Future Research on Cyber-Physical Emergency Management Systems
Abstract
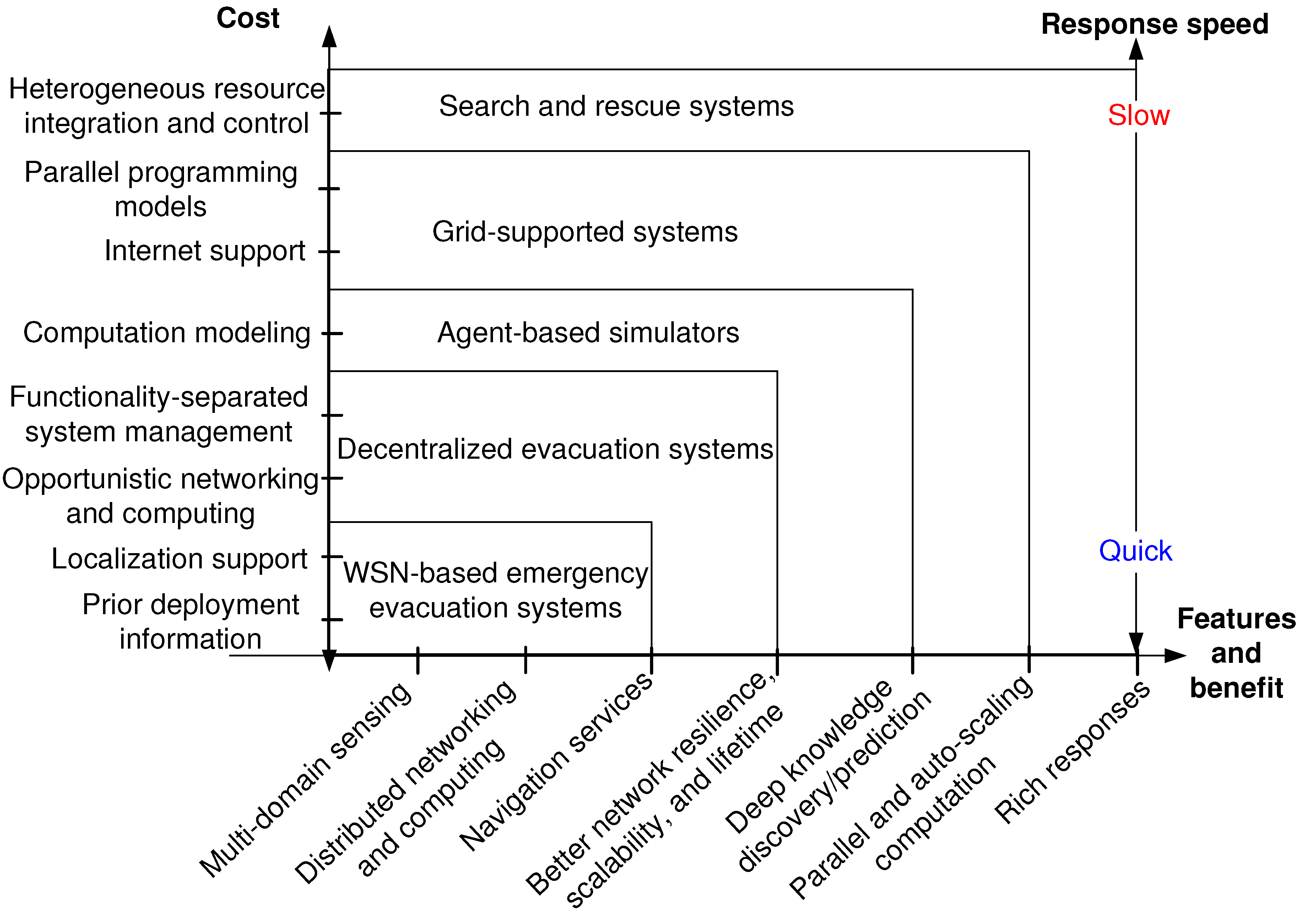
:1. Introduction and Overall Vision
2. Technically Challenging Areas
- Communication issues: many-to-many information flow [12,13,14,15,16,17,18,19,20,21,22,23] and opportunistic connection [24] are inevitable in emergencies. Considering a fire emergency, to find safe paths, sensing information may need to be conveyed from many sensors to many mobile evacuees. This will obviously be more difficult, since communications may break down and evacuees will move to escape. In addition, query-and-reply communications may also proceed between different groups of people, e.g., first responders, evacuees, members of the press and robots. In these cases, typical communication protocols, such as broadcast, convergecast, unicast, and multicast, may be not able to deal with these diverse communication requirements.
- Information acquirement and dissemination: cross-domain sensing [25,26,27] and heterogeneous information flow [28,29,30] are inherent features in an emergency response system. To guarantee the safety of people, information in different domains must be acquired (e.g., ultrasonic sensors for localizing people, temperature and gas sensors for identifying hazards, camera sensors for counting civilians and life detectors for searching civilians). Moreover, sensors are no longer the only information contributors, and in situ interactions between sensors, actuators, people, objects and events will also be involved to disseminate and contribute high-level information. These features will raise a challenge to acquire and disseminate information in an efficient way.
- Knowledge discovery: partial information and dynamic changes are inherent in an emergency. In such a rough environment, feasible and quick response must rely on data analysis technologies to extract knowledge from sensing data (e.g., counting, discovery, localization and tracking of civilians) [30,31,32,33,34,35,36,37,38]. Moreover, dynamic prediction and forecast of environmental changes should be conducted to avoid unnecessary casualties [20,21,39,40,41,42,43,44].
- Resource allocation and management: limited resources make timely response more difficult. Unlike other sensor-aided applications, the needs of intelligent actuation, scheduling and efficient resource allocation will increase in emergency response systems. Intelligent scheduling is needed to select the best action, while scarce resources must be allocated efficiently to perform actions [45,46,47,48,49,50].
- Heterogeneous system integration and asynchronous control: multi-domain technologies will be needed to enhance the capability and diversity of emergency response [26,27,30,38]. Furthermore, functionality separated tasks, such as sensing, storage, computation and decision-making, need to be conducted by independent functional units, so as to facilitate the integrated asynchronous control of multiple technologies. To achieve this goal, parallel and virtualisation technologies (e.g., grid or cloud computing) may steer the emergency response systems toward functionality-separated approaches for resource scaling, fault-tolerance and computation speed-up [25]. For instance, in an outdoor city-wide environment, large numbers of civilians may be tracked, and massive sensing information can only be stored and computed rapidly by a powerful resource pool.
- Comparison with military systems: the objective of search and rescue systems is emergency response, but military systems focus on extensive simulations for tactical planning and decision. A search and rescue system usually consists of heterogeneous nodes, while a military system is a collection of mission-oriented sub-systems with resources and capabilities that provide complex functionalities that are far more than the sum of constituent systems. A search and rescue system is usually deployed over a smaller space, while a military system emphasises value-added functionalities that usually leave more time for decision-making and resource deployment, while an emergency system must offer an urgent life-critical response. Search and rescue systems may typically also use more limited communications and sensing than the global assets that military systems typically have, such as satellite communications and wide-band radar sensing.
3. Characteristics of Existing Evacuation Systems
| functionalities | reference |
|---|---|
| Localization/tracking of civilians | [30,34,35,36,37] |
| Reduction of search/rescue space | [38] |
| Communications with civilians | [26,27,32,33] |
| Assessment of civilians status | [31] |
| Optimization of search/rescue cost | [45,46,47,48,49,50] |
| Technologies/system type | Indoor evacuation and rescue systems | Outdoor evacuation and rescue systems |
|---|---|---|
| Communications and networking | ZigBee, WiFi, Bluetooth, 3G, wired networks | WiFi, 3G, wired networks |
| Information acquirement and dissemination | clients and dissemination | crowdsourcing information |
| Knowledge discovery | RFID, RF or sensor-based positioning | GPS, WiFi, GSM positioning |
| Decentralized predication | Centralized prediction | |
| Resource allocation and management | Localized dispatching | Centralized allocation |
| Heterogeneous system integration | Distributed | Centralized |
| and asynchronous control | ||
| Existing technologies | [12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,31,32,33,34,35,36,37,39,41,42,45,46,47,48,49,50] | [30,35,38,40,43,44,50] |
4. Evolution towards Greater Complexity
5. Emerging Challenges and Opportunities
| Technical scope | Advantage | Disadvantage | Open research problems |
|---|---|---|---|
| Network integration | • interoperability with wireless sensor networks (WSNs) | •integration via gateway nodes | • seamless OppNets
• networking virtualisation |
| • compliance with networking standardds | • knowledge-centric networks | ||
| Security and privacy | • proximity-based authentication | • device-level sharing | • security of opportunistic communications |
| • pull-based service content | • only system-defined privacy | • privacy-preservation knowledge inferences | |
| • separate private data sets | • divulgence of privacy by inference | • trust, security, and privacy in mobile systems | |
| Mobile sensing systems and Cloud-enabled | • knowledge from the wisdom of crowds | • simple activity inferences | • participatory and collaborative sensing models
• energy management of mobile devices |
| decision systems | • scalable sensing/decision-making model | • one-way knowledge flow | • QoS-guaranteed cloud and big data in cloud
• load-balancing simulation models |
| • optimization of task migration |
5.1. Network Integration
5.2. Security and Privacy
5.3. Mobile Sensing and Cloud-Enabled Decisions
6. Areas for Future Work
References
- Hu, F.; Xiao, Y.; Hao, Q. Congestion-aware, loss-resilient bio-monitoring sensor networking for mobile health applications. IEEE J. Sel. Areas Commun. 2009, 27, 450–465. [Google Scholar] [CrossRef]
- Terrestrial Ecology Observing Systems, Center for Embedded Networked Sensing. Available online: http://research.cens.ucla.edu/ (accessed on 19 June 2013).
- Liu, H.; Wan, P.; Jia, X. Maximal lifetime scheduling for sensor surveillance systems with K sensors to one target. IEEE Trans. Parallel Distrib. Syst. 2006, 17, 1526–1536. [Google Scholar] [CrossRef]
- Tubaishat, M.; Zhuang, P.; Qi, Q.; Shang, Y. Wireless sensor networks in intelligent transportation systems. Wirel. Commun. Mob. Comput. 2009, 9, 287–302. [Google Scholar] [CrossRef]
- Malan, D.J.; Fulford-Jones, T.R.; Nawoj, A.; Clavel, A.; Shnayder, V.; Mainland, G.; Welsh, M.; Moulton, S. Sensor networks for emergency response: Challenges and opportunities. IEEE Pervasive Comput. 2004, 3, 16–23. [Google Scholar]
- Gelenbe, E.; Cao, Y. Autonomous search for mines. Eur. J. Oper. Res. 1998, 108, 319–333. [Google Scholar] [CrossRef]
- Gelenbe, E.; Koçak, T. Area-based results for mine detection. Geosci. Remote Sens. IEEE Trans. 2000, 38, 12–24. [Google Scholar] [CrossRef]
- Chen, P.Y.; Chen, W.T.; Tseng, Y.C.; Huang, C.F. Providing group tour guide by RFIDs and wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1536–1276. [Google Scholar]
- Fischer, C.; Gellersen, H. Location and navigation support for emergency responders: A survey. IEEE Pervasive Comput. 2009, 9, 38–47. [Google Scholar] [CrossRef]
- Gelenbe, E.; Wu, F.J. Large scale simulation for human evacuation and rescue. Comput. Math. Appl. 2012, 64, 3869–3880. [Google Scholar] [CrossRef]
- Abdelrahman, O.H.; Gelenbe, E. Time and energy in team-based search. Phys. Rev. E 2013, 87, 032125:1–032125:6. [Google Scholar] [CrossRef]
- Li, Q.; Rosa, M.D.; Rus, D. Distributed Algorithms for Guiding Navigation across a Sensor Network. In Proceedings of the ACM International Conference Mobile Computing and Networking, San Diego, CA, USA, 14–19 September 2003; pp. 313–325.
- Tseng, Y.C.; Pan, M.S.; Tsai, Y.Y. Wireless sensor networks for emergency navigation. IEEE Comput. 2006, 39, 55–62. [Google Scholar] [CrossRef]
- Pan, M.S.; Tsai, C.H.; Tseng, Y.C. Emergency guiding and monitoring applications in indoor 3D environments by wireless sensor networks. Int. J. Sens. Netw. 2006, 1, 2–10. [Google Scholar] [CrossRef]
- Chen, D.; Mohan, C.K.; Mehrotra, K.G.; Varshney, P.K. Distributed in-network path planning for sensor network navigation in dynamic hazardous environments. Wirel. Commun. Mob. Comput. 2010, 12, 739–754. [Google Scholar] [CrossRef]
- Chen, W.T.; Chen, P.Y.; Wu, C.H.; Huang, C.F. A Load-Balanced Guiding Navigation Protocol in Wireless Sensor Networks. In Proceedings of the IEEE Global Telecommunication Conference, New Orleans, LA, USA, 30 November–4 December 2008; pp. 1–6.
- Chen, P.Y.; Kao, Z.F.; Chen, W.T.; Lin, C.H. A Distributed Flow-Based Guiding Navigation Protocol in Wireless Sensor Networks. In Proceedings of the International Conference Parallel Processing, Taipei, Taiwan, 13–16 September 2011; pp. 105–114.
- Chen, P.Y.; Chen, W.T.; Shen, Y.T. A Distributed Area-based Guiding Navigation Protocol for Wireless Sensor Networks. In Proceedings of the IEEE International Conference Parallel and Distributed Systems, Melbourne, Victoria, Australia, 8–10 December 2008; pp. 647–654.
- Li, M.; Liu, Y.; Wang, J.; Yang, Z. Sensor Network Navigation without Locations. In Proceedings of the IEEE INFOCOM, Rio de Janeiro, Brazil, 19–25 April 2009; pp. 2419–2427.
- Barnes, M.; Leather, H.; Arvind, D.K. Emergency Evacuation using Wireless Sensor Networks. In Proceedings of the IEEE Conference Local Computer Networks, Clontarf Castle, Dublin, Ireland, 15–18 October 2007; pp. 851–857.
- Cherniak, A.; Zadorozhny, V. Towards Adaptive Sensor Data Management for Distributed Fire Evacuation Infrastructure. In Proceedings of the International Conference Mobile Data Management, Kansas City, MO, USA, 23–26 May 2010; pp. 151–156.
- Filippoupolitis, A.; Gelenbe, E. A Distributed Decision Support System for Building Evacuation. In Proceedings of the IEEE International Conference Human System Interaction, Catania, Italy, 21–23 May 2009; pp. 320–327.
- Filippoupolitis, A.; Gelenbe, E. An emergency response system for intelligent buildings. Sustain. Energy Build. 2011, 12, 265–274. [Google Scholar]
- Gorbil, G.; Gelenbe, E. Opportunistic Communications for Emergency Support Systems. In Proceedings of the International Conference Ambient Systems, Networks and Technologies, Niagara Falls, Ontario, Canada, 19–21 September 2011; pp. 1–9.
- Han, L.; Potter, S.; Beckett, G.; Pringle, G.; Welch, S.; Koo, S.H.; Wickler, G.; Usmani, A.; Torero, J.L.; Tate, A. FireGrid: An e-infrastructure for next-generation emergency response support. J. Parallel Distrib. Comput. 2010, 70, 1128–1141. [Google Scholar] [CrossRef]
- Kim, Y.D.; Kim, Y.G.; Lee, S.H.; Kang, J.H.; An, J. Portable Fire Evacuation Guide Robot System. In Proceedings of the IEEE/RSJ International Conference Intelligent Robots and Systems, St. Louis, MO, USA, 11–15 October 2009; pp. 2789–2794.
- Kantor, G.; Singh, S.; Peterson, R.; Rus, D.; Das, A.; Kumar, V.; Pereira, G.; Spletzer, J. Distributed search and rescue with robot and sensor teams. Field Serv. Robot. 2006, 24, 529–538. [Google Scholar]
- Gorbil, G.; Filippoupolitis, A.; Gelenbe, E. Intelligent Navigation Systems for Building Evacuation. In Proceedings of International Symposium on Computer and Information Sciences, London, UK, 26–28 September 2011; pp. 339–345.
- Inoue, Y.; Sashima, A.; Ikeda, T.; Kurumatani, K. Indoor Emergency Evacuation Service on Autonomous Navigation System using Mobile Phone. In Proceedings of the International Symposium Universal Communication, Osaka, Japan, 15–16 December 2008; pp. 79–85.
- Ko, A.; Lau, H.Y.K. Robot assisted emergency search and rescue system with a wireless sensor network. Int. J. Adv. Sci. Technol. 2009, 3, 69–78. [Google Scholar]
- Guo, S.; He, T.; Mokbel, M.F.; Stankovict, J.A.; Abdelzaher, T.F. On Accurate and Efficient Statistical Counting in Sensor-based Surveillance Systems. In Proceedings of the IEEE International Conference Mobile Ad Hoc and Sensor Systems, Atlanta, GA, USA, 29 September–2 October 2008; pp. 24–35.
- Loukas, G.; Timotheou, S.; Gelenbe, E. Robotic Wireless Network Connection of Civilians for Emergency Response Operations. In Proceedings of the International Symposium Computer and Information Sciences, Istanbul, Turkey, 27–29 October 2008; pp. 1–6.
- Timotheou, S.; Loukas, G. Autonomous Networked Robots for the Establishment of Wireless Communication in Uncertain Emergency Response Scenarios. In Proceedings of the ACM Symposium on Applied Computing, Honolulu, HI, USA, 08–12 March 2009; pp. 1171–1175.
- Reich, J.; Sklar, E. Robot-Sensor Networks for Search and Rescue. In Proceedings of the IEEE International Workshop Safety, Security and Rescue Robotics, Gaithersburg, MD, USA, 22–25 August 2006.
- Summit Safety. Available online: http://www.summitsafetyinc.com/ (accessed on 6 February 2009).
- Wilson, J.; Bhargava, V.; Redfern, A.; Wright, P. A Wireless Sensor Network and Incident Command Interface for Urban Firefighting. In Proceedings of the International Conference Mobile and Ubiquitous Systems: Computing, Networking and Services, Philadelphia, PA, USA, 6–10 August 2007; pp. 1–7.
- Klann, M. Tactical navigation support for firefighters: The LifeNet ad-hoc sensor-network and wearable system. Mob. Response 2009, 5424, 41–56. [Google Scholar]
- Huang, J.H.; Amjad, S.; Mishra, S. CenWits: A Sensor-Based Loosely Coupled Search and Rescue System Using Witnesses. In Proceedings of the ACM International Conference Embedded Networked Sensor Systems, San Diego, CA, USA, 2–4 November 2005; pp. 180–191.
- Filippoupolitis, A.; Hey, L.; Loukas, G.; Gelenbe, E.; Timotheou, S. Emergency Response Simulation Using Wireless Sensor Networks. In Proceedings of the International Conference Ambient Media and Systems, Athens, Greece, 15 March 2008; pp. 21:1–21:7.
- Schurr, N.; Marecki, J.; Tambe, M.; Scerri, P.; Kasinadhuni, N.; Lewis, J. The Future of Disaster Response: Humans Working with Multiagent Teams using DEFACTO. In Proceedings of the AAAI Spring Symposium AI Technologies for Homeland Security, Stanford, CA, USA, 21–23 March 2005.
- Liu, K.; Shen, X.; Saddik, A.E.; Boukerche, A.; Georganas, N.D. SimSITE: The HLA/RTI Based Emergency Preparedness and Response Training Simulation. In Proceedings of the IEEE Symposium Distributed Simulation and Real-Time Applications, Chania, Greece, 22–24 October 2007; pp. 59–63.
- Dimakis, N.; Filippoupolitis, A.; Gelenbe, E. Distributed building evacuation simulator for smart emergency management. Comput. J. 2010, 53, 1384–1400. [Google Scholar] [CrossRef]
- Nakajima, Y.; Shiina, H.; Yamane, S.; Ishida, T. Disaster Evacuation Guide: Using a Massively Multiagent Server and GPS Mobile Phones. In Proceedings of the IEEE International Symposium Applications and the Internet, Hiroshima, Japan, 15–19 January 2007.
- Bo, Y.; Yong-gang, W.; Cheng, W. A Multi-agent and GIS Based Simulation for Emergency Evacuation in Park and Public Square. In Proceedings of the International Conference Computational Intelligence and Security, Beijing, China, 11–14 December 2009; pp. 211–216.
- Verma, A.; Sawant, H.; Tan, J. Selection and navigation of mobile sensor nodes using a sensor network. Pervasive Mob. Comput. 2006, 2, 65–84. [Google Scholar] [CrossRef]
- Stojmenovic, I.; Liu, D.; Jia., X. A scalable quorum based location service in ad hoc and sensor networks. Int. J. Commun. Netw. Distr. Syst. 2008, 1, 71–94. [Google Scholar] [CrossRef]
- Li, X.; Santoro, N.; Stojmenovic, I. Localized distance-sensitive service discovery in wireless sensor and actor networks. IEEE Trans. Comput. 2009, 58, 1275–1288. [Google Scholar]
- Wang, Y.C.; Peng, W.C.; Chang, M.H.; Tseng, Y.C. Exploring Load-Balance to Dispatch Mobile Sensors in Wireless Sensor Networks. In Proceedings of the IEEE International Conference Computer Communication and Networks, Honolulu, HI, USA, 13–16 August 2007; pp. 669–674.
- Li, S.; Zhan, A.; Wu, X.; Yang, P.; Chen, G. Efficient emergency rescue navigation with wireless sensor networks. J. Inf. Sci. Eng. 2011, 27, 51–64. [Google Scholar]
- Gelenbe, E.; Timotheou, S.; Nicholson, D. Fast distributed near-optimum assignment of assets to tasks. Comput. J. 2010, 53, 1360–1369. [Google Scholar] [CrossRef]
- Gelenbe, E. Search in unknown random environments. Phys. Rev. E 2010, 82, 061112. [Google Scholar] [CrossRef]
- Gelenbe, E.; Hey, L. Quality of Information: An Emprical Approach. In Proceedings of the 5th IEEE International Conference on Mobile Ad-Hoc and Sensor Systems, Atlanta, Georgia, USA, 29 September–2 October 2008; pp. 730–735.
- Gelenbe, E.; Loukas, G. A self-aware approach to denial of service defence. Comput. Netw. 2007, 51, 1299–1314. [Google Scholar] [CrossRef]
- Tseng, Y.C.; Wu, F.J.; Lai, W.T. Opportunistic data collection for disconnected wireless sensor networks by mobile mules. Ad Hoc Netw. 2013, 11, 1150–1164. [Google Scholar] [CrossRef]
- Gelenbe, E.; Fourneau, J.M. Random neural networks with multiple classes of signals. Neural Comput. 1999, 11, 953–963. [Google Scholar] [CrossRef] [PubMed]
- Gelenbe, E.; Hussain, K.; Kaptan, V. Simulating autonomous agents in augmented reality. J. Syst. Softw. 2005, 74, 255–268. [Google Scholar] [CrossRef]
- Gorbil, G.; Gelenbe, E. Resilience and Security of Opportunistic Communications for Emergency Evacuation. In Proceedings of the ACM Workshop on Performance Monitoring and Measurement of Heterogeneous Wireless and Wired Networks, Paphos, Cyprus, 21–25 October 2012; pp. 115–124.
- Gelenbe, E. Natural computation. Comput. J. 2012, 55, 848–851. [Google Scholar] [CrossRef]
- Sheng, X.; Tang, J.; Zhang, W. Energy-Efficient Collaborative Sensing with Mobile Phones. In Proceedings of the IEEE INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 1916–1924.
- Gelenbe, E.; Hébrail, G. A Probability Model of Uncertainty in Databases. In Proceedings of the ICDE. IEEE Computer Society, Los Angeles, CA, USA, 5–7 February 1986; pp. 328–333.
- Gelenbe, E.; Muntz, R.R. Probabilistic models of computer systems: Part I (exact results). Acta Inform. 1976, 7, 35–60. [Google Scholar] [CrossRef]
- Gelenbe, E. Probabilistic models of computer systems Part II: Diffusion approximations, waiting times and batch arrivals. Acta Inform. 1979, 12, 285–303. [Google Scholar] [CrossRef]
- Smith, J.M. State-dependent queueing models in emergency evacuation networks. Transp. Res. Part B: Methodol. 1991, 25, 373–389. [Google Scholar] [CrossRef]
- Desmet, A.; Gelenbe, E. Graph and Analytical Models for Emergency Evacuation. In Proceedings of IEEE PerCom 2013, PERNEM 2013 Workshop, San Diego, CA, USA, 22 March 2013.
- Desmet, A.; Gelenbe, E. Graph and analytical models for emergency evacuation. Future Internet 2013, 5, 46–55. [Google Scholar] [CrossRef]
- Aguilar, J.; Gelenbe, E. Task assignment and transaction clustering heuristics for distributed systems. Inf. Sci. 1997, 97, 199–219. [Google Scholar] [CrossRef]
- Tinyos. Available online: http://www.tinyos.net/ (accessed on 01 December 2005).
- Dunkels, A. Full TCP/IP for 8-bit Architectures. In Proceedings of the ACM International Conference on Mobile Systems, Applications, and Services, San Francisco, CA, USA, 5–8 May 2003; pp. 85–98.
- Montenegro, G.; Kushalnagar, N.; Hui, J.; Culler, D. Transmission of IPv6 packets over IEEE 802.15.4 networks. REC 4944 (Proposed Standard). 2007. [Google Scholar]
- Hui, J.W.; Culler, D.E. IP is Dead, Long Live IP for Wireless Sensor Networks. In Proceedings of the ACM International Conference Embedded Networked Sensor Systems, Raleigh, NC, USA, 5–7 November 2008; pp. 15–28.
- Wi-Fi Direct. Available online: http://www.wi-fi.org/discover-and-learn/wi-fi-direct (accessed on 01 March 2000).
- Hauer, J.H.; Handziski, V.; Wolisz, A. Experimental Study of the Impact of WLAN Interference on IEEE 802.15.4 Body Area Networks. In Proceedings of the IEEE European Workshop Sensor Networks, Cork, Ireland, 11–13 February 2009; pp. 17–32.
- Musaloiu, E.R.; Terzis, A. Minimising the effect of WiFi interference in 802.15.4 wireless sensor networks. Int. J. Sens. Netw. 2007, 3, 43–54. [Google Scholar]
- Kim, T.H.; Ha, J.Y.; Choi, S.; Kwon, W.H. Virtual channel management for densely deployed IEEE 802.15.4 LR-WPANs. In Proceedings of the IEEE Conference on Pervasive Computing and Communications, Pisa, Italy, 13–17 March 2006; pp. 103–115.
- Won, C.; Youn, J.H.; Ali, H.; Sharif, H.; Deogun, J. Adaptive Radio Channel Allocation for Supporting Coexistence of 802.15.4 and 802.11b. In Proceedings of the IEEE Vehicular Technology Conference, Dallas, TX, USA, 25–28 September 2005; pp. 2522–2526.
- Liang, C.J.M.; Priyantha, N.B.; Liu, J.; Terzis, A. Surviving Wi-Fi Interference in Low Power ZigBee Networks. In Proceedings of the ACM International Conference Embedded Networked Sensor Systems, Zurich, Switzerland, 3–5 November 2010; pp. 309–322.
- Nguyen, N.P.; Dinh, T.N.; Tokala, S.; Thai, M.T. Overlapping Communities in Dynamic Networks: Their Detection and Mobile Applications. In Proceedings of the ACM International Conference Mobile Computing and Networking, Las Vegas, NV, USA, 19–23 September 2011; pp. 85–96.
- Song, Y.; Wong, S.H.; Lee, K.W. Optimal Gateway Selection in Multi-Domain Wireless Networks: A Potential Game Perspective. In Proceedings of the ACM International Conference Mobile Computing and Networking, Las Vegas, NV, USA, 19–23 September 2011; pp. 325–336.
- Mayrhofer, R.; Gellersen, H. Shake well before use: Intuitive and secure pairing of mobile devices. IEEE Trans. Mob. Comput. 2009, 8, 792–806. [Google Scholar] [CrossRef]
- Mathur, S.; Miller, R.; Varshavsky, A.; Trappe, W.; Mandayam, N. ProxiMate: Proximity-Based Secure Pairing using Ambient Wireless Signals. In Proceedings of the ACM International Conference on Mobile Systems, Applications, and Services, Washington, DC, USA, 28 June–1 July 2011; pp. 211–224.
- Yang, Y.; Zhang, Y. A Generic Scheme for Secure Data Sharing in Cloud. In Proceedings of the International Conference Parallel Processing Workshops, Taipei, Taiwan, 13–16 September 2011; pp. 145–153.
- Chen, S.; Nepal, S.; Liu, R. Secure Connectivity for Intra-Cloud and Inter-Cloud Communication. In Proceedings of the International Conference Parallel Processing Workshops, Taipei, Taiwan, 13–16 September 2011; pp. 154–159.
- Amini, S.; Lindqvist, J.; Hong, J.; Lin, J.; Toch, E.; Sadeh, N. Caché: Caching Location-Enhanced Content to Improve User Privacy. In Proceedings of the ACM International Conference on Mobile Systems, Applications, and Services, Washington, DC, USA, 28 June–1 July 2011; pp. 197–210.
- Amazon SimpleDB. Available online: http://aws.amazon.com/simpledb/ (accessed on 27 December 2007).
- Chen, Y.J.; Wang, L.C. A Security Framework of Group Location-Based Mobile Applications in Cloud Computing. In Proceedings of the International Conference Parallel Processing Workshops, Taipei, Taiwan, 13–16 September 2011; pp. 184–190.
- Chittaro, L.; Nadalutti, D. Presenting Evacuation Instructions on Mobile Devices by Means of Location-Aware 3D Virtual Environments. In Proceedings of the International Conference Human-Computer Interaction with Mobile Devices and Services, New York, NY, USA, 2–5 September 2008; pp. 395–398.
- Ahn, J.; Han, R. RescueMe: An Indoor Mobile Augmented-Reality Evacuation System by Personalized Pedometry. In Proceedings of the IEEE Asia-Pacific Services Computing Conference, Jeju, Korea, 12–15 December 2011; pp. 70–77.
- Stranders, R.; Ramchurn, S.D.; Shi, B.; Jennings, N.R. CollabMap: Augmenting maps using the wisdom of crowds. In Proceedings of the AAAI Workshop on Human Computation, San Francisco, CA, USA, 8 August 2011; pp. 111–112.
- Haiti-Ushahidi. Available online: http://haiti.ushahidi.com/ (accessed on 12 February 2010).
- Chu, L.; Wu, S.J. A Real-Time Decision Support with Cloud Computing Based Fire Evacuation System. In Proceedings of the North-East Asia Symposium on Nano, Information Technology and Reliability, Macao, China, 24–26 October 2011; pp. 45–48.
- Alazawi, Z.; Altowaijri, S.; Mehmood, R.; Abdljabar, M.B. Intelligent Disaster Management System Based on Cloud-Enabled Vehicular Networks. In Proceedings of the International Conference on ITS Telecommunications, Saint-Petersburg, Russia, 23–25 August 2011; pp. 361–368.
- Li, J.; Li, Q.; Khan, S.U.; Ghani, N. Community-Based Cloud for Emergency Management. In Proceedings of the International Conference on System of Systems Engineering, Albuquerque, NM, USA, 27–30 June 2011; pp. 55–60.
- Yang, C.; Yen, C.; Tan, C.; Madden, S.R. Osprey: Implementing MapReduce-Style Fault Tolerance in a Shared-Nothing Distributed Database. In Proceedings of the International Conference Data Engineering, Long Beach, CA, USA, 1–6 March 2010; pp. 657–668.
- Geng, Y.; Chen, S.; Wu, Y.; Wu, R.; Yang, G.; Zheng, W. Location-Aware MapReduce in Virtual Cloud. In Proceedings of the International Conference Parallel Processing, Taipei, Taiwan, 13–16 September 2011; pp. 275–284.
- Sonnek, J.; Greensky, J.; Reutiman, R.; Chandra, A. Starling: Minimizing Communication Overhead in Virtualized Computing Platforms Using Decentralized Affinity-Aware Migration. In Proceedings of the International Conference Parallel Processing, San Diego, CA, USA, 13–16 September 2010; pp. 228–237.
- Calheiros, R.N.; Ranjany, R.; Buyya, R. Virtual Machine Provisioning Based on Analytical Performance and QoS in Cloud Computing Environments. In Proceedings of the International Conference Parallel Processing, Taipei, Taiwan, 13–16 September 2011; pp. 295–304.
- Gelenbe, E.; Sevcik, K.C. Analysis of update synchronisation algorithms for multiple copy data bases. IEEE Trans. Comput. 1979, C-28, 737–747. [Google Scholar] [CrossRef]
- Gelenbe, E.; Stafylopatis, A. Global behaviour of homogeneous random neural systems. Appl. Math. Modell. 1991, 15, 534–541. [Google Scholar] [CrossRef]
© 2013 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Gelenbe, E.; Wu, F.-J. Future Research on Cyber-Physical Emergency Management Systems. Future Internet 2013, 5, 336-354. https://doi.org/10.3390/fi5030336
Gelenbe E, Wu F-J. Future Research on Cyber-Physical Emergency Management Systems. Future Internet. 2013; 5(3):336-354. https://doi.org/10.3390/fi5030336
Chicago/Turabian StyleGelenbe, Erol, and Fang-Jing Wu. 2013. "Future Research on Cyber-Physical Emergency Management Systems" Future Internet 5, no. 3: 336-354. https://doi.org/10.3390/fi5030336
APA StyleGelenbe, E., & Wu, F.-J. (2013). Future Research on Cyber-Physical Emergency Management Systems. Future Internet, 5(3), 336-354. https://doi.org/10.3390/fi5030336





