An Access Control Model for Preventing Virtual Machine Escape Attack
Abstract
:1. Introduction
2. Related Work
3. VM Escape Attack
3.1. VM Escape Attack Analysis
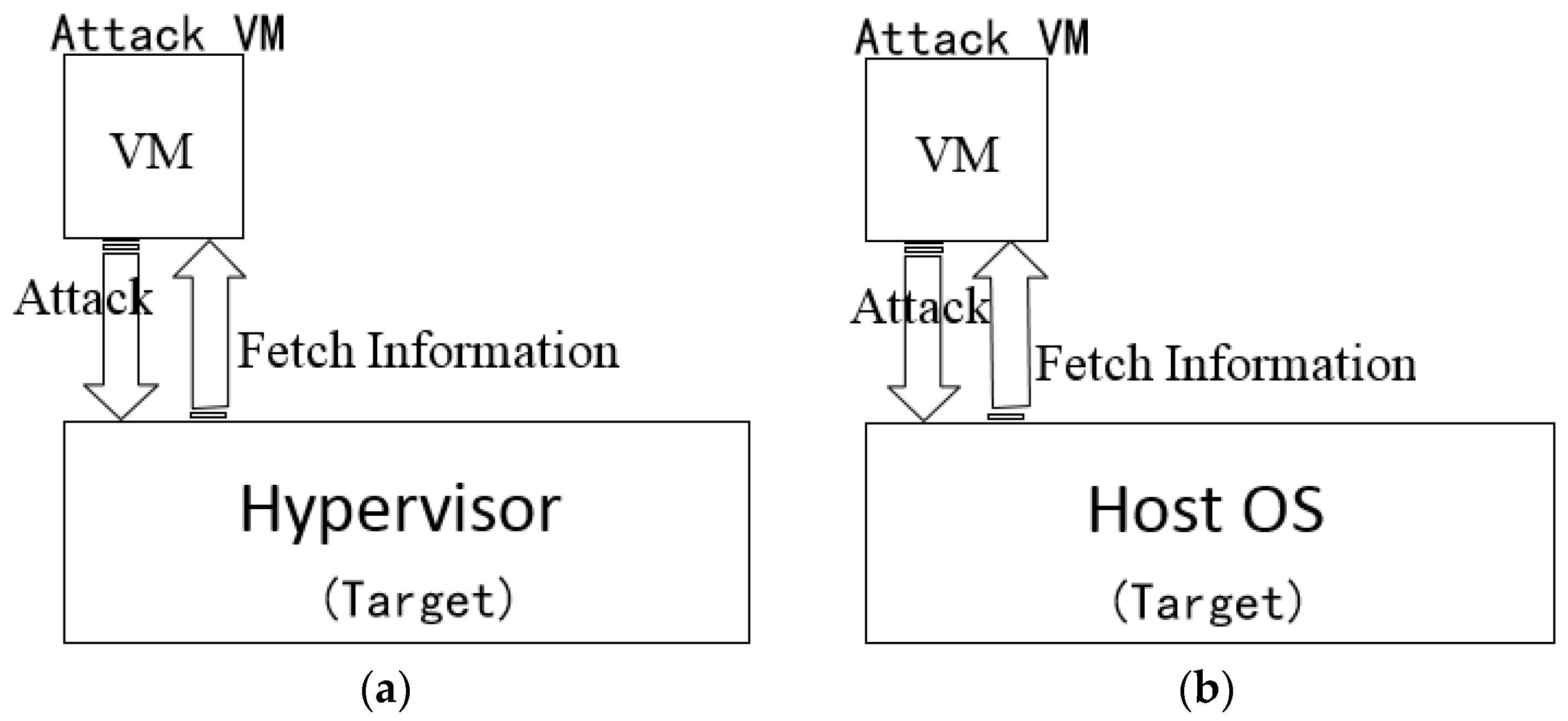
3.2. VM Escape Attack Model
- Placement. Placement refers to the activity that malicious attackers place their malicious virtual machines on the same physical machine where the target Hypervisor or hosts run. This process is a probability event and relatively complex, which needs to use a lot of co-residency detection methods.
- Extracting information. Once the placement is successful, the attacker can launch attacks to get key permissions of the Hypervisor or hosts, and then extract information from the other virtual machines on the host and Hypervisor.
- The attacker cannot determine whether the malicious virtual machine is co-resident with the Hypervisor or host that they want to attack;
- Are there security vulnerabilities that the attacker has previously known regarding the hosts?;
- Can the attacker know how to obtain critical information through the escape attack once they are deployed successfully?
4. Access Control Model for Preventing VM Escape Attack
4.1. Access Control
4.2. BLP Model
4.3. PVME Model
4.3.1. Model Elements
- Subject: the subject represents the active side that issues access operations and access requests. It usually refers the users or processes that can make the information flow. The capital S represents the subject set and the lowercase s represents a single subject, namely .
- Object: the object represents the side that can be accessed, generally documents, procedures or equipment that can be called. The capital O represents the subject set and the lowercase o represents a single subject, namely .
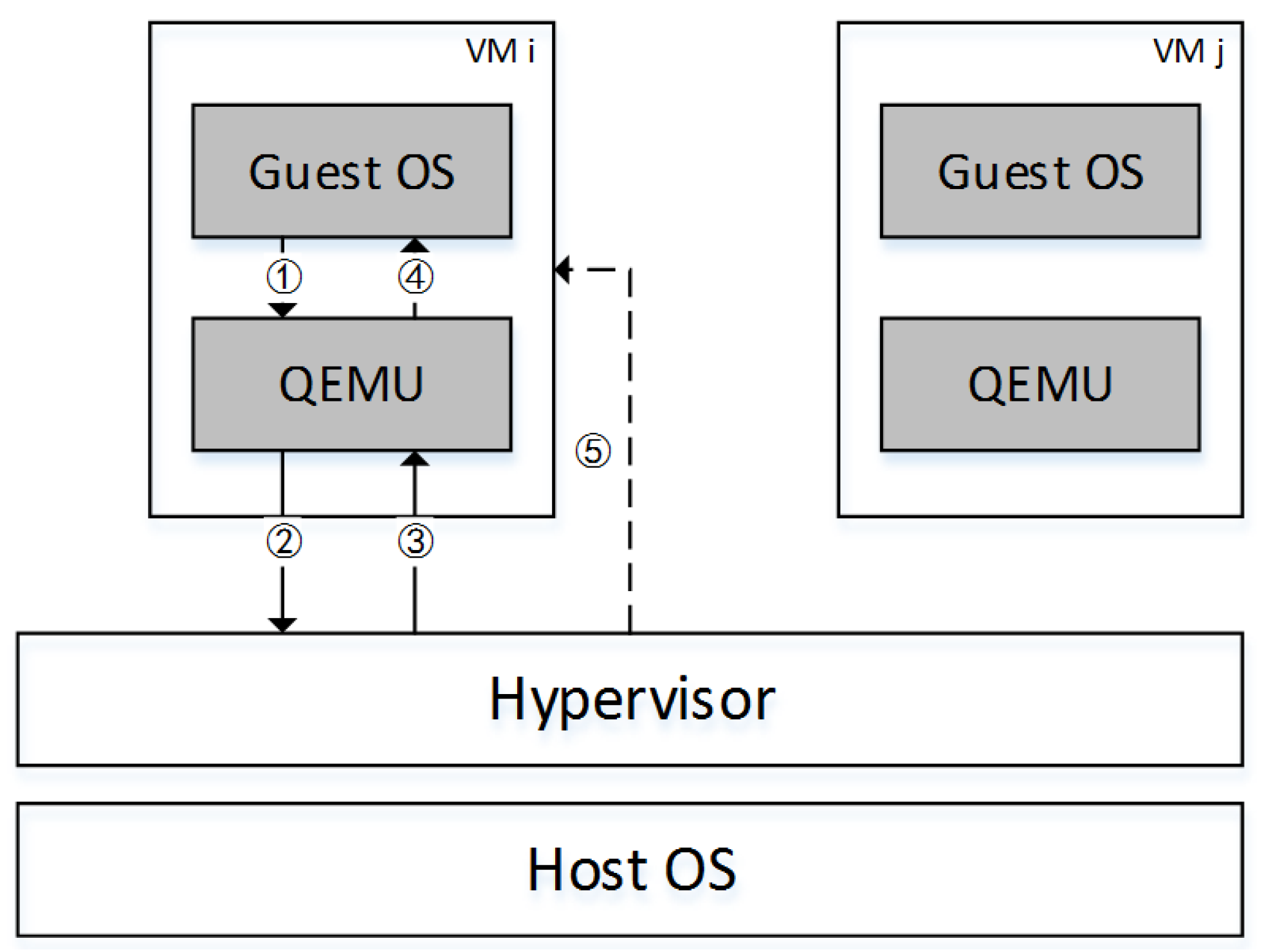
- Access Attribute Set: access set . In our research environment, the communicating parties involved Hypervisor, VM, QEMU and Guest OS. However the subject can only be Hypervisor or QEMU and the object can be Hypervisor, Guest OS, VM or QEMU. When a virtual machine communicates with the Hypervisor, in addition to traditional access modes (read-only (r), write-only (a), write-read (w)), we redefine the implementation of access mode (), and add a new access mode (). Since the execution () access in the BLP model is completely redefined in the PVME model, we use to make that distinction. The execution () and control () modes are the only two operations that exist when theHypervisor communicates with virtual machines. Therefore, the access attribute set .
- Access Control Matrix: the element of access control matrix M represents the subject owns the access to the object in current state.
- Security Level: the security level contains security classification and security category. denotes the security classification set where and represents the security category set whose element is a specific access property. Security level set is a partial ordered set, each item in the set represents a security level, which , , . If and only if then we get . Each element in security level vector set is where is the security level function of the object, is the security level function of the object and is the current security level function of the subject.
- Object Hierarchy: object level set H indicates the subordinate relationship between subject and object. In the object hierarchy, a node mostly has one and only one parent without a hierarchy ring. The symbol represents is the leaf node and is the parent node in the hierarchy.
- System Status: system Status collection is a four-tuple , every single element quadruple represents a system status, in which , , , are the current accessing set, access control matrix, security level vector set and the hierarchy of the objects, respectively. The symbol , and its element is the current access set, which records what subject can access what objects in which access property.
- Request Element Set: request element set , where the denotes get or give the requests and the denotes release or rescind the requests. The request set , whose function is as shown Table 1.
4.3.2. Security Axioms
4.3.3. State Transition Rules
- In the PVME model when the Hypervisor managers the virtual machines, in this pair the subject can only be theHypervisor. Besides, the PVME model does notconsider the communications between VMs. As a result, the PVME model removes the rules corresponding to the rule 6 and 7 in BLP model.
- The PVME model redefines the execution (e*) access property and adds a new rule (releasing execution (e*) access property).
- The Hypervisor has the control (c*) access property when it manages VMs. Thus, we add two rules (acquiring and releasing control (c*) access property).
- In the PVME model, the virtual machines have the same security level, no matter whether they are subjects or objects. Thus, we remove rule 10 of the BLP model and only keep the rule that changes objects’ security level.
- If the subject is Hypervisor and the object is QEMU or the subject is QEMU and the object is Guest OS, we denote the subject as (if the subject is Hypervisor, i = 1; if the subject is QEMU (assuming that there are n VMs), ) and designate the object as , at this time the subject only has three accesses (read-only (r), write-only (a), write-read (w)) to the object , which is mapped to twostate transition rules.
- If the subject is theHypervisor and the objects are VMs, we denote the subject as and denote the object as . As theHypervisor has absolute control over VMs, the subject can get access to subject in five ways (read-only (r), write-only (a), write-read (w), execute (e*) and control (c*)).In this case, on one hand the paper integrates the three access methods (the Hypervisor gets three types of access to the VMs, i.e., read-only (r), write-only (a), write-read (w)) into the first case, on the other the transition rules for the Hypervisor to get execute (e*) and control (c*) access to the VMs will be individually designed, which can totally map into four state transition rules. Rules 7–8 are used for subject Hypervisor to create and delete object VMs, and rule 9 can be used to change the security level of the object VMs.
4.4. PVME Model Design
4.4.1. Access Matrix
4.4.2. Security Level
4.4.3. Current Access Matrix
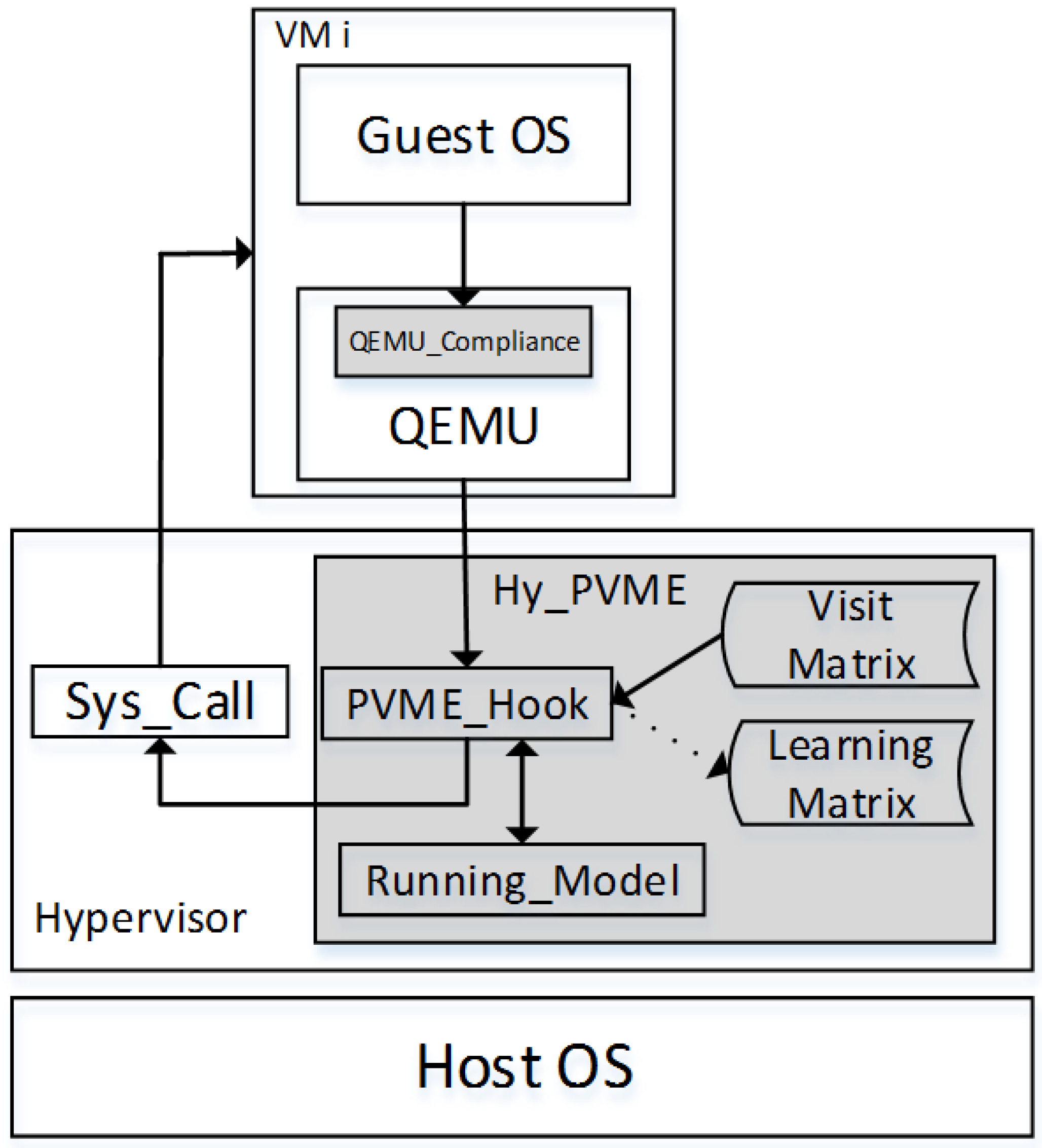
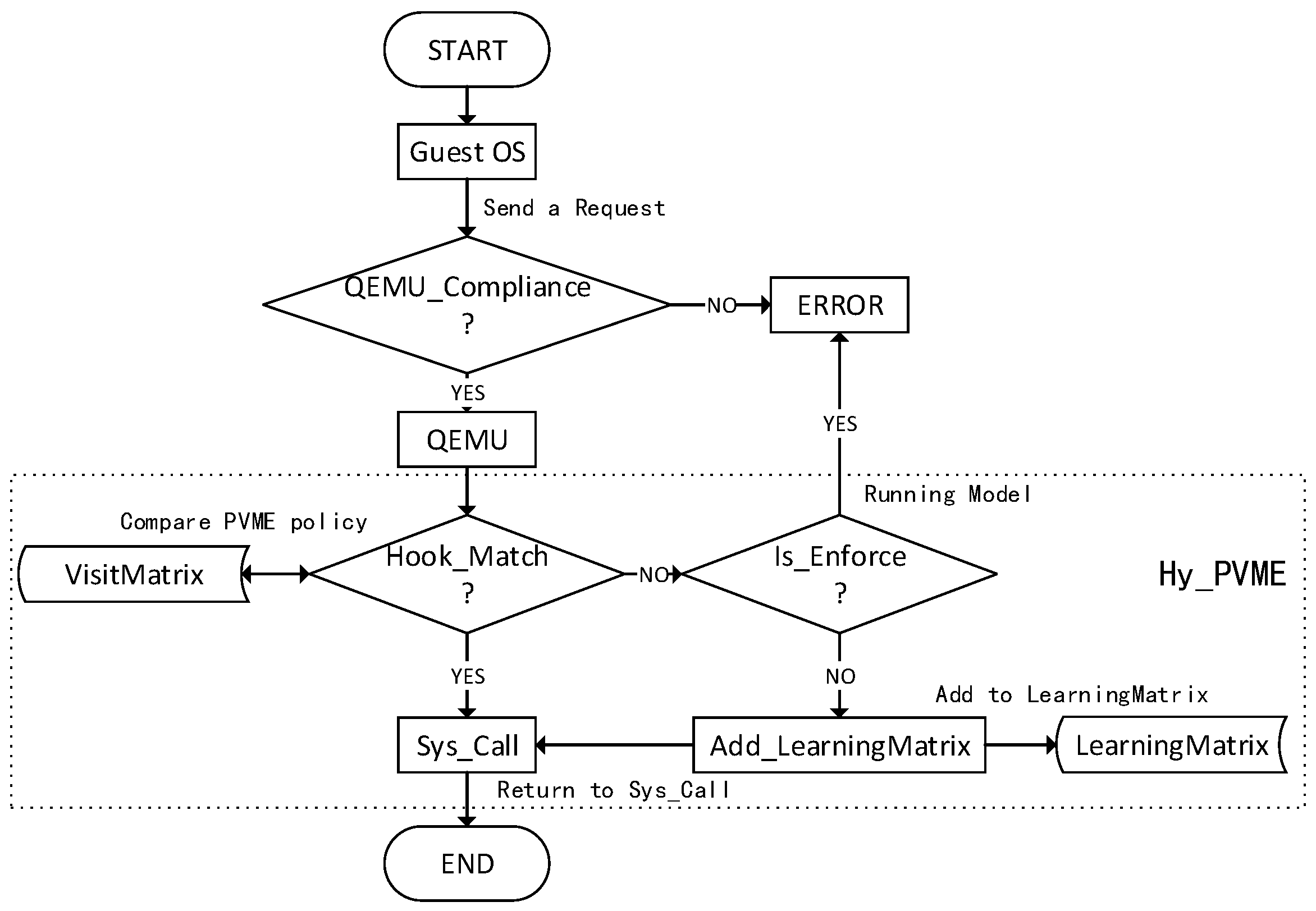
5. Design of the PVME Model
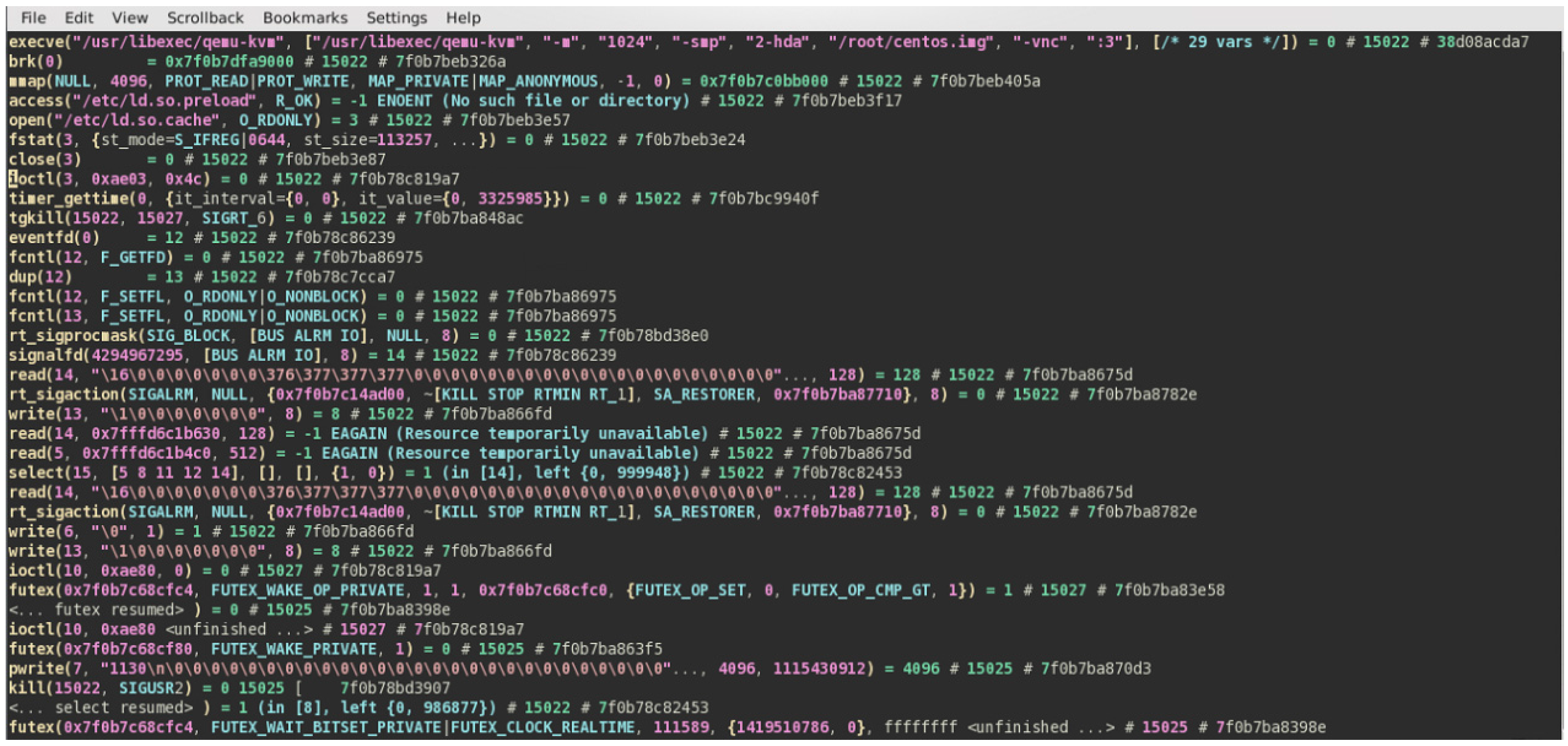
6. Experiments
6.1. Basic Environment
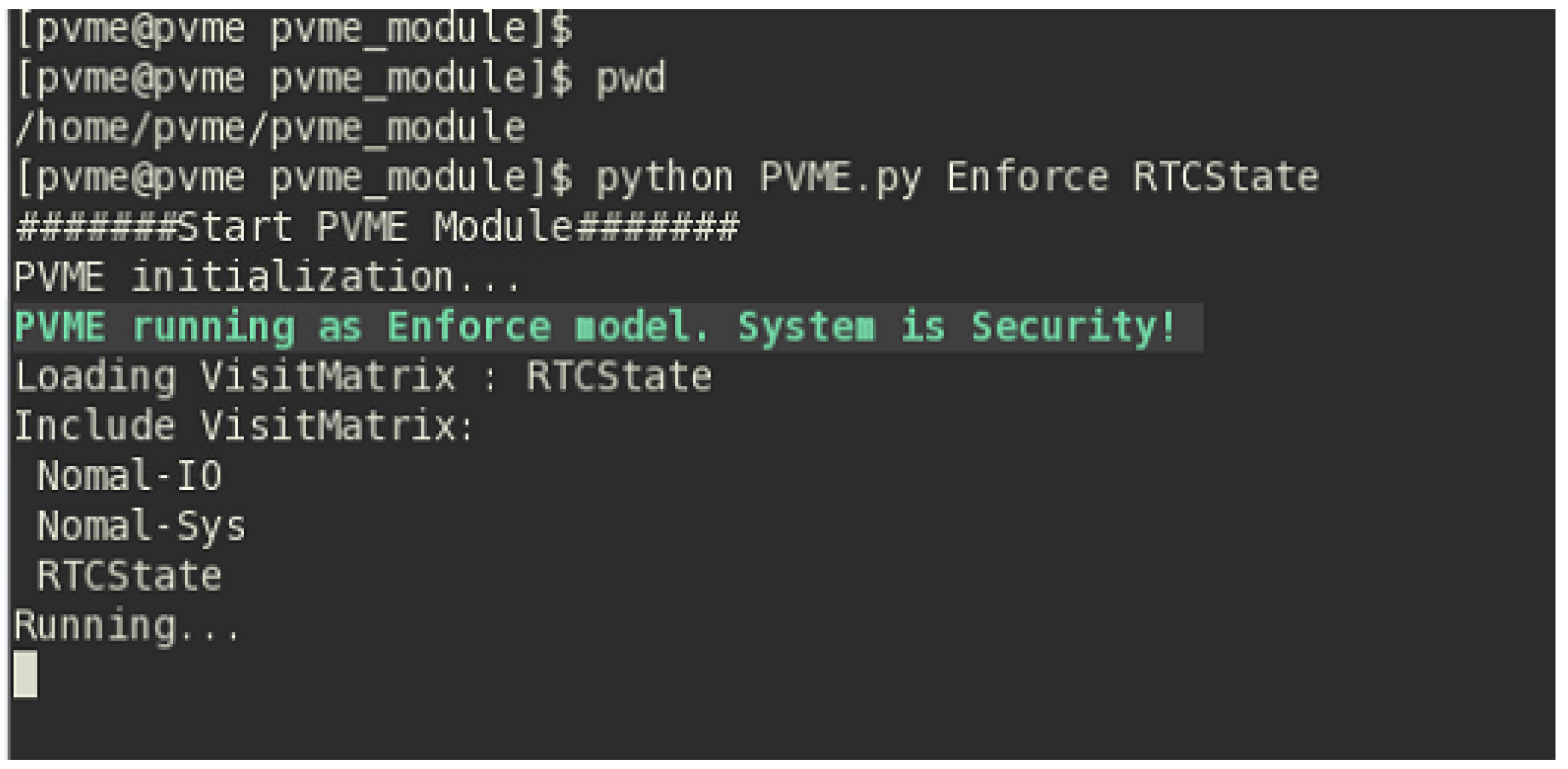
6.2. Initialization of the PVME model
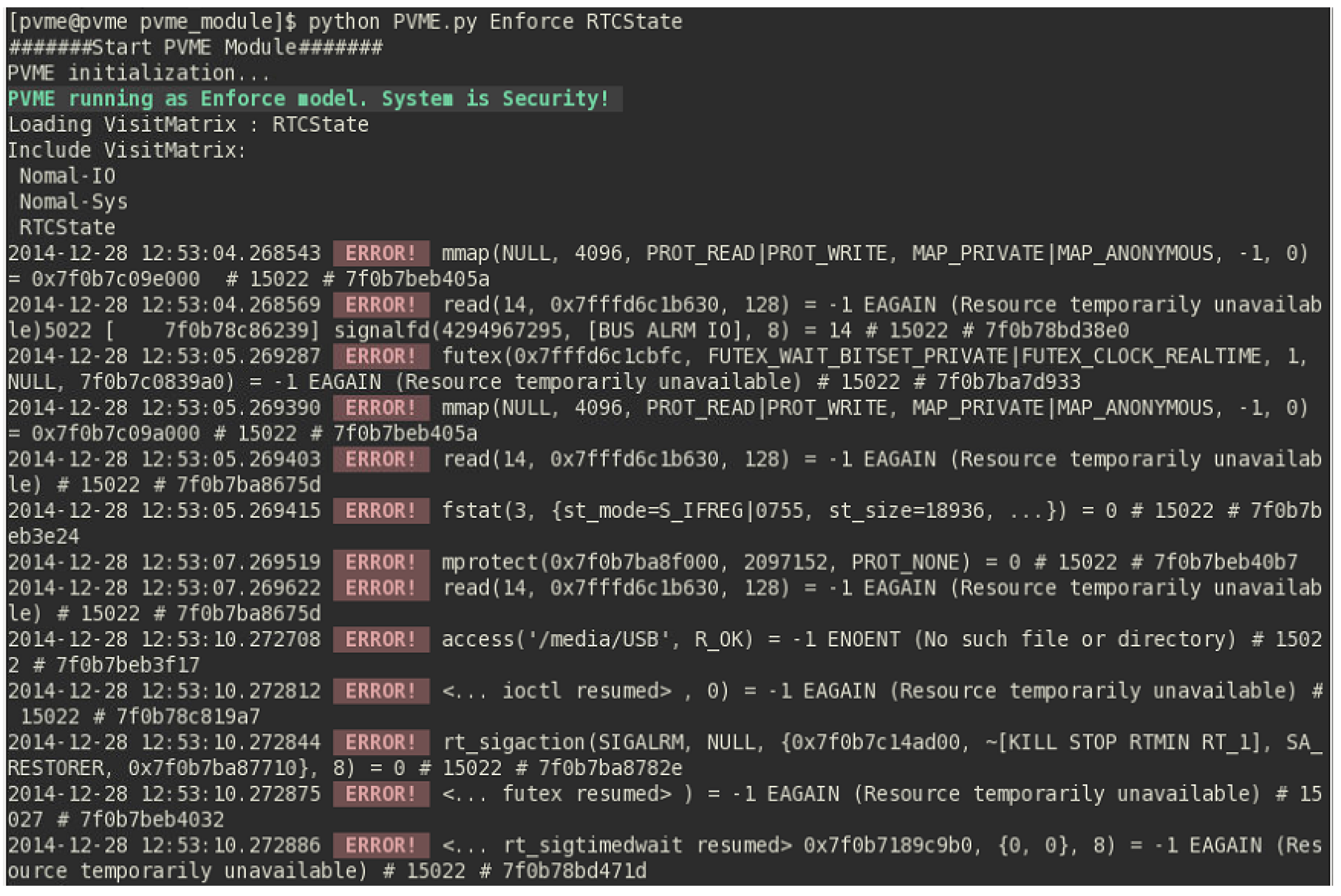
6.3. Simulation of Preventing VM Escape Attack
7. Conclusions
Author Contributions
Conflicts of Interest
References
- Wei, L.; Zhu, H.; Cao, Z.; Jia, W.; Vasilakos, A.V. SecCloud: Bridging Secure Storage and Computation in Cloud. In Proceedings of the 2010 IEEE 30th International Conference on Distributed Computing Systems Workshops, Kozani, Greece, 21–25 June 2010; pp. 52–61. [Google Scholar]
- Wei, L.; Zhu, H.; Cao, Z.; Dong, X.; Jia, W.; Chen, Y.; Vasilakors, A.V. Security and privacy for storage and computation in cloud computing. J. Inform. Sci. 2014, 258, 371–386. [Google Scholar] [CrossRef]
- Ali, M.; Khan, S.U.; Vasilakos, A.V. Security in cloud computing: Opportunities and challenges. J. Inform. Sci. 2015, 305, 357–383. [Google Scholar] [CrossRef]
- Fernandes, D.A.; Soares, L.F.; Gomes, J.; Freire, M.; Inacio, P.R. Security issues in cloud environments: A survey. Int. J. Inform. Secur. 2014, 13, 113–170. [Google Scholar] [CrossRef]
- Modi, C.; Patel, D.; Borisaniya, B.; Patel, A.; Rajarajan, M. A survey on security issues and solutions at different layers of Cloud computing. J. Supercomput. 2013, 63, 561–592. [Google Scholar] [CrossRef]
- Grobauer, B.; Walloschek, T.; Stocker, E. Understanding cloud computing vulnerabilities. IEEE Secur. Priv. 2011, 9, 50–57. [Google Scholar] [CrossRef]
- Kazim, M.; Masood, R.; Shibli, M.A.; Abbasi, A.G. Security aspects of virtualization in cloud computing. In Proceedings of the 12th IFIP TC 8 International Conference on Computer Information Systems and Industrial Management, Krakow, Poland, 25–27 September 2013; pp. 229–240. [Google Scholar]
- Borisaniya, B.; Patel, D. Evasion resistant intrusion detection framework at hypervisor layer in cloud. In Proceedings of the International Conference on Advances in Communication, Network, and Computing, Chennai, India, 21–22 February 2014; pp. 748–756. [Google Scholar]
- Khan, A.A. Isolation of Private Network from Internet, Secure Internet Virtual Environment; Foundation of Computer Science: New York, NY, USA, 2015. [Google Scholar]
- Yang, M.; Li, Y.; Jin, D.; Zeng, L.; Wu, X.; Vasilakors, A.V. Software-Defined and Virtualized Future Mobile and Wireless Networks: A Survey. J. Mob. Netw. Appl. 2015, 20, 4–18. [Google Scholar] [CrossRef]
- Singh, A.; Chatterjee, K. Cloud security issues and challenges: A survey. J. Netw. Comput. Appl. 2017, 79, 88–115. [Google Scholar] [CrossRef]
- Pearce, M.; Zeadally, S.; Hunt, R. Virtualization: Issues, security threats, and solutions. J. ACM Comput. Surv. (CSUR) 2013, 45, 17. [Google Scholar] [CrossRef]
- Islam, T.; Manivannan, D.; Zeadally, S. A classification and characterization of security threats in cloud computing. Int. J. Next-Gener. Comput. 2016, 7, 1–17. [Google Scholar]
- Liu, F.; Ge, Q.; Yarom, Y.; Mckeen, F.; Rozas, C.; Heiser, G.; Lee, R.B. CATalyst: Defeating last-level cache side channel attacks in cloud computing. In Proceedings of the 2016 IEEE International Symposium on High Performance Computer Architecture (HPCA), Barcelona, Spain, 12–16 March 2016. [Google Scholar]
- Han, Y.; Chan, J.; Alpcan, T.; Leckie, C. Using Virtual Machine Allocation Policies to Defend against Co-Resident Attacks in Cloud Computing. IEEE Trans. Dependable Secur. Comput. 2017, 14, 95–108. [Google Scholar] [CrossRef]
- Sze, W.K.; Srivastava, A.; Sekar, R. Hardening OpenStack Cloud Platforms against Compute Node Compromises. In Proceedings of the ACM on Asia Conference on Computer and Communications Security, Xi’an, China, 30 May–3 June 2016; pp. 341–352. [Google Scholar]
- Liu, Q.; Wang, G.; Weng, C.; Luo, Y.; Li, M. A Mandatory Access Control Framework in Virtual Machine System with Respect to Multilevel Security II: Implementation. China Commun. 2011, 7, 137–143. [Google Scholar] [CrossRef]
- Zhu, H.; Xue, Y.; Zhang, Y.; Chen, X.; Li, H. V-MLR: A Multilevel Security Model for Virtualization. In Proceedings of the International Conference on Intelligent Networking and Collaborative Systems, Xi’an, China, 9–11 September 2013; pp. 9–16. [Google Scholar]
- Xue, H.; Zhang, Y.; Guo, Z.; Dai, Y. A Multilevel Security Model for Private Cloud. Chin. J. Electron. 2014, 23, 232–235. [Google Scholar]
- Liu, J.; Li, Y.; Wang, H.; Jin, D.; Su, L. Leveraging software-defined networking for security policy enforcement. J. Inform. Sci. 2016, 327, 288–299. [Google Scholar] [CrossRef]
- Yan, Z.; Li, X.; Wang, M.; Vasilakors, A.V. Flexible Data Access Control based on Trust and Reputation in Cloud Computing. IEEE Trans. Cloud Comput. 2015, PP, 1. [Google Scholar] [CrossRef]
- Bell, D.E.; La Padula, L.J. Secure computer System: Unified Exposition and Multics Interpretation; MITRE Corporation: Bedford, MA, USA, 1976. [Google Scholar]
- Elhage, N. Virtunoid: Breaking Out of KVM. Available online: https://nelhage.com/talks/kvm-defcon-2011.pdf (accessed on 27 May 2017).


| The Element of Request Set | Function |
|---|---|
| The subject requires or releases some access to the object. | |
| The subject requires creating the object or changes its security level. | |
| The subject requires deletingtheobject. |
| Machine | System Version | Kernel Version | With GUI |
|---|---|---|---|
| Host machine | CentOS-6.3 | 2.6.32_279.e16.x86_64 | Yes |
| Virtual machine | CentOS-mini-6.3 | 2.6.32_279.e16.i686 | No |
| SID | OID | Access Property | Flag | ||||
|---|---|---|---|---|---|---|---|
| R | A | W | |||||
| 1101 0101 0111 0 | 1110 1111 0000 1 | 1 | 1 | 1 | 0 | 0 | 1 |
| 1101 0101 0111 0 | 1111 0111 1101 0 | 1 | 1 | 0 | 0 | 0 | 1 |
| 0010 1001 0101 0 | 1101 0101 0111 0 | 0 | 1 | 0 | 0 | 0 | 0 |
| 0010 1001 0101 0 | 0010 1001 0101 0 | 1 | 1 | 0 | 1 | 1 | |
| ID | Security Classification | Security Category |
|---|---|---|
| 0010 1001 0101 0 | 110 | 1110 1000 0000 0000 |
| 1101 0101 0111 0 | 011 | 0101 1000 0000 0000 |
| 1101 0101 0111 1 | 011 | 1101 1000 0000 0000 |
| 1110 1111 0000 1 | 010 | 0001 1000 0000 0000 |
| 1111 0111 1101 0 | 001 | 0101 0000 0000 0000 |
| Subject/Object | Id | Security Classification | Security Category |
|---|---|---|---|
| RTC | 0000 0000 0000 1 | 100 | 1111 0000 0000 0000 |
| next_second_time | 0000 0000 0001 0 | 011 | 1110 0000 0000 0000 |
| rtc_update_second | 0000 0000 0001 1 | 010 | 1110 0000 0000 0000 |
| second_timer | 0000 0000 0010 0 | 001 | 1010 0000 0000 0000 |
| second_timer2 | 0000 0000 0010 1 | 001 | 1010 0000 0000 0000 |
| SID | OID | Access Property | Flag | ||||
|---|---|---|---|---|---|---|---|
| R | A | W | |||||
| 0000 0000 0000 1 | 0000 0000 0001 0 | 0 | 0 | 0 | 0 | 0 | 1 |
| 0000 0000 0001 0 | 0000 0000 0000 1 | 1 | 0 | 1 | 0 | 0 | 1 |
| 0000 0000 0001 0 | 0000 0000 0001 1 | 1 | 0 | 0 | 0 | 0 | 1 |
| 0000 0000 0001 1 | 0000 0000 0001 0 | 1 | 0 | 1 | 0 | 0 | 1 |
| 0000 0000 0001 1 | 0000 0000 0010 0 | 1 | 0 | 0 | 0 | 0 | 1 |
| 0000 0000 0010 0 | 0000 0000 0001 1 | 1 | 0 | 1 | 0 | 0 | 1 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, J.; Lei, Z.; Chen, S.; Shen, W. An Access Control Model for Preventing Virtual Machine Escape Attack. Future Internet 2017, 9, 20. https://doi.org/10.3390/fi9020020
Wu J, Lei Z, Chen S, Shen W. An Access Control Model for Preventing Virtual Machine Escape Attack. Future Internet. 2017; 9(2):20. https://doi.org/10.3390/fi9020020
Chicago/Turabian StyleWu, Jiang, Zhou Lei, Shengbo Chen, and Wenfeng Shen. 2017. "An Access Control Model for Preventing Virtual Machine Escape Attack" Future Internet 9, no. 2: 20. https://doi.org/10.3390/fi9020020
APA StyleWu, J., Lei, Z., Chen, S., & Shen, W. (2017). An Access Control Model for Preventing Virtual Machine Escape Attack. Future Internet, 9(2), 20. https://doi.org/10.3390/fi9020020






