 0.304** | 0.375** | −0.208** | −0.280** | −0.189** | −0.154** | −0.218** | −0.187** | −0.289** | −0.364** | −0.350** | −0.459** | −0.353** | −0.167** | 0.520** | 0.499** | 0.636** | 0.614** | 1.000 | |||||||
| CWO3 | −0.066 | −0.166** | −0.104* | −0.132** | −0.120* | −0.159** | 0.005 | 0.021 | −0.122* | −0.263** | −0.311** | −0.323** | −0.154** | 0.277** | 0.313** | 0.124* | 0.427** | 0.351** | 0.416** | −0.152** | −0.227** | −0.222** | −0.140** | −0.167** | −0.189** | −0.240** | −0.327** | −0.326** | −0.468** | −0.362** | −0.154** | 0.492** | 0.394** | 0.638** | 0.579** | 0.611** | 1.000 | ||||||
| ISS1 | 0.170** | 0.313** | 0.262** | 0.213** | 0.233** | 0.202** | 0.006 | 0.053 | 0.175** | 0.569** | 0.518** | 0.088 | 0.474** | −0.084 | −0.164** | −0.489** | −0.257** | −0.264** | −0.269** | 0.432** | 0.444** | 0.440** | 0.475** | 0.501** | 0.503** | 0.443** | 0.413** | 0.275** | 0.243** | 0.346** | 0.391** | −0.137** | −0.248** | −0.166** | −0.230** | −0.189** | −0.198** | 1.000 | |||||
| ISS2 | 0.151** | 0.317** | 0.293** | 0.270** | 0.170** | 0.233** | 0.041 | 0.010 | 0.200** | 0.615** | 0.569** | 0.170** | 0.467** | −0.109* | −0.197** | −0.531** | −0.330** | −0.310** | −0.327** | 0.435** | 0.482** | 0.518** | 0.487** | 0.549** | 0.544** | 0.456** | 0.474** | 0.318** | 0.294** | 0.337** | 0.363** | −0.228** | −0.326** | −0.260** | −0.272** | −0.277** | −0.272** | 0.685** | 1.000 | ||||
| ISS3 | 0.126* | 0.326** | 0.282** | 0.241** | 0.176** | 0.187** | 0.053 | 0.064 | 0.209** | 0.600** | 0.559** | 0.175** | 0.471** | −0.141** | −0.231** | −0.517** | −0.360** | −0.317** | −0.328** | 0.473** | 0.491** | 0.487** | 0.480** | 0.542** | 0.551** | 0.465** | 0.456** | 0.344** | 0.329** | 0.333** | 0.409** | −0.173** | −0.315** | −0.241** | −0.276** | −0.252** | −0.270** | 0.684** | 0.795** | 1.000 | |||
| ISS4 | 0.234** | 0.341** | 0.330** | 0.299** | 0.268** | 0.303** | 0.112* | 0.021 | 0.218** | 0.556** | 0.529** | 0.219** | 0.433** | −0.179** | −0.275** | −0.531** | −0.356** | −0.325** | −0.340** | 0.414** | 0.461** | 0.427** | 0.395** | 0.413** | 0.482** | 0.508** | 0.526** | 0.303** | 0.341** | 0.310** | 0.404** | −0.232** | −0.319** | −0.285** | −0.336** | −0.256** | −0.271** | 0.601** | 0.711** | 0.751** | 1.000 | ||
| ISS5 | 0.152** | 0.353** | 0.325** | 0.263** | 0.226** | 0.278** | 0.056 | −0.001 | 0.221** | 0.608** | 0.601** | 0.181** | 0.482** | −0.164** | −0.247** | −0.536** | −0.357** | −0.317** | −0.343** | 0.443** | 0.452** | 0.433** | 0.409** | 0.468** | 0.521** | 0.510** | 0.538** | 0.317** | 0.324** | 0.296** | 0.414** | −0.199** | −0.290** | −0.283** | −0.284** | −0.251** | −0.270** | 0.638** | 0.717** | 0.751** | 0.833** | 1.000 | |
| ISS6 | 0.172** | 0.352** | 0.316** | 0.253** | 0.207** | 0.237** | 0.098 | 0.075 | 0.267** | 0.563** | 0.565** | 0.186** | 0.487** | −0.174** | −0.237** | −0.494** | −0.317** | −0.298** | −0.335** | 0.493** | 0.474** | 0.440** | 0.403** | 0.461** | 0.520** | 0.501** | 0.493** | 0.294** | 0.334** | 0.316** | 0.370** | −0.207** | −0.302** | −0.265** | −0.282** | −0.262** | −0.237** | 0.629** | 0.693** | 0.757** | 0.725** | 0.814** | 1.000 |
References
- Aniscenko, Z.; Robalino-López, A.; Rodrígue, T.E.; Pérez, B.E. Regional Cooperation in Dealing with Environmental Protection. E-Government and Sustainable Development in Andean Countries. In Proceedings of the International Scientific and Practical Conference, Rezekne, Latvia, 15–17 June 2017. [Google Scholar] [CrossRef]
- Nica, E.; Potcovaru, A. Effective m-government services and increased citizen participation: Flexible and personalized ways of interacting with public administrations. J. Self-Gov. Manag. Econ. 2015, 3, 92–97. [Google Scholar]
- Lee, Y.B. Exploring the relationship between E-government development and environmental sustainability: A study of small island developing states. Sustainability 2017, 9, 732. [Google Scholar] [CrossRef]
- Bernhard, I.; Wihlborg, E. Municipal contact centres: A slower approach towards sustainable local development by E-government. Eur. Plan. Stud. 2015, 23, 2292–2309. [Google Scholar] [CrossRef]
- Choi, H.; Park, M.J.; Rho, J.J.; Zo, H. Rethinking the assessment of E-government implementation in developing countries from the perspective of the design–reality gap: Applications in the Indonesian e-procurement system. Telecommun. Policy 2016, 40, 644–660. [Google Scholar] [CrossRef]
- Estevez, E.; Janowski, T. Electronic governance for sustainable development: Conceptual framework and state of research. Gov. Inf. Q. 2013, 30, S94–S109. [Google Scholar] [CrossRef]
- Janowski, T. Implementing sustainable development goals with digital government—Aspiration-capacity gap. Gov. Inf. Q. 2016, 33, 603–613. [Google Scholar] [CrossRef]
- Larsson, H.; Grönlund, A. Sustainable eGovernance? Practices, problems and beliefs about the future in Swedish eGov practice. Gov. Inf. Q. 2016, 33, 105–114. [Google Scholar] [CrossRef]
- Hu, Q.; Hart, P.; Cooke, D. The Role of External Influences on Organizational Information Security Practices: An Institutional Perspective. In Proceedings of the Annual Hawaii International Conference on System Sciences, Kauai, Hawaii, 4–7 January 2006; Volume 6, pp. 1–10. [Google Scholar]
- Zheng, D.; Chen, J.; Huang, L.; Zhang, C. E-government adoption in public administration organizations: Integrating institutional theory perspective and resource-based view. Eur. J. Inf. Syst. 2013, 22, 221–234. [Google Scholar] [CrossRef]
- Coursey, D.; Norris, D.F. Models of E-government: Are they correct? An empirical assessment. Public Adm. Rev. 2008, 68, 523–536. [Google Scholar] [CrossRef]
- Boss, S.R.; Kirsch, L.J.; Angermeier, I.; Shingler, R.A.; Boss, R.W. If someone is watching, I’ll do what I’m asked: Mandatoriness, control, and information security. Eur. J. Inf. Syst. 2009, 18, 151–164. [Google Scholar] [CrossRef]
- Hill, L.B.; Pemberton, J.M. Information security: An overview and resource guide for information managers. Rec. Manag. Q. 1995, 29, 14–24. [Google Scholar]
- Hsu, C.; Lee, J.; Straub, D.W. Institutional influences on information systems security innovations. Inf. Syst. Res. 2012, 23, 918–939. [Google Scholar] [CrossRef]
- PricewaterhouseCoopers. Key Findings from the 2013 US State of Cybercrime Survey; PricewaterhouseCoopers: Delaware, DE, USA, 2013; Available online: http://cybersafetyunit.com/download/pdf/us-state-of-cybercrime.pdf (accessed on 10 May 2018).
- Willison, R.; Warkentin, M. Beyond deterrence: An expanded view of employee computer abuse. MIS Q. 2013, 37, 1–20. [Google Scholar] [CrossRef]
- Feng, N.; Wang, H.J.; Li, M. A security risk analysis model for information systems: Causal relationships of risk factors and vulnerability propagation analysis. Inf. Sci. 2014, 256, 57–73. [Google Scholar] [CrossRef]
- National Security Institute. Cyber Security: Keeping Up with the Threat; National Security Institute: Medway, MA, USA, 2009. [Google Scholar]
- Bjorck, F. Institutional Theory: A New Perspective for Research into IS/IT Security in Organisations. In Proceedings of the 37th Hawaii International Conference on System Sciences, Big Island, Hawaii, 5–8 January 2004. [Google Scholar]
- DiMaggio, P.J.; Powell, W.W. The iron cage revisited: Institutional isomorphism and collective rationality in organizational fields. Am. Sociol. Rev. 1983, 48, 147–160. [Google Scholar] [CrossRef]
- Meyer, J.W.; Rowan, B. Institutionalized organizations: Formal structure as myth and ceremony. Am. J. Sociol. 1977, 83, 340–363. [Google Scholar] [CrossRef]
- Sun, P.L.; Ku, C.Y.; Shih, D.H. An implementation framework for E-government 2.0. Telemat. Inform. 2015, 32, 504–520. [Google Scholar] [CrossRef]
- National Information Society Agency. The United Nations Project Office on Governance E-Government of Korea: Best Practices; Ministry of Public Administration and Security: Seoul, Korea, 2009.
- Greene, G.; D’Arcy, J. Assessing the Impact of Security Culture and the Employee-Organization Relationship on IS Security Compliance. In Proceedings of the 5th Annual Symposium on Information Assurance (ASIA’10), Albany, NY, USA, 16–17 June 2010; pp. 1–8. [Google Scholar]
- Nazareth, D.L.; Choi, J. A system dynamics model for information security management. Inf. Manag. 2015, 52, 123–134. [Google Scholar] [CrossRef]
- Ifinedo, P. Information systems security policy compliance: An empirical study of the effects of socialisation, influence, and cognition. Inf. Manag. 2014, 51, 69–79. [Google Scholar] [CrossRef]
- Kraemer, S.; Carayon, P.; Clem, J. Human and organizational factors in computer and information security: Pathways to vulnerabilities. Comput. Secur. 2009, 28, 509–520. [Google Scholar] [CrossRef]
- Dhillon, G.; Backhouse, J. Current directions in IS security research: Towards socio-organizational perspectives. Inf. Syst. J. 2001, 11, 127–153. [Google Scholar] [CrossRef]
- Currie, W.L. Institutional isomorphism and change: The national programme for IT—10 years on. J. Inf. Technol. 2012, 27, 236–248. [Google Scholar] [CrossRef]
- Eom, S. Institutional dimensions of E-government development: Implementing the business reference model in the United States and Korea. Adm. Soc. 2012, 45, 875–907. [Google Scholar] [CrossRef]
- Hsu, C.W. Frame misalignment: Interpreting the implementation of information systems security certification in an organization. Eur. J. Inf. Syst. 2009, 18, 140–150. [Google Scholar] [CrossRef]
- Ashworth, R.; Boyne, G.; Delbridge, R. Escape from the iron cage? Organizational change and isomorphic pressures in the public sector. J. Public Adm. Res. Theory 2009, 19, 165–187. [Google Scholar] [CrossRef]
- Frumkin, P.; Galaskiewicz, J. Institutional isomorphism and public sector organizations. J. Public Adm. Res. Theory 2004, 14, 283–307. [Google Scholar] [CrossRef]
- Tolbert, P.S.; Zucker, L.G. Institutional sources of change in the formal structure of organizations: The diffusion of civil service reform, 1880–1935. Adm. Sci. Q. 1983, 28, 22–39. [Google Scholar] [CrossRef]
- Lawton, A.; McKevitt, D.; Millar, M. Developments: Coping with ambiguity: Reconciling external legitimacy and organizational implementation in performance measurement. Public Money Manag. 2000, 20, 13–20. [Google Scholar] [CrossRef]
- Leiter, J. Structural isomorphism in Australian nonprofit organizations. Int. J. Volunt. Nonprofit Org. 2005, 16, 1–31. [Google Scholar] [CrossRef]
- Hu, Q.; Hart, P.; Cooke, D. The role of external and internal influences on information systems security—A neo-institutional perspective. J. Strateg. Inf. Syst. 2007, 16, 153–172. [Google Scholar] [CrossRef]
- Currie, W.L.; Swanson, E.B. Special issue on institutional theory in information systems research: Contextualizing the IT artefact. J. Inf. Technol. 2009, 24, 283–285. [Google Scholar] [CrossRef]
- Herold, D.M.; Fedor, D.B.; Caldwell, S.; Liu, Y. The effects of transformational and change leadership on employees’ commitment to a change: A multilevel study. J. Appl. Psychol. 2008, 93, 346–357. [Google Scholar] [CrossRef] [PubMed]
- Carpenter, V.L.; Feroz, E.H. Institutional theory and accounting rule choice: An analysis of four US state governments’ decisions to adopt generally accepted accounting principles. Account. Organ. Soc. 2001, 26, 565–596. [Google Scholar] [CrossRef]
- Cordella, A.; Tempini, N. E-government and organizational change: Reappraising the role of ICT and bureaucracy in public service delivery. Gov. Inf. Q. 2015, 32, 279–286. [Google Scholar] [CrossRef]
- Bulgurcu, B.; Cavusoglu, H.; Benbasat, I. Information security policy compliance: An empirical study of rationality-based beliefs and information security awareness. MIS Q. 2010, 34, 523–548. [Google Scholar] [CrossRef]
- Knapp, K.J.; Marshall, T.E.; Rainer, R.K., Jr.; Ford, F.N. Information security effectiveness: Conceptualization and validation of a theory. Int. J. Inf. Secur. Priv. 2007, 1, 37–60. [Google Scholar] [CrossRef]
- Straub, D.W. Effective IS security: An empirical study. Inf. Syst. Res. 1990, 1, 255–276. [Google Scholar] [CrossRef]
- Kankanhalli, A.; Teo, H.H.; Tan, B.C.Y.; Wei, K.K. An integrative study of information systems security effectiveness. Int. J. Inf. Manag. 2003, 23, 139–154. [Google Scholar] [CrossRef]
- Hagen, J.M.; Albrechtsen, E.; Hovden, J. Implementation and effectiveness of organizational information security measures. Inf. Manag. Secur. 2008, 16, 377–397. [Google Scholar] [CrossRef]
- Selander, L.; Henfridsson, O. Cynicism as user resistance in IT implementation. Inf. Syst. J. 2012, 22, 289–312. [Google Scholar] [CrossRef]
- Orlikowski, W.J.; Barley, S.R. Technology and institutions: What can research on information technology and research on organizations learn from each other? MIS Q. 2001, 25, 145–165. [Google Scholar] [CrossRef]
- Podsakoff, P.M.; MacKenzie, S.B. Organizational citizenship behaviors and sales unit effectiveness. J. Mark. Res. 1994, 31, 351–363. [Google Scholar]
- Pavlou, P.A.; Fygenson, M. Understanding and predicting electronic commerce adoption: An extension of the theory of planned behavior. MIS Q. 2006, 30, 115–143.54. [Google Scholar] [CrossRef]
- Rao, H. The social construction of reputation: Certification contests, legitimation, and the survival of organizations in the American automobile industry: 1895–1912. Strateg. Manag. J. 1994, 15, 29–44. [Google Scholar] [CrossRef]
- Borman, W.C.; Motowidlo, S.J. Task performance and contextual performance: The meaning for personnel selection research. Hum. Perform. 1997, 10, 99–109. [Google Scholar] [CrossRef]
- Dalal, R.S. A meta-analysis of the relationship between organizational citizenship behavior and counterproductive work behavior. Am. Psychol. Assoc. 2005, 90, 1241–1255. [Google Scholar] [CrossRef] [PubMed]
- Lodge, M.; Wegrich, K. Control over government: Institutional isomorphism and governance dynamics in German public administration. Policy Stud. J. 2005, 33, 213–233. [Google Scholar] [CrossRef]
- Seo, M.; Creed, W.D. Institutional contradictions, praxis, and institutional change: A dialectical perspective. Acad. Manag. Rev. 2002, 27, 222–247. [Google Scholar] [CrossRef]
- Ashforth, B.E.; Gibbs, B.W. The double-edge of organizational legitimation. Org. Sci. 1990, 1, 177–194. [Google Scholar] [CrossRef]
- Scott, W.R. Institutions and Organizations, 2nd ed.; Sage: Thousand Oaks, CA, USA, 2001. [Google Scholar]
- Suchman, M.C. Managing legitimacy—Strategic and institutional approaches. Acad. Manag. Rev. 1995, 20, 571–610. [Google Scholar] [CrossRef]
- Westphal, J.D.; Gulati, R.; Shortell, S.M. Customization or conformity? An institutional and network perspective on the content and consequences of TQM adoption. Adm. Sci. Q. 1997, 42, 366–394. [Google Scholar] [CrossRef]
- Reichers, A.E.; Wanous, J.P.; Austin, J.T. Understanding and managing cynicism about organizational change. Acad. Manag. Exec. 1997, 11, 48–59. [Google Scholar] [CrossRef]
- Irvine, H.J. Corporate creep: An institutional view of consultancies in a non-profit organisation. Aust. Account. Rev. 2007, 17, 13–25. [Google Scholar] [CrossRef]
- Organ, D.W. Organizational Citizenship Behavior: The Good Soldier Syndrome; Lexington Books/D. C. Heath and Co.: Lexington, MA, USA, 1988. [Google Scholar]
- Lawrence, J.; Ott, M.; Bell, A. Faculty organizational commitment and citizenship. Res. High. Educ. 2012, 53, 325–352. [Google Scholar] [CrossRef]
- Williams, L.J.; Anderson, S.E. Job satisfaction and organizational commitment as predictors of organizational citizenship and in-role behaviors. J. Manag. 1991, 17, 601–617. [Google Scholar] [CrossRef]
- Sharma, U.; Lawrence, S.; Lowe, A. Institutional contradiction and management control innovation: A field study of total quality management practices in a privatized telecommunication company. Manag. Account. Res. 2010, 21, 251–264. [Google Scholar] [CrossRef]
- Evans, W.R.; Novicevic, M.M. Legitimacy of HRM practices: Managerial perceptions of economic and normative value. J. Appl. Manag. Entrep. 2010, 15, 13–27. [Google Scholar]
- Wat, D.; Shaffer, M.A. Equity and relationship quality influences on organizational citizenship behaviors: The mediating role of trust in the supervisor and empowerment. Pers. Rev. 2005, 34, 406–422. [Google Scholar] [CrossRef]
- Yen, H.R.; Li, E.Y.; Niehoff, B.P. Do organizational citizenship behaviors lead to information system success? Testing the mediation effects of integration climate and project management. Inf. Manag. 2008, 45, 394–402. [Google Scholar] [CrossRef]
- Ke, W.; Wei, K.K. Organizational culture and leadership in ERP implementation. Decis. Support Syst. 2008, 45, 208–218. [Google Scholar] [CrossRef]
- Holderness, D.; Litzky, B.; MacLean, T. When organizations don’t walk their talk: A cross-level examination of how decoupling formal ethics programs affects organizational members. J. Bus. Ethics 2015, 128, 351–368. [Google Scholar]
- Hwang, K.; Choi, M. Effects of innovation-supportive culture and organizational citizenship behavior on E-government information system security stemming from mimetic isomorphism. Gov. Inf. Q. 2017, 34, 183–198. [Google Scholar] [CrossRef]
- Dyne, L.; LePine, J.A. Helping and voice extra-role behaviors: Evidence of construct and predictive validity. Acad. Manag. J. 1998, 41, 108–119. [Google Scholar]
- McNeely, B.L.; Meglino, B.M. The role of dispositional and situational antecedents in prosocial organizational behavior: An examination of the intended beneficiaries of prosocial behavior. J. Appl. Psychol. 1994, 79, 836–844. [Google Scholar] [CrossRef]
- Crowe, E.; Higgins, E.T. Regulatory focus and strategic inclinations: Promotion and prevention in decision-making. Org. Behav. Hum. Decis. Process. 1997, 69, 117–132. [Google Scholar] [CrossRef]
- Atwater, L.E.; Waldman, D.A.; Atwater, D.; Cartier, P. An upward feedback field experiment: Supervisors’ cynicism, reactions, and commitment to subordinates. Pers. Psychol. 2000, 53, 275–297. [Google Scholar] [CrossRef]
- Dean, J.W.; Brandes, P.; Dharwadkar, R. Organizational cynicism. Acad. Manag. Rev. 1998, 23, 341–352. [Google Scholar] [CrossRef]
- Bergström, O.; Styhre, A.; Thilander, P. Paradoxifying organizational change: Cynicism and resistance in the Swedish armed forces. J. Chang. Manag. 2014, 14, 384–404. [Google Scholar] [CrossRef]
- Brown, M.; Cregan, C. Organizational change cynicism: The role of employee involvement. Hum. Resour. Manag. 2008, 47, 667–686. [Google Scholar] [CrossRef]
- Stanley, D.J.; Meyer, J.P.; Topolnytsky, L. Employee cynicism and resistance to organizational change. J. Bus. Psychol. 2005, 19, 429–459. [Google Scholar] [CrossRef]
- Martinko, M.J.; Zmud, R.W.; Henry, J.W. An attributional explanation of individual resistance to the introduction of information technologies in the workplace. Behav. Inf. Technol. 1996, 15, 313–330. [Google Scholar] [CrossRef]
- Bommer, W.H.; Rich, G.A.; Rubin, R.S. Changing attitudes about change: Longitudinal effects of transformational leader behavior on employee cynicism about organizational change. J. Org. Behav. 2005, 26, 733–753. [Google Scholar] [CrossRef]
- Wanous, J.P.; Reichers, A.E.; Austin, J.T. Cynicism about organizational change measurement, antecedents, and correlates. Group Org. Manag. 2000, 25, 132–153. [Google Scholar] [CrossRef]
- Kotter, J.P. Leading change: Why transformation efforts fail. Harv. Bus. Rev. 2007, 85, 96–103. [Google Scholar]
- McKinley, W.; Sanchez, C.M.; Schick, A.G. Organizational downsizing: Constraining, cloning, learning. Acad. Manag. Exec. 1995, 9, 32–42. [Google Scholar] [CrossRef]
- Lapointe, L.; Rivard, S. A multilevel model of resistance to information technology. MIS Q. 2005, 29, 461–491. [Google Scholar] [CrossRef]
- Joshi, K. A model of users’ perspective on change: The case of information systems technology implementation. MIS Q. 1991, 15, 229–242. [Google Scholar] [CrossRef]
- Marakas, G.M.; Hornik, S. Passive resistance misuse: Overt support and covert recalcitrance in IS implementation. Eur. J. Inf. Syst. 1996, 5, 208–219. [Google Scholar] [CrossRef]
- Gaski, J.F. The theory of power and conflict in channels of distribution. J. Mark. 1984, 48, 9–29. [Google Scholar] [CrossRef]
- Markus, M.L. Power, politics, and MIS implementation. Commun. ACM 1983, 26, 430–444. [Google Scholar] [CrossRef]
- Martinko, M.J.; Gundlach, M.J.; Douglas, S.C. Toward an integrative theory of counterproductive workplace behavior: A causal reasoning perspective. Int. J. Sel. Assess. 2002, 10, 36–50. [Google Scholar] [CrossRef]
- Vance, R.; Brooks, S.; Tesluk, P. Organizational Cynicism, Cynical Cultures, and Organizational Change Efforts. In Proceedings of the 10th Annual Conference of the Society for Industrial and Organizational Psychology, Orlando, FL, USA, 17–20 May 1995. [Google Scholar]
- MacLean, T.; Behnam, M. The dangers of decoupling: The relationship between compliance programs, legitimacy perceptions and institutionalized misconduct. Acad. Manag. J. 2010, 53, 1499–1520. [Google Scholar] [CrossRef]
- Jensen, J.M.; Opland, R.A.; Ryan, A.M. Psychological contracts and counterproductive work behaviors: Employee responses to transactional and relational breach. J. Bus. Psychol. 2010, 25, 555–568. [Google Scholar] [CrossRef]
- Band, S.R.; Cappelli, D.M.; Fischer, L.F.; Moore, A.P.; Shaw, E.D.; Trzeciak, R.F. Comparing Insider IT Sabotage and Espionage: A Model-Based Analysis; Technical Report CMU/SEI-2006-TR-026, ESC-TR-2006-091; Defense Technical Information Center: Fort Belvoir, VA, USA, 2006.
- Rhee, H.S.; Kim, C.; Ryu, Y.U. Self-efficacy in information security: Its influence on end users’ information security practice behavior. Comput. Secur. 2009, 28, 816–826. [Google Scholar] [CrossRef]
- Marcus, B.; Schuler, H. Antecedents of counterproductive behavior at work: A general perspective. J. Appl. Psychol. 2004, 89, 647–660. [Google Scholar] [CrossRef] [PubMed]
- Heugens, P.P.; Lander, M.W. Structure! Agency! (and other quarrels): A meta-analysis of institutional theories of organization. Acad. Manag. J. 2009, 52, 61–85. [Google Scholar] [CrossRef]
- Liang, H.; Saraf, N.; Hu, Q.; Xue, Y. Assimilation of enterprise systems: The effect of institutional pressures and the mediating role of top management. MIS Q. 2007, 31, 59–87. [Google Scholar] [CrossRef]
- Lee, S.; Yoon, J. The effects of corporate social responsibility. Korean Manag. Rev. 2011, 40, 919–954. [Google Scholar]
- Yoon, J.; Thye, S. Supervisor support in the work place: Legitimacy and positive affectivity. J. Soc. Psychol. 2000, 140, 295–316. [Google Scholar] [CrossRef] [PubMed]
- Bennett, R.J.; Robinson, S.L. Development of a measure of workplace deviance. J. Appl. Psychol. 2000, 85, 349–360. [Google Scholar] [CrossRef] [PubMed]
- Aquino, K.; Lewis, M.U.; Bradfield, M. Justice constructs, negative affectivity, and employee deviance: A proposed model and empirical test. J. Org. Behav. 1999, 20, 1073–1091. [Google Scholar] [CrossRef]
- D’Arcy, J.; Herath, T. A review and analysis of deterrence theory in the IS security literature: Making sense of the disparate findings. Eur. J. Inf. Syst. 2011, 20, 643–658. [Google Scholar] [CrossRef]
- Herath, T.; Rao, H.R. Encouraging information security behaviors in organizations: Role of penalties, pressures and perceived effectiveness. Decis. Support Syst. 2009, 47, 154–165. [Google Scholar] [CrossRef]
- Gefen, D.; Straub, D.W.; Boudreau, M.C. Structural equation modeling and regression: Guidelines for research practice. Commun. Assoc. Inf. Syst. 2000, 4, 2–76. [Google Scholar]
- Byrne, B.M. Structural Equation Modeling with EQS and EQS Windows; Sage: London, UK, 1994. [Google Scholar]
- Vroom, C.; von Solms, R. Towards information security behavioural compliance. Comput. Secur. 2004, 23, 191–198. [Google Scholar] [CrossRef]
- Chin, W.W.; Newsted, P.R. (Eds.) Structural Equation Modeling Analysis with Small Samples Using Partial Least Squares. In Statistical Strategies for Small Sample Research; Sage: Thousand Oaks, CA, USA, 1999. [Google Scholar]
- Podsakoff, P.M.; Mackenzie, S.B.; Lee, J.Y.; Podsakoff, N.P. Common method biases in behavioral research: A critical review of the literature and recommended remedies. J. Appl. Psychol. 2003, 88, 879–903. [Google Scholar] [CrossRef] [PubMed]
- Mezias, S.J. An institutional model of organizational practice: Financial reporting at the Fortune 200. Adm. Sci. Q. 1990, 35, 431–457. [Google Scholar] [CrossRef]
- Eisenbach, R.; Watson, K.; Pillai, R. Transformational leadership in the context of organizational change. J. Org. Chang. Manag. 1999, 12, 80–89. [Google Scholar] [CrossRef]
| Hypotheses |
|---|
| H1. Normative isomorphism is positively associated with ISS legitimacy. |
| H2. Coercive isomorphism is positively associated with ISS legitimacy. |
| H3. Mimetic isomorphism is positively associated with ISS legitimacy. |
| H4. The legitimacy of ISS is positively associated with OCB-I. |
| H5. The legitimacy of ISS is positively associated with OCB-O. |
| H6. OCB-I is positively associated with ISS effectiveness. |
| H7. OCB-O is positively associated with ISS effectiveness. |
| H8. Normative isomorphism is negatively associated with organizational cynicism toward ISS. |
| H9. Coercive isomorphism is positively associated with organizational cynicism toward ISS. |
| H10. Mimetic isomorphism is positively associated with organizational cynicism toward ISS. |
| H11. Organizational cynicism toward ISS is positively associated with ISS-related CWB-O. |
| H12. Organizational cynicism toward ISS is positively associated with ISS-related CWB-I. |
| H13. Employees’ ISS-related CWB-O is negatively associated with ISS effectiveness. |
| H14. Employees’ ISS-related CWB-I is negatively associated with ISS effectiveness. |
| No. of Institutions | Minimum No. of Responses per Institution | Average No. of Responses per Institution | Maximum No. of Responses per Institution | STD of Response |
|---|---|---|---|---|
| 35 | 10 | 11.38 | 14 | 1.414 |
| Item | Variable | Frequency | Percentage (%) |
|---|---|---|---|
| Sex | Male | 251 | 64.7 |
| Female | 137 | 35.3 | |
| Age | Under 20 years | 2 | 0.5 |
| 21–30 years | 34 | 8.8 | |
| 31–40 years | 179 | 46.1 | |
| 41–50 years | 151 | 38.9 | |
| Above 51 years | 22 | 5.7 | |
| Years Worked | Less than 1 year | 31 | 8.0 |
| 1–5 years | 95 | 24.5 | |
| 5–10 years | 98 | 25.3 | |
| 10–15 years | 48 | 12.4 | |
| More than 15 years | 116 | 29.8 | |
| Position | Staff | 298 | 76.8 |
| Assistant manager | 67 | 17.3 | |
| Manager | 15 | 3.9 | |
| Deputy director | 5 | 1.2 | |
| Above the department head | 3 | 0.8 | |
| Education | High School Diploma | 11 | 2.8 |
| Junior College | 32 | 8.2 | |
| Bachelor’s | 273 | 70.4 | |
| Master’s or above | 72 | 18.6 | |
| Marriage | No | 89 | 22.9 |
| Yes | 299 | 77.1 | |
| Income Satisfaction | Very dissatisfied | 49 | 12.6 |
| Dissatisfied | 136 | 35.1 | |
| Normal | 167 | 43.0 | |
| Satisfied | 34 | 8.8 | |
| Very Satisfied | 2 | 0.5 | |
| Type of Employment | Regular | 374 | 96.4 |
| Irregular | 14 | 3.6 | |
| Size of Institution | Under 100 | 49 | 12.6 |
| 101–300 | 28 | 7.2 | |
| 301–600 | 66 | 17.0 | |
| 601–1000 | 58 | 14.9 | |
| 1001–1500 | 90 | 23.3 | |
| Above 1500 | 97 | 25.0 |
| AVE | Composite Reliability | R Square | Cronbach’s Alpha | |
|---|---|---|---|---|
| Mimetic isomorphism | 0.645185 | 0.844393 | 0.735412 | |
| Normative isomorphism | 0.619343 | 0.825809 | 0.706008 | |
| Coercive isomorphism | 0.623745 | 0.83251 | 0.703965 | |
| Organizational cynicism | 0.597637 | 0.835573 | 0.054163 | 0.713303 |
| Organizational legitimacy | 0.6454 | 0.871665 | 0.180938 | 0.793318 |
| CPB-I | 0.771427 | 0.910104 | 0.269298 | 0.852071 |
| CPB-O | 0.734134 | 0.892285 | 0.225212 | 0.818957 |
| OCB-I | 0.72694 | 0.941019 | 0.370497 | 0.924607 |
| OCB-O | 0.5234 | 0.867371 | 0.361063 | 0.818201 |
| ISS effectiveness | 0.766965 | 0.951722 | 0.517974 | 0.938844 |
| COR | CPB-I | CPB-O | CYN | ISS | LEG | MIM | NOR | OCB-I | OCB-O | |
|---|---|---|---|---|---|---|---|---|---|---|
| COR | 0.7898 | |||||||||
| CWB-I | −0.0905 | 0.8783 | ||||||||
| CWB-O | −0.1800 | 0.7708 | 0.8568 | |||||||
| CYN | −0.1805 | 0.5189 | 0.4746 | 0.7731 | ||||||
| ISS | 0.3471 | −0.3270 | −0.3484 | −0.4554 | 0.8758 | |||||
| LEG | 0.3675 | −0.3224 | −0.3763 | −0.5106 | 0.6725 | 0.8034 | ||||
| MIM | 0.4949 | 0.0797 | −0.0466 | 0.0153 | 0.1648 | 0.2037 | 0.8032 | |||
| NOR | 0.6354 | −0.0309 | −0.1233 | −0.1606 | 0.4074 | 0.3984 | 0.4436 | 0.7870 | ||
| OCB-I | 0.2469 | −0.2013 | −0.2953 | −0.2998 | 0.6317 | 0.6087 | 0.1268 | 0.2787 | 0.8526 | |
| OCB-O | 0.2630 | −0.4822 | −0.5342 | −0.6053 | 0.6210 | 0.6009 | 0.0646 | 0.2617 | 0.5290 | 0.7235 |
| Direct Path | Direct Effect | Indirect Path | Indirect Effect | Total Effect |
|---|---|---|---|---|
| MIM→ISS | 0.220 | MIM→CYN→CWB-O→ISS | 0 | 0.21125 |
| MIM→CYN→CWB-I→ISS | −0.00875 | |||
| MIM→LEG→OCB-O→ISS | 0 | |||
| MIM→LEG→OCB-I→ISS | 0 | |||
| NOR→ISS | 0.405 | NOR→CYN→CWB-O→ISS | 0 | 0.547866 |
| NOR→CYN→CWB-I→ISS | 0.006167 | |||
| NOR→LEG→OCB-O→ISS | 0.063193 | |||
| NOR→LEG→OCB-I→ISS | 0.073506 | |||
| COR→ISS | 0.349 | COR→CYN→CWB-O→ISS | 0 | 0.435236 |
| COR→CYN→CWB-I→ISS | −0.010427 | |||
| COR→LEG→OCB-O→ISS | 0.044685 | |||
| COR→LEG→OCB-I→ISS | 0.051978 |
| Construct | Indicator | Substantive Factor Loading (R1) | Variance Explained (R12) | Method Factor Loading (R2) | Variance Explained (R22) |
|---|---|---|---|---|---|
| MIM | MIM1 | 0.812963 *** | 0.660909 | −0.073371 *** | 0.005383 |
| MIM2 | 0.846459 *** | 0.716493 | −0.124683 *** | 0.015546 | |
| MIM3 | 0.767061 *** | 0.588383 | 0.194827 *** | 0.037958 | |
| NOR | NOR1 | 0.748915 *** | 0.560874 | −0.10148 *** | 0.010298 |
| NOR2 | 0.769432 *** | 0.592026 | 0.090442 | 0.008180 | |
| NOR3 | 0.866657 *** | 0.751094 | −0.007805 * | 0.000061 | |
| COR | COR1 | 0.712957 *** | 0.508308 | 0.070066 * | 0.004909 |
| COR2 | 0.883308 *** | 0.780233 | −0.068065 | 0.004633 | |
| COR3 | 0.780284 *** | 0.608843 | 0.000226 *** | 0.000000 | |
| CYNICISM | CYN1 | 0.809017 *** | 0.654509 | 0.190741 *** | 0.036382 |
| CYN2 | 0.862651 *** | 0.744167 | 0.139019 *** | 0.019326 | |
| CYN3 | −0.136808 | 0.018716 | 0.555802 | 0.308916 | |
| CYN4 | 0.906013 *** | 0.820860 | 0.029836 * | 0.000890 | |
| CYN5 | 0.91641 *** | 0.839807 | 0.064104 * | 0.004109 | |
| CYN6 | 0.86035 *** | 0.740202 | 0.010063 | 0.000101 | |
| LEG | LEG1 | 0.908081 *** | 0.824611 | 0.010166 | 0.000103 |
| LEG2 | 0.916257 *** | 0.839527 | 0.015251 | 0.000233 | |
| LEG3 | 0.290009 ** | 0.084105 | 0.200881 * | 0.040353 | |
| LEG4 | 0.946049 *** | 0.895009 | −0.154464 *** | 0.023859 | |
| CWB_I | CWB-I1 | 0.925239 *** | 0.856067 | 0.082818 | 0.006859 |
| CWB-I2 | 0.842171 *** | 0.709252 | −0.04842 | 0.002344 | |
| CWB-I3 | 0.868912 *** | 0.755008 | −0.032614 | 0.001064 | |
| CWB_O | CWB-O1 | 0.821208 *** | 0.674383 | −0.052408 | 0.002747 |
| CWB-O2 | 0.880718 *** | 0.775664 | 0.024441 | 0.000597 | |
| CWB-O3 | 0.868561 *** | 0.754398 | 0.027931 | 0.000780 | |
| OCB_I | OCB-I1 | 0.718229 *** | 0.515853 | 0.091647 * | 0.008399 |
| OCB-I2 | 0.792826 *** | 0.628573 | 0.090358 ** | 0.008165 | |
| OCB-I3 | 0.900454 *** | 0.810817 | −0.051505 | 0.002653 | |
| OCB-I4 | 0.977428 *** | 0.955365 | −0.154143 *** | 0.023760 | |
| OCB-I5 | 0.908722 *** | 0.825776 | −0.03928 | 0.001543 | |
| OCB-I6 | 0.812118 *** | 0.659536 | 0.067176 | 0.004513 | |
| OCB_O | OCB-O1 | 0.65524 *** | 0.429339 | 0.12939 ** | 0.016742 |
| OCB-O2 | 0.627347 *** | 0.393564 | 0.176421 *** | 0.031124 | |
| OCB-O3 | 0.770986 *** | 0.594419 | −0.098541 | 0.009710 | |
| OCB-O4 | 0.903246 *** | 0.815853 | −0.154556 *** | 0.023888 | |
| OCB-O5 | 0.83539 *** | 0.697876 | −0.127826 ** | 0.016339 | |
| OCB-O6 | 0.567749 *** | 0.322339 | 0.051233 | 0.002625 | |
| ISS | ISS1 | 0.812456 *** | 0.660085 | −0.01467 | 0.000215 |
| ISS2 | 0.854762 *** | 0.730618 | 0.025532 | 0.000652 | |
| ISS3 | 0.92774 *** | 0.860702 | −0.028341 | 0.000803 | |
| ISS4 | 0.858241 *** | 0.736578 | 0.02826 | 0.000799 | |
| ISS5 | 0.920345 *** | 0.847035 | −0.015141 | 0.000229 | |
| ISS6 | 0.877293 *** | 0.769643 | 0.003752 | 0.000014 | |
| Average | 0.799848 | 0.674591 | 0.023792 | 0.015995 |
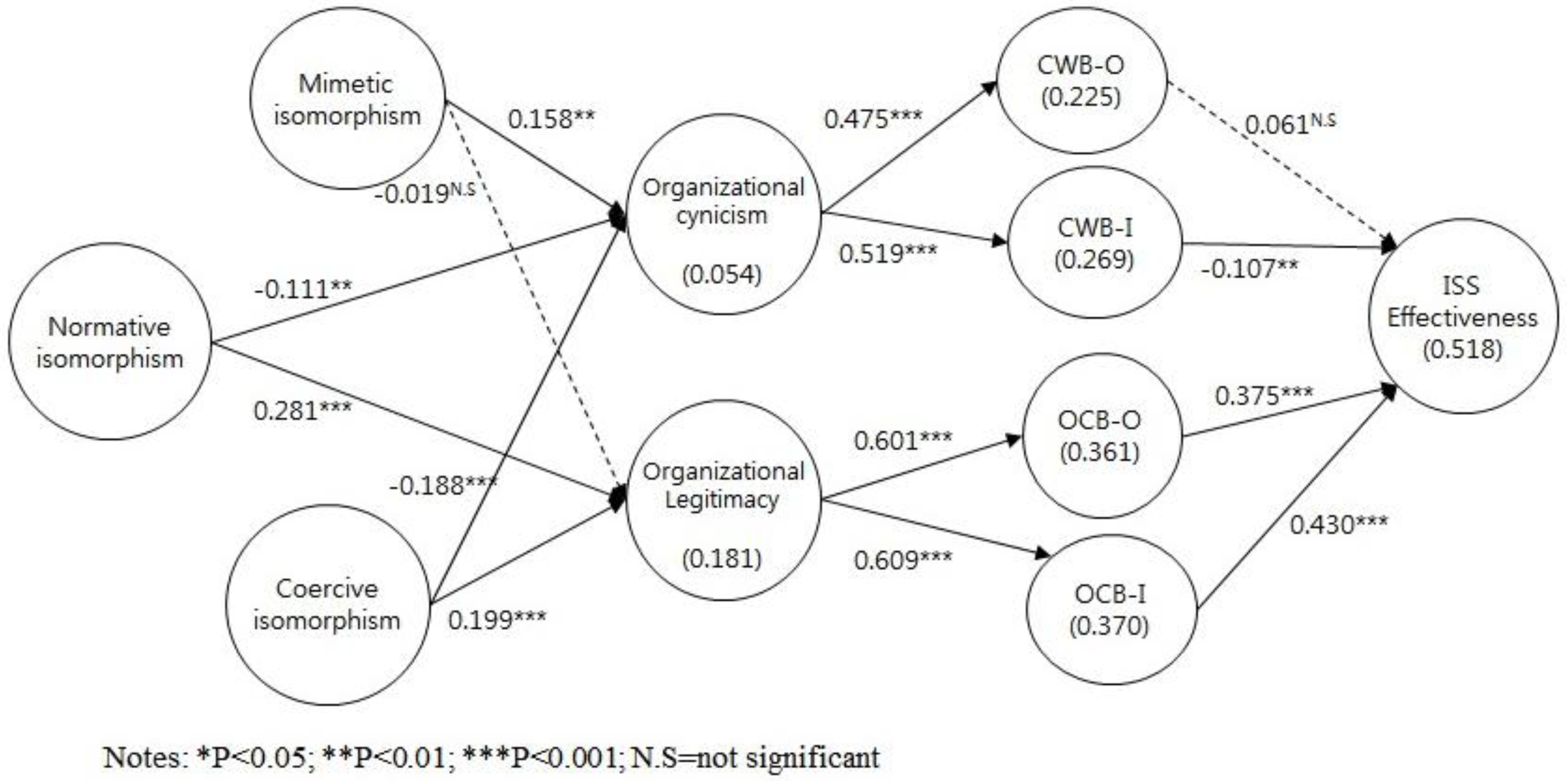
| Hypothesis | Std Regression Weight | Sig Level | Supported |
|---|---|---|---|
| H1. Normative isomorphism is positively associated with ISS legitimacy. | 0.281 | 0.001 | Yes |
| H2. Coercive isomorphism is positively associated with ISS legitimacy. | 0.199 | 0.001 | Yes |
| H3. Mimetic isomorphism is positively associated with ISS legitimacy. | −0.019 | N.S. | No |
| H4. The legitimacy of ISS is positively associated with OCB-I. | 0.609 | 0.001 | Yes |
| H5. The legitimacy of ISS is positively associated with OCB-O. | 0.601 | 0.001 | Yes |
| H6. OCB-I is positively associated with ISS effectiveness. | 0.430 | 0.001 | Yes |
| H7. OCB-O is positively associated with ISS effectiveness. | 0.375 | 0.001 | Yes |
| H8. Normative isomorphism is negatively associated with organizational cynicism toward ISS. | −0.111 | 0.01 | Yes |
| H9. Coercive isomorphism is positively associated with organizational cynicism toward ISS. | −0.188 | 0.001 | Yes |
| H10. Mimetic isomorphism is positively associated with organizational cynicism toward ISS. | 0.158 | 0.01 | Yes |
| H11. Organizational cynicism toward ISS is positively associated with ISS-related CWB-O. | 0.475 | 0.001 | Yes |
| H12. Organizational cynicism toward ISS is positively associated with ISS-related CWB-I. | 0.519 | 0.001 | Yes |
| H13. Employees’ ISS-related CWB-O is negatively associated with ISS effectiveness. | 0.061 | N.S. | No. |
| H14. Employees’ ISS-related CWB-I is negatively associated with ISS effectiveness | −0.107 | 0.01 | Yes |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Choi, M.; Lee, J.; Hwang, K. Information Systems Security (ISS) of E-Government for Sustainability: A Dual Path Model of ISS Influenced by Institutional Isomorphism. Sustainability 2018, 10, 1555. https://doi.org/10.3390/su10051555
Choi M, Lee J, Hwang K. Information Systems Security (ISS) of E-Government for Sustainability: A Dual Path Model of ISS Influenced by Institutional Isomorphism. Sustainability. 2018; 10(5):1555. https://doi.org/10.3390/su10051555
Chicago/Turabian StyleChoi, Myeonggil, Jungwoo Lee, and Kumju Hwang. 2018. "Information Systems Security (ISS) of E-Government for Sustainability: A Dual Path Model of ISS Influenced by Institutional Isomorphism" Sustainability 10, no. 5: 1555. https://doi.org/10.3390/su10051555
APA StyleChoi, M., Lee, J., & Hwang, K. (2018). Information Systems Security (ISS) of E-Government for Sustainability: A Dual Path Model of ISS Influenced by Institutional Isomorphism. Sustainability, 10(5), 1555. https://doi.org/10.3390/su10051555





