A Framework for Security Transparency in Cloud Computing
Abstract
:1. Introduction
2. Related Works
3. Transparency Basics
4. Cloud Security Transparency
The disclosure of information related to security practices and controls used in the protection of customer data and applications hosted in the cloud environment. It also entails providing synchronous and asynchronous information to events pertaining customer data and applications in order to enable them to obtain sufficient visibility of incidents concerning their assets while in the custody of a cloud service provider.
4.1. Why do We Need Security Transparency in Cloud?
4.2. Principles of Security Transparency in Cloud
- Availability. Availability means that information relating to occurrences regarding migrated assets should be available to the users. A monitoring system should be configured to stream real-time or near-real time status information regarding customer assets and every action performed to those assets.
- Clarity. Implies that information should be clear and precise for easy understanding. In other terms, clarity eliminates all elements of ambiguity so that information is delivered precisely, in a coherent and intelligible manner. The benefit of clarity is about helping CSCs utilise information to reduce complexity and uncertainty so that analysis can be applied to identify a clear path forward. An example to this is represented by a scenario where a shared responsibility model for security provisioning is adopted. The CSP should clarify their responsibility in securing a cloud infrastructure, while CSCs should take on the responsibility of securing data or applications integrated into that infrastructure.
- Current. Means that the information should be up-to-date. Information should be regularly streamed to CSCs in a real-time or near real-time flow for enabling the evaluation of actions pertaining to their assets in the cloud. Also, the information should clearly state the timestamp and occurrences of actions in relation to cloud-hosted assets. For example, anomaly detection in the cloud environment greatly depends upon current or real time information.
- Relevance. Information should be relevant to the context. Cloud systems consist of numerous virtual machines, hardware, operating systems and applications that provide valuable information. Information must be relevant to provide information from a variety of platforms. For example, if a CSC subscribes to information feed on cloud resource availability, the usage data of the cloud resource being considered should be particularly streamed to CSCs.
- Notification. Information relating to security incidents, events, deviations, or occurrences that affect customer assets in the cloud should be appropriately disseminated to concerned customers so that they can evaluate the occurrences and optionally take action. For example, the presence of dedicated monitoring systems that detect security phenomenon and notify CSCs to take remedial actions or invoke an autonomous action.
- Free of Charge or at Low Cost. Information should be automatically compiled, organised collocated and streamed to concerned cloud actors that subscribe information feed for free of charge or at a low cost.
4.3. Categories of Cloud Security Transparency
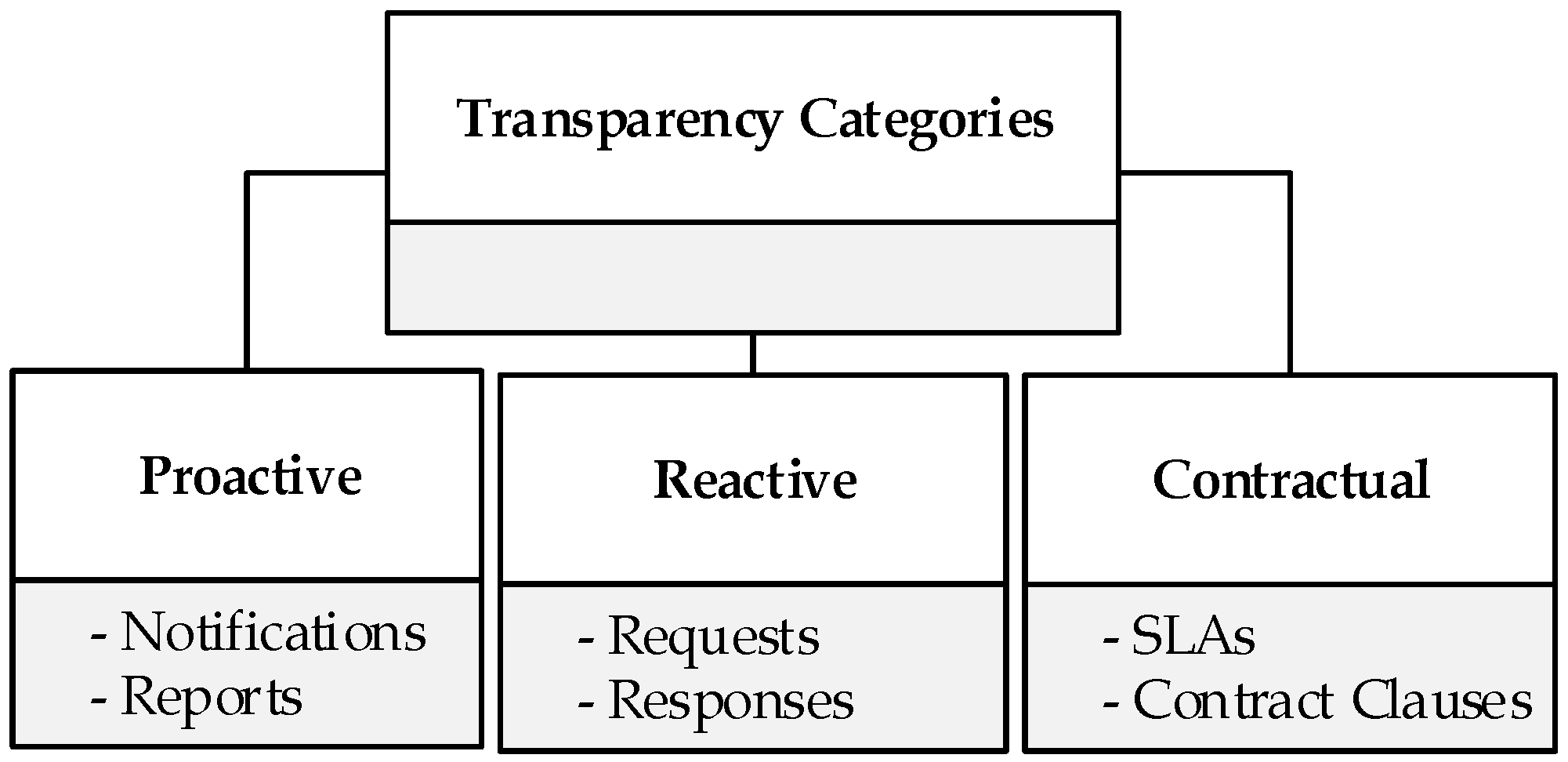
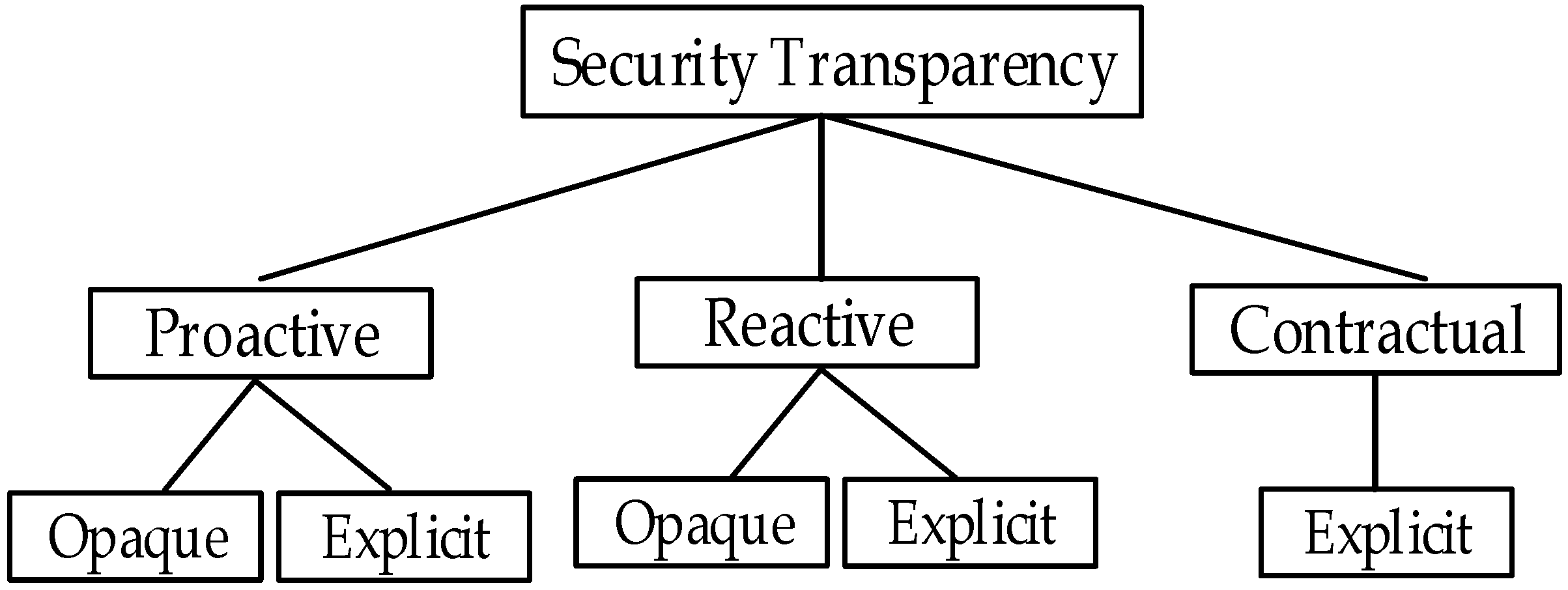
- Proactive Transparency (Voluntary). Proactive transparency involves voluntary disclosure of information, meaning that the CSP voluntarily provide information to the users by means of autonomous agents or manual process. It stems from CSPs initiatives to make security information of their offerings available to all without a request being filed. It can be generated through various methods such as notifications or reports (such as websites and portals, benchmarks, whitepapers, etc.). This disclosure is generally intended to improve customer trust and confidence, assist customers evaluate basic CSP control environments, demonstrate CSP certification to regulatory or industry requirements, and also help customers address some specific questions around general practices. It does not reveal information that could jeopardise the security posture of a CSP or expose them to harm’s way. For instance, when a CSC’s data falls under restrictions emanating from regulatory or compliance requirements, the choice of a CSP hinges on the contentment that they are fully compliant to a regulatory body, otherwise there is the risk of violating regulatory, legal or other privacy requirements [25]. The benefits that accrue from CSPs initiative to proactively disclose information include the availability of information that ensures timely access to information to help all CSCs including small, large and medium enterprises without the need to file special request, which is indeed associated with various sorts of commitments.
- Reactive Transparency (Necessary). Reactive transparency involves a request-driven approach where a CSP is expected to respond to a user’s specific request. It emerges from a request-response routine between a CSC and a CSP for the latter to provide additional information. Through the request-response regime, a prospective user files a request and receives information from an existing CSP or for an incident notification to be sent to the CSC. Generally, the contents of a CSP response represent the actual settings, offerings or security status of CSC assets rather than a meagre attempt to beat competition from other vendors, which indeed increases transparency on how individual requirements are distinctly addressed. The advantage of the request-response driven approach is its ability to enable users to exclusively specify their security requirements and the identification of suitable controls by the CSP. However, it could be argued that it has become a traditional practice for CSPs to frequently publish information in public domains so that future cloud users do not have to file a request, saving time for both the CSP and the customers.
- Contractual Transparency (Statutory). This implies that a CSP is legally mandated by the law to provide transparency while rendering services to CSCs. It involves a valid written agreement where the CSP observes utmost disclosure of all essential security services on an individual basis, while refraining from divulging information that could compromise the privacy of other users. SLAs are useful tools widely used by both CSPs and CSCs for ensuring transparency and establishing a common pact in order to manage the security requirements requested by a CSC and the security levels being offered by a CSP. Also, the SLA forms the basis for defining responsibilities and the remedies available for customers in case of a contract breach. Fundamental aspects of the SLA are the representation of the contexts shared by the two parties, and how each actor utilises the contexts in its own operations throughout the SLA. In order words, the SLA provides a comprehensive description and transparent security processes for both the CSP and customer to avoid uncertainty, apprehension and disputes. Conventional SLAs generally provide clarity on CSP service offers, unambiguous definition of expectations and obligations on both sides, and the boundaries of liability. Nevertheless, a notable limitation to this class of transparency is that essential security properties of a customer may not be captured.
4.4. Cloud Security Transparency Deployment Practices
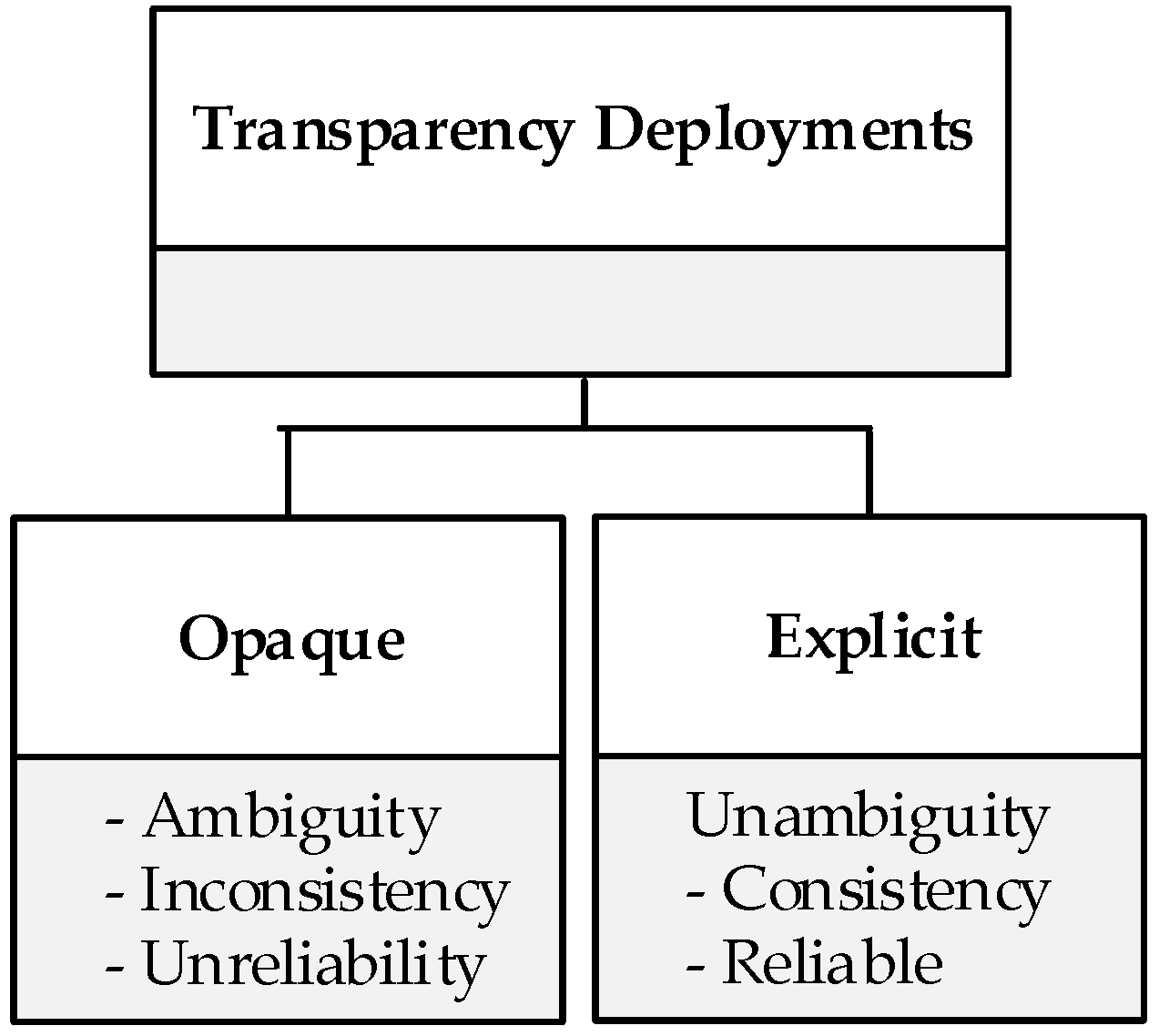
- Opaque Transparency. Opaque transparency means that information is not well clarified. It involves CSPs disclosing information that either partially represent its actual operational values or provides equivocal statements. It may also involve inconsistent or unreliable information in terms of how controls are actualised in the cloud environment. For example, a CSP might claim to operate a service with security as a key principle through the implementation of reasonable technical network security routines, but then fails to genuinely demonstrate the application or actual implementation of significant secure network architectures and security devices that monitor and control communications at the key boundaries within their environment. This would mean that transparent service is provided with virtually futile effects.
- Explicit Transparency. This refers to the disclosure and dissemination of information that represents a realistic implementation of CSP security control that precisely outlines the processes and procedures of how operations are securely managed. It provides a comprehensible elucidation on CSP’s approach to ensuring the protection of CSC assets while in their control. This type of transparency is considered as most effectively attracting customer trust and confidence, as well as supporting accountability in the cloud. An example of explicit transparency would involve a CSP supporting a system that collects data related to the state or behaviour of customer assets and sends such data for onward analysis and evaluation by the concerned customer.
4.5. Relationship between Categories of Transparency and Deployment Practices
5. Cloud Security Transparency Framework
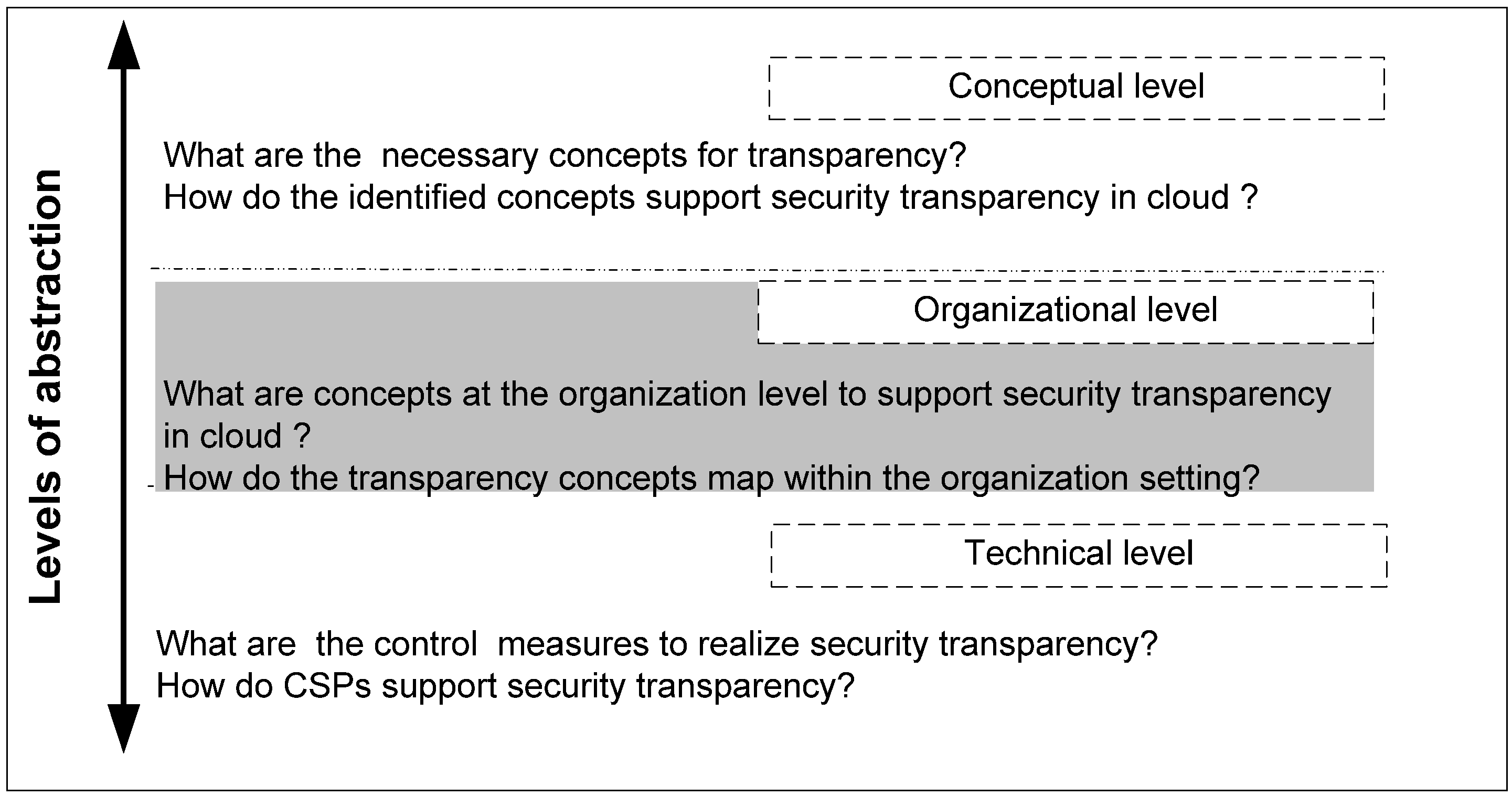
5.1. Levels of Abstractions
5.2. Conceptual View
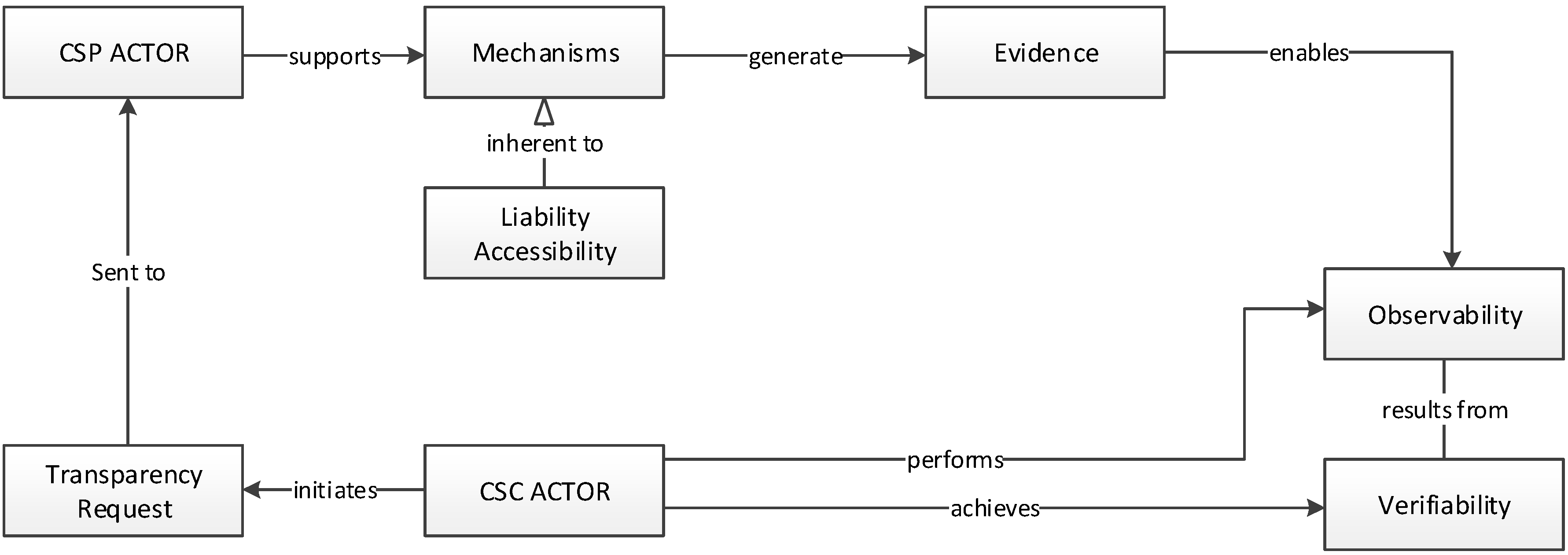
- Actor. An actor represents an entity, partiularly a CSP, a system, an organisation, a user, or a process that carries out actions to generate transparency or become the recipient of transparency generated by another actor.
- Transparency Request. The purpose of a transparency request is to allow a CSC to collect information about the capabilities of a CSP and the occurrences of incidents that affect their migrated assets within the cloud environment. It is initiated by the CSC seeking real-time or recorded information being held by a CSP, particularly information that discloses how requirements can be fulfilled and how operations are being executed on migrated assets. The core of this concept is enabling the CSC to wholly specify the information required to support their operations, thereby constituting the need for an explicit rather than opaque transparency. A way for a CSC to request transparency is achieved by way of reactive or contractual transparency, largely due to the fact that both categories support actors in their requests for additional disclosures relevant to their needs. In most cases, CSPs exclusively deploy explicit transparency in response to the transparency requests in order to avoid misinterpretation of legal liabilities. It is noteworthy to highlight the distinction between transparency requests and the requirements concept (at an organisational level). Transparency requests do not independently support the description of CSC requirements, it rather solicit details on how requirements are fulfilled and how occurrences are reported. Whereas, the requirement concept aims at enabling the specification of the most pertinent security requirements to the assets of a CSC.
- Mechanism. A mechanism is defined as a high level or low level solution being adopted for the disclosure of relevant security information pertaining to an actor’s operational processes. The term is used to imply an actor making use of proactive, reactive or contractual transparency initiatives to make operational information available and respond to transparency requests by detailing how it conforms to governing rules and providing security protections. Furthermore, a mechanism is predominantly the fore attribute that triggers the conceptualisation of other concepts because it presents first-hand information in areas of common security practices and management.
- Evidence. Evidences represent disclosures in a specific format that provide collective information about transparency mechanisms. The aim is to enable an actor to provide to other actors a status report on the general security condition of its environment. Another important aspect of the evidence is to support actors to perform a check and verification of disclosures against their transparency needs in order to purposefully determine the integrity of an actor’s response to their requests.
- Accessibility. Encompasses the credence for an actor’s transparency mechanism and emerging evidences to be requisitely made available, accessible and affordable to all other actors through various initiatives. It contains initiatives regarding information disclosure such as autonomous reporting systems, websites, policies, compliance, SLA etc.
- Liability. This is the state of being legally responsible for security transparency i.e., an actor becomes legally answerable for the contents of a disclosure. An actor that is held liable for a disclosure becomes legally responsible to render agreed redress in non-fulfilment or misstatement of information. For example, if contractual agreements have been reached between a CSP and a customer for the former to provide 99% service availability, they become legally liable to ensure such and redress the latter in the event of a failure.
- Monitoring. This is the ability to observe and check the quality of information provided. In order to substantiate the accuracy of a disclosure, it must be observable by other actors. This may be achieved through analysing evidences generated by a transparency mechanism being supported by an actor. In other words, monitoring is a function of processes that can be used to establish the effectiveness of the internal operations of an actor by observing the content in evidence.
- Verifiability. This is the degree to which a disclosure can be confirmed to be existent and to establishing its accuracy. This concept allows other actors to validate whether observable properties comply with agreed expectations or requirements. It is concerned with ensuring that materials presented are made truthfully and reflect genuine credibility about perceived quality.
5.3. Organisational Level and Modelling Concepts for the Framework
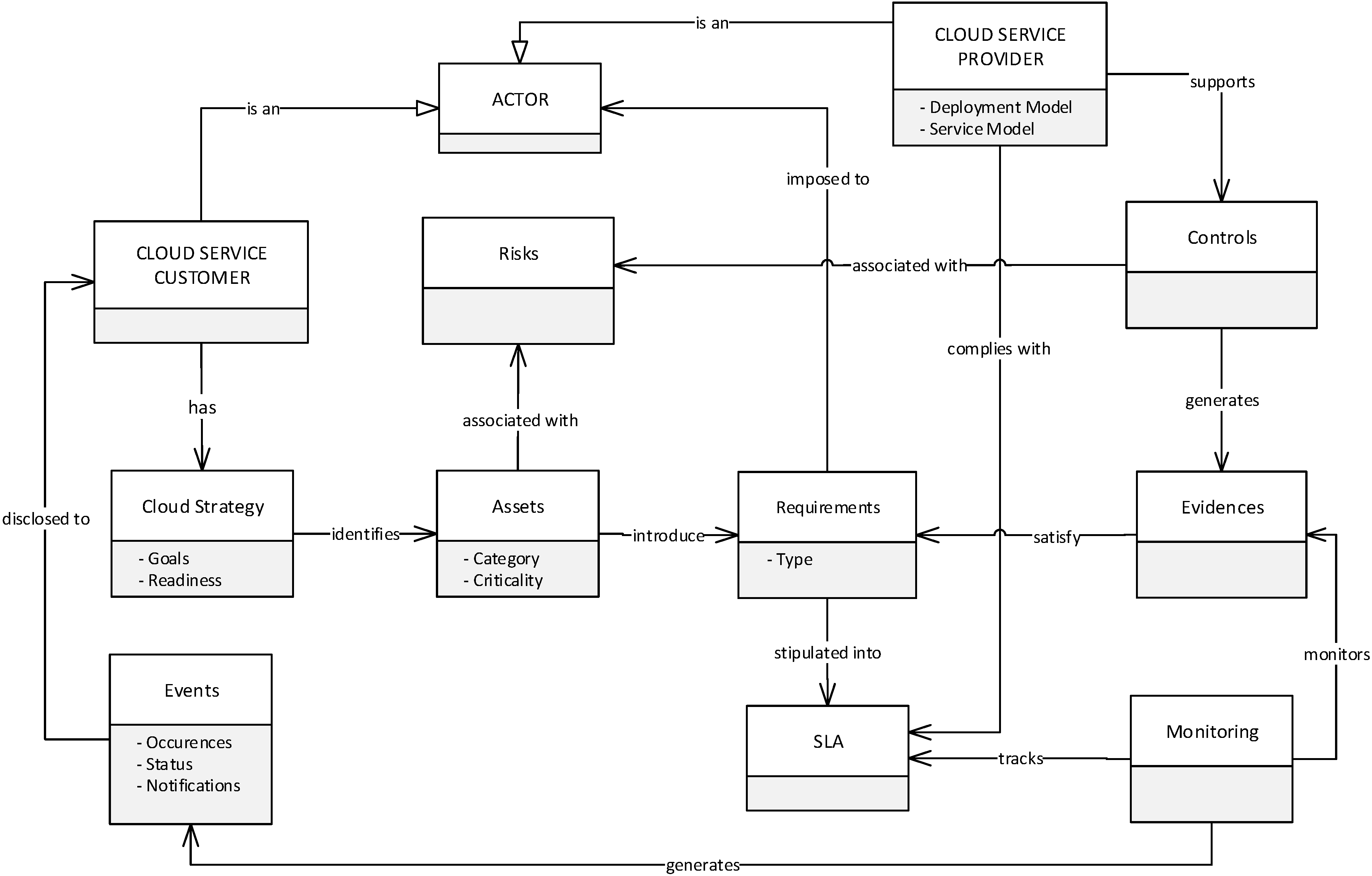
- Cloud Strategy. This supports the CSC to make sense of adopting or the reasons cloud services have been adopted. In other words, it allows CSCs to conduct an internal analysis of their goals and the readiness to adopt cloud services, and how security transparency can be realised. The cloud strategy is characterised by two attributes:
- ○
- Goals. Represent the aims and objectives of a CSC’s intention of migrating to the cloud. The goals could be cost reduction, flexibility and scalability, improved accessibility, and security etc.
- ○
- Cloud Readiness. This analyses the integration of locally hosted applications, data, or processes with cloud services in terms of standardisation, format, portability, interoperability, etc. Also, cloud readiness identifies the potential benefits associated with fulfilling goals.
- Assets. This involves the identification of CSC assets, those assets that are outsourced to the cloud environment and those that are hosted locally. Selected assets are classified according to category and criticality to the operations of the CSC. The relevance of this is to allow for the identification of the essential security requirements that are put around the assets to help the CSC maintain a track record of the assets. Asset has two attributes:
- ○
- Category. Assets are classified according to different tiers of sensitivity and security requirements such as public, open or confidential. Public means asset is accessible to the general public, open means available to every company user, confidential limits access to only authorised company users.
- ○
- Criticality. Criticality is the major indicator used by the CSC to determine the importance of the asset to the business. Criticality is not dependent upon category, however, the criticality of any asset category can be high, medium or low. Assets with a high rating are the most valuable to CSC, a medium rating represents a moderate value; while low means little value to the CSC.
- Risk. Risks are the potential consequences inherent to a CSP control environment that could potentially compromise the security of assets in the cloud. A risk could fall under one or more of areas of cloud such as: security, operational, technical, nontechnical, regulatory, governance etc.
- Controls. Controls are sets of security safeguards or countermeasures to avoid, counteract or minimise security risks in a CSP operating environment. Controls may also represent the mechanisms used by CSPs for providing transparency. They are supported by a CSP and characterised by a combination of technical and non-technical controls that describe the essential components assembled and actions taken to protect assets.
- Evidences. Are affirmations from the CSP specifying the existence of acclaimed security controls and providing a transparent overview of their implementation/management. In other words, evidences are exclusively generated by a CSP in connection with supported controls to CSCs assets. They provide a detailed representation of the actual security controls in the areas of technical, human, physical and operational safeguards adopted by a CSP to sustain security, and reveal the actions, functions and steps taken in order to provide transparency and meet CSC security expectations. They are provided through attested sources such as automated evidence collection tools, websites, security whitepapers, etc.
- Requirements. Requirements imply vital security needs for safeguarding CSC assets and enabling security transparency. In some scenarios of service negotiation, a CSC may be wholly satisfied with CSP offerings while in other scenarios the CSC may identify some inadequacies between CSP offerings and their needs. In both circumstances, the CSC identifies and clearly defines the essential security requirements that safeguard assets and which are worthy of tracking to ensure continuous transparency. Put differently, requirements represent the crucial CSC security needs that are continuously monitored for transparency once assets are outsourced to the cloud. It is important to mention that requirements’ extraction considers the identified goals from the cloud strategy, risks, security best practice and assets. For ensuring the extraction of appropriate requirements, best security practice guide such as Cloud Security Alliance’s Cloud Control Matrix (CSA CCM, 2011) should be taken into consideration.
- SLA. The pertinent CSC security needs identified through the requirements concept are stipulated as requisite clauses in the SLA. The clauses are transformed to form the subject of security transparency that deliver visibility into the security occurrences on assets migrated to the cloud.
- Monitoring. Monitoring involves the tracking of security events pertaining to CSC security requirements as specified in the SLA. It also tracks CSP controls in order to check their operational status. It consolidates several services that are supported by the CSP to enable CSCs to collect evidences on the status of their assets.
- Events. Events deal with information provided to show the incidents, or activities performed on CSC assets and the resulting status of the assets. They are the occurrences that take place in the cloud services relevant for CSC assets. Events send a status report generated by the monitoring concept to provide accurate and timely information relating to the operating conditions that are of interest to CSC requirements. This will generate evidence-based trust between cloud actors that all expectations are being met and that everything claimed to be happening in the cloud is indeed happening.
5.4. Technical Level
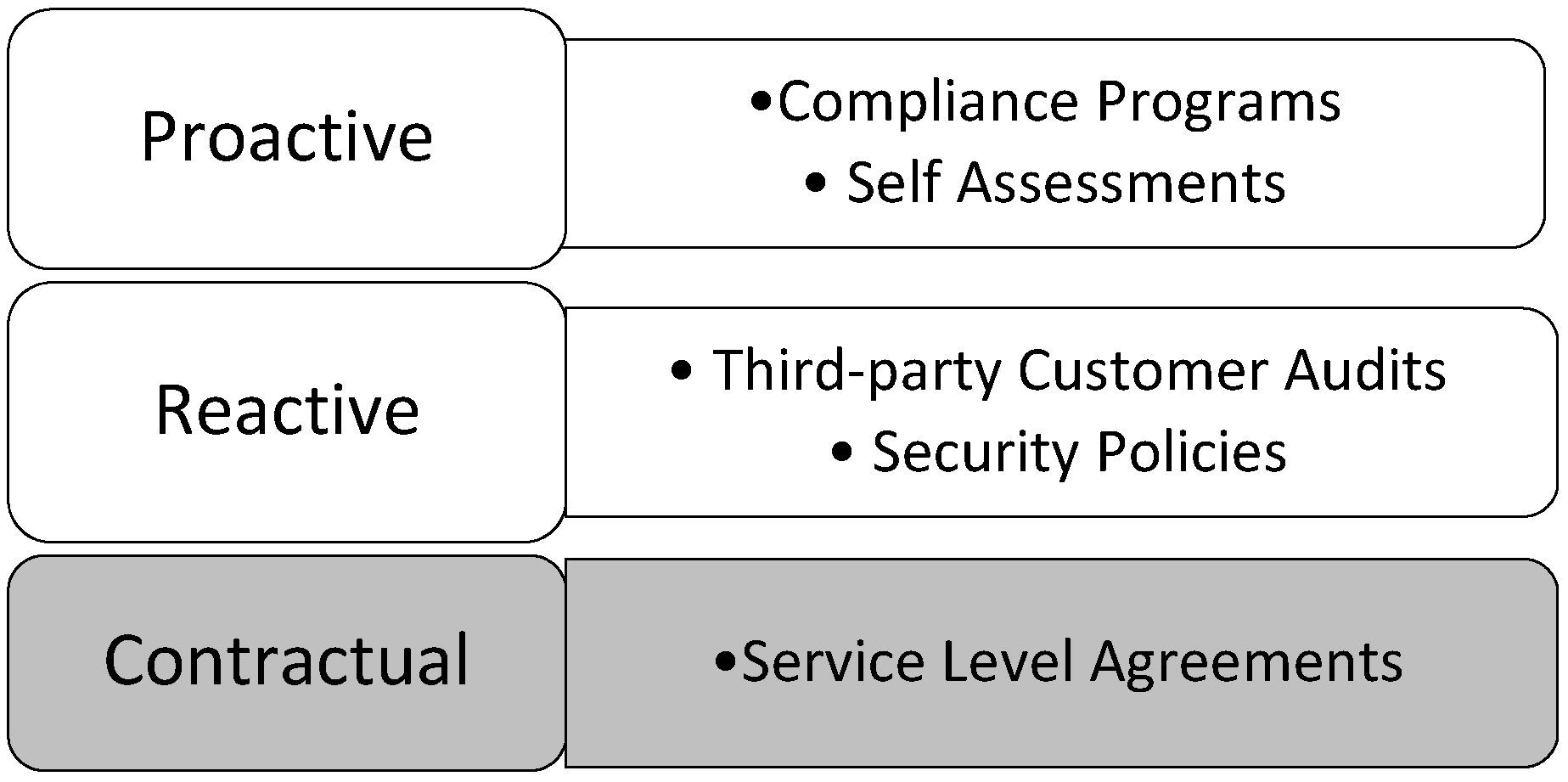
- Compliance Programs: CSPs are increasingly using compliance programs as mechanisms for demonstrating transparency through conformity with multiple traditional standards that predominantly focus on certifying the composition and management of security practices in CSP environments. Consequently, CSPs earmark a significant sum of budget for ensuring security, and spend sizeable amount of resources and time into compliance with security standards such as ISO 27001/27002, Payment Card Industry Data Security Standards (PCI DSS), and other relevant standards.
- Self-assessments: CSPs have realised the obligation to provide satisfactory transparency of their services to CSCs. CSPs often conduct a discretional self-assessment of their services by employing control objectives specified in frameworks that document and certify best security practice within CSP environment in order to provide transparency to their customers. Self-assessments are usually free and open to all CSPs. One such framework is CSA STAR Certification that embarks on a three-levelled certification scheme to certify CSP’s compliance to its set of security guidance and control objectives.
- Third-Party Customer Audit: This is another type of transparency mechanism that materialises in the form of a systematic and objective evidence gathering process initiated by an independent auditor appointed by a CSC to physically appraise the CSP environment. Also, a CSP may be mutually obliged to fill-out a questionnaire and complete a detailed checklist prepared by a CSC about areas that are of concern to them.
- Security Policies: CSPs usually enforce security transparency policies that make them committed to making information available to the public upon demand. CSPs consider access to information a key component of effective participation of all CSCs. Transparency policies are often enforced through an Information Disclosure Policy, which is guided by the underlying principles of accountability and openness concerning operational programmes and customer related aspects.
- Service Level Agreements (SLAs): Another important technique for ensuring adequate disclosure of information involves the use of SLA. The SLA is a binding contract between the CSP and a customer, which specifies customer security requirements and the CSP’s commitment to fulfilling them. It clearly describes the security responsibilities and liabilities between the two parties, states the service performance and delivery, problem management, legal compliance, etc.
6. Example
6.1. Use Case Scenario
6.2. Implementation of the Security Transparency Framework
6.2.1. Actors
6.2.2. Cloud Strategy
- Goals. The company has identified some goals as the motivating factors for outsourcing to the cloud. They are: (i) cost minimization; (ii) continuous availability of the code repository and published articles; (iii) the integrity of published articles (iv) and the portability of supporting a specified number of company users to access the codes across diverse platforms.
- Cloud Readiness. Platform as-a-Service (PaaS) was identified as being suitable service offering that provides basic computing resources for users to run applications and store data relevant for Python and PHP in terms of compatibility, portability and interoperability. Cloud services could support the CSCs to avoid large capital expenditures associated with infrastructure and software license procurement, real time application support. The main aspect for selecting PaaS is the provision of development options that support the portability, interoperability and compatibility of various applications including Python and PHP. It also supports multiple platforms such as mobile and browser platforms, which serves as an advantage in achieving the company’s aspiration to support a platform for an unlimited number of researchers that can be accessed from multiple platforms.
6.2.3. Assets
| Asset Name | Category | Criticality |
|---|---|---|
| Code repository | Confidential | High |
| Online published papers | Public | High |
6.2.4. Risks
- Loss of Integrity: This refers to unauthorised changes to the source code or intellectual property of the articles either intentionally, maliciously or by accidental acts of a legitimate user.
- Loss of Availability: This arises if the mission-critical source code repository and published articles become unavailable to the target users. Other issues deal with loss of essential functionalities and operational effectiveness such as impeding the end users’ to perform their basic functions in supporting the company’s goals.
- Loss of Confidentiality: This refers to the inability of TransparentCloud to protect the data asset from unauthorised disclosure. The impact of this is jeopardising the disclosure of mission-critical tools and private data of publishers. It could result in legal action against the company, public embarrassment as well as compliance issues.
- Loss of transparency: Outsourcing the data asset means total loss of control and management of security controls. Lack of transparency and monitoring tools for security operations may hinder the company from observing internal regulatory compliance and security due diligence.
6.2.5. Requirements
| Requirements (Req.) | Controls |
|---|---|
| Req1: Secure access control, data encryption, vulnerability scans. | Data encryption and integrity checks |
| Secure access controls | |
| Vulnerability scans | |
| Req2: Disclosure of all security activities related to the data asset. | Access logs |
| Event notification | |
| Audit reports | |
| Req3: Scalability to accommodate a significant and frequency of users. | Scalable platforms |
| Req4: Backup and redundancy plans, BCP & DRP for continuous availability. | Business continuity management |
| Disaster recovery plans | |
| Backup capabilities | |
| Req5: PCI DSS, EU & UK Data Privacy Laws and ISO27001 | PCI DSS Compliance |
| EU and UK Data Privacy laws | |
| ISO27001 |
6.2.6. Controls
6.2.7. Evidences
6.2.8. Monitoring
| CSC Requirements | CSP Controls | CSP Evidences |
|---|---|---|
| Req1 | Data encryption and integrity checks | Assets are stored using Advanced Encryption Standard (AES). Customers are supported to use preferred encryption mechanisms to encrypt data before moving assets to TransparentCloud’s environment. Data integrity checks can be performed by CSCs to protect data using Hashed Message Authentication Codes (HMACs) digital signatures, and Authenticated Encryption (AES-GCM). |
| Secure access controls | Advanced data access controls provided to ensure limited access to assets. A multi-factor authentication that uses a combination of name and password credentials for access is provided as an additional layer of security using a device that generates single-use authentication code. | |
| Vulnerability scans | Regular vulnerability scans are performed on the host operating system, web applications and databases using a variety of tools. Vulnerability patches are regularly fetched from applicable vendors. The environment is regularly assessed for new and existing vulnerabilities and attack vectors by external and internal penetration testers. | |
| Req2 | Access logs | Systems are configured to log access to data assets. The access log contains details about each access request type, the requested source, the requestor’s IP, time and date of the request. |
| Notification | Event notifications relating instances are sent to customers. An email notification service is provided to notify customers when an application status changes or application servers are removed or added. | |
| Audits | An audit log service feature is maintained that provide valuable insight into who has accessed which asset. The features enable customers to directly view logs in order to verify who has accessed what data and what was done with it. Controls are put in place to support customers’ access to the audit logs for dealing with security incidents and investigations. | |
| Req3 | Scalability | Load balancers are used to distribute workloads between cloud servers with identical configuration and data. In addition, horizontal and vertical scalability are adopted to support scalability. Horizontal (out) and vertical (up) scaling are used depending on the nature of customer needs as well as resource constraints. More resources are added to the same computing pool that host customer asset through vertical scaling, such as adding more virtual CPU, RAM or disk to handle increased application workload. Also, in some cases, horizontal scaling is used to add more machines or devices to the computing platform in order to accommodate increased customer demand. |
| Req4 | Disaster recovery plan | Various techniques are used for disaster recovery. One of such involves the continuous replication of assets in order to maintain a second version of it. These replicas are transparently backed up off-site in the form of snapshots on multiple devices across multiple facilities. Availability zones are created and dispersed across multiple geographical regions and, in case of failure, automated processes divert traffic away from the affected area to another availability zone. |
| Business continuity management | Data redundancy techniques such as image and file-based backups, and automated system failover are implemented at multiple levels. It also includes redundant disks that guard against local disk failure to full data replication across geographically dispersed data centres. | |
| Data backup | Customers are allowed to perform their own backup using their own backup service provider, and they can also specify which physical region their data will be located in. | |
| Req5 | PCI DSS | Certified compliance to the standard. |
| EU & UK Privacy Laws | Received broad validation from the European and UK data protection authorities. | |
| ISO27001 | Certified compliance to the standard. |
| Target of Verification | Verifications to Perform | Means of Verification | Derived Measures | ||
|---|---|---|---|---|---|
| Base Measures Description | Reference | Frequency of Verification | Description of Mean of Verification | Description of the Verification Outcome | |
| Data encryption & integrity | Encryption & hash functions | SLA, CSP document | Periodic | Integrity-based remote data auditing | Validate the proof of data intactness in the possession of the CSP. |
| Secure access | User account authentication & authorisation | SLA, access control policy | Regularly | Automated auditing and logging reports relating to VM and service usage | Verifying legitimate users access and perform authorised changes/modifications. |
| Vulnerability scans | Internal & external security weaknesses | SLA | Regularly | Cloud security vulnerability scan reports | Address security threats and receive notifications on emerging threats that could harm assets. |
| Data backup | Backup data, policy | SLA , backup policy | Frequently | Manual review of CSP historical data backup activities and comparison of original data and backed up data. | Verify the frequency at which data is backed up. |
| PCI DSS, ISO27001 compliance | Relevant control objectives | Compliance report | Demand driven | Periodic review of compliance documents by requesting CSP certificates. | Ensuring conformance to the standards. |
6.2.9. Events
- Unauthorized access, additions, modifications or deletion of published articles.
- Unauthorized system or application activities to source code repository.
- Audit trail of authorized changes or modifications to data assets.
7. Conclusions
Acknowledgment
Author Contributions
Conflicts of Interest
References
- Agarwal, A.; Agarwal, A. The Security Risks Associated with Cloud Computing. Int. J. Comput. Appl. Eng. Sci. 2011, 1, 257–259. [Google Scholar]
- Islam, S.; Ouedraogo, M.; Kalloniatis, C.; Mouratidis, H.; Gritzalis, S. Assurance of Security and Privacy Requirements for Cloud Deployment Model SI: Security and privacy protection on cloud. IEEE Trans. Cloud Comput. 2015. [Google Scholar] [CrossRef]
- Ouedraogo, M.; Shareeful, I. Towards the integration of Security Transparency in the Modelling and Design of Cloud Based Systems. In Proceedings of the Advanced Information Systems Engineering Worships, Stockholm, Sweden, 8–12 June 2015.
- Rak, M.; Casola, V.; Beneditics, A.; Villano, U. Preliminary design of a platform-as-a-service to provide security in cloud. In Proceedings of the 4th International Conference on Cloud Computing and Services Science, Barcelona, Spain, 3–5 April 2014.
- Santos, N.; Gummadi, K.P.; Rodrigues, R. Towards Trusted Cloud Computing. In Proceedings of the 2009 Conference on Hot Topics in Cloud Computing (Hotcloud), San Diego, CA, USA, 14–19 June 2009.
- Ouedraogo, M.; Severine, M.; Herve, C.; Steven, F.; Eric, D. Security Transparency: The Next Frontier for Security Research in the Cloud. J. Cloud Comput. 2015. [Google Scholar] [CrossRef]
- Ouedraogo, M.; Dubois, E.; Khadraoui, D.; Poggi, S.; Chenal, B. Adopting an agent and event driven approach for enabling mutual auditability and security transparency in cloud based services. In Proceedings of the International Conference on Cloud Computing and Services Science, Lisbon, Portugal, 20–22 May 2015; pp. 565–572.
- Casola, V.; Benedictis, A.; Rak, M. Security monitoring in the Cloud: An SLA-based approach. In Proceedings of the 10th IEEE International Conference on Availability, Reliability and Security (ARES), Toulouse, France, 24–27 August 2015.
- Happe, J.; Theilmann, W.; Edmonds, A.; Kearney, K. A reference architecture for multi-level SLA management. In Service Level Agreements for Cloud Computing; Springer Service-Business Media: New York, NY, USA, 2011. [Google Scholar]
- Krautheim, J.F. Private Virtual Infrastructure for Cloud Computing. In Proceedings of the Hotcloud Conference 2009, San Diego, CA, USA, 14–19 June 2009.
- Theilman, W.; Yahyapour, R.; Butler, J. Multi-level SLA management for service oriented infrastructures. In Proceedings of the 1st European Conference on Towards a Service-Based Internet, Madrid, Spain, 10–13 December 2008.
- Koller, B.; Schubert, L. Towards Autonomous SLA Management using a Proxy-Like Approach. Multiagent Grid Syst. 2007, 3, 313–325. [Google Scholar]
- Cloud Security Alliance CloudAudit Security, Trust & Assurance Registry (STAR). Available online: https://cloudsecurityalliance.org/star/certification/ (accessed on 29 August 2015).
- Jaydip, S. Security and privacy issues in cloud computing. In Architectures and Protocols for Secure Information Technology; Information Science Reference: Hershey, PA, USA, 2013. [Google Scholar]
- Granados, N.; Gupta, A.; Kauffman, R. The impact of IT on Market Information and Transparency: A Unified Theoretical Framework. J. Assoc. Inf. Syst. 2006, 7, 148–178. [Google Scholar]
- Bushman, R.; Piotroski, J.; Smith, A. What Determines Corporate Transparency? J. Account. Res. 2004, 2, 207–252. [Google Scholar] [CrossRef]
- Kopits, G.; Jon, C. Transparency in Government Operation; IMF Occasional Paper, No. 158; International Monetary Fund: Washington, DC, USA, 1998. [Google Scholar]
- Andrews, S. What is Security Transparency? Available online: http://www.zdnet.com/article/what-is-security-transparency/ (accessed on 25 August 2015).
- Aslam, M. Bringing Visibility in the Clouds. Ph.D. Thesis, Swedish Institute of Computer Science, Stokholm, Sweeden, 2014. [Google Scholar]
- Kalloniatis, C.; Mouratidis, H.; Islam, S. Evaluating Cloud Deployment Scenarios Based on Security and Privacy Requirements. Requirements Eng. 2013, 18, 299–319. [Google Scholar] [CrossRef]
- Kalloniatis, C.; Mouratidis, H.; Vassilisc, M.; Islam, S.; Gritzalis, S.; Kavaklif, E. Towards the Design of Secure and Privacy-Oriented Information Systems in the Cloud: Identifying the major concepts. Comput. Stand. Interfaces 2014, 36, 759–775. [Google Scholar] [CrossRef]
- Pauley, W. Cloud Provider Transaprency: An Empirical Evaluation. IEEE Secur. Priv. 2010, 8, 32–39. [Google Scholar] [CrossRef]
- Doelitzscher, F.; Reich, C.; Knahl, M.; Clark, N. Understanding cloud audits. In Computer Communications and Networks; Springer: London, UK, 2013; Chapter Privacy and Security for Cloud Computing. [Google Scholar]
- Kosack, S.; Fung, A. Does transparency improve governance? Annu. Rev. Political Sci. 2014, 17, 65–87. [Google Scholar] [CrossRef]
- Islam, S.; Mouratidis, H.; Weippl, E. An Empirical Study on the Implementation and Evaluation of a Goal-driven Software Development Risk Management Model. J. Inf. Softw. Technol. 2014, 56, 117–133. [Google Scholar] [CrossRef]
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ismail, U.M.; Islam, S.; Ouedraogo, M.; Weippl, E. A Framework for Security Transparency in Cloud Computing. Future Internet 2016, 8, 5. https://doi.org/10.3390/fi8010005
Ismail UM, Islam S, Ouedraogo M, Weippl E. A Framework for Security Transparency in Cloud Computing. Future Internet. 2016; 8(1):5. https://doi.org/10.3390/fi8010005
Chicago/Turabian StyleIsmail, Umar Mukhtar, Shareeful Islam, Moussa Ouedraogo, and Edgar Weippl. 2016. "A Framework for Security Transparency in Cloud Computing" Future Internet 8, no. 1: 5. https://doi.org/10.3390/fi8010005
APA StyleIsmail, U. M., Islam, S., Ouedraogo, M., & Weippl, E. (2016). A Framework for Security Transparency in Cloud Computing. Future Internet, 8(1), 5. https://doi.org/10.3390/fi8010005








