Cell-Sequence-Based Covert Signal for Tor De-Anonymization Attacks
Abstract
1. Introduction
- A More General Attack Model: We propose a more general and realistic attack model that remains effective in the modern Tor network. Unlike prior models that often assume attackers can easily determine their position within a circuit, our approach is designed to function under the uncertainty introduced by components like Tor bridges. By relaxing the need for a priori positional knowledge and instead incorporating a verification mechanism, our model overcomes a critical limitation that renders many previous attacks impractical.
- Discovery of Inherent Vulnerabilities: We identify and exploit two previously unexamined, protocol-level vulnerabilities. These vulnerabilities are not mere implementation flaws but stem from a fundamental design trade-off within Tor, where the goal of concealing circuit length inadvertently exposes subtle characteristics of cell transmission. Our attack leverages these inherent weaknesses to embed a covert signal without disrupting normal operations.
- An Adaptive and Stealthy Framework: We design a highly adaptive and stealthy attack framework operationalized by a finite state machine (FSM) embedded within each malicious router. Using this FSM, our routers can dynamically switch between several roles based on real-time circuit conditions, such as a signal injector, a detector, or a standard passive relay. This adaptability is crucial for evading detection and ensuring the resilience of the attack.
- Experimental Validation: We validate our methodology through experiments in a controlled, semi-realistic network environment. The results demonstrate that our covert signal is both stealthy, remaining undetectable by standard Tor routers and causing no performance degradation, and highly effective, enabling the reliable correlation of Tor users with their destinations.
2. Related Works
2.1. Linkage of Client Activities
2.2. Exposing the True IP Address of Hidden Services
3. More Background on Tor
3.1. Components of Tor
- Tor Client: The client runs a local software called the Onion Proxy (OP), which anonymizes client data by routing it through the Tor network.
- Application Server: This server supports TCP applications, such as web services. It can either be a public service, accessible by Tor clients through an external circuit, or a hidden service (HS), which can only be accessed by Tor clients using an internal circuit. Hidden services may use Unix sockets rather than TCP sockets to avoid leaking information about their IP address on the local network.
- Onion Routers (ORs): Onion Routers are the proxies that relay data between the Tor client and the application server. There are two types of onion routers: public onion routers and hidden onion routers, the latter of which are also known as bridges. Public onion routers are listed in the directory server and can be accessed by anyone. In contrast, hidden onion routers (bridges) are not listed publicly and can only be obtained through specific channels (e.g., websites, email, or Telegram bots). These bridges are used as the initial hop to access the Tor network in regions with heavy censorship.
- Directory Servers: These servers store and distribute the public information about onion routers and hidden services, including their public keys and configuration details.
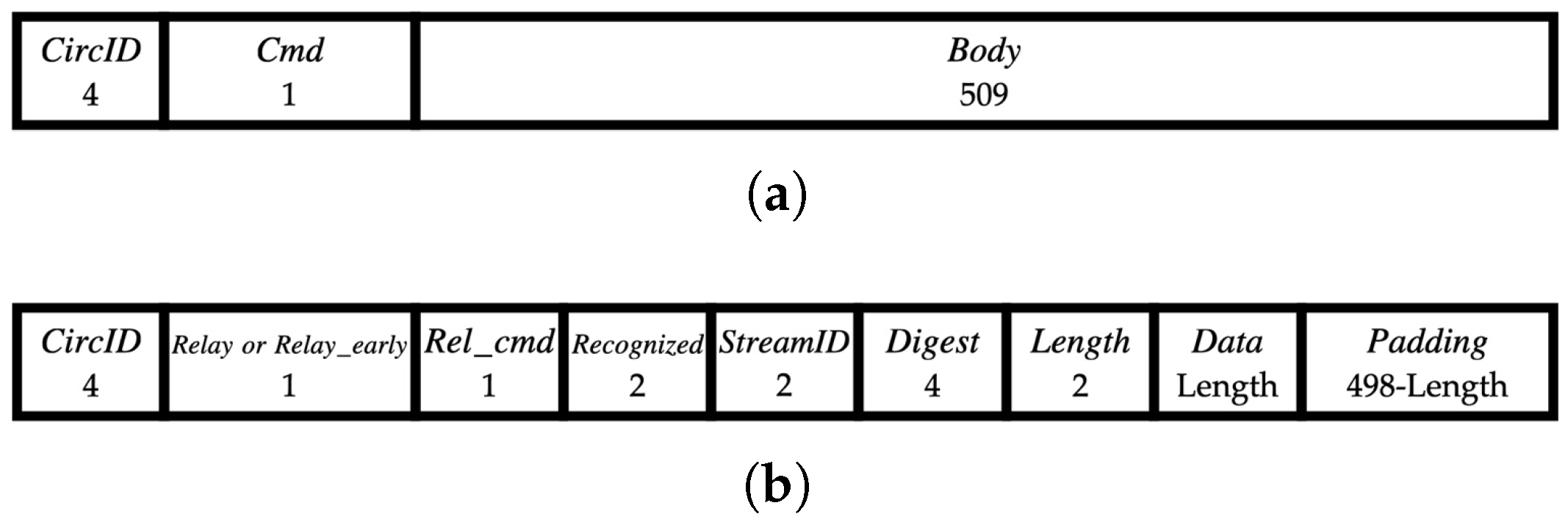
3.2. Communication Unit: Cells
- RELAY_COMMAND_EXTEND: Used for extending the circuit to the next node.
- RELAY_COMMAND_BEGIN: Used to create a stream that will be multiplexed over the circuit.
- RELAY_COMMAND_DATA: Carries application data to be sent over the circuit to the edge nodes.
- RELAY_CONFLUX_LINK: Used by the Conflux subprotocol, facilitates the linking of circuits at the edge node, as sent by the OP.
- RELAY_COMMAND_ESTABLISH_RENDEZVOUS: Used by the OP to register an OR as a rendezvous point.
- RELAY_COMMAND_RENDEZVOUS1: Used by the HS to join the OP-side rendezvous circuit.
- CREATE and CREATED: Used to establish the session key and create a circuit.
- DESTROY: Indicates that the circuit should be torn down.
3.3. Circuit Types and Construction
- HS-side Introduction Circuit (default length: 3): Created by the hidden service to designate an onion router as an introduction point. Clients use this introduction point to contact with the hidden service.
- Client-side Rendezvous Circuit (default length: 3): Established by the client to designate an onion router as a rendezvous point. The rendezvous point allows the hidden service to connect back to the client anonymously.
- Client-side Introduction Circuit (default length: 4): Constructed by the client to connect to the introduction point of a hidden service. This circuit type includes an additional hop, with the fourth node being established by the hidden service.
- HS-side Rendezvous Circuit (default length: 4): Built by the hidden service to connect to the client-established rendezvous point. Like the client-side introduction circuit, this also involves an additional hop, with the fourth node determined by the client.
3.4. Communication Between Tor Clients and Services
3.5. Evaluation of Onion Router Positions in Circuits
4. Adaptive Circuit-Level Cell Sequence Attack
4.1. Protocol-Level Vulnerabilities
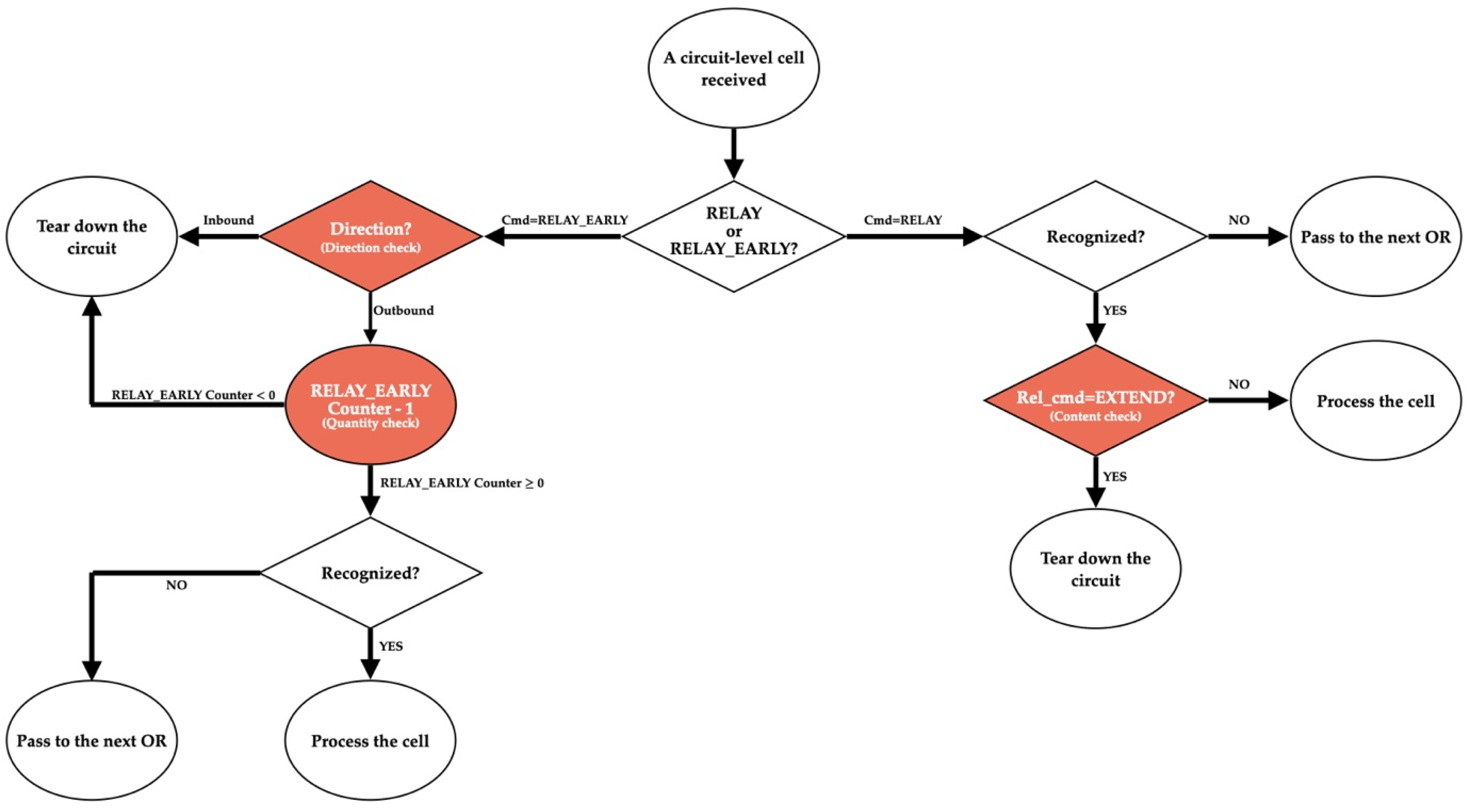
4.1.1. Behavior of Circuit-Level Cells
- Content Rule: Circuit extension requests must be encapsulated exclusively within RELAY_EARLY cells. As illustrated in Figure 1, if the Rel_cmd field is RELAY_COMMAND_EXTEND, the cell header Cmd field must be RELAY_EARLY.
- Maximum Quantity Rule: When establishing a new circuit, the OP randomly sets the maximum quantity to either 7 or 8. This means the circuit allows a maximum of 7 or 8 RELAY_EARLY cells to be sent outbound.
- Continuity Rule: To partially conceal the circuit length, the OP sends the first Maximum Quantity circuit-level cells as RELAY_EARLY cells.
- Direction Rule: For the historical security reason [26], the direction of RELAY_EARLY cells is restricted to outbound.
4.1.2. Absence of Continuity Validation (V1)
4.1.3. Residual Values in RELAY_EARLY Counters (V2)
4.2. Attack Algorithm
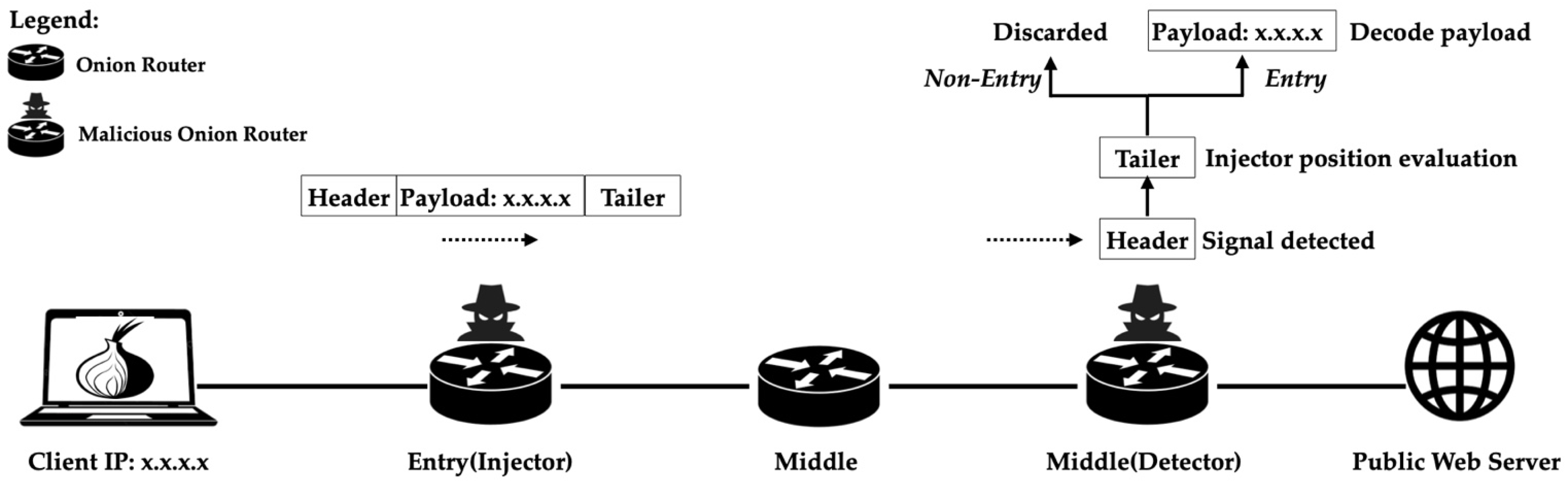
4.2.1. Functionality of the Covert Signal Injector
- 1.
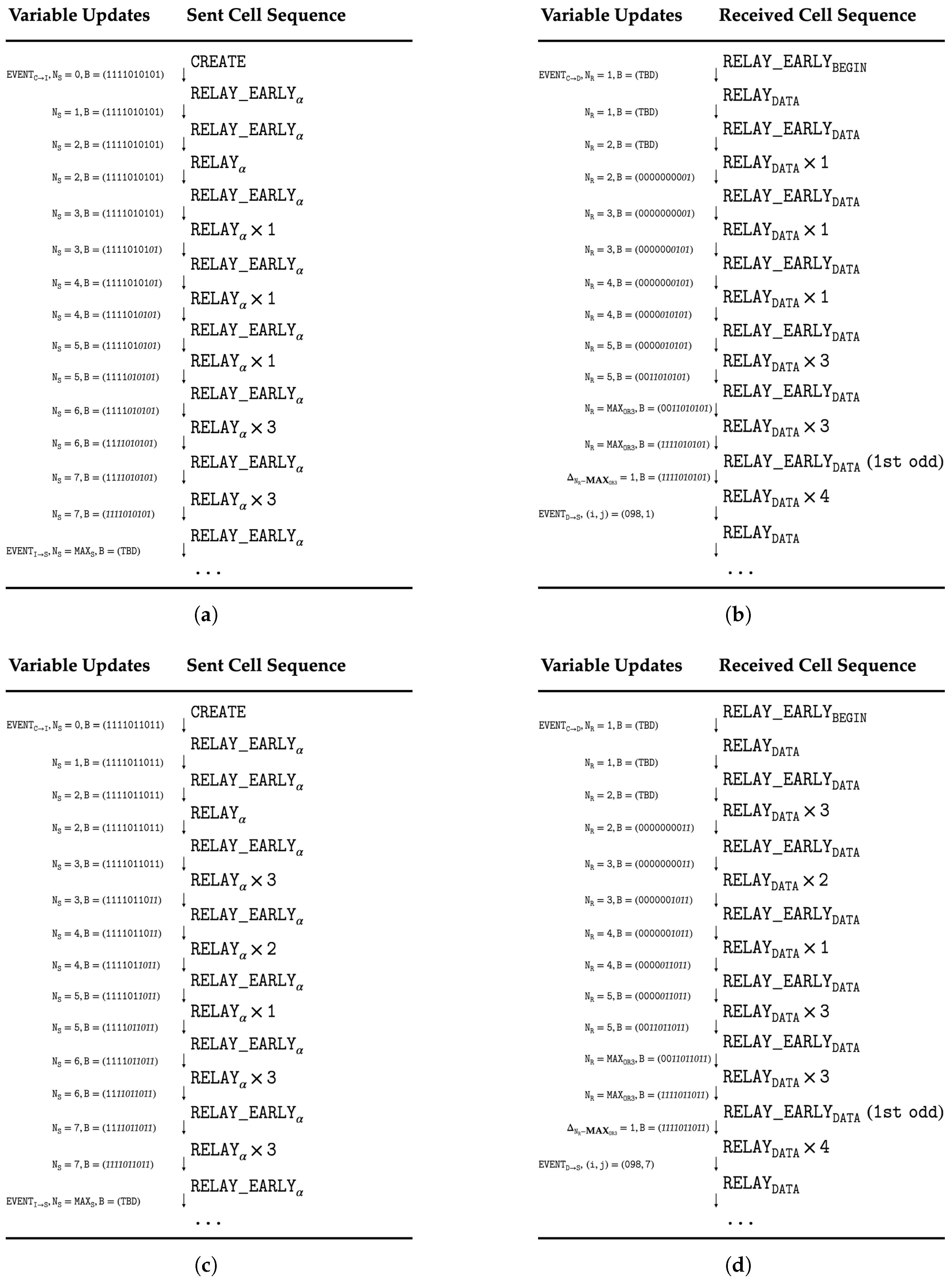
- Reserved: This field preserves the initial unmodified RELAY_EARLY cells to ensure the signal passes the content check of downstream ORs. Its length is set to , given that the maximum Tor path length is 4. Thus, the second and third RELAY_EARLY cells following the recognized RELAY_EARLYEXTEND cell remain unchanged to form this field.
- 2.
- Start Delimiter: This field exploits Vulnerability 1 (the absence of continuity validation) to mark the beginning of the covert signal. Since the OP sends consecutive RELAY_EARLY cells until COP is exhausted, the following cell transitions are valid under normal conditions: RELAY_EARLY → RELAY_EARLY, RELAY_EARLY → RELAY, and RELAY → RELAY. However, the transition RELAY → RELAY_EARLY should never occur. The injector deliberately introduces this anomalous pattern to signal the start of the covert message.
- 3.
- Payload: The payload encodes the identifier pair into five segments of RELAY cells, separated by four RELAY_EARLY delimiters. To reduce signal size and minimize message overhead, this identifier pair is further compressed using the following encoding scheme:First, the injector concatenates the three decimal digits of i (denoted ) with the single digit of j (denoted ) to form a four-digit decimal number:This decimal value N is then converted into a 10-bit binary string in big-endian bit order:The binary sequence B is divided into five consecutive 2-bit segments , for . Each pair is mapped to an integer that determines the number of RELAY cells in the k-th segment:Finally, each RELAY segment of length is inserted into the cell sequence, with RELAY_EARLY cells serving as delimiters between adjacent segments.
- 4.
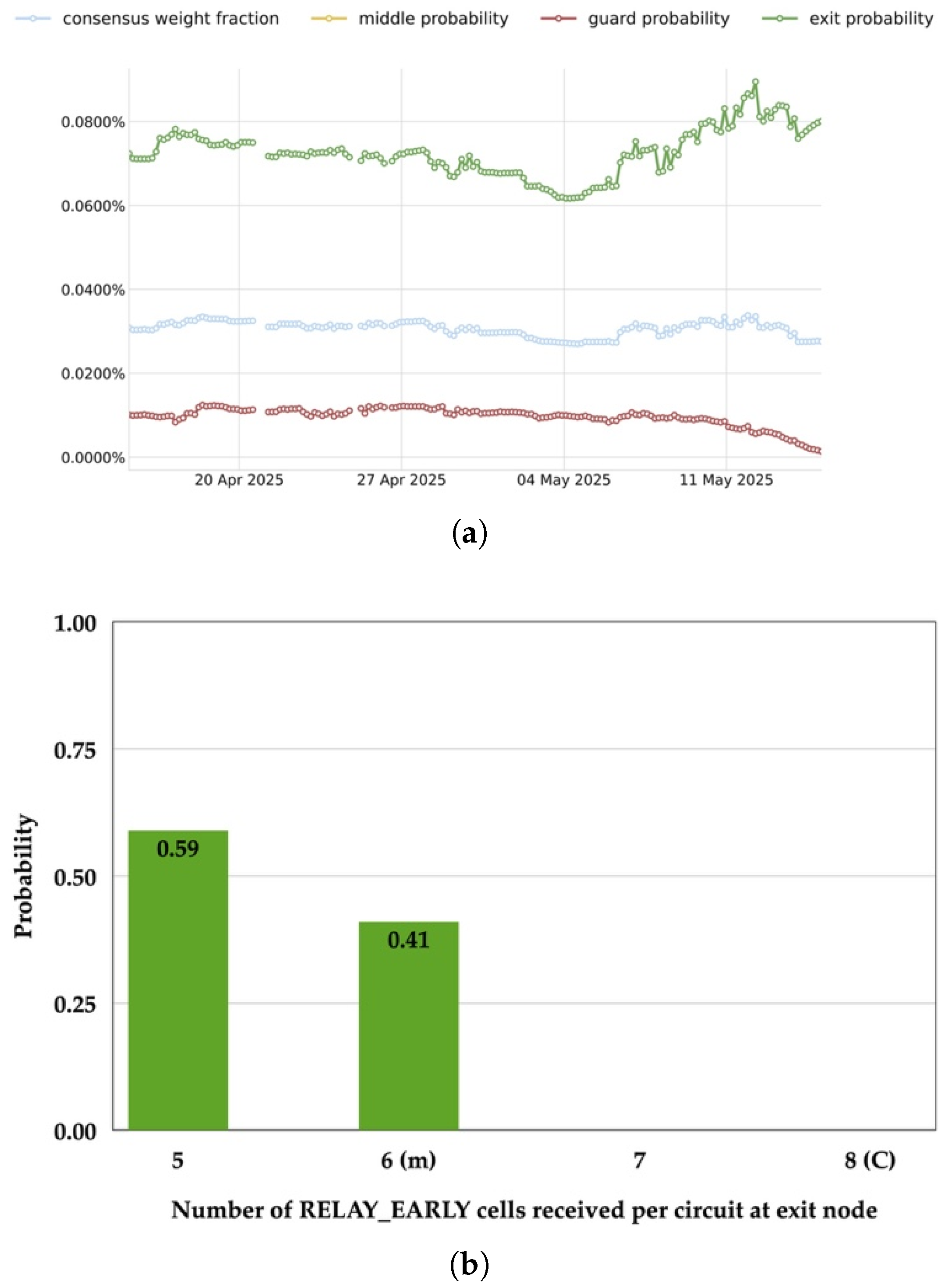
- End Delimiter: This field leverages Vulnerability 2 by deliberately exhausting the counter of the adjacent downstream router. As a result, the edge node receives at least one anomalous (odd) RELAY_EARLY cell. If this edge node is also a malicious router, it can detect the presence of the odd cell, thereby identifying both the end of the covert signal and the position of the injector. Once the eighth RELAY_EARLY cell is transmitted, the injector completes the encoding process.
4.2.2. Measuring the Stealthiness and Effectiveness of the Covert Signal
4.2.3. Functionality of the Covert Signal Detector
- Extracting Payload Data: The lengths of the five RELAY segments are extracted as decimal digits: from the payload field of the signal.
- Decompression: Each decimal digit is converted into a 2-bit binary string using the inverse function of Equation (3):
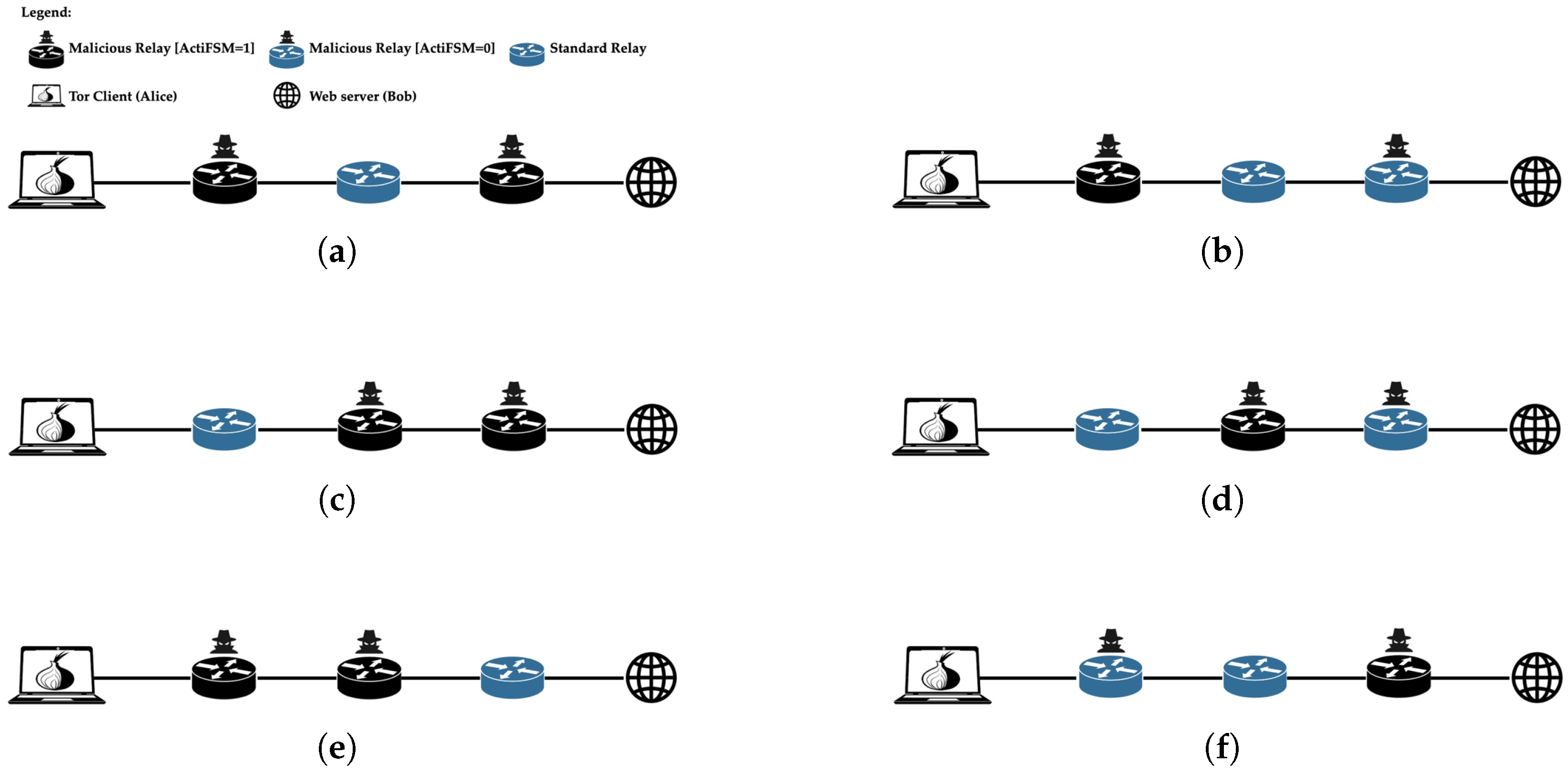
4.3. Deployment of Malicious Routers
- If the first cell received is neither a circuit extension RELAY_EARLYEXTEND nor indicative of a target edge position (RELAY_EARLYBEGIN or RELAY_EARLYRENDEZVOUS1), or if the cell suggests another malicious router is downstream, the FSM returns the router to Idle mode EVENTC→S.
- If the initial cell is a circuit-extension request RELAY_EARLYEXTEND, the router transitions into Injector mode to actively inject signals EVENTC→I.
- If the initial cell indicates the router is at a circuit edge (either RELAY_EARLYBEGIN or RELAY_EARLYRENDEZVOUS1), it transitions into Detector mode to monitor incoming signals EVENTC→D.
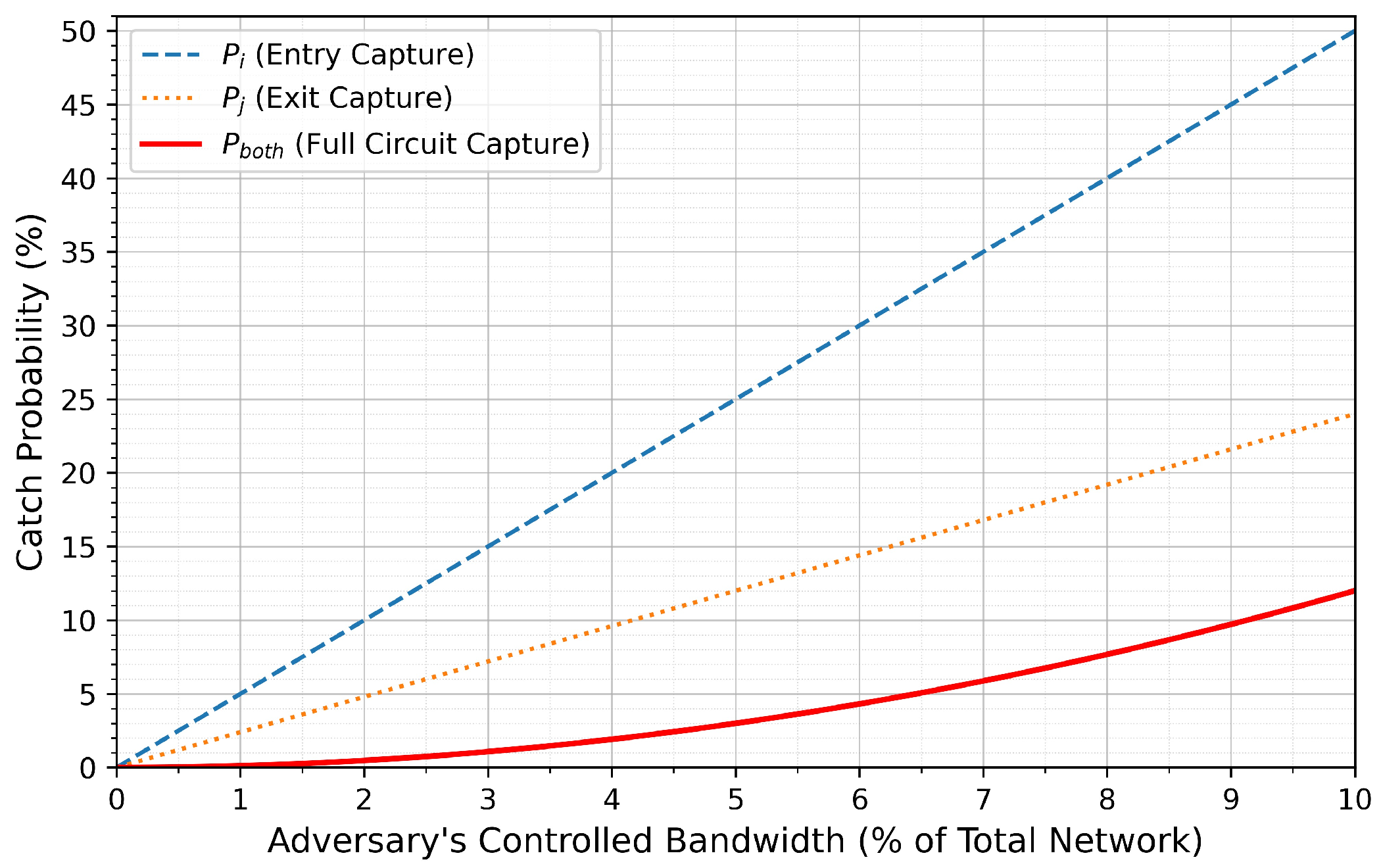
4.4. Analytical Probability of Entry-Exit Control
5. Evaluation
5.1. Experimental Setup
5.2. Phase One: Detecting Exploitation in the Wild
5.3. Phase Two: Validation of Attack Performance
5.4. Ethical Considerations
- Controlled Traffic Generation: All experimental traffic is generated exclusively between our modified Tor client and a destination web server under our control. This ensures that our experiments do not interfere with or de-anonymize other users’ activities on the Tor network.
- Private Attacker Infrastructure: The attacker-controlled onion routers are configured for private use only, meaning they do not publish their descriptors to the public Tor directory and listen on non-standard ports. This configuration prevents them from being incorporated into circuits used by other Tor users. Consequently, our active attack, which involves modifying cell headers, is limited to circuits initiated by our own client and passing through our controlled relays, thereby not affecting any other users’ traffic.
- Minimal Data Logging: We log and store only the minimal amount of data essential for our analysis.Specifically, we record the sequence of cell headers and timestamps recorded by our injector and detector components for time-correlation analysis. No payload data or user-identifiable information beyond our controlled experiment is collected.
6. Discussion on Countermeasures
6.1. Attack Detectability
6.2. Potential Mitigations
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Dingledine, R.; Mathewson, N.; Syverson, P. Tor: The Second-Generation Onion Router. In Proceedings of the 13th USENIX Security Symposium, San Diego, CA, USA, 9–13 August 2004; pp. 303–320. [Google Scholar]
- Jeffries, A. The Pentagon Is Trying to Make the Internet More Anonymous. The Verge, 16 June 2014. Available online: https://www.theverge.com/2014/6/16/5814776/the-pentagon-isbuilding-ways-to-make-the-internet-more-anonymous (accessed on 13 March 2025).
- Edman, M.; Yener, B. On anonymity in an electronic society: A survey of anonymous communication systems. ACM Comput. Surv. 2009, 42, 1–35. [Google Scholar] [CrossRef]
- Christin, N. Traveling the Silk Road: A Measurement Analysis of a Large Anonymous Online Marketplace. In Proceedings of the 22nd International World Wide Web Conference, Rio de Janeiro, Brazil, 13–17 May 2013; pp. 213–224. [Google Scholar]
- Weimann, G. Terrorist Migration to the Dark Web. Perspect. Terrorism 2016, 10, 40–44. [Google Scholar]
- Tor Project. August 2008 Progress Report. In The Tor Project Blog, August 2008. Available online: https://blog.torproject.org/august-2008-progress-report/ (accessed on 18 March 2025).
- Ling, Z.; Luo, J.; Wu, K.; Fu, X. Protocol-level hidden server discovery. In Proceedings of the IEEE Conference on Computer Communications (INFOCOM), Turin, Italy, 14–19 April 2013; pp. 1043–1051. [Google Scholar]
- Bauer, K.; McCoy, D.; Grunwald, D.; Kohno, T.; Sicker, D. Low-resource routing attacks against Tor. In Proceedings of the ACM Workshop on Privacy in the Electronic Society, Alexandria, VA, USA, 29–30 October 2007; pp. 11–20. [Google Scholar]
- Bauer, K.S.; Grunwald, D.; Sicker, D.C. Predicting Tor path compromise by exit port. In Proceedings of the 28th International Performance Computing and Communications Conference, Phoenix, AZ, USA, 14–16 December 2009; pp. 384–387. [Google Scholar]
- Tor Project. Bandwidth Authority Measurements. Tor Project Network Health. Available online: https://tpo.pages.torproject.net/network-health/bandwidth_scanners/bandwidth_authority_measurements.html (accessed on 27 March 2025).
- Abbott, T.G.; Lai, K.J.; Lieberman, M.R.; Price, E.C. Browser-based attacks on Tor. In Proceedings of the 7th International Symposium on Privacy Enhancing Technologies, Ottawa, ON, Canada, 10–12 June 2007; pp. 184–199. [Google Scholar]
- Wang, X.; Luo, J.; Yang, M.; Ling, Z. A potential HTTP-based application-level attack against Tor. Future Gener. Comput. Syst. 2011, 27, 67–77. [Google Scholar] [CrossRef]
- Tor Project. HTTPS Everywhere. In Tor Project Support Glossary. Available online: https://support.torproject.org/glossary/https-everywhere/ (accessed on 27 March 2025).
- Fu, X.; Ling, Z.; Luo, J.; Yu, W.; Jia, W.; Zhao, W. One cell is enough to break Tor’s anonymity. In Proceedings of the Black Hat Technical Security Conference, Las Vegas, NV, USA, 25–30 July 2009; pp. 578–589. [Google Scholar]
- Ling, Z.; Luo, J.; Yu, W.; Fu, X.; Xuan, D.; Jia, W. A New cell-counting-based attack against Tor. IEEE/ACM Trans. Netw. 2012, 20, 1245–1261. [Google Scholar] [CrossRef]
- Rochet, F.; Pereira, O. Dropping on the edge: Flexibility and traffic confirmation in onion routing protocols. Proc. Priv. Enhancing Technol. 2018, 2018, 27–46. [Google Scholar] [CrossRef]
- Perry, M. Vanguards Technical README. In Vanguards GitHub Repository. Available online: https://github.com/mikeperry-tor/vanguards/blob/master/README_TECHNICAL.md (accessed on 27 March 2025).
- Øverlier, L.; Syverson, P. Locating hidden servers. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 21–24 May 2006; pp. 100–114. [Google Scholar]
- Tor Project. Entry Guards. In Tor Project Support. Available online: https://support.torproject.org/about/entry-guards/ (accessed on 27 March 2025).
- Biryukov, A.; Pustogarov, I.; Weinmann, R.-P. Trawling for Tor hidden services: Detection, measurement, deanonymization. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013; pp. 80–94. [Google Scholar]
- Chakravarty, S.; Barbera, M.V.; Portokalidis, G.; Polychronakis, M.; Keromytis, A.D. On the effectiveness of traffic analysis against anonymity networks using flow records. In Proceedings of the 15th International Conference on Passive and Active Network Measurement, Los Angeles, CA, USA, 10–11 March 2014; pp. 247–257. [Google Scholar]
- Iacovazzi, A.; Sarda, S.; Elovici, Y. Inflow: Inverse network flow watermarking for detecting hidden servers. In Proceedings of the IEEE Conference on Computer Communications (INFOCOM), Honolulu, HI, USA, 16–19 April 2018; pp. 747–755. [Google Scholar]
- Iacovazzi, A.; Frassinelli, D.; Elovici, Y. The DUSTER attack: Tor onion service attribution based on flow watermarking with track hiding. In Proceedings of the 22nd International Symposium on Research in Attacks, Intrusions, and Defenses (RAID), Beijing, China, 23–25 September 2019; pp. 213–225. [Google Scholar]
- Fifield, D.; Perry, M. Proposal 324: Congestion Control Using Round Trip Time Measurements. Tor Project, Proposal 324, 2020. Available online: https://spec.torproject.org/proposals/324-rtt-congestion-control.txt (accessed on 27 March 2025).
- Dingledine, R.; Mathewson, N. Tor Path Specification. Tor Project Specification, Version 3, 2021. Available online: https://spec.torproject.org/path-spec/index.html (accessed on 27 April 2025).
- Tor Project. Tor Security Advisory: “Relay Early” Traffic Confirmation Attack. In The Tor Project Blog, 30 July 2014. Available online: https://blog.torproject.org/tor-security-advisory-relay-early-traffic-confirmation-attack (accessed on 14 April 2025).
- Tor Project. Tor Protocol Specification. Tor Project Specification Repository. Available online: https://spec.torproject.org/ (accessed on 16 April 2025).
- Nusenu. Is “KAX17” Performing De-Anonymization Attacks against Tor Users? Medium, 29 November 2021. Available online: https://nusenu.medium.com/is-kax17-performing-de-anonymization-attacks-against-tor-users-42e566defce8 (accessed on 30 July 2025).
- Tor Project. Tor Metrics. Official Network Statistics Portal. Available online: https://metrics.torproject.org/ (accessed on 27 April 2025).
- Dingledine, R. The Lifecycle of a New Relay. Available online: https://blog.torproject.org/lifecycle-of-a-new-relay/ (accessed on 27 April 2025).
- Tor Project. Research Safety Board. Available online: https://research.torproject.org/safetyboard/ (accessed on 27 April 2025).





| Sequence | Rel_cmd | Src → Dst | COP | COR1 | COR2 | COR3 |
|---|---|---|---|---|---|---|
| COP = 8 | COR1 = 8 | COR2 = 8 | COR3 = 8 | |||
| 1st | EXTEND | OP → OR1 | COP = 7 | COR1 = 7 | COR2 = 8 | COR3 = 8 |
| 2nd | EXTEND | OP → OR2 | COP = 6 | COR1 = 6 | COR2 = 7 | COR3 = 8 |
| 3rd | OP → OR3 | COP = 5 | COR1 = 5 | COR2 = 6 | COR3 = 7 | |
| 4th | OP → OR3 | COP = 4 | COR1 = 4 | COR2 = 5 | COR3 = 6 | |
| 5th | OP → OR3 | COP = 3 | COR1 = 3 | COR2 = 4 | COR3 = 5 | |
| 6th | OP → OR3 | COP = 2 | COR1 = 2 | COR2 = 3 | COR3 = 4 | |
| 7th | OP → OR3 | COP = 1 | COR1 = 1 | COR2 = 2 | COR3 = 3 | |
| 8th | OP → OR3 | COP = 0 | COR1 = 0 | COR2 = 1 | COR3 = 2 |
| Cell Sequence | Received | Malicious Router Action | Sent | Signal Field |
|---|---|---|---|---|
| 1st | RELAY_EARLYEXTEND | Injector mode | CREATE | - |
| 2nd | RELAY_EARLY | Forward | RELAY_EARLY | Reserved |
| 3rd | RELAY_EARLY | Forward | RELAY_EARLY | |
| 4th | [Cmd] | [Cmd] → RELAY | RELAY | Start Delimiter |
| 5th | [Cmd] | [Cmd] → RELAY_EARLY | RELAY_EARLY | |
| th | [Cmd] × | [Cmd] × → RELAY × | RELAY × | Payload |
| th | [Cmd] | [Cmd] → RELAY_EARLY | RELAY_EARLY | |
| th | [Cmd] × | [Cmd] × → RELAY × | RELAY × | |
| th | [Cmd] | [Cmd] → RELAY_EARLY | RELAY_EARLY | |
| th | [Cmd] × | [Cmd] × → RELAY × | RELAY × | |
| th | [Cmd] | [Cmd] → RELAY_EARLY | RELAY_EARLY | |
| th | [Cmd] × | [Cmd] × → RELAY × | RELAY × | |
| th | [Cmd] | [Cmd] → RELAY_EARLY | RELAY_EARLY | |
| th | [Cmd] × | [Cmd] × → RELAY × | RELAY × | |
| th | [Cmd] | [Cmd] → RELAY_EARLY | RELAY_EARLY | End Delimiter |
| Circ. Type | Circ. Path | Injector Positions and Signal Properties | Reason for Ineffectiveness |
|---|---|---|---|
| External_ClientSide | OR1 -…- OR3 (Exit) | Out-of-order signal Incomplete signal Improper position | |
| Rend_ServerSide | OR1 -…- OR4 (Rendezvous) | ||
| Intro_ClientSide | OR1 -…- OR4 (Introduction) | ||
| Rend_ClientSide | OR1 -…- OR3 (Rendezvous) | ||
| Intro_ServerSide | OR1 -…- OR3 (Introduction) |
| Topology No. | Injector Node | Detector Node | Validation Objective |
|---|---|---|---|
| 1st | OR1 | None | |
| 2nd | OR2 | None | |
| 3rd | OR1 | OR3 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xin, R.; Wang, Y.; Huang, X.; Yang, X.; Im, S.K. Cell-Sequence-Based Covert Signal for Tor De-Anonymization Attacks. Future Internet 2025, 17, 403. https://doi.org/10.3390/fi17090403
Xin R, Wang Y, Huang X, Yang X, Im SK. Cell-Sequence-Based Covert Signal for Tor De-Anonymization Attacks. Future Internet. 2025; 17(9):403. https://doi.org/10.3390/fi17090403
Chicago/Turabian StyleXin, Ran, Yapeng Wang, Xiaohong Huang, Xu Yang, and Sio Kei Im. 2025. "Cell-Sequence-Based Covert Signal for Tor De-Anonymization Attacks" Future Internet 17, no. 9: 403. https://doi.org/10.3390/fi17090403
APA StyleXin, R., Wang, Y., Huang, X., Yang, X., & Im, S. K. (2025). Cell-Sequence-Based Covert Signal for Tor De-Anonymization Attacks. Future Internet, 17(9), 403. https://doi.org/10.3390/fi17090403







