1. Introduction
The Industrial Internet of Things (IIoT) is an innovative infrastructure and ecosystem that combines new-generation communication technologies with the industrial economy [
1]. It is a key enabler of Industry 4.0. Based on networks, with platforms at the core and data and security as key elements, the IIoT connects people, machines, objects, and systems. This enables the manufacturing sector to expand its industrial chain and create interconnectivity across devices, systems, factories, and regions. As a result, it boosts industrial productivity and drives the intelligent transformation of the manufacturing service system. Integrating the IIoT with manufacturing leads to intelligent production, networked collaboration, mass customization, and service extension upgrades. This shifts manufacturing from isolated models to more collaborative systems. As reported by MarketsandMarkets, the IIoT sector is expected to expand from USD 194.4 billion in 2024 to USD 286.3 billion by 2029, reflecting a compound annual growth rate (CAGR) of 8.1% [
2].
In the collaborative process of the IIoT, ensuring the trusted identity of devices is crucial [
3]. Malicious devices can fake their identity to join the collaboration, steal sensitive data, or disrupt tasks. Without a unified identity authentication mechanism, devices cannot establish mutual trust, which prevents effective collaboration across the domains. Currently, networks in different management domains face identity isolation. They use separate identity management systems, with inconsistent standards for identity formats and authentication policies. This makes it difficult for devices to exchange and verify credentials across domains. As a result, trust cannot be easily established, leading to significant identity fragmentation. In IIoT, devices often interact across different management domains, making secure cross-domain authentication essential. Traditional centralized methods face challenges such as single points of failure, poor scalability, and limited trust interoperability [
3]. To address this, a distributed identity authentication mechanism across management domains is needed. This will enable trusted authentication and identity management for cross-domain devices, allowing seamless collaboration between networks [
4].
The decentralized, tamper-resistant, and traceable characteristics of blockchain make it particularly suitable for identity authentication in cross-domain collaboration within the IIoT [
5]. It enables secure, transparent, and efficient authentication while addressing trust and efficiency issues in traditional authentication methods. Blockchain’s decentralization allows different administrative domains to reach consensus on a unified identity authentication mechanism without relying on a single centralized certification authority. This enables cross-domain identity information sharing and authentication. Its tamper-resistant property ensures that once identity information is recorded on-chain during cross-domain collaboration, it cannot be maliciously altered, thus guaranteeing the integrity and authenticity of the shared identity data. The traceability feature of blockchain enables the recording of all authentication operations in chronological order, allowing identity verification and access history to be traced at any time. This is particularly important for multi-party collaboration and security auditing. In addition, using smart contracts in blockchain technology can automate identity authentication processes, thereby reducing the complexity and cost of manual verification and improving collaboration efficiency.
However, existing blockchain-based cross-domain identity authentication schemes in IIoT scenarios lack a sufficient lightweight design. Industrial environments often have stringent latency constraints, with some time-critical applications requiring end-to-end delays in 10 to 100 milliseconds. Current blockchain-based cross-domain identity authentication schemes are mainly categorized into three types: authentication based on blockchain and Public Key Infrastructure (PKI) [
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17], authentication based on blockchain and Identity-Based Authentication (IBA) [
18,
19,
20,
21,
22,
23,
24,
25,
26,
27], and authentication based on blockchain and Certificateless Public Key Cryptography (CL-PKC) [
28,
29,
30,
31,
32,
33,
34]. The hierarchical structure of most blockchain-based PKI schemes still poses a challenge. It increases interaction overhead during authentication and indirectly raises latency [
7,
12,
14,
15,
16,
17]. Moreover, most existing blockchain-based PKI schemes [
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17] rely on computationally intensive operations such as RSA exponentiation, bilinear pairings, and elliptic curve point multiplications. In addition, most blockchain-based IBA [
18,
19,
20,
21,
22,
23,
24,
25,
26,
27] and blockchain-based CL-PKC schemes [
28,
29,
30,
31,
32,
33,
34] have the inherent privacy risk of using a user’s identity as their public key. While their design eliminates the need for digital certificates, it also exposes identity-related information. Once written to the immutable blockchain ledger, such data becomes vulnerable to linkage attacks and long-term privacy compromises. To address these risks, researchers have proposed various privacy-preserving techniques. These include cryptographic obfuscation [
19] and zero-knowledge proofs [
20,
21,
32,
34]. However, implementing these mechanisms often introduces significant computational overhead and increased protocol complexity. This is particularly problematic in resource-constrained environments such as IIoT. As a result, while blockchain helps alleviate the trust and key escrow issues in traditional IBA by removing the need for a centralized KGC, it simultaneously necessitates more sophisticated and costly mechanisms to preserve user privacy.
To address this issue, this paper presents an efficient and lightweight cross-domain authentication scheme that integrates blockchain technology with Chebyshev chaotic mapping. By leveraging blockchain technology to achieve the trusted sharing of device identity information, the scheme significantly reduces the number of interactions required during cross-domain authentication. It simplifies the identity verification process for industrial devices. Furthermore, it employs the semigroup property of Chebyshev polynomials to construct session keys, effectively reducing the authentication process’s computational complexity and enhancing the system’s overall efficiency and security. Our scheme also assigns IoT devices pseudonyms that are periodically generated using Chebyshev chaotic maps, effectively mitigating traceability risks during cross-domain operations and preserving device privacy. To summarize, our contributions are the following:
To address the complexity and single point of failure associated with third-party-dependent cross-domain identity authentication in traditional IIoT systems, we propose a blockchain-based cross-domain authentication scheme tailored for the IIoT. By integrating edge computing, the scheme effectively reduces the number of interactions and latency during device authentication.
To reduce the high overhead and latency of existing blockchain-based authentication methods unsuitable for constrained devices, we propose a lightweight authentication method using Chebyshev chaotic maps and blockchain, significantly lowering computational cost and delay.
We conduct a formal security analysis of the proposed method using the Real-Or-Random (ROR) model, demonstrating its security. Furthermore, we implement simulations using Hyperledger Fabric [
35] and the MIRACL cryptographic library [
36] to evaluate the performance of our scheme. Comparative analysis with related work confirms the superiority of our proposed method.
The remainder of this paper is structured as follows:
Section 2 surveys the related literature.
Section 3 covers the foundational concepts relevant to our scheme. In
Section 4, we describe the system architecture.
Section 5 defines the security objectives.
Section 6 presents the proposed authentication protocol in detail. A thorough security evaluation is conducted in
Section 7.
Section 8 compares the computational and communication overhead of our method with existing solutions. Lastly,
Section 9 summarizes the conclusions of this work.
2. Related Work
Given the advantages stated in the
Section 1, many researchers and enterprises have begun researching the use of blockchain for cross-domain authentication and generating reliable cross-domain authentication without needing trusted third parties.
Existing blockchain-based cross-domain authentication schemes can be broadly categorized into three types: authentication based on blockchain and Public Key Infrastructure (PKI), authentication based on blockchain and IBA, and authentication based on blockchain and Certificateless Public Key Cryptography (CL-PKC).
2.1. Cross-Domain Authentication Based on PKI and Blockchain
Although traditional Public Key Infrastructure (PKI) has played a pivotal role in digital identity authentication, its reliance on centralized Certificate Authorities (CAs) exposes it to a series of inherent weaknesses [
6]. As the sole trust anchors, CAs represent single points of failure—once compromised, either by attack, mismanagement, or negligence, the entire authentication system becomes vulnerable. Moreover, PKI implementations vary widely across organizations and platforms, making cross-domain identity authentication prone to issues such as certificate incompatibility, inconsistent trust anchor configurations, and mismatched key management protocols. These inconsistencies often result in failed authentications, insecure fallback mechanisms, or increased administrative burden. A common approach to addressing the above issue is to involve a third-party Certificate Authority (CA) to handle authentication in cross-domain communications. However, this solution poses practical challenges, as it may introduce security risks like collusion, lack of fairness, and vulnerability to single points of failure.
To address these structural limitations, growing research interest has turned to blockchain as a foundation for decentralized authentication architectures. Due to its immutable and consensus-driven design, blockchain can serve as a shared ledger for recording identity information, thereby reducing dependence on any single CA and mitigating the systemic risks of centralized trust. Guided by this idea, many researchers have proposed blockchain-based cross-domain authentication schemes. For example, Wang et al. [
7] designed a consortium-based CA collaboration model using blockchain to eliminate isolated trust silos. Similarly, Zhang et al. [
8] proposed the BCAE scheme, which replaces traditional CA-signed X.509 certificates with blockchain-based credentials, improving identity consistency and interoperability across domains. Tong et al. [
9] proposed CCAP, a complete cross-domain authentication based on consortium blockchain for the Internet of Things. They introduce verification servers to form a consortium blockchain, assisting authentication servers (i.e., CAs) in enabling secure cross-domain authentication between IoT domains with different configurations. Cui et al. [
10,
11] utilized blockchain-based mechanisms maintained by edge servers to allow for mutual authentication without central CAs and combine smart contracts and dynamic accumulators to optimize communication and computation during the authentication process. Zhang et al. [
12] introduced smart contracts in vehicular networks to manage certificate lifecycles autonomously, reducing the administrative workload and improving the responsiveness of revocation and renewal operations. Saleem et al. [
13] presented a blockchain-based Public Key Infrastructure (PKI) framework named ProofChain. It aims to decentralize the CA pool and ensure compatibility with X.509 standards. Yang et al. [
14] presented a blockchain-enhanced hybrid authentication framework for vehicular networks. In their scheme, Certificate Authorities (CAs) handle initial identity issuance, while blockchain supports cross-domain credential verification and pseudonym lifecycle management. The framework enables real-time coordination among CAs via blockchain.
However, despite these improvements, blockchain-based PKI systems also introduce new layers of complexity. First, existing consensus mechanisms (such as PoW (Proof of Work) [
37], PoS (Proof of Stake) [
38], or PBFT (Practical Byzantine Fault Tolerance) [
39]) often bring significant computational and latency overhead, especially in high-frequency authentication scenarios. Second, blockchain’s inherently transparent nature conflicts structurally with the need for privacy. Thirdly, blockchain’s append-only nature leads to increased storage overhead. To solve these problems, Luo et al. [
15] observed this bottleneck. They proposed a split-chain mechanism to accelerate write operations, though the trade-off between consistency and performance remains a challenge. Su et al. [
16] employed decentralized oracles and zero-knowledge proofs to enable anonymous identity verification across heterogeneous domains, effectively preventing identity tracking. Likewise, Cui et al. [
10,
11] utilized pseudonym-based mechanisms distributed by edge servers to allow for mutual authentication. Tong et al. [
9] proposed a complete cross-domain authentication based on consortium blockchain with a privacy protection scheme for the Internet of Things to preserve device privacy. Xue et al. [
17] proposed integrating a blacklist Merkle tree to support revocation while maintaining data integrity. However, this introduces additional computational and storage costs.
Although existing research has made notable progress in integrating blockchain with PKI, the hierarchical structure of PKI still poses a challenge. It increases interaction overhead during authentication and indirectly raises latency. Furthermore, few studies have explored optimizations of the computational and latency overhead from the perspective of cryptographic primitives employed in the authentication workflow. For example, related work [
7,
10,
11,
12,
14,
15,
17] still relies heavily on traditional PKI mechanisms. In particular, the certificate-based signature verification in their scheme typically employs elliptic curve cryptography (ECC), which is computationally intensive for resource-constrained IIoT devices. Zhang et al. [
8] claim lightweight key agreement, but the use of modular arithmetic over elliptic curves and multiple temporary key exchanges still results in resource-intensive cryptographic computations on the device side. Tong et al. [
9] and Su et al. [
16] rely on relatively complex cryptographic operations such as threshold cryptography, bilinear pairings, and non-interactive zero-knowledge proofs, which can impose significant computational overhead on the system.
We eliminate the complexity of traditional PKI hierarchical structures by leveraging blockchain as a decentralized and trusted authority for public key verification, thereby improving both authentication efficiency and system scalability. Moreover, most existing blockchain-based PKI schemes rely on computationally intensive operations such as RSA exponentiation, bilinear pairings, and elliptic curve point multiplications. To reduce this overhead, we propose an authentication scheme for IIoT based on Chebyshev chaotic maps. Chaotic-map-based authentication mechanisms have been proven to offer superior computational efficiency compared to conventional cryptographic techniques. According to [
40,
41,
42], the Chebyshev polynomial computation operation takes one-third of the computational time of the ECC point multiplication operation.
2.2. Cross-Domain Authentication Based on IBA and Blockchain
Identity-Based Authentication (IBA) [
18] is a method where a user’s identity (e.g., email or username) serves as their public key, thereby eliminating the need for digital PKI certificates. In this approach, a trusted entity called the Key Generation Center (KGC) is responsible for generating the corresponding private keys of all users. During authentication, users demonstrate possession of their private keys by generating a valid cryptographic response, which can be verified by others using the public key derived from the user’s identity. As a result, IBA significantly simplifies key management and reduces the overhead associated with certificate handling. Therefore, it is particularly suitable for distributed environments such as IoT and IIoT. However, since the KGC holds the power to generate any user’s private key, IBA introduces potential key escrow and trust concerns.
To address these concerns, researchers have turned to blockchain technology, leveraging its decentralized, tamper-resistant architecture to reconstruct IBA frameworks without the need for a centralized KGC. For instance, Xiong et al. [
19] proposed DIBRS-CE, a blockchain-based distributed identity-based ring signature scheme with identity abort, tailored for consumer electronics. Their design features a decentralized threshold identity-based ring signature protocol that removes reliance on a Key Generation Center (KGC). Zhang et al. [
20] presented an identity-based data rights governance (IDRG) framework designed for blockchain-enabled, human-centric metaverse communication. By integrating blockchain technology with polynomial functions, their scheme supports access policies involving multiple users, thereby addressing the constraint of conventional identity-based encryption methods, which typically allow only single-user policies. Li et al. [
21] presented a blockchain-assisted distributed identity-based signature scheme designed to enhance security in resource-constrained IoT applications. By eliminating reliance on a centralized Key Generation Center (KGC), the scheme enables users to collaboratively generate master and signing keys through threshold protocols, addressing key escrow risks and single points of failure. Li et al. [
22] introduced the Advanced Hierarchical Identity-Based Security Mechanism by Blockchain (AHISM-B) for Named Data Networking (NDN). Their approach leverages hierarchical identity-based cryptography to associate data names with public keys while utilizing blockchain to oversee public parameters, thereby mitigating the risk of single-point failures. Yang et al. [
23] proposed an efficient identity-based aggregate signcryption scheme with blockchain (B-ID-ASC) for IoT-enabled maritime transportation systems (IMTSs). They design decentralized device authentication and tamper-proof transaction logging to replace centralized authorities, mitigating single-point failures. Suresh Babu et al. [
24] introduced a decentralized Identity-Based Authentication framework for IoT devices, leveraging a permissioned blockchain. In their approach, the blockchain functions as a distributed Private Key Generator (PKG), effectively mitigating issues such as single points of failure and key escrow that are commonly associated with conventional Public Key Infrastructure (PKI) and IBA.
Despite these advancements, blockchain-based IBA systems are not without challenges. First of all, resource-constrained devices in IIoT may struggle with blockchain’s computational and storage requirements, particularly when managing extensive data. To reduce computational overhead, Srivastava et al. [
25] proposed a provably secure multivariate identity-based multi-signature scheme (MV-MSS) for the Internet of Vehicles (IoV) environment. The MV-MSS produces a single compact signature for multiple signers, reducing communication overhead. Zhang et al. [
26] proposed two novel identity-based key agreement protocols tailored for the blockchain-powered intelligent edge. The first protocol ensures extended Canetti–Krawczyk (eCK) security, while the second protocol further achieves continuous after-the-fact leakage resilience (CAFL-eCK) security, resistant to side-channel attacks. Both protocols are lightweight and suitable for edge and end devices with limited computational resources. Li et al. [
21] presented a blockchain-assisted distributed identity-based signature scheme for resource-constrained IoT applications. They propose a tree-based broadcasting strategy that reduces communication complexity from O (
) to O (nlogn), optimizing bandwidth efficiency for IoT devices. They further employ oblivious transfer protocols instead of homomorphic encryption for signature construction, achieving lightweight computational overhead without compromising security. To reduce storage overhead, Sharma et al. [
27] proposed a blockchain-based IoT architecture for securing healthcare data using identity-based encryption (IBE). The system combines blockchain with Swarm off-chain storage to efficiently manage large-scale healthcare datasets. IBE secures data at rest, while Swarm enables decentralized data distribution, effectively addressing storage challenges. Second, privacy risks emerge from the immutable nature of blockchain, as identity or key-related metadata, once written to the ledger, may be susceptible to linkage attacks over time. Zhang et al. [
20] proposed a privacy-preserving identity-based data rights governance scheme (IDRG) for blockchain-empowered human-centric metaverse communications. They protect user privacy by enabling encrypted identity-based data access policies that hide both policy content and size, ensuring data, identity, and policy privacy while supporting accountability and revocation via cryptographic techniques and blockchain.
Although prior studies have made notable progress in addressing the challenges introduced by integrating blockchain into IBA systems, several critical issues remain. One key concern is the inherent privacy risk of using a user’s identity as their public key [
22,
23,
24,
25,
26,
27]. While this design eliminates the need for digital certificates, it also exposes identity-related information. Once written to the immutable blockchain ledger, such data becomes vulnerable to linkage attacks and long-term privacy compromises. To address these risks, researchers have proposed various privacy-preserving techniques. These include cryptographic obfuscation [
19] and zero-knowledge proofs [
20,
21]. However, implementing these mechanisms often introduces significant computational overhead and increased protocol complexity. This is particularly problematic in resource-constrained environments such as the Internet of Things (IoT) and Industrial Internet of Things (IIoT). As a result, while blockchain helps alleviate the trust and key escrow issues in traditional IBA by removing the need for a centralized KGC, it simultaneously necessitates more sophisticated and computationally intensive mechanisms to preserve user privacy.
Our scheme assigns IoT devices pseudonyms that are periodically generated using Chebyshev chaotic maps, effectively mitigating traceability risks during cross-domain operations and preserving device privacy. Furthermore, Chebyshev chaotic maps have demonstrated superior computational efficiency compared to traditional privacy-preserving techniques in most blockchain-based IBA frameworks.
2.3. Cross-Domain Authentication Based on CL-PKC and Blockchain
Certificateless Public Key Cryptography (CL-PKC) presents a compelling alternative to traditional PKI and identity-based encryption (IBE) by eliminating certificate management while preventing key escrow. In CL-PKC, a semi-trusted Key Generation Center (KGC) generates a partial private key based on the user’s identity. This key is then combined with a user-chosen secret value to form a complete private key. Since the KGC lacks knowledge of this secret value, it cannot reconstruct the full private key, thereby mitigating the inherent trust risks associated with IBE. Additionally, CL-PKC-based authentication systems do not rely on digital certificates, reducing administrative complexity and improving scalability in large-scale distributed systems.
However, CL-PKC has its limitations. The partial trust assumption on the KGC still poses a security concern—particularly in adversarial or multi-domain environments. To overcome these shortcomings, researchers have explored a variety of blockchain-integrated CL-PKC frameworks that distribute trust and improve operational efficiency. For example, Yao et al. [
28] introduced ECB-CLS, an authentication scheme for the automatic dependent surveillance broadcast (ADS-B) systems, combining blockchain and certificateless signatures to eliminate certificate management. It integrates blockchain for decentralized key management, mitigating single points of failure. Zhang et al. [
29] developed an enhanced certificateless authentication and key agreement (CL-AKA) protocol based on blockchain technology in an Internet of Drones (IoD) environment. The protocol achieves resistance to key compromise impersonation attacks. Wang et al. [
30] presented a revocable certificateless cross-domain authentication scheme leveraging a primary–secondary blockchain model. The scheme enhances cross-domain authentication efficiency and security by eliminating complex certificate management and mitigating centralized authority issues using the primary–secondary blockchain model. Feng et al. [
31] proposed a cross-domain authentication method (CABC) that integrates blockchain with certificateless signatures for Industrial Internet of Things (IIoT) devices. CABC enables trusted authentication across different management domains (e.g., factories) and supports decentralized identity verification, thereby eliminating the reliance on trusted third parties and centralized servers. Wang et al. [
32] proposed a blockchain-based certificateless conditional anonymous authentication scheme (BCCA) for the Industrial Internet of Things (IIoT). The BCCA enables traceability and user revocation with a chameleon hash algorithm for illegal information rectification on the evidence blockchain, aiming to mitigate security threats such as forgery, man-in-the-middle, and replay attacks. Dong et al. [
33] developed a certificate-free, blockchain-enabled cross-domain authentication scheme tailored for the Industrial Internet. Their method relies on an Ethereum consortium blockchain to serve as a trusted foundation across various regions. Within each region, industrial entities collaborate with a local Key Generation Center to produce users’ private keys, thereby addressing the key escrow issue. Liu et al. [
34] introduced a blockchain-assisted certificateless anonymous cross-domain authentication scheme for the Internet of Vehicles (IoVs). By leveraging blockchain, the approach minimizes redundant authentication overhead. The proposed scheme guarantees message integrity, supports traceability, and defends against multiple types of attacks.
Although existing research has made considerable progress in addressing the challenges introduced by integrating blockchain into CL-PKC systems, a fundamental issue remains. Similar to IBA, CL-PKC inherently uses the user’s identity as part of the public key [
28,
29,
30,
31,
32,
33,
34], which poses significant privacy risks. To mitigate these risks, additional privacy-preserving mechanisms are required. However, these measures inevitably introduce further computational overhead [
32,
34].
Likely, to enhance privacy and prevent traceability in cross-domain scenarios, our scheme uses Chebyshev chaotic maps to generate pseudonyms for IoT devices at regular intervals. This approach keeps device identities unlinkable over time and protects sensitive information. In addition, Chebyshev chaotic maps provide better computational efficiency than traditional methods like RSA, ECC, or bilinear pairing that are used in most blockchain-based CL-PKC methods.
3. Preliminaries
This section describes the prerequisite knowledge for the proposed work.
3.1. Blockchain
Blockchain is a distributed ledger composed of a sequence of blocks , where each block contains a set of validated transactions. A blockchain system can be formally modeled as a state-based transition system , where the following are true:
S is the set of global states. The global state refers to the complete and shared snapshot of all relevant data that defines the current status of the blockchain network. This includes information such as account balances, smart contract storage, and other protocol-defined data.
I is the set of valid inputs (e.g., transactions, blocks).
is the deterministic state transition function.
is the initial state.
The evolution of the blockchain system is described by the following transition sequence:
Each state may represent the current ledger view, set of valid transactions, and configuration of participating nodes. Consensus protocols determine how a new input is selected and verified before applying .
A block B can be defined generically as
where
is the set of transactions and the
contains metadata such as the previous block hash
timestamp
t and consensus-specific proof
. The validity of a block is determined by a predicate:
This model accommodates various consensus mechanisms. For example, in PoW, verifies that the proof satisfies , where D is the difficulty target. In PBFT, it verifies a quorum of signed messages from validator nodes.
Blockchains can be broadly classified into public, private, consortium, and hybrid types. This classification is based on factors such as access permissions, governance models, and intended applications.
Public blockchains are open and permissionless. Anyone can join the network, read data, submit transactions, and participate in consensus. These networks are fully decentralized and trustless. Public blockchains are well-suited for open systems where transparency, immutability, and user autonomy are essential.
Private blockchains, also known as permissioned blockchains, restrict access to a single organization or a specific group. Only authorized users can validate transactions, access records, or operate nodes. These blockchains are often used in enterprise environments. They enhance data integrity, enable traceability, and support process automation, while keeping sensitive information private.
Consortium blockchains sit between public and private models. They are jointly managed by a group of predefined organizations, creating a decentralized but controlled network. Each member operates a node and takes part in the consensus process. This model is effective for sectors like finance, supply chain, and healthcare, where multiple parties need to share data without depending on a single authority.
Hybrid blockchains combine features of both public and private systems. They support selective transparency—some data can be public, while other parts remain private or permissioned. This approach offers both flexibility and scalability. It is suitable for use cases that require public verification along with controlled access, such as government services, enterprise systems, and IoT platforms.
In the context of the IIoT, consortium blockchains offer a robust solution for device authentication by enabling a decentralized yet collaboratively governed registry of devices. This approach reduces dependence on a single centralized Certificate Authority while maintaining control within a trusted group of stakeholders. Consortium blockchains enhance resistance to spoofing and unauthorized access and support secure, auditable interactions among industrial entities. By integrating this model, industrial systems can achieve higher levels of trust, traceability, and operational resilience that are essential for secure and efficient performance in interconnected industrial environments.
3.2. Extended Chebyshev Chaotic Maps
Definition 1 (Chebyshev Chaotic Maps)
. Let n be an integer, and , the Chebyshev polynomial, denoted by , maps the interval to itself and is defined as follows: The recurrence formula defining the Chebyshev polynomial is as follows:
where
,
, and
.
Definition 2 (Semigroup Property)
. The Chebyshev polynomials are closed under the semigroup operation, which is given aswhere are integers and . Chebyshev polynomials also satisfy the semigroup property over the entire real line
. The extended form of the Chebyshev polynomial is expressed as
where
and
p is a large prime number.
Definition 3 (Chaotic Maps Discrete Logarithm Problem—CMDLP)). Given a Chebyshev polynomial and a real number , the CMDLP states that it is computationally infeasible to determine the value a such that . In other words, the advantage of a probabilistic polynomial-time (PPT) adversary A in solving CMDLP within time t is defined as , which is negligible. That is, of a PPT adversary A within a time bound t, to solve CMDLP, is negligible. That means , where ϵ denotes a negligible function.
4. System Model
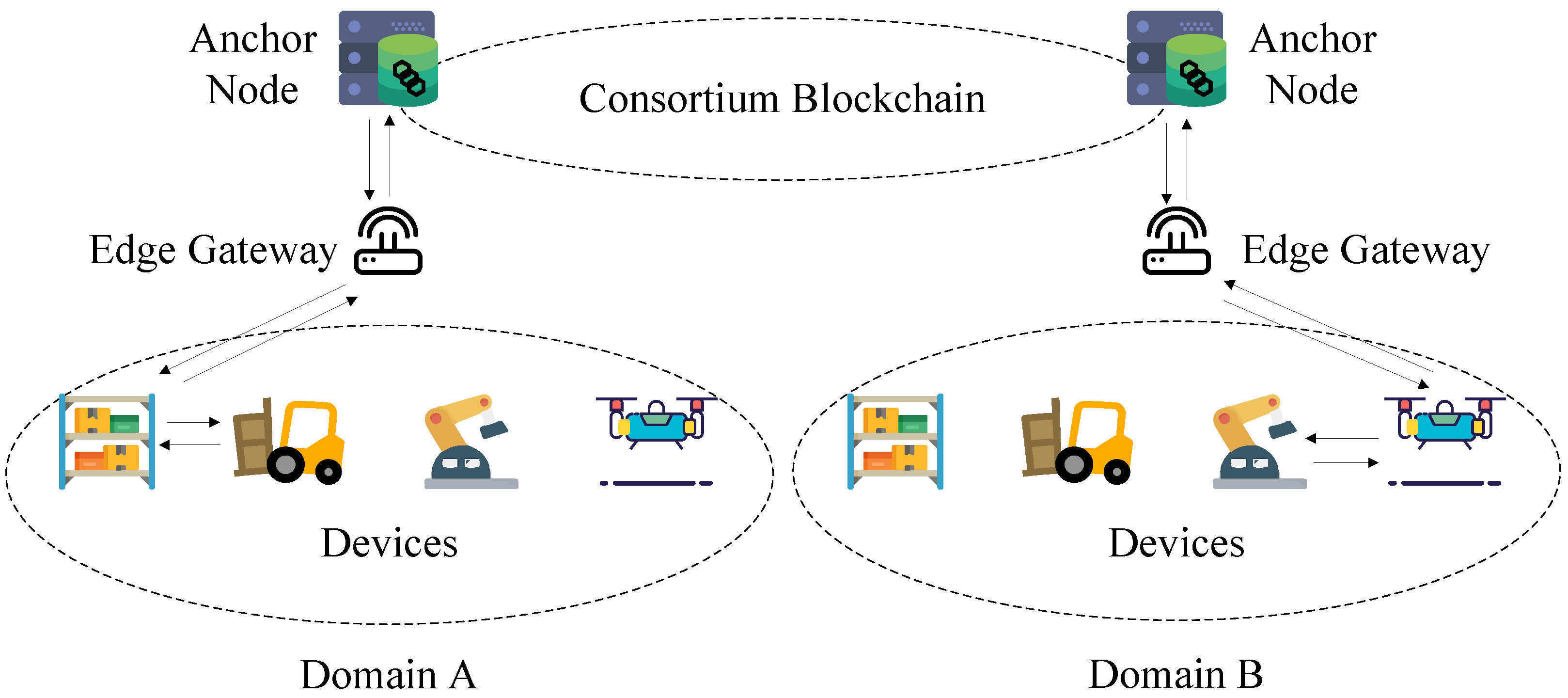
In the system model of our authentication method, there are four kinds of entities, as shown in
Figure 1:
industrial device,
edge gateway,
blockchain anchor node, and
consortium blockchain network.
Industrial devices refer to smart machines, sensors, actuators, and control systems deployed within manufacturing or operational environments. Each device is uniquely identifiable and equipped with a digital identity. These devices typically possess limited computational resources and are often constrained in terms of connectivity. As such, they rely on nearby infrastructure, the edge gateways, for identity verification and secure network onboarding.
Edge gateways act as intermediaries between industrial devices. Positioned close to the devices at the network edge, an edge gateway performs initial identity verification for devices within its administrative domain. It maintains local access control policies and authentication protocols. The edge gateway collaborates with blockchain anchor nodes in cross-domain scenarios to validate device identities from other domains.
Blockchain anchor nodes are specialized entities participating directly in the consortium blockchain network. They are responsible for maintaining a synchronized ledger of authenticated device identities across different domains. Each anchor node represents a local domain or administrative zone and communicates with peer anchor nodes to exchange identity verification records. When a device seeks access in a foreign domain, the local edge gateway can query its associated anchor node, which in turn consults the blockchain to verify the authenticity of the device’s identity as issued by another domain’s anchor node. In the context of the Industrial Internet, a domain refers to a logical segment where devices, data, networks, applications, and services are managed in a distributed manner. The division of domains is typically based on functionality, geographic location, permissions, or management requirements. It aims to enhance the system’s management efficiency, security, and controllability. The domain serves as a boundary for administrative tasks and resource management. Typically, different domains are independent of each other, especially the authentication service.
The consortium blockchain network is a permissioned ledger infrastructure where only authorized anchor nodes are allowed to validate transactions and contribute to consensus. This network ensures decentralized trust and provides tamper-evident storage for device identity credentials. It supports smart contracts that encode identity registration, revocation, and cross-domain verification logic. The use of a consortium model balances scalability with security, avoiding the performance drawbacks of fully public chains while still achieving distributed consensus.
The authentication workflow is orchestrated through a multi-entity collaboration:
(1) Industrial devices request authentication from the local edge gateway.
(2) The edge gateway forwards the request to the anchor node for cross-domain verification.
(3) The anchor node queries the consortium blockchain network to check the validity of the device identity as registered by a remote anchor node.
This layered and federated architecture ensures that device identity is managed in a secure, decentralized, and scalable manner across the IIoT ecosystem.
The primary role of blockchain is to replace traditional trusted authorities in storing and managing identity information, thereby enabling a decentralized identity authentication mechanism. Unlike conventional identity systems that rely on centralized Certificate Authorities (CAs) or Key Generation Centers (KGCs), blockchain leverages consensus protocols and tamper-resistant ledger structures to enhance the security, transparency, and auditability of identity data. By integrating lightweight cryptographic techniques—Chebyshev chaotic mapping—it becomes possible to design authentication protocols that are both computationally efficient and resource-friendly. This is particularly beneficial for environments with constrained devices, such as the Internet of Things (IoT). The fusion of blockchain and lightweight cryptography paves the way for a next-generation identity authentication system characterized by high scalability, strong security, and decentralized autonomy.
In addition, our proposed scheme exhibits strong scalability and can support large-scale device authentication (e.g., thousands of devices across multiple management domains). As the number of devices within or across domains increases, additional edge gateways can be deployed in the corresponding domains. These new edge gateways can quickly join the consortium blockchain network and synchronize with existing gateways. Once synchronized, they can operate in parallel to handle intra-domain and cross-domain authentication requests, thereby significantly enhancing the overall scalability of the system.
5. Security Requirements
During the design of the authentication scheme, it is essential to ensure both the integrity and confidentiality of messages exchanged during transmission, as well as the protection of device identity information. To achieve robust security in an Industrial Internet environment, the protocol must satisfy the following security requirements:
(1) Mutual Authentication and Key Agreement
The protocol must ensure mutual authentication between the device and the authentication server (e.g., edge gateway or anchor node). Only after both parties have authenticated each other should they engage in a secure key agreement phase to derive a session key used for subsequent communication.
(2) Resistance to Man-in-the-Middle (MitM) Attacks
The protocol must be designed to prevent attackers from intercepting, modifying, or injecting messages during transmission over public or insecure channels.
(3) Resistance to Impersonation Attacks
The protocol should be resilient against adversaries attempting to impersonate a legitimate device or authentication entity. This requires robust identity verification methods, often involving cryptographic proofs bound to unique device credentials.
(4) Device Anonymity and Privacy Preservation
The protocol should preserve device anonymity, ensuring that a device does not expose its real identity during authentication. Techniques such as pseudonym-based identifiers or zero-knowledge proofs can be employed to achieve unlinkability and identity concealment.
(5) Resistance to Replay Attacks
The protocol must prevent attackers from reusing previously captured messages or authentication exchanges to gain unauthorized access. Common countermeasures include nonces, timestamps, and session tokens that ensure message freshness and temporal uniqueness.
(6) Resistance to Ephemeral Key Leakage
Even if an adversary obtains temporary (ephemeral) session-specific keys, they should not be able to derive the session key or any other sensitive long-term credentials. This property, often referred to as ephemeral key compromise resilience, ensures the confidentiality of session keys under partial exposure scenarios.
(7) Forward Secrecy (Perfect Forward Secrecy, PFS)
The protocol must ensure that the exposure of long-term private keys does not affect the confidentiality of either past or future session keys. Forward secrecy protects earlier session keys from being compromised, even if a device’s long-term credentials are revealed at a later point in time.
6. Proposed Cross-Domain Authentication Method
The proposed authentication method is explained in detail in this section. First, the system generates essential parameters (e.g., secret key, shared key, and public key) for the IIoT devices. Then, the proposed method and its detailed procedures for both intra-domain and cross-domain authentication of IIoT devices are thoroughly described. The notations of the proposed scheme are listed in
Table 1.
6.1. System Initialization Phase
In the consortium blockchain, blockchain anchor nodes from different domains collaboratively generate a random integer
using a distributed random number generation algorithm. A representative anchor node from the consortium blockchain generates the secret key
, the shared key
S, and a large prime number
p. It then computes the public key:
The representative anchor node securely transmits the shared key S to the blockchain anchor nodes of each domain via a secure channel. It then selects a one-way hash function
and publishes the system parameters
on the blockchain. Besides the shared key
S, the initialization parameters of the system are recorded in the blockchain’s genesis block.
Subsequently, the consortium blockchain network, through a consensus mechanism, assigns a unique identifier
to each Domain
Edge Gateway
. Each Edge Gateway then locally generates its own private key
and computes the corresponding public key:
The identity and public key pair are submitted to the blockchain through the respective local blockchain anchor node, ensuring that each gateway is verifiably registered and authenticated within its domain.
The consortium blockchain network leverages the Industrial Internet Identification System to generate or retrieve a unique identifier
for each Device
of each Domain
X. Based on
, the device generates a private key
and computes its corresponding public key as
The device then sends its identifier along with the public key to Edge Gateway in its Domain X. Upon receiving the message, first verifies the validity of using the Industrial Internet Identification System. If valid, it computes the pseudonymous identity for the device . The edge gateway then uploads to the blockchain via its associated anchor node . This allows anchor nodes in other domains to retrieve the registration information of the device using its pseudonymous identifier. The pseudonymous identity is periodically updated to prevent continuous tracking by potential attackers. The update interval can be adjusted flexibly based on the specific context.
Edge Gateway then sends the pseudonymous identity back to Device . Upon receiving the response, the device locally stores the tuple .
This initialization phase establishes the trust foundation for subsequent mutual authentication and secure communication between industrial devices, edge gateways, and cross-domain nodes.
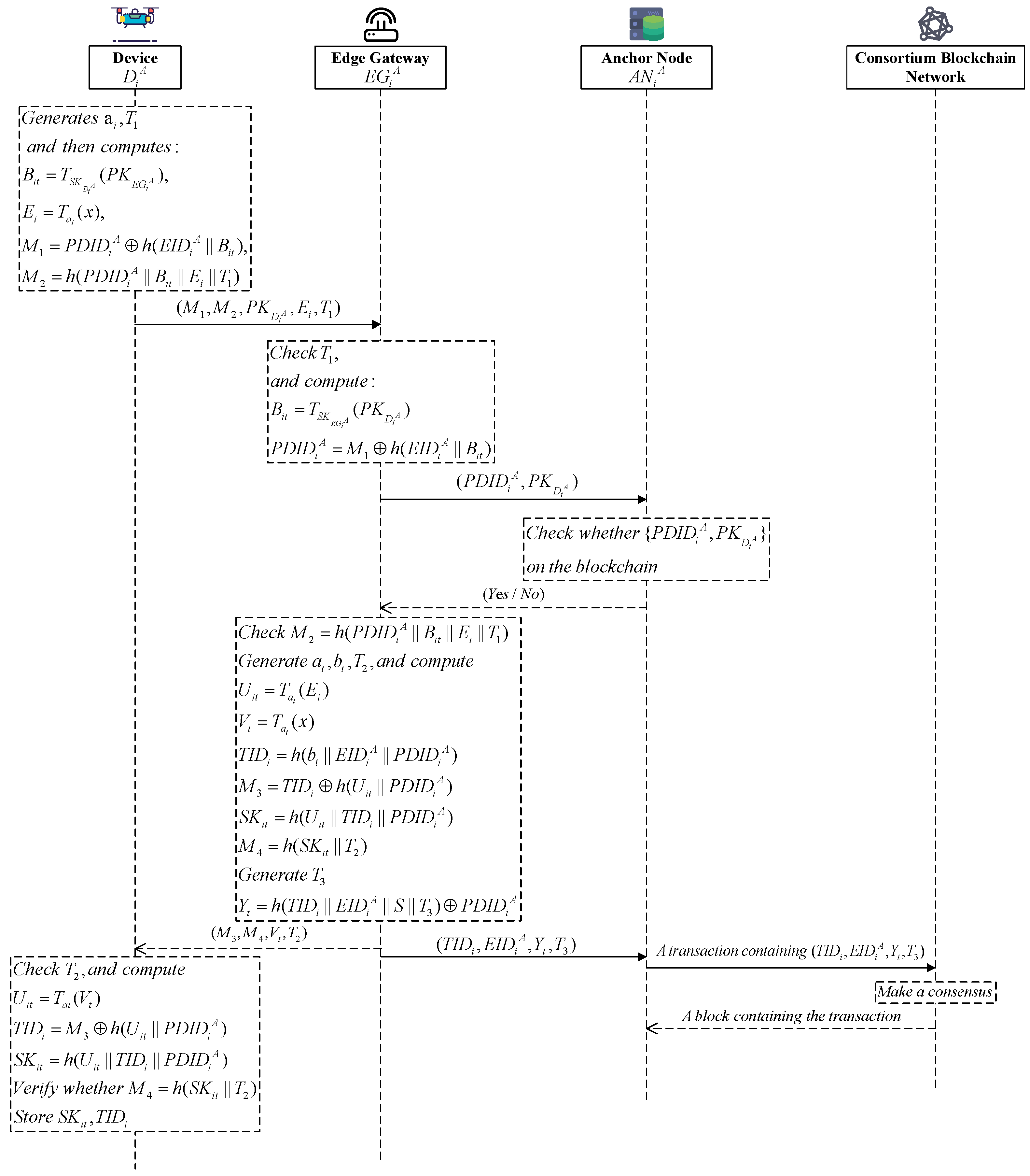
6.2. Intra-Domain Device Mutual Authentication
After the registration phase of Device
is completed, it can perform mutual authentication with Edge Gateway
in the same Domain A. Here, we use Domain A as a concrete example of Domain X. As shown in
Figure 2, the authentication process is as follows:
(1) Initial authentication message from the device to the edge gateway. Device
retrieves the registration information of Edge Gateway
from the blockchain through the blockchain anchor node, generates a random number
and a timestamp
, and then computes
Device sends to , where is the identifier of Edge Gateway .
(2) Authentication verification by the edge gateway. Upon receiving the message, Edge Gateway
verifies whether the timestamp is within the valid range, i.e.,
, where
T is the current timestamp and
is the valid time that represents the maximum allowable round-trip time for messages under normal conditions. Its value should be determined through statistical analysis based on the specific scenario. If the timestamp is valid,
computes
Edge Gateway
checks whether
exists on the blockchain through the anchor node. If
exists on the blockchain and
, then
is successfully authenticated. Edge Gateway
then generates two random numbers
and
, along with
a timestamp
, and computes
sends
to
. Then,
generates a new timestamp
and computes
Edge Gateway uploads to the blockchain with the help of the associated anchor node. The successful recording of the message on the blockchain indicates that Device has successfully passed authentication by at time . Leveraging the immutability and transparency of the blockchain, edge gateways in other domains can quickly perform handover authentication for device Device via anchor nodes based on its initial authentication record stored on the blockchain.
(3) Authentication verification by the device. Upon receiving the message, Device
first checks the validity of the timestamp
, ensuring that
, where
T is the current timestamp.
Device verifies whether . If the values match, the authentication is successful, and the vehicle stores the session key and the temporary identity .
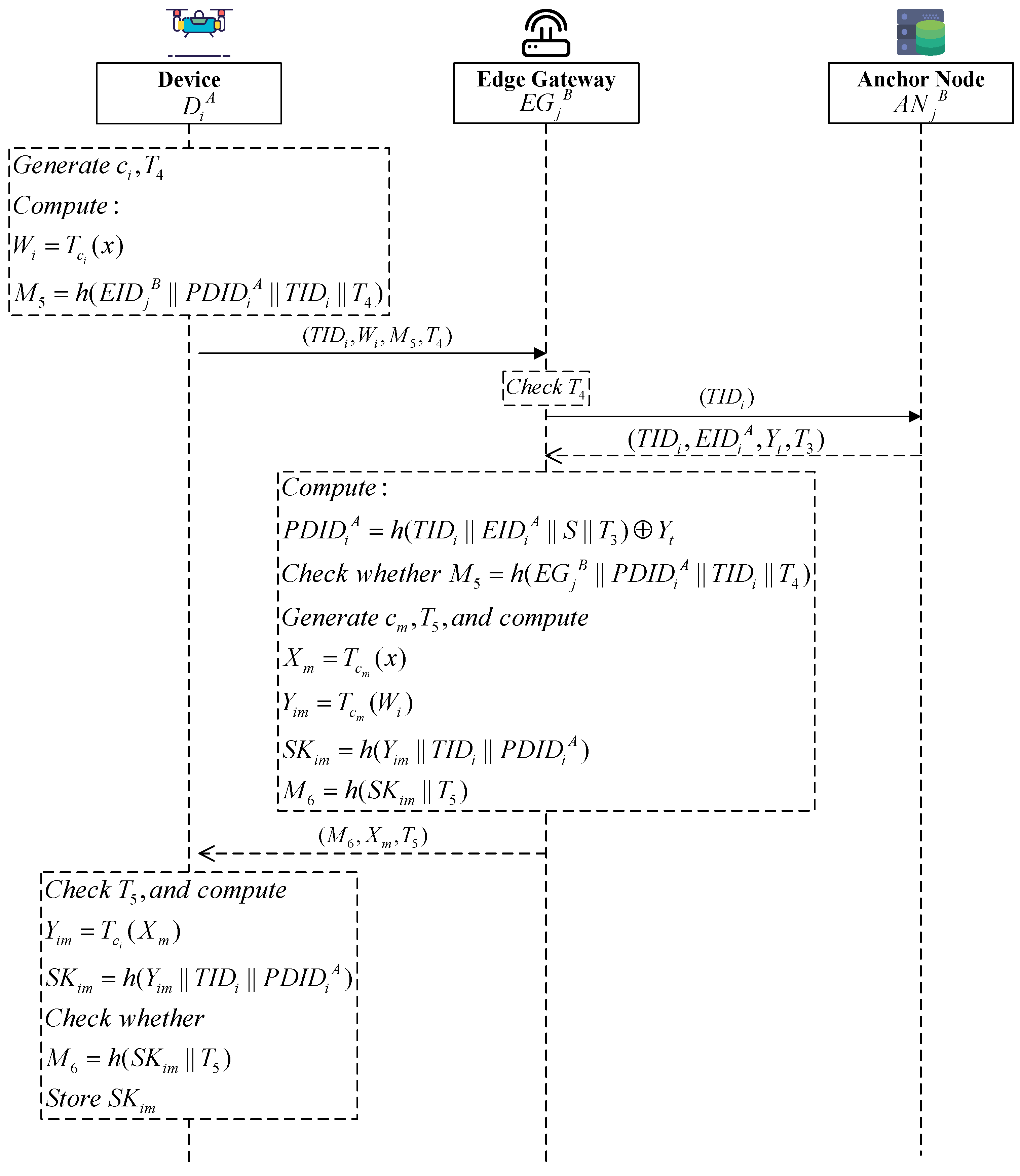
6.3. Cross-Domain Device Mutual Authentication
When Device moves into Domain B, Device and Edge Gateway should perform mutual authentication.
At this time, as shown in
Figure 3, the authentication process is as follows:
(1) Initial authentication message from the device to the edge gateway of another edge gateway. Device
generates a random number
and a timestamp
and then computes
Afterwards, Device sends to Edge Gateway .
(2) Authentication verification by the edge gateway. After receiving the message, Edge Gateway
checks the validity of the timestamp
by verifying C where
T is the current timestamp. If the timestamp is valid, Edge Gateway
then retrieves the authentication record
from the blockchain through the blockchain anchor node using
and computes
Edge Gateway
verifies whether
. If they are equal, Device
is successfully authenticated. Then, Edge Gateway
generates
and a timestamp
and then computes
Edge Gateway sends to Device .
(3) Authentication verification by the device. After receiving the information, Device
checks the validity of the timestamp
by verifying whether
. If the timestamp is valid, Device
then computes
Device verifies whether . If they are equal, the device stores the session key .
7. Security Analysis
We have demonstrated the security of the proposed method using both informal and formal approaches.
7.1. Informal Security Analysis
(1) Mutual Authentication: Edge Gateway can obtain and the public key from the message sent by Device and retrieve the device’s registration information from the blockchain through the anchor node. Edge Gateway in a different domain can also retrieve the verification record containing from the blockchain through the anchor node. By using and the verification record, both and can authenticate Device . Device can receive during the intra-domain authentication phase and during the cross-domain handover authentication phase. By utilizing and , Device can confirm that the messages are from Edge Gateway and Edge Gateway , respectively. As a result, the proposed protocol supports mutual authentication.
(2) Session Key Agreement: Device generates session keys and during intra-domain authentication and cross-domain handover authentication, respectively. An attacker may attempt to compute the session keys; however, without solving the discrete logarithm problem, the attacker cannot compute and . Therefore, the attacker is unable to obtain the session keys and .
(3) Replay Attack: Each authentication message contains a timestamp. The receiver verifies the timestamp before performing any processing. If the timestamp is invalid, the receiver will discard the received message. This mechanism prevents attackers from replaying previously captured messages.
(4) Man-in-the-Middle Attack: Even if an attacker captures messages transmitted over public channels, they are unable to forge or modify the messages, because the attacker cannot obtain the valid parameters contained in the hash values of . Therefore, the proposed scheme can effectively defend against man-in-the-middle attacks.
(5) Impersonation Attack: A malicious Device may attempt to impersonate the legitimate Device . However, during intra-domain authentication, cannot obtain and the private key of . Therefore, it is unable to impersonate or generate a legitimate authentication request message during cross-domain authentication.
(6) Anonymity: During the authentication phase, Device uses a pseudonym for verification; therefore, its real identity is not exposed during the authentication process. In addition, the temporary identity contains a random number , making it impossible for an attacker to obtain any identity information about Device through . Thus, the proposed protocol can ensure the anonymity of the device.
(7) Short-Term Key Exposure: Even if the random numbers are exposed to an attacker, the attacker still cannot obtain . Since and , the attacker is unable to compute the session keys.
(8) Forward Security: In this protocol, the generation of session keys and requires and , which are generated by the device and the edge gateway during each authentication process based on random numbers. Even if an attacker knows all the long-term keys, they still cannot obtain or compute previous or current session keys. Therefore, the proposed protocol ensures forward security.
(9) Malicious Message Tracing: In the protocol proposed in this paper, the pseudonym of a legitimate device is assigned by the edge gateway, where , with being the real identity of the device and being the private key of Edge Gateway . Therefore, is unforgeable. When a legitimate user sends malicious messages, the edge gateway can trace back to the user’s real identity by decrypting .
7.2. Formal Security Analysis
During the authentication phase, another session key is established between the device and the edge gateway. In this section, it will be proven that the established session key is secure under the ROR (Real-Or-Random) model. Definition 1 provides the security definition of session keys within the ROR model. In the proposed cross-domain authentication model, there are three types of entities: Device , Edge Gateway , and Edge Gateway . Each type of entity contains multiple instances. Let denote the t-th instance of an entity. Then, , , and represent instances of , , and , respectively. All instances are treated as random oracles. Additionally, the adversary A is allowed to make the following queries:
(1) : The adversary A can perform this query to simulate an eavesdropping attack and obtain all the information exchanged between entities.
(2) : By performing this query, the adversary A can simulate an active attack by sending a message m to the entity and obtaining the response information from that entity.
(3) : The adversary A performs this query to obtain the session key of Entity . If does not have a session key, the query returns an undefined symbol ⊥; otherwise, it returns the session key of .
(4) : This query simulates the semantic security of the session key between entities. When the adversary A performs this query, if Entity does not have a defined session key, or if A has previously issued a REVEAL query to or any of its partners, the query returns an undefined symbol ⊥. Otherwise, randomly generates a bit c, and the output is kept secret from the adversary A. If , the real session key is returned; if , a random number of the same length as the session key is returned.
Next, we will use these queries to prove the semantic security of the proposed method. In an authentication protocol, the semantic security proof plays a crucial role by providing formal guarantees of confidentiality and resistance to attacks in the presence of adversaries.
Theorem 1 (Semantic Security)
. Let denote the semantic security advantage of adversary A in breaking the proposed protocol within polynomial time , in order to obtain the session key between and during the initial authentication phase and the session key between and during the handover authentication phase. Let ,, and represent, respectively, the number of hash queries made, the output space of the one-way collision-resistant hash function , and the adversary’s advantage in solving the chaotic map-based discrete logarithm problem. Then, Proof. The adversary
A can engage in three independent games
(where
) using the allowed queries. At the end of each game, if
A can correctly guess whether the bit
c in game
corresponds to the real session key or a random number, then
A is considered to have won the game. Let
denote the event that
A wins game
. Therefore, the advantage of
A in winning game
is defined as
Here, denotes the probability of event E. The games conducted by adversary A are as follows:
: Game
simulates a real attack launched by adversary A against the protocol under the ROR model. Since the probability that
A correctly guesses the bit
c is equal to the probability that A successfully breaks the real scheme, it follows from the definition of semantic security that
: Within the game, adversary A carries out an eavesdropping attack through the EXECUTE query. The adversary A can obtain the messages and exchanged during the initial authentication phase, as well as the messages and exchanged during the handover authentication phase.
Subsequently,
A may also perform REVEAL and TEST queries to determine whether the returned bit
c corresponds to a real session key or a random function. However, the values
contain random parameters
, which
A cannot obtain. Therefore,
A is unable to extract any useful information. In this round of the game,
A’s winning probability does not increase. Thus,
A’s advantage in winning game
is equal to that in
:
: In this game, the adversary
A simulates an active attack by performing hash and SEND queries, attempting to forge messages that deceive the protocol participants into believing they are legitimate authentication messages. The game terminates only if
A successfully constructs a valid message. During the initial authentication phase, A attempts to forge the message
, where
. To obtain the parameters
and
,
A must solve the CMDLP problem to compute
or, alternatively, find a hash collision to forge the message. Similarly, in the cross-domain handover authentication phase, A also needs to solve the CMDLP problem or find a hash collision. If hash collisions and CMDLP-solving capabilities are excluded in game
, A’s advantage in winning
is the same as in
. Based on the birthday paradox, the likelihood of a hash collision can be estimated as
. Therefore,
A’s advantage in winning game
is given by
At this point, A has completed all queries. In order to win game
, A performs the TEST query and then randomly guesses the bit
c. Therefore,
By using Equations (1)–(4), the following equation can be derived:
By multiplying both sides of Equation (5) by 2, we obtain
Theorem 1 is thus proved, and the advantage of adversary A is negligible. Therefore, the session key in the proposed protocol is semantically secure under the ROR model. □
8. Result Analysis
This paper compares the proposed protocol’s computational and communication overhead with existing cross-domain authentication protocols that are currently the most efficient and cost-effective works. For a fair evaluation, the compared schemes are all assumed to have security levels equivalent to the Advanced Encryption Standard (AES) 128-bit. Specifically, the key length for symmetric encryption and decryption is 128 bits, the key length for elliptic curve encryption is 256 bits, the hash function output is 256 bits, and the lengths of random numbers and identity identifiers are 128 bits. The timestamp length is 32 bits. According to reference [
43], since the Chebyshev discrete logarithm problem can only be solved through exhaustive search, this paper assumes that the key length of the Chebyshev polynomial is 128 bits.
8.1. Computation Cost
This section evaluates the computational overhead of the proposed cross-domain handover authentication protocol and compares it with other protocols. The experiments were conducted in an environment with a quad-core Intel(R) Core(TM) i7-8750H 2.20GHz CPU, 16GB RAM (Intel, Santa Clara, CA, USA), and the operating system Ubuntu-22.04.4-desktop-amd64. Various cryptographic primitives were implemented using the MIRACL cryptographic library. In addition, the matrix iteration algorithm was used to write the corresponding C language code for testing the computation time of Chebyshev polynomials. Since the execution time of the XOR operation is negligible, it was ignored in the evaluation. The data is generated from the experiments implemented by MIRACL cryptographic library and Hyperledger Fabric frameworks.
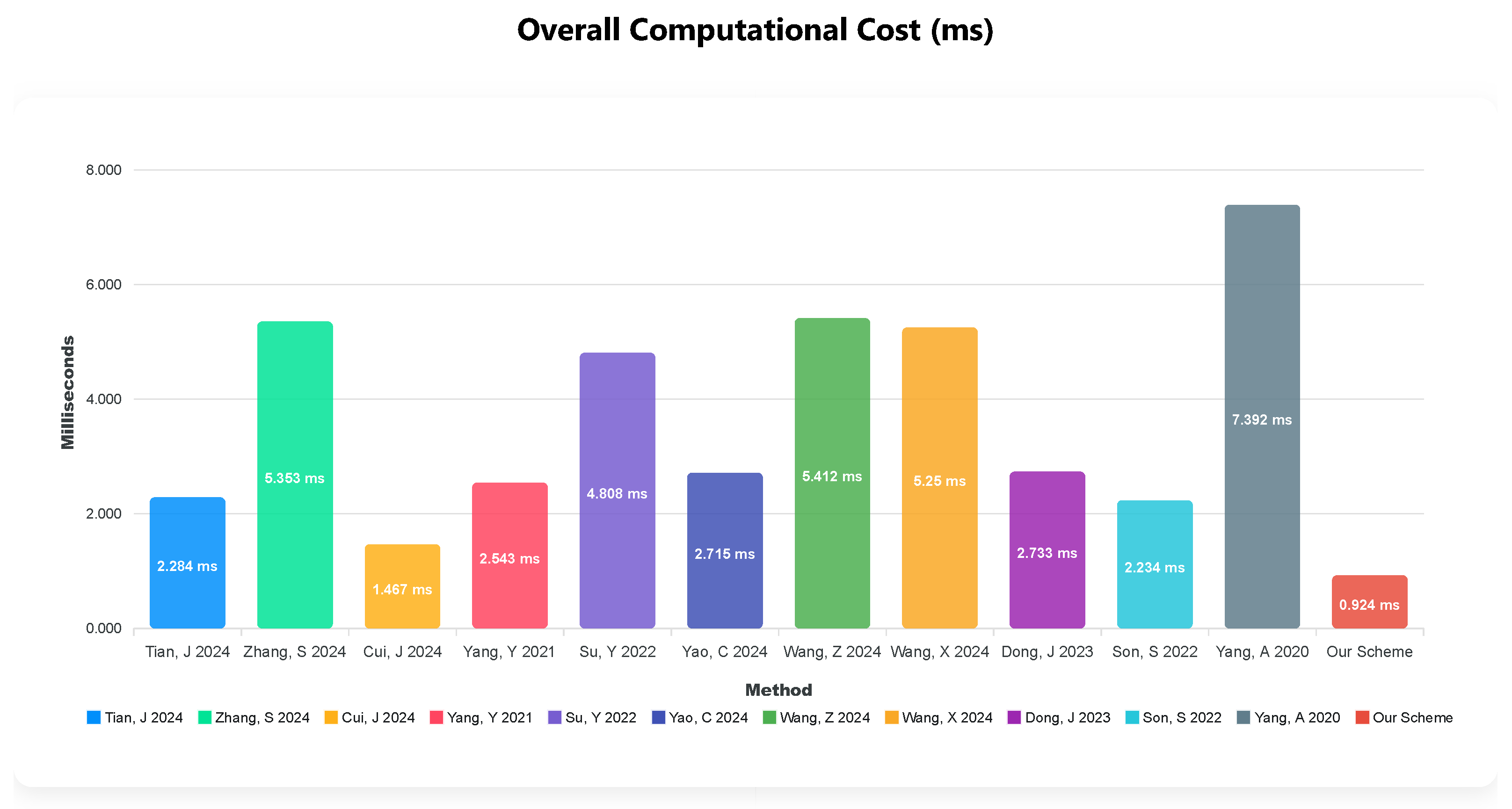
Table 2 and
Figure 4 present the execution times of various cryptographic primitives.
In the cross-domain handover authentication protocol proposed in this paper, the device side performs three hash operations and two Chebyshev chaotic map computations, with an execution time of ms. On the edge gateway side, four hash operations and two Chebyshev polynomial computations are carried out, resulting in an execution time of ms. Therefore, the total computational overhead is 0.924 ms.
According to the computational overhead comparison in
Table 3, bilinear pairing operations incur significantly higher costs. As shown in
Figure 5, the scheme in Reference [
44] exhibits the highest computational overhead, while the proposed protocol incurs the lowest. This efficiency stems from the use of the semigroup property of Chebyshev polynomials to establish session keys, thereby avoiding computationally intensive operations such as bilinear pairing and elliptic curve point multiplication.
The proposed protocol thus achieves low computational overhead while ensuring security, making it a lightweight and efficient solution.
8.2. Communication Cost
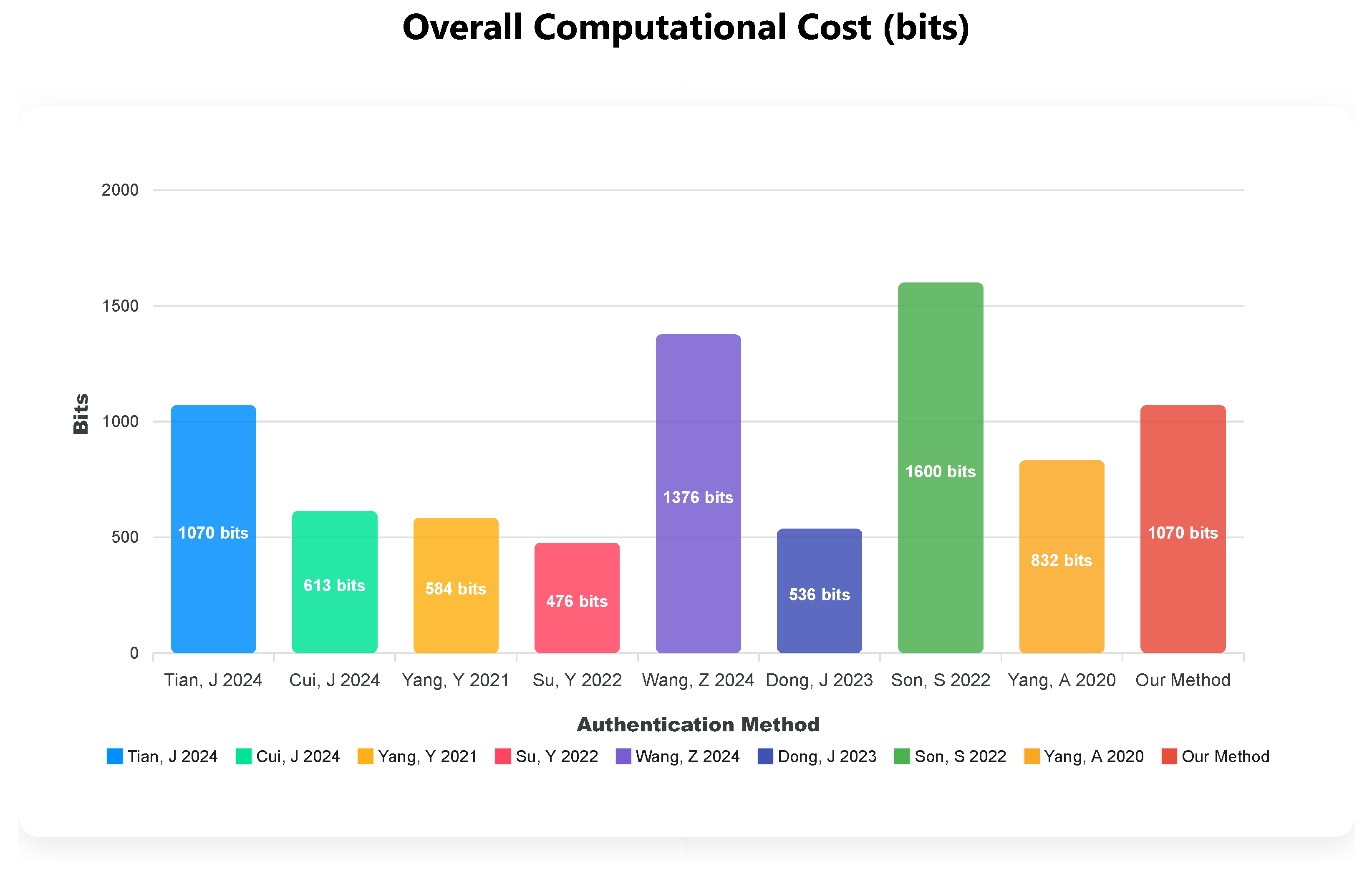
Table 4 lists the communication overhead between the device and the edge gateway for the proposed cross-domain handover authentication protocol and the comparison schemes. It is worth noting that
Table 4 does not cover all methods listed in
Table 3, as not all of the related works conducted experiments on communication overhead. As shown in
Table 4, the proposed protocol involves the exchange of two messages. Specifically, the device sends the message
to the edge gateway, resulting in a communication overhead of 660 bits on the device side. In response, the edge gateway sends the message
to the device, with a corresponding overhead of 410 bits. Therefore, the total communication overhead is 1070 bits. While our method may not be the most optimal in terms of communication cost, as shown in
Figure 6, it provides a superior trade-off by achieving the best computational efficiency, making it highly suitable for resource-constrained IIoT environments.
8.3. Authentication Latency
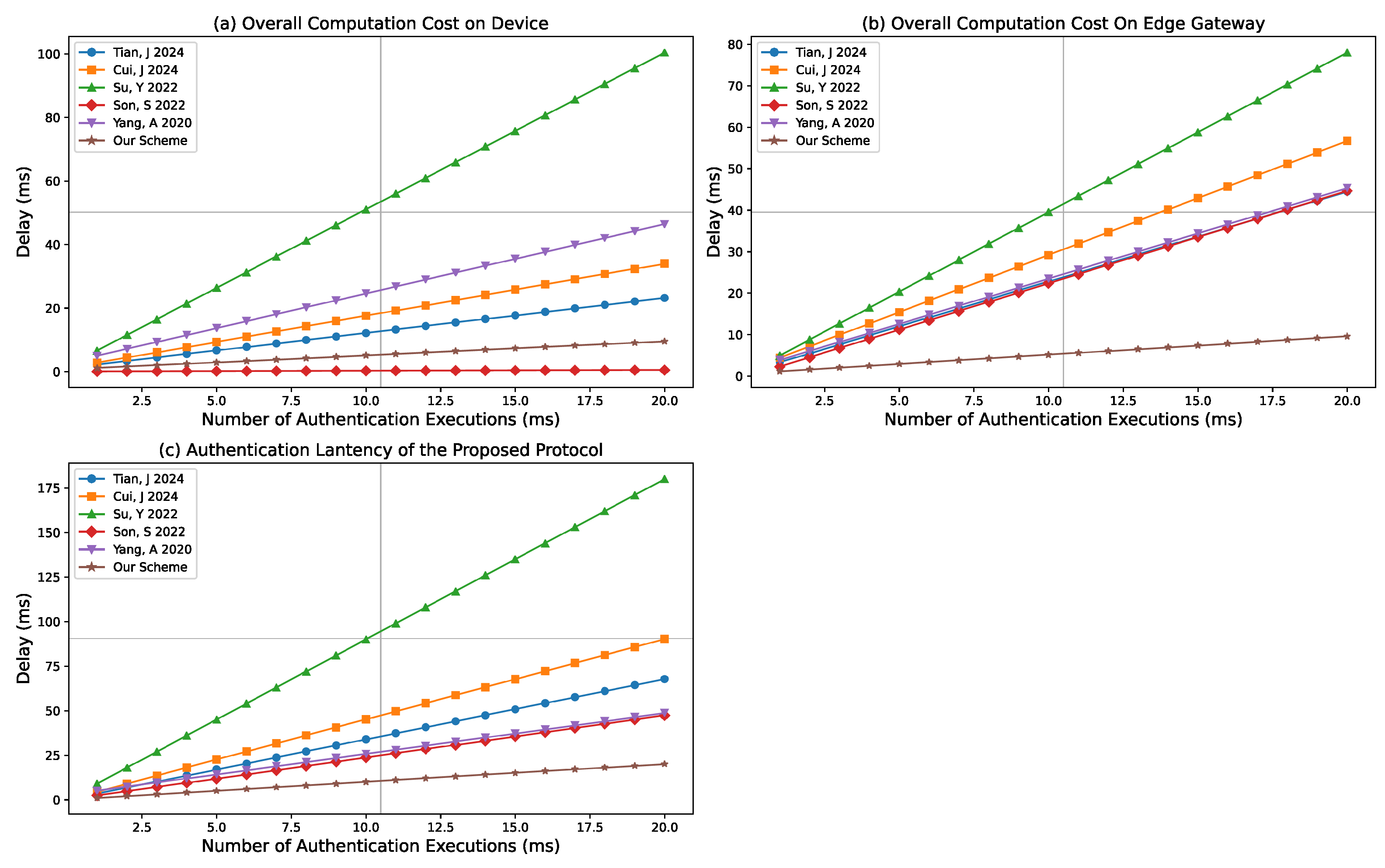
Authentication latency means the delay was caused by the mutual authentication, which contains the computation time both on device and edge gateway and the message propagation time.
From the device’s perspective, as the number of cross-domain authentications
m increases, the local computation delay can be expressed as
, where
represents the computation time required during the initialization phase and
denotes the computation delay incurred during mutual authentication with edge gateways in different domains. In contrast, the local computation delays of the device for the scheme [
4,
10,
17,
44,
45] are
,
,
,
, and
, respectively. As illustrated in
Figure 7a, the scheme [
45] exhibits the lowest computation delay, as it relies solely on hash operations for device-to-gateway authentication. Our scheme achieves the second-lowest computation overhead by replacing computationally intensive elliptic curve scalar multiplication and addition with Chebyshev chaotic map operations.
From the perspective of the edge gateway, as the number of cross-domain authentications
m increases, the local computation delay can be expressed as
, where
represents the computation time required during the initialization phase and
denotes the computation delay incurred during mutual authentication with devices from other domains. In comparison, the local computation delays of the edge gateway for the scheme [
4,
10,
17,
44,
45] are
,
,
,
, and
, respectively. As illustrated in
Figure 7b, our proposed scheme achieves the lowest computation delay on the edge gateway side, outperforming scheme [
45]. This is because scheme [
45] offloads the computationally intensive elliptic curve operations required for device authentication onto the more powerful edge gateway, whereas our scheme avoids such operations entirely by adopting lightweight Chebyshev chaotic map-based computations.
Above all, the overall authentication latency can be approximated as
, where
denotes the message transmission delay from the device to the edge gateway and
represents the latency associated with querying the blockchain. According to [
44],
is approximately 100 ms, and based on our experimental results,
is around 15 ms. In comparison, the total authentication latencies of schemes [
4,
10,
17,
44,
45] are
,
,
,
, and
, respectively. As illustrated in
Figure 7c, our proposed scheme achieves the lowest overall authentication latency, benefiting from the use of lightweight Chebyshev chaotic map operations in place of computationally expensive elliptic curve operations.
9. Conclusions
In this paper, we propose a lightweight and secure cross-domain authentication scheme for the Industrial Internet of Things (IIoT) by integrating blockchain technology with Chebyshev chaotic maps. The proposed method effectively addresses the critical challenges of identity fragmentation, computational complexity, and communication latency that plague traditional blockchain-based authentication frameworks. By leveraging the decentralized and tamper-resistant nature of blockchain for device identity management and employing the semigroup property of Chebyshev polynomials to facilitate efficient session key generation, our scheme ensures both robustness and performance in resource-constrained and latency-sensitive industrial environments. A formal security analysis based on the Real-Or-Random (ROR) model confirms that the protocol satisfies key security requirements, including mutual authentication, resistance to various attacks, anonymity, and forward secrecy. Furthermore, empirical evaluations using the Hyperledger Fabric platform and the MIRACL cryptographic library demonstrate that our scheme achieves lower computational and communication overhead compared to existing solutions, without compromising on security. Overall, the proposed authentication framework presents a promising direction for enhancing trust and efficiency in cross-domain collaborations within IIoT systems. Future work may explore the integration of privacy-preserving techniques and scalability optimizations to further adapt the scheme to emerging industrial scenarios and large-scale deployments.
Author Contributions
Conceptualization, Z.Z.; methodology, Z.Z.; software, J.L.; validation, Z.Z. and X.L.; formal analysis, X.Z.; investigation, Z.Z.; resources, J.M.; data curation, Z.Z.; writing—original draft preparation, Z.Z. and J.L.; writing—review and editing, C.J. and Y.M.; visualization, X.L.; supervision, C.J.; project administration, Z.Z.; funding acquisition, Z.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Huaian Science and Technology Plan Project Natural Science Research grant number HAB2024048.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors on request.
Conflicts of Interest
The authors report no conflicts of interest. The funding sources did not influence the study’s design, data collection, analysis, interpretation, or manuscript preparation or the decision to publish the findings.
Abbreviations
The following abbreviations are used in this manuscript:
| ROR | Real-Or-Random |
| CAGR | compound annual growth rate |
| PKI | Public Key Infrastructure |
| IBC | identity-based cryptography |
| CL-PKC | Certificateless Public Key Cryptography |
| ECC | elliptic curve cryptography |
| IIoT | Industrial Internet of Things |
| CA | Certificate Authority |
| KGC | Key Generation Center |
| CMDDHP | Chaotic Maps Decisional Diffie–Hellman Problem |
|
PoW
|
Proof of Work
|
|
PoS
|
Proof of Stake
|
|
PBFT
|
Practical Byzantine Fault Tolerance
|
References
- Hu, Y.; Jia, Q.; Yao, Y.; Lee, Y.; Lee, M.; Wang, C.; Zhou, X.; Xie, R.; Yu, F. Industrial internet of things intelligence empowering smart manufacturing: A literature review. IEEE Internet Things J. 2024, 11, 19143–19167. [Google Scholar] [CrossRef]
- Industrial IoT Industry Worth $286.3 Billion by 2029. Available online: https://www.marketsandmarkets.com/PressReleases/industrial-internet-of-things.asp (accessed on 18 June 2025).
- Alsheavi, A.; Hawbani, A.; Othman, W.; Wang, X.; Qaid, G.; Zhao, L.; Al-Dubai, A.; Zhi, L.; Ismail, A.; Jhaver, R.; et al. IoT Authentication Protocols: Challenges, and Comparative Analysis. ACM Comput. Surv. 2025, 57, 1–43. [Google Scholar] [CrossRef]
- Tian, J.; Shen, Y.; Wang, Y. Blockchain-based fast handover authentication protocol for Internet of Vehicles in small industrial parks. Veh. Commun. 2024, 50, 100848. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, A.; Xia, Y.; Hu, B.; Liu, J.; Wu, Q.; Tiwari, P. A Blockchain-Based Cross-Domain Authentication Management System for IoT Devices. IEEE Trans. Netw. Sci. Eng. 2023, 11, 115–127. [Google Scholar] [CrossRef]
- Khan, S.; Luo, F.; Zhang, Z.; Ullah, F.; Amin, F.; Qadri, S.; Heyat, M.; Ruby, R.; Wang, L.; Ullah, S.; et al. A survey on X. 509 public-key infrastructure, certificate revocation, and their modern implementation on blockchain and ledger technologies. IEEE Commun. Surv. Tutorials 2023, 25, 2529–2568. [Google Scholar] [CrossRef]
- Wang, M.; Rui, L.; Yang, Y.; Gao, Z.; Chen, X. A Blockchain-Based Multi-CA Cross-Domain Authentication Scheme in Decentralized Autonomous Network. IEEE Trans. Netw. Serv. Manag. 2022, 19, 2664–2676. [Google Scholar] [CrossRef]
- Zhang, S.; Yan, Z.; Liang, W.; Li, K.; Martino, B. BCAE: A Blockchain-Based Cross Domain Authentication Scheme for Edge Computing. IEEE Internet Things J. 2024, 11, 24035–24048. [Google Scholar] [CrossRef]
- Tong, F.; Chen, X.; Wang, K.; Zhang, Y. CCAP: A complete cross-domain authentication based on blockchain for Internet of Things. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3789–3800. [Google Scholar] [CrossRef]
- Cui, J.; Zhu, Y.; Zhong, H.; Zhang, Q.; Gu, C.; He, D. Efficient blockchain-based mutual authentication and session key agreement for cross-domain IIoT. IEEE Internet Things J. 2024, 11, 16325–16338. [Google Scholar] [CrossRef]
- Cui, J.; Liu, N.; Zhang, Q.; He, D.; Gu, C.; Zhong, H. Efficient and anonymous cross-domain authentication for IIoT based on blockchain. IEEE Trans. Netw. Sci. Eng. 2024, 10, 899–910. [Google Scholar] [CrossRef]
- Zhang, H.; Zhao, F. Cross-domain identity authentication scheme based on blockchain and PKI system. High-Confid. Comput. 2023, 3, 100096. [Google Scholar] [CrossRef]
- Saleem, T.; Janjua, M.U.; Hassan, M.; Ahmad, T.; Tariq, F.; Hafeez, K.; Salal, M.A.; Bilal, M.D. ProofChain: An X. 509-compatible blockchain-based PKI framework with decentralized trust. Comput. Networks 2022, 213, 109069. [Google Scholar] [CrossRef]
- Yang, Y.; Wei, L.; Wu, J.; Long, C.; Li, B. A Blockchain-Based Multidomain Authentication Scheme for Conditional Privacy Preserving in Vehicular Ad-Hoc Network. IEEE Internet Things J. 2021, 9, 8078–8090. [Google Scholar] [CrossRef]
- Luo, D.; Cai, Q.; Sun, G.; Yu, H.; Niyato, D. Split-chain based efficient blockchain-assisted cross-domain authentication for IoT. IEEE Trans. Netw. Serv. Manag. 2024, 21, 3209–3223. [Google Scholar] [CrossRef]
- Su, Y.; Wang, Y.; Li, J.; Su, Z.; Pedrycz, W.; Hu, Q. Oracle based privacy-preserving cross-domain authentication scheme. IEEE Trans. Sustain. Comput. 2024, 9, 602–614. [Google Scholar] [CrossRef]
- Xue, L.; Huang, H.; Xiao, F.; Wang, W. A cross-domain authentication scheme based on cooperative blockchains functioning with revocation for medical consortiums. IEEE Trans. Sustain. Comput. 2022, 19, 2409–2420. [Google Scholar] [CrossRef]
- Manasrah, A.; Yaseen, Q.; Al-Aqrabi, H.; Liu, L. Identity-Based Authentication in VANETs: A Review. IEEE Trans. Intell. Transp. Syst. 2025, 26, 4260–4282. [Google Scholar] [CrossRef]
- Xiong, H.; Gong, L.; Li, R.; Kumari, S.; Chen, C.; Amoon, M. Blockchain-enabled distributed identity-based ring signature with identity abort for consumer electronics. IEEE Trans. Consum. Electron. 2024, 70, 5340–5352. [Google Scholar] [CrossRef]
- Zhang, C.; Zhao, M.; Zhang, W.; Fan, Q.; Ni, J.; Zhu, L. Privacy-preserving identity-based data rights governance for blockchain-empowered human-centric metaverse communications. IEEE J. Sel. Areas Commun. 2023, 42, 963–977. [Google Scholar] [CrossRef]
- Li, R.; Wang, Z.; Fang, L.; Peng, C.; Wang, W.; Xiong, H. Efficient blockchain-assisted distributed identity-based signature scheme for integrating consumer electronics in metaverse. IEEE Trans. Consum. Electron. 2024, 70, 3770–3780. [Google Scholar] [CrossRef]
- Li, B.; Ma, M. An advanced hierarchical identity-based security mechanism by blockchain in named data networking. J. Netw. Syst. Manag. 2023, 31, 13. [Google Scholar] [CrossRef]
- Yang, Y.; He, D.; Vijayakumar, P.; Gupta, B.; Xie, Q. An efficient identity-based aggregate signcryption scheme with blockchain for IoT-enabled maritime transportation system. IEEE Trans. Green Commun. Netw. 2022, 6, 1520–1531. [Google Scholar] [CrossRef]
- Babu, E.; Dadi, A.; Singh, K.; Nayak, S.; Bhoi, A.; Singh, A. A distributed identity-based authentication scheme for internet of things devices using permissioned blockchain system. Expert Syst. 2022, 39, e12941. [Google Scholar] [CrossRef]
- Srivastava, V.; Debnath, S.; Bera, B.; Das, A.; Park, Y.; Lorenz, P. Blockchain-envisioned provably secure multivariate identity-based multi-signature scheme for Internet of Vehicles environment. IEEE Trans. Veh. Technol. 2022, 71, 9853–9867. [Google Scholar] [CrossRef]
- Zhang, J.; Zhang, F. Identity-Based Key Agreement for Blockchain-Powered Intelligent Edge. IEEE Internet Things J. 2021, 9, 6688–6702. [Google Scholar] [CrossRef]
- Sharma, P.; Moparthi, N.; Namasudra, S.; Shanmuganathan, V.; Hsu, C. Blockchain-based IoT architecture to secure healthcare system using identity-based encryption. Expert Syst. 2022, 39, e12915. [Google Scholar] [CrossRef]
- Yao, C.; Zhang, X.; Liu, Y.; Zhao, B.; Wu, Q.; Susilo, W. Blockchain-Based Secure and Efficient ADS-B Authentication via Certificateless Signature With Packet Loss Tolerance. IEEE Internet Things J. 2024, 12, 10574–10588. [Google Scholar] [CrossRef]
- Zhang, J.; Chen, X.; Cheng, Q.; Chen, X.; Luo, X. An Enhanced Certificateless Blockchain-Assisted Authentication and Key Agreement Protocol for Internet of Drones. IEEE Trans. Netw. Sci. Eng. 2025, 12, 3065–3081. [Google Scholar] [CrossRef]
- Wang, Z.; Zong, Z.; Li, F.; Sun, S.; Zhao, P. Revocable Certificateless Cross-Domain Authentication Scheme Based on Primary—Secondary Blockchain. IEEE Trans. Comput. Soc. Syst. 2024, 11, 5880–5891. [Google Scholar] [CrossRef]
- Feng, L.; Qiu, F.; Hu, K.; Yu, B.; Lin, J.; Yao, S. CABC: A Cross-Domain Authentication Method Combining Blockchain with Certificateless Signature for IIoT. Future Gener. Comput. Syst. 2024, 158, 516–529. [Google Scholar] [CrossRef]
- Wang, X.; Wang, W.; Huang, C.; Cao, P.; Zhu, Y.; Wu, Q. Blockchain-based certificateless conditional anonymous authentication for IIoT. IEEE Syst. J. 2024, 18, 656–667. [Google Scholar] [CrossRef]
- Dong, J.; Xu, G.; Ma, C.; Liu, J.; Cliff, U. Blockchain-based certificate-free cross-domain authentication mechanism for industrial internet. IEEE Internet Things J. 2023, 11, 3316–3330. [Google Scholar] [CrossRef]
- Liu, X.; Wang, L.; Li, L.; Zhang, X.; Shufen, N. Certificateless Anonymous Cross-Domain Authentication Scheme Assisted by Blockchain for Internet of Vehicles. Wirel. Commun. Mob. Comput. 2022, 2022, 3488977. [Google Scholar] [CrossRef]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. Proc. Thirteen. Eurosys Conf. 2018, 1–15. [Google Scholar] [CrossRef]
- Pigatto, D.; Silva, N.; Branco, K. Performance evaluation and comparison of algorithms for elliptic curve cryptography with El-Gamal based on MIRACL and RELIC libraries. J. Appl. Comput. Res. 2011, 1, 95–103. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 18 June 2025).
- Gavin, W. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2008, 151, 1–32. [Google Scholar]
- Miguel, C.; Liskov, B. Practical byzantine fault tolerance. OsDI 1999, 99, 173–186. [Google Scholar]
- Abbasinezhad-Mood, D.; Nikooghadam, M. Efficient design of a novel ECC-based public key scheme for medical data protection by utilization of NanoPi fire. IEEE Trans. Reliab. 2018, 67, 1328–1339. [Google Scholar] [CrossRef]
- Zhu, H.; Zhang, Y.; Xia, Y.; Li, H. Password-Authenticated Key Exchange Scheme Using Chaotic Maps towards a New Architecture in Standard Model. Int. J. Netw. Secur. 2016, 18, 326–334. [Google Scholar]
- Abbasinezhad-Mood, D.; Ostad-Sharif, A.; Mazinani, S.; Nikooghadam, M. Provably secure escrow-less Chebyshev chaotic map-based key agreement protocol for vehicle to grid connections with privacy protection. IEEE Trans. Ind. Inform. 2020, 16, 7287–7294. [Google Scholar] [CrossRef]
- Ma, R.; Cao, J.; Feng, D.; Li, H.; Li, X.; Xu, Y. A robust authentication scheme for remote diagnosis and maintenance in 5G V2N. Veh. Commun. 2022, 198, 103281. [Google Scholar] [CrossRef]
- Yang, A.; Weng, J.; Yang, K.; Huang, C.; Shen, X. Delegating authentication to edge: A decentralized authentication architecture for vehicular networks. IEEE Trans. Intell. Transp. Syst. 2020, 23, 1284–1298. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).