e-Health Cloud: Opportunities and Challenges
Abstract
:1. Introduction
2. e-Health Cloud Opportunities
- (a) High cost of implementing and maintaining HIT: the cost of HIT requires investments in software, hardware, technical infrastructure, IT professionals, and training. This can result in a considerable cost to healthcare organizations in particular for the medium and small sized entities. HIT implementations can be time consuming and stressful for the already stressed healthcare organizations due to demands on healthcare professionals who have to share project responsibilities with their patient care duties. Finally, HIT requires dedicated teams and proper funding to handle day to day management and maintenance.
- (b) Fragmentation of HIT and insufficient exchange of patient data: HIT in most cases exists as separate small clinical or administrative systems within different departments of the healthcare provider’s organization. Therefore, the patients’ data exist in a dispersed state where certain portions of this data are restricted within separate departmental systems, certain clinics or areas of the healthcare organization. Such dispersed pockets of data make it challenging to bring information together and share it across the organization or across different healthcare providers.
- (c) Lack of regulations/laws mandating the use and protection of electronic health care data capture and communication: currently, there are no well established laws or regulations mandating the electronic capture of patient data in addition to law covering issues of protection and security of this data. For example, there is no general law protecting the privacy of patients and the interchanges of their medical data between countries [23]. The data protection standards and regulations are at different levels across countries; for example, the directive on privacy and electronic communications in Europe [24] protects the personal information of patients while the Health Insurance Portability and Accountability Act (HIPPA) and Subtitle D of the HIT for Economic and Clinical Health (HITECH) Act in the United State [25] enforces privacy and security standards for organizations covered by HIPPA.
- (d) Lack of e-Health Cloud design and development standards: There are no well established standards available for healthcare providers to use to design and build their systems. This would include definitions of data types, forms and at times frequency of data capture in addition to defining how the data is obtained, stored, used and protected. One of the biggest challenges in the area of e-health standardization is the production of multitudinous e-health standards (e.g., DICOM, ISO/TC 215, HL7, etc.) developed by numerous standardization bodies (e.g., NEMA, ISO, etc.). Many of these are not interoperable or not directly coordinated with each other at an organizational level. More about existing e-health standards is available in the ITU-T technology Watch Report, 2011 in [26].
- Better patient care: the ability to offer a unified patient medical record containing patient data from all patient encounters across all operators. These records will be available anywhere and anytime allowing healthcare providers to have a comprehensive view of the patient’s history and provide the most suitable treatments accordingly.
- Reduced cost: the ability to take advantage of the capabilities of CC and create a collaborative economic environment where the overhead costs are shared among the participants; with the flexibility to only pay for actual resource utilization. This feature is very suitable for small and medium sized healthcare providers where they can utilize advanced IT infrastructures and services to support their healthcare operations without facing high initial and operational costs. Another cost reduction aspect is the savings gained from making medical records available globally, thus there are no costs incurred in exchanging and sharing patients’ data around the world.
- Solve the issue of resources scarcity: the ability to overcome shortages issues in terms of IT infrastructures and health care professionals. This is very important in some areas (such as remote rural communities) with the shortage in primary healthcare facilities [27]. The Cloud enables healthcare providers to use remote medical services and data that help in providing primary healthcare in such areas. It also allows various health care specialists to offer their services remotely thus saving time and effort and reducing the need to have experts available everywhere.
- Better quality: the health care operators by having their clinical data stored in the cloud will facilitate supplying concerned entities such as the Ministry of Health or the World Health Organization with information on patient safety and the quality of care provided. The information will be attained by one of two methods; (1) aggregating existing data to arrive at the indicators requested and/or (2) providing on-line ability for health care operators to enter/access data directly. Health care data stored on the Cloud can be aggregated and reported along the lines of generally accepted health care quality indicators such as ones published by the Agency for Healthcare Research and Quality (AHRQ) [28]. AHRQ quality indicators are accepted worldwide and many health care operators use these indicators as measures of performance. For example, the US government will be rewarding US health care operators in 2012 on their ability to meet quality indicators by increasing the payouts they receive from it. This measure was a byproduct of the American Recovery and Reinvestment Act signed by President Barack H. Obama in 2009 [29]. Quality indicators can includes infection rates, lengths of stay and readmission percentages. The other method to collect indicators is for the Cloud owner to provide an on-line tool for health care operators to report incidents such as sentinel events or adverse drug reactions. Such data is important and sometimes it may not be available in the operational data that the operators send to the Cloud, hence creating the need to setup specialized tools to gather it and make it available.
- Support research: the e-Health Cloud can offer an integrated platform to host a huge information repository about millions of patients’ cases which can be uniformly and globally accessed. This integrated platform can be easily utilized to develop data mining models to discover new medical facts and to conduct medical research to enhance medications, treatments and healthcare services.
- Support national security: the e-Health Cloud can increase the ability to monitor the spread of infectious diseases and/or other disease outbreaks. The Cloud can be serviced as an alert system for monitoring the diffusion of any dangerous infectious diseases as well as it can be used to determine the infection areas, the spreading patterns and hopefully the reasons of the outbreaks.
- Support strategic planning: decision makers can use the e-Health Cloud data for planning and budgeting for healthcare services. It can also be integrated with other Cloud services to help in forecasting future healthcare services needs. This will help for example in planning the needs for doctors, medical labs and equipments, operating rooms, patient beds, and other medical facilities.
- Support financial operations: the ability to streamline financial operations as the Cloud can act as a broker between healthcare providers and healthcare payers. The billing, settlements, and approval processes can be automated and integrated among both parties.
- Facilitate clinical trials: the data stored allow the Cloud owner to partner with pharmaceutical companies and medical research institutions for clinical trials for new medicines. As data is collected in an integrated fashion, it is easy to detect the availability of special patients’ cases and provide appropriate pools of trial cases.
- Facilitate forming registries: the data shared will allow for the formation of specialized registries targeted for specific types of patients such as cancer and diabetes registries.
- Data security risks: as in accessing patient data by unauthorized users. Many Cloud services offer some security measures. For example, Today’s systems in particular HIPAA compliant health care systems—have the ability to record every access attempt by user names and to include date, time as well as relationship to the patient. However, more work is to be done to enhance security and more importantly increase the users’ trust levels of these security measures.
- The risk of loss of data: Although it is a significant issue, advancements in database management systems such as Oracle, Cache’ and SQL have created concepts of hot and cold backups, mirroring and data base restores to provide efficient solutions that minimizes this risk. Not to mention, off site backups and disaster recovery sites.
- The risk of systems unavailability: losing an e-Health service could be a major issue especially in an emergency situation. However, advancements in the science of business continuity have increased systems reliability and availability.
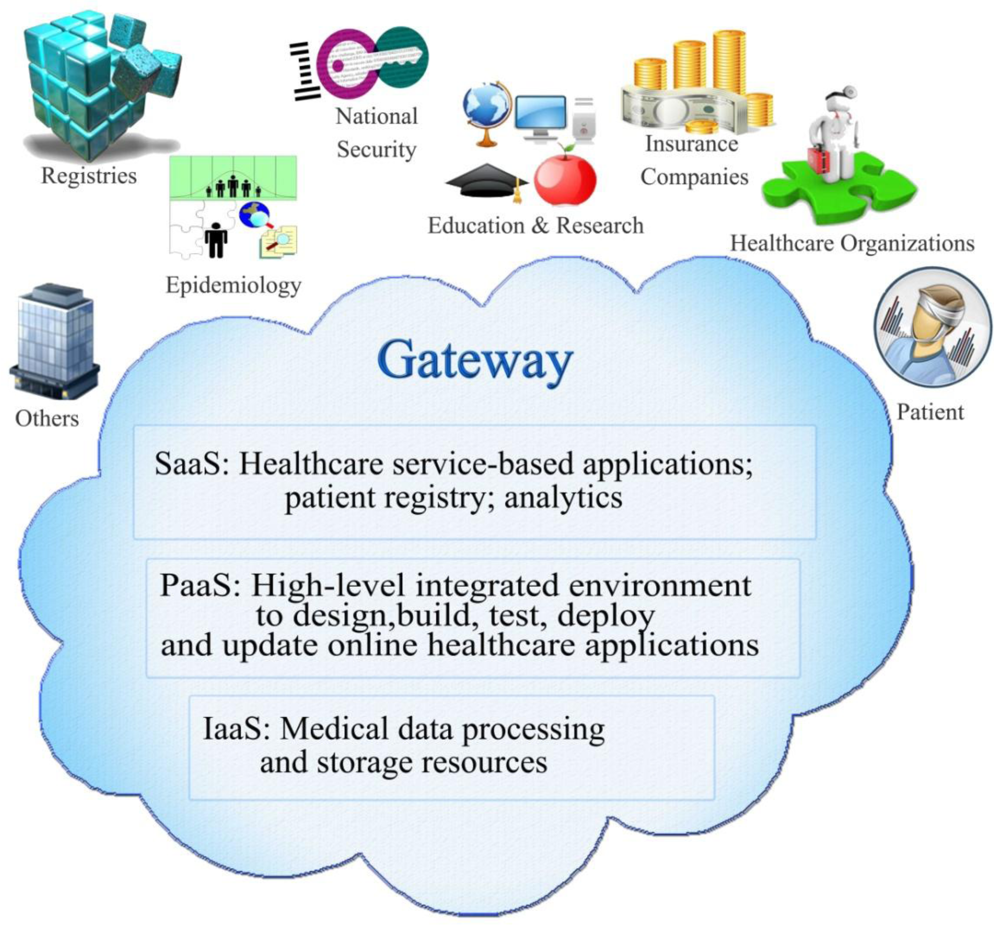
- Gateway: This component can be set to perform several important tasks: (i) managing access to the Cloud; (ii) verifying EHR (Electronic Health Record) provided by different health care providers in terms of integrity, authenticity, confidentiality and compliance with medical data exchange regulations; (iii) combining and integrating EHR data into a new composite Cloud-based EHR; (iv) selecting and de-identifying EHR to share with the public Cloud for research, educational and industrial purposes [22].
- Service Based Applications: such as services for national security and epidemiology, registries, Web Portal, Picture Archiving and Communication Systems (PACS); all of which provided as services that are easily managed through CC operational parameters.
- Software as a Service: provides Cloud-based software solutions (e.g., clinical systems; CSM) where consumers such as healthcare providers or financial and insurance brokers receive access to the software capabilities of the cloud.
- Platform as a Service: extends the basic infrastructure with High-level integrated environment to design, build, test, deploy and update online healthcare applications.
- Infrastructure as a Service: physical processing and storage resources.
3. e-Health Cloud Challenges
3.1. Technical Challenges
- Availability: Most healthcare providers require high availability of the e-Health Cloud services. Service and data availability is crucial for healthcare providers who cannot effectively operate unless their applications and patients’ data are available. The e-Health Cloud services should be available continuously with no interruptions or performance degradation. Cloud services could experience failures due to software and hardware faults, network faults, security attacks, and natural disasters among many other reasons. As CC resources are distributed over an open network such as the Internet, they will not offer better availability compared to owning and maintaining IT infrastructures within the organization [42]. e-Health Cloud environments need to make serious provisions to react rapidly and efficiently to such outages and ensure service continuity to the participating healthcare providers and other organizations. In addition, hardware and software installations, upgrades, and reconfigurations should be managed such that they are done without any service interruptions for the healthcare providers.
- Data/Service Reliability: using the cloud for an important application like e-Health Cloud requires assurances of good reliability for the provided services. All e-Health Cloud services and data must be error-free. Some important decisions regarding single human or society health can be taken depending on the data and services provided by the e-Health Cloud. As such services are distributed and may come from a number of Cloud providers, the chance of having faulty or incorrect data or services can increase. The data in e-Health Cloud must be consistent and constantly in a valid state regardless of any software, hardware, or network failures. In addition, all e-Health Cloud must deliver error-free services for healthcare providers.
- Data Management: Huge numbers of medical records and images related to millions of people will be stored in e-Health Clouds. The data may be replicated for high reliability and better access at different locations and across large geographic distances. Some of the data could be also made available locally. Most medical applications require secure, efficient, reliable, and scalable access to the medial records. These requirements enforce the need to have some storage services that provide fault tolerance, secure storage over public clouds, and rich query languages that allow efficient and scalable facilities to retrieve and process the application data.
- Scalability: hundreds of healthcare providers with millions of patient records could be handled by an e-Health Cloud, which is only achievable if and only if the services provided are scalable. The ability to scale (grow while maintaining acceptable performance) is one of the most important factors in providing successful cloud services. Cloud scalability is mainly enabled by increasing the capacity and number of IT resources such as compute nodes, network connections, and storage units and providing suitable operational and management facilities. Scalability requires dynamic configuration and reconfiguration as well as an automatic resizing of used virtualized hardware resources [43]. In addition, scalability requires maintaining an acceptable level of performance regardless of the size and utilization levels of the services.
- Flexibility: an e-Health Cloud must be capable of serving multiple healthcare providers with different requirements. These requirements are in terms of functions, operations, users, auditing, management, and quality of service (QoS) requirements. The e-Health Cloud infrastructures and services should be flexible enough to be configured for different healthcare providers’ requirements. In addition, the e-Health Cloud should be very flexible in adding new needed services to support healthcare processes. While e-Health Cloud services must be flexible to meet different healthcare requirements, they also must be easily configurable to meet with different needs. In other words, the configuration of cloud services to meet different requirements must be achieved with minimum effort and cost.
- Interoperability: services for the e-Health Cloud can be provided from multiple cloud service providers. For example, one provider may provide storage and processing services for high resolution medical images while another provider may provide storage and other services for storing patient electronic records or data mining and analysis services. The main issue here is interoperability which involves defining an agreed-upon framework or some open protocols/APIs that enable easy servers and data integration among different cloud service providers [44]. The common framework or protocol should also include mechanisms for secure information exchange and services’ integration. The issue of interoperability is also faced when integrated e-Health Cloud services are provided from both local and external clouds. For example, some e-health functions can be developed by integrating some local and external services. These e-Health Cloud services cannot be formed easily unless there is a good degree of interoperability among the local and external service providers. A good degree of interoperability can also facilitate easy migration among different available systems. Data migration between an old local application and a new e-Health Cloud can be simplified if open protocols and APIs are provided. One approach is to utilize the concept of Service-Oriented Architecture (SOA) [45,46] for implementing the e-Health Cloud. SOA aims to make services available and easily accessible through standardized models and protocols without having to worry about the underlying infrastructures, development models or implementation details. This helps achieve interoperability and loose coupling among e-Health Cloud components and also among e-Health Cloud users.
- Security: the e-Health Cloud services can be provided by multiple cloud service providers and be used by multiple healthcare providers. The cloud service providers provide a number of recourses that are collected in a virtualized pool to be utilized by healthcare providers. High security concerns are usually associated with open environments which are provided by a number of service providers and shared among a number of service consumers. A healthcare provider that owns IT applications within its premises can apply and monitor proper security policies and controls for identity and access control managements. However with open environments, it is very important to provide cloud services which support suitable and adequate access control and authentication mechanisms in addition to mechanisms to secure the transfer of such data to and from clients and service providers. That is essential since data must be kept secure in the multi-tenant clouds where it is stored along with other healthcare providers’ data. In addition, it is necessary to make sure that the service provider itself cannot access or use the healthcare providers’ data. Another issue is the need for efficient security mechanisms for the e-Health Cloud. While there are several ways to apply strong security measures, these impose high computation and communication costs rendering them inefficient in distributed open environments such as the Cloud. In addition, another issue is the wide range of security requirements among healthcare providers, thus an organization’s security requirements and policies may not be fully reflected in cloud services [47].
- Privacy: privacy is an important CC issue that could prevent the full utilization of its capabilities for different types of organizations and applications [48]. Privacy is particularly one of the main concerns in e-Health systems [49,50]. When using the Cloud for e-Health services, this concern is amplified. The concerns here involve the ability to protect patient’s records from each other, other healthcare providers and the cloud service providers. In addition, all associated organizations also require certain access to records or parts of records, while trying to protect their own data. Controlling such a maze of interconnected data and entities and using it is a huge issue. Patients, healthcare providers and any other associated organization will worry about the privacy of their information and would like to see proper solutions to offer acceptable privacy levels before moving to the cloud.
- Maintainability: Unlike having an e-health system for individual healthcare service providers, an e-Health Cloud can be used for hundreds of healthcare service providers. This increases the complexity of system maintainability in the e-Health Cloud compared to an individual e-health system. The increase is mainly due to the need to consider the requirements and characteristics of the multiple heath services providers and clients. These requirements can be completely different while maintenance in the cloud infrastructures, software, or platforms must be done without having any negative affects on any services provided for any clients. In this regard and to simplify the maintenance processes, all cloud resources and provided services must be designed for easy and reliable maintenance. In addition, testing models can be developed to simplify the process and to reduce the time needed for maintenance.
3.2. Non-Technical Challenges
- Organizational change: the move towards e-Health Cloud will require significant changes to clinical and business processes and also to the organizational boundaries in the healthcare industry. This challenge is concerned with the changes that an e-Health Cloud will introduce upon participants. Examples of such changes could be in the form of new policies, procedures and workflows in addition to changes in how medical processes and documentation are done.
- Legislations and standards: there are still no clear or adequate legislations and guidelines for clinical, technical and business practices of healthcare in the e-context. This includes the lack of standards for medical informatics, policies, inter-operability, and transmission methods in e-Health Cloud. In such a case, the stakeholders in the e-Health Cloud do not have a solid base to start offering and using it. As a result, more issues and problems may occur due to this shortage and technical, social and ethical concerns will arise. Currently, there are some standards and classifications for health information systems in general some of which can be adopted for the e-Health Cloud. One example is the International Classification of Diseases tenth revision (ICD-10) issued by the World Health Organization (WHO) [51]. It defines a medical classification list for the coding of diseases, signs or abnormal findings, complaints, social conditions, and external causes of injury or diseases. Another classification is The Systematized NOmenclature of MEDicine (SNOMED) which was designed as a detailed categorization of clinical medicine for the purpose of storing and/or retrieving records of clinical care in human and veterinary medicine [52]. The e-Health Cloud developers can agree on adopting some of these defined standards and classifications to enable interoperability among different organizations.
- Data ownership: ownership of data in the healthcare industry in general is an area with no clear guidelines. A patient’s record for example could be the sole property of the patient, yet can his physician also claim ownership? What about the patient’s insurer or the hospital management? This challenge is concerned with the creation of policies and guidelines that draw clear ownership boundaries.
- Privacy, trust and liability issues: this challenge is concerned with the risks of private data exposure, data leakage, and data loss and the lack of knowledge about the location and jurisdiction of the medical data. From the healthcare providers' perspective, e-Health Cloud presents a high risk of liability (legal responsibility) in cases of data loss or leakage causing loss of reputation and patients’ trust.
- Usability and end users experiences: this challenge is concerned with the degree and level of adoption obtained by the e-Health Cloud users including patients, healthcare professionals, and administrative and insurance personnel. Proper and adequate pre-implementation training and marketing along with continuous post-implementation training are important to help overcome this challenge.
4. Research Efforts
4.1. Cloud-based Storage Solutions, HIT Applications and Systems
4.2. Platform Solutions
4.3. e-Health Cloud Implementation Models
5. Security and Privacy Challenges in e-Health Cloud
- Confidentiality: ensuring that healthcare data is not accessed by unauthorized parties.
- Integrity: ensuring the accuracy and consistency of healthcare data.
- Authentication: ensuring that users are the persons they claim to be.
- Access control: ensuring that users access only healthcare data that they are allowed to access based on their authentication and access levels.
- Non-repudiation: ensuring that a party of a communication cannot deny having sent or received the data.
- Privacy: ensuring that patients maintain the right to control what healthcare data is collected about them, how it is used, who uses it, who maintains it, and what purpose it is used for.
- Audit: ensuring the safety of healthcare data and the e-Health Cloud overall system by recording and monitoring all users and data access activities.
| Work | Objective | Approach | Advantages | Limitations |
|---|---|---|---|---|
| [64] | Secure personal health record (PHR). | Patient-Centric and fine-grained data access control through multiple-owner settings model. | Fine-grained access; user revocation; flexible data access policy; beak-glass access. | Computation overhead on data owner; risks of privacy exposure by cloud owner. |
| [65] | Secure PHR, maintain data confidentiality against cloud owner; reduce overhead on the data owner for key distribution and data/user management. | Allow data owner to delegate computation tasks in fine-grained data access control to cloud owners without disclosing content by combined advanced cryptographic techniques: Key-Policy Attribute- Based Encryption (KP-ABE), Proxy Re-Encryption (PRE) and lazy re-encryption. | Cloud owner is not able to learn any “plaintext medical data”; computation overhead is reduced on users which saves their efforts and time online; scalability. | Limited data access policies management; no mechanisms to serve emergency scenarios. |
| [66] | Ensure privacy and confidentially of EHR; Track activities at the Cloud owner end of the e-Health Cloud infrastructure. | Install Computer forensic tools on the cloud machines to capture any volatile information. Different mechanisms of authentication, authorization and access control procedures to protect nonvolatile information. | Protect medical data confidentially against cloud owners; CFT provides digital evidence to be used to establish cyber crime in courts of law. | CFT promises to track volatile actions and to support cases in courts; but it does not physically stop volatile actions. |
| [21] | Secure end user platforms when accessing e-Health Cloud. | Trusted privacy domains (TVD): Systems in the end-user platform should be able to divide the execution environment for applications into separated domains isolated from each other. | Overcome limitations of security features within end user platforms; reduce security risks; Automatic management (transparent TVD establishment, key management and policy enforcement). | Hardware requirements; complexity and scalability |
| [17] | Secure EHR exchange when a referral is made. | EHR is only stored at the physicians’ practices (the only trusted environment). EHRs are encrypted and signed before leaving the physician’s practice and decrypted only by the receiving specialist. | Provides secure encryption and signatures for all documents transferred. | Patient and patient-centric functions are not integrated in the current model. |
| [58] | Develop and disseminate specialized secure services/platforms for e-Health Cloud. | Digital signature, hashing and encryption, integrity check-sum, Single Point of Contact (SPoC), access control, audit trial, identity mapping, etc. | A complete e-Health Cloud services platform, provides mechanisms to reinforce medical data confidentiality, security, integrity & auditing. | Comprehensive evaluation in a real medical environment;Integration with other public e-Health Clouds. |
6. Discussion
- Reducing the cost of owning and maintaining an IT infrastructure and support personnel within each organization.
- Providing better integration and exchange of medical records across multiple organizations and across sparse geographical areas.
- Allowing multiple parties to benefit from the information repository to streamline processes, enhance diagnosis, support medical research activities, and simplify administrative operations.
- Increasing the availability, scalability and flexibility of the health information systems.
7. Conclusions
Acknowledgments
References
- Goldschmidt, P.G. HIT and MIS: Implications of health information technology and medical information systems. Commun. ACM 2005, 48, 69–74. [Google Scholar]
- Davidson, E.; Heslinga, D. Bridging the IT adoption gap for small physician practices: An action research study on electronic health records. Inf. Syst. Manag. 2006, 24, 15–28. [Google Scholar] [CrossRef]
- Klein, R. An empirical examination of patient-physician portal acceptance. Eur. J. Inf. Syst. 2007, 16, 751–761. [Google Scholar] [CrossRef]
- Young, H.M. Challenges and solutions for care of frail older adults. Online J. Issues Nurs. 2003, 8, 5. [Google Scholar]
- HEALTHCAST 2020: Creating a Sustainable Future; PricewaterhouseCoopers: London, UK, 2006.
- Singh, H.; Naik, A.D.; Rao, R.; Petersen, L.A. Reducing diagnostic errors through effective communication: Harnessing the power of information technology. J. Gen. Internal Med. 2008, 23, 489–494. [Google Scholar] [CrossRef]
- Douglas, T.J.; Ryman, J.A. Understanding competitive advantage in the general hospital industry: Evaluating strategic competencies. Strateg. Manag. J. 2003, 24, 333–347. [Google Scholar] [CrossRef]
- Lenz, R.; Reichert, M. IT support for healthcare processes—Premises, challenges, perspectives. Data Knowl. Eng. 2006, 61, 39–58. [Google Scholar]
- Saranummi, N. In the spotlight: Health information systems. IEEE Rev. Biomed. Eng. 2008, 1, 15–17. [Google Scholar] [CrossRef]
- Saranummi, N. In the spotlight: Health information systems—PHR and value based healthcare. IEEE Rev. Biomed. Eng. 2009, 2, 15–17. [Google Scholar] [CrossRef]
- Saranummi, N. In the spotlight: Health information systems—Mainstreaming mHealth. IEEE Rev. Biomed. Eng. 2011, 4, 17–19. [Google Scholar] [CrossRef]
- Vasilakos, A.V.; Lisetti, C. Special section on affective and pervasive computing for healthcare. IEEE Trans. Inf. Technol. Biomed. 2010, 14, 183–359. [Google Scholar] [CrossRef]
- Foster, I.; Zhao, Y.; Raicu, L.; Lu, S. Cloud Computing and Grid Computing 360-Degree Compared. In Proceedings of the Grid Computing Environments Workshop (GCE), Austin, TX, USA, 12–16 November 2008; 2008; pp. 1–10. [Google Scholar]
- Shimrat, O. Cloud Computing and Healthcare. Available online: http://www.himss.org/content/files/Code%2093_Shimrat_CloudComputingandHealthcare_2009.pdf (accessed on 28 June 2012).
- Teng, C.C.; Mitchell, J.; Walker, C. A Medical Image Archive Solution in the Cloud. In Proceedings of the 2010 IEEE International Conference on Software Engineering and Service Sciences (ICSESS), Beijing, China, 16–18 July 2010; pp. 431–434.
- Cloud Computing: Clear Benefits: The Emerging Role of Cloud Computing in Healthcare Information Systems. Available online: http://www.techrepublic.com/whitepapers/cloud-computing-clear-benefits-the-emerging-role-of-cloud-computing-in-healthcare-information-systems/2384337 (accessed on 28 June 2012).
- Kaletsch, A.; Sunyaev, A. Privacy Engineering: Personal Health Records in Cloud Computing Environments. In Proceedings of the 32nd International Conference on Information Systems (ICIS 2011), Shanghai, China, 4–7 December 2011; pp. 1–11.
- Mahony, M. Trust remains key barrier to eHealth. Available online: http://euobserver.com/893/31958 (accessed on 28 June 2012).
- Zhang, T.; Liu, L. Security Models and Requirements for Healthcare Application Clouds. In Proceedings of the IEEE 3rd International Conference on Cloud Computing, Miami, FL, USA, 5–10 July 2010; pp. 268–275.
- Maria, A.F.; Fenu, G.; Surcis, S. An Approach to Cloud Computing Network. In Proceedings of the 3rd International Conference on Theory and Practice of Electronic Governance, Bogota, Colombia, 10–13 November 2009; pp. 409–410.
- Lohr, H.; Sadeghi, A.; Winandy, M. Securing the E-Health Cloud. In Proceedings of the 1st ACM International Health Informatics Symposium (IHI 2010), Arlington, VA, USA, 11–12 November 2010; pp. 220–229.
- AbuKhousa, E.; Najati, H.A. UAE-IHC: Steps towards Integrated E-Health Environment in UAE. In Proceedings of the 4th e-Health and Environment Conference in the Middle East, Dubai, UAE, 30 January 2012–2 February 2012.
- Kaletsch, A.; Sunyaev, A. Privacy Engineering: Personal Health Records in Cloud Computing Environments. In Proceedings of the International Conference on Information Systems (ICIS 2011), Shanghai, China, 4–7 December 2011.
- European Commission. Protecting Your Personal Data. Available online: http://ec.europa.eu/justice/data-protection/individuals/index_en.htm (accessed on 28 June 2012).
- U.S. Department of Health & Human Services. Protecting Personal Health Information in Research: Understanding the HIPAA Privacy Rule. Available online: http://privacyruleandresearch.nih.gov/pdf/HIPAA_Booklet_4-14-2003.pdf (accessed on 28 June 2012).
- ITU-T Technology Watch Report—Standards and eHealth. Available online: http://www.itu.int/dms_pub/itu-t/oth/23/01/T23010000120003PDFE.pdf (accessed on 28 June 2012).
- Wootton, R.; Patil, N.G.; Scott, R.E.; Ho, K. Telehealthin the Developing World, Electronic Version; Royal Society of Medicine Press/IDRC: London, UK, 2009. [Google Scholar]
- Agency for Healthcare Research and Quality. Available online: http://www.ahrq.gov/ (accessed on 28 June 2012).
- The US Government Printing Office (GPO). Public Law 111—5—American Recovery and Reinvestment Act of 2009. Available online: http://www.gpo.gov/fdsys/pkg/PLAW-111publ5/pdf/PLAW-111publ5.pdf (accessed on 28 June 2012).
- Commonwealth Secretariat. Progress report. Available online: http://www.thecommonwealth.org/files/189921/FileName/HealthProgressReports-E-Health.pdf (accessed on 28 June 2012).
- Momtahan, L.; Lloyd, S.; Simpson, A. Switched Lightpaths for E-Health Applications: Issues and Challenges. In Proceedings of the Twentieth IEEE International Symposium Computer-Based Medical Systems (CBMS’07), Maribor, Slovenia, 20–22 June 2007; pp. 459–464.
- Agrawal, D.; Abbadi, A.; Antony, S.; Das, S. Data Management Challenges in Cloud Computing Infrastructures. In Proceedings of the 6th International Workshop on Databases in Networked Information Systems (DNIS 2010), Aizu-Wakamatsu, Japan, 29–31 March 2010.
- Hasan, J. Effective telemedicine project in Bangladesh: Special focus on diabetes health care delivery in a tertiary care in Bangladesh. Telemat. Inform. 2012, 29, 211–218. [Google Scholar] [CrossRef]
- Rayport, J.F.; Heyward, A. Envisioning the Cloud: The Next Computing Paradigm. A MarketspaceNext Point of View. Available online: http://marketspacenext.com/inthemedia/envisioning-the-cloud/ (accessed on 28 June 2012).
- Introduction to Cloud Computing Architecture; Sun Microsystems: Santa Clara, CA, USA, 2009.
- Varia, J. Cloud Architectures. Available online: http://aws.amazon.com/articles/1632?_encoding=UTF8&jiveRedirect=1 (accessed on 28 June 2012).
- Hosseini, A.; Sommerville, I.; Sriram, I. Research Challenges for Enterprise Cloud Computing. Available online: http://arxiv.org/abs/1001.3257 (accessed on 28 June 2012).
- Mei, L.; Chan, W.K.; Tse, T.H. A Tale of Clouds: Paradigm Comparisons and Some Thoughts on Research Issues. In Proceedings of the Asia-Pacific Services Computing Conference (APSCC’08), Yilan, Taiwan, 9–12 December 2008; pp. 464–469.
- Armbrust, M.; Fox, A.; Griffith, R.; Joseph, A.; Katz, R.; Konwinski, A.; Lee, G.; Patterson, D.; Rabkin, A.; Stoica, I.; Zaharia, M. Above the Clouds: A Berkeley View of Cloud Computing. Available online: http://inst.cs.berkeley.edu/~cs10/fa10/lec/20/2010-11-10-CS10-L20-AF-Cloud-Computing.pdf (accessed on 29 June).
- Sriram, I.; Khajeh-Hosseini, A. Research Agenda in Cloud Technologies. In Proceedings of the 1st ACM Symposium on Cloud Computing, SOCC 2010, Indianapolis, IN, USA, 10–11 June 2010.
- Youseff, L.; Butrico, M.; da Silva, D. Toward a Unified Ontology of Cloud Computing. In Proceedings of the Grid Computing Environments Workshop (GCE’08), Austin, TX, USA, 12–16 November 2008; pp. 1–10.
- Leavitt, N. Is cloud computing really ready for prime time? Computer 2009, 42, 15–20. [Google Scholar]
- Vaquero, L.M.; Rodero-Merino, L.; Caceres, J.; Lindner, M. A Break in the clouds: Towards a cloud definition. ACM SIGCOMM Comput.Commun. Rev. 2009, 39, 50–55. [Google Scholar] [CrossRef]
- Rimal, B.P.; Jukan, A.; Katsaros, D.; Goeleven, Y. Architectural requirements for cloud computing systems: An enterprise cloud approach. J. Grid Comput. 2011, 9, 3–26. [Google Scholar] [CrossRef]
- Al-Jaroodi, J.; Mohamed, N. Service-oriented middleware: A survey. J. Netw. Comput. Appl. 2012, 35, 211–220. [Google Scholar] [CrossRef]
- Nguyen, D.K.; Lelli, F.; Papazoglou, M.P.; van den Heuvel, W.-J. Blueprinting Approach in Support of Cloud Computing. Future Internet 2012, 4, 322–346. [Google Scholar] [CrossRef]
- Chow, R.; Golle, P.; Jakobsson, M.; Shi, E.; Staddon, J.; Masuoka, R.; Molina, J. Controlling Data in the Cloud: Outsourcing Computation without Outsourcing Control. In Proceedings of the 2009 ACM Workshop on Cloud Computing Security, Chicago, IL, USA, 9–13 November 2009; pp. 85–90.
- Pearson, S. Taking Account of Privacy when Designing Cloud Computing Services. In Proceedings of the ICSE Workshop on Software Engineering Challenges of Cloud Computing at CLOUD’09, Washington, DC, USA, 23 May 2009; pp. 44–52.
- Goldman, J.; Hudson, Z. Virtually exposed: Privacy and e-health. Health Aff. 2000, 19, 140–148. [Google Scholar] [CrossRef]
- Kelly, E.P.; Unsal, F. Health information privacy and e-healthcare. Int. J. Healthc. Technol. Manag. 2002, 4, 41–52. [Google Scholar] [CrossRef]
- International Classification of Diseases (ICD). Available online: http://www.who.int/classifications/icd/en/ (accessed on 11 May 2012).
- Cote, R.A. Architecture of SNOMED: Its Contribution to Medical Language Processing. In Proceedings of the Annual Symposium on Computer Applied Medical Care, Washington, DC, USA, 25–26 October 1986; pp. 74–80.
- Guo, L.; Chen, F.; Chen, L.; Tang, X. The building of cloud computing environment for e-health. In Proceedings of the International Conference on e-Health NetworkingDigital Ecosystems and Tech. (EDT), Shenzhen, China, 17–18 April 2010; pp. 89–92.
- Chen, P.; Freg, C.; Hou, T.; Teng, W.-G. Implementing RAID-3 on Cloud Storage for EMR System. In Proceedings of the 2010 International Computer Symposium (ICS), Taiwan, 16–18 December 2010; pp. 850–853.
- Rolim, C.O.; Koch, F.L.; Westphall, C.B. A Cloud Computing Solution for Patient’s Data Collection in Health Care Institutions. In Proceedings of the Second International Conference on eHealthTelemedicineand Social Medicine (ETELEMED'10), St. Maarten, The Netherlands, 10–16 February 2010; pp. 95–99.
- Lo, O.; Fan, L.; Buchanan, W.; Thümmler, C.; Khedim, A.; Lawson, A.; Uthmani, O.; Bell, D. Patient Simulator: Towards Testing and Validation of e-Health Infrastructures. In Proceedings of the Pervasive Health, Dublin, Ireland, 23–26 May 2011.
- White, J. Cloud Computing in Healthcare: Is there a Silver Lining? Available online: http://www.aspenadvisors.net/results/whitepaper/cloud-computing-healthcare-there-silver-lining (accessed on 28 June 2012).
- Fan, L.; Buchanan, W.; Thummler, C.; Lo, O.; Khedim, A.; Uthmani, O.; Lawson, A.; Bell, D. DACAR Platform for eHealth Services Cloud. In Proceedings of the 4th International Conference on Cloud Computing, Miami, FL, USA, July 2011; pp. 219–226.
- Baru, C.; Botts, N.; Horan, T.; Patrick, K.; Fedman, S.S. A Seeded Cloud Approach to Health Cyberinfrastructure: Preliminary Architecture Design and Case Applications. In Proceedings of the 45th Hawaii International Conference on System Sciences, Maui, HI, USA, 4–7 January 2012; pp. 2727–2734.
- He, C.; Jin, X.; Zhao, Z.; Xiang, T. A Cloud Computing Solution for Hospital Information System. In Proceedings of the Intelligent Computing and Intelligent Systems (ICIS), Xiamen, China, 29–31 October 2010; pp. 517–520.
- Yu, W.D. A Service Modeling Approach to Service Requirements in SOA and Cloud Computing—Using a U-Healthcare System Case. In Proceedings of the IEEE 13th International Conference on e-Health NetworkingApplications and Services, Columbia, MO, USA, 13–15 June 2011; pp. 233–236.
- Rosado, D.G.; Gómez, R.; Mellado, D.; Fernández-Medina, E. Security analysis in the migration to cloud environments. Future Internet 2012, 4, 469–487. [Google Scholar] [CrossRef]
- Grobauer, B.; Walloschek, T.; Stocker, E. Understanding cloud computing vulnerabilities. IEEE Secur. Privacy Mag. 2011, 9, 50–57. [Google Scholar] [CrossRef]
- Li, M.; Yu, S.; Ren, K.; Lou, W. Securing Personal Health Records in Cloud Computing: Patient-centric and Fine-grained Data Access Control in Multi-owner Settings. In Proceedings of the 6th International ICST Conference on Security and Privacy in Communication Networks (SecureComm 2010), Singapore, 7–9 September 2010; pp. 89–106.
- Yu, S.; Wang, C.; Ren, K.; Lou, W. Achieving secure, scalable and fine-grained data access control in cloud computing. In Proceedings of INFOCOM 2010, San Diego, CA, USA, 15–19 March 2010; pp. 1–9.
- Ahmed, S.; Raja, M.Y.A. Tackling cloud security issues and forensics model. In Proceedings of the High-Capacity Optical Networks and Enabling Technologies (HONET 2010), Cairo, Egypt, 19–21 December 2010; pp. 190–195.
© 2012 by the authors; licensee MDPI, Basel, Switzerland. This article is an open-access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
AbuKhousa, E.; Mohamed, N.; Al-Jaroodi, J. e-Health Cloud: Opportunities and Challenges. Future Internet 2012, 4, 621-645. https://doi.org/10.3390/fi4030621
AbuKhousa E, Mohamed N, Al-Jaroodi J. e-Health Cloud: Opportunities and Challenges. Future Internet. 2012; 4(3):621-645. https://doi.org/10.3390/fi4030621
Chicago/Turabian StyleAbuKhousa, Eman, Nader Mohamed, and Jameela Al-Jaroodi. 2012. "e-Health Cloud: Opportunities and Challenges" Future Internet 4, no. 3: 621-645. https://doi.org/10.3390/fi4030621
APA StyleAbuKhousa, E., Mohamed, N., & Al-Jaroodi, J. (2012). e-Health Cloud: Opportunities and Challenges. Future Internet, 4(3), 621-645. https://doi.org/10.3390/fi4030621





