The Adaptive Ecosystem of MaaS-Driven Cookie Theft: Dynamics, Anticipatory Analysis Concepts, and Proactive Defenses
Abstract
1. Introduction
1.1. The Inadequacy of Reactive Defense Paradigms
1.2. Scope, Contributions, and Structure
- Novel Ecosystem Characterization (Section 4): We delineate the adaptive ecosystem by introducing a comprehensive conceptual model that uniquely maps the interdependencies, resource flows, key actors, economic incentives, and critical feedback loops that sustain this illicit economy.
- Systematic and Comparative Tactical Analysis (Section 6 and Section 7): We present a systematic deconstruction and visual comparative analysis of the co-evolving offensive and defensive strategies, evaluating their operational mechanics and strategic trade-offs to provide a clear view of the current arms race.
- A Conceptual Framework for Predictive Analytics (Section 8): We propose an innovative, multi-dimensional framework and a formal algorithm designed to anticipate future trajectories of the MaaS-driven cookie theft ecosystem by integrating disparate technical, economic, and behavioral indicators.
- Actionable Proactive Defense Guidance (Section 8): We consolidate our insights into a novel decision-tree framework designed to assist organizations in selecting appropriate defensive techniques tailored to their specific contexts, addressing a practical gap in translating threat understanding into strategic posture.
2. Methodology: A Holistic and Integrative Review
- RQ1: What are the key actors, interdependencies, and economic drivers that constitute the MaaS-driven cookie theft ecosystem?
- RQ2: How have offensive cookie theft techniques and corresponding defensive strategies co-evolved from January 2020 to May 2025?
- RQ3: What are the conceptual foundations for a framework that can anticipate future threat trajectories in this ecosystem?
- RQ4: What are the primary open challenges and future research directions for effectively countering this threat?
2.1. Search Strategy and Source Selection
- Academic Databases: Searches were conducted in key scientific databases, including IEEE Xplore, ACM Digital Library, SpringerLink, and Google Scholar. Keywords included combinations of “cookie theft,” “session hijacking,” “infostealer malware,” “Malware-as-a-Service,” “cybercrime economics,” and “proactive defense”.
- Grey Literature (Industry and Vendor Intelligence): Recognizing that cutting-edge threat intelligence often originates outside of academia, we systematically reviewed reports from leading cybersecurity vendors (e.g., Secureworks, Kaspersky, SpyCloud, and Mandiant), security news outlets (e.g., The Hacker News), and government agency publications (e.g., CISA and ENISA).
- Backward and Forward Snowballing: The reference lists of key foundational papers and reports were reviewed to identify additional relevant sources (backward snowballing). We also tracked new publications that cited these key sources (forward snowballing) to ensure inclusion of the latest research.
2.2. Inclusion and Exclusion Criteria
2.3. Data Synthesis and Analysis
3. State-of-the-Art and Literature Review
3.1. Analysis of the MaaS Ecosystem and Cybercrime Economics
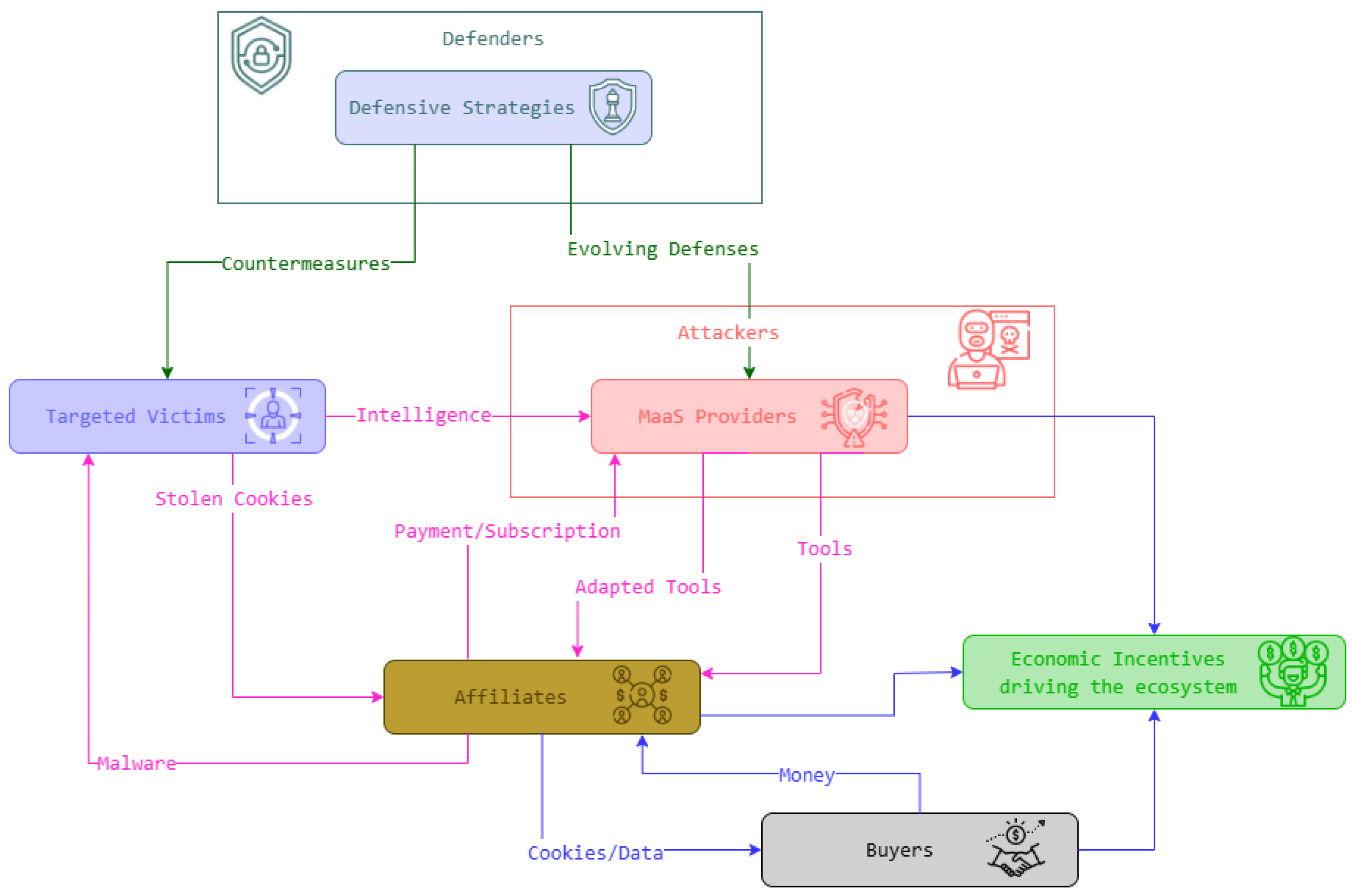
- Identified Gap: A primary limitation of this body of work is the frequent separation between economic analysis and the evolution of technical Tactics, Techniques, and Procedures (TTPs). While these studies expertly detail the financial incentives, they often do not provide a granular, integrated model that explicitly links specific economic drivers (e.g., a drop in cookie prices) or external pressures (e.g., a law enforcement takedown as detailed by Europol [81]) to corresponding shifts in malware development or attacker strategy. The cause-and-effect feedback loops that sustain the ecosystem—a central focus of our work (Figure 2)—remain undertheorized.
3.2. Studies on Technical Exploit and Defense Mechanics
- Identified Gap: These technical analyses, while valuable, are often presented in isolation. A paper on ZTA will comprehensively cover its implementation, and a report on an infostealer will detail its TTPs. However, there is a notable lack of a systematic, comparative synthesis that places these offensive and defensive techniques in direct opposition to one another to analyze the “arms race” dynamically. A holistic view that evaluates the strategic trade-offs of cost, complexity, and effectiveness for both sides is missing.
3.3. Research into Advanced Analytical and Predictive Concepts
- Identified Gap: While these papers establish the promise of predictive and AI-driven security, they often remain at a high conceptual level or focus on generic threat detection rather than on a specific, industrialized ecosystem like MaaS-driven cookie theft. There is a lack of a concrete, multi-dimensional predictive framework designed specifically to anticipate shifts within this ecosystem by integrating the disparate data sources—technical, economic, and behavioral—that define it.
4. The Foundational Concepts of MaaS-Driven Cookie Theft
4.1. The HTTP Cookie as a Session Bearer Token
- A user authenticates with a service, typically by providing credentials (e.g., username/password) and passing a Multi-Factor Authentication (MFA) challenge.
- Upon successful authentication, the server generates a unique, temporary identifier known as a session token and sends it to the user’s browser encapsulated within an HTTP cookie.
- The browser stores this cookie. For all subsequent requests to that domain, the browser automatically includes the session cookie in the HTTP headers.
- The server validates this cookie on each request to identify the user and serve them the appropriate content for their authenticated session, without requiring re-authentication for every action.
4.2. The Adaptive Ecosystem
5. Key Challenges in Countering Adaptive Cookie Theft
5.1. Rapid Evolution of Attacker Techniques
5.2. The Scale and Speed of MaaS Dissemination
5.3. The Economic Engine: Quantifying the MaaS Profit and Reinvestment Cycle
5.4. Complexity and Operational Overhead of Proactive Measures
6. Counter-Strategies in the Adaptive Arms Race
6.1. Attacker Adaptive Strategies
- AI-Driven Evasion Techniques: This involves using Machine Learning (ML), such as generative models, to create polymorphic or metamorphic malware. Instead of using static, reusable code, attackers employ AI to automatically alter the malware’s structure such as randomizing function names, changing control flow, or re-ordering data structures with each new build. The goal is to generate functionally identical but syntactically unique variants that do not match the static fingerprints used by traditional antivirus (AV) and signature-based detection systems [12,13,22]. Furthermore, adversarial perturbation can subtly modify malware traffic patterns to fool network-based ML detectors without impacting the core malicious functionality [39,41,42].
- Dynamic Command and Control (C2) Infrastructure: To prevent their C2 servers from being easily blocked or sinkholed, attackers use techniques to make their infrastructure ephemeral. Domain Generation Algorithms (DGAs) programmatically create thousands of potential C2 domain names daily, with the malware attempting to contact them until it finds the one the attacker has actually registered [43,44]. This makes proactive domain blacklisting nearly impossible. Fast Flux networks add another layer of evasion by rapidly changing the IP addresses associated with a single malicious domain in the DNS records, sometimes rotating every few minutes, as noted by CISA [14,15,45].
- Living Off The Land (LotL): This strategy involves the use of legitimate, pre-installed system tools for malicious purposes. Instead of dropping custom malicious executables that can be easily flagged, attackers use trusted utilities already present on the system, such as PowerShell, Windows Management Instrumentation (WMI), or certutil.exe. For cookie theft, an attacker might use PowerShell to query the sqlite3 database where Chrome stores cookies and then use certutil to base64-encode the stolen data for exfiltration. This malicious activity blends in with legitimate administrative traffic, making it incredibly difficult for security tools focused on spotting known-bad files to detect [27,28,85].
- Hook Randomization: Security products like Endpoint Detection and Response (EDR) tools often “hook” critical Application Programming Interfaces (APIs) or system calls to monitor for malicious behavior. Advanced malware employs anti-hooking techniques to counteract this. It may detect that a function (e.g., in kernel32.dll) is hooked and then either remove the hook or, more sophisticatedly, bypass the hooked function entirely by calling the underlying, lower-level function directly in ntdll.dll (a direct syscall). This allows the malware to perform its malicious actions (e.g., process injection) without triggering the security tool’s monitoring system [23,29].
- Environment-Aware Payloads: This refers to malware designed to first perform reconnaissance on its execution environment before detonating its main payload. The goal is to detect and evade automated analysis sandboxes used by security researchers. The malware checks for signs of a virtualized or analytical environment, such as the presence of VMWare or VirtualBox drivers, specific usernames (e.g., “analyst” or “sandbox”), a low CPU core count, or a lack of recent user interaction (mouse movements and open documents). If a sandbox is detected, the malware remains dormant, showing no malicious behavior and thus receiving a “benign” classification. It will only activate its payload on what it assesses to be a genuine user system [1,13,30].
6.2. Proactive Defender Strategies
- Deception-Based and Adversarial Hardening: These strategies focus on misleading attackers and hardening defenses against intelligent evasion:
- Honeypots and Decoy Systems: These are deception-based defenses that create attractive, monitored targets for attackers. A honeypot is a decoy system (e.g., a fake server) designed to be attacked, allowing defenders to study adversary TTPs in a safe environment. A honeytoken is a more granular decoy asset, such as a fake AWS API key, a Canary token, or a planted session cookie placed in a specific file path. If this token is ever accessed or used, it triggers a high-confidence alert, providing an early warning of a breach long before legitimate systems are impacted [65,66,81].
- Adversarial Training for Machine Learning Models: Standard ML detection models are vulnerable to evasion. Adversarial training is a technique to make these models more robust by explicitly training them not just on benign and malicious samples, but also on specially crafted adversarial examples—malicious inputs that are intentionally modified to look benign. By including these deceptive samples in the training set, the model learns to recognize the subtle patterns of evasion, hardening it against future, unseen morphing techniques and AI-driven attacks [13,37,40,42].
- Architectural and Opportunity-Reduction Defenses: This category includes fundamental shifts in security architecture and tactics that shrink the attacker’s window of opportunity:
- Ephemeral Session Tokens: This strategy directly targets the value of stolen cookies by drastically reducing their lifespan. Instead of issuing session tokens that are valid for hours or days, applications are configured to issue tokens with a very short Time-To-Live (TTL), for instance, 5–10 min. While this may require more frequent, seamless re-authentication for the user (e.g., via refresh tokens), it means that a stolen cookie becomes useless almost immediately after it is exfiltrated and put up for sale, thus disrupting the economic incentives of the attacker [63,64].
- ZTA: This is a security model built on the principle of “never trust, always verify”. ZTA eliminates the outdated concept of a trusted internal network where lateral movement is easy. Instead, every access request—regardless of its origin—must be continuously and explicitly verified against policies that check user identity, device health, and other contextual signals. In a ZTA environment, a stolen cookie is insufficient on its own to gain access to a critical application, as a ZTA policy would likely trigger a step-up MFA challenge or block the request based on an unrecognized device posture, thus containing the breach [59,61,67,68,69].
- Moving Target Defense (MTD): MTD is a proactive defense strategy that increases attacker complexity by continuously and unpredictably changing the attack surface. Instead of a static environment that attackers can map and plan against, MTD techniques dynamically alter system and network characteristics. Examples include randomizing memory layouts (ASLR), shuffling network port numbers, rotating IP addresses, or cycling through different virtual machine instances. This makes reconnaissance data obsolete almost instantly and breaks static, hard-coded exploits, forcing the attacker to expend significantly more effort [28,62].
- Dynamic and Analytical Defenses: These approaches rely on continuous monitoring, intelligence, and real-time adaptation to detect and respond to threats as they emerge:
- Proactive Threat Hunting: This is a human-driven, intelligence-led process where analysts actively search for signs of compromise, assuming that automated defenses have already been bypassed. Instead of waiting for an alert, threat hunters form hypotheses based on threat intelligence (e.g., “We believe MaaS Group X uses scheduled tasks for persistence”) and then systematically query endpoint and network telemetry (e.g., EDR logs AND SIEM data) for subtle evidence of those specific TTPs. This allows for the detection of advanced adversaries who use LotL techniques and other stealthy methods [38,47,48].
- Dynamic Policy Enforcement: This involves creating security policies that can adapt automatically in real-time based on changing risk signals. For example, a system can be configured to monitor post-authentication user behavior. If a session, initially authenticated with a valid cookie, suddenly starts accessing unusual resources or exhibiting behavior patterns that deviate from the user’s baseline, a dynamic policy can automatically trigger a risk response. This could range from forcing an MFA re-prompt to limiting the session’s privileges or terminating it altogether, neutralizing the threat from a hijacked session [38,49,71,72].
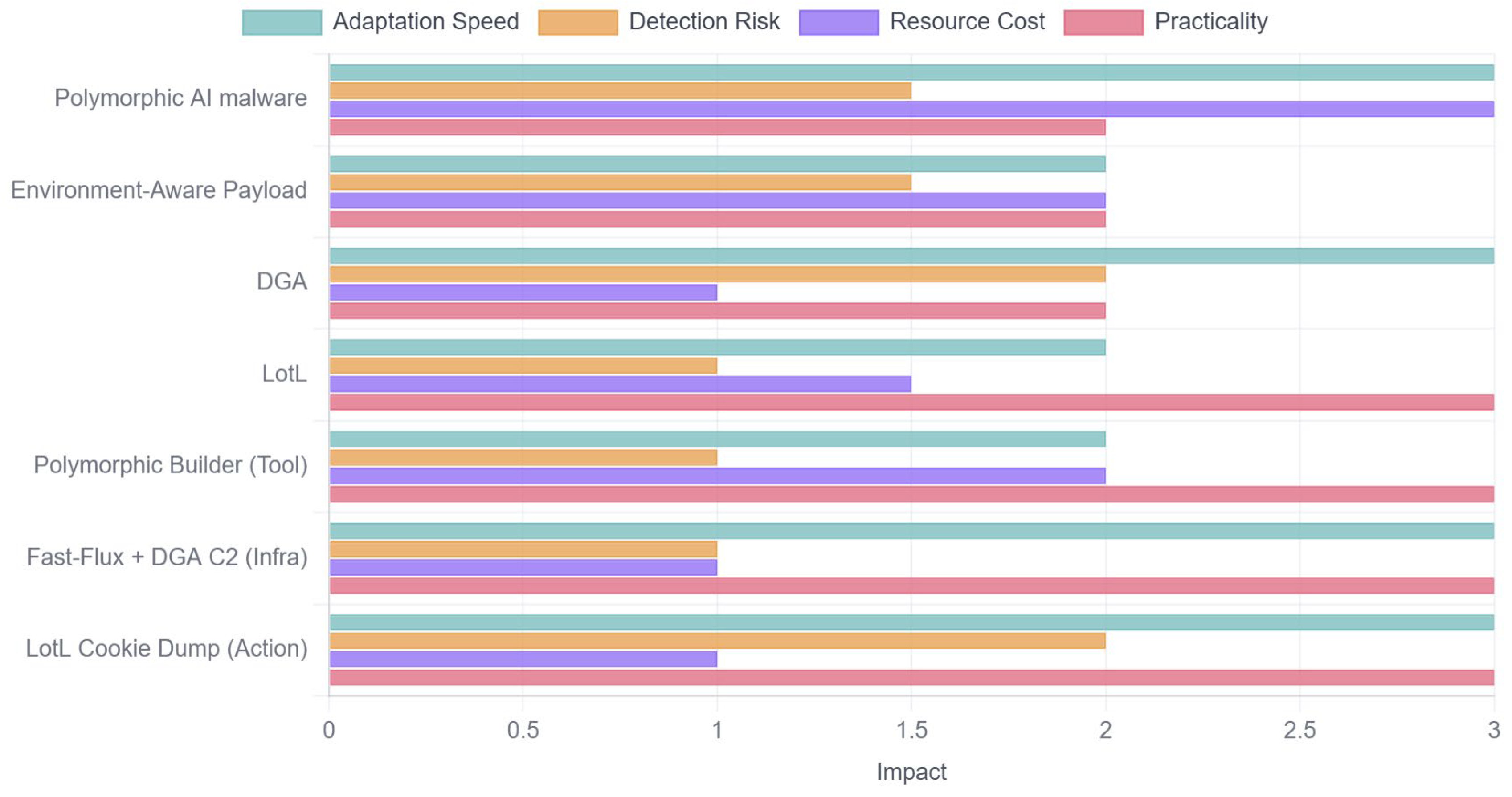
7. Comparative Analysis and Cross-Cutting Perspectives
- Adaptation Speed: This metric assesses the agility and velocity with which a technique can be deployed, modified, or reconfigured. A “High” score (2–3) indicates a technique that can be adapted in near real-time (e.g., rotating C2 infrastructure in minutes), while a “Low” score (0–1) reflects a structural or long-term implementation (e.g., a multi-quarter ZTA rollout).
- Detection Risk: This evaluates the likelihood of a technique being detected by an adversary. For attacker techniques, it represents the risk of being caught by defensive systems. For defender techniques, it represents the efficacy of the defense in detecting an attack (i.e., the risk imposed upon the attacker).
- Resource Cost: This is a composite metric representing the total investment required. A “High” score (2–3) signifies a substantial investment in one or more of the following areas: (i) Computational/Infrastructure Cost (e.g., requiring significant GPU power for ML model training or extensive cloud services); (ii) Human Expertise Cost (e.g., requiring a dedicated team of skilled security analysts or data scientists); and (iii) Operational Complexity Cost (e.g., high management overhead or potential for user friction). A “Low” score (0–1) implies the technique is cheap and requires minimal specialized resources.
- Practicality: This metric measures the ease of deployment and management. A “High” score (2–3) indicates a technique is highly accessible and requires minimal specialized knowledge to implement (e.g., using a pre-built MaaS tool), whereas a “Low” score (0–1) indicates a complex, bespoke implementation requiring significant planning and integration effort.
7.1. Trends and Dominant Methods
7.2. Case Studies
- Industrial IoT (IIoT): A Belgian smart-manufacturing plant suffered a Meduza stealer infection via an Open Platform Communications Unified Architecture (OPC UA) gateway, harvesting 9320 browser cookies, causing a 12 h production halt (€380,000 downtime). Planted honeytokens alerted the Security Operations Center (SOC) in 18 min, limiting token resale to 3% of stolen [66]. Simulations of adaptive filtering at the edge against adversarial data injection (mimicking behavioral analysis targeting) showed a 30% reduction in false positives and a 15% increase in genuine anomaly detection [51,52].
- Smart Healthcare: A US hospital system saw a Lumma-loader (via malicious insulin-pump firmware) collect 22,141 session cookies for EHR portals in 24 h [8,31]. Ephemeral tokens (5–10 min validity) reduced unauthorized access windows from hours to minutes [63]. Lightweight ZTA (requiring re-authentication for sensitive record access) led to a 95% decrease in simulated unauthorized data exfiltration [59,67]. Device-bound access proxies invalidated 97% of token replay attempts [35,64].
- Environmental Monitoring: An EU climate-sensor network (RedLine infostealer) had 1400 Raspberry Pi nodes compromised and 6500 cookies stolen [82]. Dynamic policy enforcement (analyzing data stream consistency, location, and patterns) detected malicious data injection 40% faster than static alerts. Proactive Threat Hunting for LotL on gateways identified persistence 50% faster in simulations [38]. MTD (shuffling network configurations) reduced C2 callbacks by 64% in the first rotation.
8. From Prediction to Disruption: A Proactive Framework
8.1. Conceptual Multi-Dimensional Predictive Framework
Framework Concept and Potential Data Requirements
- Data collection (ongoing and from 2020–2025 for foundational understanding):Synthesizing data from diverse sources would be essential, including the following:
- Dark Web Market Data: Aggregated and anonymized data from major dark web marketplaces focusing on cookie/bot profile listings (pricing, volume, and features) [78].
- MaaS Provider Channels: Monitoring of prominent MaaS provider communication channels (e.g., on Telegram) for announcements.
- Enterprise Security Logs: Anonymized telemetry from participating organizations (web proxy, authentication, Endpoint Detection and Response (EDR), and SIEM).
- Public Threat Intelligence Feeds and Security Reports: IOCs, TTPs, and malware analyses.
- Potential feature engineering:Indicators would need to be extracted and quantified:
- Technical Indicators: Reflect evolving attacker capabilities and defense effectiveness, including the prevalence of new malware obfuscation techniques (e.g., malware family entropy change and novel API call sequences); frequency of zero-day browser session exploits; new malware-hash velocity; DGA domain entropy [43,44]; TLS JA3 fingerprints; and also, adoption rates of advanced defenses (ZTA [67], behavioral analytics [38], and EDR) and average time-to-patch.
- Economic Indicators: Reflect financial underpinnings, including average price of stolen cookie sets; cost of MaaS subscriptions/malware builds [5,9]; dark-web cookie-price medians; affiliate-program revenue–share ratios; volumes in criminal escrow services [77]; and also, trends in legitimate cybersecurity spending.
- Behavioral Indicators: Capture human, organizational, and collaborative elements, including shifts in attacker targeting patterns (industry verticals and geographic regions); Telegram-channel MaaS builder ID/C2 address bursts; and also, organizational adoption speed of security best practices and proactive defenses (Table 3); and volume, timeliness, and quality of shared threat intelligence on new TTPs and countermeasures.
- Potential model selection and training (future work):
- The target variable could be, for example, a binary classification predicting significant spikes in new dark-web cookie-bot listings within a defined future window (e.g., 72 h).
- Rigorous data splitting, hyperparameter tuning, and cross-validation would be essential in any future development.
- Future validation (essential step):
- Any developed model would require extensive validation using appropriate metrics (e.g., F1 score, Precision, Recall, and Area Under the Receiver Operating Characteristic Curve (AUC-ROC)) on held-out test data and ideally in pilot studies within operational SOC environments to assess real-world efficacy and practical utility.
8.2. Algorithmic Formalization of the Predictive Framework
8.2.1. Parameters and Notation
- D: The complete multi-modal time-series dataset.
- t: A discrete time step (e.g., one hour or one day).
- X_t: The feature vector at time t.
- Y_t: The target variable (event) at time t.
- L: The lookback window (number of past time steps used for feature engineering).
- H: The prediction horizon (number of future time steps to predict).
- θ_event: The threshold for defining a significant event.
- P(Y_{t + H}|X_t): The probabilistic forecast of the event Y at time t + H, given the feature vector at time t.
8.2.2. Algorithm Steps
Phase 1: Data Ingestion and Temporal Alignment
- Establish Data Streams: Configure collectors (e.g., APIs, web scrapers, and log forwarders) for the three core data dimensions:
- Technical (Tech): EDR/SIEM telemetry (e.g., malware hash counts), public vulnerability feeds, threat intelligence platform IOCs (e.g., DGA domain lists), and network sensor data (e.g., JA3/JA3S hashes).
- Economic (Econ): Dark-web market scrapers (for cookie/log prices and volumes), MaaS provider subscription costs (from public channels like Telegram), and cryptocurrency transaction data associated with known threat actor wallets.
- Behavioral (Behav): MaaS provider channel monitoring (new builder IDs and announcements), targeting data from incident reports (industry/geography), and security community discussions (new defense adoption rates).
- Synchronize and Resample: Align all data streams onto a single temporal index at a fixed frequency t (e.g., t = 1 h). Use appropriate resampling methods (e.g., forward-fill for stateful data and summation for event counts) to handle missing data and different native frequencies. Store in a time-series database D.
Phase 2: Feature Engineering and Vectorization
- For each time step t, construct the feature vector X_t.
- Transform Raw Indicators:
- Tech(t):
- Malware hash velocity: count(new_hashes_t).
- DGA domain entropy: mean_shannon_entropy(domains_t).
- Zero-day exploit frequency: count(new_CVEs_t) related to browsers.
- Defense adoption: percentage(organizations_with_ZTA_policy_t).
- Econ(t):
- Cookie price median/volatility: median(price_t), stddev(price_t).
- MaaS subscription cost: cost(MaaS_kit_t).
- Affiliate revenue share: ratio(affiliate_payout_t).
- Behav(t):
- MaaS builder ID bursts: count(new_builder_IDs_t).
- Targeting shifts: one_hot_encode(targeted_industries_t).
- Generate Time-Series Features: For each transformed indicator i, create lagged and windowed features over the lookback period L:
- Lagged values: i_{t − 1}, i_{t − 2}, …, i_{t − L}.
- Rolling window statistics: mean(i_{t − L:t}), stddev(i_{t − L:t}), max(i_{t − L:t}).
- Momentum/Derivatives: i_t − i_{t − 1} (first difference), (i_t − i_{t − L})/L (slope).
- Concatenate all features to form the final high-dimensional feature vector X_t.
Phase 3: Target Variable Definition
- Define the Event to Predict: Based on the paper’s example, we define the target Y as a binary classification task: “forecasting a significant spike in dark-web cookie-bot listings.”
- Formalize the Target Y_{t + H}:
- Let N_t be the number of new cookie-bot listings on dark-web markets at time t.
- Calculate the rolling mean μ_N(t) and standard deviation σ_N(t) of N over a long-term window (e.g., 30 days).
- The target variable for a prediction made at time t is as follows:Y_{t + H} = 1 if N_{t + H} > (μ_N(t) + k * σ_N(t)), else 0.(where k is a sensitivity parameter, e.g., k = 3 for a three-sigma event).
Phase 4: Model Training and Selection
- Time-Series Data Splitting: Partition the dataset D chronologically. Do not use random k-fold cross-validation to avoid data leakage from the future.
- D_train: e.g., data from 2020-01-01 to 2023-12-31.
- D_validation: e.g., data from 2024-01-01 to 2024-12-31.
- D_test: e.g., data from 2025-01-01 to present (held-out set).
- Model Selection:
- Instantiate a GBDT model (e.g., XGBoost and LightGBM). These models inherently handle feature scaling, interactions, and mixed data types well.
- Hyperparameter Optimization: Use D_train and D_validation with a time-series cross-validation scheme (e.g., sliding window or forward-chaining validation) to tune key hyperparameters (e.g., n_estimators, learning_rate, and max_depth). Optimize for a primary metric like AUC-ROC or F1-score.
- Final Model Training: Train the final model M with the optimal hyperparameters on the combined D_train + D_validation dataset.
Phase 5: Model Evaluation and Validation
- Performance on Hold-Out Set: Evaluate the trained model M on the unseen D_test.
- Calculate Key Metrics:
- Discrimination: AUC-ROC and Precision-Recall AUC (PR-AUC).
- Classification Accuracy: F1-score, Precision, Recall, and Specificity.
- Analyze the Confusion Matrix: Critically assess the trade-off between false positives (leading to alert fatigue in a SOC) and false negatives (missed threats).
- Feature Importance Analysis: Use model-agnostic methods (e.g., SHAP—SHapley Additive exPlanations) to understand which indicators (technical, economic, or behavioral) are the primary drivers of predictions. This provides crucial insight back into the ecosystem’s dynamics.
Phase 6: Deployment, Inference, and Feedback Loop
- Operationalization: Deploy the serialized model M into a production environment.
- Inference Pipeline:
- At each time step t, run the data ingestion and feature engineering pipeline (Phase 1 and 2) to generate the current feature vector X_t.
- Feed X_t to model M to get the forecast P(Y_{t + H} = 1|X_t).
- If P > θ_confidence (a predefined confidence threshold), generate a strategic alert for SOC analysts or threat intelligence teams, enriched with the top contributing features from the SHAP analysis.
- Feedback Loop and Model Retraining:
- Continuously collect new data (D_new) and ground truth (Y_new).
- Monitor the model’s performance in production for signs of concept drift (i.e., when the statistical properties of the relationship between X and Y change).
- Periodically (e.g., quarterly) or based on performance degradation triggers, retrain the model M using the updated dataset D U D_new to adapt to the evolving threat landscape, fulfilling the feedback loop in Figure 5.
8.3. Disrupting the Economic Model
- Operational Takedowns and Infrastructure Disruption: Law enforcement actions, such as Europol’s “Operation Endgame” [79], which dismantled bulletproof hosting infrastructure, directly increase MaaS operational costs and disrupt service availability. Such actions demonstrably impact the MaaS economy, evidenced by phenomena like the 23% Lumma MaaS fee increase following the 2025 “Operation Endgame” sinkhole [79], as criminals sought more resilient, and thus more expensive, infrastructure.
- Financial Disruption and Collaborative Models:
- With Financial Institutions: Establishing dedicated channels for rapid identification and freezing of accounts associated with MaaS subscriptions, affiliate payouts, or laundering of illicit proceeds. This includes collaboration on typologies of suspicious financial activities linked to MaaS operations [77].
- With Cryptocurrency Exchanges and Payment Processors: Implementing enhanced Anti-Money Laundering/Know Your Customer (AML/KYC) measures specifically targeting known MaaS operator wallets or marketplace addresses. Development of information-sharing agreements to trace and disrupt illicit financial flows through crypto-assets.
- With Law Enforcement: Fostering international public–private partnerships to facilitate intelligence sharing, enabling coordinated takedowns of MaaS C2 servers, marketplaces, and arrests of key actors.
- Economic Impact Studies: Commissioning and publicizing studies that quantify the direct and indirect financial losses attributable to MaaS-driven cookie theft for various sectors. Such data can galvanize industry investment in defenses, inform regulatory policy, and prioritize law enforcement resource allocation. For instance, demonstrating a multi-billion-dollar annual loss for the e-commerce sector due to ATO via stolen cookies would be a powerful motivator for change.
- Targeting Resale Markets: Collaborative efforts to monitor and disrupt dark web marketplaces where stolen cookies are traded. This can involve strategic purchasing by defenders for intelligence gathering or coordinated takedowns of market platforms.
8.4. Enhanced Threat Intelligence Sharing
8.5. AI for Offense and Defense
9. Open Challenges and Future Directions
- Developing and Validating Predictive Analytics Frameworks: A primary open challenge is the rigorous development, empirical validation, and operationalization of predictive analytics frameworks, like the conceptual one proposed in Section 6. Moving beyond a conceptual model requires addressing substantial practical hurdles. Future work must focus on developing robust data fusion techniques to ingest and correlate heterogeneous data sources, from unstructured, high-noise data on dark-web forums and Telegram channels to structured, high-volume telemetry from enterprise security tools. A critical research area is feature engineering for adversarial behavior, which involves quantifying abstract concepts like shifts in attacker TTPs or the emergence of new MaaS marketing language. Furthermore, any resulting models must undergo extensive, chronologically sound validation using techniques like forward-chaining cross-validation to prevent lookahead bias and ensure they provide genuine, actionable foresight into events like infostealer release waves or price drops for stolen credentials.
- Establishing Robust, Quantitative, and Standardized Ecosystem-Health Metrics: There is currently no consensus on standardized indices to measure the “health” or intensity of the cybercrime ecosystem. The predictive indicators in Section 6 are a starting point, but a more comprehensive suite of verifiable metrics is needed for benchmarking threat levels, measuring defensive ROI, and guiding policy. Future research could borrow from other fields; for instance, epidemiology’s “R-number” (basic reproduction number) could be adapted to model the propagation rate of a new malware variant or infostealer kit. Similarly, financial risk models like Value at Risk (VaR) could be transformed into “Account at Risk” metrics based on the volume and value of stolen cookies targeting a specific sector. Developing metrics such as “MaaS kit churn rate,” “average time-to-resale of a stolen cookie,” or “price elasticity of credential markets” would provide a common language for assessing the impact of defensive actions and long-term security posture effectiveness.
- Systemic Disruption of MaaS Infrastructure, Supply Chains, and Business Models: Takedowns like “Operation Endgame” show potential but also highlight the operational resilience of MaaS actors, who often leverage decentralized, jurisdictionally ambiguous infrastructure [79]. The challenge is to move from reactive, actor-specific takedowns to a strategy of systemic disruption that attacks the underlying business model. Future research should investigate more automated and scalable disruption techniques, such as the proactive sinkholing of emergent C2 infrastructures at the Autonomous System Number (ASN) level. A critical frontier lies in fostering deeper, operational partnerships with the private-sector linchpins of the internet: cloud service providers, domain registrars, ISPs, and cryptocurrency exchanges. Developing streamlined legal and technical frameworks for these entities to rapidly identify and dismantle MaaS-related resources would fundamentally increase the operational cost and risk for cybercriminals [77].
- Application of Advanced Analytical Techniques for Ecosystem Modeling: Understanding the MaaS ecosystem requires moving beyond static analysis to modeling the strategic interactions of its human actors. Advanced techniques like game theory and agent-based modeling (ABM) are essential for this purpose [80]. Future research should focus on developing sophisticated ABMs where MaaS providers, affiliates, and defenders are modeled as agents with distinct goals (e.g., maximizing profit and minimizing risk), strategies, and constraints. Such models would allow for complex simulations to test the second- and third-order effects of defensive strategies. For instance, one could model how a widespread adoption of ephemeral tokens might impact the MaaS affiliate recruitment market or force a pivot in malware development, identifying non-obvious leverage points for long-term ecosystem disruption [9,36,49].
- Addressing Usability, Operational Complexity, and User Experience of Proactive Defenses: As detailed in Table 3, many advanced defenses suffer from high operational overhead and complexity, hindering their widespread adoption. A significant challenge lies in making robust security both effective and manageable. Future work must focus on reducing analyst burden through AI-augmented security tools and Security Orchestration, Automation, and Response (SOAR) platforms that can automate the triage of low-level alerts. For collaborative defense, research into Privacy-Preserving Machine Learning (PPML) is critical. Technologies like federated learning and confidential computing could enable organizations to train powerful, shared predictive models on their collective security data without exposing sensitive proprietary information, thus overcoming major legal and competitive hurdles to threat intelligence sharing [48,56].
- Enhancing International Law Enforcement Collaboration: The borderless nature of cybercrime is in direct conflict with the jurisdictional limitations of national and local law enforcement agencies. This friction creates safe havens for MaaS operators and significantly delays cross-border investigations and prosecutions. A critical challenge is to move beyond ad-hoc international task forces to establishing more permanent, agile frameworks for collaboration [5,79]. Future efforts should focus on developing standardized international playbooks for digital evidence collection, sharing, and preservation. Fostering dedicated platforms for the real-time exchange of tactical intelligence and operational best practices between agencies like Europol’s EC3, INTERPOL, and national cybercrime units is essential to match the speed and global scale of MaaS operations [5,79].
- Improving User Education to Mitigate Social-Related Attacks: The initial vector for many cookie theft infections is not a technical vulnerability but a human one, typically stemming from phishing, malvertising, or the installation of trojanized software [1,6]. Traditional, annual compliance-based security awareness training is largely ineffective against the sophisticated social engineering tactics employed today [7]. The future direction must be towards continuous, context-aware, and behavior-focused education. This includes training users to recognize modern threats like SEO poisoning (malicious sites ranking high in search results), the risks of downloading “cracked” commercial software, and the specific danger of browser profile compromise [1,7]. By shifting the focus from generic awareness to specific digital hygiene practices, organizations can empower users to act as a resilient first line of defense rather than the primary entry point for infostealer malware [6,7].
10. Content Enhancements for Practical Utility
10.1. Decision Tree for Technique Selection in Proactive Defense
10.1.1. Decision Node (A): Device-Bound Identity Feasibility
- Pathways:If yes: The recommended strategic direction is the implementation of a Zero-Trust Architecture (ZTA). This path immediately branches to a sub-decision regarding “Token-Binding Feasibility.” A positive response leads to the integration of token-binding as an additional control, while a negative response defaults to reliance on other ZTA controls. Both sub-paths then proceed to consider Moving Target Defense (MTD) at Node (C).If no: If device-bound identity is not feasible due to technical or operational constraints (e.g., legacy systems), the strategy must pivot to Deception and Detection. This involves emphasizing honeytokens, enhanced DNS analytics, and user training. This path proceeds to Node (B).
10.1.2. Decision Node (B): IR Staffing for Honeytoken Response?
- Rationale: The efficacy of deception technologies is contingent upon the organization’s capacity to investigate the generated alerts. Without adequate incident response (IR) personnel and processes, these alerts can lead to operational “alert fatigue” and provide diminished value.
- Pathways:If yes: The organization possesses the capacity to manage alerts and should “Deploy Comprehensive Honeytokens.”If no: The organization should prioritize foundational controls and “Use Simpler Decoys/Focus on Training” to avoid generating unactionable alerts.Both outcomes from this node converge at the central budget decision (D).
10.1.3. Decision Node (C): Sufficient Infrastructure Elasticity for MTD?
- Pathways:If yes: A positive response leads to a final validation sub-decision: “MTD Elasticity Confirmed?” If confirmed, the recommendation is to “Prioritize MTD Deployment.” If not, the organization should “Re-evaluate MTD feasibility/De-prioritize.”If no: MTD is not considered a practical option, and the organization should “Focus on primary emphasis without MTD.”All pathways from this MTD assessment converge at the budget decision (D).
10.1.4. Decision Node (D): Budget and Expertise?
- Rationale: Financial and human resources are universal and practical constraints that determine the scale and sophistication of any implementable security strategy.
- Pathways:High Budget/High Expertise: This enables an “Advanced Layered Defense,” encompassing a comprehensive ZTA implementation, adversarial ML training, and Proactive Threat Hunting. This path proceeds to the final enhancement check at Node (E).Medium Budget/Moderate Expertise: This supports a “Balanced Proactive Defense,” involving a phased ZTA implementation, use of ephemeral tokens, and SIEM-based analytics.Low Budget/Limited Expertise: This prioritizes a “Foundational Proactive Defense,” focusing on built-in security features, essential patching, and strong user education.
10.1.5. Decision Node (E): SIEM Data Science for Predictive Analytics?
- Rationale: The effective implementation of predictive analytics requires two key prerequisites: high-quality, centralized data from a platform like a SIEM and specialized data science expertise to build and validate models.
- Pathways:If yes: The organization can and should “Deploy Predictive Analytics” to augment its defensive posture.If no: The recommendation is to “Focus on other advanced detection” methods, as attempting to implement predictive systems without the necessary foundation would be inefficient.
10.2. Key Insights Box: Concise Takeaways
10.3. Commercial Tooling Snapshot
- Endpoint Detection and Response (EDR): EDR platforms serve as the primary sensor on the endpoint, providing the deep visibility required to detect the initial infostealer execution and subsequent malicious activity [6,7]. While traditional antivirus focuses on static file signatures, modern EDR is crucial for detecting LotL techniques [27,85]. Key capabilities include the following:
- Behavioral Analysis and Process Lineage: EDR tools monitor for suspicious parent–child process relationships, such as a web browser or a document application (e.g., winword.exe) spawning a command-line interpreter like powershell.exe [6,27]. They can also detect direct memory access attempts into browser processes to steal cookies in-memory [6].
- Identity and Access Management (IAM): Modern IAM solutions are the central nervous system for implementing a Zero-Trust Architecture and are foundational to devaluing stolen cookies [67,71]. Their role extends far beyond simple authentication. Key capabilities include the following:
- Conditional Access Policies: These are the core of an IAM-based defense. They evaluate a rich set of contextual signals with every access request. A stolen cookie replayed from an attacker’s machine would likely fail policy checks for device compliance (the device is nor managed or trusted), geographic location (“impossible travel” scenarios), or IP address reputation (coming from a known TOR exit node or malicious proxy) [17,67,71].
- Session Risk Detection: Advanced IAM platforms can analyze user behavior in real-time. If a session initiated with a valid cookie suddenly exhibits anomalous behavior (e.g., accessing applications for the first time or unusual data download patterns), the IAM can flag the session as high-risk and trigger a step-up authentication challenge (e.g., re-prompting for MFA) or terminate the session entirely [17,60].
- Token Binding and Passwordless Authentication: IAM solutions are central to deploying FIDO2/WebAuthn, which cryptographically binds a session to a specific hardware key. They also manage the lifecycle of ephemeral tokens, enforcing short TTLs to drastically reduce the utility window of any stolen cookies [64,74].
- Network Segmentation (Micro-segmentation): While traditional network segmentation relies on static VLANs, modern Zero-Trust-aligned tools enable dynamic micro-segmentation [67,71]. This applies the principle of least privilege directly to network traffic, drastically limiting an attacker’s ability to move laterally even if they have successfully compromised an endpoint and stolen a cookie [67,71]. Key capabilities include the following:
- Identity-Based Policy: Instead of relying on IP addresses, micro-segmentation policies are based on the identity of workloads, applications, or users. This means a policy can be written to state, “The HR application server can only be accessed by authenticated users from the HR department on managed devices,” regardless of where those components are on the network [62,67].
- Breach Containment: In a cookie theft scenario, micro-segmentation contains the blast radius. The attacker, operating from the compromised user endpoint, would be blocked from scanning the network, accessing file shares, or connecting to critical database servers, even if the user themselves had legitimate access [62,67]. The stolen session’s utility is limited only to the specific services it was originally intended for, preventing a minor compromise from escalating into a full network breach [62,71].
- Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR): These platforms act as the central brain for correlating signals from all other tools and automating the response. Their power lies in data fusion and orchestration [58,85].
- Cross-Domain Correlation: A SIEM can ingest logs from IAM, EDR, and network firewalls to build a high-fidelity picture of an attack. A single alert might be low-confidence, but correlating an IAM alert for a high-risk login from an unusual country, with an EDR alert for PowerShell accessing browser files on the legitimate user’s machine moments earlier, creates a high-confidence incident that points directly to cookie theft [58,85].
- Automated Response Playbooks: A SOAR platform can translate this correlated detection into an automated response. For example, upon receiving the correlated alert from the SIEM, a SOAR playbook could be triggered to do the following: (1) automatically enrich the alert with threat intelligence on the attacker’s IP address; (2) execute a command via an API to the IAM solution to terminate all active sessions for the compromised user; (3) execute another command via API to the EDR to isolate the user’s host; and (4) create a prioritized ticket in the helpdesk system for an analyst to investigate. This reduces response time from hours to seconds, mitigating damage before it can escalate [58,85].
11. Scope, Limitations, and Directions for Future Inquiry
- The Conceptual-Empirical Gap of the Predictive Framework: A primary limitation is that the multi-dimensional predictive framework proposed in Section 8 remains, at this stage, conceptual and algorithmic. While it is rigorously grounded in a systematic analysis of the ecosystem’s dynamics and provides a testable blueprint, it has not yet been subjected to empirical validation with live, operational data. The practical efficacy—measured by metrics such as Precision, Recall, and AUC-ROC in a real-world Security Operations Center (SOC) environment—is an open and critical question. Future research must prioritize bridging this conceptual-empirical gap. This would involve longitudinal data collection to train the proposed models and pilot studies to assess their real-world utility in generating high-fidelity, low-noise strategic alerts versus contributing to analyst fatigue.
- Data Sourcing Challenges and the Potential for Adversarial Perturbation: The efficacy of the proposed predictive model is contingent on access to diverse and often challenging data sources. Our analysis acknowledges reliance on dark-web and underground forum data, which presents inherent limitations of opacity, ephemerality, and the potential for active disinformation. A sophisticated threat actor, aware of such monitoring, could theoretically poison the data pool by manipulating credential prices or posting false MaaS advertisements to mislead a predictive system. Furthermore, acquiring the necessary enterprise security telemetry for model training across organizations faces significant real-world hurdles, including commercial data sensitivity, data privacy regulations (e.g., GDPR), and the technical complexity of normalizing heterogeneous data schemas. These data acquisition and verification challenges are not trivial and constitute a major research domain in their own right.
- The Generalizability of Prescriptive Frameworks: This review proposes practical frameworks, such as the decision tree for technique selection (Figure 6). It is crucial to acknowledge that such models are, by necessity, abstractions designed to guide strategic thinking rather than serve as universally applicable blueprints. The optimal defensive posture for any given organization is highly context-specific, depending on its unique risk appetite, regulatory environment (e.g., healthcare vs. finance), technical maturity, and legacy system constraints. For instance, an organization with a large, unmanaged BYOD population cannot implement device-bound identity controls in the same way as a high-security government agency. Consequently, while our decision tree provides a structured starting point, practitioners must adapt its logic to their specific operational realities. The framework is a map, but the organization must still navigate the territory.
- The Temporal Scope and the Relentless Pace of Innovation: This analysis is benchmarked against the state of the MaaS ecosystem from 2020 to mid-2025. While this provides a comprehensive view of the current arms race, the pace of technological innovation in both cybercrime and defense is relentless. The strategic landscape could be fundamentally altered by disruptive technologies on the horizon. For example, the maturation of adversarial AI capable of fully automating novel exploit discovery, the impact of quantum computing on current cryptographic session integrity, or the widespread adoption of decentralized identity protocols could render aspects of this analysis obsolete. Therefore, the findings and models presented here must be understood as a detailed snapshot of the current conflict. They will require continuous re-evaluation and recalibration as the ecosystem inevitably evolves, a challenge inherent to all cybersecurity research.
12. Conclusions
13. A Strategic Roadmap for Future Research
13.1. Phase 1: Foundational Development and Near-Term Wins (1–2 Years)
- Priority: Establish baseline accuracy for forecasting key ecosystem shifts (e.g., price volatility and emergence of new MaaS kits). This is paramount for building trust and demonstrating the viability of predictive approaches.
- Action: Define and pilot a core set of quantifiable metrics (e.g., MaaS kit churn rate, average stolen cookie lifespan before resale, and affiliate-to-provider revenue ratios) to benchmark ecosystem risk and defense effectiveness.
- Priority: Provide a common language and measurement framework for assessing the threat landscape.
- Action: Conduct detailed case studies on the economic impact of successful takedowns (e.g., “Operation Endgame” [49]) and the widespread adoption of specific defensive measures (e.g., FIDO2). Model the financial repercussions for MaaS actors.
- Priority: Provide evidence-based recommendations for economically disrupting the MaaS ecosystem.
13.2. Phase 2: Operationalization and Advanced Modeling (2–4 Years)
- Action: Transition validated predictive models (from Phase 1) into pilot deployments within consenting SOC environments. Develop practical playbooks for SOC analysts to act upon predictive intelligence.
- Priority: Bridge the gap between conceptual models and real-world defensive utility.
- Priority: Enhance the speed and scalability of defensive responses to adaptive threats.
- Priority: Improve understanding of complex ecosystem dynamics and identify optimal long-term disruption strategies.
13.3. Phase 3: Scaling, Policy, and Holistic Understanding (4+ Years)
- Action: Develop and standardize technologies (e.g., advanced federated learning [61] and confidential computing) for sharing sensitive threat intelligence at scale without compromising privacy or commercial interests.
- Priority: Overcome critical barriers to collective defense by enabling richer, more timely intelligence exchange.
- Priority: Address the inherently global and often jurisdictionally ambiguous nature of MaaS operations.
- Action: Conduct qualitative and quantitative research into the motivations, decision-making processes, social structures, and technical skill progression of MaaS actors.
- Priority: Provide deeper insights into the “human element” of the MaaS ecosystem to inform more nuanced disruption and prevention strategies.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AAD | Azure Active Directory |
| AI | Artificial Intelligence |
| AML | Anti-Money Laundering |
| API | Application Programming Interface |
| ASN | Autonomous System Number |
| ATO | Account Takeover |
| AUC-ROC | Area Under the Receiver Operating Characteristic Curve |
| AV | Antivirus |
| C2 | Command and Control |
| CISA | Cybersecurity and Infrastructure Security Agency |
| CPU | Central Processing Unit |
| CVE | Common Vulnerabilities and Exposures |
| DGA | Domain Generation Algorithm |
| DNS | Domain Name System |
| EDR | Endpoint Detection and Response |
| FIDO2 | Fast Identity Online 2 |
| FS-ISAC | Financial Services Information Sharing and Analysis Center |
| GBDT | Gradient Boosting Decision Trees |
| GPU | Graphics Processing Unit |
| HTTPS | Hypertext Transfer Protocol Secure |
| IAM | Identity and Access Management |
| IIoT | Industrial Internet of Things |
| IOC | Indicator of Compromise |
| IP | Internet Protocol |
| IR | Incident Response |
| ISP | Internet Service Provider |
| KYC | Know Your Customer |
| LotL | Living off the Land |
| MaaS | Malware-as-a-Service |
| MFA | Multi-Factor Authentication |
| MISP | Malware Information Sharing Platform |
| ML | Machine Learning |
| MTD | Moving Target Defense |
| OPC UA | Open Platform Communications Unified Architecture |
| PPML | Privacy-Preserving Machine Learning |
| R&D | Research and Development |
| RL | Reinforcement Learning |
| RQ | Research Question |
| SEO | Search Engine Optimization |
| SIEM | Security Information and Event Management |
| SLR | Systematic Literature Review |
References
- SpyCloud Labs. How Infostealers Are Bypassing New Chrome Security Feature to Steal User Session Cookies. SpyCloud. 2024. Available online: https://spycloud.com/blog/infostealers-bypass-new-chrome-security-feature/ (accessed on 14 April 2025).
- Cox, J. Inside the Massive Crime Industry That’s Hacking Billion-Dollar Companies. Wired. 2024. Available online: https://www.wired.com/story/inside-the-massive-crime-industry-thats-hacking-billion-dollar-companies (accessed on 14 April 2025).
- Sophos. The 2024 Sophos Threat Report: Cybercrime on Main Street. 2024. Available online: https://assets.sophos.com/X24WTUEQ/at/wwf5phjtj9bjvmpqqsbfxc/sophos-2024-threat-report.pdf (accessed on 14 April 2025).
- Rodríguez-Galán, G.; Torres, J. Personal data filtering: A systematic literature review comparing the effectiveness of XSS attacks in web applications vs. cookie stealing. Ann. Telecommun. 2024, 79, 763–802. [Google Scholar] [CrossRef]
- Patsakis, C.; Arroyo, D.; Casino, F. The Malware as a Service ecosystem. arXiv 2024, arXiv:2405.04109. [Google Scholar]
- Secureworks Counter Threat Unit. The Growing Threat from Infostealers. Secureworks. 2023. Available online: https://www.secureworks.com/research/the-growing-threat-from-infostealers (accessed on 14 April 2025).
- Kaspersky Global Research. The Evolving Threat Landscape of Infostealers: Trends, Statistics, and Mitigation Strategies. Kaspersky Global Research. 2025. Available online: https://content.kaspersky-labs.com/se/media/en/enterprise-security/data-stealer-storm-2025.pdf (accessed on 14 April 2025).
- Darktrace. The Rise of the Lumma Info Stealer. Darktrace. 2024. Available online: https://www.darktrace.com/blog/the-rise-of-the-lumma-info-stealer (accessed on 14 April 2025).
- Nurmi, J.; Niemelä, M.; Brumley, B.B. Malware Finances and Operations: A Data-Driven Study of the Value Chain for Infections and Compromised Access. In Proceedings of the ARES ’23: The 18th International Conference on Availability, Reliability and Security, Benevento, Italy, 29 August–1 September 2023; Association for Computing Machinery: New York, NY, USA, 2023. [Google Scholar] [CrossRef]
- FS-ISAC. Navigating Cyber 2024: Annual Threat Review and Predictions. FS-ISAC. 2024. Available online: https://www.fsisac.com/navigatingcyber2024 (accessed on 14 April 2025).
- Danish, M. Enhancing Cyber Security Through Predictive Analytics: Real-Time Threat Detection and Response. arXiv 2024, arXiv:2407.10864. [Google Scholar]
- Kasarapu, S.; Shukla, S.; Hassan, R.; Sasan, A.; Homayoun, H.; Dinakarrao, S.M.P. Generative AI-Based Effective Malware Detection for Embedded Computing Systems. arXiv 2024, arXiv:2404.02344. [Google Scholar]
- Sims, J. BlackMamba: Using Al to Generate Polymorphic Malware. 2023. Available online: https://www.hyas.com/blog/blackmamba-using-ai-to-generate-polymorphic-malware (accessed on 19 April 2025).
- Cybersecurity and Infrastructure Security Agency, National Security Agency, Federal Bureau of Investigation, Australian Signals Directorate’s Australian Cyber Security Centre, Canadian Centre for Cyber Security, & New Zealand National Cyber Security Centre. 2025. Fast Flux: A National Security Threat. CISA. Available online: https://www.cisa.gov/news-events/alerts/2025/04/03/nsa-cisa-fbi-and-international-partners-release-cybersecurity-advisory-fast-flux-national-security. (accessed on 19 April 2025).
- Roy, S.; Sharmin, N.; Acosta, J.C.; Kiekintveld, C.; Laszka, A. Survey and Taxonomy of Adversarial Reconnaissance Techniques. ACM Comput. Surv. 2023, 55, 1–38. [Google Scholar] [CrossRef]
- Ogundele, I.O.; Akinade, A.O.; Alakiri, H.O. Detection and Prevention of Session Hijacking in Web Application Management. IJARCCE 2020, 9, 1–10. [Google Scholar] [CrossRef]
- Okta. Defending Against Session Hijacking. Okta Security Blog. 2022. Available online: https://sec.okta.com/articles/sessioncookietheft/ (accessed on 15 April 2025).
- Hoxha, E.; Tafa, I.; Ndoni, K.; Tahiraj, I.; Muco, A. Session hijacking vulnerabilities and prevention algorithms in the use of internet. Glob. J. Comput. Sci. Theory Res. 2022, 12, 23–31. [Google Scholar] [CrossRef]
- Kwon, H.; Nam, H.; Lee, S.; Hahn, C.; Hur, J. (In-)Security of Cookies in HTTPS: Cookie Theft by Removing Cookie Flags. IEEE Trans. Inf. Forensics Secur. 2020, 15, 1204–1215. [Google Scholar] [CrossRef]
- More_eggs MaaS Expands Operations with RevC2 Backdoor and Venom Loader. The Hacker News, 6 December 2024. Available online: https://thehackernews.com/2024/12/moreeggs-maas-expands-operations-with.html (accessed on 19 April 2025).
- Sahay, S.K.; Sharma, A.; Rathore, H. Evolution of Malware and Its Detection Techniques. In Information and Communication Technology for Sustainable Development, Proceedings of the ICT4SD 2018, Goa, India, 30–31 August 2018; Springer: Singapore, 2020; pp. 139–150. [Google Scholar] [CrossRef]
- Catalano, C.; Chezzi, A.; Angelelli, M.; Tommasi, F. Deceiving AI-based malware detection through polymorphic attacks. Comput. Ind. 2022, 143, 103751. [Google Scholar] [CrossRef]
- Ling, X.; Wu, L.; Zhang, J.; Qu, Z.; Deng, W.; Chen, X.; Qian, Y.; Wu, C.; Ji, S.; Luo, T.; et al. Adversarial attacks against Windows PE malware detection: A survey of the state-of-the-art. Comput. Secur. 2023, 128, 103134. [Google Scholar] [CrossRef]
- Prapty, R.T.; Md, S.A.; Hossain, S.; Narman, H.S. Preventing Session Hijacking Using Encrypted One-Time-Cookies. In Proceedings of the 2020 Wireless Telecommunications Symposium (WTS), Washington, DC, USA, 22–24 April 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Aboaoja, F.A.; Zainal, A.; Ghaleb, F.A.; Al-rimy, B.A.S.; Eisa, T.A.E.; Elnour, A.A.H. Malware Detection Issues, Challenges, and Future Directions: A Survey. Appl. Sci. 2022, 12, 8482. [Google Scholar] [CrossRef]
- Session Hijacking 2.0—The Latest Way That Attackers Are Bypassing MFA. The Hacker News, 30 September 2024. Available online: https://thehackernews.com/2024/09/session-hijacking-20-latest-way-that.html (accessed on 25 April 2025).
- Fortinet. Living Off The Land (LOTL) Attacks and Techniques. 2023. Available online: https://www.fortinet.com/resources/cyberglossary/living-off-the-land-lotl (accessed on 13 April 2025).
- Stamp, R. Living-off-the-Land Abuse Detection Using Natural Language Processing and Supervised Learning. arXiv 2022, arXiv:2208.12836. [Google Scholar]
- Etter, B.; Hu, J.L.; Ebrahimi, M.; Li, W.; Li, X.; Chen, H. Evading Deep Learning-Based Malware Detectors via Obfuscation: A Deep Reinforcement Learning Approach. arXiv 2024, arXiv:2402.02600. [Google Scholar]
- Apriorit. Malware Sandbox Evasion: Detection Techniques & Solutions. Apriorit Blog. 2023. Available online: https://www.apriorit.com/dev-blog/545-sandbox-evading-malware (accessed on 23 April 2025).
- Health Sector Cybersecurity Coordination Center (HC3). Malvertising and Healthcare. 2024. Available online: https://www.aha.org/system/files/media/file/2024/09/hc3-analyst-note-tlp-clear-malvertising-and-healthcare-9-25-2024.pdf (accessed on 23 April 2025).
- Drakonakis, K.; Ioannidis, S.; Polakis, J. The Cookie Hunter: Automated Black-box Auditing for Web Authentication and Authorization Flaws. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, Virtual, 9–13 November 2020; ACM: New York, NY, USA, 2020; pp. 1953–1970. [Google Scholar] [CrossRef]
- Rai, S. Behavioral Threat Detection: Detecting Living of Land Techniques. Master’s Thesis, University of Twente, Enschede, The Netherlands, 2020. Available online: https://essay.utwente.nl/83610/ (accessed on 23 April 2025).
- Kaur, R.; Gabrijelčič, D.; Klobučar, T. Artificial intelligence for cybersecurity: Literature review and future research directions. Inf. Fusion 2023, 97, 101804. [Google Scholar] [CrossRef]
- Rosenberg, I.; Shabtai, A.; Elovici, Y.; Rokach, L. Adversarial Machine Learning Attacks and Defense Methods in the Cyber Security Domain. ACM Comput. Surv. 2022, 54, 108. [Google Scholar] [CrossRef]
- Samia, N.; Saha, S.; Haque, A. Predicting and mitigating cyber threats through data mining and machine learning. Comput. Commun. 2024, 228, 107949. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Chen, S.; Liu, D.; Li, J. Performance Comparison and Current Challenges of Using Machine Learning Techniques in Cybersecurity. Energies 2020, 13, 2509. [Google Scholar] [CrossRef]
- Mahboubi, A.; Luong, K.; Aboutorab, H.; Bui, H.T.; Jarrad, G.; Bahutair, M.; Camtepe, S.; Pogrebna, G.; Ahmed, E.; Barry, B.; et al. Evolving techniques in cyber threat hunting: A systematic review. J. Netw. Comput. Appl. 2024, 232, 104004. [Google Scholar] [CrossRef]
- Musser, M.; Lohn, A.; Dempsey, J.X.; Spring, J.; Kumar, R.S.S.; Leong, B.; Liaghati, C.; Martinez, C.; Grant, C.D.; Rohrer, D.; et al. Adversarial Machine Learning and Cybersecurity: Risks, Challenges, and Legal Implications. Int. J. Innov. Res. Technol. (IJIRT) 2023, 11, 85–90. [Google Scholar] [CrossRef]
- Bostani, H.; Cortellazzi, J.; Arp, D.; Pierazzi, F.; Moonsamy, V.; Cavallaro, L. On the Effectiveness of Adversarial Training on Malware Classifiers. arXiv 2024, arXiv:2412.18218. [Google Scholar]
- Ren, K.; Zheng, T.; Qin, Z.; Liu, X. Adversarial Attacks and Defenses in Deep Learning. Engineering 2020, 6, 346–360. [Google Scholar] [CrossRef]
- Macas, M.; Wu, C.; Fuertes, W. Adversarial examples: A survey of attacks and defenses in deep learning-enabled cybersecurity systems. Expert Syst. Appl. 2024, 238, 122223. [Google Scholar] [CrossRef]
- Kalapgar, A.; Dobariya, H.; Kamble, M. DGA Based Malware Detection Using Machine Learning Techniques. Int. J. Res. Anal. Rev. 2021, 8, 676–681. [Google Scholar]
- Hassaoui, M.; Hanini, M.; El Kafhali, S. Data Science in Cybersecurity to Detect Malware-Based Domain Generation Algorithm: Improvement, Challenges, and Prospects. J. Comput. Cogn. Eng. 2024, 3, 213–225. [Google Scholar] [CrossRef]
- Akibis, M.; Pereira, J.; Clark, D.; Mitchell, V.; Alvarez, H. Measuring Ransomware Propagation Patterns via Network Traffic Analysis: An Automated Approach. Res. Sq. 2024. preprint. [Google Scholar] [CrossRef]
- Muhtadi, A.F.; Almaarif, A. Analysis of Malware Impact on Network Traffic using Behavior-based Detection Technique. Int. J. Adv. Data Inf. Syst. 2020, 1, 17–25. [Google Scholar] [CrossRef]
- Shan, A.; Myeong, S. Proactive Threat Hunting in Critical Infrastructure Protection through Hybrid Machine Learning Algorithm Application. Sensors 2024, 24, 4888. [Google Scholar] [CrossRef]
- Sindiramutty, S.R. Autonomous Threat Hunting: A Future Paradigm for AI-Driven Threat Intelligence. arXiv 2023, arXiv:2401.00286. [Google Scholar]
- Melaku, H.M. Context-Based and Adaptive Cybersecurity Risk Management Framework. Risks 2023, 11, 101. [Google Scholar] [CrossRef]
- Vassilev, A.; Oprea, A.; Fordyce, A.; Anderson, H. Adversarial Machine Learning: A Taxonomy and Terminology of Attacks and Mitigations. In NIST AI Publication 100-2e2023; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2024. Available online: https://nvlpubs.nist.gov/nistpubs/ai/NIST.AI.100-2e2023.pdf (accessed on 24 April 2025).
- Raeiszadeh, M.; Ebrahimzadeh, A.; Glitho, R.H.; Eker, J.; Mini, R.A.F. Real-Time Adaptive Anomaly Detection in Industrial IoT Environments. IEEE Trans. Netw. Serv. Manag. 2024, 21, 6839–6856. [Google Scholar] [CrossRef]
- Serror, M.; Hack, S.; Henze, M.; Schuba, M.; Wehrle, K. Challenges and Opportunities in Securing the Industrial Internet of Things. IEEE Trans. Ind. Inform. 2021, 17, 2985–2996. [Google Scholar] [CrossRef]
- Pan, Z.; Mishra, P. Explainable AI for Cybersecurity; Springer Nature: Cham, Switzerland, 2023. [Google Scholar] [CrossRef]
- Rakibul, H.; Nayem, U.; Salman, M.; Labonno, A. The role of predictive analytics in cybersecurity: Detecting and preventing threats. World J. Adv. Res. Rev. 2024, 23, 1615–1623. [Google Scholar] [CrossRef]
- Apruzzese, G.; Laskov, P.; de Oca, E.M.; Mallouli, W.; Rapa, L.B.; Grammatopoulos, A.V.; Di Franco, F. The Role of Machine Learning in Cybersecurity. Digit. Threat. Res. Pract. 2023, 4, 8. [Google Scholar] [CrossRef]
- Sarhan, M.; Layeghy, S.; Moustafa, N.; Portmann, M. Cyber Threat Intelligence Sharing Scheme Based on Federated Learning for Network Intrusion Detection. J. Netw. Syst. Manag. 2023, 31, 3. [Google Scholar] [CrossRef]
- Arfeen, A.; Ahmed, S.; Khan, M.A.; Jafri, S.F.A. Endpoint Detection & Response: A Malware Identification Solution. In Proceedings of the 2021 International Conference on Cyber Warfare and Security (ICCWS), Islamabad, Pakistan, 23–25 November 2021; pp. 1–8. [Google Scholar] [CrossRef]
- González-Granadillo, G.; González-Zarzosa, S.; Diaz, R. Security Information and Event Management (SIEM): Analysis, Trends, and Usage in Critical Infrastructures. Sensors 2021, 21, 4759. [Google Scholar] [CrossRef]
- Tyler, D.; Viana, T. Trust No One? A Framework for Assisting Healthcare Organisations in Transitioning to a Zero-Trust Network Architecture. Appl. Sci. 2021, 11, 7499. [Google Scholar] [CrossRef]
- Microsoft Mechanics. Token Theft Protection with Microsoft Entra, Intune, Defender XDR & Windows. Microsoft Mechanics Blog. 2024. Available online: https://techcommunity.microsoft.com/blog/microsoftmechanicsblog/token-theft-protection-with-microsoft-entra-intune-defender-xdr--windows/4265675 (accessed on 25 April 2025).
- He, Y.; Huang, D.; Chen, L.; Ni, Y.; Ma, X. A Survey on Zero Trust Architecture: Challenges and Future Trends. Wirel. Commun. Mob. Comput. 2022, 2022, 6476274. [Google Scholar] [CrossRef]
- Casola, V.; De Benedictis, A.; Iorio, D.; Migliaccio, S. A Moving Target Defense Framework to Improve Resilience of Cloud-Edge Systems. In International Conference on Advanced Information Networking and Applications; Springer Nature: Cham, Switzerland, 2025; pp. 243–252. [Google Scholar] [CrossRef]
- Satheesh, K. Improving Security and Session Handling in Distributed Networks with JSON Web Tokens. Master’s Thesis, KTH Royal Institute of Technology, Stockholm, Sweden, 2024. Available online: https://kth.diva-portal.org/smash/record.jsf?pid=diva2%3A1939019&dswid=-5186 (accessed on 24 April 2025).
- Flanagan, H. Token Lifetimes and Security in OAuth 2.0: Best Practices and Emerging Trends. IDPro Body Knowl. 2024, 1, 15. [Google Scholar] [CrossRef]
- Ahmad, W.; Raza, M.A.; Nawaz, S.; Waqas, F. Detection and Analysis of Active Attacks using Honeypot. Int. J. Comput. Appl. 2023, 184, 27–31. [Google Scholar] [CrossRef]
- Priya, V.S.D.; Chakkaravarthy, S.S. Containerized cloud-based honeypot deception for tracking attackers. Sci. Rep. 2023, 13, 1437. [Google Scholar] [CrossRef]
- Rose, S.; Borchert, O.; Mitchell, S.; Connelly, S. Zero Trust Architecture. In NIST Special Publication 800-207; National Institute of Standards And Technology: Gaithersburg, MD, USA, 2020. [Google Scholar] [CrossRef]
- Ghasemshirazi, S.; Shirvani, G.; Alipour, M.A. Zero Trust: Applications, Challenges, and Opportunities. arXiv 2023, arXiv:2309.03582. [Google Scholar]
- Ahmadi, S. Autonomous Identity-Based Threat Segmentation in Zero Trust Architectures. arXiv 2025, arXiv:2501.06281. [Google Scholar]
- Cybersecurity and Infrastructure Security Agency (CISA). Zero Trust Maturity Model Version 2.0. 2023. Available online: https://www.cisa.gov/sites/default/files/2023-04/zero_trust_maturity_model_v2_508.pdf (accessed on 23 April 2025).
- Syed, N.F.; Shah, S.W.; Shaghaghi, A.; Anwar, A.; Baig, Z.; Doss, R. Zero Trust Architecture (ZTA): A Comprehensive Survey. IEEE Access 2022, 10, 57143–57179. [Google Scholar] [CrossRef]
- National Security Agency. Advancing Zero Trust Maturity Throughout the Visibility and Analytics Pillar. 2024. Available online: https://media.defense.gov/2024/May/30/2003475230/-1/-1/0/CSI-VISIBILITY-AND-ANALYTICS-PILLAR.PDF (accessed on 23 April 2025).
- Parmar, V.; Sanghvi, H.A.; Patel, R.H.; Pandya, A.S. A Comprehensive Study on Passwordless Authentication. In Proceedings of the 2022 International Conference on Sustainable Computing and Data Communication Systems (ICSCDS), Erode, India, 7–9 April 2022; pp. 1266–1275. [Google Scholar] [CrossRef]
- Microsoft. Passwordless by Default: FIDO2 Deployment Case Study. 2024. Available online: https://fidoalliance.org/case-study-microsoft/ (accessed on 24 April 2025).
- Yu, J.; Li, Q. Moving Target Defense for Detecting Coordinated Cyber-Physical Attacks on Power Grids via a Modified Sensor Measurement Expression. Electronics 2023, 12, 1679. [Google Scholar] [CrossRef]
- Edwards, J. A Comprehensive Guide to the NIST Cybersecurity Framework 2.0: Strategies, Implementation, and Best Practice; John Wiley & Sons: Hoboken, NJ, USA, 2024; Available online: https://www.amazon.com/dp/B0DFRYXNZ8 (accessed on 23 April 2025).
- Sviatun, O.V.; Goncharuk, O.V.; Roman, C.; Kuzmenko, O.; Kozych, I.V. Combating Cybercrime: Economic and Legal Aspects. WSEAS Trans. Bus. Econ. 2021, 18, 751–762. [Google Scholar] [CrossRef]
- Basheer, R.; Alkhatib, B. Threats from the Dark: A Review over Dark Web Investigation Research for Cyber Threat Intelligence. J. Comput. Netw. Commun. 2021, 2021, 1302999. [Google Scholar] [CrossRef]
- Europol. Operation ENDGAME Strikes Again: The Ransomware Kill Chain Broken at Its Source. 2025. Available online: https://www.europol.europa.eu/media-press/newsroom/news/operation-endgame-strikes-again-ransomware-kill-chain-broken-its-source (accessed on 19 April 2025).
- Padur, K.; Borrion, H.; Hailes, S. Using Agent-Based Modelling and Reinforcement Learning to Study Hybrid Threats. J. Artif. Soc. Soc. Simul. 2025, 28, 1. [Google Scholar] [CrossRef]
- Flashpoint. Flashpoint 2025 Global Threat Intelligence Report: Stay Ahead of Emerging Threats. Flashpoint. 2025. Available online: https://flashpoint.io/resources/report/flashpoint-2025-global-threat-intelligence-gtir/ (accessed on 28 April 2025).
- European Union Agency for Cybersecurity (ENISA). ENISA Threat Landscape 2024. 2024. Available online: https://securitydelta.nl/media/com_hsd/report/690/document/ENISA-Threat-Landscape-2024.pdf (accessed on 18 April 2025).
- AhnLab Security Emergency Response Center (ASEC). January 2025 Threat Trend Report on Ransomware. 2025. Available online: https://asec.ahnlab.com/en/86339/ (accessed on 24 April 2025).
- Microsoft. Microsoft Digital Defense Report 2024. Microsoft. 2024. Available online: https://www.microsoft.com/en-us/security/security-insider/intelligence-reports/microsoft-digital-defense-report-2024 (accessed on 24 April 2025).
- FBI; CISA; EPA; ACSC; UK-NCSC. Joint Guidance: Identifying and Mitigating Living Off the Land Techniques. CISA. 2024. Available online: https://www.cisa.gov/resources-tools/resources/identifying-and-mitigating-living-land-techniques (accessed on 21 April 2025).
- Mandiant. M-Trends 2025; Google: Mountain View, CA, USA, 2024; Available online: https://services.google.com/fh/files/misc/m-trends-2025-en.pdf (accessed on 22 April 2025).
- Kaspersky Security Services. Managed Detection and Response Analyst Report 2023. Moscow, Russia. 2024. Available online: https://securelist.com/kaspersky-mdr-report-2023/112411/ (accessed on 13 April 2025).
- Palo Alto Networks Unit 42. 2025 Unit 42 Global Incident Response Report; Palo Alto Networks: Santa Clara, CA, USA, 2024; Available online: https://www.paloaltonetworks.com/resources/research/unit-42-incident-response-report (accessed on 25 April 2025).



| Thematic Category | Key Focus Areas | N | Representative Citations |
|---|---|---|---|
| Technical Exploit Mechanics | Infostealer capabilities, session hijacking, cookie theft methods, malware evasion techniques, browser security model analysis. | 25 | [1,4,6,8,12,13,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33] |
| Advanced Analytical Methods | Predictive analytics, ML/AI in security, adversarial training, threat hunting, DGA/Fast-Flux detection, data science for cybersecurity. | 27 | [11,14,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58] |
| Proactive Defense Concepts | ZTA, Moving Target Defense (MTD), ephemeral tokens, honeytokens, dynamic policy, FIDO2/WebAuthn. | 18 | [59,60,61,62,63,64,65,66,67,68,69,70,71,72,73,74,75,76] |
| Ecosystem and Economic Analysis | MaaS business models, cybercrime economics, illicit marketplaces, value chains, takedown impacts, game theory applications. | 8 | [2,5,7,9,77,78,79,80] |
| Government and Industry Reports | Threat landscape overviews, incident trends, official guidance, real-world statistics, specific infostealer family reports. | 10 | [3,10,51,81,82,83,84,85,86,87] |
| Total | 88 |
| Attacker Actor | Evasion Strategy | Targeted Defense | Effectiveness | Limitations | Refs. |
|---|---|---|---|---|---|
| MaaS Provider | Polymorphic AI malware | Signature AV; Static Analysis | High | High computational cost for attacker; pattern leakage risk; performance anomalies | [12,13,22] |
| Affiliate | Adversarial Perturbation | ML Detection Models; Behavioral AI Detection | Medium-High | Requires expertise; model/data specific; potential subtle anomalies | [39,41,42] |
| Affiliate | Environment-Aware Payload | Sandboxes; Virtual Machines; Analysis Tools | High | Advanced sandbox fingerprinting; detectable via behavioral analysis on real systems | [1,13,30] |
| MaaS Provider | DGA | Domain Blacklisting; Static C2 Blocking | High | Detectable via DGA pattern analysis; reliance on central algorithm | [43,44] |
| MaaS Provider | Fast Flux Networks | IP Blocking; Sinkholing; Static Network Forensics | High | Requires complex setup/botnet; still uses DNS; potential performance issues | [14,45] |
| Affiliate | Living Off The Land (LotL) | App Whitelisting; Executable Monitoring; Signature-based EDR | High | Relies on trusted tools (can be restricted); advanced behavioral analysis needed | [27,28,85] |
| Affiliate | Hook Randomization | API Monitoring; Hooking Defenses; Integrity Monitoring | Medium-High | Complex to implement reliably; potential system stability; detectable via comprehensive monitoring | [29] |
| MaaS Provider/Affiliate | Reinforcement Learning Evasion | Adaptive Defenses; Game Theory Defenses; Behavioral Monitoring | Emerging High | High computational cost; complex training; data-dependent; requires exploration | [34,35,36] |
| Buyer | Malicious browser-extension exfiltration | Store Vetting | Medium | Takedown reduces dwell time | [1,17] |
| Strategy | Description | Strengths Against Adaptive Attackers | Weaknesses/Challenges | Implementation Complexity | Refs. |
|---|---|---|---|---|---|
| Honeypots/Decoy Cookies | Deploys fake assets (incl. cookies) to lure and detect attackers | Gathers real-time TTP intelligence; detects early reconnaissance | Risk of attacker identifying decoys; potential false positives; requires careful setup | Medium | [65,66,81] |
| Adversarial Training | Trains ML models against adversarially crafted examples | Increases model robustness against AI evasion (Table 1); improves detection | Requires expertise; data-dependent; computationally intensive; needs continuous retraining | High | [13,37,39,40,42] |
| Ephemeral Session Tokens | Limits cookie lifespan to reduce hijack window | Reduces value of stolen cookies; minimizes persistence; limits attack window | Can impact user experience (frequent logins); requires application changes | Medium-High | [63,64] |
| ZTA | Continuous verification of access requests; micro-segmentation | Limits lateral movement; reduces implicit trust; n capabilities | Complex to design/implement; requires policy overhaul; potential performance impact | High | [59,61,67,68] |
| Proactive Threat Hunting | Actively searches for signs of compromise | Detects novel/evasive TTPs (LotL, dynamic C2); reduces dwell time | Requires skilled analysts; labor-intensive; not a preventative measure on its own | Medium-High | [38,47,85] |
| Dynamic Policy Enforcement | Adapts security policies in real-time based on risk/behavior | Responds to behavioral anomalies; limits risk dynamically; context-aware controls | Requires robust behavioral analysis; potential high false positives; complex rule sets | High | [38,49,71] |
| Moving Target Defense (MTD) | Dynamically changes the attack surface | Increases attacker uncertainty; hinders static exploits; reduces reconnaissance value | Complex to implement; potential system instability; requires significant planning | High | [28,62] |
| Code Diversification | Creates multiple software versions | Increases cost for attacker R&D; breaks static exploits; complicates targeting | Complex build processes; maintenance overhead; requires toolchain support | High | [39,50] |
| Predictive Security Analytics | Forecasts future threats based on indicators | Guides strategic prioritization; anticipates shifts (Sec VI); optimizes resource use | Data quality dependent; requires validation; relies on models; not a direct countermeasure | Medium-High | [11,36] |
| Automated Moving Target Defense | Automated surface randomisation | Raises attacker cost | Integration complexity | High | [62] |
| Automated Session-cookie anomaly detection | ML + device fingerprinting | Blocks lateral movement, replay | UX friction; legacy gaps | High | [11,36] |
| Token replay analytics | AAD risk graph | Shrinks resale window; stateful infra overhead | Backend scaling | Medium | [11,86] |
| Browser-artefact rollback quarantine | Kernel sensor + rollback | Attacker profiling | Evasion via env-checks | Low-Medium | [87,88] |
| Technique | Adaptation Speed | Detection Risk (Relative) | Resource Cost (Computational/Human) | Practicality (Ease of Deploy/Manage) | Refs. (Illustrative) |
|---|---|---|---|---|---|
| Attacker Techniques | |||||
| Polymorphic AI malware (Attacker) | High | Low-Medium | High | Medium | [11,22] |
| Environment-Aware Payload (Attacker) | Medium | Low-Medium | Medium | Medium | [1,30] |
| DGA (Attacker) | High | Medium | Low | Medium | [44] |
| LotL (Attacker) | Medium | Low | Low-Medium | High (Requires deep understanding) | [27,85] |
| Polymorphic Builder (AI) (Attacker Tool) | Sub-24 h | Low | Moderate GPU | High (SaaS kits) | [12,22] |
| Fast-Flux + DGA C2 (Attacker Infra) | Minutes | Low | Low (Cloud VPS) | High | [14,44] |
| LotL Cookie Dump (Attacker Action) | Instant | Medium | Negligible | Very High | [28,85] |
| Defender Techniques | |||||
| Zero-Trust Architecture (Defender) | Low (Structural) | High (For Attacker Post-Compromise) | High | Low-Medium (Complex Policy) | [61,67] |
| Proactive Threat Hunting (Defender) | High (Human-driven) | High (For Attacker If Detected) | High | Medium-High | [38] |
| Dynamic Policy Enforcement (Defender) | High | Medium | High | Medium-High | [11,53,60] |
| Predictive Security Analytics (Defender) | High (Insights) | N/A (Defense Tool) | Medium-High | Medium | [11,36] |
| Ephemeral Session Tokens (Defender) | Low (Implementation) | Medium-High | Low-Medium | High (App Modification) | [63,64] |
| Moving Target Defense (MTD) (Defender) | Medium-High | Low-Medium | High | Low-Medium | [62] |
| Zero-Trust Proxy (Defender Tool) | Hours (Setup) | Low | Licensing + Ops | Medium | [67] |
| Token TTL Rotation (Defender Policy) | Minutes | Low | Backend scaling | High | [63,64] |
| Honeytoken (Defender Tool) | N/A (Passive) | Medium | Low | High | [65,66] |
| Adversarially Trained ML (Defender Model) | Days (Retraining) | Medium | High GPU | Low | [13,39,40] |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pazmiño Ortiz, L.A.; Maldonado Soliz, I.F.; Guevara Balarezo, V.K. The Adaptive Ecosystem of MaaS-Driven Cookie Theft: Dynamics, Anticipatory Analysis Concepts, and Proactive Defenses. Future Internet 2025, 17, 365. https://doi.org/10.3390/fi17080365
Pazmiño Ortiz LA, Maldonado Soliz IF, Guevara Balarezo VK. The Adaptive Ecosystem of MaaS-Driven Cookie Theft: Dynamics, Anticipatory Analysis Concepts, and Proactive Defenses. Future Internet. 2025; 17(8):365. https://doi.org/10.3390/fi17080365
Chicago/Turabian StylePazmiño Ortiz, Leandro Antonio, Ivonne Fernanda Maldonado Soliz, and Vanessa Katherine Guevara Balarezo. 2025. "The Adaptive Ecosystem of MaaS-Driven Cookie Theft: Dynamics, Anticipatory Analysis Concepts, and Proactive Defenses" Future Internet 17, no. 8: 365. https://doi.org/10.3390/fi17080365
APA StylePazmiño Ortiz, L. A., Maldonado Soliz, I. F., & Guevara Balarezo, V. K. (2025). The Adaptive Ecosystem of MaaS-Driven Cookie Theft: Dynamics, Anticipatory Analysis Concepts, and Proactive Defenses. Future Internet, 17(8), 365. https://doi.org/10.3390/fi17080365







