Smart Contract Vulnerability Detection Based on Hybrid Attention Mechanism Model
Abstract
1. Introduction
- To our knowledge, we are the first to present the idea of fusing the single-head feature and the multi-head attention feature for smart contract vulnerability detection.
- We propose to extract code fragments with richer data flow and control flow information, which obviously enhance the detection performance of deep learning models.
- We compare our model with other ten state-of-the-art method and the comparison results show that our model performs best in the detection of five types (reentrancy, timestamp dependency, unchecked return value, tx.origin, and arithmetic vulnerability) of smart contract vulnerabilities.
2. Background
2.1. Ethereum and Smart Contract
2.2. Security Vulnerability in Smart Contracts
2.2.1. Reentrancy
2.2.2. Arithmetic Vulnerability
2.2.3. Tx.origin
2.2.4. Timestamp Dependency
2.2.5. Unchecked Return Value
2.3. Source Code Vulnerability Detection
3. Related Work
3.1. Symbol Execution
3.2. Fuzzing Testing
3.3. Formal Verification
3.4. Program Analysis
3.5. Machine Learning
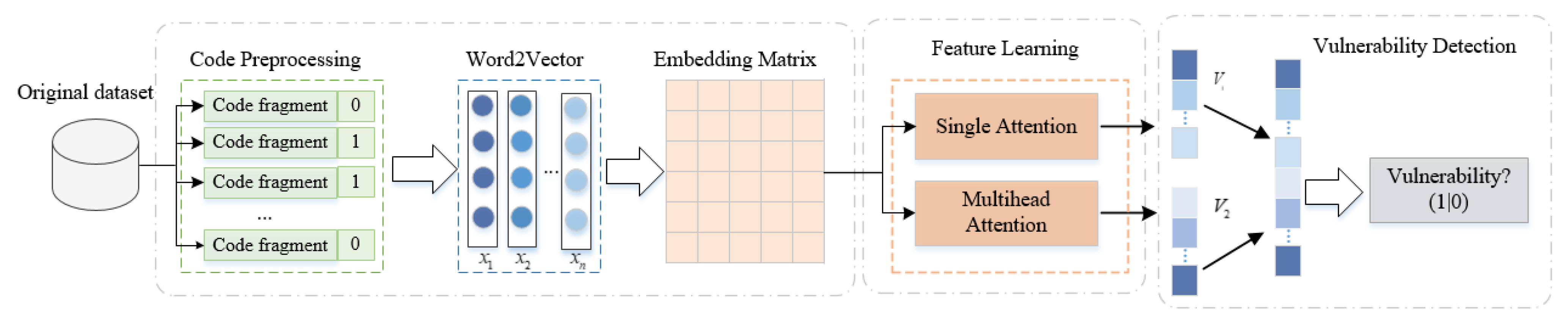
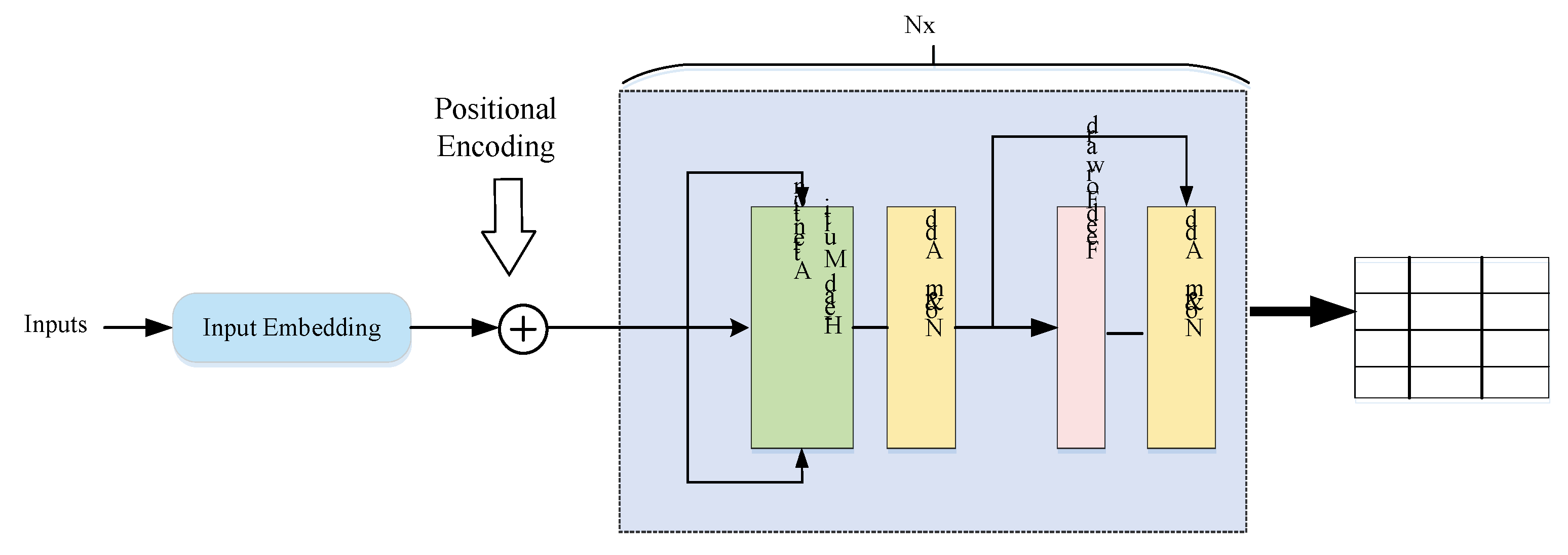
4. Our Approach
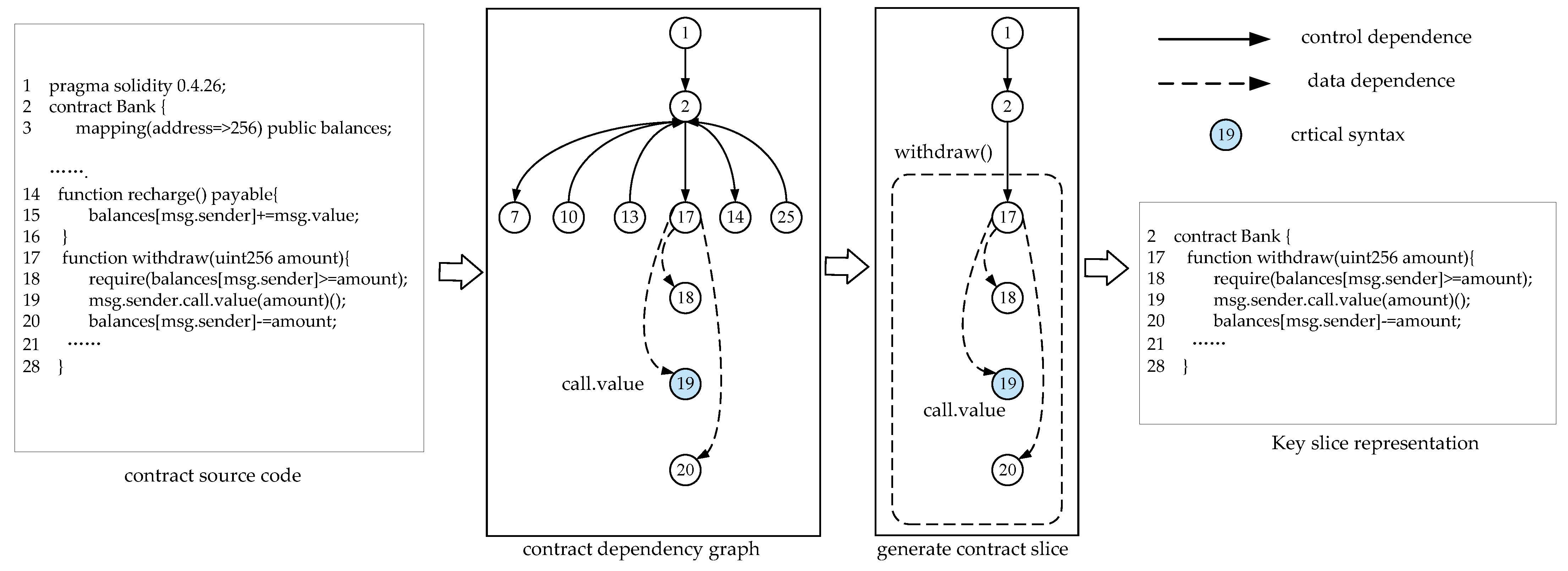
4.1. Code Fragments Extraction
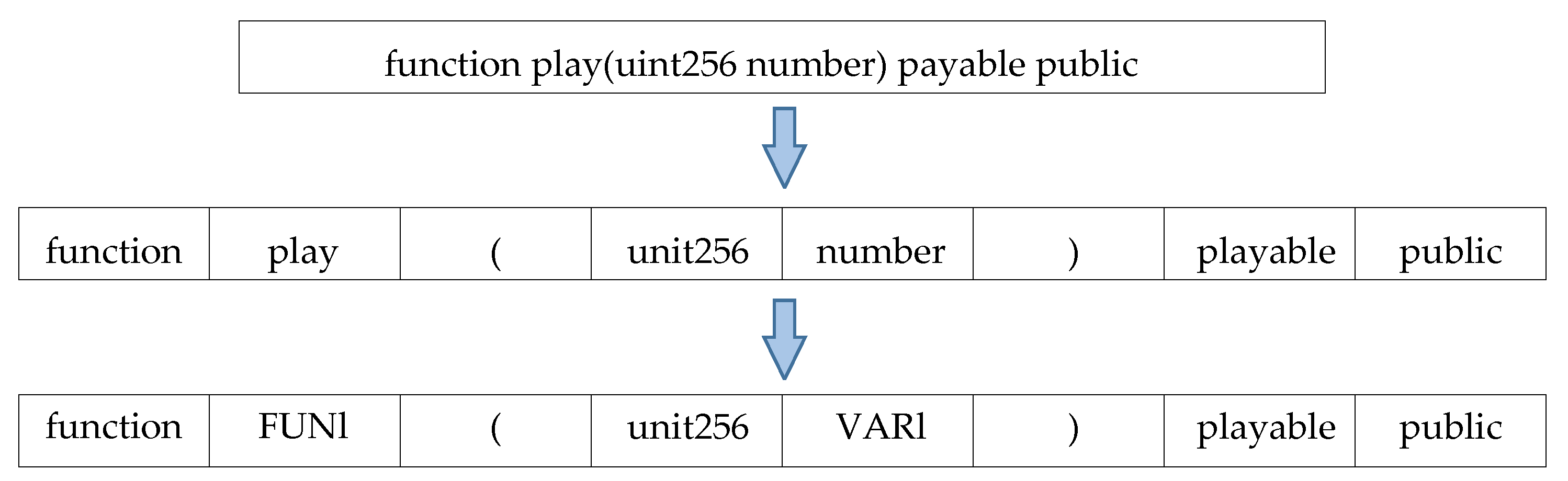
4.2. Word Embedding Layer
4.3. Hybrid Attention Mechanism
4.3.1. Single-Head Attention Encoder
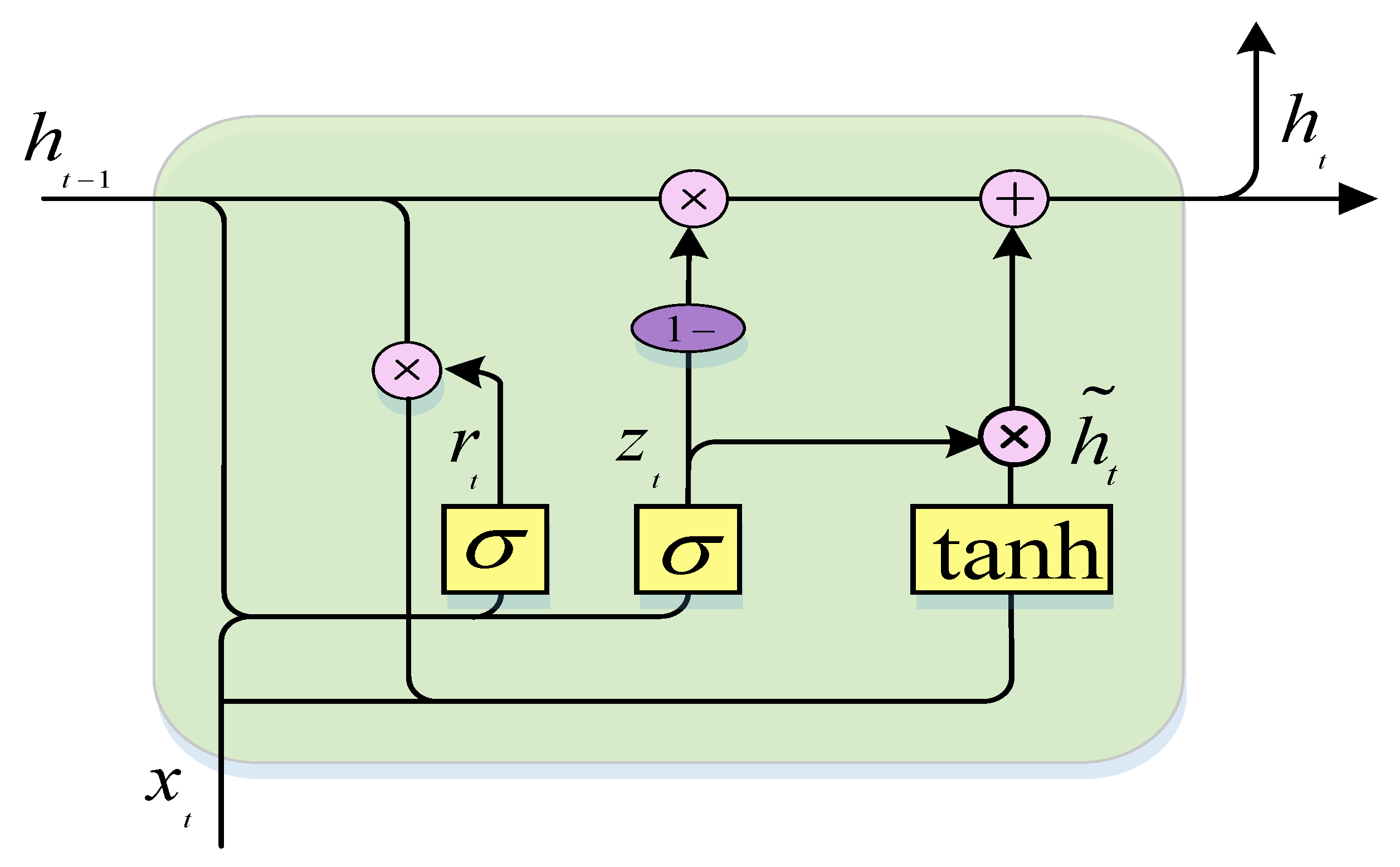
4.3.2. Multi-Head Attention Encoder
4.4. Vulnerability Classification Detection
5. Experiments and Results
5.1. Datasets and Processing
5.2. Implementation Detail
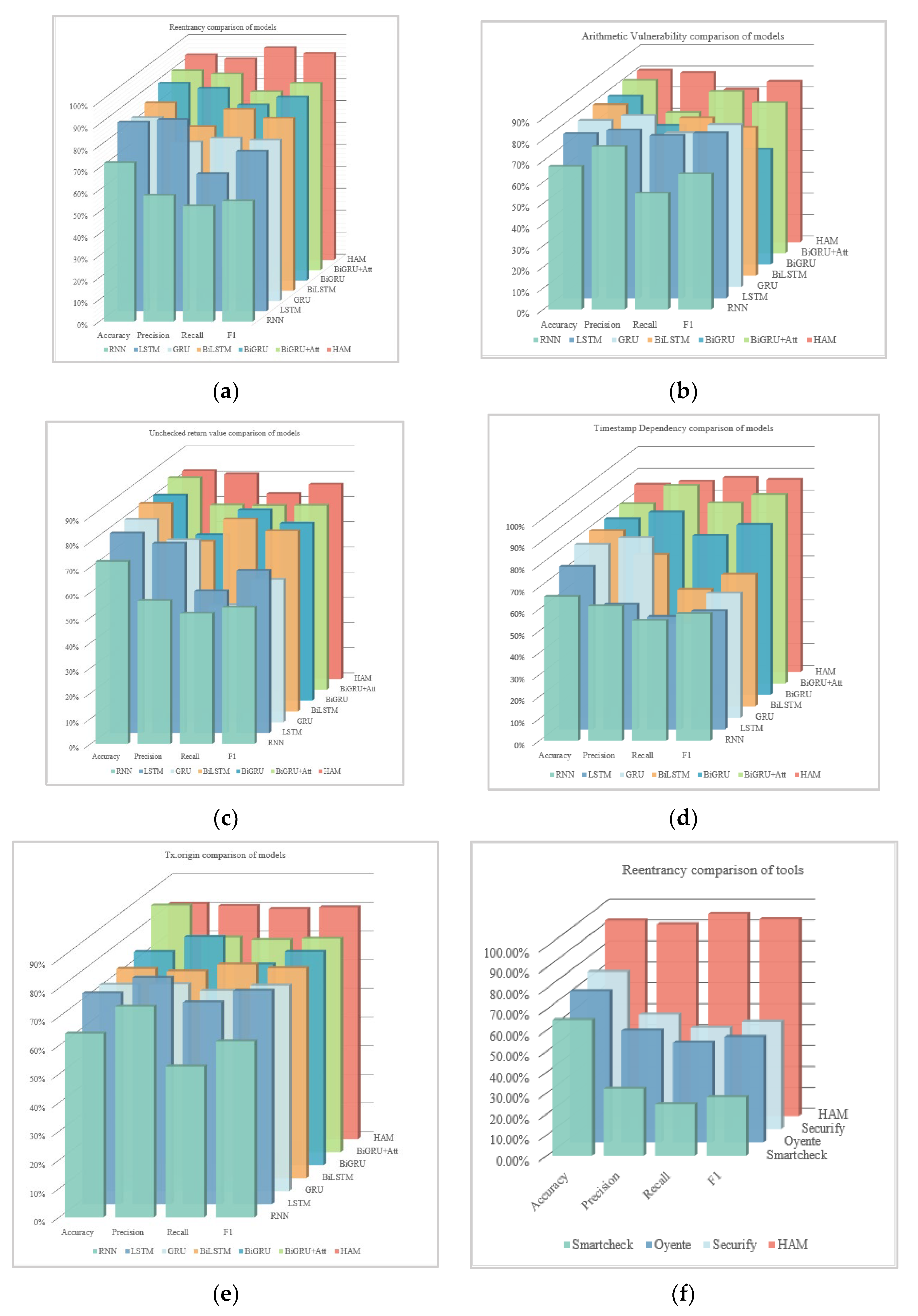
5.3. Experimental Results
6. Discussions and Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 1, 21260. [Google Scholar]
- Hofman, D.L. Legally speaking: Smart contracts, archival bonds, and linked data in the blockchain. In Proceedings of the 2017 26th International Conference on Computer Communication and Networks (ICCCN), Vancouver, BC, Canada, 31 July–3 August 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–4. [Google Scholar]
- Saberi, S.; Kouhizadeh, M.; Sarkis, J.; Shen, L. Blockchain technology and its relationships to sustainable supply chain management. Int. J. Prod. Res. 2019, 57, 2117–2135. [Google Scholar] [CrossRef]
- Chen, S.; Shi, R.; Ren, Z.; Yan, J.; Shi, Y.; Zhang, J. A blockchain-based supply chain quality management framework. In Proceedings of the 2017 IEEE 14th International Conference on e-Business Engineering (ICEBE), Shanghai, China, 4–6 November 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 172–176. [Google Scholar]
- Kang, J.; Yu, R.; Huang, X.; Wu, M.; Maharjan, S.; Xie, S.; Zhang, Y. Blockchain for Secure and Efficient Data Sharing in Vehicular Edge Computing and Networks. IEEE Internet Things J. 2018, 6, 4660–4670. [Google Scholar] [CrossRef]
- Hatim, S.M.; Elias, S.J.; Ali, R.M.; Jasmis, J.; Aziz, A.A.; Mansor, S. Blockchain-based internet of vehicles (biov): An approach towards smart cities development. In Proceedings of the 2020 5th IEEE International Conference on Recent Advances and Innovations in Engineering (ICRAIE), Jaipur, India, 1–3 December 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–4. [Google Scholar]
- Xia, Q.; Sifah, E.B.; Smahi, A.; Amofa, S.; Zhang, X. BBDS: Blockchain-Based Data Sharing for Electronic Medical Records in Cloud Environments. Information 2017, 8, 44. [Google Scholar] [CrossRef]
- Azaria, A.; Ekblaw, A.; Vieira, T.; Lippman, A. Medrec: Using blockchain for medical data access and permission management. In Proceedings of the 2016 2nd International Conference on Open and Big Data (OBD), Vienna, Austria, 22–24 August 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 25–30. [Google Scholar]
- Zhang, P.; Schmidt, D.C.; White, J.; Lenz, G. Blockchain technology use cases in healthcare. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 2018; Volume 111, pp. 1–41. [Google Scholar]
- Agbo, C.C.; Mahmoud, Q.H.; Eklund, J.M. Blockchain technology in healthcare: A systematic review. Healthcare 2019, 7, 56. [Google Scholar] [CrossRef]
- Christidis, K.; Devetsikiotis, M. Blockchains and Smart Contracts for the Internet of Things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Bahga, A.; Madisetti, V.K. Blockchain platform for industrial internet of things. J. Softw. Eng. Appl. 2016, 9, 533–546. [Google Scholar] [CrossRef]
- Kshetri, N. Can Blockchain Strengthen the Internet of Things? IT Prof. 2017, 19, 68–72. [Google Scholar] [CrossRef]
- Szabo, N. Formalizing and Securing Relationships on Public Networks. First Monday 1997, 2. [Google Scholar] [CrossRef]
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Etherscan. Total Ether Supply. Available online: https://cn.etherscan.com/stat/supply (accessed on 20 November 2022).
- Zhao, X.; Chen, Z.; Chen, X.; Wang, Y.; Tang, C. The DAO attack paradoxes in propositional logic. In Proceedings of the 2017 4th International Conference on Systems and Informatics (ICSAI), Hangzhou, China, 11–13 November 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1743–1746. [Google Scholar]
- Praitheeshan, P.; Pan, L.; Doss, R. Security evaluation of smart contract-based on-chain ethereum wallets. In Proceedings of the International Conference on Network and System Security, Melbourne, Australia, 25–27 November 2020; Springer: Cham, Switzerland, 2020; pp. 22–41. [Google Scholar]
- Mohan, V. Automated market makers and decentralized exchanges: A DeFi primer. Financ. Innov. 2022, 8, 20. [Google Scholar] [CrossRef]
- Luu, L.; Chu, D.H.; Olickel, H.; Saxena, P.; Hobor, A. Making smart contracts smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 254–269. [Google Scholar]
- Nikolić, I.; Kolluri, A.; Sergey, I.; Saxena, P.; Hobor, A. Finding the greedy, prodigal, and suicidal contracts at scale. In Proceedings of the 34th Annual Computer Security Applications Conference, San Juan, PR, USA, 3–7 December 2018; pp. 653–663. [Google Scholar]
- Torres, C.F.; Schütte, J.; State, R. Osiris: Hunting for integer bugs in ethereum smart contracts. In Proceedings of the 34th Annual Computer Security Applications Conference, San Juan, PR, USA, 3–7 December 2018; pp. 664–676. [Google Scholar]
- Jiang, B.; Liu, Y.; Chan, W.K. Contractfuzzer: Fuzzing smart contracts for vulnerability detection. In Proceedings of the 2018 33rd IEEE/ACM International Conference on Automated Software Engineering (ASE), Montpellier, France, 3–7 September 2018; pp. 259–269. [Google Scholar]
- Gao, J.; Liu, H.; Liu, C.; Li, Q.; Guan, Z.; Chen, Z. Easyflow: Keep ethereum away from overflow. In Proceedings of the 2019 IEEE/ACM 41st International Conference on Software Engineering: Companion Proceedings (ICSE-Companion), Montréal, QC, Canada, 25–31 May 2019; pp. 23–26. [Google Scholar]
- Tann, W.J.W.; Han, X.J.; Gupta, S.S.; Ong, Y.S. Towards safer smart contracts: A sequence learning approach to detecting security threats. arXiv 2018, arXiv:1811.06632. [Google Scholar]
- Qian, P.; Liu, Z.; He, Q.; Zimmermann, R.; Wang, X. Towards Automated Reentrancy Detection for Smart Contracts Based on Sequential Models. IEEE Access 2020, 8, 19685–19695. [Google Scholar] [CrossRef]
- Zhuang, Y.; Liu, Z.; Qian, P.; Liu, Q.; Wang, X.; He, Q. Smart Contract Vulnerability Detection using Graph Neural Network. In Proceedings of the International Joint Conferences on Artificial Intelligence Organization (IJCAI), Online, 7–15 January 2020; pp. 3283–3290. [Google Scholar]
- Conti, M.; Kumar, E.S.; Lal, C.; Ruj, S. A Survey on Security and Privacy Issues of Bitcoin. IEEE Commun. Surv. Tutor. 2018, 20, 3416–3452. [Google Scholar] [CrossRef]
- Buterin, V. A next-generation smart contract and decentralized application platform. White Pap. 2014, 3, 1–2. [Google Scholar]
- Xu, B.; Luthra, D.; Cole, Z.; Blakely, N. EOS: An Architectural, Performance, and Economic Analysis. Retrieved June 2018, 11, 2019. Available online: https://blog.bitmex.com/wp-content/uploads/2018/11/eos-test-report.pdf (accessed on 22 November 2022).
- Elrom, E. Neo blockchain and smart contracts. In The Blockchain Developer; Apress: Berkeley, CA, USA, 2019; pp. 257–298. [Google Scholar]
- Cachin, C. Architecture of the hyperledger blockchain fabric. In Proceedings of the Workshop on Distributed Cryptocurrencies and Consensus Ledgers, Chicago, IL, USA, 25 July 2016; Volume 310, pp. 1–4. [Google Scholar]
- Dannen, C. Introducing Ethereum and Solidity; Apress: Berkeley, CA, USA, 2017. [Google Scholar]
- Atzei, N.; Bartoletti, M.; Cimoli, T. A survey of attacks on ethereum smart contracts (sok). In Proceedings of the International Conference on Principles of Security and Trust, Uppsala, Sweden, 24–25 April 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 164–186. [Google Scholar]
- Dika, A. Ethereum Smart Contracts: Security Vulnerabilities and Security Tools. Master’s Thesis, NTNU, Trondheim, Norway, 2017. [Google Scholar]
- Dingman, W.; Cohen, A.; Ferrara, N.; Lynch, A.; Jasinski, P.; Black, P.E.; Deng, L. Defects and vulnerabilities in smart contracts, a classification using the NIST bugs framework. Int. J. Netw. Distrib. Comput. 2019, 7, 121–132. [Google Scholar] [CrossRef]
- King, J.C. Symbolic execution and program testing. Commun. ACM 1976, 19, 385–394. [Google Scholar] [CrossRef]
- Tsankov, P.; Dan, A.; Drachsler-Cohen, D.; Gervais, A.; Buenzli, F.; Vechev, M. Securify: Practical security analysis of smart contracts. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 67–82. [Google Scholar]
- Feist, J.; Grieco, G.; Groce, A. Slither: A static analysis framework for smart contracts. In Proceedings of the 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB), Montreal, QC, Canada, 27 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 8–15. [Google Scholar]
- He, J.; Balunović, M.; Ambroladze, N.; Tsankov, P.; Vechev, M. Learning to fuzz from symbolic execution with application to smart contracts. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 531–548. [Google Scholar]
- Nguyen, T.D.; Pham, L.H.; Sun, J.; Lin, Y.; Minh, Q.T. sfuzz: An efficient adaptive fuzzer for solidity smart contracts. In Proceedings of the ACM/IEEE 42nd International Conference on Software Engineering, Seoul, Republic of Korea, 27 June–19 July 2020; pp. 778–788. [Google Scholar]
- Bai, X.; Cheng, Z.; Duan, Z.; Hu, K. Formal modeling and verification of smart contracts. In Proceedings of the 2018 7th International Conference on Software and Computer Applications, Kuantan, Malaysia, 8–10 February 2018; pp. 322–326. [Google Scholar]
- Amani, S.; Bégel, M.; Bortin, M.; Staples, M. Towards verifying ethereum smart contract bytecode in Isabelle/HOL. In Proceedings of the 7th ACM SIGPLAN International Conference on Certified Programs and Proofs, Los Angeles, CA, USA, 8–9 January 2018; pp. 66–77. [Google Scholar]
- Hildenbrandt, E.; Saxena, M.; Rodrigues, N.; Zhu, X.; Daian, P.; Guth, D.; Moore, B.; Park, D.; Zhang, Y.; Stefanescu, A.; et al. Kevm: A complete formal semantics of the ethereum virtual machine. In Proceedings of the 2018 IEEE 31st Computer Security Foundations Symposium (CSF), Oxford, UK, 9–12 July 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 204–217. [Google Scholar]
- Bhargavan, K.; Delignat-Lavaud, A.; Fournet, C.; Gollamudi, A.; Gonthier, G.; Kobeissi, N.; Kulatova, N.; Rastogi, A.; Sibut-Pinote, T.; Swamy, N.; et al. Formal verification of smart contracts: Short paper. In Proceedings of the 2016 ACM Workshop on Programming Languages and Analysis for Security, Vienna, Austria, 24 October 2016; pp. 91–96. [Google Scholar]
- Permenev, A.; Dimitrov, D.; Tsankov, P.; Drachsler-Cohen, D.; Vechev, M. Verx: Safety verification of smart contracts. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 18–21 May 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1661–1677. [Google Scholar]
- Tikhomirov, S.; Voskresenskaya, E.; Ivanitskiy, I.; Takhaviev, R.; Marchenko, E.; Alexandrov, Y. Smartcheck: Static analysis of ethereum smart contracts. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothenburg, Sweden, 27 May–3 June 2018; pp. 9–16. [Google Scholar]
- Yu, X.; Zhao, H.; Hou, B.; Ying, Z.; Wu, B. DeeSCVHunter: A Deep Learning-Based Framework for Smart Contract Vulnerability Detection. In Proceedings of the 2021 International Joint Conference on Neural Networks (IJCNN), Shenzhen, China, 18–22 July 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 1–8. [Google Scholar]
- Huang, T.T.H.D. Hunting the ethereum smart contract: Color-inspired inspection of potential attacks. arXiv 2018, arXiv:1807.01868. [Google Scholar]
- Gupta, R.; Patel, M.M.; Shukla, A.; Tanwar, S. Deep learning-based malicious smart contract detection scheme for internet of things environment. Comput. Electr. Eng. 2022, 97, 107583. [Google Scholar] [CrossRef]
- Li, Z.; Zou, D.; Xu, S.; Jin, H.; Zhu, Y.; Chen, Z. SySeVR: A Framework for Using Deep Learning to Detect Software Vulnerabilities. IEEE Trans. Dependable Secur. Comput. 2021, 19, 2244–2258. [Google Scholar] [CrossRef]
- Mikolov, T.; Chen, K.; Corrado, G.; Dean, J. Efficient estimation of word representations in vector space. arXiv 2013, arXiv:1301.3781. [Google Scholar]
- Niu, Y.; Xie, R.; Liu, Z.; Sun, M. Improved word representation learning with sememes. In Proceedings of the 55th Annual Meeting of the Association for Computational Linguistics, Vancouver, BC, Canada, 30 July–4 August 2017; pp. 2049–2058. [Google Scholar]
- Mikolov, T.; Karafiát, M.; Burget, L.; Cernocký, J.; Khudanpur, S. Recurrent neural network based language model. In Proceedings of the Interspeech, Chiba, Japan, 26–30 September 2010; Volume 2, pp. 1045–1048. [Google Scholar]
- Hochreiter, S.; Schmidhuber, J. Long short-term memory. Neural Comput. 1997, 9, 1735–1780. [Google Scholar] [CrossRef] [PubMed]
- Chung, J.; Gulcehre, C.; Cho, K.H.; Bengio, Y. Empirical evaluation of gated recurrent neural networks on sequence modeling. arXiv 2014, arXiv:1412.3555. [Google Scholar]
- Vaswani, A.; Shazeer, N.; Parmar, N.; Uszkoreit, J.; Jones, L.; Gomez, A.N.; Kaiser, Ł.; Polosukhin, I. Attention is all you need. In Advances in Neural Information Processing Systems; Morgan Kaufmann: San Francisco, CA, USA, 2017; Volume 30. [Google Scholar]
- Durieux, T.; Ferreira, J.F.; Abreu, R.; Cruz, P. Empirical review of automated analysis tools on 47,587 Ethereum smart contracts. In Proceedings of the ACM/IEEE 42nd International Conference on Software Engineering, Seoul, Republic of Korea, 27 June–19 July 2020; pp. 530–541. [Google Scholar]
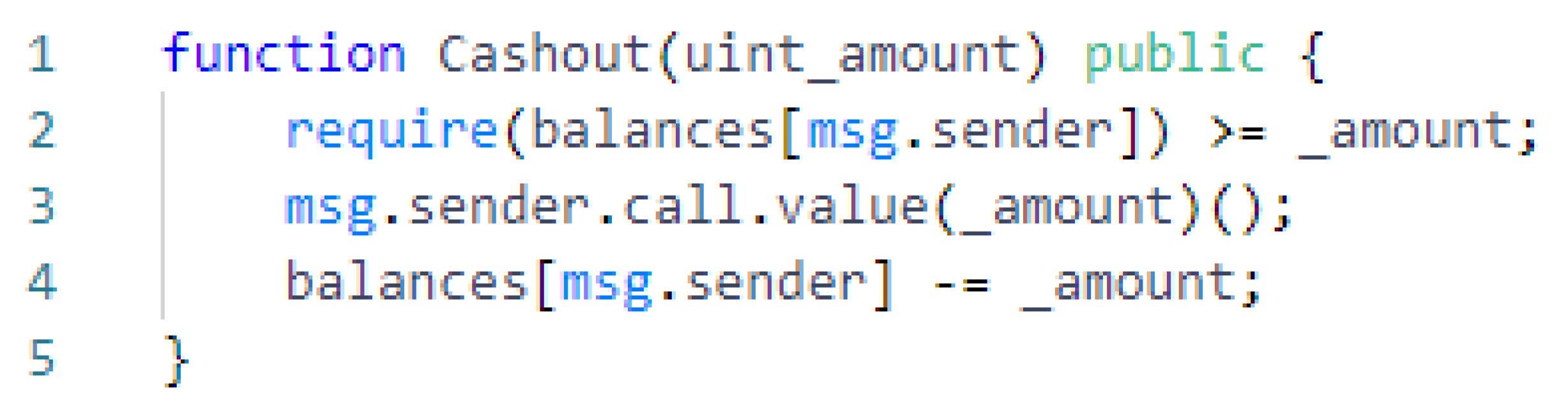
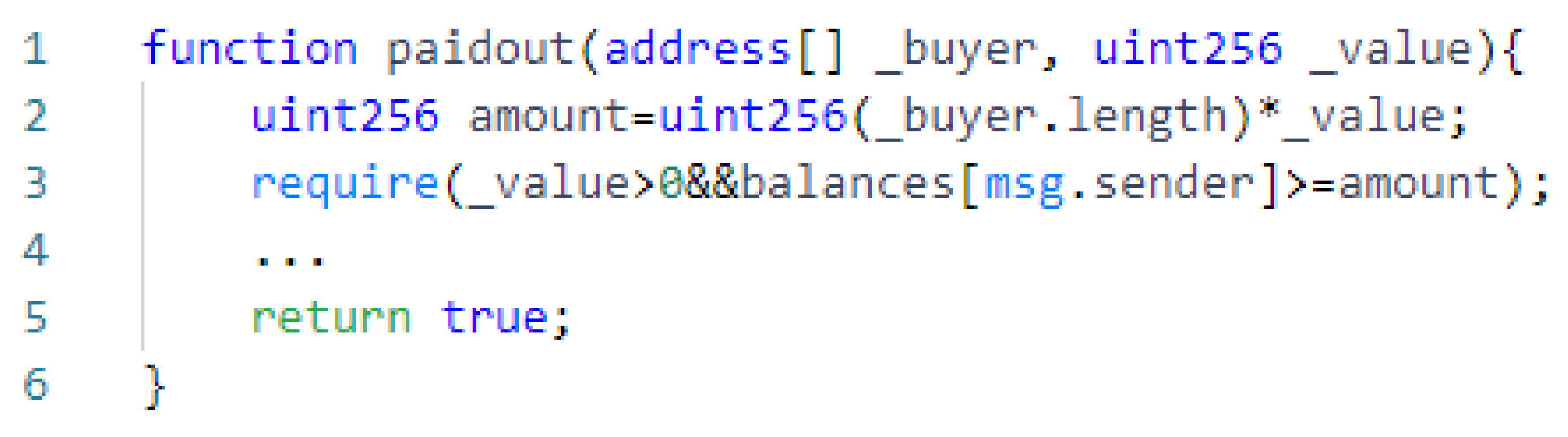
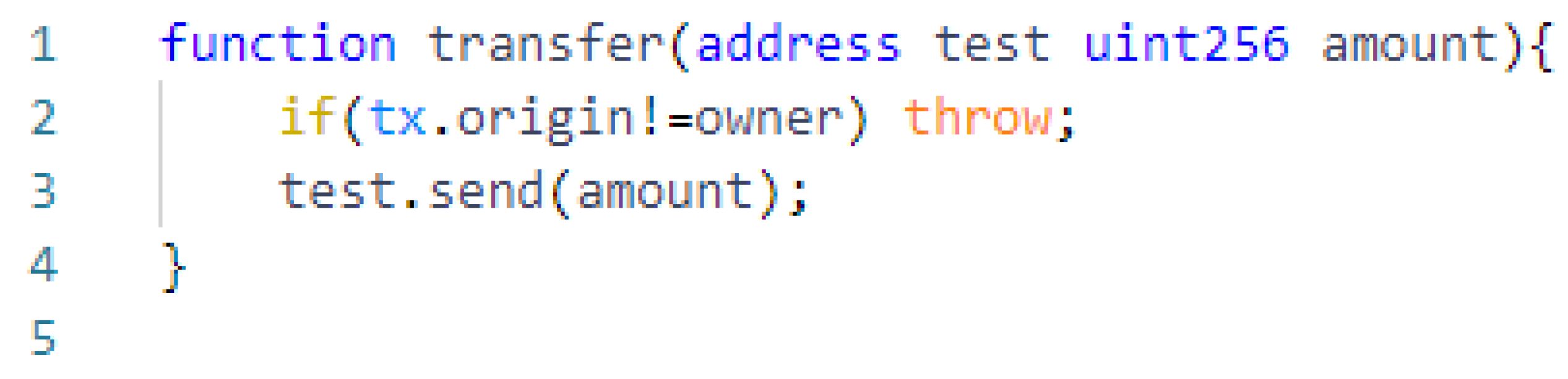

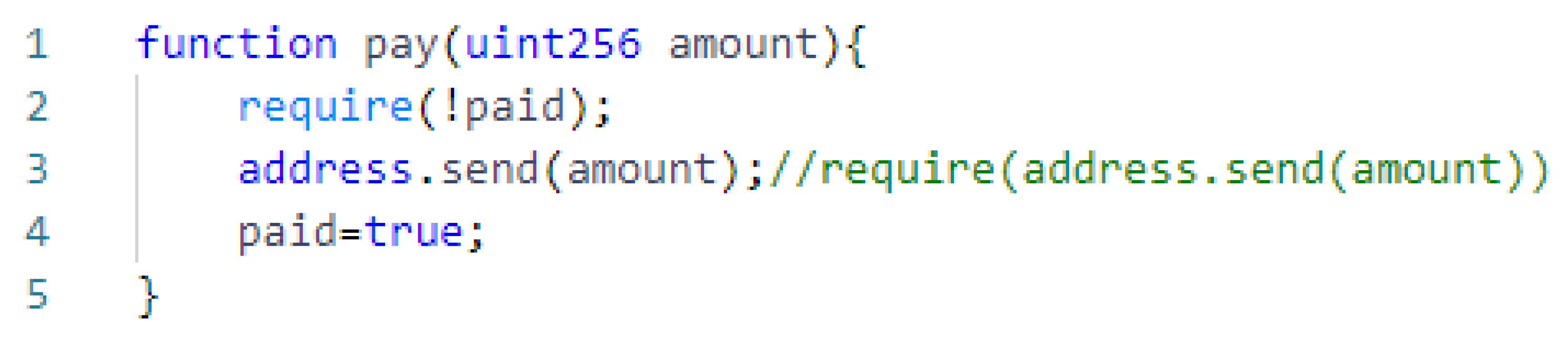

| Vulnerability | Vulnerable Features |
|---|---|
| Reentrancy | call.value(), fallback() |
| Tx.origin | tx.origin variable |
| Timestamp dependence | block.number, now, or block.timestamp |
| Unchecked Return Value | send(), call() |
| Arithmetic vulnerability | integer variables |
| Category | Training Set | Testing Set | Total Samples |
|---|---|---|---|
| Vulnerable sample | 6281 | 1570 | 7851 |
| Non-vulnerable sample | 13,685 | 3221 | 17,106 |
| Arithmetic vulnerability | 1086 | 272 | 1358 |
| Reentrancy | 1152 | 288 | 1440 |
| Timestamp dependency | 1542 | 385 | 1927 |
| Unchecked Return Value | 1696 | 423 | 2119 |
| Tx.origin | 806 | 201 | 1007 |
| Predicted | 1 | 0 | |
|---|---|---|---|
| Actual | |||
| 1 | True Positive(TP) | False Negative(FN) | |
| 0 | False Positive(FP) | True Negative(TN) | |
| Model | Number(P|N) | Accuracy | Precision | Recall | F1 |
|---|---|---|---|---|---|
| HAM (Unsliced) | 2000(1183|817) | 84.57% | 86.38% | 84.56% | 85.46% |
| HAM (code fragment) | 2000(1064|936) | 88.96% | 89.58% | 91.64% | 90.51% |
| Vulnerability | Performance Metrics | Models | ||||||
|---|---|---|---|---|---|---|---|---|
| RNN | LSTM | GRU | BiLSTM | BiGRU | BiGRU + Att | HAM | ||
| Reentrancy | Accuracy | 72.28% | 86.02% | 83.48% | 85.57% | 89.78% | 90.94% | 93.36% |
| Precision | 57.40% | 87.18% | 72.35% | 74.73% | 87.48% | 89.40% | 91.58% | |
| Recall | 52.54% | 62.56% | 74.19% | 82.59% | 79.89% | 81.23% | 96.64% | |
| F1 | 54.86% | 72.84% | 73.23% | 78.46% | 83.51% | 85.12% | 94.04% | |
| Arithmetic Vulnerability | Accuracy | 67.19% | 77.36% | 78.26% | 80.39% | 79.16% | 81.36% | 80.85% |
| Precision | 76.57% | 78.99% | 80.61% | 65.80% | 65.38% | 66.20% | 79.65% | |
| Recall | 54.56% | 76.49% | 72.47% | 74.23% | 46.23% | 76.11% | 71.89% | |
| F1 | 63.72% | 77.72% | 76.32% | 69.76% | 54.16% | 70.81% | 75.57% | |
| Unchecked Return Value | Accuracy | 72.18% | 79.12% | 80.28% | 82.34% | 81.39% | 84.05% | 82.56% |
| Precision | 56.64% | 75.10% | 72.18% | 67.31% | 65.68% | 73.18% | 81.24% | |
| Recall | 51.58% | 56.21% | 46.35% | 76.20% | 75.54% | 73.02% | 73.46% | |
| F1 | 53.99% | 64.30% | 56.45% | 71.48% | 70.27% | 73.10% | 77.15% | |
| Timestamp Dependency | Accuracy | 65.76% | 74.24% | 79.02% | 80.12% | 80.29% | 81.98% | 85.62% |
| Precision | 61.46% | 56.85% | 82.11% | 69.21% | 83.37% | 90.26% | 87.03% | |
| Recall | 54.78% | 51.33% | 42.89% | 53.26% | 72.67% | 82.29% | 88.69% | |
| F1 | 57.97% | 53.95% | 56.81% | 60.20% | 77.65% | 86.09% | 87.85% | |
| Tx.origin | Accuracy | 64.06% | 73.57% | 72.11% | 73.11% | 74.43% | 86.11% | 82.19% |
| Precision | 73.57% | 79.08% | 72.26% | 72.19% | 79.67% | 74.98% | 81.45% | |
| Recall | 52.66% | 70.41% | 69.94% | 74.57% | 70.03% | 74.13% | 80.32% | |
| F1 | 61.38% | 74.50% | 71.8% | 73.36% | 74.54% | 74.55% | 80.88% | |
| Vulnerability | Performance Metrics | Method | |||
|---|---|---|---|---|---|
| Smartcheck | Oyente | Securify | HAM | ||
| Reentrancy | Accuracy | 64.89% | 72.39% | 75.23% | 93.36% |
| Precision | 32.16% | 53.47% | 54.79% | 91.58% | |
| Recall | 24.79% | 47.78% | 48.54% | 96.64% | |
| F1 | 28.00% | 50.47% | 51.48% | 94.04% | |
| Arithmetic Vulnerability | Accuracy | 42.19% | 67.36% | N/A | 80.85% |
| Precision | 38.24% | 37.13% | N/A | 79.65% | |
| Recall | 36.50% | 27.39% | N/A | 71.89% | |
| F1 | 37.35% | 31.52% | N/A | 75.57% | |
| Unchecked Return Value | Accuracy | 38.66% | N/A | 37.36% | 82.56% |
| Precision | 32.50% | N/A | 34.13% | 81.24% | |
| Recall | 87.54% | N/A | 92.48% | 73.46% | |
| F1 | 47.40% | N/A | 47.16% | 77.15% | |
| Timestamp Dependency | Accuracy | 58.34% | 60.32% | N/A | 85.62% |
| Precision | 48.12% | 46.68% | N/A | 87.03% | |
| Recall | 27.36% | 30.48% | N/A | 88.69% | |
| F1 | 34.89% | 36.88% | N/A | 87.85% | |
| Tx.origin | Accuracy | 70.86% | N/A | 35.57% | 82.19% |
| Precision | 49.85% | N/A | 31.28% | 81.45% | |
| Recall | 54.86% | N/A | 86.19% | 80.32% | |
| F1 | 52.24% | N/A | 45.90% | 80.88% | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, H.; Dong, H.; He, Y.; Duan, Q. Smart Contract Vulnerability Detection Based on Hybrid Attention Mechanism Model. Appl. Sci. 2023, 13, 770. https://doi.org/10.3390/app13020770
Wu H, Dong H, He Y, Duan Q. Smart Contract Vulnerability Detection Based on Hybrid Attention Mechanism Model. Applied Sciences. 2023; 13(2):770. https://doi.org/10.3390/app13020770
Chicago/Turabian StyleWu, Huaiguang, Hanjie Dong, Yaqiong He, and Qianheng Duan. 2023. "Smart Contract Vulnerability Detection Based on Hybrid Attention Mechanism Model" Applied Sciences 13, no. 2: 770. https://doi.org/10.3390/app13020770
APA StyleWu, H., Dong, H., He, Y., & Duan, Q. (2023). Smart Contract Vulnerability Detection Based on Hybrid Attention Mechanism Model. Applied Sciences, 13(2), 770. https://doi.org/10.3390/app13020770






