Abstract
Medium Access Control (MAC) protocol is one of the key network protocols that ensure Wireless Sensor Networks (WSNs) maintain high performance during communication. MAC protocol design plays an important role in improving the performances of the whole network. First, Wireless Passive Sensor Networks (WPSNs) and MAC protocols are introduced in this paper. Second, some existing MAC protocols are introduced. Sensor MAC (S-MAC) protocol is analyzed and existing improved backoff algorithms are introduced. A new MAC protocol called Improved Sensor MAC (IS-MAC) is then proposed to solve the problem that the contention window (CW) during carrier sense is fixed in S-MAC protocol. IS-MAC protocol is able to adjust CW in terms of network load, so energy consumption can be decreased. Finally, according to the simulation results on NS2, the proposed protocol has better performance in terms of throughput and energy consumption.
1. Introduction
Wireless Sensor Networks (WSNs) are a kind of multi-hop ad-hoc network and are composed of large amounts of tiny and low-cost sensor nodes. Nodes have the capability to communicate and compute. They connect with each other wirelessly [1]. In WSNs, sensor nodes cooperate with each other under a certain topology to accomplish the goals of monitoring environments, gathering data, processing data, and communicating [2]. WSNs are classified into two types according to two different kinds of sensor nodes: active wireless sensor networks and passive wireless sensor networks [3]. At present, active wireless sensor networks called classic WSNs in this paper are widely used. Active wireless sensor networks are composed of active sensor nodes that are powered by batteries, so their energy is limited [4]. Meanwhile, Wireless Passive Sensor Networks (WPSNs) are composed of passive sensor nodes. Passive sensor nodes are powered via an external Radio Frequency (RF) source that provides infinite power [5]. In a word, the fundamental difference between classic WSNs and WPSNs is the way of power supply [6]. In order to ensure nodes to maintain work as much as possible when the RF source can not provide enough energy, the super capacitor has been applied to the design of passive sensor nodes [7], but it is not sure that nodes can acheive communication. In WSNs, Medium Access Control (MAC) protocols determine the usage of the wireless channel, which will ensure a reasonable allocation of cmmunication resources for a large number of wireless nodes and avoid the collision of nodes while they transmitting data at the same time [8]. At present, nodes mainly consume the energy for hardware platforms. MAC protocols directly control the activities of the radio frequency transceiver and determine when to send out data or receive data [9]. The same MAC protocol can be used in both classic WSNs and WPSNs. However, the same protocol has different effects in two networks. For example, the S-MAC protocol used in classic WSNs saves more energy than in WPSNs. WPSNs only focus on saving energy. Therefore, MAC protocols that cannot save much energy are not fit for WPSNs. Although the energy of WPSNs is infinite, the infinite energy is relative to infinite time. The energy per unit time is limited. For example, WPSNs can only provide 10 mA current, but 100 mA current is needed to achieve communication, so it is necessary to minimize energy to maintain daily work. MAC protocols for WPSNs only need to consider saving energy and do not need to consider delay, throughput, or other parameters. This is the difference in the design of MAC protocols for WPSNs.
The four main sources of energy consumption in the MAC layer are idle listening, data collision, overhearing, and control overhead. Idle listening and data collision are the main factors leading to excessive energy consumption [10]. This paper mainly discusses data collision. One of the strategies to avoid data collision is to design effective backoff algorithms. Based on dynamically changing the contention window of communication, some classic backoff algorithms were previously proposed, but they mainly focused on throughput.
This paper presented an energy efficient MAC protocol called the Improved Sensor MAC (IS-MAC) protocol based on dynamically changing the contention window. It compares the IS-MAC protocol, the Sensor MAC (S-MAC) protocol, and the IEEE 802.11 protocol using the NS2 simulator from two aspects of energy consumption and throughput. The remainder of this paper presents related work in Section 2, a brief description of the IS-MAC protocol in Section 3, the analysis of the simulation in Section 4, and concluding remarks in Section 5.
2. Related Work
This section first introduces several existing MAC protocols. Then, S-MAC protocol’s backoff mechanism is analyzed. Finally, some classic improved backoff algorithms are introduced.
2.1. Several Existing MAC Protocols
There are several existing MAC protocols for WSNs, including the S-MAC protocol, the Timeout MAC (T-MAC) protocol, the Data gathering tree-based MAC (D-MAC) protocol, and the Berkeley MAC (B-MAC) protocol. The S-MAC protocol works with a periodic sleep/listening mechanism and a low duty cycle in order to reduce the energy consumption of nodes. Each node independently controls its working state and should be in sleep state as much as possible. When a node wakes up, it will determine whether to send or receive data packets after listening to the channel. Neighboring nodes consult with each other to have a common sleep/listening mechanism, so they will sleep and listen at the same time. The idle time of nodes is reduced, and the transmission delay is reduced through the adaptive traffic mechanism [11]. The neighboring node of the communication node does not sleep immediately after the communication but keeps listening for some time. If the node receives the RTS frame during this period, it can receive the data packets without waiting for the next listening period. Therefore, the transmission delay of the data packets is reduced. The T-MAC protocol is proposed based on the S-MAC protocol. The S-MAC protocol cannot adaptively change duty cycle according to the current network load. The T-MAC protocol solves this problem: the scheduling period is divided into active states with variable length and sleep states. The idle time can be reduced by dynamically changing the duration of the active states. However, the disadvantage of the T-MAC protocol is that random sleep leads to nodes sleeping early and the delay increases relative to the delay of the S-MAC protocol [12]. In view of the problems of the S-MAC and T-MAC protocols, the D-MAC protocol is proposed. According to the data gathering tree formed by the nodes forwarding data, the D-MAC protocol adopts the staggered wakeup scheduling mechanism to divide a period into receiving time, sending time, and sleeping time. The scheduling of each node has different offsets and the sending time of the lower nodes corresponds to the receiving time of the upper nodes. Ideally, the data can be transmitted continuously from the source node to the sink node so the sleep delay can be eliminated. However, the D-MAC protocol also has its disadvantage. Nodes need strict clock synchronization and the protocol is not suitable for mobile nodes and larger WSNs [13]. The B-MAC protocol has the biggest difference. It adopts a clock asynchronization mechanism so the sleep scheduling has more initiative and the dependence on the accuracy of clock synchronization is reduced. B-MAC protocol uses the Low Power Listening (LPL) mechanism. The nodes have the same duty cycle but do not need to be synchronized. When the nodes wake up from sleep, LPL is used for channel sampling. If the preamble sequence is detected, it means the node will receive data packets. The node will be synchronized by the preamble sequence and then receive data. The sending nodes must send a long preamble sequence before sending data packets so that the receiver can be synchronized. However, the B-MAC protocol has advantages only when network traffic is low [14].
2.2. Analysis of S-MAC Protocol’s Backoff Mechanism
2.2.1. A Description of S-MAC Protocol’s Backoff Algorithm
The discrete backoff algorithm is adopted in S-MAC protocol and it is adopted in IEEE 802.11 MAC protocol as well [11]. The basic idea is the use of a random backoff time in the range of 0 to . refers to the value of current contention window. Each time the node fails to send out data, the value of current is doubled. If the transmission is successful, the value of current is set to the minimum [15]. The random backoff time is obtained based on Equation (1).
In Equation (1), refers to the size of time slot that is determined by the physical layer. represents the random integers that uniformly distribute in . is a random integer in . When the first transmission starts, is set to (the minimum value of ). If the transmission fails, is doubled until it increases by (the maximum value of ). will be reset to after a successful transmittion.
2.2.2. The Disadvantages of S-MAC Protocol’s Backoff Algorithm
The backoff algorithm of the S-MAC protocol is known for its high efficiency and simple implementation. The last node that successfully sends out data has the shortest backoff time, so it can keep its advantage during next competition. However, these kind of nodes always have the maximum competition priority, so the actual condition of the channel is not able to be reflected, which leads to a poor fairness [16]. The contention window drops to the minimum value immediately after the successful transmission and it increases until it reaches the maximum. It is obvious that the wide fluctuations of contention window have adverse effects on the network. The contention window for calculating random backoff time during carrier sense is fixed, which leads to unreasonable channel allocation [17]. In an actual network environment, the load of the network is constantly changing. On one hand, a small contention window is enough for a network to achieve backoff when the network load is not large. Although adopting a big contention window can primely avoid collision, this will lead to too much idle listening. On the other hand, when the network load is large, a relatively small contention window will lead to fierce competition and data retransmission caused by collision. Both of these conditions make throughput and energy efficiency decrease [15]. Apparently, the S-MAC protocol cannot adapt to the dynamic changes of network load due to the fixed contention window.
2.3. Some Improved Classic Backoff Algorithms
In order to improve the throughput and energy efficiency of sensor nodes, different backoff algorithms were proposed in recent years. Dynamically changing contention windows and the size of contention windows can adapt to the dynamic changes of network load. However, they have a common shortcoming: energy efficiency is hardly improved.
- (1)
- Multiplicative Increase Linear Decrease (MILD) algorithm [18]. When data collision occurs in the network, the contention window becomes two times larger than the original window. The contention window will decrease linearly after sending out data successfully. When the number of nodes in the network is not yet large, the contention window is large. This algorithm cannot reduce the contention window rapidly and causes larger transmission delays that reduce the utilization rate of channel.
- (2)
- Multiplicative Increase Multiplicative Decrease (MIMD) algorithm [19]. When collision happens, the contention window is doubled. When data is sent out successfully, the contention window becomes half the size of the original window. MIMD solves the problem of initializing contention window, but there is still no way to satisfy the dynamic changes of network topology and traffic.
- (3)
- Slow Decrease (SD) algorithm [19]. The current contention window of nodes becomes times () as much as the original contention window while accomplishing data transmission. Moreover, this algorithm can improve throughput and fairness among nodes when the number of nodes is large. However, when there are fewer nodes, nodes need to successfully send multiple times to reduce contention window.
- (4)
- Gentle Distributed Coordination Function (GDCF) algorithm [20]. Parameter is introduced in this algorithm and it refers to the number of messages. The current contention window decreases by half of the original window only if nodes successively succeed in sending messages. The value of is related to the number of nodes in the network. When the number of nodes is unknown, is in the range of 4–16. The advantage of this algorithm is that it can provide priority services to the nodes working in the network. The contention window of nodes with smaller value of decreases rapidly, so nodes have higher priority to access the channel. In this algorithm, throughput is greater than in the Binary Exponential Backoff (BEB) algorithm when the number of nodes is large.
3. IS-MAC Protocol
This study proposes a new MAC protocol based on dynamically changing the value of contention window by summarizing the disadvantages of backoff algorithms mentioned in Section 2. The new protocol is called the IS-MAC protocol. The IS-MAC protocol uses several methods including multiplicative increase and multiplicative/linear reduction to adjust the contention window. At the same time, the IS-MAC protocol dynamically adjusts the size of the contention window according to the load of the network.
3.1. Parameters Used in the Improved Algorithm
- (1)
- Current contention window : The size of contention window is not fixed, and it can be dynamically changed within a specific range. This parameter is used to record the value of current contention window.
- (2)
- Minimum of contention window : The lower limit of the range of the current contention window is fixed from the beginning.
- (3)
- Maximum of contention window : The upper limit of the range of the current contention window, , is fixed from the beginning.
- (4)
- The initial value of contention window : , values of and will be set in accordance with the network environment.
- (5)
- Counter for successful competition : This value is used to record the number of consecutive successful transmission and its initial value is 0. The counter plus one as long as the node sends out data successfully. On the contrary, the counter is reset the moment of transmission fails. The counter has an upper limit determined by network load.
- (6)
- Threshold of counter for successful competition : This is the maximum of . The current window will change on the basis of the network load when reaches its limit. It is fixed from the beginning.
- (7)
- Counter for failed competition : The purpose of this counter is to protect nodes that fail to compete and to prevent nodes from unsuccessfully accessing channel for a long time because of its increasing contention window. This value is used to record the number of consecutive failed transmission and its initial value is 0. The value of this counter increases by one while collision happens. Meanwhile, the counter is reset after successfully sending out data.
- (8)
- Threshold of counter for failed competition : This is the upper limit of . The current window will change in line with network load when reaches its limit. It is fixed from the beginning.
The values of those parameters used in our simulation are shown in Table 1.

Table 1.
Parameters and their values in the improved backoff algorithm.
3.2. The Improved Backoff Algorithm
- (1)
- Node fails to access channel. is reset and plus one. It is divided into two cases as follows.
- When the number of continuous failed competition of channel is more than its corresponding threshold, the value of is greater than . The current contention window is too small and needs to be adjusted much larger via multiplicative increase. The new contention window is expressed as , which rapidly makes the contention window depart from area where collision happened just now.
- When the number of continuous failed competition of the channel is less than its corresponding threshold, the value of is less than . If the current contention window is smaller than , then the new contention window becomes . If the current contention window is larger than , then the new contention window is .
- (2)
- Node succeeds in accessing channel. is reset and plus one. It is also divided into two cases as follows.
- When the number of continuous successful competition of channel is more than its corresponding threshold, the value of is greater than . It is considered that the current contention window is too large. There are not so many nodes in the network or there is not so high data traffic. Therefore, the competition of the channel is not intense. In this case, it is not essential to set such a large contention window, so the current contention window value needs to be appropriately adjusted. The new contention window is expressed as . The contention window will be maintained within a certain area in case of its frequent changes.
- When the number of continuous successful competition of channel is less than its corresponding threshold, the value of is less than . The traffic load is relatively large right now, and the competition of channel is intense. Therefore, the current contention window merely requires minor adjustment, so it will be reduced by two to get the new contention window, .
The flow chart of this improved backoff algorithm is shown in Figure 1.
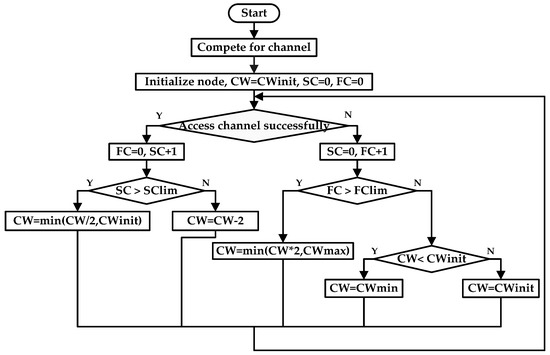
Figure 1.
Flow chart for the improved backoff algorithm.
4. Experiments and Analysis
NS2 is adopted in this paper to analyze the new protocol—IS-MAC. NS2 is a network simulator which is object-oriented and driven by discrete event. It is widely used in a variety of network simulations.
4.1. Network Model and Parameters Configuring
4.1.1. Network Model Selection
A network model is set up before evaluation. The network model includes the number of nodes, the communication range of each node, the size of data packets, and other ingredients. In order to choose a suitable network model, indicators named energy rate and throughput are introduced. Energy rate refers to the energy consumption of transmittiong one bit data of all nodes. Throughput is the total amounts of data packets received by nodes in unit time. Time interval refers to the transmission interval of per data packet. For example, the time interval is 1 s means that when accomplishing sending a data packet, the node will send the next data packet after 1 s. When the time interval is 1 s, the energy rate and throughput of different numbers of nodes are compared. The time interval is chosen as 1 s because at this time the channel competition is very intense and the superiority of the IS-MAC protcol is verified strongly. Figure 2 shows the curves of energy rate and throughput. The horizontal ordinate represents the number of nodes.
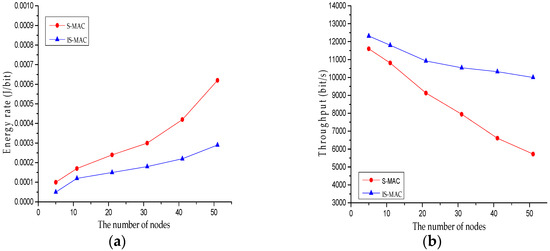
Figure 2.
(a) Energy Rate of S-MAC protocol and IS-MAC protocol under different numbers of nodes; (b) throughput of S-MAC protocol and IS-MAC protocol under different numbers of dodes.
It can be concluded from (a) that with the increase of nodes’ numbers, the gap of energy rate between IS-MAC protocol, and S-MAC protocol become larger and larger. This means that the network saves more and more energy and the IS-MAC protocol performs better than the S-MAC protocol when the number of nodes is large. In (b), the throughput of both protocols declines. With the increase of the number of nodes, channel competition will become more intense, and data collision will happen more frequently. The throughput of nodes will reduce. The throughput of the IS-MAC protocol declines relatively gentle and the throughput of the S-MAC protocol declines rapidly. This means that the IS-MAC protocol performs better than the S-MAC protocol, especially when the number of nodes is large. In conclusion, the IS-MAC protocol performs better than the S-MAC protocol when the number of nodes is large.
Limited to the complexity of large number of nodes, the network model is set up with five nodes. If a conclusion that IS-MAC protocol is better than S-MAC protocol can be drawn when the number of nodes is small, it is obvious that the conclusion will remain when the number of nodes is large.
4.1.2. Network Model Establishment and Parameters Configuring
To quantitatively evaluate the performance of the IS-MAC protocol, the IS-MAC protocol is compared against the S-MAC protocol under a random network scenario. There are five nodes deployed in a square area of 1000 * 1000 m and there are no hidden terminal and exposed terminal problems. The communication range of each node is 250 m. The topology of nodes is a star topology. In a star topology, each node in the network is connected to a central node through the point-to-point mode and information is transmitted to the destination node by the central node. The central node performs centralized communication control strategy, so the central node is very complex. The central node is 200 m away from each node. The topology of the network is shown in Figure 3.
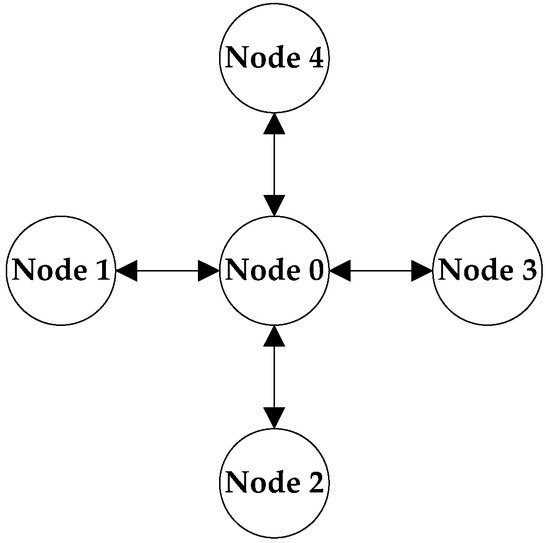
Figure 3.
Topology of Nodes in the Network.
In this experiment, the nodes are classified into three types: sending nodes, receiving nodes, and forwarding nodes (central nodes). When communication starts, sending nodes will send data flow to their fixed destination (receiving node) by forwarding nodes. Forwarding nodes can forward data from sending nodes as well as sending their own data. Events happen randomly within the field and nodes can generate one unit of data packet when one event happens within their sensing range. Table 2 lists the key network parameters used in this simulation.

Table 2.
Network parameters.
The size of per data packet used in these simulations was 512 bytes and the max packets of each node’s interface queue was 50. In order to generate comparable results, all parameters were the same for all three protocols. The initial energy of each node was 1000 J in order to provide unlimited energy. Compared with classic WSNs, the energy provided for each node in unit time is reduced by half in order to simulate WPSNs.
The duty cycle was set 30% because the proposed algorithm performs best when the duty cycle is 30%. When the duty cycle was changed from 30% to 80%, the S-MAC protocol and the IS-MAC protocol were compared in energy consumption and throughput. Energy consumption is the total energy consumption of all nodes during a time period in the network. The vertical ordinate represents energy consumption and throughput. The horizontal ordinate represents duty cycle. The results are shown in Figure 4.
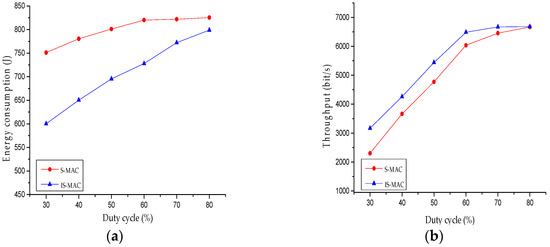
Figure 4.
(a) Energy consumption of S-MAC protocol and IS-MAC protocol under different duty cycles; (b) throughput of S-MAC protocol and IS-MAC protocol under different duty cycles.
It is obvious that the gap of energy consumption and throughput between the IS-MAC protocol and the S-MAC protocol is biggest when duty cycle is 30%. Moreover, to simplify the experiments, the influence of routing traffic was negrlected and it was assumed that there was no obstacle and interference between any two nodes. The energy consumption of MAC protocol was considered to be the most significant indicator.
4.2. Simulation Results
In order to confirm the high energy efficiency of the IS-MAC protocol, the IS-MAC and S-MAC protocols were simulated under the same network environment and the results were compared and analyzed from two aspects—energy consumption and throughput.
4.2.1. Energy Consumption
The vertical ordinate represents energy consumption and the horizontal ordinate represents time interval. The time interval changed from 1 s to 10 s and one point was taken every second. The results of energy consumption are shown in Figure 5.
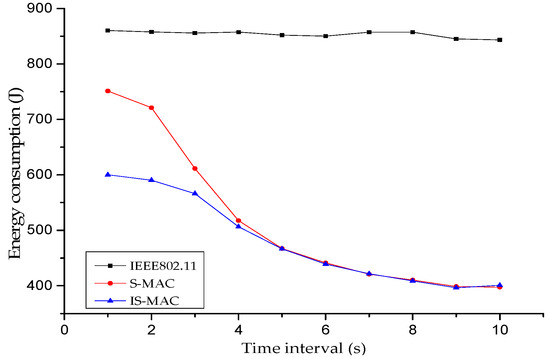
Figure 5.
Energy consumption of sensor nodes under different loads.
With the increment of time interval, both curves decrease in different degrees. With the increase of time interval, the transmission interval of data packets in the network becomes larger and the competition of the channel is not as intense as before. This indicates that the probability of data collision becomes small, and nodes rarely retransmit data because of data collision, so the energy consumption becomes smaller. In the backoff algorithm of the S-MAC protocol, the contention window is a fixed value, which means that it will not be adjusted adaptively with the change of the network load. On the contrary, the IS-MAC protocol is able to dynamically change the contention window according to the channel condition. When the channel is in an extraordinarily intense condition, the current contention window is increased. When the channel is not intense, the current contention window is reduced. This leads to the result that data collision is easier to happen in the S-MAC protocol, so the S-MAC protocol requires more energy to maintain packet retransmission. However, the IS-MAC protocol adopts the method of dynamically changing contention window and obviously consumes less energy. When the time interval is bigger than 4 s, the collision of data packets becomes small. The energy consumption of the nodes mainly come from transmitting data packets. The total amounts of data packets are almost the same in both protocols. Meanwhile, nodes using the IS-MAC or S-MAC protocol can successfully transmit the vast majority of data packets. Therefor, the energy consumption of the IS-MAC and S-MAC protocols is the same. It can also be concluded from the figure that the energy consumption of the IEEE 802.11 MAC protocol is high all the time. Although it has the same backoff mechanism as the S-MAC protocol, it does not follow the periodic sleep/listening mechanism and the nodes are always active. The amount of energy when the medium is idle is almost consumed as much as when the medium is busy. Therefore, large amount of energy will be consumed during the whole work.
4.2.2. Throughput
Throughput is another important indicator to measure network performances. Figure 6 shows curves of throughput. The vertical ordinate represents throughput and the horizontal ordinate represents time interval.
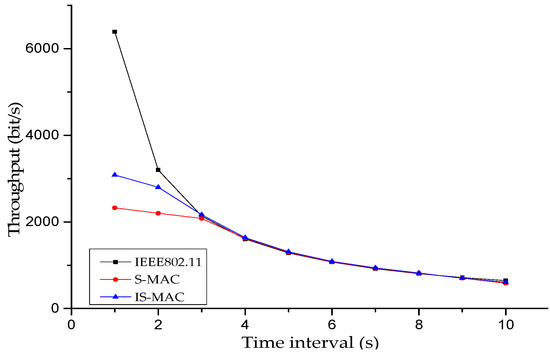
Figure 6.
Throughput under different loads.
In the S-MAC protocol, each node uses a fixed contention window to compete for the access of channel. Therefore, the probability of collision among nodes is extraordinarily high. As can be seen from the figure, all curves show a downward trend with different degrees because the throughput of the network naturally decreases with the decrease of the data flow of the network. The throughput of the IEEE 802.11 MAC protocol is the heaviest because the nodes are always in the listening state. When data is incoming or outgoing, data transmission happens immediately, so the amounts of data packets are large. When the time interval is less than 4 s, the network load is relatively heavy and the throughput of the IS-MAC protocol is higher than that of the S-MAC protocol. When the time interval is 1 s, the advantage of the IS-MAC protocol is most obvious. In this case, the transmission interval of data packets is 1 s, the network load is the heaviest, and the competition is the most intense. The value of the contention window determines the backoff time. When the network load is relatively heavy, the fixed contention window will lead to consecutive data collisions, so data retransmission will be frequent. This reduces the network throughput. The fixed contention window is adopted in the S-MAC protocol while the contention window is dynamically changed according to the network load in the IS-MAC protocol. Therefore, the data collision is more likely to happen in the S-MAC protocol than in the IS-MAC protocol under heavy network load, which means that data retransmission has less frequency and the throughput is larger in the IS-MAC protocol. However, when the time interval is more than 4 s, the network load is relatively small and the data collision becomes little. The throughput of the IS-MAC protocol is only slightly higher than that of S-MAC protocol. In summary, when the network load is small, the IS-MAC protocol has no greater advantage than the S-MAC protocol in throughput. When the network load is larger, the IS-MAC protocol has an obvious advantage over the S-MAC protocol.
5. Conclusions
WPSNs are developing rapidly in practical applications. A MAC protocol called IS-MAC was proposed for avoiding data collision in WPSNs based on a dynamically changing contention window. The proper contention window is computed for energy conservation according to the current network load. Meanwhile, this study introduced some parameters into the procedure of computing the contention window. Besides, this study verified the effectiveness of the improved algorithm on the NS2 platform. The simulation results show that the IS-MAC protocol can significantly outperform the S-MAC protocol in terms of throughput and energy consumption when the network load is heavy.
Acknowledgments
This research was supported in part by the Science and Technology Development Project of Shandong, China, (No. 2015GSF120003), the Independent Innovation Foundation of Shandong University, China, and the Science and Technology Development Plan Project of Weihai Municipal in 2016. The authors would like to thank Chengyou Wang and Zunhua Guo for their help and valuable suggestions. The authors also thank the anonymous reviewers and the editor for their valuable comments for improving the presentation of the paper.
Author Contributions
Q.Y. and G.L. conceived and designed the experiments; Q.Y. performed the experiments; Q.Y. and X.H. analyzed the data; K.F. and T.L. contributed reagents/materials/analysis tools; Q.Y. wrote the paper.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Yang, X.; Deng, D.T.; Liu, M.F. An Overview of Routing Protocols on Wireless Sensor Networks. In Proceedings of the 4th International Conference on Computer Science and Network Technology, Harbin, China, 19–20 December 2015. [Google Scholar]
- Padalkar, S.; Korlekar, A.; Pacharaney, U. Data Gathering in Wireless Sensor Networks for Energy Efficiency with and without Compressive Sensing at Sensor Node. In Proceedings of the International Conference on Communication and Signal Processing, Melmaruvathur, India, 6–8 April 2016. [Google Scholar]
- Akan, O.B.; Isik, M.T.; Baykal, B. Wireless Passive Sensor Networks. IEEE Commun. Mag. 2009, 47, 92–99. [Google Scholar] [CrossRef]
- Tudose, D.S.; Marin, A.; Geantǎ, M. Adaptive Duty-cycling Algorithms for Efficient Energy Harvesting in Wireless Sensor Networks. In Proceedings of the 15th RoEduNet Conference of Networking in Education and Research, Bucharest, Romania, 7–9 September 2016. [Google Scholar]
- Correia, R.; Carvalho, N.B.; Kawasaki, S. Continuously Power Delivering for Passive Backscatter Wireless Sensor Networks. IEEE Trans. Microw. Theory Tech. 2016, 64, 3723–3731. [Google Scholar] [CrossRef]
- Hong, Y.W.P.; Hsu, T.C.; Chennakesavula, P. Wireless Power Transfer for Distributed Estimation in Wireless Passive Sensor Networks. IEEE Trans. Signal Process. 2016, 64, 5382–5395. [Google Scholar] [CrossRef]
- Fernandes, R.D.; Boaventura, A.S.; Carvalho, N.B.; Matos, J.N. Increasing the Range of Wireless Passive Sensor Nodes Using Multisines. In Proceedings of the IEEE International Conference on RFID-Technologies and Applications, Sitges, Spain, 15–16 September 2011. [Google Scholar]
- Ojo, M.; Adami, D.; Giordano, S. Performance Evaluation of Energy Saving MAC Protocols in WSN Operating Systems. In Proceedings of the International Symposium on Performance Evaluation of Computer and Telecommunication Systems, Montreal, QC, Canada, 24–27 July 2016. [Google Scholar]
- Le Guennec, L.; Rachkidy, N.E.; Guitton, A.; Misson, M.; Kelfoun, K. MAC Protocol for Volcano Monitoring Using a Wireless Sensor Network. In Proceedings of the 6th International Conference on the Network of the Future, Montreal, QC, Canada, 30 September–2 October 2015. [Google Scholar]
- Kakria, A.; Aseri, T.C. Survey of Synchronous MAC Protocols for Wireless Sensor Networks. In Proceedings of the Recent Advances in Engineering and Computational Sciences, Chandigarh, India, 6–8 March 2014. [Google Scholar]
- Munadi, R.; Sulistyorini, A.E.; Fauzi S, F.U.; Adiprabowo, T. Simulation and Analysis of Energy Consumption for S-MAC and T-MAC Protocols on Wireless Sensor Network. In Proceedings of the IEEE Asia Pacific Conference on Wireless and Mobile, Bandung, Indonesia, 27–29 August 2015. [Google Scholar]
- Mihai, G.; Alina, D.A.; Ion, B. Performance analysis on T-MAC protocol over a body area network. In Proceedings of the 3rd International Symposium on Electrical and Electronics Engineering, Galati, Romania, 16–18 September 2010. [Google Scholar]
- Kebkal, O.; Kebkal, K.; Bannasch, R. Long-baseline Hydro-acoustic positioning using D-MAC communication protocol. In Proceedings of the OCEANS, 2012—Yeosu, Yeosu, Korea, 21–24 May 2012; pp. 1–7. [Google Scholar]
- Bdiri, S.; Derbel, F.; Kanoun, O. Wireless sensor nodes using energy harvesting and B-Mac protocol. In Proceedings of the 10th International Multi-Conferences on Systems, Signals and Devices, Hammamet, Tunis, 18–21 March 2013. [Google Scholar]
- Shurman, M.; Al-Shua’b, B.; Alsaedeen, M.; Al-Mistarihi, M.F.; Darabkh, K.A. N-BEB: New Backoff Algorithm for IEEE 802.11 MAC protocol. In Proceedings of the 37th International Convention on Information and Communication Technology, Opatija, Croatia, 26–30 May 2014. [Google Scholar]
- Dai, G.; Miao, C.; Ying, K.; Wang, K.; Chen, Q. An Energy Efficient MAC Protocol for Linear WSNs. Chin. J. Electron. 2015, 24, 725–728. [Google Scholar] [CrossRef]
- Pandit, S.; Singh, G. Backoff Algorithm in Cognitive Radio MAC Protocol for Throughput Enhancement. IEEE Trans. Veh. Technol. 2015, 64, 1991–2000. [Google Scholar] [CrossRef]
- Wu, H.; Cheng, S.; Peng, Y.; Long, K.P.; Ma, J. IEEE 802.11 Distributed Coordination Function (DCF): Analysis and Enhancement. In Proceedings of the IEEE International Conference on Communications, New York, NY, USA, 28 April–2 May 2002. [Google Scholar]
- Pang, Q.X.; Liew, S.C.; Lee, J.Y.B. Performance Evaluation of an Adaptive Backoff Scheme for WLAN. Wirel. Commun. Mob. Comput. 2004, 4, 867–879. [Google Scholar] [CrossRef]
- Ziouva, E.; Antonakopoulos, T. CSMA/CA Performance under High Traffic Condition: Throughput and Delay Analysis. Comput. Commun. 2002, 25, 313–321. [Google Scholar] [CrossRef]
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).